


Schritt 1 - Mulitple Protection - The Basic Security Level
starting situation |
groundworking theory - the security-functions |
The essential idea |
ISO-LSB-OpenSource with Changelogs |
beautiful KDE (4.4.5, mdv, el6: "The cows are prettier than the girls!") |
Hardware: driver, support, hardware-databasis |
SSD optimization |
seachengine/Gooken |
data bases |
anonymous proxy |
fundamental theory |
security concepts |
data backup and restore |
(no) updates (at last up from year 2026, "UNIX", german: "you? no.": Miro´s suneater has spoken so far, hugh!): "UNIVERSAL-LINUX" on the DAILY UPDATE-PATCH-CHANNEL (el6, el7, rosa2014.1) |
Secure and stable "Universal-Linux": updates and actualizations for CentOS 6 (el6) and Mandriva |
emulation of MS Windows |
emulation of MS Windows |
update firefox |
Ad- resp. Scriptblocker: blocking everything |
msec-security-levels ( level.secure: no-remote-root-login, no root-login, ... and perm.secure) |
msec -MAC Tomoyo-Linux (mdv2010/el6) - Advanced Acess-Control for the process-interaction |
Ordinary access control as part of msec |
ACL - Advanced Access Control on files and directories for user and groups, in order to prevent brakes for example |
/etc/passwd - allen entkommen: no login-shell accessible |
Linux-Sandboxes: docker and firejail: to start programs going online |
Root-Partition with enough memory free |
Root-Partition read-only |
New Kernel - Howto install and Howto patch Kernel-Sources resp. Kernel-Source |
full system encryption (FSE) by LUKS |
encrypting methods |
LAN: connecting Linux- and Windows-hosts, file release |
anti-hacker and anti-trojan iptables/Linfw3 |
additional filter-concepts |
Konqueror: integrated script- and adblocker, importable filter list from our update-side |
system integrity check: IDS (intrusion detection systems): incron, iptables by psd (linfw3), aide, ... |
installation following rootkit-scan |
Session |
Anonymized (and encrypted) name resolution without censorship and surveys by DNS-Proxy pdnsd with dnscrypt-proxy and /etc/hosts |
Goal or own goal (Goal-Tor or self-goal)? TOR, the onion-router: Anonymization-Network |
Program troubleshooting |
Network Troubleshooting |
X-Troubleshooting (x11-server) |
Clever and Smart: All for the "little elephant": Printer Troubleshooting (CUPS) |
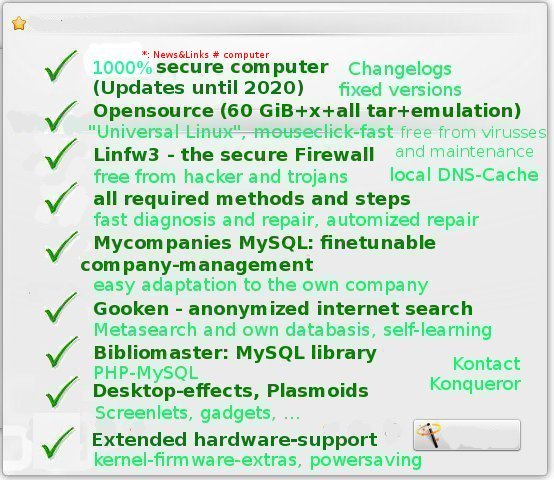
News&Links: All (and more) about the computer, repair, network, printer, tips and tricks, more Troubleshooting |
single methods and repair |
WLAN |
CIAO hardware-problems! Just hot and still functioning today: datasheed "certified lifetime-hardware" (energy saving, mouseclick-fast): Operating System: mdv2010.2 (updated with CentOS/EPEL (el6, el7) and Rosa on the update-channel pro-linux.de, All-in-one-Mainboard (from year 2009/2010, Mini-ITX-220/ASUS-Express 945GC/ICH7 with classical 1,2GHz-64-bit-Celeron-CPU up to 8 GB DDR-2 and INTEL GMA 950, 82945G/GZ Integrated Graphics Controller, max. 224MB 4800×1200 px, Atheros-Gigbit-Ethernet-LAN-Chip, VIA VT 1705 High Definition Audio-6-Kanal-HD-Azalia-Audio CODEC Soundsystem, 19W, socked and crashfree EZ-Bios AMI, 6×USB 2.0, MS Windows 7- and Linux-tested, 29,95€), 18,5 inch (48 cm) Ultraslim WLED-TFT-Monitor Brilliant Display (18W, 95€), SSD (1W, 128GB, 30&euro,), Steel-Computer-Tower with tower-cooler and front-LEDs, 4,95€, netadapter SL-A 500 W (19,95euro;), ...|
More than 1000 Linux-Top-Games (mdv2010 resp. rosa2014): OpenGL, SDL, PyGames and more |
mdv2010-final: Printer, Printer-Troubleshooting |
MS Windows: Tips and Tricks for more security |
mdv-2010-final: Software (65 GB + 50 GB (26 DVD ) |
CIAO hardware-problems: mdv-2010-final: powersaving hardware (stable and mouseclick-fast) |
Hardware (quit) for free |
Hardware for free |
Energy power for free (pyhsical motion incl.) |
World culture shame: Defrustration and dereaction for free |Sex for free |
money for free, country for free ("A revolution never took place", Niko.L.), system for free (FED, EZB, Draghi & Co.) |
Everything for free |
Complains and ads for free |
News&Links#Computer |
Everlasting Browser Konqueror: Download Konqueror-Update ( all rpm-based distributions? )|
Computer |
Monitor |
Printer / Drucker |
SSD |
Network / Netzwerk |
Smartphone |
MS Windows
Advertisement |
spends, thanksgiving and quiz |
Society - Computer - The Huge Fun of Sun Eating |
Society - Niue-Muenzen - Pay with Mickey Maus! |
No Horror in Sodom and Gomorrha: Weak point human ( weak point Germany ) - Society Report, Part 1-6 |
Society, Part 2 - Crawler´s Century (Book) |
Society Part 12 - Superrich.de (Forbes) - She got eyes of the bluest sky - and when there comes the rain ... ( open eye sleeping performances and arts ) - wet, wet, wet! |
Beauty on Gooken: 1000× more beautiful than you: Marching to die - Narcissism into death
Ads |
... unimprovable? News&Links |
BACK
From News&Links ( and all the essential security actions for Linux in this excurs... )
"2020: The world is lamed", STERN.de, 21.03.2020
https://www.stern.de/reise/deutschland/tourismus-in-zeiten-der-coronakrise---die-welt-ist-lahmgelegt---sagt-ury-steinweg-von-gebeco-9190342.html
"Uncanny, mad, horrible", tagesschau.de, 12.09.2020
Die Busch- und Waldbrände in Kalifornien gehören zu den Schlimmsten, die es je gab. Mehr als 12.500 Quadratkilometer sind von den Feuern betroffen. Und nicht nur Kalifornien, die gesamte Westküste der USA brennt.
https://www.tagesschau.de/ausland/kalifornien-waldbraende-135.html
Spend or pay Gooken by PayPal.me :
Pay by Paypal.me: Please click here! / Spenden oder zahlen Sie an Gooken: Bitte hier klicken!
 Continuation of the excurs form webside 1 (2/2)
Continuation of the excurs form webside 1 (2/2)
 Beware building network profiles within drakconf (MMC, mdv2010)! This can destroy the building up of connections in some situations. So delete all profiles out of network profiles, do not backup any of them here!
Depending on instructions within file INSTALL, ./config resp. cmake or similar commads are used instead. The session comes to an end with
Our system-reference collects such UNIX-commands.
 Configuration of /etc/sysctl.conf (rpm initscripts el6, mdv2010)
# etc/sysctl.conf
Configuration of /etc/sysctl.conf (rpm initscripts el6, mdv2010)
# etc/sysctl.conf
# Kernel sysctl configuration file for Mandriva Linux mixed up with Centos 6
#
# For binary values, 0 is disabled, 1 is enabled. See sysctl(8) and
# sysctl.conf(5) for more details.
net.ipv6.conf.lo.use_tempaddr = 0
# Disables IP dynaddr
net.ipv4.ip_dynaddr = 1
# Disable ECN
net.ipv4.tcp_ecn = 1
# Controls source route verification
net.ipv4.conf.all.rp_filter =1
net.ipv4.conf.default.rp_filter = 1
# Do not accept source routing
net.ipv4.conf.default.accept_source_route = 0
# Controls the System Request debugging functionality of the kernel
kernel.sysrq =0
# Controls whether core dumps will append the PID to the core filename.
# Useful for debugging multi-threaded applications.
kernel.core_uses_pid = 0
kernel.dmesg_restrict = 1
# If you set this variable to 1 then cd tray will close automatically when the
# cd drive is being accessed.
# Setting this to 1 is not advised when supermount is enabled
# (as it has been known to cause problems)
dev.cdrom.autoclose=1
# removed to fix some digital extraction problems
# dev.cdrom.check_media=1
# to be able to eject via the device eject button (magicdev)
dev.cdrom.lock=0
# Disable netfilter on bridges.
#net.bridge.bridge-nf-call-ip6tables = 0
#net.bridge.bridge-nf-call-iptables = 0
#net.bridge.bridge-nf-call-arptables = 0
net.ipv4.ip_forward =0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.tcp_max_syn_backlog =512
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
net.ipv4.tcp_syncookies = 1
net.ipv4.ip_local_port_range = 2000 65000
# Increase TCP max buffer size setable using setsockopt()
net.ipv4.tcp_rmem = 4096 87380 8388608
net.ipv4.tcp_wmem = 4096 87380 8388608
net.ipv6.conf.default.router_solicitations=0
net.ipv6.conf.default.accept_ra_rtr_pref=0
net.ipv6.conf.default.accept_ra_pinfo=0
net.ipv6.conf.default.accept_ra_defrtr=0
net.ipv6.conf.default.autoconf=0
net.ipv6.conf.default.dad_transmits=0
net.ipv6.conf.default.max_addresses=0
#
# https://en.wikipedia.org/wiki/TCP_congestion-avoidance_algorithm#TCP_CUBIC
# cat /proc/sys/net/ipv4/tcp_congestion_control
# modprobe tcp_htcp
# modprobe tcp_cubic
# modprobe tcp_bbr
# net.core.default_qdisc=sch_fq_codel
net.ipv4.tcp_congestion_control=cubic
 # Fix (bufferbloat), https://assimilationsystems.com/2015/12/29/bufferbloat-network-best-practice/ # Fix (bufferbloat), https://assimilationsystems.com/2015/12/29/bufferbloat-network-best-practice/
net.core.default_qdisc=sch_fq_codel
#
# BBR - Network-turbo for Linux (notice: We are still in /etc/sysctl.conf)
# The new flow control is ideal for server in the local network (LAN) too as much as for streamingserver
# https://www.pcwelt.de/ratgeber/BBR-Netzwerkturbo-fuer-Linux-im-Ueberblick-10612165.html
#
# net.core.default_qdisc=fq
# net.ipv4.tcp_congestion_control=bbr
# Increase Linux auto tuning TCP buffer limits
# min, default, and max number of bytes to use
# set max to at least 4MB, or higher if you use very high BDP paths
net.core.rmem_max =212992
net.core.wmem_max =212992
net.core.netdev_max_backlog = 5000
#
kernel.sysrq = 0
kernel.core_uses_pid = 1
fs.file-max=65535
kernel.pid_max=65536
net.ipv4.tcp_syncookies = 1
kernel.msgmnb = 65536
kernel.msgmax = 65536
kernel.shmmax = 134217728
kernel.shmall = 4294967296
kernel.randomize_va_space = 2
net.ipv4.tcp_window_scaling=1
net.ipv4.tcp_timestamps=0
net.ipv4.conf.all.log_martians=1# sysctl.conf(5) for more details.
net.ipv6.conf.lo.use_tempaddr = 0
# Disables IP dynaddr
net.ipv4.ip_dynaddr = 1
# Disable ECN
net.ipv4.tcp_ecn = 1
# Controls source route verification
net.ipv4.conf.all.rp_filter =1
net.ipv4.conf.default.rp_filter = 1
# Do not accept source routing
net.ipv4.conf.default.accept_source_route = 0
# Controls the System Request debugging functionality of the kernel
kernel.sysrq =0
# Controls whether core dumps will append the PID to the core filename.
# Useful for debugging multi-threaded applications.
kernel.core_uses_pid = 0
kernel.dmesg_restrict = 1
# If you set this variable to 1 then cd tray will close automatically when the
# cd drive is being accessed.
# Setting this to 1 is not advised when supermount is enabled
# (as it has been known to cause problems)
dev.cdrom.autoclose=1
# removed to fix some digital extraction problems
# dev.cdrom.check_media=1
# to be able to eject via the device eject button (magicdev)
dev.cdrom.lock=0
# Disable netfilter on bridges.
#net.bridge.bridge-nf-call-ip6tables = 0
#net.bridge.bridge-nf-call-iptables = 0
#net.bridge.bridge-nf-call-arptables = 0
net.ipv4.ip_forward =0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.tcp_max_syn_backlog =512
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
net.ipv4.tcp_syncookies = 1
net.ipv4.ip_local_port_range = 2000 65000
# Increase TCP max buffer size setable using setsockopt()
net.ipv4.tcp_rmem = 4096 87380 8388608
net.ipv4.tcp_wmem = 4096 87380 8388608
net.ipv6.conf.default.router_solicitations=0
net.ipv6.conf.default.accept_ra_rtr_pref=0
net.ipv6.conf.default.accept_ra_pinfo=0
net.ipv6.conf.default.accept_ra_defrtr=0
net.ipv6.conf.default.autoconf=0
net.ipv6.conf.default.dad_transmits=0
net.ipv6.conf.default.max_addresses=0
net.ipv4.icmp_echo_ignore_all=1
net.ipv4.icmp_echo_ignore_broadcasts=1
net.ipv4.icmp_ignore_bogus_error_responses=1
net.core.rmem_default =212992
net.core.wmem_default =212992
net.ipv4.tcp_fin_timeout =3600
net.ipv4.tcp_keepalive_time =7200
net.ipv4.tcp_keepalive_probes =7
net.ipv4.tcp_syn_retries =6
net.ipv4.tcp_retries1 =1
net.ipv4.tcp_retries2 =3
net.ipv4.tcp_retrans_collapse =1
net.ipv4.tcp_sack =1
net.ipv4.ip_default_ttl =64
net.ipv4.ipfrag_time =30
net.ipv4.ip_no_pmtu_disc =0
net.unix.max_dgram_qlen =10
vm.overcommit_memory =2
vm.overcommit_ratio=120 # mouseclick-fast
# or: vm.overcommit_kbytes=1496000
vm.page-cluster =3
kernel.ctrl-alt-del =1
kernel.panic =0
kernel.acct =4 2 30
kernel.printk =4
kernel.shmall =-1
kernel.shmmax =134217728
dev.raid.speed_limit_min =1000
dev.raid.speed_limit_max =200000
net.ipv4.conf.all.rp_filter=1
Encryption: HTTPS-connections and E-mail
http://www.tecchannel.de/sicherheit/management/3281630/verschluesselung_ist_nicht_gleich_verschluesselung/: It is quit impossible for the user to distinguish between the many kinds of encryption. Some were used automatically without consciousness. HTTPS-connections of the Transport Layer Security Protokoll (TLS, previous SSL) are applied for homebanking or online-shopping. In the internet, the way (connection) of the data from the client to the server is encrypted. Good luck, that this becomes quit the standard, especially for significant (sensible) data. Many internet user are sensitized in this matter. But what is the encrypted data transfer good for, if security lacks enpossible hacker to make them encrypted data accessible again? One more example: One does not really know, that an email is receipt the addressed receiptor through its transfer, that is always encrypted. Since the popular internet provider in Germany used TLS to secure up connections betweeen e-mail-clients (desktop, mobil) and e-mail-server, the e-mail transfer got in a quit reliable way even more secure, but in general this is not the truth. For e-mail-transfer, at least two popular methods are already in use for many years: S/MIME and PGP respective OpenPGP, what is also part of the end-to-end-encryption. The sender encrypts the e-mail, and only the meant receiptor can decrypt it again. This refers to the content of the email only and not the metadata in the header like subject, mail-addresses or the timestamp. Once more a digital signature protects the e-mail from manipulation during its transfer.
So are you such "kmail", or interested in becoming one? Please read our section about Kmail (and other email-client-programs) then!
FSE: Full System Encryption
It is not very difficult to chroot or mount partitions by rescue-CD from the "inside" or over many networks from the "outside". Their files can be reinstalled or installed as much as getting manipulated to dangerous trojans and other malware or contribute to serious hard system-defects. Therefore FSE is needed.
Loop-AES can be take into its effect by the simple option "encrypt" out of the package-manager of the system-configuration drakconf.real resp. Yast2. For some Linux, you need to download some of the mentioned packages to get Loop-AES started (you can get them from the mdv-update server fr2.rpmfind.net), while cryptsetup resp. LUKE does its best from installation-DVD/CD without the need of further packages. Now the access time from hd is increasing a little bit (although you might get the impression like I have, that it declines...). An overview upon the different methods for encryption is given from our linkside. Notice reports about the weakness of methods like XOR-encryption. Nevertheless, processes like those for browser should always be deactivated, especially right before an USB-stick is plugged in. At least, all temporary directories, the user resp. home-directory and even the partition with the swap file should be encrypted, but see our linkside, some think, it is most important to do it for the SWAP. Newer Versions of distributions prefer LUKE-cryptsetup, see links. For single files, the popular kleopatra resp. kgpg resp. gpg freeware provides a good addition. Methods for encyption itself like AES, serpent, two- and blowfish are secure as much as XOR-encryption already depends on the conrete passphrase. Nevertheless, cracking supercomputers might exist... The amount of attempts for decryption might be restricted there, but it is still not possible to beware from unlimited attempts to crack the passphrase. At least a relative long delay between the input of two phassprases of more than 30 seconds should take into effect. Intern this can be already performed by many login into Unix/Linux. Mycompanies as much as online-banking do only allow three false-logins to need the administrator for three more attempts. For internet choose the SSL with equal or more than 128 bit encryption. Nearby Tunnel-concepts are still interesting for the case online. See linkside and checklist for more details.
1 Filesystem stacked level encryption
1.1 eCryptfs - It is a cryptographic stacked Linux filesystem. eCryptfs stores cryptographic metadata in the header of each file written, so that encrypted files can be copied between hosts; the file will be decrypted with the proper key in the Linux kernel keyring. This solution is widely used, as the basis for Ubuntu´s Encrypted Home Directory, natively within Google´s ChromeOS, and transparently embedded in several network attached storage (NAS) devices.
1.2 EncFS -It provides an encrypted filesystem in user-space. It runs without any special permissions and uses the FUSE library and Linux kernel module to provide the filesystem interface. You can find links to source and binary releases below. EncFS is open source software, licensed under the GPL.
2 Block device level encryption
2.1 Loop-AES - Fast and transparent file system and swap encryption package for linux. No source code changes to linux kernel. Works with 3.x, 2.6, 2.4, 2.2 and 2.0 kernels.
2.2 Truecrypt - It is free open-source disk encryption software for Windows 7/Vista/XP, Mac OS X and Linux.

2.3 dm-crypt+LUKS - dm-crypt is a transparent disk encryption subsystem in Linux kernel v2.6+ and later and DragonFly BSD. It can encrypt whole disks, removable media, partitions, software RAID volumes, logical volumes, and files.

The full disk encryption resp. full system encryption (FDE, FSE) through the secure LUKS/dm-crypt has always been most important! LUKS also bewares several seconds between two manual login-attempts increasing its security. Only the entire encryption of the harddisc prevents from its "preparation" by exchanging packets, tarballs and files from outside for example managed by using a Live-DVD or even without. Many years ago I have met an elder computer-expert on the railway-station of Essen with the opinion, that all you need for security-tasks is an entire encrypted harddisc (I even undestood including the boot-partition!). But existing communication protocols tell us, that this is not the truth. Indeed, a complete encryption of the root-partiton and SWAP-partition of a SSD do theirself best against cases of mounting and chrooting in conjunction with the installation of manipulated tarballs and packets (for example by agents from foreign countries after breaking in into the computer-room). Full disk encryption solutions with LUKS only protect the data, if your computer is off. Once the computer is on and LUKS has decrypted the disk, the files on that disk are available to anyone who would normally have access to them. To protect your files when the computer is on, use full disk encryption in combination with another solution such as file based encryption. Also remember to lock your computer whenever you are away from it. A passphrase protected screen saver set to activate after a few minutes of inactivity is a good way to keep intruders out. Methods for encryption are described over links from our linksite, links from the left menu, section "alternatives". But for entire encryption of the root-partition we think
the following method using dracut contributing to FSE in main does its best: Gentoo-Schnatterente: Entire (complete) encryption of Linux WITHOUT ANY LVM and WITHOUT NEW-INSTALLATION REQUIRED!
We prefer this method also because of the possiblities of the command dracut. Notice: Only dracut (mdv2011) run with success on our environment. One more advantage: The harddrive resp. SSD gets completely demirrored by this method, so that invisible and so called "deleted" files get removed from them Then such invisible files can not be made visible anymore... For mdv2010 this method requires two SSD or two harddrives or one SSD and one harddrive and the packet dracut and cryptsetup (Luks/dm-crypt), you can get not only for Gentoo but from fr2.rpmfind.net also for mdv2010. At first, a around 500 MB sized boot-partition should be created by the partiton-manager out of MCC. I won it out of the my relative large swap-partition. Now you can follow the depicted method form the linked site even for mdv2010 using dracut and cryptsetup (LUKS/dm-crypt). Depending on the kernel, in our example kernel-desktop-2.6.39, you can also use btrfs or ext4, reiserfs etc for the formatting by mkfs.filesystem. In order to format by Luks, cryptsetup is not performed as described there, but as follows
mdv2010 offers all, full and partial system- and disc-encryption (FDE) by LUKS and the encryption of the boot-partition and the load of memtest by grub2 in the sense of the configuration of /boot/grub/menu.lst, where an md5-encrypted password can be set for each bootable kernel and memtest.
man fstrim: Intensive usage of fstrim or "mount -o discard" can influences the life age of minor-qualitative SSD-devices. For workstation and server It is recommended to execute this command one time the week. Notice, that not all devices support a overruling-queue, therefore such overruling command causes minor performance for all devices and commands accessing the harddrive.
Mandriva-Community: | cryptsetup -h sha256 -c twofish-cbc-essiv:256 -s 256 luksFormat Root-Partition |
oder
Gentoo-"Schnatterente": | cryptsetup -c aes-xts-plain64:sha256 -y -s 256 luksFormat Root-Partition |
Gentoo-Wiki: | cryptsetup -c twofish-xts-plain:wd256 -s 256 luksFormat Root-Partition |
Ubuntu 10.4: | cryptsetup -c aes-xts-plain64 -s 256 -h sha256 luksFormat Root-Partition |
and since Kernel 2.6.20, they told us in general: | cryptsetup -c aes-lrw-benbi -y -s 256 luksFormat Root-Partition |
all for 128, 256, 384 and 512 bit, here 256.
dracut itself should be started by
 | dracut -c /etc/dracut.conf -f /boot/initramfs-4.19 4.19.126.pclos1 |
To be careful, take dracut (el6) or dracut-008-3 for mdv2010.0 and 2010.1 (from mdv2011, but we do not recommend higher!).
For SSD useful kernel options to add in /etc/fstab and /etc/crypttab even for the encrypted swap-partition are:
| noatime (or relatime) and data=writeback |
We prefer notaime. noatime stands for "no atime", the same for relatime except time to time. data=writeback finds an effective compromise between journalling and non-journalling of journalling filesystems. Such options are provided up from kernel 2.6.39 or some earlier. Option discard does only work, if luksFormat has been made with option --allow-discards.
Have a look at your kernel-modules by the command
and add to dracut.conf, section " # additional kernel modules to the default the following modules:
| add_drivers+="dm-crypt dm-mod twofish twofish_common cbc cryptd aes aes_x86_64 aes_generic sha256 sha256_generic xts lrw twofish twofish_common snd_hda_codec_via loop sr_mod dm-mod dm_region_hash dm-crypt dm-snapshot dm-multipath dm-mirror dm-log dm-log-userspace pata_acpi ide_core binfmt_misc ide-pci-generic ata_generic ata_piix libata ide-cd_mod i2c_core ohci_hcd ehci_hcd usbcore pata_amd ide_pci_generic ide_gd_mod ide_core pata_acpi sd_mod reiserfs i915 drm i2c_algo_bit i2c_cor sd_mod scsi_mod dv1394 ieee1394 ohci1394 raw1394 sbp2" |
Same modules should be entered in /etc/modules.
For /etc/dracut.conf.d/dracut.conf of dracut (el6, 008-mdv2011) for kernel like kernel-desktop-2.6.39.4-5.1 (mdv2011) as much as kernel-4.9.49 and 4.20 (PCLinuxOS) with mkinitrd (mga2), nash (mga2), dracut (el6), glibc (pclos) and LUKS/dm-crypt (cryptsetup (pclos, rosa2014.1, fc, el6, ...)) we enter the following:
# Sample dracut config file
i18n_vars="/etc/sysconfig/i18n:SYSFONT-FONT,SYSFONTACM-FONT_MAP,UNIMAP-FONT_UNIMAP,LANG,LC_ALL /etc/sysconfig/keyboard:KEYTABLE,KEYMAP,GRP_TOGGLE"
# Specific list of dracut modules to use
#
dracutmodules+=" crypt dm dmraid dash i18n resume base kernel-modules biosdevname lvm mdraid rdma fips fips-aesni rootfs-block udev-rules rootfs-block terminfo base fs-lib shutdown"
# Dracut modules to omit
omit_dracutmodules+=" img-lib redhat-i18n usrmount selinux network debug nfs fcoe iscsi ifcfg gensplash nbd"
# Dracut modules to add to the default
add_dracutmodules+="10i18n 45ifcfg 50gensplash 50plymouth 90crypt 90dm 90dmraid 90kernel-modules 95fstab-sys 95iscsi 95udev-rules
97biosdevname"
# additional kernel modules to the default
add_drivers+=" dm_crypt dm dm_mod dax dm_region_hash dm_mirror dm_log evdev cbc cryptd aes aes_x86_64 iso9660 ext4 asus-nb-wmi ahci libahci ata_generic aes_generic sha256 sha256_generic lrw xts twofish twofish_common twofish_x86_64_3way twofish_generic snd_hda_codec_via loop sr_mod dm_snapshot dm_multipath dm_log pata_acpi ide_core binfmt_misc ide-pci-generic ata_generic ata_piix libata ide-cd_mod i2c_core ohci_hcd ehci_hcd usbcore pata_amd ide_pci_generic ide_gd_mod ide_core pata_acpi libata sd_mod reiserfs i915 drm i2c_algo_bit i2c_cor sd_mod scsi_mod dv1394 ieee1394 ohci1394 raw1394 sbp2 video reiserfs ext4 jbd2 sata_piix pata_acpi algif_skcipher af_alg asus_atk0110 ahci libahci gpio_ich mfd_core iTCO_wdt iTCO_vendor_support drm drm_kms_helper cryptd cryptd_simd asus_atk0110"
#
add_device+=" /dev/mapper/luks-8fa1..."
# list of kernel filesystem modules to be included in the generic initramfs
#
filesystems+=" proc tmpfs"
# build initrd only to boot current hardware
#
install_items=" path-to-keyfile-with-key-if-existent "
#
hostonly=" no"
#
# install local /etc/mdadm.conf
mdadmconf="no"
# install local /etc/lvm/lvm.conf
lvmconf="no"
Not all SSD (microcontroller) support allow-discards resp. TRIM, although TRIM is strongly recommended to increase their performance. This has to do with the kind of deletion. With TRIM, 4 KB blocks are deleted at once instead of large 512 KB blocks at "any" time causing many hugh gaps called fragments.
Notice, that the keycode for the keyboard is not loaded completely for special chars during the boot with dracut. Whenever the passwords for the decrypted root-partition are entered, keys for special chars still exchanged, so that the typed-in passwords containing special chars do not fit to the meant regardless from setkey in /boot/menu.lst of grub. For example key y still stands for key z! dracut stops the booting after three times wrong passwords have been entered. In this case the root-partition is quit lost!
We think, that a Live-CD/DVD or an USB-stick is not needed except (but then as a must) for repair of the encrypted partitons (and up-to-now we ourselves do not know even such cases...), where they can be mounted followed by password-request, but in the well-known way by the command mount, if package mount_pam is installed! Use Knoppix-DVD or create such DVD through Mindi or Mondo or install mdv on USB using mandriva_seed. For the last purpose you can also download MandrivaOne out of the internet. Did I tell you? Nevertheless do not use Live-Linux from such media for luksFormat! So all in all, thanks, "Gentoo-Schnatterente" it managed us to achieve full disc- and system-encryption without a new installation and without any LVM, all doing fine for mdv2010.0 too! It is working such fine, that you can also order a dd-command (dd always worked fine on my SSD for many and all times, although some tell us the opposite...) based copy onto your (except boot-partition with dracut and kernel-2.6.39.4-5.1.1mnb) full-encrypted, at least 120GB sized SSD including the encrypted SWAP and main-themed root-Partition reiserfs, reiser4fs, ext4 (recommended) or btrfs! 60GB-packaged mdv2010.0-x86_64 (64 bit) with a separat encrypted home- and free-partition from us (Gooken) for 20 €, password for all encrypted partition: "full-encrypted-ssd-mdv-2010-x86_64-software60GB". Please tell us, if you ever get any problems with your computer based on this SSD (we think it´s impossible...)!
A report about FDE (full disc encryption) on the base of LVM with Luks on the base of Ubuntu, but with new installation required for example is linked here..
There you can read about the fact, that quit all efforts for security remain still essential, what is based upon the usage of communication-protocols by their nature and remaining risks of system-interna.
One more report about FDE resp. FSE on the base of LVM for Ubuntu, that is offering a link to a script for automized FDE: FDE (full disk encryption) by LUKS for Ubuntuusers (in german language, but we think there is one in english available too).
Trim the SSD (if its micocontroller permits it): http://wiki.ubuntuusers.de/SSD/TRIM
And for mdv2010 by Live-CD/DVD for example please read this well illustrated article: FDE (full disk encryption) with Luks and LVM by installation- or Live-CD/DVD.
 FSE means to encrypt all USB-sticks too. If you want to know, howto encrypt an USB-memory-stick with LUKS, please click here.
FSE means to encrypt all USB-sticks too. If you want to know, howto encrypt an USB-memory-stick with LUKS, please click here. Whenever an USB-stick is put into the USB-slot, KDE4.4.5 immediately opens a window for the typing in of the password, if autodetection is activated by the user. After this, a special plasma for plugged-in media and harddrives offers several programs to open the USB-stick. If you do not like to open it this way, take dolphin to access files from the stick.
One more encryption for mdv2010 still without new installation required is performed by LUKS on single partitions, at least upon the partion for home, swap and temporary files, all without LVM, click here.
We also link in links section alternative to a website explaining how to encrypt USB-memory-sticks without LVM, but with LUKS (analog, just the device has to be set for the stick). Now, with installed packet mount_pam the stick can be easyly mounted as all LUKS-encrypted partitions by "mount /dev/USB-device_name any_mountpoint" and unmounted by "umount.crypt mountpoint".
LUKS Cryptsetup Iso9660 - howto setup encrypted CDs and DVDs with LUKS: LUKS has also some great features for encoding iso-images: http://www.sourcentral.org/luks/iso9660/
In some of such cases knowledge about LVM (logical volume management) becomes quit essential, please click here.
Against the unyielding opinion of a the 90th personally met expert, the complete encryption of his harddisc protects against everything, communication-protocols do still their work upon even once encrypted but decrypted working directories and files. Nevertheless, in order to prevent not only the risk from the inside (computer-room), but also the outside (online and other net), it makes most sense to create an FSE consisting of a separate LUKS_encrypted partition for all the sensible user-data beneath the decrypted root-partiton using dracut and by LUKS.
A hardened kernel called RSBAC-Kernel (mdv2010 kernel-rsbac-2.6.31.14) can also be booted up in the case of disc-encryption like FSE and FDE through dracut, by
 | rsbac_softmode rsbac_um_no_excl |
These two boot-parameters are added to the other boot-parameter like "nosmp" and "speedboot=yes" in /boot/grub/menu.lst of Grub (mentioned rsbac-version is also running for mdv-kernel-2.6.39). We have made best experiences as the hardened kernel did not seem to restrict any functionalities.
One more access-control is pregiven for the X11-server in the case of LAN, therefore named X11-Server-Access-Control. The core of the x-protocol provides a authentification for hosts. By the command xhost a list of allowed hosts can be set. After a first query by typing xhost, access control is already enabled, so that only authorized X-clients can connect. X11 offers place for so called extensions, one interesting here is named the X11-SECURITY-EXTENSION.
It differences in trusted and untrusted X-clients keeping away from reading windows-contents, controling inputs of other clients etc.. This all is documented within within the package xorg-docs, the documentation of the X11-server.
For server, for example Apache webserver, you can configure apache.conf resp. httpd.conf after configuring samba for your local network (LAN), Squid for Proxy Server and Privoxy for netfilter as a kind of firewall-(pre)filter, although rules are collected in what is called firewall pure. All in all, against backdoors and hacker, a firewall like the iptables based linfw3 (other OS: remark the referential character of linfw3) is still needed in many cases, even, if it is just making up the background, which iptables-code (incl. logging) has been certified by ICSA and tested by generations of mighty communities like universities, banks and industries as much as private-investigators from all over the world. With linfw3, the construction-time should become nearly no one anymore, while transparency of computer-age is increasing up to a maximum. Proofs for its correct, reliable working are supported by its many test-opportunities the modules and its strategy conditioned scientific completeness, companioned by transparent and good understandable code. Ports of each connection are iptables-natured distinguished into source- and destination, not all FW support this concept. While other FW almost depend on version and distribution, linfw3 keeps stable independent from (most) all of them. The higher flexibility: Any increasing amount of iptable-modules can be integrated. Even if your kernel or iptables-version does not support all modules of iptables, through always present includes of all fundamental blocks, linfw3 does not loose much of its effectivity - so that the system is always reacting basically secure.


So linfw3 sets an end to naivety in basic IT-security matters for a lot of more than six main reason:
1 Like Klean it is written in UNIX-SH (OS-mother UNIX). This provides unbeatable transparency of code for everyone. Rules, that can be implemented in many wrong ways, are described in all details instead of at last somehow but nowhere
2 its basement on (by years-long tested) built-in open-source filter-set iptables/ipchains and
3 the possibility of modification and enhancement to a standard you like
4 the block of ALL HACKER,HACKER-REQUESTS A N D ALL TROJANS in a good understandable and one of the best ways on INPUT (client/server)
and FORWARD (router) by state "NEW" as much by a "beaming" prefilter on NEW and match OWNER
5 its optional, detailed protocoling of each intrusion-attempt in possible limitation and
6 the increase of throughput up to a maximum, higher than without or by many other FW
eth+, ppp+, ippp+, .... : What kind of interface (ppp0, ippp0, eth0,...) you are using doesn´t matter. Certainly I can´t give you any guarantees that this firewall solves all of your security-tasks. Also remember in security-matters, that firewalls generally can´t be blamed for all lacks in IT-security. We are going to see this in the second step of the excursion, where the question of concrete analyzes of data burdened in payload is almost more user-friendly supported by the concept of what we like to call "a d d i t i o n a l (REFINING) p a c k e t - f i l t e r s" (than by iptable´s module string). This helps to reach a sufficient security-level (for any system), especially after the just two steps of this excursion have been performed.
Now we dare to compare linfw3 with other FW more concretely: no hackers, no trojans anymore- no intrusions possible! GUIs are not expandable, or one can get difficulties by misunderstandings - with DIALOG everything is explainable and bewaring software-transparency. You can choose and modify dialog-(alternative cdialog-) widgets in order to get an easy to handle OSD-like outfit. Help-items guarantee user´s right answers to different questions instead of not knowing what to enter. By many FW Hacker often still have chances to intrude, they do not have any (!) through the consequent integration of iptable´s state NEW. Installation- and configuration-time take several minutes or more than one hour, with linfw3 you just need one up to five seconds for installation (i.e. with krpm) and up to 1 to 10 minutes only for configuration. The handling with Samba might not be correct, so that Samba does not work, with linfw3 Samba works within seconds. The quality of the FW-socket can´t be tested - linfw3 presents a statistic for different iptables-version that helps quickly to separate the secure from the lacked ones to patch. Protocoling does not come to an end - linfw3 can limit the amount of log-entries by time or packets through time, packets, general restrictions and many log-levels. Many firewalls suffer from one update or upgrade to another, while linfw keeps the highest possible transparency for self-correcting: instead of authors by its users. The same for the expansion of the filtering rules: It is almost very difficult for many firewalls to expand, with linfw3 it is nearly childish and as without any dimensions. ICMP Traffic is not blocked in many firewalls, linfw3 can block all ICMP-type by -type. A lot of FW forget to block
trojans (risky outgoings). linfw3 blocks trojans and programs port-ranges by port-ranges, by match OWNER containing CMD, PID respective USER- and Group-ID, last ones configured to 2, the daemon of privoxy, that enables the block of scripts similar to special firefox-addons and ad-filter (for Firefox <= 2.0.0 recommended), or by adding any new group only not belonging to root, even sessions by session-id; work in all FTP-modes (especially by opening such ports like ftp-data resp. ftps-data and ftp resp. ftps), change characteristics up from single- or multi-user, client, server up to router, enjoy special hardening of rules by choosing the right FW-strategy (DROP-policy), change log-levels from simple protocoling info(rmation) to warn(ing) by default up to alert, crit(ical) or even emerg(ancy), where each intrusion is indicated by its own window in accordance with beeps - here´s the overview:
Packet filter: Firewall
Linfw3-(UID- und GID)- OWNER- and ELSE-PORT-LOG (all deactivateable!) on the base of Mandriva 2010: Trojans and hacker "squeaking" mad

Most features of the dynamic firewall linfw3:
COMPROMIZLESS GOOD, SINGLE USER - DESKTOP - CLIENT - SERVER and ROUTER-FIREWALL IN ONE TESTED ON LAN/WAN/GAN - SECURE, TRANSPARENT AND EASY TO HANDLE
For beginners and advanced on their look out for the really secure solution up to the expert for formulation of high-end ones
With this firewall you WON´T GET ANY HACKER, TROJANS AND SPYWARE anymore!
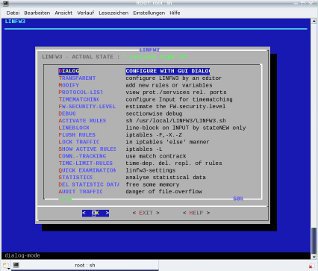
Simple&effective Kernel-konsole-GUI dialog (resp. cdialog) with permanent help-item in native UNIX-sh(ell-language)/bash
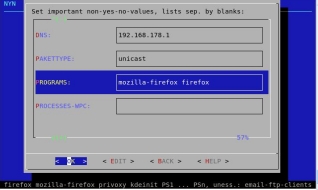
main configuration by dialog is structured by all (NYN+YN+kernel-parameter), NYN (non-yes-no-values), YN (yes-no-values) and kernel-parameter (KP); advantage: fast reaction in detailled configuration depend from different situations; for port-release, and for example you can allow and forbid downloads out of the internet via ftp, many single log-options, STATE-NEW-lined-blocks, modules of iptables, change single IP for mailserver, ...
configuration is possible from two sides: by GUI-dialog or by the UNIX-Standard-editor for the konsole xedit, ed, vi, vim, further on pico resp. nano within the textmode as much as by a common text-editor like kwrite upon the main shell-script
native design, sufficient transparency, easy configuration, high extendability, maximal secure
for 2.4.x and 2.6.x kernel or higher, all kernel, all UNIX (please mail, if not)
Linfw3 runs on all terminal-programs like Konsole, xterm, aterm, yakuake, ...
and can also work beneath a separate router-firewall ( "doing it all more or less twice" ) as much as alone.
A kernel still might be able to build-up connections through glibc. Therefore choose the glibc we recommended above for example: glibc from mdv2012 in mix with glib-utils, glibc-profile, glibc-i18ndata from Mageia Cauldron 3 (mga3), alternatively all glibc-packages from mdv2010. A secure running glibc is indicated by a calm working of the computer-system (the never blinking red LED).
for all protocols within the address-rooms iptables-ipv4 resp. iptables-ipv6
Add into /etc/rc.local: sh /etc/init.d/ip6tables restart # if iptables-ipv6 (el6) gets installed beneath iptables (el6); all gets blocked for IPv6 on INPUT, OUTPUT AND FORWARD by Linfw3, see rules within /etc/sysconfig/ip6tables. Instead of the general block of IPv6, all rules of the IPv4 within /usr/local/LINFW3/LINFW3.sh can be imported into /etc/sysconfig/ip6tables by exchanging ipt="iptables" with ipt="ip6tables". Also look, if /sbin/ip6tables* got linked right to /sbin/ip6tables-multi.
support of all interfaces: DSL- and analogous modems (ppp), ethernet-cards (eth) and isdn (ippp)
Indication of the state for activated and deactivated iptables-rules in * (active) and # (deactivated), ftp for disabled ftp-downloads, ftp for enabled ftp-downloads, lined for either state-new-lineblock-only or addition UID-/GID-owner or UID-/GID-owner root in the headline of the main menu in addition by the indication of the reached FW-security-level in percent and the last called menu-item
Linfw3 also for server and anonymized surfing: To make it very secure, server (httpd/Apache, SAMBA (LAN), SSH/SFTP/FTP, media, printer, Tor (even Tor-Browser/client), browser...) might have got their own user accounts with belonging groups upon UNIX/Linux-file-systems (in coordination with protecting owner- and access-rights (including ACL: chown, chmod and getfacl/setfacl). User accounts can be freed, (login-shell-) blocked and locked manually or within the system-configuration). On this website, we describe in detail, how to set such owner- and acess-rights and how to configure the configuration-files for different server. At last through setfacl other user neither can see quit anything (no possible reading of files and directories), nor overwrite (files and directories), nor execute (files and directoires, sandbox), while the server-configuration-file often sets more internal filter. And additionally do not forget the other concepts of LINFW3 like port-release/-blocking, relevant for server too. As a sandbox, firejail is recommended additionally (but it is not a must anymore).
All this methods and concepts are explained in detail within this step of our excurs.
connection- resp. traffic-monitor (iptables module contrack) in refreshed frequency 1 up to 9 seconds: In some seldom cases, client programs require the releases of IP or ports, especially those, increasing security-lacks. Contrack helps to find out such IP and ports, to be set in LInfw3 for releases (e.g. in section I P - h a n d l i n g)
Connection-Tracking:
Time-Wait: blocked conncetions, listed with the IP of hacker and Trojans, that can be precised by the command whois. Many are invoked by the call of websites in the address-line of the browser
Close: closed connections
Established: established connections
Color-adjustment: /root/.dialogrc
iptables-ruleset-monitor (after each activation by the debugger)
Estimation of the FW-security-level past each new-configuration
We recommend in future, to use "https" (resp. port 443) in TCP-INPUT-SPORTS only by removing www (resp. port 80) from this list. Use Tor for port 80, although this is not recommended for Tor too.
„just-surf“-concept: almost default for the mode single-user
With this native firewall of a strong referential character you can even make presentations in detail ... without risking hacks after configuration. Now the secret of howto get rid of (hacker and) all trojan is known by Gooken for a larger public audience instead just a small circle of some UNIXer.. Beneath viruses you can get rid of hacker, trojan (except the risk with the browser itself), dialer and connection-breakdowns! Therefore this FW is closing ENTIRELY ALL PORTS from the outside to the inside within its main part and through infinite beams - while only those from inside to outside for the from you built-up connections are opened. This is made possible in at least one of three main ways marked by H1, ..., Hn for methods against hacker and T1, ...., Tm against trojans:
1) some kernel > 2.6.12 by PID- or the reliable automized pid-Agent of LINFW3 (please notice, that we did not test kernel >= 3.X.X) (T1)
2) kernel <= 2.6.12 (we recommend the last version 2.6.12-31): like 1) and/or CMD-(command-name)-owner (T2) of the command resp. process by name especially for some browsers only like mozialla-firefox (mozilla-firefox, firefox or firefox-bin) for firefox, kdeinit for Konqueror and so on
3) independent from the kernel version (almost, but not 100% secure) by the usage of a separate netfilter like privoxy pre- resp. reconfigured for user daemon and group daemon (T3), where the user- and the group-ID have to be set to daemon resp. almost number 2 in Linfw3 through GUI dialog, especially if the netfilter is advised to a free determinable port and if connections of that netfilter as in this case privoxy, are limited within all its configuration resp. action-files of /etc/privoxy to 80 (www) and 443 (SSL): "+limit-connect{80,443}".
CMD-owner and its more secure (!), but also within SMP-(mulitprocessor-)Linux-kernel destroyed subsitution SID-owner, what would have been a userful addition even to the following, can only take quit similar in effect by UID- and GID-owner (T3) as follows:
UID- and GID-Owner enpossibles the access into internet for processes like firefox only, while all other processes are blocked by LINFW3:
set chmod 700 -R to /home/surfuser.
1. Create a new group and add a new user to it:
* Create: groupadd surfgroup
* Validation: grep surfgroup /etc/group
* Add a user, that ONLY is allowed to surf to this group: useradd -g surfgroup surfuser
If the user should already exist, enter "usermod -g surfgroup surfuser"
2. Only a password protected user named other_user_member_of_surfgroup is allowed to change the group (by command sg) to the group named surfgroup in future after performing the next steps, while the server-port 80 as an exception of the (rare to keep) ports allowed from the other end of all conneciton only does not enpossible any uploads of files resp. information:
|
/bin/su - surfuser
|
|
Password for surfuser
|
|
sg surfgroup firefox
|
You can enter this commands for the entry, here firefox, in the K-menu, you just have to enter: kmenuedit (or right mouseclick on K-Menu, where to choose "edit") "surfuser" for the input-field for the starting user and "sg sufgroup firefox" for the field for the command. Now you do not need a terminal to start firefox anymore. Instead, the password-window for surfuser appears before firefox starts. You can not, you should do this for all communicating programs like ifup eth0, ifdown eth0, konqueror, gftp, kphone, kdict, xchat, tv-browser, eboard and so on. You do not have to do anything else to get with the programs into the net.
4. Now the process, here named firefox, is starting. The connection is owned (exclusiv resp.) only by surfuser with group surfgroup, where surfuser is member. In order to preven read and write access, access-rights should have been set adequately. Therefore you can close or end the terminal already now (never forget to logout from terminal by command exit or clicking with the mouse onto close or the command for end out of the menu of the terminal, especially as superuser root!)
After the field "remind password" is filled up by making a cross per mouseclick, the password for "su - surfuser" from above needs not to be typed in once more the actual session.
or, if you closed the terminal by mouseclick, in order to free some capacity for surfuser you can type:
Do this step by step 1.-4.for each process (here it is firefox) that should build up connections. You always have to enter the very ensecuring password for a change to the other_uer_member_of_surfgroup. Now process firefox is started by surfuser and group surfgroup. The terminal, if K-Menu remains unused, became a center for all online traffic (here of process firefox). It is also possible to write an adequate shell-script for the input of the meant process to click upon by mouse, but this is not such secure for the storage of the name resp. ID of the surfuser and surgroup. Also think of a script containing the questions for even them.
3. Now start Linfw3 or edit its main-script LINFW3.sh and configure GID within the NYN-section by assigning the UID and GID for "surfgroup" resp. belonging user name and group name. Please care for LINFW3 being configured in the YN-section to block all other UID and GID. This way is secure. One more advantage: you do not have to release and block each of the many, many programs that is elected to build-up a connection into the net like essential within the configuration of many other firewalls!
To be even more careful, do not let surfuser be member of the group named "wheel", all other users are members of. It would be one more advantage to remove the option "exec" for the (we hope like the root- and separate partition: encrypted) home-partition out of /etc/fstab (although this might be unnecessary), while the option "nodev" can be added. In MCC (drakconf), part msec, where this opportunity is explicitly mentioned, you can configure resp. set by convenience, that only users, that are member of the group named "wheel" (wheel-mice) are allowed to change to superuser(-mode) by su. After this, members of this group wheel are all user including root except surfuser. The directory with the locked desktop-icons can be moved to /usr/local to get unlocked again.
 Hooray! First the risc was reduced to trojans and then upon once opened connections only - a risc of many firewalls! With this method (most perfect would be to add the protection by the integrated port-concept or SID-Owner instead of the insecure CMD-owner), a process, here named firefox, is assigned a new user-ID and group-ID that allows to comunicate password-protected only within the net, while his previous one belongs to all those blocked like all the other ones including root. After perfoming this for firefox (similar for programms with other communication-protocol like xchat, filesharing, kphone, TV-browser and bidwatcher (Ebay-auctions), you can do this process by process for all processes you are going to allow to communicate within the net up from any certain time you want. The group-ID itself should be less all those ones listed for the groups of user by the command "id", for example choose GID 28 (< 500) for surfgroup. The BIS recommends this method starting processes with another, second user-account for important bank-transactions and so on. Remember this kind of start of firefox by su and sg in future. Notice, that Linfw3 can be enabled to allow processes for E-mail-transfer (smtp, ssmtp, pop3 and pop3s, imap), time server ntp, news, (s)ftp either in conjunction with the IP or in general, the same for all your server after their configuration within Linfw3. There is a special option for ftp- and ftps-clients (ftp and ftps) to run for set UID resp. "surfuser" and GID resp. "surfgroup" only.
Hooray! First the risc was reduced to trojans and then upon once opened connections only - a risc of many firewalls! With this method (most perfect would be to add the protection by the integrated port-concept or SID-Owner instead of the insecure CMD-owner), a process, here named firefox, is assigned a new user-ID and group-ID that allows to comunicate password-protected only within the net, while his previous one belongs to all those blocked like all the other ones including root. After perfoming this for firefox (similar for programms with other communication-protocol like xchat, filesharing, kphone, TV-browser and bidwatcher (Ebay-auctions), you can do this process by process for all processes you are going to allow to communicate within the net up from any certain time you want. The group-ID itself should be less all those ones listed for the groups of user by the command "id", for example choose GID 28 (< 500) for surfgroup. The BIS recommends this method starting processes with another, second user-account for important bank-transactions and so on. Remember this kind of start of firefox by su and sg in future. Notice, that Linfw3 can be enabled to allow processes for E-mail-transfer (smtp, ssmtp, pop3 and pop3s, imap), time server ntp, news, (s)ftp either in conjunction with the IP or in general, the same for all your server after their configuration within Linfw3. There is a special option for ftp- and ftps-clients (ftp and ftps) to run for set UID resp. "surfuser" and GID resp. "surfgroup" only.
Do not forget to adapt the access-rights, so that reads and writes especially upon user-accounts are really forbidden! In order to prevent the reading of emails and news, do not follow this way for email-clients and news-reader. Use certificated by BSI ones like kmail, knodes or kontact by just choosing the options "allow pop3s", "allow smtp" and "allow nntp" within Linfw3
One more (similar to the refered) portlist additionaly cares for the traffic through ports independent from OWNER, for example needed for ntp
Alternatively, in order to resign from the terminal for net-communication-processes, we can use a proxy with its own user and group like privoxy with UID and GID 2 for daemon. Such owner and group do own only a few directories and files, but not all clients do allow to configure proxies. As there is no password-protection build up of connection owned by user squid or daemon, this has the advantage, that processes and trojans can build up connecitons over the proxy. For this purpose the proxy should be started password-protected by "su - surfuser-daemon-or-squid" and "sg surfgruppe-daemon-oder-squid "/usr/sbin/squid-or-privoxy /etc/privoxy/config"".
The use of sg similar to su (change to superuser), in conjunction with following methods, trojans (and hacker) do not have chances anymore!
4) all kernel: fundamental block of hacker and trojans follows the (server-)port-release of INPUT-source- and -destination-ports - (H2 and T4) with belonging OUTPUT-port-settings
almost independent from kernel-ver: UID- and GID-owner by user-ID and prelonging group-ID (T4)
You see: Once descripted how and howto, you know everything too! All methods do profit from the distinction between incoming and outgoing ports (H2 and T4), so that many connections can not be established neither from the inside to the outside nor from the outside to the inside. Therefore it is good to know, that one port stands for one and the same certain service resp. server resp. communicaton-protocol only. Anyhow such services should be restricted on your side (H3 and T5), what can be done within the system-configuration. Hackers from outside to inside do not have any chance by the additional target DROP in conjunction with their STATE NEW on chain INPUT lined completely out at the beginning as much as on all opened and closed ports in the following parts (H4). You can also use the iptables-module STRING (H5 and T6) and/or a scriptfilter (H6) like netfilter privoxy, firefox addon-plugins like adblockplus and disconnect. Last one is recommended by prism-break.org. Tagesschau.de already critizised adblockplus for some includes. NRW-TV recommended Noscript, consisting of ABE and blocker of plugins like shockwave-flash. This plugin enables read-write-operations on harddisc resp. SSD. Forbid this by configuring this plugin within the kontrol-center resp. workout-configuration by clicking on the appearing self-named icon. We also think of the adblocker of the standard-browser Konqueror with the opportunity to import actual lists out of the internet for its adblocker, that is also functioning as adblockplus (even out of the toolbar to add new items) or many other scriptfilter, and do not forget servers by additional specifications like within httpd.conf (Apache). Noscript itself should block all scripts by default (configuration). Now elements of the website might not be shown anymore, that are shown again, if belonging blocking scripts gets sequences allowed. We suggest the adfilter of konqueror, that is working like ublock-origin and noscript. If all javascripts are blocked by the expression like "*.js*", same for perl by "*.pl" each blocked script can be allowed again after clicking on the symbol for the adblocker in the status bar within the opening administration-windows. This follows our firewall-strategy "forbidden is, what is not (explicitly) allowed!". The adfilter finds out all suspicious scripts, listing them loaded webside by webside within the administartion-window. You can order an importable filterlist for the adfilter of Konqueror with more than 8.000 regular expressed entries from Easylist and other collection for such entries also from us to download by our order-formular for a onetime protection-fee of 10 €. In general, such list actually cuts out neither too much nor too few elements out of websites, but still has to be actualized permanently in the way we described (from webside to webside).
P(rocess-)ID-Agent for all kernel version:
The PID-agent (T1) of linfw3 periodically checks out the activation of any allowed processes resp. their PID (CMD section with acceptedprograms) in 25 seconds (by default), in order to enable only their access from inside to outside during activation (except always accepted processes from WPC-processes resp. from a list named processeswithoutportcheck, if set). The only point is, that you have to wait up to default 25 seconds each browser newstarts before websites can be built up for the first time. This all does not influence the guaranteed transfer for email (pop3, pop3s, imap, imap3, imaps, smtp), time sever ntp, Usenet news (nntp), filt transfer ftp and ftps, independent from all this as described in another list-item), although alternatively by the fact that many trojans send email such processes can also be started like the other communication processes only, by typing again "su surfuser" and "sg surfgroup process" after allowing belonging ports through the Dialog-menu (or manually).
Special programs with many ports to open named in a separate list (called processeswithoutportcheck) like for internet telephony (skype, skypeforlinux, kphone, ...) can be trusted by the PID-agent in the same way, but without essential port-check!
Further on Linfw3 sets an end to all system-dependencies and lacks in configuration-possibilities
Process names to resolve for the owner-concept can initally be found out by the process-audit of linfw3
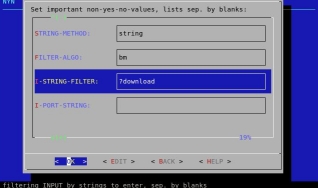
Dialog menu with direct-help-support, nothing that could be overseen or configured wrong: The configuration part is structured into three, all significant values configuring sections: NON-YES/NO-values NYN, YES/NO-values YN and kernel-parameters. In mode transparent, more values and default rules based upon iptables can be edited by pico resp. nano (default: nano)
standarized protocoling: fine-tuneable by example-file syslog-example.conf, what opens the into the control-bar beneath the tray minimizable, each attack blue blinking live UNIX-system-message-window (KWrited, see our picture below) for all (log-level) emergency including the protocolings resp. loggings of LINFW3 (we ourself always prefer this mode); after each new log-entry such window remains blue colored until you have analyzed it by maximizing its window out of the system-tray; beneath that, each log-entry is stored in a system-logfile; of course you can always find out the needed data about the right in time protocoled actual hacker by "whois IP" delivering the information
name,
address,
telephone-number,
organization,
domain,
server and
e-mail-address
right onto your computer
alternativ geioplookup from geoip
>geoiplookup 100.10.10.10
GeoIP Country Edition (Land): US, United States
GeoIP City Edition (Stadt), Rev 1: US, RI, Rhode Island, Riverside, 02915, 41.772701, -71.350304, 521, 401
GeoIP ASNum Edition (Provider): AS701 MCI Communications Services, Inc. d/b/a Verizon Business
geoip-Blocking (of countries like de, en, cn, ...)
not only complete blocking, but also proctocoling through kwrited
fast checks of modules of "firewall-language" iptables- related to different kernel versions
Lined out blocking from outside to inside by state NEW at the beginning, over ports in the middle and complete like at the beginning in the end part, hardened by blocking through the rules for POLICY
certified norms from universities, ICSA and international press
regard of Internet-Telephony (configuration see checklist)
multi-layered firewall by the GUI for kernel-configuration Dialog, rules in dialog mode with explicit help items and transparent-mode
extensible protection by Dialog supported settings of kernel-flags like ECN (Early Recognition Notification), bootprelay,
TCP-keep-alive time, IP-fragtime, against redirects, source-route, IP-hightresh and -lowtresh, martians, ...
The strong referential (universal and optimized) FW-character presents the right configuration for all FW
Beneath several strategies, Linfw3 mainly follows the more efficient (for all better to handle) FW-strategy
„forbidden is, what is not (explicit) allowed“ (and not:“ allowed is, what is not forbidden“)
In order to achieve the promised security for the calculation of delays of iptables itself, network should be up after the booting of the operating system (you can control this for example by the command ifup and a belonging network-applet), while the amount of services (server-ports) generally got restricted through settings made within the MCC (control-center) of the operating system
quick activation and deactivation by DIALOG-Menu: secure receipt of email (POP3, POP3s), news (NNTP), secure news (NNTPS), ssh, telnet, up-/download of files and name resolving WHOIS- and (D)NSLOOKUP-queries - all independent from SATE, IP and subnet-mask and from configured modules like Owner and concepts etc.. You can also set different belonging IP resp. IP/subnet-masks for more restrictions. We repeat: alternatively by the fact that many trojans send email, such processes can also be started like the other communication processes only, by typing again "su surfuser" and "sg surfgroup process" after allowing belonging ports.
The main output of LINFW3 consists of an UNIX fundamental usability also by one shell-script only

fast script-switching through the Dialog-menu of LINFW3 between the configurable main part and alternative parts with alternative scripts by dialog-menu-item "STATE-NEW-LINE-BLOCKS": either a) closed STATE NEW lineblocks on chain INPUT only or b) STATE NEW lineblocks on INPUT in addition with blocks upon UID- and GID-owner for the arranged surfuser and the surfgroup only on chain OUTPUT (using above concept) resp. c) like a) and b), but only for the user and group named root (this case is not unimportant for quick updates of software and packages), very effective for system-updates with auto-installation, some other updates, updating firefox, still disabling all hacker and quit all trojan
with section for router ( that can be supported in addition by tcp_wrapper )
hardened, cored UNIX; highest orientation on UNIX by UNIX-sh
iptables-rules are in effective order/structure
blockrate: default 100% (each packet), depending on the iptables-ver
protection up from the first connection built-up during system-start
prevention for health and time reason from always typing „iptables“
living support by authors of iptables. For (if ever necessary) expansion you can find plenty of sources out of the internet
ability for auto-configuration through own boot- resp. runlevel-init-script for quick autostarts, with statistics for quick tests on different iptables-versions/-sets;
ready for Samba (Netbios) within seconds. Each modules of iptables can be activated or not and therefore be tested
expandable, dialog-styled GUI in the look of iptraf (iptraf-ng(rosa2016.1, rosae2014.1)), one of the best for firewalls and well-known from kernel-configuration
In its configuration, domain names can get typed in and entered (strored) as much as belonging IP (domain names are recommended, as changing IP have to get changed in your /etc/hosts too)
Dialog based, scaled indication in percent of the estimated FW-Security-Level reached by each configuration, details about basing security-lacks,
with the opportunity to precise all evaluating factors and information about detailed single lacks within the configuration up to any aimed exactness
stability by TCP-FLAG-PROTECTION against sudden connection-breakdowns, shoot-ups (of processes like browser or FW itself), unexpected system-newstarts,
annoying application-closures, system´s and application´s hangs and halts
configurable kernel-parameter like martian-option, freeable from any false alarms
For installation all one need is an any secure, not necessarily the newest, a rel. tested and patched iptables, eventually patch-o-matic from
netfilter.org, dialog equal or greater 0.9b-20030316, because of INPUTMENU with several textfields and an editor like pico or nano (default: nano), all see
download-section
transparent: without any black or complicate source-code
 easy configuration by almost simple „yes“/„no“-settings
easy configuration by almost simple „yes“/„no“-settings
reliability: linfw3 is never the cause of any net-problems, neither during ftp-transfer, for tunneling, usage of a proxy-server or anything else
working upon all protocols and ICMP-TYPES e.g. to reach stealth-mode
detailed protocoling of all kind of attacks, if wanted, even martians by a window opening kwatch or the each log-entry of linfw3 in blue color blinking kwrited (/dev/pts/0 or /dev/pts/1 and so on), both minimized for the system-tray; for such purpose, linfw3 contains an exemplary configuration /etc/syslog.conf of syslog to envoke kwrited and to protocol FW-messages and system-messages into different logfiles within /var/log
user-section "user-defined" 65) to formulate Linfw3 up to a high-end, in order to allow more protocols than just UDP and TCP, to integrate iptables-rules using further iptables-modules and so on
LINFW3, section 63) iptables-rules for IPSEC (freeswan)
LINFW3, section 64),NFQUEUE and QUEUE, packets storing queues for the authentification-firewall-addon nufw and other applications
Many different test-opportunities consist of: a debugger for the syntax, a compare-base for "SHOULD- AND IS"-log-analyzes-compares;
full-compatible with other "additional" filters mentioned in step 2
CMD-audit for the easy prevention and deinstallation of all trojan
speed-optimisation: increase of data-transfer-rates up to 30% by maximizing TCP-throughputs, minimized UDP-(DNS)-delays by choosing the right TOS
(Type-Of-Service) and through prefiltering through beamy state NEW,
address-and packet-type-filter, address-verification, filter for blackholes
Internet telephony in simple activation and deactivation
during modifications: fast station-wise checks of syntax-errors
for nearly all kind of client-/server-architectures (router, single-user, samba-, ftp-client, samba-, ftp-server, ...)
fast overview of services by an integrated port-list
internet-lock for breakdown-situations
Blacklists are positioned right before the NEW-line-blocks, in order to block single IP, false alarms causing malformed IP, IP-ranges, on HTTPS, for router and LAN
prevention of smurf-, tcp-syn-flood, ip-spoofing, martians, land- and large-packet-attacks as much as all attacks basing upon too large packets
support of active and the more secure passive ftp-mode
Rules can be limited, disposed, exchanged and/or reconfigured by time
The files referring to linfw3 can be secured by one mouseclick - no chance for their manipulation from the outside
Route verification
Exclusion of all interfaces not declared explicitly
Special rules within the mangle table prevent the scan of the computer or router
log-statistics follow arbitrary time-periods
structured iptables-rules by theme
association of kernel-flags with belonging iptables-rules
full-compatible with additional filter-concepts like the already inherent port-scan-detector psd, arptables and arpwatch for protection against ARP-protocol based Man-In-The-Middle-(Proxy)-Attacks within a LAN, ebtables (Bridge-FW), system-logger syslog and log-alert-window kwrited, proxies like squid and privoxy, netfiltering proxies, browser-addons and spamfilter
LAN-prewarning-system: The integrated alarm-system also indicates each unwelcome local visit
Module-support (some modules are included in the rpm xtables-addons from netfilter.org or libxtables from SuSE, both are successors of patch-o-matic)
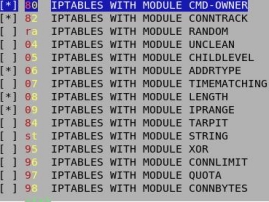
dialog support of module TIME-MATCHING
module STRING to filter any strings on packet´s field data payload (the field with the main part of information)
Please notice, that a script-blocker res. ad-filter is strongly recommended!
filtering of malformed or unusual packets by module UNCLEAN, MAC-addresses
blacklists
blocks all IP out of /etc/hosts.deny
additional filtering with program-/process-control, CMD-, User-,Group- Process- and Session-ID by module OWNER
adjustable blocking-rates of packets in percentages from 0 up to 100% (contin.), just 50 by default (each second package) through module RANDOM; to increase the blocking-rate from 1% up to 99% ); notice, that Linfw3 in main already blocks twice up to threefold, so that RANDOM becomes not essential.
PSD: Port Scan Detection: this all is possible with iptables (mga2), lib64iptables (mga2) and xtables-addons (OpenSuSE 12.3 or mga2).
 with CONNection-LIMITation and XOR-encryption of packages and connections
with CONNection-LIMITation and XOR-encryption of packages and connections
indication of slow, bad connections by TTL
modul QUOTA for volume-tariffs, TARPIT instead of DROP
modul IP-CONNection-TRACKing for further analyzes on traffic
usage of modul CONNBYTES for download-restriction and
modul ACCOUNT: traffic-ACCOUNT for counting visitors
modul RECENT to trap single IP by (trap-)ports like 139 - unlimited long or restricted by time
modul ECN
modul PSD: protocols and/or prevents detected serious hard portscans
modul POLICY: place for the integration of IPSEC
modul RATEEST: Router-balancing rules
many other modules, a right place for all
Notice: Depending on the version of itables and xtables-addons, not all modules might work. Find out, which one are working and those, who don´t by LINFW3.
IP can be entered directly with subnet-mask
Linfw3 within the K- resp. Startmenü: call it by /usr/bin/konsole -e sh /usr/local/LINFW3/fwdialog.sh (alternatively you can use xterm or any other terminal for konsole)
Do everything against fatal system-errors: Do you know the shutdown-supplement for WIN98/SE...? Each system-shutdown all connections are closed completely by the bootup-script resp. daemon linfw, quit before the open sourced linfw3 resp. iptables deactivate itself
 ebtables and arptables (both similar to iptables) can be added (resp. are already included) in LINFW3.sh at quit any place, here LINFW3.sh, end of section 49; all services ebtables and/or arpwatchd resp. arptables) have to be started beneath service iptables in /etc/init.d before, what can be done by MCC (services), ntsysv7, systemd, chkconfig or manually by "sh /etc/init.d/arpwatchd start", "sh /etc/init.d/iptables start" and "sh /etc/init.d/ebtables start"), for example (to add completely) take this basic ebtables: ebtables and arptables (both similar to iptables) can be added (resp. are already included) in LINFW3.sh at quit any place, here LINFW3.sh, end of section 49; all services ebtables and/or arpwatchd resp. arptables) have to be started beneath service iptables in /etc/init.d before, what can be done by MCC (services), ntsysv7, systemd, chkconfig or manually by "sh /etc/init.d/arpwatchd start", "sh /etc/init.d/iptables start" and "sh /etc/init.d/ebtables start"), for example (to add completely) take this basic ebtables:
iptables-equivalent for ebtables: $ipt -A FORWARD -s $myip -m mac ! --mac-source $ ETHERNET-CARD-MACADDRESS -j DROP # myip is the local (static) IP like 192.168.178.14
followed by ebtables:
ebtables -P FORWARD DROP
ebtables -A FORWARD -p IPv4 -j ACCEPT
ebtables -A FORWARD -p ARP -j ACCEPT
ebtables -A FORWARD -p LENGTH -j ACCEPT
ebtables -A FORWARD --log-level info --log-ip --log-prefix EBFW
ebtables -P INPUT DROP
ebtables -A INPUT -p IPv4 -j ACCEPT
ebtables -A INPUT -p ARP -j ACCEPT
ebtables -A INPUT -p LENGTH -j ACCEPT
ebtables -A INPUT --log-level info --log-ip --log-prefix EBFW
ebtables -P OUTPUT DROP
ebtables -A OUTPUT -p IPv4 -j ACCEPT
ebtables -A OUTPUT -p ARP -j ACCEPT
ebtables -A OUTPUT -p LENGTH -j ACCEPT
ebtables -A OUTPUT --log-level info --log-ip --log-arp --log-prefix EBFW -j DROP
# If you have many such rules, you can also use the among match to speed up the filtering
ebtables -N MATCHING-MAC-IP-PAIR
ebtables -A FORWARD -p IPv4 --among-dst 00:11:22:33:44:55=172.16.1.4,00:11:33:44:22:55=172.16.1.5 -j MATCHING-MAC-IP-PAIR
# We first make a new user-defined chain MATCHING-MAC-IP-PAIR and we send all traffic with matching MAC-IP source address pair to that chain, using the among match. The filtering in the MATCHING-MAC-IP-PAIR chain can then assume that the MAC-IP source address pairs are correct.
...
https://ebtables.netfilter.org/examples/basic.html
Linfw3, concipated to leave the word firewall forever behind yourself within short time
 

Erscheinungsdatum: 12.31.2006
Updates: 06.27.2025 ( removing a bad conditioned rule, that enpabled unpredictable SSL-connection-build-ups, ... ), 03.29.2023 (intergation of rules for Gmail (IMAP))
 Download from this server (browser-addressline): Download from this server (browser-addressline):
linfw3-1.1.2-1.tar.gz (recommended), checksum md5: 0c1605d8f1e8f9ac9d9e14ef10fb1897, sha: 608c86dc456b0437b3f6afbd330313a70be9f31a
linfw3-1.1.2-0.noarch.rpm (predecessor version)
linfw3-1.1.2-0.src.rpm
Please type in this packages or tarball into the address-bar of your browser like "https://gooken.safe-ws.de/linfw3-1.1.2-1.tar.gz".
On patches, malfunction and bugs, please mailto: info@gooken.de. Then your name will be listed in the changelog.
 Additional filter concepts
Additional filter concepts
Be such careful not to forget to reinstall iptables-rpm after you have installed linfw3 and all the packages from your distribution! The Filesystem Hierarchy Standard (FHS) defines the directory structure and directory contents in Unix and Unix-like operating systems, maintained by the Linux Foundation. The current version is 2.3, announced on 29 January 2004.[1]. Notice that protocol ftp remains insecure resp. risky. Enable ftp-downloads as seldom as you can (although ftp can not do us much harm after configuring Linfw3 quit right!)
Portscan-detectors like psad are useful additions for the iptables-based LINFW3, especially in the case of unnecessary opened ports by evaluating logentries made by protocolling rules of iptables. The arpwatch package contains arpwatch and arpsnmp. Arpwatch and arpsnmp are both network monitoring tools. Both utilities monitor Ethernet or FDDI network traffic and build databases of Ethernet/IP address pairs, and can report certain changes via email. Install the arpwatch package if you need networking monitoring devices which will automatically keep track of the IP addresses on your network. For not using GID-owner only, but also CMD-owner, kernel up to 2.6.12 is recommended. In this matter, look out for all kernel versions in future! To take firewalls in effect, some points of the checklist by Gooken have to be also checked out! The start of the process for iptables itself follows a delay, so that connections should be build up (manually) from a point past the newstart through the command "ifup device" with a device like eth0, and some connection opening or keeping routines may remain in the RAM during system shutdown, so that it is recommended to build down all connections completely quit before by "ifdown device".
 /etc/psad/psad.conf, extraction of an example /etc/psad/psad.conf, extraction of an example
#
### Supports multiple email addresses (as a comma separated
### list).
EMAIL_ADDRESSES myemailaddress@localhost;
### Machine hostname
HOSTNAME localhost;
### Specify the home and external networks. Note that by default the
### ENABLE_INTF_LOCAL_NETS is enabled, so psad automatically detects
### all of the directly connected subnets and uses this information as
### the HOME_NET variable.
HOME_NET any;
EXTERNAL_NET any;
### The FW_SEARCH_ALL variable controls how psad will parse iptables
### messages. If it is set to "Y" then psad will parse all iptables
### messages for evidence of scan activity. If it is set to "N" then
### psad will only parse those iptables messages that contain logging
### prefixes specified by the FW_MSG_SEARCH variable below. Logging
### prefixes are set with the --log-prefix command line option to iptables.
### Setting FW_SEARCH_ALL to "N" is useful for having psad only analyze
### iptables messages that are logged out of a specific iptables chain
### (multiple strings can be searched for, see the comment above the
### FW_MSG_SEARCH variable below) or a specific logging rule for example.
### FW_SEARCH_ALL is set to "Y" by default since usually people want psad
### to parse all iptables messages.
FW_SEARCH_ALL Y;
### The FW_MSG_SEARCH variable can be modified to look for logging messages
### that are specific to your firewall configuration (specified by the
### "--log-prefix" option. For example, if your firewall uses the
### string "Audit" for packets that have been blocked, then you could
### set FW_MSG_SEARCH to "Audit"; The default string to search for is
### "DROP". Both psad and kmsgsd reference this file. NOTE: You can
### specify this variable multiple times to have psad search for multiple
### strings. For example to have psad search for the strings "Audit" and
### "Reject", you would use the following two lines:
#FW_MSG_SEARCH Audit;
#FW_MSG_SEARCH REJECT;
FW_MSG_SEARCH DROP;
### Set the type of syslog daemon that is used. The SYSLOG_DAEMON
### variable accepts four possible values: syslogd, syslog-ng, ulogd,
### or metalog. Note: this variable is only used if ENABLE_SYSLOG_FILE is
### disabled, and this in turn will mean that the legacy kmsgsd daemon will
### collect firewall logs from syslog via the old named pipe mechanism.
SYSLOG_DAEMON syslogd;
### What type of interface configuration do you use? Set this variable to
### "iproute2" if you want to use the iproute2 type configuration.
### iproute2 does not use aliases for multi-homed interfaces and
### ifconfig does not show secondary addresses for multi-homed interfaces.
#IFCFGTYPE iproute2;
IFCFGTYPE ifconfig;
### Danger levels. These represent the total number of
### packets required for a scan to reach each danger level.
### A scan may also reach a danger level if the scan trips
### a signature or if the scanning ip is listed in
### auto_ips so a danger level is automatically
### assigned.
DANGER_LEVEL1 5;
### Number of packets.
DANGER_LEVEL2 7;
DANGER_LEVEL3 8;
DANGER_LEVEL4 9;
DANGER_LEVEL5 10;
### Set the interval (in seconds) psad will use to sleep before
### checking for new iptables log messages
CHECK_INTERVAL 5;
### Search for snort "sid" values generated by fwsnort
### or snort2iptables
SNORT_SID_STR SID;
### For systems with an init daemon like ´upstart´ that offer built-in process
### monitoring, it is not necessary to run the psadwatchd daemon. For such
### systems, the following variable can be set to ´N´ to disable psadwatched
### altogether.
ENABLE_PSADWATCHD Y;
### Set the minimum range of ports that must be scanned before
### psad will send an alert. The default is 1 so that at
### least two port must be scanned (p2-p1 >= 1). This can be set
### to 0 if you want psad to be extra paranoid, or 30000 if not.
PORT_RANGE_SCAN_THRESHOLD 0;
### For IP protocol scan detection (nmap -sO). While it may be relatively
### common for a host to trigger on tcp, udp, and icmp, it is more unusual if
### a host triggers on, say, five different IP protocols
PROTOCOL_SCAN_THRESHOLD 3;
### If "Y", means that scans will never timeout. This is useful
### for catching scans that take place over long periods of time
### where the attacker is trying to slip beneath the IDS thresholds.
ENABLE_PERSISTENCE Y;
### This is used only if ENABLE_PERSISTENCE = "N"
SCAN_TIMEOUT 3600;
### seconds
### Specify how often to timeout old scan data relative to CHECK_INTERVAL
### iterations. This feature is only used if ENABLE_PERSISTENCE is disabled.
### Note that for psad processes that have tracked a lot of scans, it is
### advisable to leave this threshold at the default value of 5 or greater
### because the scan tracking hash may be quite large.
PERSISTENCE_CTR_THRESHOLD 5;
### Limit the number of src->dst IP pairs that psad will track. The default
### is zero (i.e. unlimited), but if psad is running on a system with limited
### memory, this can be handy to restrict psad´s memory usage. It is best to
### combine this option with disabling ENABLE_PERSISTENCE so that older scans
### are deleted and therefore newer scans will on average continue to be
### tracked. A good non-zero value is, say, 50000, but this will vary
### depending on available system memory.
MAX_SCAN_IP_PAIRS 0;
### If "Y", means all signatures will be shown since
### the scan started instead of just the current ones.
SHOW_ALL_SIGNATURES N;
### Allow reporting methods to be enabled/restricted. This keyword can
### accept values of "nosyslog" (don´t write any messages to syslog),
### "noemail" (don´t send any email messages), or "ALL" (to generate both
### syslog and email messages). "ALL" is the default. Both "nosyslog"
### and "noemail" can be combined with a comma to disable all logging
### and alerting.
ALERTING_METHODS noemail;
### By default, psad acquires iptables log data from the /var/log/messages
### file which the local syslog daemon (usually) writes iptables log messages
### to. If the ENABLE_SYSLOG_FILE variable below is set to "N", then psad
### reconfigures syslog to write iptables log data to the
### /var/lib/psad/psadfifo fifo file where the messages are picked up by kmsgsd
### written to the file /var/log/psad/fwdata for analysis by psad. On some
### systems, having syslog communicate log data to kmsgsd can be problematic
### (syslog configs and external factors such as Apparmor and SELinux can play
### a role here), so leaving the ENABLE_SYSLOG_FILE variable set to "Y" is
### usually recommended.
ENABLE_SYSLOG_FILE Y;
IPT_WRITE_FWDATA Y;
IPT_SYSLOG_FILE /tmp/messages;
### When enabled, this instructs psad to write the "msg" field
### associated with Snort rule matches to syslog.
ENABLE_SIG_MSG_SYSLOG Y;
SIG_MSG_SYSLOG_THRESHOLD 10;
SIG_SID_SYSLOG_THRESHOLD 10;
### Expect that all logged TCP SYN packets include the options portion of the
### TCP header (requires the --log-tcp-options argument to the iptables LOG
### rule). If a SYN packet is received that does not include TCP options, then
### it may be created by a scanner such as Eratta Security´s "masscan"). Note
### that psad still does a check to see if at least one log message is seen
### includes the OPT field before expecting the remaining messages to also
### include this field.
EXPECT_TCP_OPTIONS Y;
# .. (SHORTENED.)
### Minimum danger level a scan must reach before any logging or
### alerting is done. The EMAIL_ALERT_DANGER_LEVEL variable below
### only refers to email alerts; the MIN_DANGER_LEVEL variable
### applies to everything from email alerts to whether or not the
### IP directory is created within /var/log/psad/. Hence
### MIN_DANGER_LEVEL should be set less than or equal to the value
### assigned to the EMAIL_ALERT_DANGER_LEVEL variable.
MIN_DANGER_LEVEL 1;
### Only send email alert if danger level >= to this value.
EMAIL_ALERT_DANGER_LEVEL 3;
### Enable detection of malicious activity that is delivered via IPv6. If
### ip6tables is not logging any traffic, then psad won´t know anything
### about IPv6, or this variable can be set to "N" (this would be slightly
### faster if ip6tables isn´t logging anything).
ENABLE_IPV6_DETECTION N;
### Treat all subnets on local interfaces as part of HOME_NET (this
### means that these networks do not have to be manually defined)
ENABLE_INTF_LOCAL_NETS Y;
### Include MAC addresses in email alert
ENABLE_MAC_ADDR_REPORTING N;
### Look for the iptables logging rule (fwcheck_psad is executed)
ENABLE_FW_LOGGING_CHECK N;
.
# ... ( SHORTEND )
 Start psad Start psad
before start: nano /etc/init.d/psad
exchange "daemon..." with line: "daemon /usr/sbin/psad --no-whois --no-rdns --no-snort-sids --messages-file /tmp/messages"
and start psad: sh /etc/init.d/psad restart
If the iptables-based Linfw3 remains a kind of trust for you, you can also (beneath Linfw3) activate the firewall of your router (AVM FritzBox!) , the perl-based (pre-)firewall nufw (mdv2010) and various acl-lists within the configuration-files for activated server. Tell us, if you think, that this solution is not secure!
For the prevention of weak-hosts (including localhost) command netstat -apn is listing opened ports related to opening programs. Such ports can be closed by firewall, deactivation of programs and/or changing or unlinking runlevel-scripts of /etc/init.d.
Generally all points of this list contribute to higher IT security-level. Therefore Gooken still asks you for your contributes for its completion!
You can login to KDE by all user as as much as by root after configuring /etc/kde/kdm/kdmrc (allowrootlogin=yes beneath further more interesting options like allowshutdown=true and AutoReLogin=false)). Beware the activation of Linfw3 resp. a closed connection to the network. This and not the many confusing postings to the same question of mine from alt.linux.de with their advice to reconfigure the login-manager can enable this quality (back) for root, same with most browser´s useragent (about:config, we prefer "Privoxy/1.0", followed by something like general.useragent.override (do not use overwrite) or through belonging addons) instead of recompiling as one of the many reason to keep yourself away from all that SuSE, with this newsgroup full of questions, typically generally not new to me (see other reports of Gooken...). If the geo-localization, the data about the local location of your computer should be concealed by firefox, set the possibility of WLAN-identification "geo.enabled" to "false", see links how to do this within other browsers. Also have a look on the performance increasing settings for firefox from our linksite, links, in the section for alternatives.
 Secure E-Mail-services Secure E-Mail-services
Secure E-Mail: Secure E-Mail-mailboxes by comparison
Howto send, receive and store E-mail securely, heise.de, 11.04.2021
Some E-Mail-services do pay attention for the privacy of their user, collect only absolut essential data and encrypt as many E-mail-messages as possible. Which secure E-Mail-mailbox is suitable for whom?
Most important short-facts
So called secure E-Mail-services encrypt the mailbox and support the sending of encrypted messages for their users.
These mail-provider care much for the privacy of their user. As they resign completely from advertisement, mailboxes cost a monthly fee.
The range of functions of such services just differs in detail, for example about storage capacities.
Whoever looks out for the highest security and privacy as possible should choose a service from Germany. These are Posteo, Mailbox.org and Tutanota.
https://www.heise.de/download/specials/Secure-E-Mail-Sichere-E-Mail-Postfaecher-im-Vergleich-6237824
 Kmail (Email-client with PGP and Antivirus Scanner) Kmail (Email-client with PGP and Antivirus Scanner)
 "Alternative: claws-mail"
"Alternative: claws-mail"
 fr2.rpmfind.net: "libspf2 is an implementation of the SPF (Sender Policy Framework) specification as found at: http://www.ietf.org/internet-drafts/draft-mengwong-spf-00.txt fr2.rpmfind.net: "libspf2 is an implementation of the SPF (Sender Policy Framework) specification as found at: http://www.ietf.org/internet-drafts/draft-mengwong-spf-00.txt
SPF allows email systems to check SPF DNS records and make sure that an email is authorized by the administrator of the domain name that it is coming from. This prevents email forgery, commonly used by
spammers, scammers, and email viruses/worms."
A lot of effort has been put into making it secure by design, and a great deal of effort has been put into the regression tests."
Kmail ( German insultation for you as a camel )?
kplayer, kmplayer (working upon phonon), kmail including kontact, browser and filemanager konqueror, filemanager dolphin and krusader, kdeenlive and kino, konversation, klipper, koffice, kivio, kwrite and kate, file-and E-mail-encryption kgpg, burner k3b, kompozer, kaudiocreator, kover, konsole, kuickshow, kbillards, kde-Desktop, kde-Plasma, kde-Desktop-Effects, kmenuedit, ... nevertheless we almost do believe, that software is really much better and more reliable than that (kept up-to-date) OpenSource one beginning with "K" - for KDE resp. widgets out of Qt from Trolltec.inc like so many (if not all) software from introduced UNIX/Linux!
In the same way of Mozilla Firefox, the many information including User-Agent within the header of Mozilla Thunderbird (we refer to version 3.0.1 and 10, actually, also going: ESR (el6, el7, rosa2014.1) ) can be changed: Click onto edit -> settings -> register card General -> and overwork the configuration. Kmail manages this too: Click onto settings ->, configure Kmail -> E-Mail-Editor -> Header -> type in one header without colon, in this case User-Agent and assign any (short) expression. Kmail can be configured in detail within file kmailrc out of .kde4/share/config sectionwise: [General] CloseDespiteSystemTray=true for the behaviour during the closing (finishing) of kmail, [MDN] SendMDNsWithEmptySender=true for the acknowledgement of E-Mail-receipts, [Reader] with ShowUserAgent=true (or false), [Composer] MaximumAttachmentSize=30 (in megabyte) and so on. As already recommended, E-mails should be always encrypted by their includes and be sent and receipt only over encrypted TLS-connections too. The receipt by kmail is secure, but If you do not want the word "kmail" in the header X-sender of the E-mail you send, you have to choose another E-mail-client like thunterbird with "thunderbird" in the header instead involving a for us unknown server from third party on port 641 or so as a result of conntrack of LINFW3. Actual Thunderbird like ESR (el6,el7), do not do this, so updates are recommended. Notice, that Kmail is working very slow in comparison to Thunderbird. That has to do with the virus-scanner clamav. But in comparison with kmail, the much too fast emails receiving Thunderbird seems not to integrate the virus-scanner (clamav), although the integration of clamav can be configurated too. If you handle email-attachements with care, you can delete the filter-rules for clamav from menu. Spamassassin has got a tiny virus-scanner in one of its modules. To increase the speed a little bit more, use bogofilter instead of spamassassin and filter out email by the sender you already know having a minimum size of some KB (we suggest 10 KB), before the filter-rules for clamav can take into effect. Then "camel" Kmail is running even faster than the thunderbird flies!
 One advantage of kmail is, that a menu appears each request for the sending of the E-mail (resp. spam) from the mailer or freemailer with following options each E-mail to choose: One advantage of kmail is, that a menu appears each request for the sending of the E-mail (resp. spam) from the mailer or freemailer with following options each E-mail to choose:
1 "send the e-mail", 2 "keep it on the server" and 3 "delete it from the server" - that means all right before the sending of all the e-mail !
[ SOLVED by sources out of the internet: kopete, kmail, kontact and so on do not start because of a khtml-css-version conflict of html4.css. ]
Add into /usr/share/apps/.../css/html4.css the following line right up at first at the beginning:
KHTML_STYLE_VERSION: 1
It is also strongly recommended to read the following article written by Mike Pilone:
"It is widely known that POP3 is a very insecure protocol, since it is a plain text protocol that transmits passwords and usernames with no protection. Anyone on a private network can quickly sniff packets and determine all the passwords used on the network. Although advances in POP3 authentication have surfaced (APOP, SSL, etc.) many servers still use the old plain text format.
SSH tunneling is the process of establishing a secure, encrypted tunnel between you and the mail host. This tunnel can be used for anything, but by using the Precommand feature of KMail, I will show you how to use a tunnel for POP3 and SMTP.
Signature for and encryption of E-mail (E-Mail) with PGP/MIME and the help of the gnu-GPG-Privacy-assistent gpg (mdv2011 or mdv2010.1) and GnuPG (el7, el6, mdv2010.1):
At first, Kmail or any other E-mail-client should "not be allowed to load extern references". Also prefer Plain-Text instead of the view upon HTML-messages in settings of Kmail, what is demanded by reports from News&Links#computer.
Now following packages should be installed:
KGpg
gnupg-agent
gnupg
pinentry-qt
Configure GnuPG and the gpg-agent
Enter or uncomment within ~/.gnupg/gpg.conf the following line
use-agent
Within ~/.gnupg/gpg-agent.conf add at the end of the lines:.
pinentry-program /usr/bin/pinentry-qt
no-grab
default-cache-ttl 1800
and start the gpg-agent:
eval "$(gpg-agent --daemon)"
Now make a test with another key-id as listed:
echo "test" | gpg -ase -r 0xDEADBEEF | gpg
Confirm yourself, that the OpenPGP-backend is active:
"settings -> configure KMail -> securityt -> cryptographic-modules" should be set for OpenPGP."
Source: http://developer.gauner.org/kmail-pgpmime/index.de.html
https://docs.kde.org/stable5/de/kdepim/kmail/pgp.html .
In order to make it really work each start of kmail, write a shell-script for /usr/sbin with the following simple content:
/usr/sbin/startkmail-including-signature-encryption.sh
#!/bin/sh
killall gpg-agent
eval "$(gpg-agent --deamon)"
kmail
 Now start kmail always by sh /usr/sbin/kmail-including-signature-encryption.sh, if the E-Mail aimed to send should be encrypted and signatured. Otherwise firejail can used for kmail too. Or adjust firejail to enable these features. Now start kmail always by sh /usr/sbin/kmail-including-signature-encryption.sh, if the E-Mail aimed to send should be encrypted and signatured. Otherwise firejail can used for kmail too. Or adjust firejail to enable these features.
 Mouseclick-fast: Kill the together with kmail started gpg-agent by creating a file in /usr/share/autostart like kill-gpg-agent with the content exec=killall gpg-agent. Some ressources get freed by this. As known, try this for as much root-prozesses as possible. Mouseclick-fast: Kill the together with kmail started gpg-agent by creating a file in /usr/share/autostart like kill-gpg-agent with the content exec=killall gpg-agent. Some ressources get freed by this. As known, try this for as much root-prozesses as possible.
Enigmail (thunderbird (el6)):
/usr/sbin/startthunderbird-including-signature-encryption.sh
#!/bin/sh
killall gpg-agent
eval "$(gpg-agent --deamon)"
/usr/lib64/thunderbird/thunderbird
Like kmail by now, start thunderbird always by sh /usr/sbin/startthunderbird-including-signature-encryption.sh.
Some more configurations can be made within kmail:
kmail -> settings -> configure kmail -> identities -> change/modify/edit -> cryptography,
kmail -> settings -> configure kmail -> security -> "create messages", and within "warnings and cryptographical-modules"
You might want to autostart gpg-agent. This can be done by creating a .desktop-file gpg-agent.desktop in /usr/share/autostart with the entry exec=gpg-agent --daemon and name=gpg-agent.
OpenPGP (rpm-package gnupg). Encyption is done by the public key for the E-mail-address of the recipient, obtainable by CD/DVD, sent USB-memory-stick, out of the internet especially from the homepage, menu or editorial, per E-mail, key-server or that can be ordered through whois by phone. The key itself has to be imported into the key-ring by kgpg or "gpg --import keyfile". The sender can send his own public key in any attachement as a key file exported from this keyring too.
For the decryption of an E-Mail the include of the message is within a file like msg.asc within the attachement. This file has eventually stored into a home directory for decryption with kgpg or gpg by the belonging own private key. For this, all keys should be marked at least as "trusted" by kgpg or gpg.
As each key consists of its own passphrase, encryption gets secure - as much as the signature can be considered like a real signature.
"One kmail (camel) less!" Now both, encrytion and signment of E-mail should really function! So please tell us, if not!
Instead of presented small shell-script, for the receipt of E-Mail only, you still might like to start kmail by
firejail --nice=17 --profile=/etc/firejail/kmail.profile kmail
KDE KMail: Secure Email Through SSH Tunneling"
http://www.slac.com/~mpilone/projects/kde/kmailssh/
Signature and Decryption of e-mail with the help of GnuPG: https://docs.kde.org/stable5/de/kdepim/kmail/pgp.html .
So all you need is gpg and gpa, kgpg does not matter too. There, in the linked article, it is not mentioned, that the gpg-agent has to be startet as much as pineentnry, done by the command "gpg-agent --daemon [ --use-standard-socket ]", what can be entered in /etc/rc.local, but we found out, that this is not necessary. The with kgpg or gpa by ID and key signed key for encryption entered into Kmail-> Identity-> cryptography should consist of your own public and private key and your own email-address (of you as the sender). The pulic key from that key should be exported onto a key-server. Now, if you want to send a message (an E-Mail), Kmail automatically suggests the fitting public key of the recipient (and not the own one) from the keyring in gpa and gpg (kgpg and gpa) after pressing the lock symbol out of the toolbar of Kmail. If missing, import this public key from the key-server or by contacting the recipient for its ID (email-address or sequence of characters). Eventually use Enigmail of Thunderbird instead of Kmail: All e-mail-decryption is funcitoning, even without signature and without gpgms (MIME).
The internet offers the opportunity to download the filter-extension kmailpt consisting of perl-Scripts for Kmail to delete, separate and decrypt e-mail-attachements automatically and manually with the help of the gpg-agent. Two icons are presented in the tool-bar of Kmail as much aus two new items in the context-menu: http://jice.free.fr/kmailpt
Finally, choose a suitable charset for kmail in "settings" from menu like unicode (locale) and unicode.
More about Kmail including toubleshooting in News&Links withn section alternatives!
KDE 4: akonadi (API-cache) - nepomuk (desktop search) - kmail ..:
 Akonadi (UK) is essential required by kmail (of course this is not all the truth, remarks by us, Gooken: Empty all akonadi-tasks within akonadi (by akonaditray), what we´d like to recommend because of the following, and kmail will still work fine, or deactivate akonadi (by akonaditray) completeley and kmail might still work... !). Akonadi (UK) is essential required by kmail (of course this is not all the truth, remarks by us, Gooken: Empty all akonadi-tasks within akonadi (by akonaditray), what we´d like to recommend because of the following, and kmail will still work fine, or deactivate akonadi (by akonaditray) completeley and kmail might still work... !).
Demystifying Akonadi (UK), Sebastian K., seba̡s blog, posted on August 26, 2010
The exotic-sounding ´Akonadi´ refers to both a mythological figure and the KDE platform´s central information framework. This article will dispel some of the mystery about how Akonadi will improve performance and integration, and how it is being rolled out into KDE applications. I´ll also provide some insight how the technology works, and what will become possible with this new PIM framework.
Many people have been asking what the status of the new, Akonadi-based Kontact Groupware suite is. As I´ve been working closely with the PIM hackers, I thought I´d give my readers a heads-up on what´s going on and what to expect. In this article, I will often take KMail as an example for the port, but similar things apply to the other PIM applications that form the Kontact suite as well.
The What &How?
I´m sure many of you haven´t heard the name Akonadi yet, so let me quickly explain what it is. Let´s get technical.
Akonadi is a groupware cache that runs on the local machine, a shared data store for all your personal informatio. Akonadi offers a unified API to receive and synchronise data with groupware, email servers or other online services. Agents called "resources" are responsible for communicating with the remote service, say your email server. These resources run out-of-process and communicate via separate control and data channels with the mothership (your local Akonadi). Resources are easy to implement and can interface any data source with Akonadi, be it your local calendar file, your companies groupware, email servers or address directories, or anything else you can come up with. More on that specifically later.
The Akonadi groupware cacheA common misunderstanding is that Akonadi is some sort of groupware server. In fact, Akonadi does not store any data itself, but just provides a common means to access data to your local applications.
So Akonadi does not store user data, it caches it. The user data is still stored in the traditional formats, be it on an online server (for example IMAP) or local files (ICAL calendar files). Locally, Akonadi provides a cache to speed up access and to make collections (email folders, for example) and their items available offline. To allow Akonadi to work on both powerful desktops and lean mobile devices, Akonadi can use different databases for its cache. Currently, the most complete backing store for Akonadi is MySQL, but PostGreSQL and sqlite backends are also available. In the case of MySQL, the database is started and handled by Akonadi itself, using a local socket, and no network access. This is intentional, for speed and security, since Akonadi´s database is really only a detail of the implementation.
The storage concept of Akonadi is straightforward. The team looked at many types of PIM data and found that items stored in folders are common to all of them. In Akonadi, Items represent mails, contacts or other individual pieces of data Folders are generally referred to as Collections, which can contain other Collections. Items themselves carry a type (using the freedesktop.org standard mimetype definitions), metadata and the actual data payload. Items can be identified by URLs. This URL is of course only valid locally, but it allows passing references to Akonadi items and collections around without copying the actual data. This makes Drag and Drop across applications (or in my favourite case, from the email notifier in Plasma into KMail) very easy. The receiving application can use any Akonadi client library to take the Akonadi URL and fetch its headers, or data. Akonadi Items may be retrieved partially, so if an app wants tod display a list of emails, it doesn´t have to copy around the whole inbox, attachments and all, but can just ask for a list of headers of those emails.
In order to access the Akonadi cache, and more importantly the underlying data, you can use one of the Akonadi access libraries. To my knowledge, there are Akonadi bindings for GTK+, Python and the Qt-style Akonadi classes already available. As you can see in the diagram, the design allows for different ways of accessing the Akonadi data, in the diagram the examples are called the "GNOME API" and "KDE API".
As you´d expect, I´ve mostly worked with the KDE API, which you can find in kdepimlibs. This Qt-style library has been available for a couple of KDE Platform releases already, and is being further enhanced for more coding convenience, stability and performance all the time. There is a bunch of job classes, that allow for async access to Akonadi items. Relatively new are the MVC classes, notably EntityTreeModel and friends. The ETM and its friends and API sugar around it also provide async access to Akonadi data as well, and also allow for easier sorting, querying and filtering of all the data and metadata. Metadata handling is another very interesting aspect of Akonadi in itself, more on that later, as well.
Many people are interested in the current status of Kontact´s Akonadi port. Initially, KDE had planned to release the new Kontact along with the rest of the KDE Applications 4.5. This did not quite work out, so we pushed the release back a bit, and are planning to release it along with one of the 4.5.x updates. The current plan is to release the Akonadi port of Kontact still this year. In contrast to our usual releases, this step is a bit different. Since PIM data is critically important, we are extending the beta phase until the Akonadi port of Kontact passes a much wider range of QA tests. When we are able to release depends a lot on the feedback we get from users. We are therefore making available monthly beta releases of the new Kontact suite. Data loss in this late phase of the port is extremely unlikely, and we made sure that trying the new Kontact doesn´t mean you must now also do the switch. You can in fact just reinstall the old one and use that again, since separate configuration files are used.
Simply put, traditional email clients don´t satisfy today´s expectations and work flows around personal data. Well, this of course needs some explanation: Already in times when KDE 3 was state-of-the-art, we noticed that more and more applications became interested in PIM data. Popular examples are Kopete, the instant messenger which held its own list of contacts, data which is mostly duplicated, including the inefficiency and maintenance nightmare you´re facing when you duplicate frequently changing information. So you want some kind of interface for contacts, and it should be something service-like, after all, you don´t want to run a seemingly unrelated application(your address book), just to get some more rich information about your chat contacts. Then, there´s of course my favourite example: Email monitoring. In essence, a full-fledged email client is a bit of an overkill, if you just want to know if there´s new email in your inbox. On of those overkill aspects is performance, or rather resource consumption. The solution to this is of course to share all this data. By using one central storage, and an easy to use access layer we can share the data across applications, and enable applications to make use of already available personal data. Enter Akonadi.
[...] Akonadi has been built with performance and memory consumption in mind. Will Stephenson has put this very nicely: "In the 2.0 <= KDE <= 4.4 days, each program loaded the entire address book, calendars, and more specialised stuff like email, RSS feeds, and IM chat logs into its memory, so memory usage for PIM data increased linearly with the number of PIM apps running. Same goes for non-PIM apps using PIM data (the Kickoff menu´s contact search data, Konqueror´s Copy To IM Contact feature). Because Kontact is just a shell for KMail, KAddressbook, KOrganizer etc, it caused the same memory multiplication even though it´s all one process.
With the Akonadi design, only the Akonadi process loads all the data into memory. Each PIM app then displays a portion of that data as it needs it, so the amount of extra resources taken by each extra PIM app is smaller, and the initial amount of memory used by each app is less. It should also provide extra stability, because each app no longer has to maintain its own data storage infrastructure, with all the caching, integrity and performance gotchas that keep computing science graduates employed."
Plasma´s new email notifier
Plasma´s Email Notifier (alpha version)During Akademy, I´ve picked up the work on Lion Mail again. It is not quite done yet, but already looking very good. I´m nearing feature completion for a first release now, so I´m almost sure it will become part of Plasma 4.6 in January, currently it´s in alpha state but quite fun already. Interested users can of course check out the source from SVN, it´s currently located in playground unti the code is ready for review by my eagle-eyed fellow hackers. Lion Mail is a set of Plasma widgets that can be used to display and manipulate emails in Plasma. In Tampere, Finland, during Akademy, I´ve discussed design and workflow of email notifications with a lot of people, after that I sat down for some serious hacking and have already implement most of what I would like to see, email-wise, in Plasma 4.6. The main goal is to be non-intrusive, and making it as easy as possible to manage your email in your daily workflow. The email notifier provides a queue of your emails, but does so without the need to switch to the full-blown KMail, so no full context / attention switch is needed if you just quickly want to see what´s going on in your inbox.
The new email notifier sits, as you might expect, in your panel´s notification area. It´s hidden by default, but becomes visible when there are new emails in your inbox. When you click on it, you get a list of your new messages. Those messages are expandable, so you can peek into the email to quickly judge if it´s something you want to act upon right away, or not. The individual messages are interactive. When hovered with the mouse, four buttons overlay the email. These buttons allow you to mark an email as read, or important (and of course remove those flags). Disappearing emails slowly fade out, so you have a couple of seconds to undo your action before the list is cleaned up.
You can choose to display new email in arbitrary foldersUnfortunately, most normal email notifiers are pretty useless for high-volume emailers, especially if you use server-side filtering (which you should because it´s much more convenient when using multiple clients, especially mobile ones). In my case, I have about 60 folders, on3 different email accounts (work-work, private, gmail). Emails are filtered before they reach the client. I am personally far less interested in new emails in all folders called "inbox". The Plasma email notifier allows you to choose the folder you want it to monitor. You can also set up multiple folders. As a nice extra, you can choose to also display emails marked as important, either merged or in a separate list (actually, the latter is not implemented yet, but on my short-term TODO list :-)). Emails are draggable, so you can drag an email from the email notifier into a folder in KMail2 if you want to copy or move it there. As I mentioned before, we´re not actually dragging the email around, but an Akonadi reference as a URL. This is fully transparent between applications, and even across toolkit and access libraries. I´ve also written a full-fledged single email Plasmoid, which allows you to put individual emails on your desktop (or dashboard) for quick reference. Just drag the email from the list onto your desktop, and it´ll appear as Plasma widget there, expandable, with HTML if you´re into that. The missing bits are rather overseeable at this point: clearing the list, separate list for important emails, refreshing logic for individual folders and queuing the re-jigging of the list until the mouse moves out, so items don´t change under your mouse while clicking on them. Not just minor bugfixes, but at the current pace, also not a lot of work left to do.
PUSH IMAP
As you can imagine, the email notifier´s design suits itself very well for PUSH IMAP. PUSH IMAP means that instead of checking in intervals for new email, the server notifies your client when a new email comes in. This means less useless mail checks and more importantly instant notification when a new email arrives. With "instant" I mean within a couple of seconds. In my tests, it took between 3 and 17 seconds from pushing the "Send" button on one machine until the email showed up in the email notifier. That´s pretty neat compared to checking your email every 30 minutes or so. So it´s all the more important that new email notifications become too annoying, hence the non-intrusive approach to the UI. PUSH IMAP is currently only enabled for the inbox folder of a given IMAP account, and of course your server needs to support it. The first email received in Lion Mail using PUSH IMAP
Kontact Mobile
The migration of the desktop version of Kontact is another big step in Akonadi´s existence. Akonadi has its uses outside of Kontact on the desktop as well. The new Kontact Mobile suite builds on top of Akonadi as well, but offers a completely different UI, optimized for smartphones and touch-screen devices. Kontact mobile is part of the upcoming Kontact suite as well. The infrastructure is this way shared across the device spectrum while the user interface is optimized for a certain device and use case. Akonadi does the hard work of talking to all kinds of groupware servers in the background, and caching of this data if you want to make it available on the go. The Dot has an excellent article about Kontact mobile, including a cool screencast.
Beyond Groupware - Akonadi and the Social-Semantic Desktop
The new email notifier is a good example what Akonadi makes possible in the near future, but there are more things brewing in the kitchen. As Akonadi is a generic cache, it comes handy in a much wider number of use cases. In the future, Akonadi can take care of managing and caching all kinds of interesting data, as you can stuff into it what you want. One interesting case is managing your online photo collection. Akonadi can provide standardised photo streams locally on your machine which are backed up by online services. In the same vain, microblogging can be handled through Akonadi, free caching, searchability and semantic linking to your contact are made very easy this way. There is actually already a microblog resource for Akonadi available, I´ve heard rumours of a FlickR one as well…
Emails now also in the desktop searchAkonadi plugs into the Nepomuk semantic framework for its indexing and searching needs. Items in Akonadi are therefore magically available for applications using Nepomuk to query and display data. Tags and other metadata is shared across the desktop, arbitrary items can be linked semantically (think emails and attachments linked to contacts in your address book). Akonadi in Kontact does not only mean that Akonadi is coming to full bloom, but also the semantic desktop built on top of Nepomuk. One nice example is shown in the screenshot, where the KRunner mini-commandline (hit ALT+F2!) also finds emails now. Part of the semantic desktop are also the Activities, which provide context to applications. You can think of ´context´ as a project your working on, your current location, and many other "metadata" of your workflow. One features of Lion Mail which has been part of its idea from the beginning is showing different sets of emails per activity, the email notifier is built with activities in mind.
Plasma´s dataengines provide another fantastic opportunity for Akonadi to shine. The Plasma team is working on a generic cache for data supplied by dataengines, the idea is to transparently allow caching of arbitrary data from dataengines, so offline usage becomes completely transparent for many Plasma widgets. Akonadi forms one of the cornerstones of Project Silk which aims at deeper integration of online services and content into the user experience.
Concluding
With all the above in mind, there´s little less than a revolution going on in the groupware area. Akonadi matures further and makes possible a full-fledged groupware client in the form of Kontact, with excellent scalability and extensibility. Akonadi is built with a whole spectrum of target devices in mind, which shows in the Kontact Mobile suite running successfully on a N900. With more applications being available in their Akonadi versions, Akonadi will become a lot more useful, and enhance many other applications in the process. Akonadi also allows for a better user experience around email and calendaring in the primary workspace. Groupware is becoming a generic service on the local client. The upcoming new Kontact groupware suite is only the tip of the iceberg of what´s coming thanks to Akonadi. Quite inspiring, isn´t it?
Special thanks go to Will Stephenson for proof-reading the article.
Posted in Akonadi, English, KDE, Plasma, SilkTagged Akonadi, Hacking, KDE, Plasma, Silk
https://vizzzion.org/blog/2010/08/demystifying-akonadi/
Security audit for Enigmail and Thunderbird: Posteo warns against security leaks, 21.12.2017
https://netzpolitik.org/2017/sicherheitsaudit-fuer-enigmail-und-thunderbird-posteo-warnt-vor-schwachstellen/
Reader opinion by Gooken
Patched Enigmail >0.99 on the base of gnupg2 seem to work fine by now.
One more PGP- and SMIME-encrypting email-client with easy to handle en- and decryption, recommended by CHIP year 2019 and us: claws-mail (el6) with claws-mail-plugins (el6).
It is safer to login through a terminal for root by su (for superuser resp. root) instead of the general login for root like by the mask belonging to (here:) kdm. Therefore the file named su itself has to be set always correctly by the commands "chown root:root /bin/su" and "chmod 4755 /bin/su", where the suid-bit is set. With these commands lost permissions and ownership of su can be restored from another Linux-System after a mount.
E-Mail encryption
 2FA-configuration 2FA-configuration
GMX & Web.de: Howto secure your account by 2-factor-authentification, PC-Magazin, 17.07.2019
GMX and Web.de offer 2FA (2-factor-authentification) for more security. In this report t is shown, how 2FA can be configured for both popular freemailer.
https://www.pc-magazin.de/ratgeber/gmx-webde-2fa-einrichten-konto-absichern-2-faktor-authentifizierung-3200768.html
 System Integrity Check by IDS (Intrusion Detection Systems)
System Integrity Check by IDS (Intrusion Detection Systems)
In order to avoid childish operating systems without encryption, encryption should be performed as one can. So no way keeps away from external backups, especially by MCC with drakbackup!
You can use an Intrusion Detection System (IDS) with similar rules to iptables like
lids (PDF) to verify the work of LINFW3. IDS like watchdog and Samhain do scan from hard-disk for configurable, but several, almost longer periods resp. times during the increase of the access time, while those like the console-program tripwire and aide register attacks just the timepoint past their actual time up from the point of the manual or cron-tab envoked scan. Both IDS can be configured to scan some directories and files like those for configuration, especially directory /etc and /boot of UNIX/Linux. Notice, that IDE like aide also perfrom important checks by different checksums, atime, mtime and ctime
aide (el6), configuration: /etc/aide.conf. Start: Initialize the databasis through aide -i in order to update the databasis through aide -u.
The inotify-based taskmanager incron provides beneath psd of iptables (LINFW3) one of the best IDS, for he is able to control the file-system for changes and manipulations of directories and files. Have a look in News&Links # computer, look out for the report from PCWelt and see, how easy it is to configure incron him by "incrontab -e" for this purpose, although using LINFW3, you almost do not need an IDS anymore!
tripwire (el6): Tripwire requires two key-pairs generated during the installation or manually, a site-key to protect files used by several systems and a local key, in order to protect files belonging to the localhost including the tripwire-database itself. The manually way is to start sh tripwire-setup-keyfiles, before the initialization and configuration of the databasis through tripwire --init. Comment out all error-messages in /etc/tripwire/twpol.txt by commenting in belonging lines with "#" like #/proc/driver/rtc. Finish the configuraiton with twadmin -m P /etc/tripwire/twpol.txt. Now the intergrity check can start through "tripwire --check" or "tripwire --check --interactive". Of course the output of the check can be deflect to a file.
gnome-schedule (cron and crontabs): Regulary Tasks
Not only the configuration and start by buttons for daily, monthly and weekly within the security-section of MCC but also cron and crontab configuring frontend "gnome-schedule" can perform scheduled security checks and other checks: integrity checks, backups, data rubbish deletion and so on. This has got the disadvantage for the user, that the control over the computer gets influenced by the computer itself.
"Here it is hälpt you!"
For remaining weakness of netfilter and firewall upon connections opened by users, in conjunction with sensible data, all connection administrating processes like browser and ftp-client should be terminated resp. deactivated.
UNIX/Linux are well known as operating-systems for server. If the security-level is set to "server", or if you set REMOTE_ROOT_LOGIN and ROOT_LOGIN to false, one of the most important steps for security is done. Cases of vandalism
become quit impossible now! Linfw3 can harden this principle until such settings are made, but especially concentrates on the data-streams.
One more risk remains in the way from the inside through boot of other OS like from USB or CD/DVD for achieving root-rights passing by even the password protection of bootloader like lilo, what is enabled through a simple reset of the BIOS or by exchanging the mainboard, furthermore offering the opportunity for password hacks. Partition-manager indicate the existence of tools to "spear" access through partitions independent from file systems. Therefore only System-Administrators should be allowed to install new software!
 Guaranted password protection is achieved by the method Two-Factor-Authentification similar to online banking per PIN and chipcard. There a login follows within two steps: one for the typing in the pin or password, the next step for the typing in of a code sent by an SMS to the user´s handy or smartphone each time after you entered the PIN, changing each login.
Guaranted password protection is achieved by the method Two-Factor-Authentification similar to online banking per PIN and chipcard. There a login follows within two steps: one for the typing in the pin or password, the next step for the typing in of a code sent by an SMS to the user´s handy or smartphone each time after you entered the PIN, changing each login.
Some more security tipps we once described in our step 2 are already well known like checking the signatur and checksum by comparing it with the key from installation-DVD/CD, the check of file-integrity by their own database creating progs like tripwire and the advise to resign from telnet, rlogin and ftp. IDS can be considered as a similar method we already introduced.
Linux was recommended by a good old friend of mine (today living in Hamburg - and still Linuxer). In this time I still used SE and asked myself on the phone, why I do not have it too! I had to wait for a quit stable SuSE Linux 8.2. Until this time, this has it costs! To go really sure, if you ask me in person, which computer-system to take, I recommend a quit old one but manufactured past 2001 at low energy costs, good would be with IDE to S-ATA adapter or direct support for hard-drives greater at least 65 GB and USB equal or greater 2.0, but still fulfilling ergonomic aspects, especially by access-time. System-requirements as a mix of CPU, capacity for RAM and hard-disk have always been minimal for Linux. To go really sure, we like to recommend Mandriva (previous name Mandrake) mdv.2010 64-bit (almost independent from platforms, but for well made for the small factorized ASUS Mini-ITX-220 from year 2009/2010 with crashfree bios, graphic, sound and LAN onboard, max. 8 GB DDR-2, crashfree BIOS (socked) with possible EZ-Flash from DVD or USB-stick, Samsung TSSTcorp. DVD-ROM SH-D162D, CD-RW BCE4816, 500-Watt-power-transformator SL-500A), source packages, the UNIX distribution like from the Linux fan article store, a very stable and almost secure behaving, quit full functional and comfort distribution from Poland and France with many applications like 3ddesktop (quit independent from many other distributions) by an exactly one version downgraded (patched) kernel 2.6.31-14, mdv2007.0 still with support of the mentioned iptables module CMD-OWNER, although the mentioned PID-agent works fine, so that you can use both owner concepts. Such operating system installs itself in less than one hour (in my case about 20 minutes) and runs stable and, as the errata-list shows, it does not need to be updated anyhow except ekiga softphone (if you do not use kphone, gphone or ohphone), alacarte for gnome (if really needed..) and Firefox 1.5 patched up to a fast and secure 2.0.0.12, inspite of some incomplete loading websites and marquee (HTML-tag) resigning from any higher versions! Firefox 12 up to Firefox ESR are also running fine (although I ask myself for the difference, except adblock plus did not work) as everything on this distribution. Even predecessor mdk10.1 from year 2004 convinced.
Related to Debian Linux, the typical linux bewaring mdv2007.0 (resp. mdv2010) with an immense repertoire of applications is quit easy to handle.
Manuals and information material to system-applications and other applications can be found in /usr/share/docs, within the help-center "khelpcenter", by the gnome-help-browser yelp, by the system-package-manager drakrpm, by rpm, by the command man <command> and info <command> , a first introduction by the commandname followed by the option -help, -h, --h.
As generally known, beneath an increasing amount of various applications accompanied with manuals resp. manpages within the directory man you can read by command man, all kind of server can be installed from DVD and activated within the MCC (control-center, kcontrol and drakconf.real (SuSE: Yast2), if you like, each newstart.
For mdv, before the boot of the operating system, run bootmanager grub, press F3, choose default and an adequate runlevel (3 up to 6) to type drakx11 into the opening terminal resp. konsole.
The Same for Yast2 started from a konsole/terminal. Mentioned MCC (control-center) summarizes most configurations and settings. At the very beginning, the many fonts importing OpenOffice was starting with some delays. Until now that´s all that should be patched, bugfixed or updated for that distribution. An excellent support was guaranteed for more than five years through rpmseek by the server ftp://ftp-stud.fht-esslingen.de. Each system-shutdown, the daemon of klean named tmpdel does the last important step to free the system from any unwanted files against maintenance. Together with apt and its graphical front-end Synaptic you can get from rpmfind.net, Debian packages can also be intalled (if ever needed...). Partitions got encrypted not only such with the sensible data but also other ones containing firefox, thunderbird and the ftp-client gftp, many executables and many configurations out of /etc and Linfw3 moved together with dialog to such encrypted one. In most cases, for the mozilla products, this managed after moving preloging directory out of /usr/lib to an encrypted partition after reconfiguring their shell scripts in /usr/bin and by adopting just two of their linked library (.so) files with ln -sf. So symbolic links should already be studied, before any data are moved onto encrypted partitions, quit the same for some directories within /etc and so on! The more parts of directories and files got encrypted, the faster the system runs! All in all this in conjunction with this excursion might be ready for eternity. Only the alsa sound-server sometimes does report errors like "fatal error: sound server overloaded, CPU aborted!" from time to time, although still everything worked (and sounded) fine! If this should still disturbs, an update of alsa leads into a placid stable system like our downloads without any error-messages and anything (although alsa still remained beta)- quit weird (can´t believe in the times before)! At last you can reconfigure xorg.conf for the mouse. This is necessary, if an unpredictable amount of windows is ever opening after the selection of several files by mouse lied frames and mouseclicks.
Keylogging resp. audit trace of commands on the server should be prevented, so look out for commands like "script -f pathtologfile/keylog.log" within /etc/profile enabling the audit of commands entered in bash. Timestamp for commands typed into the bash-history are set by adding "export HISTTIMEFORMAT=´%F %T ´" in /etc/profile.
 Spam-Filter
Spam-Filter
Train Spamassassin by
| sa-learn -L --spam --progress /~/surfuser/.kde4/share/apps/kmail/mail/Spam/cur/* |
and add additional filter-action "exec by program spamassassin -L" (Bogofilter:
| cat /~/surfuser/.kde4/share/apps/kmail/mail/Spam/cur/* | bogofilter -s |
Notice: For formatted printout (prittyprint), use bat instead cat.
 resp. bogofilter -s --input-file=single_filename" upon e-mails to registrate as spam. E-mail-clients like kmail automatically configure these spam-filter in their filter-part. Notice, that bogofilter works faster than spamassassin. The email themselves is placed in the directory "mail" sub the user-directory ~. Spamassassin is configured in the directory mail/spamassassin and /etc/mail/spamassassin. There modules of spamassassin can be activated and deactivated and the number of essential registrations for a mail as spam for incoming mail to register in future be set, we recommend to decline pregiven five times to one time only.
resp. bogofilter -s --input-file=single_filename" upon e-mails to registrate as spam. E-mail-clients like kmail automatically configure these spam-filter in their filter-part. Notice, that bogofilter works faster than spamassassin. The email themselves is placed in the directory "mail" sub the user-directory ~. Spamassassin is configured in the directory mail/spamassassin and /etc/mail/spamassassin. There modules of spamassassin can be activated and deactivated and the number of essential registrations for a mail as spam for incoming mail to register in future be set, we recommend to decline pregiven five times to one time only.
Linux resp. KDE offer a lot of useful functions. One of them helps to make windows sticky keeps windows from minimizing into the symbol-tray just by clicking into the upper left corner whenever further ones are opened - as known by (certain) other OS.
One generally should think about updates, especially not referring to the installed distribution. Information are exchanged suspiciously. Since mdv2007.0 the general need for them is not given and the possibility to achieve just the opposite in kinds of degress.
Diagnosis and Repair
Mindi of mdv like 2007.0 takes the installed kernel to create an ISO-file, that can be burnt on CD/DVD for the rescues. It offers a hugh set of UNIX-commands for maintanence. You still have to mount partitions to repair by the command mount and chroot.
| chroot mountpoint /bin/bash [-i] |
.
enpossibles to load the bash from the system to maintain. Then any UNIX-sh commands can be entered like paket-manager rpm, passwd for resetting the password, rcp and scp for copying files over the net. Alternatively you can use Knoppix, SuSE LiveEval or bootable USB-Sticks. SuSE Live Eval 9.2 did not manage to mount the partitions to repair, after I tried to increase the performance by setting the fstab-parameters noatime and relatime for the SSD, recommended by OpenSuSE, see our linksite, related to kernel >= 2.6.16 (I still prefer 2.6.12-31). fstab crashed awfully, even after booting in mode failsafe! But I was so lucky to have the great Mindi iso-burnt onto CD! In every case, look out for the mount-command by the common "man mount" resp. "mount --help".
Later on I found out, that mdv2007.0 set those mount-options in the file for devices named /etc/mtab already by itself. Now the computer resp. mouse seems to turn quit over by his clocking! So also notice, that not only btrfs, but also reiserfs fits for SSD, especially by setting the kernel-options relatime or noatime.
Whenever the boot-loader gets overwritten by partitioning from another operating-system, rescue by installation-DVD helps to install him again.
If the main directory for the temporary files named /tmp should be emptied the system-shutdown, a belonging option for experts from the section "system-start" of drakconf.real (resp. Yast2) can be chosen. For such demands you can also use the service resp. daemon tmpdel of klean, that can delete by seed (batch file editor), rm, srm, shred, wipe and by blanks. The secure deleting srm is working like the "insecure" deleting rm.

| wipe -f filename |
 shred -fu filename
shred -fu filename
|
 srm -dfr directory_or_filename
srm -dfr directory_or_filename
|
In the case of boot-failures, especially long waiting time the initrd-Ramdisk should be recreated by the command "bootloader --config --action rebuild-initrds" or "update-initramfs". Maybe the bootloader got overwritten or destructed. The mdv-installation-DVD, part rescue, can restore the MBR. Alternatively use bootloader-utils or the ISO-burnt CD "boot-repair". You can get the ISO-file to burn for free from Sourceforge.net, alternative: with method 1 up to 6, 1: super_grub2_disk_hybrid_xxx.iso.
Bootloader repair, http://linuxwiki.de/GRUB
Howto get the bootloader again:
The Linux-root-partition in this example is /dev/hda8 .
Start the Knoppix-CD (or any other Live-CD with grub installed).
Start x-term (or change to konsole)
sudo -s
# Make the root-partition writeable (through devices for chroot):
mount -o rw,dev /dev/hda8 /mnt/hda8
# Install all essential grub-files onto /mnt/hda8/boot/grub:
# and write the grub-masterboot-sector onto /dev/hda:
grub-install --root-directory=/mnt/hda8 (hd0)
# update-grub always works upon /boot:
chroot /mnt/hda8
# Create menu.lst:
update-grub
exit
reboot
Here an alternative basing on Knoppix::
sudo -s
# Make the root-Partition accessible:
mount -o rw /dev/hda2 /mnt/hda2
# Exchange the /boot of Knoppix with the original /boot
rmdir /boot
link /mnt/hda2/boot /boot
# Execute grub
grub
# and tell grub, that root is assigned to hda2
grub# root (hd0,1)
# and that he shall write the MBR
grub# setup (hd0)
# Leave grub:
grub# quit
# and restart the system
reboot
Starting with a distribution like mdv2007.0, all other linux-distributions can be quit good installed too. You have to care for glibc-version, where I´d like to recommend glibc of mdv2007.1. Or you can travel back into the past, where many apps of mdk10.0 out of seven CD from year 2004 can be also installed! But notice, that all this can results in an overwhelming repertoire of software almost found already on installation-DVD, where, see fr2.rpmfind.net, most software can be found for mdv!
Everything is configured by the system-configuraiton drakconf.real and the MCC (control-center including the login-manager for determining the user for logins as much as allowed for shutting down the system)..
Draksec: Periodical checks by draksec and drakperm are not essential anymore. A one-time performed, closing check for rootkits (tarned malware like trojan and for exploits) by utils like rkhunter zeppoo and chkrootkit by the result of "nothing found" can almost not be quit bad, while a login as superuser should ony be enabled for members of the wheel-group. A remote-login (of the superuser) should never be possible, what can also be configured by the login-manager of the operating-system. See step 2 about msec resp. draksec: The some access-rights and ownerships reconfiguring security-level 3- "high" might suffer the needs for single users, 4 - server, while mode paranoid disables any access completely.
General backup and recover of the system almost done by drakbackup out of the MCC (system-control-center) introduced shortly in step two.
In order to avoid errors, for compilation of the content of tarballs with gcc executing "./configure [--prefix=/usr]" resp. ./config [--prefix], cmake or similar commands at first, the underlying partition must be mounted with option exec. Therefore remember this option well, in order to set for most partitions almost the opposite called noexec!
UNIX/Linux-filesystems with errors become seldomly.
As a file-system we have chosen Reiserfs (where we can set performance-values for the already fast working SSD see links (our linkside), section alternatives).
This one is enabled to repair itself on data loss automatically within a short time, which is enabled by its Journalling feature. Manually, think of USB-sticks, you can repair all common file systems by the one fast working command named
|
lsblk lists information about all available or the specified block devices. The lsblk command reads the sysfs filesystem to gather information.
|
|
lsblk
|
Shortened mount and unmount of a LUKS-encrypted and discard supporting SSD-Partition by (rpm) pam_mount instead of using cryptsetup and mount:
|
mount -o discard device_filename_like_/dev/sda1 mountpoint_like_/mnt/mymountpoint1
|
|
umount.crypt mountpoint_like_/mnt/mountpoint1
|
... instead of the explicit, long termed
|
cryptsetup luksOpen device_filename_like_/dev/sda1 any_container_filename_like_container1
|
|
mount -o discard any_container_filename_like_container1 mountpoint_like_/mnt/mymountpoint1
|
|
umount /mnt/mymountpoint1
|
|
fsck [-t filesystem_name] [-C0] /dev/device-name -r
|
|
resp.
|
|
reiserfsck -check /dev/device_name [--rebuild-tree]
|
|
resp.
|
|
e2fsck -yf /dev/device_name (same for btrfs by fsck automatic through fsck.btrfs)
|
|
If the message: "Inode extent tree (at level 1) could be shorter IGNORED.": is shown, optimize (repair) the filesystem with:
|
|
e2fsck -fpDv -E bmap2extent /dev/device_name
|
|
or
|
|
e2fsck -C0 -f /dev/device_name
|
resp. for LUKS-encrypted partitions (cryptsetup), one is named sde1 for example, analogous for LVM with the partition name out of vgscan or lvdisplay):
|
cryptsetup luksOpen /dev/sde1 checkitout-container1
|
|
fsck -r /dev/mapper/checkitout-container1
|
|
resp.
|
|
reiserfsck -check /dev/mapper/checkitout-container1 [--rebuild-tree]
|
|
resp.
|
|
e2fsck -yf /dev/mapper/checkitout-container1 (analogous btrfs)
|
|
cryptsetup luksClose checkitout-container1
|
VERY IMPORTANT, FULL ATTENTION PLEASE!: So are there any problems with harddrives, SSD, USB-memory sticks, difficulties in mounting them or copying directories and files onto them? Never get them back:
Never plug USB-memory sticks into hubs! And as already written far above, exec=/usr/bin/kded4 should instead of exec=/usr/bin/kded be entered in /usr/share/dbus-1/services/org.kde.kded.service.
 Update dosfstools (this time from OpenSuSE) with the archived fsck and perform fsck upon the USB-memory-stick, fsck from right above was chosen with Option r for repair and device_file out of /dev like /dev/sde1 (accompanied with automatical search for routines for belonging file-systems like fsck.vfat after an unmount of belonging partitions by umount. fsck helps in most but not all cases for repair - fsck.<filesystem> with filesystem like ext2, ext3, ext4, reiserfs, reiser4fs, vfat, btrfs, ... . If errors should still occur, the partition is almost overfilled. Be careful, repeat performing "fsck"! And as already told, we recommend for mdv20 Update dosfstools (this time from OpenSuSE) with the archived fsck and perform fsck upon the USB-memory-stick, fsck from right above was chosen with Option r for repair and device_file out of /dev like /dev/sde1 (accompanied with automatical search for routines for belonging file-systems like fsck.vfat after an unmount of belonging partitions by umount. fsck helps in most but not all cases for repair - fsck.<filesystem> with filesystem like ext2, ext3, ext4, reiserfs, reiser4fs, vfat, btrfs, ... . If errors should still occur, the partition is almost overfilled. Be careful, repeat performing "fsck"! And as already told, we recommend for mdv20 10 (el7, el6) file system reiserfs-utils (el7) - we never have had any serious hard problems with it.. 10 (el7, el6) file system reiserfs-utils (el7) - we never have had any serious hard problems with it..
In order to mount an LUKS/dm-crypt-encrypted partition and having mount_pam installed just type
| mount [-o discard] /dev/device mountpoint (of course also per mouseclick in Dolphin or a certain plama of the taskline |
unmounted:
If the harddrive is out of order, try safecopy: http://www.pcwelt.de/ratgeber/Festplatte-defekt-So-klappt-die-Datenrettung-9787775.html. Many programs for repair are already integrated in fsck. fsck checks out filesystems like btrfs, ext4, reiserfs, reiser4fs and vfat:
| ln -sf /sbin/dosfsck /sbin/fsck.vfat |
Alternatively use even more precise checks and repairs of blocks like badblocks -ns, e2fck -f /dev/sdb6 for the sixth partition on the device connected to the second S-ATA-port named b (get informed by the partiton-manager which partition is named by what), for the repair of superblocks additionally with option b followed by the amount of superblocks and the same by reiserfsck upon files-systems, both in the case of serious deep errors like inode-errors, mdadm for LVM, e2fsck -c and mke2fs -c, details see manuals (man-command). You can tune reiserfs and ext4 by reiserfstune and tune2fs like

| tune2fs -c 1 /dev/mapper/cryptedroot_resp_home_resp_boot_partition |
(1 for each boot is recommended) resp.

| reiserfstune -m 1 /dev/mapper/cryptedroot_resp_home_resp_bootpartition |
or

| reiserfstune -d 7 /dev/mapper/cryptedrootpartition |
for the maximal amount of and maximal days before reboots (system-newstarts) of an ext-filesystem resp. reiser-filesystem are performed (upon the root-, home- and the unencrypted boot-partition and so on, but not upon the kernel-partiones proc, shm and tmp) automatically, regardless from the case, if errors have ocurred before or not. Value "1" for each boot is seriously recommended, taking about a few seconds only during boot. Instead of the container-file "/dev/mapper/cryptedhomepartition" any device-filename of a not encrypted ext-partition like /dev/sda1 can be entered.
fsck is also needed for USB-Sticks with malfunction. Duration (incl. repair even on VFAT32) of fsck and e2fsck -yf resp. reiserfsck lasts a few seconds only. Generally link fsck for (V)FAT-partitions by
| ln -s /sbin/dosfsck /sbin/fsck.vfat |
before the first use of fsck. This step is not essential for newer mdv-versions equal or higher mdv2010.
For Reiserfs type fsck -t reiserfs ... resp. fsck.reiserfs ... instead of fsck, analog other file-systems. Journaling-filesystems consist of a special structure, that shortens the time for repair very much, while file systems of MS windows like vfat and ntfs can not be repaired in any case. In order to go sure, the standard linux partition-manager should have always been used for partitionings and formattings. With such commands a repair can be done in most cases within few seconds! Notice, that from file-systems like ext3 and reiserfs, how difficult it is in opposite to vfat of MS Windows to restore once deleted data, while it is always possible to restore the system resp. data from garbage cans and tarballs (archives like zip, tar.gz and bz2), especially if the operating system has already started. Klean reflects a kind of dilemma in conjunction with the restoration of data. If you use the program qphotorec or rlinux, data recovery is not the problem, even not for the filesystems ext3 and ext4.
Did I already tell you? Damaged files from media like DVD and CD can be almost partially rescued by the command.
ddrescue: | ddrescue [ -options ] infile outfile |
Extern partitions are made and by mirroring (Limone:)

| dd if=filename of=filename |
is copying (mirroring) files, sectors, partitions and complete hard discs, ready for more.
Example:
#>dd if=/dev/hda1 of=/dev/hdb1
copies the 1. partition of the 1. hard drive onto the 1. partition of the 2. hard drive
#>dd if=dev/hda of=/dev/hdb
copies the complete 1. hard drive 1:1 onto the 2. hard drive - where the capacity should reach. CD/DVD-Rom drives are named by device files /dev/cdrom, /dev/dvd and /dev/sr0. Time needed for mirroring our complete SSD: 20 GB per hour and therefore around 6 hours. Processes for power-saving should be deactivated before. So nothing speaks against such backup on extern media of at least the free capacity of the original!
Backup: is performed by the MCC (drakconf.real) resp. Yast2, but it might be best to use the command dd we already decribed or to store the files and directories within a Tarball resp. ZIP-Archive. Prefer extern media to keep it, but as some person might wait for manipulaton of it, do not store anything online. The period for the succeeding backups should be short enough to take all actual data into account.
See the datasheed: If you use SSD with MC technique instead of harddiscs, backups might almost not be needed anymore, but more secure is more secure... .
"partimage" enpossibles to make img-screenshots from partitions excluding the mounted one for root.
WLAN (for the unimprovable one)
Software-packages should almost be from the best reliable source and therefore from rpmfind.net. Check out their checksums keeping integrity of downloaded files.
Following our steps, such strength is not essential. You can install Linux-Taballs from anywhere in the user-mode user, although it is still not recommended to do this in the files-ovewriting mode root.
Always use a modern internet-browser with modern mechanisms for security like a sandbox also containing a filter-mechanism against maligny websides before using it, for example those ones for phising and malware-protection of Mozilla Firefox in advantage with scriptblockers like ublock-origin and noscript.
Only use the browser-plugins really needed. They should be OpenSource. Chronique should be deactivated, Cookies deleted after each session, the private-mode should almost be preferred-
Let the browser question for all attempts to connect online by himself when asking for browser-updates and addons. Deactiate many protecition by clicking onto the proteciton shield in the statusbar.
Do not resign from SSL-encryption, if possible. Warnings should not be missed before the load of suspect websites. Passwords should not be stored- except in some cases by the master-password beyond the protection of certificates. .
Debian Ubuntu seems to be hopeless out. One reasan are established connecitons to Amazon. We do not recommend automatic software-actualisations. They cause mammouthed data-transfers and once more contribute to loose the control about the computer. Nothing can be more dangerous! So actualize from time to time, we recommend for mdv2010 each year and shortly past new-installation (and not during). Therefore use MCC. The full functionality of software is what counts in main, so you have only to look out for security-updates.
Never install programs inprehictable suggested online. The worst thing you can do is to enter also any passwords for their download.
Command "rpm - checksig paketname.rpm" evaluates a checksum for intergrity-check of downloaded files.
Following all introduced methods, for mdv2010 it is still possible to install so many progs as you want on SSD resp. harddisc.
Email should not be presented in the format HTML. Use format for text instead, so that intergrated images as the output of scripts can not function as backdoors.
Do not use the same password for different online-services. Regulary change such passwords. By manfacturer pregiven passwords should be changed immediately. Secure passwords consits of letters, special chars and numbers and can be suggested by programs like pwgen.
Java and Browser-Plugins: Resign from runtime as much as plugins as possible. Deactivate and activate java within the browser-configuration.
Sensible resp. personal data should be kept secret as much as possible. Within formulars, only fill out fields mandatory Never open e-mail attachements. Verify the sender by an identifying telephone-call.
Resign from wireless LAN (WLAN). If you do not want this, notice all those additional steps from our linkside to care for essential security. The protocol must be WPA2-encryption.
Periodically check out the security state of your system. This can be performed automatically by a MCC-Function taking care of many pregiven security-configurations and settings.
... Now I am waiting for many years for any system breakdown, essential repair for the file-system, the first hacker, trojan, virus, worm, spyware, dialer, update, upgrade, newstart, hard-disk-scan, restriction of file-capacities during copying and so on, but, good luck, that has become a quit seldom, if not an impossible case!
If an application ever should not start, try to start it by entering the name of its executable into the terminal. Then the cause is almost listed. In most cases, a simple repair can follow to start it again. The name of the executable itself can be found out by kmenuedit or within /usr/bin.
Thanks from manufacturer delivered rpm- (resp. deb) packages out of the internet, all drivers on the easy to handle mdv-2007.0 also work fine, even the one for Brother DCP-115C multifunction device from year 2012 I got from my relatives for free, costs for a cartridge less than 3 €, out of printer, scanner, copying and fax. Inspite of proprietary drivers for my nvidia graphic card I took the already integrated one without opengl-function, resp. I prefer the power-saving and less poisoning onboard (IGP) S3 Unichrome (3D!) with 64 MB of the VIA KM 400 by installing the 3D resp. many opengl-functions supporting uni- or the gl-functions less supporting openchrome-drivers presenting the even more sharp graphic without having any complications. First one, the unichrome driver, was already included into mdv2007.0. Good luck: If Linux sould ever be missing the driver for a graphic-card, it takes the standard-VESA-driver. Also onboard: the AC97-sound- and Ethernet-LAN-Chip). The air in my chamber refreshed, and the network-adapter enburdened itself. Network started up within few minutes without configuring, same for the printer.
If there should ever something be missed for mdv2007.0, you can extend it by upgrading the GLIBC from mdv2007.1. Now it is possible to install many packages from at least mdk10.0 up to mdv2010. Beneath this, emulation of Amiga through uae, basilisk for MAC, wine and wine64 with wine-gecko and wine-gecko64 and xwine for MS Windows 98 and/or XP helps to complete. Installed on linux-partitions, by the help of LINFW3 such programs are again running free from trojan and by the help of the access-control also virus-free, for about estimated more than 100.000 program-packages.
All in all this satisfying "snapshot" can be a quit good sign for UNIX-Systems in future. This reliability can be kept by licensing at least one distribution to high schools keeping the sources well and packing the binaries - the place, where UNIX / Linux origins.
In order to complete our computer-care, I prefered a brilliant about 48 cm display of a modern 1920x1200 (1366×768 @ 60Hz for films, websites and in order to prevent anatural widenings of that wide screen) WLED-TFT-monitor with 18 Watt power-consumption only for less than 100 € (asian AOC 943Fws), brilliant focus, in conjunction with well-functioning ACPI-functions and a power-saving mode of this operating system for the CPU (I still have the one 32-bit Sempron for this power-saving reason, that still is working far below 60 Watt, especially in the CPU-power-saving mode of Linux), the same aspect for the hardware from about year 2004, but with at least IDE and/or USB 2.0- or modern S-ATA- and USB 3.0-devices. Hard-disk can be replaced by one up to three Watt power-consumption , I read everlasting SSD-HDD from SanDisk (typ: Solid State Drive) by support of the S-ATA interface resp. IDE-S-ATA-adapter. Such modern powerful devices do consume power of around some Milliwatt only and have got very low access-times. Generally refresh your battery up (caution: such celle isn´t the the same celle!) from time to time (beware the contact of its maybe cheap-built socket!) and replace your hard-disk for life-expectancies of about five years, if you do not use an USB-stick instead, in order to get your computer started. If the computer ever has problems after his powering on, check out for the net-adapter and the RAM by type like DDR, DDR-2, DDR-3..., by regarding downward-compatible frequencies and by memtest, before the BIOS is reseted by a jumper of the mainboard or even flashed by firmware from a medium like floppy, CD or USB-stick. If BIOS strikes, check out the net-adapter and pull off slot-cards, that can cause many malfunctions. BIOS-configuration for PCCHIPS M851G with "SPD (automatic mainboard hardware detection) enabled" and for the case of non-IGP "PCI-graphic" and "ALLOCATE IRQ to PCI (IGP-graphic)" by disabled and AUTO-detection is strongly recommended. Against malfunction, also use as few slot-cards as possible. If the BIOS-chip is socked, in many cases it is also possible to order a complete new one including a special nippers by an address see our linksite. The computer can start and boot without any battery for the BIOS by default-BIOS-settings. Then each boot of the operating-system the NTP-daemon, which is part of each Linux-distribution, can set the date and time instead of the BIOS. Also it is possible to boot by USB-sticks, if a function-key like F8 is pressed. If nothing helps, even not following biosflash.com and www.bios-chip.com from linksite, the net-adapter should always run in mode standby. Please notice, that Gooken still can not give you any guarantees!
Howto adjust the TFT resp. monitor: http://www.pcwelt.de/ratgeber/Monitor_und_TV_professionell_kalibrieren_-Lebensechte_Farben-8525546.html
WLAN (for the unimprovable ones)
WLAN: troubleshooting and howto make secure: see News&Links, section Computer and section Alternatives. We recommend wired networking.
Fonts
mdv2010 provides all kind of Windows- and Linux-fonts. Fonts should not be presented distorte or smeared, so the screen solution should be the right one, selected auto by the sytem whereever possible. For our hardware the resolution is 1366 x 768 square pixel. Choose systemsettings or gnome-control-center to adjust fonts. Arial seems to looks a little bit slimed, so what about "Linux-Arial" Liberation Sans? We choosed Liberation Sans 10pt for our workspace. After an update of freetype (rpm resp. Tarball, rpm recommended) fonts can appear smallened or refined. But for a brilliant sharp display, we still prefer Arial.
 Gooken´s data sheed - always lifetime hardware Gooken´s data sheed - always lifetime hardware
Plastic rubbish, electronic scrap
How to avoid rubbish in Europe
More batch for recyclling?, tagesschau.de, 09.02.2021
Ob Plastikmüll oder Elektroschrott: Die Abfall-Mengen wachsen. Die EU will deshalb ein Recht auf Reparatur etablieren und höhere Recyclingquoten durchsetzen. Doch der Weg ist noch weit.
Waschmaschinen, die einen Tag nach Ablauf der Garantiezeit kaputtgehen. Handys, die nicht repariert werden können. Smarte Fernseher, für die es plötzlich keine Updates mehr gibt. Damit soll bald Schluss sein. Das Europaparlament will jedenfalls den Herstellern kräftig Druck machen und die Verbraucherinnen und Verbraucher dazu bringen, bewusster einzukaufen. Auch, damit unnötiger Müll gar nicht erst entsteht. "Denn wenn wir mit dem Rohstoffverbrauch so weiter machen wie bisher", sagt der niederländische Liberale Jan Huitema, "dann brauchen wir 2050 nicht einen Planeten, sondern drei."
https://www.tagesschau.de/wirtschaft/verbraucher/eu-recycling-muellvermeidung-101.html
 Badly wiped hard discs Badly wiped hard discs
Sensible company data per classified ads on Ebay, tagesschau.de, 30.06.2021
Gebrauchte Festplatten sollten gelöscht werden, bevor sie weiterverkauft werden. Schließlich können darauf sensible Firmendaten gespeichert sein. Eine BR-Recherche zeigt, wie einfach es ist, an solche Datensätze zu kommen.
Schlampige Entsorgung durch externe Dienstleister?
Genau hier kann den ARD-Recherchen zufolge der Fehler passieren: Manche Dienstleister, die mit der Datenlöschung beauftragt werden, kommen dieser Anforderung offenbar nicht sachgemäß nach.
[...] In einigen Fällen sind die Daten auf den Festplatten, die dem BR vorliegen, sofort nach Anschluss der Hardware verfügbar. In anderen Fällen sind die Festplatten wohl zwar formatiert worden, aber nur im Schnellverfahren. Das reicht nicht aus, auch diese Daten lassen sich wiederherstellen. Dabei sind auf praktisch allen modernen Betriebssystemen kostenlose Programme vorinstalliert, die ein sicheres Löschen von Daten ermöglichen.
https://www.tagesschau.de/investigativ/br-recherche/entsorgung-it-datenschutz-101.html
Data sheed: Super-powersaving mouseclick-fast Lifetime-Hardware: mainboard ITX-220, 19 Watt only, with brilliant high resolution graphic and sound, Ethernet with free activateable LAN-BIOS-Chip and SSE2-support at lowest costs
Look out for the right connection of the cables and their contacts (mainboard, monitor, netzwork, SSD/hdd (S-ATA), USB-memory-stick,...)! Do not connect the USB-memory stick into a hub, thuse a prolonging cable can be used. Do you remember? The trick from right at the beginning with the chalk in the inside of the tower keeps from troubles and defects as the cause of moisture and rust.
Now we can go on with our next theme: lifetime-hardware:
Mouseclick-fast "Universal Linux" on Celeron:
Data sheed ergonomic and mouseclick-fast 40-Watt-PC out of Intel ASUS-Mini-ITX-220-All-On-One-Mainboard 19W year 2009/2010 crashfree BIOS with EZ-flash from DVD/USB-stick, Operating System mdv2010.0, WLED-TFT AOC 18 W, 128 GB SanDisk SSD SDSSDP128 1W (year 2013), Chassis and stable netadapter all in all for about 200 € (Stand 2009-2016)
Linux/Unix - ("time to say goodbye")
Mandriva forever
Mandriva 2010 ( Mandriva = Mandrake + Connectiva + Lycoris) is the result of the merging of three distros; I have bought the following french-brasilian Mandriva past SuSE 7.3 professional and SuSE 8.2 professional): mdk10.1 (2004), mdv2007.0, mdv2008.0, mdv2010.0-final (updates of mdv2010 are already included; mdv2010 is almost compatible with Linux-Enterprise resp. CentOS (resp. ALT Linux) el3-el6, Fedora Core fc <= 18 and PCLinuxOS <=2010 and other distributions, many rpm from Mageia1 up to 4, mdv2011 and 2.6-and 3.x-kernel from mdv2012, Debian (also packages will not be missed here) by alien, dpkg and apt for mdv2010)
Show your computer the green card: extraction mdv2010.0-final for quit all devices, three DVD: mdv2010.0-final installation-DVD (X86_64, 64-Bit) plus update-DVD with listed software (packages) and updated SOURCE-CODE-DVD (mdv2010.0-final) you can order from us
Update- resp. upgradeable to mdv2010.1 and mdv2010.2 and Mageia (by packet mgaonline-2.77.29-1.mga1.noarch)
Mandriva is according to ISO-standard LSB 4.0
simple handling, almost independent from companies, banks and states
for beginners, advanced and professionals, most software is already known from 7 CD since secure and stable Mandrake 2004
Opensource from DVD 3, free access to the libraries
mouseclick-fast and secure Linux: free from instablity, viruses, trojans and other backdoors (certified resp. eliminatable through rkhunter and chkrootkit)
to get installed completely on SSD resp. harddisc without risks, if you want:
desktop-PC, server, tablet-PC, notebook, touchlet, kcm_touchpad and gsynaptics (touchpad driver), support for mobil phone, wammu (mobile phone manager), from harddrive, SSD, DVD/CD as much as USB-stick (of at least 4GB installable out of the pregiven one resp. Mandriva-one)...
all languages
MCC:
Software administration: installation and removal of software, actualizing the system, actualize-frequency, packet sources for installation and actualization, more opportunities for maintenance, packet statistics
Filerelease: configure FTP, configure the webserver
Network-interfaces: DHCP, DNS, Proxy, NTP, OpenSSH-Daemon
Hardware: view upon and configuration of the hardware, sound-configuration, configuring the 3D-desktop-Effects, configure the graphical server, keyboard-layout, pointer-device (mouse, touchpad), printer and printer queue, scanner , Fax-server, USV for power control
Network&Internet: network-center, network interfaces (LAN, ISDN, ADSL, ...), remove a connection, proxy, share internet connection with other computer, network-profiles, VPN-connections, hosts-definition
System: authentification, menü-style, Activate/Deactivate system-services, fonts, import fonts, date and time, regions and languages, view and anlayze system-logs, konsole with administration-rights, user- and group- administration, import of documents from other operating systems and settings, backups, snapshots, virtualization
Network-interfaces: shared Windows-harddrives and directories (SMB), shared harddrives and directories with Windows-systems (SMB), NFS (network filesystem), shared harddrives and directories by NFS, Web-DAV (Online harddrives)
Local harddrives: partitionmanager, CD/-DVD-burner, release partitions in the network
Security: finetuning of system-security-rights, Tomoyo-Linux, Firewall, authentification for Mandriva-tools, extended configuraiton of network-interfaces and firewall, child-protection
System start: Auto-Login for automatic login, boot-manager, display-Manager
Systemsettings separted into groups: Desktop (Workplace, workplace-effects, screen-edges, screensaver, program start display, virtual desktop), systemmessages (signals, messages), appearances (emoticons, colors, windows, GTK-styles and fonts, startscreen, stylel, symbols), windows-configuration, Adobe Flash Player (security settings), country/region/language (spell and grammar checkings, keyboard-layout and so on), personal information (fingerprint-manager, passwords and user-accesses, pathes), standard components (for the services), access help (speech processor, access), bluetooth, release, network settings (service-search, network-settings, network monitor, proxy, connections), screen resp. display (gamma, size and orientation, several monitors), date and time, printer configuration,
(infrared) remote controls, multimedia (audio- and videoprocessing), font installation, keyboard & mouse (short commands, joystick, mouse, keyboard, touchpad), key-combinations, Work-Design-Details, semantic search by Nepomuk and Strigi (mdv2010.2 only), Audio-CDs, Autostart, CDDB-requests, file allocation, service administration, digital wallets, digital cams, powermanagement (contrasts, and brightness, suspend modes, power-profiles), device-actions, hardware (device-integration through Solid), KDE-ressources, Open-Collaboration-Services, session management, storage media, login-manager, task planer, K3B-configuration-wizard, child protection, PolicyKit, Samba
Kernel 2.6.31-14.mnb2 (alternativ 2.6.33-7.mnb2) with enhanced hardware-support for all well-known desktop-PC and netbooks like ASUS EeePC, Acer Aspire One, MSI Wind and other ones, actual kernel from kernel.org (with SuSE-fillup, -insserv and -permissions, nash, udev, cpuid, ... from DVD 1 and 2), kernel-types, but almost kernel-modules (driver): desktop, server, Linus (Tovald´s Kernel), desktop, SMP-support, SMB, RSBAC, RSBAC-client, RSBAC-server, RT, TMB, TMB-Laptop, TMB-Server, libafs, squashfs-lzma (high compressed filesystem for embedded systems), UML (sandbox for userspace), virtualbox (system-emulation in hosts), vboxaddition, madwifi (WLAN), Xen (virtual machines), convirt (graphical Xen management), Netbook, ... with drivers broadcom-wl, em8300, fglrx, hsfmodem, lirc (infrared), lzma (data compression), nvidia, atmel-firmware, bluez-firmware, fxload, makebootfat (bootable USB-stick), kernel-rsbac (hardened), ...
Kernel of mdv2010.0, alternative kernel or enhanced kernel module (device drivers): kernel-desktop-2.6.39 (standard-kernel), actual kernel-3.x.x, kernel-desktop-3.4.1-1.4 (Mandriva Devel Cooker), kernel-server-2.6.39 (standard-kernel), kernel-linus-2.6.31 (original kernel from Linus Tovalds), kernel-rsbac (hardened kernel), kernel-uml (protected usermode-kernel), xen-Kernel (XEN-virtual machines), javabin_fmt (service to load the kernel modul, in order to directly execute Java applications and
applets), lirc-kernel (infrared-driver), kernel-tmb (laptop), kqemu-kernel (kquemu-driver for the standard-kernel), vpnclient-kernel (vpnc-driver), fglrx-kernel (nvidia-driver), em8300-kernel, broadcom-wl-kernel, hfsmodem-kernel, madwifi-kernel (WLAN-driver), libafs-kernel, lzma-kernel, kernel-rt (SMP-onboard-Realttek/Atheros-LAN-BIOS-Chip), fusion-kernel (fusion-driver), kernel-netbook, kernel-openvz (SMP: multiprocessor-kernel), libafs-kernel, kernel-kerrighed (kerrighed-Support), obencbm-kernel, psb-kernel, actuator-kernel (actuator-driver), lzma-kernel (lzma-driver), m560x-kernel, broadcom-wl-kernel, nvidia-current-kernel, nvidia96xx-kernel, nvidia173-kernel, netfilter-rtsp-kernel, fortune-kernel, vhba-kernel (vhba-driver), em8300-kernel, r5u870-kernel, r5u870-kernel-laptop, squashfs-lzma-kernel, vboxadditions-kernel, virtualbox-kernel, actual Kernel-3.X.X (from fr2.rpmfind.net or kernel.org), ...
kernel-uml: "User-Mode Linux is a safe, secure way of running Linux versions and Linux processes. Run buggy software, experiment with new Linux kernels or distributions and poke around in the internals of Linux, all without risking your main Linux setup. User-Mode Linux gives you a virtual machine that may have more hardware and software virtual resources than your actual, physical computer. Disk storage for the virtual machine is entirely contained inside a single file on your physical machine. You can assign your virtual machine only the hardware access you want it to have. With properly limited access, nothing you do on the virtual machine can change or damage your real computer, or its software."
free access onto kernel-source to select moduls by commands like make config and make gconfig
kernel-security-modules: to startup with speedboot=yes or speedboot=none, self-learnable "NSA" Tomoyo Linux with the four editors for the domains (processes) and their exclusion (security=tomoyo or security=none), selinux (like tomoyo, but from NSA), pxelinux
One everlasting update-source: ftp://fr2.rpmfind.net/linux/Mandriva/official/2010.0/x86_64/media/contrib/release
tabatha (popup-menu for tablet-pc and handhelds), enlargeable desktop-icons 32, 64, ..., 256 pixel, onboard and matchbox-keyboard (on-screen-keyboard), florecne (virtual keyboard), btkbdd (Bluetooth keyboard service), wizardpen (driver), ...
kernel-firmware (mga6, el6), if you want, plus kernel-firemware (rosa2014.1) plus kernel-firemware-extra (rosa2014.1) plus kernel-firmware (OpenSuSE 42.2, 32 MB) plus kernel-firmeware (OpenSuSE 13.2, 22 MB) plus linux-firmware (fc27), firmwarekit (Linux firmware tester), initrd-nonfree-firmware, prism54-firmware, speedtouch-firmware, zd1201-firmware, rt-firmware, ueagle-firmware, iscan-firmware (Epson flatbed scanner), ivtv-firmware (iCompression or Conexant video capture cards), ipw-firmware ((Intel PRO/Wireless WLAN Cards), mpt-firmware, multipath-tools, pmtools (check of Kernel ACPI tables), sane-backends-firmware, sane-backends-iscan, zd1211-firmware, Atheros/Realtek-LAN-chip-driver (atl1), ...
Graphic-card-driver resp. onboard (needed for some games only): independency from driver: (24 bit-) VESA-STANDARD-graphic-card-driver (for all graphic-cards) with svgalib, psb, psb-kernel, nvidia-kernel, ati-kernel with an ati-catalyst-control-center, atieventsd (ATI events daeomin), VIA, Intel, openchrome, unichrome, Xorg, nvidia-kernel, ati-kernel, atieventsd (ATI-events-daemon), VIA, Intel, openchrome, unichrome, 3Dlabs, Ark Logic, Chips, Cirrus Logic, Diamond, Digital, Intel, Matrox, NeoMagic, Number Nine, Redition Verite, S3, SiS, Silicon Motion, Sun, Trident, 915resolution, crystalspace (3D-engine), ...
parallel computing: lib64mm14, ...
OpenGL: mesa, glut (mesa, lib64mesagl1, lib64mesaglu1, lib64mesaglut3, lib64mesaglw1, lib64gii..., lib64gigii..., ), OpenAL (lib64openal) and alut (lib64freealut), jogl (Java-Bindings für die OpenGL API), ...
SDL and SDL2 (rosa2016.1, rosa2014.1 el7, el6): SDL-xxx, lib64sdl-xxx, ...
lsmod: lists all used kernel-modules (device-drivers), modprobe and /etc/.../modules.conf: manual or automized use of kernel-modules
util-linux (rpm) with fstrim support taken over by util-linux for mdv2011), support for allow-discard since kernel 2.6.36
man fstrim: Intensive usage of fstrim or "mount -o discard" can influences the life age of minor-qualitative SSD-devices. For workstation and server It is recommended to execute this command one time the week. Notice, that not all devices support a overruling-queue, therefore such overruling command causes minor performance for all devices and commands accessing the harddrive.
OSD (On Screen Display for volume, brightness, ...): kosd, xosd-tools, ...
Monitor/Graphics: driconf, xcalib, xgamma, redshift, MCC -> Hardware -> Monitor/Graphikkarte, ...
redshift - cares for more ergonomy by continuosly adjusting the color temperature of your screen depending from the time of the day and the location by latitude and longiute (for brilliant display and against becoming red eyes; we use the following command: "redshift -l 59.6:6.5 -t 6500:6200"; you can autostart it like many other programs in /usr/share/autostart), DDCcontrol (to control monitor-parameter like brightness and contrast, by software, i.e. without using the OSD and the buttons in front of the monitor), .....
Sound-card-driver resp. onboard: alsa, alsaconf, alsa-firmware, pulseaudio, arts, High Definition Audio, 2/4/5.1/7.1-channel audio, AC97, Dolby surround, ..., eventually missing printer-driver can be installed by belonging postscript-files (filetype .ps) or from the support-side of manufacturer (if you can hear no tone, check out kmix), ...
Printer-driver: cups for Epson, HP, Brother, Lexmark, Canon, Kyoccera, Turboprint (not included on DVD), MCC section hardware printers, localhost:631/admin, system-config-printer, xpp (configuration), upsddk (cups driver development kit), foomatic, gutenprint, ..., mpage brings more sites to print on one
To set up a printer configuration only a printer description file (PPD file) is required. A printer description file is not a driver. For non-PostScript printers a driver is needed together with a PPD file which matches exactly to the particular driver. For PostScript printers, a PPD file alone is sufficient (except for older PostScript level 1 printer models). The PPD files are provided in the following sub-packages depending on which kind of driver software is needed: rpm manufacturer-PPD and OpenPrintingPPDs-ghostscript provides PPDs which use Ghostscript built-in drivers. OpenPrintingPPDs-hpijs provides PPDs which use the hpijs driver from HPLIP. OpenPrintingPPDs-postscript provides PPDs which need no driver, xplsprinters (lists x-printers), ...
Installation of a printer-driver: MCC -> add a printer -> select the ppd-file (in our case out of the directory /usr/share/cups/model/), thats all, ready. You can set him there as the defauft printer, letter size (A4) and choose some color opitions like grayscale and truecolor. Follow the installation instructions from Brother.inc. or https://ubuntuforums.org/showthread.php?t=105703 .
cups-windows (pclos), /usr/share/cups/drivers: MS-Windows-printing-system and -drivers for all postscript-printer:
cups6.inf
cups6.ini
cups6.ppd
cupsps6.dll
cupsui6.dll
ps5ui.dll (out of MS Windows or download out of the internet)
pscript5.dll (out of MS Windows or download out of the internet)
USB 2.0 and 3.0 (under secure unmount), bluetooth (kbluetooth, bluez-firmware, ...) and firewire; madwifi and rt-driver, ...;.if a driver for LAN/Ethernet-Chip onboard should ever be missed and loading of modules like atl1 do not help, the driver for PCI-ethernet-cards for about 5 € also does its best, TV-card-driver, dfu-util (reflash firmware of usb-devices), ...
Credit cards and some other cards: pcsc or pcsc-lite
PCI: pciutils, pcitools, ...
Hardware database hwinfo for compatiblity checks
hwinfo --<hwitem> bios, block, bluetooth, braille, bridge, camera, cdrom, chipcard, cpu, disk, dsl, dvb, fingerprint, floppy, framebuffer, gfxcard, hub, ide, isapnp, isdn, joystick, keyboard, memory, modem, monitor, mouse, netcard, network, partition, pci, pcmcia, pcmcia-ctrl, pppoe, printer, scanner, scsi, smp, sound, storage-ctrl, sys, tape, tv, usb, usb-ctrl, vbe, wlan and zip, ldetect, hcl, ...
CPU: cpuinfo, cpuid (dumps cpu-info), cpudynd (power-saving-functions), cpulimit, cpufreq and cpufreqd on the base of cpufrequtils (automatic fine-tuning and exhaust of many CPU to mouseclick-fast (to resign from new ones in future), hyperthreading), uname (Anzeige des vollständigen Rechnernamens samt seiner Umgebung), tuna (el6), ...
Firewire: coriander - GUI for controlling IEEE1394-cameras, gscanbus (scans IEEE1394-firewire-bus) ...
ACPI, ACPI powermanagement (Modi: performance, aggressiv performance, Xtreme powersave and presentation; console-kit of powermanagement-debil should be activated!; empty screen, screensaver, shutdown, poweroff monitor, monitor standby, standby CPU, standby for harddisc, standby for the complete system, standby onto RAM and standby onto the harddrive (all functioning on listed hardware below, red. )
Manuals: khelpcenter (glossary resp. advise for the OS, applications and tools), man (manpages, if not in english, you also can get actual versions from rpmfind.net in the language of your country from other distributions as it managed us from mga5, margeia 5 of increased size), info, /usr/share/doc (including. books.rpm mit "Linux Installation and getting started", "Linux Programmers Guide", "Linux Network Administrators Guide, Second Edition" "Linux System Administrators Guide", "Linux Users Guide", "Linux Kernel Internals", "The Linux Kernel Module Programming Guide" yelp, rpmdrake, "--help" for quick help, info, howtos ...
elearning (computer course): dokeos, ...
Speech recognition and speech-output: festival and espeak, gnome-speech, jsspeex, CVoiceControl enables a user to connect spoken commands to unix commands. It automagically detects speech input from a microphone, performs recognition on this input and in case of successful recognition - executes the associated unix command.
KDE-start-image: Login splashes (after the login with kdm): hand with fingerprint, air,...
pregiven boot-splashes, designs, desktop-wallpapers, themes, kdm-themes, styles, windows, window-decorations, kwin-effects, wallpaper, mouse-themes, icons, colors, fonts, free choice of colors for title, progress-bar and so on, unllmited self-mades or for example from kde-look.org and kde-apps.org, ...
Window-manager: kwin, openbox, compiz and metacity
Desktop-manager: KDE 4.3.4 (or any version, KDE with plasma), GNOME, LXDE, XFCE4, fvwm, fvwm2, IceWM, Fluxbox, Matchbox, Openbox, Blackbox, e, enlightment, sawfish, drak3d, safe-mode, sddm (el6), GTB and GWB (Guido´s Toolbox, each more than 50 MB, pclos), ...
KDE-Icon-themes, K-Desktop-icons & Co.: free-positionable or ordered by criteria like "from upper left to lower right", storable positions, optional by a grid, within a free determinable directory, faenza icon theme with scalable icons (format svg), armor (desktop-mascot: person, smiley, tux, cat, ghost, eyes, BSD-mascot, bonhome, neko, worm, taho, ...), aphorisms, cowsay, superkarmba (system-monitors like on foils) and kiba, oneko (cat chasing the cursor), ...
Effects for the desktop (composite, if. translucency, since 2010, you almost need fast graphic-hardware to avoid delays): 3D-window-galery, 3D-windows-stack, cube, preview, showcase with miniaturized images, transparency, dimming, zoom, gliding, magnifier, shadow, wonderlamp, wave, ... on the base of composite: spotlighter (justable desktop-spotlight), ardesia (desktop-sketching), curtain (curtain to move on the desktop from one side to the other)...
KDE tuning with the monitor and graphic card: vsync, direct rendering, ...
Color-schemes: infnite: LinuxMint, Mint-RGS, Oxygen, Kinomoto-colors, Caledonia6, Lucky Eyes, Perso, Black Velvet, New Wave, glass of wine, openSUSE, Midnight, Aqua, Lightsteel, Blue Sky, Ardour3, Black Frost, Pink, Dracula, Midnight Sun, Gaia, Delta Colors, solarized dark, Tea Sun, Jupiter, la Ora Steel, Silicon, Wonton Soup, Cherry Blossom, la Ora blue, Polyester Orange Juice, Whitewater, Skulpture stone, Desert, Skulpture Vanilla, Win7, Evening Lilac, la Ora Orange, Honeycomb, ... by download
Desktop-design: any design from kde-look.org and kde-apps.org (user definable), Mandriva, blend, oxygen, silicon, slim glow, elegance, heron, Aya, Air, Mandriva, Klassik, Klassik-blue, Marysia, Metalized, Mirado, Neon Glow, Nitro, Old-Oxygen, Oxyglass, Oxywin, Plateau, Silicon, Slim Glow, Svista, ThinAir2, Tibanna, Tragedy, Transparet-sima, USU, Underworld, Unity Ambiance, Unity Radiance, Violet Pastel, XP-Desktop and Windows7 (MS), downloadbare oder hausgemachte, ximian-desktop, ..., XP-Desktop and Windows 7 (MS), downloadable or self-made ones, ximian-desktop, ... by download
Login-screens: Standard, G-Air, login-scan-splash-cg (hand-fingerscan), md2 (Mandriva2), Bespin, Powerpack, Simple, kde_XP, ..., downloadable
Types for desktop-wallpapers under more submenues (mdv2010.0): globus, pattern, Mandelbrot, color, weather, image (any importable wallpaper (bmp, jpg, ...), diashow, Time of The Day, ...
Desktop-wallpapers: Mandriva dolphins (mdv2010), Mandriva free (2007), aisbaa (Gentoo), Gentoo12.1-walllpapers, Debian-forest, bliss (XP), SuSE-bliss, Propaganda Vol. 1-13, xpenguins, ...
Screensaver: OpenGL, xfishtank, ...
 Plasmoids resp. plasma (applets) for the desktop and the controlbar (please notice, that in differnence to mdv2010-rpm-packages actually not all of them do function, so we have to wait, and that some of them get their information to present out of the internet): Daisy (free program choice within rings or bars), Lancelot (desktop-menu), timezones and weather, birthday-reminder, calculator, widget-dashboard, system-monitoring, multiple rowed fast-loader (more-rowed compressing collector for icons with optional mini-pull-down-(up-)menu), unit-conversion, LCD-weather-station, weather forecast, wordclock with timezones, accu-check, image frame, comic, egg-clock, jumping ball, colorchoosing stick, calculator, moon phases, zoom, social desktop, ToDo-lists, remember the milk, system-monitor, guitar-tuner, image-preview, widget-dashboard, birthday-reminder, flickr, language-translator, sun-system, fishtank, DVB-signal-meter, newsticker, Mountoid, Bundesliga, Facebook, Flickr, bsun (wandernde Sonne), FrustML resp. (Mensch-Ärger-Dich-Nicht), Fancy Tasks (quickstarter similar to cairo-dock), Koala (similar to Tamagocchi), Astrocalendar, Plasmio (SMS), daisy (desktop-icons in a cricle), 15 stones,Tomatoid, egg-clock, spell verification, blackboard, WorkContext (nepomuk) and much more ...
Plasmoids resp. plasma (applets) for the desktop and the controlbar (please notice, that in differnence to mdv2010-rpm-packages actually not all of them do function, so we have to wait, and that some of them get their information to present out of the internet): Daisy (free program choice within rings or bars), Lancelot (desktop-menu), timezones and weather, birthday-reminder, calculator, widget-dashboard, system-monitoring, multiple rowed fast-loader (more-rowed compressing collector for icons with optional mini-pull-down-(up-)menu), unit-conversion, LCD-weather-station, weather forecast, wordclock with timezones, accu-check, image frame, comic, egg-clock, jumping ball, colorchoosing stick, calculator, moon phases, zoom, social desktop, ToDo-lists, remember the milk, system-monitor, guitar-tuner, image-preview, widget-dashboard, birthday-reminder, flickr, language-translator, sun-system, fishtank, DVB-signal-meter, newsticker, Mountoid, Bundesliga, Facebook, Flickr, bsun (wandernde Sonne), FrustML resp. (Mensch-Ärger-Dich-Nicht), Fancy Tasks (quickstarter similar to cairo-dock), Koala (similar to Tamagocchi), Astrocalendar, Plasmio (SMS), daisy (desktop-icons in a cricle), 15 stones,Tomatoid, egg-clock, spell verification, blackboard, WorkContext (nepomuk) and much more ...
Gadgets, Apps-installer, Google-App-Installer...
Software::Android
Android Studio 2.3 released, pro-linux.de, 03.03.2017
https://www.pro-linux.de/news/1/24514/android-studio-23-erschienen.html
 Desktop-Screenlets: GUI screenlet-administration and -daemon with actually more than 100 screenlets plus downloadable ones, running in the foreground, background, scalable size, widget-option, many settings like: growing flower (to give some water and so on), slideshow, pager, control for adding screenlets, radio, meter, stocks, speech, sensors, ringssensors, ruler, convert, example of howto create a screenlet, copystack, clear weather from weather.com, ...
Desktop-Screenlets: GUI screenlet-administration and -daemon with actually more than 100 screenlets plus downloadable ones, running in the foreground, background, scalable size, widget-option, many settings like: growing flower (to give some water and so on), slideshow, pager, control for adding screenlets, radio, meter, stocks, speech, sensors, ringssensors, ruler, convert, example of howto create a screenlet, copystack, clear weather from weather.com, ...
Active Desktop: wallpaper, fly mode, slideshow, colors, time-of-the-day, globus: weather-maps, day-and-night, Mercator, original, Mandelbrot, patterns, desktop-icon-sizes, association for mouseclicks left, middle, right like freely set KDE-startmenu the left mouseclick upon the desktop, ...
KDE-Colors (qt-curves): LinuxMint, Mint-RGS, MAC-OS, Oxygen, Kinomoto-colors, Caledonia6, Lucky Eyes, Perso, Black Velvet, New Wave, glass of wine, openSUSE, Midnight, Aqua, Lightsteel, Blue Sky, Ardour3, Black Frost, Pink, Dracula, Midnight Sun, Gaia, Delta Colors, solarized dark, Tea Sun, Jupiter, la Ora Steel, Silicon, Wonton Soup, Cherry Blossom, la Ora blue, Polyester Orange Juice, Whitewater, Skulpture stone, Desert, Skulpture Vanilla, Win7, Evening Lilac, la Ora Orange, Honeycomb, .
..
Design, Styles: unifyable for gtk to all KDE (systemsettings), gnome-control-center, Diamond, Doomsday, Mandriva, Heron, Elegance, Neon Glow, Nitro, Oxywin, Oxyglass, PerlaNegra, Plateau, Blue Sora, Blend, Air for netbooks, Air, Ambience, Androbit, Arezzo, Atelier,. Black Glass, ...
infinite amount of designs
Taskline: from different desktop-manager and KDE with optional cairo-dock (3D-icon-desktop-look with zoom upon the icons following the mousepointer-position), glx-dock, kiba-dock, ...
wm-applets: wmweather (weather-applet), wmmoonclock (moon-pases), wmglobe, wmfishtime, wemmemmon, wmstock (stock market), wmnut, wmnat, wmwebcam, ...
gai-applets: weather, gai-sun (sunset time and sunrise time), gai-pal (verdicts), ...
gtkmotd (Message-of-The-Day-Display), ...
more applets: netapplet, printer-applet (mga5 for mdv2010), knemo, monitor-applet, KRandRTray (variable screen resolution), ...
Boss-key: alarm-clock-applet (SuSE 11.4), ...
kde-look.org: more design, themes, styles, kwin-effects, dekstop-icons, wallpapers, system-sounds, ...
Desktop-icons: svg, icon-themes, screenlets, ...
K-Menu in classic and modern look: kmenuedit (free configuration of the start-menu),
quick configuration by tiny orange half-moons within the right upper corner and the control-bar
Control-line for example with K-menu (plasmoid); terminal (plasmoid), MCC (system control), system-settings, quick launcher (plasmoid), opened windows (plasmoid), workplaces-desktop-switcher (plasmoid), E-mail-client, browser, system-area (plasmoid), system-messages (plasmoid), clock with calendar and organizer, power-on/off-button (plasmoid), desktop-settings half-moon, ...
font generator: fontopia (el6), ...
Quick launcher (example): out of help-center khelpcenter, telephone linphone3, sflphone, phonebook, addressbook, global atlas marbles, maps, cronie-task-manager gnome-scheduler, dictionary kdict, Linfw3, kmail, gftp, IRC-client kvirc, pocket calculator kcalc, speedcrunch, notices: knotes and tomboy, kteatime (alarm-ticker), qstardict and stardict (Dictionary and full-text-translator), gedit (Texteditor), Schreibtischglobus marbles, bosskey, ...
system-area within the control-line (tray, autostarted programs) for example out of: net_applet (NetworkManager), printer-applet (printer jobs), klipper, loudspeaker-symbol resp. mixer (kmix), kgpg (encryption keys), krandr (screen resolution), nepomuk (semantic search), USB-media (one more Plasmoid), ...
 Remote-Desktop and remote access (it might be wise to deinstall all packages (resp. deactivate programs and servces) for such remote, that you do not need...): chroot (Chrooting), putty, vino, kvnc, krdc, rdesktop, rlogin, rsh, tsh, telnet, ssh (OpenSSH), capture, concordance, ftpsync, sftp, ftp, proftpd, gftp, FileZilla, rexec, gexec, pam_mount, php_pear_remote_installer, rsnaphost, rstart, nc, scp, vmware: vmware-view-open-client (omv3, omv2013.0), portmap (NFS-server), smbd and nmbd (Samba), automount (to bring up NFS, the network file system), named (DNS), salt... Remote-Desktop and remote access (it might be wise to deinstall all packages (resp. deactivate programs and servces) for such remote, that you do not need...): chroot (Chrooting), putty, vino, kvnc, krdc, rdesktop, rlogin, rsh, tsh, telnet, ssh (OpenSSH), capture, concordance, ftpsync, sftp, ftp, proftpd, gftp, FileZilla, rexec, gexec, pam_mount, php_pear_remote_installer, rsnaphost, rstart, nc, scp, vmware: vmware-view-open-client (omv3, omv2013.0), portmap (NFS-server), smbd and nmbd (Samba), automount (to bring up NFS, the network file system), named (DNS), salt...
Salt is a distributed remote execution system used to execute commands and query data. It was developed in order to bring the best solutions found in the world of remote execution together and make them better, faster and more malleable. Salt accomplishes this via its ability to handle larger loads of information, and not just dozens, but hundreds or even thousands of individual servers, handle them quickly and through a simple and manageable interface.
tcp_wrapper: tcp_wrappers (el6)
With this package you can monitor and filter incoming requests for the SYSTAT, FINGER, FTP, TELNET, RLOGIN, RSH, EXEC, TFTP, TALK, and other network services.
It supports both 4.3BSD-style sockets and System V.4-style TLI. Praise yourself lucky if you don´t know what that means.
Secure environment especially for gopher and www-server: chrootuid (omv)
Desktop-Indixing-systems: nepomuk, strigi, beagle, pinot, kerry, ...
Net/internet with DSL: Applet for ifup and ifdown), immediate configuration, ipv4, with mdv2010 you can still communicate and surf with the dynamic ipv4-address, and ipv6 (ipv6 past ipv4-support), wicd (WLAN- and LAN-network-manager), knemo (simple-traffic-monitor blinking depending on the traffic for the taskline, useful addition replacing a red LED of the tower)), pppoe...
Firewall: Linfw3 (not on the DVD) resp. iptables-1.4.12 with IPSEC, xtables-addons or libxtables from OpenSuSE (both are successors of patch-o-matic for some iptables-modules), arptables, ebtables, ... , ipflood (detector), deynhosts ( protocols and blocks SSH and/or other services in hosts.deny), dropwatch (el6), ...
Desktop-indexing-system: beagle, pinot, ...
Internet easy access with DSL by self-configuration, wicd (wireless and wired network manager for Linux starting at boot time), ...
Packet-type: RPM, packet-manager: drakrpm and rpm, alien, dpkg and apt (Debian Linux packet manager), gurpmi and urpmi (care for no problems anymore with package-dependencies!), smart, yum, kpackage, stow, alien (packages from foreign distributions), packagekit, qtrpm, ...
Debian: alien, dpkg, apt, dpatch (Debian patch tool), debmirror, ...
Data compression / archive-manager (manager for the rpm and tarballs): file-roller, ark, Xarchiver, karchiver, zipios+ (el6), bzip2, unzip, tar, untar, rar, unrar, xz, pxz, star, 7zip, bzip2, squeeze, mscompress, nscompress, cabextract, advancecomp, ...
Update, but also installation (!) by packet-manager rpm: rpm -U packet-name. Wildcards like * are allowed. Installation by rpm (analogous dpkg) according to man rpm (but its better to choose option -U): rpm -i packet-name-including-version.rpm, rpm -i --force packet-name-version.rpm resp. "rpm -i --force --nodeps packet-name-version.rpm", you can use wildcards like * within the packet name, deinstallation: "rpm -e packet_name_WITHOUT_VERSION", option: --nodeps and only in the case of happend installation of several packages the name with version, but still without naming the distribution; queries to the packet-database: -qa, -qf, ..., see: "man rpm". Rebuild the packet-database on errors (almost database db-errors) by
followed by
rpm also enpossibles to check the checksum and signature of a packet, but there is no need of it from rpmfind.net. Notice, that rpm by comparison to urpmi urpmi is installing all dependent packages during the installation of one package, if present.
Installation of tarballs: waf (frontend for the following:), /configure or install, make, eventuallyy make clean, make install, alternatively by xmake, cmake, ... (option "exec" has to be set in /etc/fstab)
Bootmanager (that also can boot MS Windows): grub (takes over belonging configuration /boot/grub/menu.list by command update-grub) and lilo (with password-protection by adding the line with "password=xxx" past prompt in /etc/lilo.conf); bootsplash: draksplash and bootsplashchooser with bootsplash-themes and skripts like switch-themes out of /usr/share/bootsplash (for better control, we recommend the text-modus)
Runlevel-concept with Runlevel-editor
Partition-manager: fdisk, sfdisk, mkfs, drakconf and gparted for parted
Local filesystem: reiserfsprogs-3.6.24 endversion (journalling: self repairing within seconds, fsck), best might be version mdv2011 or el6 and e2fsprogs (1.43.2) with ext4 (2010) resp. ext3, encfs and more (including vfat and ntfs), btrfs-progs, Benchmark: bonnie++, hfsutils (Macintosh-fs), macutils (MAC), bwbar (bandwith benchmark), macchanger (MAC), btrfs (actual kernel 3.X.X), ...
Search for character strings, files and directories: gnome-search-tool from gnome-utils, gtkfind, find, grep, sgrep, fgrep, agrep (char-sequences with typing-errors) ...
Extern webserver (configuration in the section network-interfaces of the system-configuration MCC): SMB (together used windows-harddrives), NFS (network-filesytem), WebDAV (online-harddrives), ...
Filesystem-check and fast, effective repair of many different filesystems: fsck
Defragmentation: shake (defragmenter for live systems), ...
Encryption: FDE (full disk encryption by installer), dracut (creates /boot/initramfs.img for entire harddisc-enryption), LUKS/dmcrypt (ab 2010) des Pakets cryptsetup, by parted the easy-to-handle LoopAES up from mdv2007.0, truecrypt, encfs (special encryption for userspace (home-partition, home) and belonging system-tray-applet cryptkeeper (from mdv2011.0), clauer (cryptographic keyring on a USB-storage-device) , ...
Cryptography
 https://www.nethinks.com/blog/it-ueberwachung/debugging-ssltls-connections/
https://www.nethinks.com/blog/it-ueberwachung/debugging-ssltls-connections/
TLS steht f ür "Transport Layer Security" und ist ein Protokoll, mit dem TCP-Verbindungen abgesichert werden. Es bietet auf einer TCP-Verbindung eine Ende-zu-Ende Verschl üsselung an, sorgt für Datenintegrität (stellt also sicher, dass übertragene Nachrichten nicht verändert werden) und ermöglicht eine gegenseitige Authentifizierung der Kommunikationspartner mit Hilfe von Zertifikaten. Entwickelt wurde es vom Unternehmen "Netscape Communications" unter dem Namen "SSL" (Secure Socket Layer) und wird seit der Version "SSL3" unter dem Namen TLS standardisiert und weiterentwickelt. Die aktuelle Version ist TLSv1.2.
Fehlerbehebung bei SSL/TLS-Verbindungen
In letzter Zeit haben uns mehrere Support-Anfragen zu demselben Problem erreicht: Eine TLS/SSL-gesicherte Verbindung kommt nicht zustande. Dieser Artikel soll mögliche Ursachen und Lösungsmöglichkeiten aufzeigen.
Zum besseren Verständnis: Eine kurze Einführung in TLS/SSL
TLS steht f ür "Transport Layer Security" und ist ein Protokoll, mit dem TCP-Verbindungen abgesichert werden. Es bietet auf einer TCP-Verbindung eine Ende-zu-Ende Verschlüsselung an, sorgt für Datenintegrität (stellt also sicher, dass übertragene Nachrichten nicht verändert werden) und ermöglicht eine gegenseitige Authentifizierung der Kommunikationspartner mit Hilfe von Zertifikaten. Entwickelt wurde es vom Unternehmen "Netscape Communications" unter dem Namen "SSL" (Secure Socket Layer) und wird seit der Version "SSL3" unter dem Namen TLS standardisiert und weiterentwickelt. Die aktuelle Version ist TLSv1.2.
Eine mit TLS abgesicherte Verbindung wird mit Hilfe eines Handshakes aufgebaut. Hierbei durchlaufen Server und Client folgende Aufgaben:
überprüfung des Server-Zertifikats durch den Client
optional: Überpr üfung des Client-Zertifikats durch den Server
Einigung auf die verwendete TLS/SSL-Version
Einigung auf ein gemeinsames Verschlüsselungs- und Signaturverfahren (Cipher-Suite)
Generierung eines gemeinsamen geheimen Schlüssels (Master-Key) für die Session
Der Handshake startet mit der Nachricht Client Hello, die der Client an den Server sendet. Hierbei enthalten ist unter anderem die höchste SSL/TLS-Version, die der Client unterstützt, sowie eine Liste der durch den Client unterstützten Verschlüsselungs- und Signaturverfahren (sogenannte "Cipher-Suites"). Der Server antwortet daraufhin mit der Nachricht Server Hello, die die verwendete Cipher Suite und SSL/TLS-Version, die für die Verbindung verwendet werden soll, enthält. In einer weiteren Nachricht sendet der Server sein SSL/TLS-Zertifikat an den Client, das vom Client überprüft wird. Anschließend findet die Aushandlung eines gemeinsamen geheimen Schlüssels statt, der für die Verbindung verwendet werden soll. Nach Abschluss des Handshakes wird mit einer Nachricht auf die ausgehandelte Cipher Suite gewechselt und die weitere Verbindung findet verschlüsselt statt.
Mögliche Probleme
Kommt eine per TLS/SSL gesicherte Verbindung nicht zustande, kann dies unter anderem folgende Ursachen haben:
Die TCP Verbindung zum Server und dem entsprechenden Port ist nicht möglich
Das Serverzertifikat konnte durch den Client nicht verifiziert werden
Die Einigung auf eine gemeinsame Cipher Suite war nicht erfolgreich
Die Einigung auf eine gemeinsame TLS/SSL-Version war nicht erfolgreich
Gerade der letzte Punkt - die Einigung auf eine gemeinsame TLS/SSL-Version - ist nach Bekanntwerden der Sicherheitsl ücke Poodle und dem Deaktivieren bestimmter SSL-Versionen in unserem Umfeld häufig aufgetreten. Auf dem Server werden dabei ältere SSL-Versionen (in der Regel SSLv2 und SSLv3) deaktiviert. Ein TLSv1.2 Client, der neben der aktuellen Version auch noch SSLv2 unterstützen möchte, muss nach dem RFC5246 die Nachricht Client Hello im Handshake selbst in der Version SSLv2 senden (http://tools.ietf.org/html/rfc5246#appendix-E.2). Der Server muss diese Nachricht entgegennehmen und verarbeiten, auch wenn er selbst SSLv2 für die spätere Verbindung nicht zulassen möchte. In einigen Projekten und Supportanfragen gab es in der letzten Zeit aus diesem Grund einen Handshake Failure - die TLS-Verbindung kam nicht zustande.
Analysemöglichkeiten
Um eine fehlerhafte Verbindung zu analysieren, gibt es verschiedene Möglichkeiten:
Überprüfung des Aufbaus der TCP-Verbindung (telnet)
Überpr üfung des Aufbaus der TLS-Verbindung (openssl s_client)
Weitere überpr üfung mit wireshark
Zuerst kann gepr üft werden, ob überhaupt eine TCP-Verbindung vom Client zum Server aufgebaut wird. Dies kann mit dem Tool telnet geschehen. Folgender Befehl testet den Verbindungsaufbau zu einem Server (in unserem Beispiel 10.9.24.11 auf Port 443):
root@test1:~# telnet 10.9.24.11 443
Trying 10.9.24.11...
Connected to 10.9.24.11.
Escape character is ´^]´.
Erhält man die oben stehende Ausgabe, hat der Verbindungsaufbau funktioniert. Im Falle einer unverschlüsselten Verbindung könnte man nun direkt mit der jeweiligen Anwendung auf dem Server kommunizieren.
Der Aufbau der TLS-Verbindung mit dem Handshake kann mit dem Tool openssl s_client getestet werden. Folgender Befehl stellt eine TLS-gesicherte Verbindung zu einem Server her:
openssl s_client -connect 10.9.24.11:443
Hiermit kann man testen, ob der TLS-Handshake richtig durchgeführt wird. Kommt eine Verbindung zustande, lässt sich das Tool anschließend wie Telnet verwenden und man kann direkt mit der jeweiligen Anwendung auf dem Server kommunizieren.
Kommt hierbei keine Verbindung zustande, gibt die Ausgabe des Tools gegebenfalls Hinweise auf die Ursache. Um zu überprüfen, ob die Einigung auf eine gemeinsame SSL/TLS-Version nicht möglich ist, kann man durch die Angabe eines Parameters eine bestimmte SSL/TLS-Version erzwingen:
openssl s_client -connect 10.9.24.11:443 -ssl2
openssl s_client -connect 10.9.24.11:443 -ssl3
openssl s_client -connect 10.9.24.11:443 -tls1
Kommt mit TLSv1 als erzwungene Version nun eine Verbindung zustande, lässt sich das Problem vermutlich darauf zur ückführen, dass der Server keine SSLv2 Client Hello Messages unters ützt.
Weitere Analysen lassen sich mit dem Mitschneiden von Netzwerktraffic mit den Tools tcpdump / Wireshark durchführen. Mit folgendem Befehl werden die Pakete vollständig mitgeschnitten und in eine Ausgabedatei geschrieben:
tcpdump -s 0 -w output.pcap
Die mitgeschnittenen Pakete lassen sich anschließend mit dem Tool Wireshark genauer ansehen und analysieren.
Lösungsansätze
Je nach ermittelter Ursache sollte zunächst die Serverkonfiguration überprüft werden. Folgende Fragen sollte man dabei durchgehen:
Problem: Das Serverzertifikat konnte durch den Client nicht verifiziert werden.
Ist das Zertifikat noch gültig?
Ist das Zertifikat für den Host ausgestellt?
Ist das Zertifkat von einer vertrauenswürdigen Zertifizierungsstelle ausgestellt?
Problem: Die Einigung auf eine gemeinsame TLS/SSL-Version war nicht erfolgreich.
Sind alte SSL-Versionen (SSLv2 und SSLv3) deaktiviert?
Wird SSLv2 Client Hello unterstützt?
Manchmal hat man keine Möglichkeit, die Konfiguration des Servers zu verändern. Dann gibt es folgende Möglichkeiten:
Problem: Das Serverzertifikat konnte durch den Client nicht verifiziert werden.
Verifizierung des Servers deaktivieren.
Problem: Die Einigung auf eine gemeinsame TLS/SSL-Version war nicht erfolgreich.
Eine bestimmte SSL/TLS-Version im Client zu erzwingen.
Weiterführende Links
Wikipedia: Transport Layer Security
RFC 5246 (TLSv1.2)
Cryptographic encryption following RFC-rules, developed and known by highschools,partially based upon secure hash-functions, but still not end-to-end): insecure XOR, (not total secure) MD5 (Unix/Linux-command: "echo "any-text-to-encrypt" | md5sum"), (almost secure) SHA (Unix/Linux-command shasum, sha256sum, shaXXXsum) , see lsmod to list kernel-modules, the still secure aes-x86_64, aes-i586, aes_generic, sha256_generic, TWOFISH, SHA, SHA2, AES (RIJNDAEL), SERPENT, 3DES, GOST, SAFER+, CAST-256, RC2, XTEA, 3WAY, BLOWFISH, ARCFOUR, WAKE, TLS (Firefox 14, kmail depending on the freemailer, ...), ...
File-encryption, certifcates-administration by pgp-keys: kgpg, kleopatra, gpgp (gnupg2), mcrypt, crypt, ... (this openscource together with KMail is developed by the BSI 2005, details see links, section alternatives), gnutls (TLS), ...
On the fly encryption: scramdisk
Connections: TLS and SSL (openSSL 1.0.2), ipsec/Freeswan (VPN, tunnel, host-to-host and host-to-subnet), MCC section for connections, connman (connection manager), ...
encryption of files and text by hash-functions: UNIX-sh-commands md5sum, shasum and the up to now secure sha256 by sha256sum, sha512sum, ...
Raid: raidtools, dmraid, a320raid, sasraid, adp94xx and adpahci (Adaptec), Quota: quotatool, quota, vzquota, ...
Logical Volumen Management (LVM), separate lvmd
USB 2.0 and 3.0: usb-driver, usbmuxd (communication with Apple ipod Touch and iPhone), usbmon, usbstress, usbutils, usb_modeswitch, dkms-usbvision and usbview (USB-TV-driver/viewer), ...
ATA over Ethernet: aoetools (programs for users of the ATA over Ethernet (AoE) network storage protocol, a simple protocol for using storage over an ethernet LAN), ...
UDF: udftool
Bluetooth: kbluetooth, bluez-firmware, blueman (bluetooth-manager) ....
USB-mice fine-adjustment: lmctl, lomoco, logitech, ...
Network: self-configuration for DSL, ipv4 and ipv6 (including translation ipv6 to ipv4), knemo (can contribute to the certain red LED or replace it, by presenting two small tiny monitors in the taskline, one for client, one for server/router. Depending on the online-traffic they are shining lightblue), pppoe, ...
Sandboxes, Container: docker (docker-io), firejail
System-configuration: MCC (drakconf, drakconf.real) and desktop-configuration-center resp. control-center kcontrol for mdv2007.0 resp. systemsettings, gnome-control-center and help-center
Kernel-Parameter: sysctlconfig-gtk for experts
Child-Protection (like within Linfw3): control-level, user account, time based access control, blacklist (websides by domain and IP), whitelist
Server: nginx (reverse proxy and http-server), lighttp (Webserver, el6), XAMPP (actual version from internet, Webserver (httpd resp. Apache, even local on localhost, webalizer for the logfiles), FTP (proftpd, vsftpd), database (MySQL, even local on localhost, phpMyAdmin, firebird, postgresql, adabas out of OpenOffice.org, also databasis of SAP), bind (DNS Server), noip (DNS), pdns (DNS-server), unbound (local DNS cache), pdnsd (local DNS cache), dnsmasq (DNS Cache, DNS Server), knot (DNS), Router (quagga, il4li, xorp), 383-ds-base (el6, Directory Server), LAN (Samba), printer (CUPS), Fileserver (mars-nwe), DNS (bind, maradns, mydns, security-tools: dnsflood, dnsdoctor, dnsa (audit), ...), DHCP (dhcpclient, dhcpserver, dhcpcd, dhcpxd), Mail (dovecot, roundcubemail (PHP based webmail server), egroupware-emailadmin, popa3d, masqmail (POP3-server), cyrus-imap-sasl, ... ), Mailinglisten (mailman), Fax (hylafax, drakfax), Radius-Server (freeradius), krb5-server, WINS, Proxy (Squid, localhost: privoxy, dansguardian, pdnsd (DNS-proxy)), USENET (noffle, ...), Tunnelingsever (pptpd, a PoPToP Point to Point Tunneling Server, openvpn is a Secure (ssl-) TCP/UDP Tunneling Daemon), openconnect (client for the Cisco AnyConnect VPN protocol), NAS-Server (freeNAS, not included on DVD 1 and DVD 2!), NIS: ypbind and ypserv, nfs-utils (server) and nfs-utils-client...
httpd-Module (el6), moduls for the Apache Webserver: mod_auth_cas, mod_auth_kerb, mod_auth_mellon, mod_auth_mysql, mod_auth_openid, mod_auth_pgsql, mod_auth_shadow, mod_auth_tkt, mod_auth_token, mod_auth_xradius, mod_authnz_external, mod_authnz_pam, mod_authz_ldap, mod_autoindex_mb, mod_bw , mod_cluster, mod_dav_svn, mod_dnssd, mod_evasive, mod_extract_forwarded, mod_fcgid, mod_flvx, mod_form, mod_geoip, mod_h264_streaming, mod_intercept_dav, mod_lcgdm_dav, mod_limitpconn, mod_log_post, mod_lookup_identity, mod_mirrorbrain, mod_nss, mod_perl, mod_proxy_fcgi, mod_proxy_html, mod_proxy_uwsgi, mod_python, mod_qos, mod_revocator, mod_rivet, mod_ruid2, mod_security, mod_security_crs, mod_security_crs-extras, mod_speedycgi, mod_ssl, mod_suphp, mod_wsgi, mod_xsendfile
Smartphone: apps-installer or google-apps-installer, gadget-creator or google-gadgets, wammu, ...
Emulators: virtualbox (MS Windows and other OS), qtemu, qemu (MS Windows, virtual emulators of many operating systems), mingw (the MSWindows-dll) and wine (MS Windows), dosemu-freedos (rosa2014.1, MSDOS, PC-DOS), basiliskII, basilisk (Macintosh), puae and uae (Amiga), hatari (ATARI ST), vice and micro64 (VC64), dosbox, dos2unix (text format converter), yabause (saturn emulator), xroar (dragon 32, 64, Tandy coco emulator), fbzx (Spectrum), caprice (Amstrad CPC), zboy (Nintendo Gameboy), ...
MS Windows Software like MS Office on Linux: https://www.codeweavers.com/store
DNS-Server: dnsmasq, bind, knot, ...
Virtual machines: kvm (Kernel Virtual Machine virtualization environment), (the popular) XEN with xen-hypervisor, lib64xen3 (pclos, mga), VirtualBox (el6), virt (el6, libvirt (el6)), qemu (el6), hyperv / hyperv-daemon (el6), kde-cdemu-manager, cdemu ...
Howto use Windows within Linux through Virtualbox, PC-WELT.de, 08.05.2019
Per virtualization it is possible to use software and apps for Windows for Linux too. We show, howto.
https://www.pcwelt.de/ratgeber/Windows-als-virtuellen-PC-in-Linux-weiternutzen-9790033.html
Virtualbox (el6, all Linux): VirtualBox-5.2-5.2.28_130011_el6-1.x86_64.rpm 12-Apr-2019 20:25 78M, VirtualBox-6.0-6.0.6_130049_el6-1.x86_64.rpm 16-Apr-2019 15:58 118M ( or VirtualBox-5.2-5.2.28_130011_Linux_x86.run ) from https://download.virtualbox.org/virtualbox/5.2.28 resp. https://download.virtualbox.org/virtualbox/6.0.6
and Virtualbox: UserManual.pdf, https://download.virtualbox.org/virtualbox/6.0.6/Oracle_VM_VirtualBox_Extension_Pack-6.0.6-130049.vbox-extpack, https://download.virtualbox.org/virtualbox/6.0.6/VBoxGuestAdditions_6.0.6.iso
Actual version from March 2020: https://download.virtualbox.org/virtualbox/6.0.18/
Terminals: bash (with the update containing all mentioned three patches by bash for CentOS (resp. ALT Linux) 6.5 and 6.6 resp. el6), colorprompt for bash (green and other colors for users, red for root), konsole, xterm, kterm, lxterminal, gnome-terminal, gnash, yakuake, ...
Task-manager: incron (cron with inotify), fcron, cronie (from el6, cron, cron-daemon) together with cronie-anacron and cronie-noanacron, crontabs (el6), ...
Data rubbish deletion: "clean tmp" in section system start of MCC (automatically each reboot), sweeper (KDE), bleachbit (does not clean everyting as told to), klean, ...
IDE (Entwicklungsumgebungen) and GUI: scratch (Games, Animation, Music, ...), wedit, codeblocks (C/C++), kdevelop, anjuta, Qt-Creator und Qt4-Designer (C++ - IDE für Qt), geany (C editor using GTK2), glade, glade2, Glade3, gazpacho (glade clone), wxpython und wxglade (automatisierte GUI-Erstellung für GTK), eric (Python), boa, boa-constructor (IDE für Python), codeblocks (C++-IDE), ncurses, curses, cdialog (UNIX-sh), IDLE (python), anjuta, Kdevelop4, ksi und drscheme (Scheme), sbcl (common lisp), ciao (Prolog), openmotif und lesstif (motif), gtk, Programmiersprachenbindungen für qt3 und qt4, KAppTemplate, edyuk und qdevelop (Qt4), tk (tcl/tk), motor, spe (Python basierte IDE), lazarus (IDE für fpc bzw. Freepascal), monodevelop (IDE Gtk# und mono), coq (proof IDE), scratch (programming sytem and content development tool), chicken (Scheme), spyder (scientific python IDE), ...
Programming Languages and development tools: rust (el7, "Rust is a systems programming language that runs blazingly fast, prevents segfaults, and guarantees thread safety"), sourceinstall, PCCTS Purdue Compiler Construction Tool, gcc-c, gcc-c++, ddd und gdb (Debugger), pcc, gcc-Java, gcc-Fortran, gcc-gnat (ADA), gnat (ADA), cxmon (Disassembler), R-base und R-cran (GNU S - für statistisches Computing und Graphiken) (nicht im Lieferumfang), gcc (C/C++), C# (mono, sharp), clips (Expertensysteme), Erlang (mdv, el6), golang (mdv, el6), clang (mdv, el6), clang-analyzer (el6), Delphi, R (mdv, el6), mp (el6, mathematical programming), Ruby (el6, mdv), g95 (gfortran), Fortran77, Perl, PHP 5, Python, clisp und gcl (Lisp), Lua (el6, mdv), ruby (el6, mdv), TCL/TK (el6, mdv) with tix (el6, mdv), gnat (Ada), Smalltalk, sci-prolog, gprolog, gforth, bigforth (el6, mdv), Falcon (el6, mdv), fpc und fpc-src (Pascal), chicken (el6, mdv), and umbscheme, plt-mzscheme und plt-drscheme (PLT Scheme), guile (el6, mdv), bigloo (scheme compiler), nemerle (el6, mdv), yabasic, Basic, sdlbasic, Algol68, mocka (modula-2), clisp, 64tass and nasm (Assembler), mono, C# (sharp), bash/UNIX-sh, Allegro (Spieleprogrammierung), nasm (Intel-Assembler), vala, li, maxima (symbolic computation program), ocatve (command line interface for solving linear and nonlinear problems numerically, and for performing other numerical experiments), cn (GPU shaping programming language), ..., javascript, see and jythen (Java Source Interpreter), java, jre (Java Runtime Environment), javacc, jikes (Java Quellcode nach Bytecode Compiler), jay ( LALR(1)-Parse-Code-Generator für Java und C#), ocaml (el6), caml5, caml4 (parallel), hugs98, bigloo (el6), jruby (Jave-embedded Ruby), js (die Javascript-Engine), haskell, hugs98, UNIX-sh (bash, Shellprogrammierung, Shellsprache), rpmlint, weblint (HTML-Code-Validierung), wml (Website META language), Kbugbuster, nemiver und ddd (Debugger), make, a-a-p, pmake, imake, qmake, remake and cmake, bakefile (creates makefiles), bison++ (Parser), lemon (Parser), parserd, sparse und dparser (Parser), malaga, agda, gnome-do (quick launch and search), aikido (objektorientierte Sprache mit C++ Semantik), c-0.05 C-Pseudo-Interpreter, clips (Expertensysteme), open64 (sourceforge compiler suite, around 60 MB), biopython, QEdje, regexp, f4lm (Flash für Linux), execline, mawk, listres (Widget-Ressourcen), orc (Oil runtime compiler), sourceinstall, shedskin (Python to C compiler), ragel (Finite state machine compiler), rkward (kde gui to R language), ...
Web development, Content Management Systems (CMS) u.a.: Wordpress (CMS, mdv, el6), Drupal (CMS, mdv, el6), Joomla (CMS, mdv, el6), Typo3 (CMS) , Aptanastudio (pclos, 111 MB, Aptana Studio 3.60 english: create Web- and mobile apps in a comfortable IDE ) and Kompozer (CMS, mdv, el6), moodle (el6, Online Learning Communities, used very often since "coronavirus",https://www.pro-linux.de/news/1/27954/schulen-komplettl%C3%B6sung-linuxmusternet-in-version-7-freigegeben.html ), nvu (Web Authoring System), Bluefish (HTML-Editor), screem (HTML-Editor), clearsilver (HTML-Templates), sitecopy, w3cvalidate, weblint und jtidy (HTML Syntax-Checker und Prettyprinter), jigl (Perl Script zum Generieren statischer HTML-Photogallerien), booh (Webalbum-Generator), gtkasp2php, htmlc (html-file-generator for text-files), blue-griffon (pclos), brackets (pclos), ...
Medicine: gnuhealth, freemed (php-MySQL), gnumed, more transparency in medicine: symptoms - diagnosis - therapie/meds - Neben- und Wechselwirkungen - Prävention : auf Datenbank gestützte "Selbstdiagnose" wie bspws. von Data Becker für MS Windows (emulierbar?; Linux-Entsprechung? beachte: nicht im Lieferumfang enthalten!) or upon any MySQL-DBMS, netdoktor.de, ...
Browser: Microsoft-Edge (pclos), Firefox (OpenSUSE, el6), Pale Moon (pclos, palemoon.org resp., if your CPU does not support AVX, up from version 33.3.0 from https://ftp.palemoon.org/AVX/linux), Konqueror 4.4.5 resp. 4.3.4 (el6, patched) with the built-in adblocker resp. skriptfilter (we recommended), rekonq, hv3 (based upon the tcl/tk-widget tkhtml3, this really does function!), Arora, Midori, Fennec for Mandriva-Mini (Firefox for mobile phone), Mozilla Firefox (you can upgrade by now to Firefox ESR) with firefox-extensions like noscript, ublock-origin, useragent-overrider, flash-plugin and mplayerplugin (all available as rpm except downloadable addon disconnect, Pale Moon (pclos), Cherokee (not included), Chromium, Opera, Seamonkey, qupzilla, Falkon (needs qt5), Galeon, Epiphany, Kazehakase, Amaya, Lynx, Links, Dillo, brave, ....
Browser-Plugins and firefox-addons: flash-plugin 11.2 (adobe shockwave), adobe-reader, mplayerplugin-3.55, IcedTea6 1.8.7, noscript, addblockplus, ublock-origin (extensive adblocker), totem, windows-media-player-plugin (mplayerplugin), vlc-player, realplayer9, lib64kipiplugins1-0.7.0-2mdv2010.0, plymouth-plugin-label, lib64gstreamer-plugins-base, soprano-plugin-redland, alsa-plugins-pulse-config, soprano-plugin-sesame2, qt4-database-plugin-sqlite, plymouth-plugin-script, konq-plugins, libalsa-plugins-pulseaudio, xine-plugins, qca2-plugin-openssl, lib64pt2.6.5-plugins, kipi-plugins, nspluginwrapper, nspluginwrapper, lib64audiocdplugins4, gstreamer0.10-plugins-ugly, soprano-plugin-common, lib64konqsidebarplugin4, java-1.6.0-sun-plugin, alsa-plugins-doc, qt4-database-plugin-mysql, lib64alsa-plugins, gstreamer0.10-plugins-good-0.10.16-3mdv2010.0, kde4-nsplugins, lib64vamp-plugin-sdk1, lib64opal3.6.6-plugins, lib64koplugin6, gstreamer0.10-plugins-base, libalsa-plugins-1.0.21-2mdv2010.0, lib64alsa-plugins-pulse, ...
Filemanager: mc (Midnight Commander), dolphin (together with the complex kde-servicemenu with much more entries for the context-menu from fedora dolpin: action-submenu, virus-scan, ssh-tools, security-tools, secure file deletion, midnight-tools, annotate: nepomuk semantic search and ginkgo (not KDE (el6) resp. pygobject2 (el6)), Repository functionos, fast file encryption, archiving, subversion, preview, TABs, splittable windows, preview, text-, image-, video-preview, directory- and file-includes-preview direct and/or per mouse-hover, ... ), doublecmd (pclos2017), gnome-commander, konqueror, krusader (el6.ru recommended), Cowdancer, nautilus, PCMan/pcmanfm, mc (Midnight Commander), thunar, ...
E-Mail-Clients: kmail (el6, openpgp and SMIME), thunderbird (el6, enigmail: openpgp and SMIME), claws-mail (el6, gnupg: openpgp andSMIME), claws-mail-plugins (el6), mutt (el6), xmail (el6), ...
E-Mail-Encryption (included wrote text): openssl (openpgp and SMIME), gnupg (openpgp and SMIME), enigmail for thunderbird (el6)
Rescue-system: mindi and direct from installation-CD/DVD, mandriva_seed (for Linux like Mandrivaone on USB-stick), draklive or mklivecd (creates a Live-DVD/-CD/-USB-stick of a mandriva-installation) or from USB-stick (liveusb-creator, mandriva-seed, unetbootin, ...), isodumper (iso-images on usb-stick, you can use the package from Mageia mga4 without needing other packages), ...
Ready for (old kind of backups) with streamer, taper, ...
Ebay-auctions: JBidwatcher, ...
Allrounder: klipper (encryptable clipboard), device control and system-info (taskline), work surface switch (of a free configurable amount), Konqueror, Kontact (kmail for Email, rn, slrn, knode and gpan for Usenet, yencode ( encoder, decoder, and posting package for the popular Usenet yEnc encoding format. It features the ability to encode single or multipart archives, a smart decoder which can decode multiple files (including files specified out of order or with nonsense filenames), an optional scan mode with recursion, and an easy to use Usenet posting utility. It is fully compliant with the yEnc specifications), notecase, knotes, keepnote and tomboy (notices), calender, ...), Evolution, Mozilla Thunderbird, blogtk (weblog client) ...
FTP-Clients: kftpgrabber, gftp, proftp, kbear, kasablanca, filezilla, anonftp, wu-ftpd, ...
News-at-once: empathy, ...
USV (unbreakable power supply): nut-server with nut, lib64upsclient and lib64powerman0
Company management (on localhost and LAN) over departments: Mycompanies (from Gooken)
Office: dayplanner, koffice, OpenOffice 3.1.1 (also tested: actual OpenOffice, you can download out of the internet, today 4.0.1), Libreoffice (not on DVD), drakoo (file format wizard for OpenOffice), libreoffice (not included on our DVD), kile and lyx (LaTeX), koffice, goffice, klatexformula, texmaker, Tetex, KPlato, web2project and planner (project management), dia and kivio (flow charts), xmind (110 MB), semantik and freemind (mindmapping and brainstorming software), docear (pclos2017), gtodo and gtg (todo-list and todo-manager) korganizer (calendar and follow up chart), ktouch, gtypist and tuxtype2 (type-writing), wordpress (online publishing), scribus 1.3.5 (desktop publishing) and magicpoint (presentation software), exodus (Bitcoin software, concurrency exchange, pclos), skrooge (finance manager), aqbanking, gnucash and Homebank, units (conversion), parley (vocabulary trainer), ding and dict (dictionary), steak, stardict (multilingual dictionary), rhyme, lokalize, gtranslator, tkbabel and kbabel (language translator, frontend for babelfish), oscommerce (e-commerce, online store), sunclock, knewsticker, xournal (pen-based journal and PDF annotator), Bibus (biographic database manager with intergration in OpenOffice) gnutu (dayplanner for students and pupils), gcstar (collection management), glabels (gLabels is a lightweight program for creating labels, etiquettes, cd-etiquettes, images for candidacies, window-foils, visitor cards, address-sticks, cd-sticks, ring-binders, business cards and so on)visitor cards, etiquettes)
Natural language translators: gnome-translate, kbabel, babelfish, gtranslator, ..
GNOME Translate is a GNOME interface to libtranslate library. It can translate a text or web page between several natural languages, and it can automatically detect the source language as you type.
Archiving: calibre (ebooks), tellico (collection book manager, organizer for videos, books and music), gcfilms (for films), comic-organizer, zotero (pclos2017, collect, organize, cite, and share your research sources, description: Zotero is the only research tool that automatically senses content in your web browser, allowing you to add it to your personal library with a single click. Whether you´re searching for a preprint on arXiv.org, a journal article from JSTOR, a news story from the New York Times, or a book from your university library catalog, Zotero has you covered with support for thousands of sites.), ...
workrave (accomanying, illustrated computer-fitness starting out of the tray against illness and disease like RSI), ...
Telephony: BigBlueButton (BBB) und Jitsi Meet (both: video conferences), kiax on the base of asterisk (PBX, not on DVD), usbmuxd (daemon for the communication with ipod touch and iphone), kphone, gphone, linphone, ekiga softphone, sflphone, antphone, sflphone, glinuxsms, smssend, mail2sms, gammu (command line utility and library to work with mobile phones from many vendors. Support for different models differs, but basic functions should work with majority of them. Program can work with contacts, messages (SMS, EMS and MMS), calendar, todos, filesystem, integrated radio, camera, etc. It also supports daemon mode to send and receive SMSes), kpilot (Palm Pilot), gnokii (Nokia Mobilphone), gnokii-smsd (SMS), ...
Scanner: skanlite, xsane and kooka with tesseract, gocr and clara (pattern recognition out of scanned-in documents), flex (to generated scanner with text-pattern-recognition),
Sensors, especially such ones to find more mainboard-characteristics for the integration of more kernel-modules: ksensors, lm_sensors, lm_sensors-sensord (sensord), motion (software motion detector), sensor-viewer, ...
Library (for media on localhost and LAN): Bibliomaster (from Gooken), artha (English Thesaurus), kdict and gdict (MIT online dictionary), goldendict (dictionary lookup program), ...
Editors and viewer: kwrite, kate, gedit, medit, ghex, vi, vim, manedit, ed (konsole, terminal), joe (syntax highlighted UTF-8 editor), nano, pico, xedit, vi, vim, ed, bvi (for binary files), xmlwriter, leafnode, poedit, yudit, awk and sed (batch file editor), emacs, dailystrips (download of online-comic-strips), comix (comic viewer), qcomicbook (database for comics), Adobereader (acroread), okular (with this, pdf-documents can not be read but pdf-formulars also filled out and overworked), xpdf, qpdfview (el6), kpdftools, epdfview and pdftk (pdf-toolkit:: If PDF is electronic paper, then pdftk is an electronic staple-remover, hole-punch, binder, secret-decoder-ring, and X-Ray-glasses. Pdftk is a simple tool for doing everyday things with PDF documents. Keep one in the top drawer of your desktop and use it to: * Merge PDF Documents * Split PDF Pages into a New Document * Decrypt Input as Necessary (Password Required) * Encrypt Output as Desired * Burst a PDF Document into Single Pages * Report on PDF Metrics, including Metadata and Bookmarks * Uncompress and Re-Compress Page Streams * Repair Corrupted PDF (Where Possible) Pdftk is also an example of how to use a library of Java classes in a stand-alone C++ program. Specifically, it demonstrates how GCJ and CNI allow C++ code to use iText´s (itext-paulo) Java classes., coolreader and fbreader resp. FBReader (ebook reader), calibre (ebook-library: international press, newspapers, websites and journals), modlogan, gnome-system-log from rpm gnome-utils, ksystemlog, chainsaw and logfactor5 (logfile-viewer), sword (bible texts), mlview (xml-tree-editor), TeXMacs (WYSIWYG mathematical text editor), pdfgrep (el6, pclos), pdfedit (el6, pclos), pdfmerge (el6, pclos), pdfshuffler (el6, pclos), pdfcrack (el6, pclos), pdfsam (el6, pclos), kid3 (ID3-tag editor), id3, eric (python and ruby editor), geany (C editor using GTK2), atom (pclos, 66 MB), ...
hdd-anaylizes: kdiskfree, kwikdisk, baobab from gnome-utils, nagios (system-, host- and network-monitor) ...
Filesharing: nfs-utils, kdenetwork-filesharing-kde4, kfilebox (front-end for dropbox), dropbox, nautilus-filesharing, qbittorrent, transmission, frostwire (java based filesharing), limewire and gtk-gnutella (Filesharing)
Cloud Computing: cloud-init (el6) and cloud-utils (el6), nextcloud (el6), owncloud (el6, el7), cf-cli (OpenSuSE 15, this is the official command line client for Cloud Foundry), kfilebox (front-end for dropbox), dropbox, csync (file synchronizer, which provides the feature of roaming home directories for Linux clients. csync makes use of libsmbclient in Samba/Windows environments),...
Short-communication by terminal (internet and LAN): whoami, users, up, mesg, talk, ytalk (short-messages), netatalk (Appletalk and Appleshare/IP services), whois (information about an IP), who, whereis, whatis, finger (active user), which, last, lastb and lastlog (last logins of different user), resign from insecuring ptrace, traceroute, ..., logrotate, logfinder (finding unwanted log files, logfinder informs system
administrators when their servers are collecting personal data and gives them the opportunity to turn logging off if it isn´t gathering information necessary for administering the system), whowatch (el6, display information about users currently logged on), ... ...
Globe, streetmaps: merkaartor (OpenStreet global focusable mapping program with the opportunity to search for street names of the whole world), marble (desktop globe with street-names), google-earth (you can use a google-earth-installer), gpxviewer (https://www.pcwelt.de/a/gps-aufgezeichnete-wege-in-linux-visualisieren,3463983, download out of the internet), viking (el7, like google earth and google maps: global gps-gui with free global determinable location (search) by city, streets and house number; this did function by opening maps with OpenStreetMap (mapnik) and by clicking on city/locations ), mapserver, qlandkartegt, Map&Route (seperate software from Telekom AG), spearfish (GIS data), geoip resp. geoiplookup (to an IP), geoclue ( network, GPS, cell), navit, gpsd, qlandkartegpsd, gpsbabel, gpscorrelate, gpspoint (transferring maps), gpsutil and gpsdrive (GPS navigation, view, edit and transform GPS-maps), ...
Weather, climate maps: zyGrib, kweather, plamoids, wmweather, ...
Phone-books (for mdv2010, but not included): Map&Route (Telekom), das Telefonbuch (Telekom AG), KlickTel (emulated), Telefonbuch (Data Becker, emulated), ...
Password-key-manager: pm, KeyPassX, seahorse and revelation (secure password-manager), kwallet, kwalletmanager, pwgen and makepasswd (password-generators), steghide (hides passwords in image-files), zinnia (online hand recognition system with machine learning).. ...
Anti-spam-filter: clement (E-Mail-firewall resp. -filter), Spamassassin (with Mail::SpamAssassin::Plugin::AntiVirus activated within /etc/mail), qsf (quick spam-filter), Spamoracle, spampd (spam proxy daemon), spampl, Bogofilter, mailscanner, mailfilter, Spamprobe, dspam, pyzor, rblcheck, Junk-Filter (Thunderbird), internal filter-system (kmail, kontact), spampd (spam proxy filter), ...
recommended software by prism-break.org: tinc (virtual private network daemon), mumble (voice communication), hexchat and weechat (IRC), unbound (DNS), kolab (Groupware-Server), kontact, ...
IRC/IRQ/SMS/MMS: konversation, WhatsApp (rpm: whatsapp-desktop (pclos)), alternativ (allgemein empfohlen): signal messanger (rpm: signal-desktop (OpenSuSE 15.1, 15.0, fc30)), ipmiview, pidgin, kopete, gajim, gaim, quassel and xchat, telepathy, kvirc, deluge, supybot (IRC), xcam, kamera, kamoso, xcam, camorama, cambozola and cheese (webcam), ...
Pidgin-news services (protocols): Bonjour, MSN, MXit, Mail.Ru Agent, MySpaceIM, QQ, SILC, Sametime, WLM, Yahoo, ...
Kopete-services: GroupWise, AIM, Bonjour, Gadu-Gadu, ICQ, Jabber, Meanwhile, QQ, SMS, Skype, Testbett, WLN Messanger, WinPopup, Yahoo
Blogger: blogilo, blogtk, choqok, ...
CD-/DVD-burning applications: tkdvd, k3b, brasero and xcdroast (dvd-/cd-burner) with cdlabelgen and tkdvd, bombono-DVD ( for the creation of Video-DVD with title and menus), openshot (to create and mix several audio- and videotracks as much as a title generator, cross fades and effects. OpenShot is a non-linear-video-editor for free, open-source, based on Python, GTK, and MLT. It can edit video and audio files, composite and transition video files, and mix multiple layers of video and audio together and render the output in many different formats), kmediafactory, gtkatalog (catalogue for storage media), k9copy (DVD-Format-converter, not included on DVD1 and DVD2!), isomaster, iso-codes, uif2iso, nrg2iso, pdi2iso, mdf2iso, daa2iso, cdi2iso, ccd2iso, bin2iso, b52iso, iso2uif, iso2nrg (changing of DVD/CD-image-file-types), gtktalog, DivFix++ (repair of broken AVI-file-streams), batik-slideshow and imagination (in order to create DVD slideshows), actoneiso (CD/DVD-image-manipulation), dvdisaster (failure-correcture of data against data-loss from CD/DVD, repair-program), ...
CD-/DVD-Ripper: ripperx, acidrip (DVD-ripper), transcode, rubyripper (high precision cd ripper),...
dvdstyler, dvdauthor, dvdsubs (subtitle), gaupol (subtitle editor), subcomposer (subtitle composer), chaplin (DVD-chaptering), kover, disk-cover, ...
encyclopaedia (Wikipedia): mediawiki (el6), wikipediafs, dokuwiki (helper for the authorization of documents for Wikipedia), Wikipedia-DVD 2006-2014, twiki, ...
Medicine: freemed (PHP-MySQL), freemed, health ( unknown vendor and distribution), gnumed, diagnosis - symptoms - therapy - slide-effects and interaction databasis like "Self-Diagnosis" from Data Becker (MS Windows, emulable?; adequate software for Linux?; notice: This software is not included in our offer, so you can not find them on DVD 1 up to 3!), ...
Astrology and astronomy: universe (OpenSpace Simulator), kstars and stellarium, spacechart, WmGlobe, real-time simulation called celestia, astrolog, ATpy (astronomical tables in Python), ast (world coordinates of the astronomy), astronomy-bookmarks, astronomy-menus (el6), cpl (el6, ESO library for automated astronomical data-reduction tasks), erfa (essential routines for fundamental astronomy), libnova ( Libnova is a general purpose astronomy and astrodynamics library), nightfall (el6, Nightfall is an astronomy application for emulation of eclipsing stars), nightview (el6, a general astronomical software package to control of a CCD camera), pyephem (el6, the astronomy library for Python), saoimage (el6, utility for displaying astronomical images), sextractor (el6, extract catalogs of sources from astronomical images), siril (el6, an astronomical image processing software for Linux), xvarstar (el6, astronomical program used for searching GCVS), ... ...
Mathmatics: mathomatic and axiom (Computer Algebra system. It is useful for research and development of mathematical algorithms. It defines a strongly typed, mathematically correct type hierarchy. It has a programming language and a built-in compiler (not on DVD)), singular and linalg-linbox (computing linear algebra), drgeo (geometry), kcalc and qualculate (pocket calculators), mathplot, kig (interactive geometry), kalgebra, kig (interactive geometry), yacas (computer algebra language), sagemath (complex mathematic-system), rocs (graph-editor and programming language), gnuplot and zhu3d (plotter), gnumexp, pari (number oriented Computer Algebra System), geogebra (dynamische Mathematik), genius, sagemath (Open-Source-Mathematik), singular, jama and kalgebra (Lineare Algebra), mathplot, kig (interaktive Geometrie), yacas (computer algebra programming language), sagemath (umfassendes Mathematik-System, nicht auf DVD 1 and 2 enthalten), rocs (Graphen-Editor and Programmierumgebung), pari (numerisch orientiertes Computer Algebra System), rlplot, gnuplot, zhu3d (3d-Plot), gnumexp, rkward, R out of R-Base and R-cran (Sprache für Datenanalysen and Graphik), R-bioconductor (statistische Analysen genomischer Daten), atlas (Lineare Algebra), axiom (Symbolische Programmierung), bc (numerisch prozessierende Programmierung), dc (zugehöriger Rechner) cdd (Motzkin), cliquer (Cliquen-Finder in gewichteten Graphen), eclip-mwrank (elliptische Kurven über Q via 2-Deszendent),. flint (Zahlentheorie), fplll (LLL-Reduktion auf euklidische Dimensionen), gap-system (programmierbare diskrete Algebra), gbase (Zahlen-Basen-Konvertierung), gfan (Gröbner), ghmm (Markov), hexcalc, iml (ganzzahlige Matrizen), k3dsurf (3D-Oberflächen aus mathematischen Funktionen and Formularen), macauley2 (algebraische Geometrie), wxmaxima and maxima (Computer-Algegra-System, symbolische Programmierung), Octave (numerisch orientierte Programmiersprache) pari (Algebra), polybori (Polynome über booleschen Ringen), polymake, ratpoints (Sieve-Verfahren, um rationale Punkte in hyperelliptischen Kurven zu bestimmen), rattle (R data mining), scilab (numerisch orientierte Programmierung), surf (Visualisierung algebraischer Geometrie), symmetrica (mehr Mathematik für C), sympow (Estimation of special values from symmetric ellipses Graph-L-functions), tesseracttrainer, .xaos (Echtzeit-Fraktal-Zoomer), xaos (fractals, fractal graphic in realtime), qtpfsgui (image workflow), Macaulay (el6), Mayavi (el6), atlas (pclos, Automatically Tuned Linear Algebra Software), ...
rocrail (railroad control system), ...
Chemistry: ghemistry, gchempaint (not on DVD), gchemcal, gchemtable, IQmol (el6), IBSimu (el6), easychem, gperiodic and kalzium (atom periodic system), bkchem (python 2D-chemical-structures), jmol (Java viewer for chemical structures in 3D), chemtool, qbrew, genchemlab, xdrawchem, viewmol, oregano and spice (electronic circuits), mpqc (rosa2014.1, Ab-inito chemistry program), wise (comparisons of DNA and protein sequences), ...
Physics: step (complex physics simulation system), units and gonvert (unit converter), ...
Electrotechnique: qelectrotech (electric diagams), oregano and elektra and gnucap (electronic circuit simulator), gtkwave, circuits and PCB design: gEDA Attribute editor, gerbv (Gerbv Gerber File Viewer), gschem (create and edit electronic schemas and symbols), step ( interactive physics simulation ), Archimedes ( design and simulation of submicron semiconductor devices. It is a 2D Fast Monte Carlo simulator which can take into account all the relevant quantum effects, thank to the implementation of the Bohm effective potential method. The physics and geometry of a general device is introduced by typing a simple script, which makes, in this sense, Archimedes a powerful tool for the simulation of quite general semiconductor devices), Arduino ( electronics prototyping platform based on flexible, easy-to-use hardware and software. It´s intended for artists, designers, hobbyists, and anyone interested in creating interactive objects or environments. This package contains an IDE that can be used to develop and upload code to the micro-controller), ....
Cooking: krecipes, gourmet, ...
Biology: R-bioconductor (not on DVD), qrna (prototype rcDNA-genfinder), emboss (molecular biology), hmmr (Protein-Sequence-Analyzis), primer3 (PCR-reactions), qrna (ncRNA-genfinder), readseq (read and write of nucleoid- and protein-sequences in different formats), sim4 (cDNA and genomical DNA), tree-puzzle (nucleocid-, aminoacid-analyzis and Two-State-Data), ...
Identity kit: ktuberling, ...
Children: childsplay (pclos), omnitux ( pclos, 133 MB, education platform for children which aim is to provide various educational activities around multimedia elements ( images, sounds, texts ) )
Genealogy: ancestris, Genealogy J, GenJ, gramps (Genealogical Research and Analysis Management Programming System), ...
Ebay-auctions: jbidwatcher, bidwatcher, ...
Stocks and finances: electron-cash (Bitcoin), bitcoin (pclos2017, Bitcoin is a free open source peer-to-peer electronic cash system %{that} is completely decentralized, without the need for a central server or trusted parties. Users hold the crypto keys to their own money and transact directly with each other, with the help of a P2P network to check for double-spending. Full transaction history is stored locally at each client. This requires several GB of space, slowly growing), gretl (economics analysis tool), qstalker (stock market charts and -analyzis), kchart (charts and other diagrams), gnucash, kmymoney, grisbi, skrooge, homebank, quasar-client (accounting software), QuantLib (el6), bitcoin ( pclos, peer-to-peer electronic cash system %{that} is completely decentralized, without the need for a central server or trusted parties. Users hold the crypto keys to their own money and transact directly with each other, with the help of a P2P network to check for double-spending. Full transaction history is stored locally at each client. This requires several GB of space, slowly growing ), codelite (pclos), , ...
celtx with celtx-en is a project planner for scriptwriters and regisseurs for complete screenplays resp. scripts, storyboards, termins and information about all actors, for scene books with sketches, photographes and images, calendars for the scene termins and scene locations. Bookmarks allow linking to websites and archives. The scene book can be provided in PDF-format. There are tools to organize, participate and to inform about film projects.
Technical data analysis and graphics: scigraphica (data analysis and technical graphics), ...
OpenFOAM is a free, open source computational fluid dynamcis (CFD) software package released by the OpenFOAM Foundation. It has a large user base across most areas of engineering and science, from both commercial and academic organisations. OpenFOAM has an extensive range of features to solve anything from complex fluid flows involving chemical reactions, turbulence and heat transfer, to solid dynamics and electromagnetics. This package provides the platform specific binaries and modules located in /usr/libexec/openfoam and /usr/lib64/openfoam respectively.
Filetype-conversion: winff (pclos), ffmpeg with frontend feff and transcode (filetype-converter), tidy (charsets), ...
Webside and ftp-side mirror tool (downloads): khttrack resp. webhttrack (httrack) and pavuk (el6, GUI: option -x), nntpgrab (USENET)
more applications: decibel (realtime communications framework, meant to integrate services like CTI (Computer Telephone Integration), VoIP (Voice over IP), text based chat and instant messaging), unetbootin resp. mandriva-seed (script to to put a bootable Linux by ISO onto usb-memory-sticks), primer3, apps installer (smartphone), gco (gnome comics organizer), lecaviste and gwine (wine-cellar), cadaver (command line webDAV-client), macchanger (changes the MAC-address of the ethernet-card), maui (job scheduler for use on clusters and supercomputers), moin (MoinMoin is a WikiEngine to collaborate on easily editable web pages), flowtool, smtpscan (remote smtp server detection), garden planner (table), akregator and liferea (RSS-feeds), ggradebook, flvtool2, flvstreamer (RTMP client intended to stream audio or video content from all types of flash or rtmp servers.), hamster-applet (time-tracker), uptodate, kchildlock (Child protection), Sweet Home 3D is a free interior design application that helps you place your furniture on a house 2D plan, with a 3D preview. Available at http://www.sweethome3d.eu/, this program is aimed at people who want to design their interior quickly,
whether they are moving or they just want to redesign their existing home. Numerous visual guides help you draw the plan of your home and layout furniture. You may draw the walls of your rooms upon the image of an existing plan, and then, drag and drop furniture onto the plan from a catalog organized by categories. Each change in the 2D plan is simultaneously updated in the 3D view, to show you a realistic rendering of your layout), zint (C library for encoding data in several standarized barcode variants. The bundled command-line utility provides a simple interface to the library), ...
Image above: image filter with special effects gmic for Gimp 2.8
photoprint: "PhotoPrint is a utility designed to assist in the process of printing digital photographs. PhotoPrint can do the following:
* Print photographs 1-up, 2-up, 4-up or with any user-selectable number of rows and columns.
* Create posters, split over several pages.* Arrange images into a sort of Carousel, fading from one to another. (Ideal for CD labels)
* Crop images to fit a specific frame.
* Apply a decorative border to an image.
* Make use of ICC colour profiles to provide accurate output.
* Send 16-bit data to the printer, to avoid "contouring" problems in smooth gradients.
* Apply a handful of effecs to an image, including sharpening, removing colour and adjusting colour temperature (ideal for cooling or warming black-and-white prints)."
Image processing: gimp (el7, 2.8), gmic (hugh image-filter-plugin for gimp and program), inkscape, darktable, blender, bforartists (modified blender, 200 MB), k3d (3D modeling, animation, and rendering system, aoi (Art of Illusion, free open source 3D modelling and rendering studio. Many of its capabilities rival those found in commercial programs. Highlights include subdivision surface based modelling tools, skeleton based animation and a graphical language for designing procedural textures and materials), phatch (image-stack-overwork and image-renaming), quat (3D-frakcal-objects), openimage, scrot and ksnaphot (screenshots), qimageblitz, Gimp (2.6), k3dsurf (3D graphical surfaces), gliv (OpenGL image viewer with sharp image-auto-zoom), kuickshow, gpicview (pclos2017), xnview, gwenview, digiKam, albumshaper, shotwell, hotsthots, flphoto and f-spot (for times photoalbum with different center of gravity), wings3d resp. kpovmodeller resp. povray (raytracing), xmorph, potrace (vector graphic converter), kicad, openscad, qcad and gcad3d (CAD), kbarcode, barcode and zint (barcode generators), animata, darktable (negatives and raw), socnetv (social networks analyzer and visualizer), manslide (slideshow), tintii, hugin (can be used to stitch multiple images together. The resulting image can span 360 degrees. Another common use is the creation of very high resolution pictures by combining multiple images), jpegoptim (optimizer, compression), jpegpixie (black-hole-correcture in images), png2ico (png to icon), pngcheck, pngcrush and pngrewrite (PNG-compression resp. Umfang-Optimierung), ktoon (2D animation), kiconedit, synfig and synfigstudio (vector based 2D-animation), mtpaint, ...
Construction (CAD) and Modelling: Art Of Illusion (rpm aoi), blender, leocad (pclos), synfigstudio, qelectrotech, mm3d, gcad3d, freecad, SweetHome3D, kpovmodeller, ardesia (Desktop Sketchpad), pencil, wings3d, k3d, ...
Cliparts: clipart-openclipart (over 300 MB cliparts), ...
Animations: clipart-openclipart (pclos2017), clipgrab (pclos2017), pencil (el6, cartoons, vector- and bitmapgraphic), ktoon, ...
Media player: exmplayer (3D video player), rhythmbox (internet-radio, start by rhythmbox-client), amarok resp. exaile (el6.nux), audacious, kaffeine, banshee, banshee-ipod, podracer (versatile Podcast fetcher), lapod (submit the songs played on an iPod to last.fm), gnupod (command line interface for the iPod), gtkpod, gpodder (podcast-catcher), gnupod (command line tool for iPod), totem, icepodder (Graphical podcast catcher and player), podsleuth (extract meta-data from ipods), podhtml (converts pod to html), python-gpod (pod-access),..., get_iplayer (Streaming-Werkzeug für Podcast, TV and Programme), gnuradio, xmms, xmms2, gst123 (gstreamer audio player), qmmp, gmpc, vlcplayer and MediathekView (from http://zdfmediathk.sourceforge.net/) and miroplayer (including Internet Radio streams and Live- and Internet-TV), kplayer (one of our favorite), kmplayer (best is phonon, plays videos even from damaged files, mp4-codec: xvidcore(el6)), smplayer, gmplayer, mplayer, miro, vlcplayer, kaboodle, Adobe Flashplayer, flashplayer, swfdec (free flashplayer), flvplayer (Flashplayer), flvstreamer (opensource commandline RTMP client), flvtool (manipulation tool for Macromedia Flash Video Files (FLV)), audacious, gxine and xine (tcl/tk- based mediaplayer, Internet-TV), SpiralLoops and synaesthesia (audio visualization), cowbell (music organizer), timemachine (records sounds/audio from times ago), Linvdr and vdr (video disc recorder), dvr (compressed record of video and films from video-capture-cards in realtime into codecs like divx4 and Indeo5), bangarang, lplayer, songbird, last-exit (last.fm web radio player), jorbis-player, foobnix (music player), bino (rosa2014.1, Video Player with 3D and Multi-Display Video Support), enjoy (rosa 2014.1, music player), popcorntime (rosa2014.1, allow any computer user to watch movies easily streaming from torrents, without any particular knowledge), atunes (pclos, 17 MB), bomi (pclos), ...
flv-player: flash-plugin, gnash, PCLinuxOS-FLV-Player (pclos2017), vlc, ...
Screen recorder: recordmydesktop (el6), byzanz (el6), vlc (el6), ...
Screen-Snapshot: ksnapshot (el6, mdv2010.2), scrot (el6), ...
Streaming Software for Linux: Plex
remote: lirc, allremote, ...
vdr: amarok resp. exaile (el6.nux), analogradio, analogtv, archive, autosort, autotimer, bitstreamout, calc, cdda, channelscan, channelswitcher, dxr3, externalplayer, filebrowser, fussball, games, iptv, iaxphone, image, joystick, loadepg, mailbox, mp3, newsticker, osdimage, podcatcher, prefermenu, remote, sky, streamdev, timersync, vdrrip, weather, xineliboutput, zaphistory, ...
Codecs: mplayer-codecs, mplayer-codecs-extra, all codecs, xlv (extended video library), get_iplayer (iPlayer, TV, Radio, Podcase program-streaming Tool), ...
Converter: ffmpeg with frontend feff and transcode, handbrake-cli, handbrake-gui, oggconvert (any audio-files into ogg-format), abcde, dvdrip (ripper and encoder), transcode, sox, glame, lame, soundconverter, soundkonverter, ...
Abb.:Video-Editor pitivi
TV, Video processing: streamripper, mediainfo, f4l (flash-editor), fly (to generate GIF on the fly), ifdvbtune (tuner for DVB-cards), antenna-dtv (free and open-source dvb-t (terrestrial digital tv) tuner for linux desktops. Antenna is a full featured tool to see what´s going on in the sky. It enables you to scan, watch and record television, radio and services broadcasted on air), dvbsnoop, dvbstream, dvb-utils, kdenlive, kino, cinelerra, pitivi, auteur, lives, openshot and avidemux (video-cut and -processing), videoporama ( image slideshow, export to video file), video4fuze ( video format converter by fuze ), alevt, zvbi and zapping (BTX), tvok (TV: watching and recording), kwintv, xawtv, tvtime (TV), irkick (infrared), gshowtv and nxtvepg and tvbrowser (TV-program), xvidcap (an efficient way of capturing your video into a video using console-based commands), openshot (with 3D-effects), fb2png (screenshots from framebuffer), shutter, mando (interactive camera-projector-system), luciole (stop motion software for animation movie realization), cinepaint (colorize movies), griffith (film collection manager), smtube and minitube (play and download videos from youtube), tvok (watching and recording TV), subtitleeditor (el6), stopmotion (rosa2014.1), ...
Audio processing: derrick (stream recorder), csound (Music-synthesis sound-mixer), gnupod, gtkpod, podracer (versatiler, downloads from Podcasts), gpodder (graphical podcast), gnupod (commandline-tool for iPod), lapod (iPod-last-played songs on last.fm), dopi (Song-uploader for ipod), icepodder (graphical podcast catcher and player), podsleuth (extract meta-data from ipods), podhtml (converts pod to html), python-gpod (pod-access), ipod, mscore (compose and notation), kwave, audacity and gramofile (audio processing of LP), Tutka and tse3 (MIDI sequencer), mma (MIDI-accompainment), rosegarden (midi-, audio- and noteeditor), streamripper (audiostream-recorder), bristol (sound machine), jamin (multi-track-studio, soundtrack-mixer, for example for techno music), zynaddsubfx (MIDI-syntheziser), TiMidity++, mixxx (Music DJing Software), timidity++, puddletag (audio-tag-editor), WhySynth (versatile softsynth, which operates as a plugin for the DSSI Soft Synth Interface. Some of its features are 4 oscillators, 2 filters, 3 LFOs, and 5 envelope generators per voice, 10 oscillator modes: minBLEP, wavecycle, asynchronous granular, three FM modes, waveshaper, noise, PADsynth, and phase distortion, 6 filter modes, flexible modulation and mixdown options, plus effects), songwrite (composer with guitar-tabulators), songwrite2, gscore (note editor), lingot (instrument tone tuner), gtkguitune and lingot (two instrument- resp. guitar-tuner), fretsonfire (guitar playing by keyboard), gnuitar, ktabedit (tabulators) and rakarrack (effects for the guitar), gnometab, ecasound and Tuxguitar (guitar-tabulators), guitarix (guitar amplifier) with jackit (jackd, for the line-in-input and output), kguitar, gtkguitune and gnuitar (effects), drumstick, hydrogen (drum-machine, drum computer), terminatorx (audiosynthesizer for DJ works to scratch and for realtime-effect), FreeJ (vision mixer, a digital instrument for realtime video manipulation used in the fields of dance teather), veejaying, medical visualisation and TV), kaudiocreator and streamripper (audio stream recorder), swami (GPL sound font editor),cowbell (music organizer), streamtuner (Internetradio-streambrowser), last-exit ( last.fm Webradio- Player), kradio (a simple radio), qtradio, gnomoradio (searches for provided music for free), radio, hinedo (hinet-radio), sSpiralLoops and synaesthesia (Audio-visualizer), timemachine (records sounds from the past), lilypond, Sound Juicer, ripperx, rubyripper, dagrab and grip (Audio-Dateien von CD/DVD rippen), JuK, beep, clamz (downloader for the Amazon Music Store), csound, mp3info, mp3blaster, mp3stat, mp3val, mp3asm and mp3gain (mp3-player and mp3-failure-correction), DarkIce (IceCast, IceCast2 and ShoutCast live audio-streamer), dap (audio-Processing and editing), songbird (media player mixed up with the web), speaker-test, gnusound, jokosher and jorbis-player, kaudiocreator, extace ( rosa2014.1, Waveform Viewer with ALSA support ), flacon (rosa2014.1, audiofile-splitter), qtractor (el6, an Audio/MIDI multi-track sequencer), soundtouch (el6), calf (pclos, 14 MB, audio plugins for the DSSI, LV2, and LADSPA interface. Calf contains the following audio effects: vintage delay, rotary speaker, reverb, multi chorus, flanger, phaser, filter, compressor. It also contains two full-blown synthesizers: monosynth and organ), ....
... and more: cclive (Tool for downloading media from youtube and similar websites), ...
Amateur broadcasting: ax25-apps, hamradio, hamlib, lib64ax25, talk-ax25, dpaccess, ghu, gnuradio, hamfax, demorse, acfax (Amateur Broadcast Fax Receiver), ...
wireless LAN Access Point controller: chillispot, Coova-Chilli is a fork of the ChilliSpot project - an open source captive portal or wireless LAN access point controller. It supports web based login
(Universal Access Method, or UAM), standard for public HotSpots, and it supports Wireless Protected Access (WPA), the standard for secure roamable networks. Authentication, Authorization and Accounting (AAA) is handled by your favorite radius server. Read more at http://coova.org/ and http://www.chillispot.org/), ...
wammu (mobile phone manager)
Multimedia-center: lmmc (linux multimedia studio, techno sound producer and techno sampler), xbmc (Home Entertainment System and mediaplayer), mms My Media System is an application that manages, displays and plays media content such as videos, music, pictures, scripts, TV, TV-program (EPG), wheather forecast, search resp. find and more. MMS runs perfectly on anything from a Set-Top-Box connected to your TV-Set, to your specially tailored multimedia PC and HD display. As the name implies, MMS is a media system with you in control. It lets other applications such as MPlayer, VDR, or Xine take care of what they respectively do best, and integrates them into one system, that is easy to understand and operate. By combining their individual strength, you get the best of all worlds, in one media application, slimrat (downloads from Rapidshare.com), movida, ....
Lotto: expertlotto (Linux, zip-archive, start by "sh expertlotto", download out of the internet), skoloto, LottoSE_v0.1, melm, lottozahlen-50
Games for Linux (mdv2010) from fr2.rpmfind.net (many of them provided by SDL and/or OpenGL)
The amount of OpenGL- and SDL-games, pygames, games from steam and windows emulatable and other games becomes quit unlimited for introduced "Universal-Linux" and is still increasing. Most of them still can not be found on installation-DVDs. Advantage of Universal-Linux: The operating system and platform must not change to play many of them.
Many, but not all games care for the right screen-resolution by themselves. krandrtray cares for its manual adjustment. The resolution might differ each open-GL-program. This configuration-tool should be loaded into the tray, by creating the desktop-file krandrtray.desktop in /usr/share/autostart.
Games (DVD 1 and DVD 2 depending on their capacities; as we do not have to care too much about insecurties anymore...): playonlinux (prepare for games other OS), opengl-games-utils, game-compat (additional compatiblity), joystick, jscalibrator (joystick calibration), qjoypad, opengl-games-utils, ...
Many Linux-Games can be played alone against the computer as much as against other player all over the net! Configure the pathes in ~/.bashrc and ~/.bash-profile, by adding /usr/games.
###################################################################################################################################################################################
# xorg.conf with automized hardware detection
# Consult /var/log/Xog.0.log on errors!
###################################################################################################################################################################################
#
# Einzelheiten: "man xorg.conf"
# File generated by XFdrake (rev )
# **********************************************************************
# Refer to the xorg.conf man page for details about the format of
# this file.
# ******
# ****************************************************************
Section "ServerLayout"
Identifier "XFree86 Configured"
Screen 0 "Screen0" 0 0
# InputDevice "Keyboard0" "CoreKeyboard" # commented in: hotplug
# InputDevice "Mymouse1" "CorePointer"# commented in: hotplug
Option "AIGLX" "true"
EndSection
Section "ServerFlags"
Option "DontVTSwitch" "true"
Option "DontZap" "true" # disable <Ctrl><Alt><BS> (server abort)
Option "AllowMouseOpenFail" "true" # allows the server to start up even if the mouse does not work
DontZoom # disable <Ctrl><Alt><KP_+>/<KP_-> (resolution switching)
Option "DPMS" "true"
Option "Xinerama" "true"
# Option "DRI2" "true"
Option "UseDefaultFontPath" "true"
# Option "Pixmap" "32"
Option "IgnoreABI" "true"
Option "AutoAddDevices" "true"
Option "AutoEnableDevices" "true"
EndSection
Section "Files"
ModulePath "/usr/lib64/xorg/modules/extensions,/usr/lib64/xorg/modules"
FontPath "/usr/share/fonts/X11/misc:unscaled"
# FontPath "/usr/share/fonts/X11/cyrillic"
FontPath "/usr/share/fonts/X11/100dpi/:unscaled"
FontPath "/usr/share/fonts/X11/75dpi/:unscaled"
FontPath "/usr/share/fonts/X11/Type1"
FontPath "/usr/share/fonts/X11/100dpi"
FontPath "/usr/share/fonts/X11/75dpi"
FontPath "/usr/share/fonts/truetype"
FontPath "built-ins"
EndSection
Section "Module"
Load "dbe" # Double-Buffering Extension
Load "v4l" # Video for Linux
Load "type1"
Load "freetype"
Load "glx" # 3D layer
Load "dri" # direct rendering
# Load "record"
Load "extmod"
# Load "speedo" # Speedo fonts, this module doesn´t exist in Xorg 7.0.17
# The following are deprecated/unstable/unneeded in Xorg 7.0
# Load "ddc" # ddc probing of monitor, this should be never present, as it gets automatically loaded.
# Load "GLcore" # This should be never present, as it gets automatically loaded.
# Load "bitmap" # Should be never present, as it gets automatically loaded. This is a font module, and loading it in xorg.conf makes X try to load it twice.
SubSection "extmod"
Option "omit xfree86-dga"
EndSubSection
EndSection
Section "Extensions"
# compiz needs Composite, but it can cause bad (end even softreset-resistant)
# effects in some graphics cards, especially nv.
Option "Composite" "Enable"
EndSection
Section "Monitor"
Identifier "Monitor0"
ModelName "Generic Monitor"
# HorizSync 47.7
# VertRefresh 59.8
Option "PreferredMode" "1366×768"
# DisplaySize 361 203
# Vesa values! You can comment in all following Modeline for Monitor AOC e943FwS preferred modeline (59.8 Hz vsync, 47.7 kHz hsync, ratio 16/9, 84 dpi)
# ModeLine "1366×768" 85.5 1366 1436 1579 1792 768 771 774 798 +hsync +vsync
# ModeLine "1368x768_120" 185.67 1368 1472 1624 1880 768 769 772 823 -hSync +vsync
# ModeLine "1368x768_100" 151.73 1368 1464 1616 1864 768 769 772 814 -hSync +vsync
# ModeLine "1368x768_85" 125.67 1368 1456 1600 1832 768 769 772 807 -hSync +vsync
# ModeLine "1368x768_75" 110.19 1368 1456 1600 1832 768 769 772 802 -hSync +vsync
# ModeLine "1368x768_60" 85.86 1368 1440 1584 1800 768 769 772 795 -hSync +vsync
ModeLine "1368x768" 85.86 1368 1440 1584 1800 768 769 772 795 -hSync +vsync
# ModeLine "1368x768_50" 69.92 1368 1424 1568 1768 768 769 772 791 -hSync +vsync
# Option "MonitorLayout" "LVDS,AUTO"
EndSection
Section "Device"
Identifier "Card0"
# Driver (chipset) autodetect
VendorName "All"
BoardName "All"
# BusID "PCI:1:0:0"
# VendorName "Intel Corporation"
# BoardName "Intel 810 and later"
# Driver "intel"
Screen 0
# BusID "PCI:0:2:0"
Option "DPMS"
# Option "AccelMethod" "EXA"
# Option "AccelMethod" "sna"
Option "AccelMethod" "glamor"
Option "AddARGBGLXVisuals" "true"
Option "fbdev" "true"
Option "DRI" "true"
### Available Driver options
# sw_cursor is needed for some ati and radeon cards
# Option "sw_cursor"
# Option "hw_cursor"
# Option "NoAccel"
# Option "ShowCache"
# Option "ShadowFB"
# Option "UseFBDev"
# Option "Rotate"
# Option "VideoKey"
# Option "Linear Framebuffer <bool>
# Option "SwapbuffersWait" <bool>
# Option "XvPreferOverlay" <bool>
# Option "Backlight" <str>
# Option "ColorKey" <i>
# Option "HotPlug" "true"
Option "XvMC" &quto;true"
;
# Option "RelaxedFencing" <bool>
# Option "RelaxedFencing" # [<bool>]
# Option "Throttle" # [<bool>]
# Option "ZaphodHeads" # <str>
# Option "DelayedFlush" # [<bool>]
# Option "TearFree" # [<bool>]
# Option "PerCrtcPixmaps" # [<bool>]
# Option "FallbackDebug" # [<bool>]
# Option "DebugFlushBatches" # [<bool>]
# Option "DebugFlushCaches" # [<bool>]
# Option "DebugWait" # [<bool>]
# Option "BufferCache" # [<bool>]
# Option "TripleBuffer" # [<bool>]
# Option "DisableGLXRootClipping" "true"
# Option "EnablePageFlip" "true"
# Option "ColorTiling2D" "true"
Option "TripleBuffer" "true"
# Option "MigrationHeuristic" "greedy"
# Option "ColorTiling" "true"
Option "TearFree" "true"
Option "ZaphodHeads" "VGA1"
# Tweaks for the xorg 7.4 (otherwise broken) "intel" driver
Option "Tiling" "no"
# Option "Legacy3D" "false"
# compiz, beryl 3D-Support with DRI &Composite
# Option "XAANoOffscreenPixmaps"
# Option "AllowGLXWithComposite" "true"
# These two lines are (presumably) needed to prevent fonts from being scrambled
# Option "XaaNoScanlineImageWriteRect" "true"
# Option "XaaNoScanlineCPUToScreenColorExpandFill" "true"
EndSection
Section "Screen"
Identifier "Screen0"
Device "Card0"
Monitor "Monitor0"
DefaultColorDepth 24
Option "AddARGBGLXVisuals" "true"
Option "DisableGLXRootClipping" "true"
SubSection "Display"
Depth 24
Modes "1366×768"
EndSubSection
SubSection "Display"
Depth 32
Modes "1366×768"
EndSubSection
SubSection "Display"
Depth 16
Modes "1366×768"
EndSubSection
SubSection "Display"
Depth 15
Modes "1366×768"
EndSubSection
EndSection
Section "DRI"
Mode 0666
EndSection
Section "InputDevice"
Identifier "Mymouse1"
Driver "mouse"
# Option "Device" "/dev/ttyS0"
Option "Protocol" "ImPS/2"
# Option "Device" "/dev/psaux"
# Option "Device" "/dev/ttyS0"
Option "Device" "/dev/input/mice"
Option "Emulate3Buttons" "true"
Option "CorePointer"
# Option "Protocol" "Auto"
# Option "Protocol" "ExplorerPS/2"
# Option "Protocol" "auto"
Option "ZAxisMapping" "4 5"
# Option "ZAxisMapping" "4 5 6 7"
EndSection
Section "InputDevice"
# generated from default
Identifier "Keyboard0"
Driver "kbd"
Option "XkbModel" "pc105"
Option "XkbLayout" "de"
Option "CoreKeyboard"
Option "XkbRules" "xorg"
Option "AccelerationProfile" "0"
EndSection
 Warning: Some Linux-Games can damage the Bios-part for your graphik-chip, so that the computer restarts or starts with a blackened screen, for example prboom-gl, prboom. Therefore use prboom (pclos) only! Warning: Some Linux-Games can damage the Bios-part for your graphik-chip, so that the computer restarts or starts with a blackened screen, for example prboom-gl, prboom. Therefore use prboom (pclos) only!
In this case the Bios has to get resettted (by the Bios-jumper upon the mainboard) or to get flashed by the firmware-file (.ROM). You might have to try it more times. If this doesn´t help, the Bios-Chip should be exchanged with a new flashed one!
Boswars (bos (mdv2010.1, game)): cd /usr/share/games/bos/graphics/ui && cp -f ui_1280_bpanel.png ui_1366_bpanel.png && chown root:root *.png && chmod 644 *.png
 Graphic card ITX mouseclick-fast, set in BIOS of ITX-220 Northbridge to COMBO-mode or DVMT > 128 MB (we´d like to recommend); notice that graphics of a few games still have to be configured through their menu. For some games at least 4 Gb ( 2 × 2 Gb) DDR-2 666 Mhz is recommended! Graphic card ITX mouseclick-fast, set in BIOS of ITX-220 Northbridge to COMBO-mode or DVMT > 128 MB (we´d like to recommend); notice that graphics of a few games still have to be configured through their menu. For some games at least 4 Gb ( 2 × 2 Gb) DDR-2 666 Mhz is recommended!
Increasing amount of OpenGL-, SDL-, Python-games and other games!
Beneath listed OpenGL,- SDL- und Python-Games of mdv2010 up to mdv2012, el6, el7, rosa2014.1, rosa2016.1 and fc an increasing amount (even of new releases) can be downloaded out of the internet too!
The italian-american way of life?
Sabotage, corruption, arms trading up to serious hard attacks against all kind of competitions
"Pizza Connection 3" for Linux
Der PC-Spiel-Klassiker Pizza Connection bekommt eine Fortsetzung und Linux wird aller Voraussicht nach mit an Bord sein. Das geht aus einer kürzlich durch den Publisher "Assemble Entertainment" bekannt gegebenen Meldung hervor.
Spielszene aus "Pizza Connection 3"
Pizza Connection stellt ein bereits 1994 durch das deutsche Entwicklerstudio "Cybernetic Corporation" entwickeltes und durch "Software 2000" veröffentlichtes Aufbausimulationsspiel dar, in dem der Spieler eine europaweite Pizzeria-Kette aufbaut. Dazu muss der Spieler einen passenden Raum in einer Stadt finden, dort eine Niederlassung eröffnen, Personal schulen und Pizzen ausliefen. Ein grundlegendes Element des Spiels war der Pizza-Editor, der es dem Spieler erlaubte, nicht nur Standardpizzas zu erstellen, sondern auch eigene Kreationen auszuprobieren. Wichtig war dabei nicht nur eine passende Pizza zu erstellen, sondern auch die Geschmäcker der Zielgruppen der verschiedenen Stadtteile zu treffen. Ein weiterer wichtiger Aspekt des Spiels stellte das "graue Geschäft" dar, das von Sabotage, Bestechungen, über Waffenhandel bis hin zu schweren Anschlägen auf die Konkurrenz. [...] In der Wirtschaftssimulation werden neben den Grundzutaten der Serie einige Neuerungen Einzug halten. "Arbeite dich in einer herausfordernden Kampagne vom einfachen Pizzabäcker in den Straßen Roms hoch zum Eigentümer der erfolgreichsten Pizza-Kette der Welt! Erschaffe dazu mithilfe des berühmten Pizza Creator deine individuellen Pizza-Kreationen", so die grobe Beschreibung,
https://www.pro-linux.de/news/1/24784/pizza-connection-3-für-linux-angekündigt.html
mdv2010 (maintained by rosa2014, rosa2016, ...) - Top-Games (all error-free and wrinkless, but updating with rosa2014.1 might extend his feauture): njam (kind of "Pacman"), SDL-games, gnome-sudoku (Sudoku), sudoku, PySOL, Klondike, xpat, kpat and AisleRiot and klondike (Passiencen), kpatience (Asse hoch, Simple Simon, Freecell, Golf, Klondike, Mod3, Spider, Fourty and Eight, Yukon, ...), foobillard (3D billiard), kbilliards (fc22, kdelibs3 (el6), frozen bubble and monkey bubble, rapaigawpoker (RA Pai Gaw Poker), poker2D, xskat (Skat), lskat, jskat, freedoko (Version 0.6.0 oder aktuell), kiriki and tali (Kniffel), dreamchess, eboard (local and online), gnuchess, glchess, chessx, knights, xtengen, brutalchess, samuel (Dame), quarry (Go, Amazons, Reversi), gnome-sudoku, tetravex, muehle 2D (muehle2D_bin122.zip), mahjongg3d (MahJongg 3D Solitaire), ksquares (Käsekästchen), tali and kiriki (Kniffel), grhino and iogno (Reversi/Othello), njam ("pacman"), clusterball (emulated by wine), gl117, flightgear, searchendrescue (helicpoter), mario: mari0, mario secret chronicles and megamario, goonies (pclos2017), ri-li, bubbros, blinken, bse_schlacht (similar to Mensch-Ärger-Dich-Nicht, emulated and from http://www.onlinewahn.de), palapeli, brainparty, gbrainy, arcade-puzzle, frozen-bubble, plee-the-bear, abe (processed only on elder packages resp. elder files), kiki (the nanobot, omv2015), fillets-ng, unknown-horizons, amphetamine, FooBillard, tuxfootball, freetennis, tuxpuck, canonsmash (3D table tennis), volley, blobby (Blobby Volley), trackball, neverball, neverputt, kolf, skijump (did not process on our system), csmash (CannonSmash, 3D table tennis), stepmania, pydance, freeorion (rosa 2014.1, 120 MB-Game), freeminer (rosa2014.1), freeplane (rosa2014.1), armagetron, armagetron-advanced, vdrift, tuxkard, supertuxkard, tuxracer, supertuxracer, extremetuxracer, penguinracer, whereverracer, supertux, Stormbaancoureur, torcs and speed-dreams (Formel1), ktron, supertuxkart, tuxkart, xmoto, motogt, triggerrallye, maniadrive, stuntrally, ultimatestunts, fretsonfire, tecnoballz, blobboats, searchandrescue (helicopter simulation), glx-copter-commander, urbanterror (1-GB-Game), 0ad (0.A.D., around 550 MB, pronounced "zero ey-dee") is a free, open-source, cross-platform real-time strategy (RTS) game of ancient warfare. In short, it is a historically-based war/economy game that allows players to relive or rewrite the history of Western civilizations, focusing on the years between 500 B.C. and 500 A.D. The project is highly ambitious, involving state-of-the-art 3D graphics, detailed artwork, sound, and a flexible and powerful custom-built game engine. The game has been in development by Wildfire Games (WFG), a group of volunteer, hobbyist game developers, since 2001..), warzone2000, lgeneral, scorched3d, adonthell, aisleriot, barrage, bzflag, netpanzer, granatier, btanks, atanks, blobwars (Metal Blob Solid), bjs, wesnoth, dccnitghtmare, mog (maze of galious), naev (300 MB, Space Combat Game), 7kaa (Seven Kingdoms), simutrans, micropolis, openttd, cultivation, stratagus, freecol, freeciv, d2x and d2x-rebirth (Descent2), freeciv, globulation2, simutrans, cultivation, micropolis, openttd, opencity and lincity-ng (city simulation), scourge, slune, luola, wormux, worminator, towertoppler (Nebulous), egoboo, glest, megaglest, einstein (puzzle), sdlwolv and wolf3d-shareware (Wolvenstein), hexen2, hheretic, halfd, millions, edgar, chromiumBSU, superburgerwld, freedroidrpg, freedroid, frogatto, astromenace (hardcore 3D shooter), kobodl (KOBO De Lux), highmoon, Might and Magic IV, clusterball (wine-emulated), criticalmass, cdvst, noiz2sa, glaxium (fc24, fc25, fc26), xsoldier, xgalaxy, xgalaga, eternallands, nethack (nethack falcons eye), flare (role playing, adventure), paintown, openmortal, orbital-eunuchs-sniper, pingus, flaw, luola, tux_afqh, nexuiz (1Gb, rosa2021), urbanterror (1,2 GB, rosa2021), draftsight (288 MB, rosa2021), flight-of-the-amazon-queen (rosa2021), dangerdeep (rosa2021), iridium ( pclos, 95 MB, Iridium is a retro styled 2D shoot ´em up, taking inspiration from: Uridium, Xenon 2 Mega Blast, Nemesis/Gradius and R-Type. ), openspades (pclos), smokingguns, warsow, prboom, vavoom, chocolate-doom (pclos2017), chocolate-hexen (pclos2017), doom/doom-games, world of padman (wop), teeworlds, adanaxisgpl, quakespasm, America´s Army, Hexen2 - Hammer Of Thyrion, chickennix (pclos, shoot´em-up game), teeworlds, engine chocolate-doom, alienarena, openarena, xonotic (successor of nexuiz), assaultcube (similar to counter strike, mkdir ~/assaultcube_v1.0/config, configuration file: ~/assaultcube_v1.0/config/init.cfg: "fullscreen1 scr_w 1366 scr_h 768 colorbits 24 depthbits 0 stencilbits 8 fsaa 0 vsync -1 audio 1 soundchannels 32 lang de"), abuse, vegastrike, darkplaces, marathon-infinity, alephone, tremulous, 0verkill (zero-overkill), dcctnitghmare (dnt), bobobot, 5ball, spacepong, warmux, freeorion, solarwolf, performous, apricots, asylum, Project: starfighter, openttd, drugwar, beret, minetest, nukem3d, highmoon, unvanquished, Mirror Magic, marsshooter (mdv2010.2 runs fine on glibc-rosa2014.1), pinball, freelords, reeciv, freecol, eternallands, nukem3d, holotz-castle, naev, nil, corsixth, liquidwar6, liquidwar, t-crisis, drascula (adventure), dreamweb (el6, adventure, around 300 MB), nethack (mga8), bubbros, heroes, hedgewars, instead, openlierox, pinball, supermethanebrothers, xblast, krank, biniax2, defendguin, sudoku, krank, kiki (the nanobot), plee-the-bear resp. Plee The Bear (orig-tar or rosa2014.1), meandmyshadow, bloboats, retrovaders (Space Invaders Clone), jumpingcube, kubrick, asteroids3d, defendguin, lpairs, dragonmemory, memorypairs, mirrormagic, briquolo, xfrisk, frisk, gtkatlantic, pandemic, kapitalist (Art Monopoly), 3D Train Studio, ri-li, biniax2, bjs (3D tank wars), bse_schlacht (with bse-cows: wine-emulated, like Malefiz resp. Mensch-Ärger-Dich-Nicht), berusky, adonthell, ardentryst, flare, pathological, eternallands, widelands, digger, luola, pydance, stepmania, criticalmass, cdvst, amoebax, highmoon, tux_afqh (3D adventure), xpired, rocksndiamonds, funguloids (buggish code), stratagus, wargus (Warcraft II), knubrick and gnubrick (magic cube), lincity-ng (city simulation), dangerdeep (German submarine simulation), desurium, mures, djl, kbtin, manaplus, secondlife (Life 3D virtual world), halfd, simsu, swell-foop, xletters, dcctnithgtmare, xkarel, vassal (Engine), ksudoku, pythonsudoku, sudokuki, tetrinetx, instead (Adventure), freedink (pclos), roadfighter (rosa2021), flare, tmw, quadrapassel, rolisteam, goatattack (rosa2014.1), crack-attack (pclos2017), steam (Engine), openmw, performous, nfrotz (Engine), pushover (pclos, domino game), oilwar, Ogres (Engine), minetest, monster-masher, mudix, netrek-client-cow, lucidlife, lutris (to install any video game), kmuddy, iagno, gytha, freelords, fheroes (freeheroes), gnotravex, xye (puzzle), gnome-games, gnome-games-extra, gmudix, fglc, fgrun, fizmo, dvorak7min, pangzero (pclos), canta, bluedj, bsd-games, auralquiz (music quiz), dark-oberon (similar to Warcraft II, but with a texture made of plasticine), xsw (XStarshipWars), voxelands (OpenSuSE 15.0, around 200 MB) and funguloids (both actually did not work), anglewars, alienpool, koules, minetest (pclos), viruskiller (pclos), zaz (pclos), playonlinux (around 200 Top-Windows-Games), steam: Counterstrike, Half Life 2, Wasteland 2, uqm (UrQuanMaster, Star Control2 with voice files), Civilization V and The Witcher 2. System requirement: for the steam-client of Linux is a graphic-card with drivers from Nvidia, AMD or Intel.and more Win&Mac&Amiga&... depending on the "grad" of emulation and
more OpenGL-, SDL-games, pygames and other games from all over the internet
Critics for online-plattform
Roblox and the young games-developer, netzpolitik.org, 23.12.2021
Children can develop their own games on the popular platform Roblox and earn money with it. Journalists and juvenile-protectors critizise, that the games giant almost profits hisself with it and doesn´t protect enough his under aged user. The company contradicts.
https://netzpolitik.org/2021/kritik-an-online-plattform-roblox-und-die-jungen-spiele-entwicklerinnen/
The best Linux-games for Steam, Ubuntu etc., PC-WELT.de, 08.31.2020
From Steam, Holarse, Ubuntu and Gog - we introduce the best games for Linux. Many are costless, for free.
https://www.pcwelt.de/ratgeber/Die-besten-Linux-Spiele-steam-Gog-464058.html
PlayOnLinux: Je nach Vorbereitung des MSWindows-Emulators playonlinux von wine (wine32 oder wine64) lassen sich unzählige Windows-Games installieren und emulieren, das Gleiche für Games ursprünglich von Amiga, Commodore, Atari, Cedega usw.. Es gibt neben jeder Menge solcher Games for free auch free und kostenpflichtige Games für Linux wie aufgelistet auf http://holarse.de/ und https://www.gamingonlinux.com/sales/
Around 200 Linux-Games from: http://files.holarse-linuxgaming.de/native/Spiele/
Spiele von PlayOnLinux (playonlinux (pclos2010)):
Wheels of Steel, 3D Train Studio, A.R.E.S (Extinction Agenda), Age Of Empires I und II, Age of Mythology, Age Of Wonders, Alien Breed 2 und 3, Alien Carnage (Halloween Harry), Alien Swarm, Alone In The Dark (The New Nightmare), Anno 1602, Assassin´s Creed, BLAZE - mechforces, BMW M3 Challenge, Baldur´s Gate: Tales of the Sowrd Coast, II, Throne of Bhaal, Battlefield 2, Best One Poker, Bioshock, Black and White 2, Blade Runner, Blood Bol, Blur, Borderlands, Breath of Fire IV, Bulletstorm, Cacodemons Barbecue Party in Hell, Caesar III, Call of Duty 2, Call Of Juarez Gunslinger, Call of Chtulhu: Dark Coners of the Earth, Call of Duty 4: Modern Warfare 1, 2, 3, Cars 2, Champions Online, Chuzzle PC CD-Rom, Cities XL Platinum, CivCity Rome, CivNet, Civilization IV: Complete Edition, Clive Barker´s Jericho, Colin Mcrae Rally 04, 2005, Command and Conquer 1 und 3, Crayon Physics, Crea Vures, Croc Legend of the Gobbos, Dark Age of Camelot,: Labyrith of the Minotaur, Dark Messiah of Might and Magic, Dawn of War: Dark Cursade and Soulstorm, Dead Space 1 and 2, Deadpool The Game, Deep Finesse, Desura, Devil May Cry 4, Diablo II: Lord of Destruction, Diabolo III, Divine Divinity, DmC: Devil May Cry, Dragon Age2: DLC, Awakening, Origins, Driftmoon, Druid Soccer, Dungeion Siege III, EVE online, Emperor, Escape from Monkey Island, Eherlords 2, EveryQuest II Sentinenl´s Fate, F.E.A.R 1 and 2: Project Origin, FEZ (Steam), FIFA 11, Fable: The Lost Chapters, Fallout 3 - DLC, New Vegas, Far Cry 2, Final Fantasy: III and IV, FlatOut II, Football Manager 2010, Forbidden, Full Tilt Poker, GEX 1.0, many games from GOG.com, GTR2, Geheimakte Tunguska - German, GhostRecon, Goblins 3, Gothic 1, Grand Theft Auto 3 and Vice City, Guild Wars, Half-Life 2: Episode One and Two + Lost Coast + Blue Shift, Hanahira!, Hard Reset (Steam) Heroes of Might and Magic 5: Tribes Of the East, V, Heroes of the Storm, Hidden and Danerous Deluxe, Hitman 2 and 3, I Miss the Sunrise, IL2: Sturmovik, Indiana Jones and the Fate of Atlantis, Industry Giant II, Jerusalem: The 3 Roads To The Holy Land, King´s Bounty: The Legend, Kingdoms Of Amalur, LIMBO, LRose Online, La Panthere Rose 1 and 2, Lara Croft and the Guardian Light, Last Chaos, Legacy of Kain, Legions: Overdrive, Lemmings 2, Lume, Mafia, Mafia II, Magicka, Mansion Poker, Marine Malice 2, Mass Effect 1 and 2, Max Payne 1 and 2, Metal Slug Collection, Micosoft Freecell, MS Fury 3, MS Pinball, MS Spider Solitaire, Midnight Club II, Might and Magic IV: The Mandate of Heaven Platinum Edition, Monkey Island 2, Mount and Blade, Myst III and IV, Need for Speed, NeverWinter, NosTale, Nox, OnLive, Orcs Must Die! 1 + 2, RKR Poker, Paddy Power Poker, Path of Exile, Pathologic Classic HD, Pharaon, Pizza Syndicate, Planesape Torment, Planet Pokémon, Pluto Strkes Back, Poker Stars, Poker Stove, Portal 1 and 2, Prehistorik, Prince of Persia, Project 64, Proun, Q.U.B.E, Race Driver: GRID, Rage, Rally Championship 2000, Rayman2, Rayman Origins, Re-Volt, Red Faction II, Rex Cribbage, Richard Burns Rally, Risen 3: Titan Lords, RolleCoaster Tycoon 3, Runaway 1, 2 and 3, Runes Of Magic, Runespell: Overture, Ryzom, S.T.A.L.K.E.R., Sacrifice, Sam and Max 201, Sanctum, Seals with Clubs, Secret of Monkey Island Special Edition, Serious Sam, Settlers 4, Silent Hill 2, SimCity, Ski Challenge, Soldat, Soldier of Fortune Platinum, Sonic Adventure DX, Sonic and SEGA: All Stars Racing, Sonic Fan Remix, Spelunky, Spore, Star Trek Online, Star Wars, Star-Twine, Starcraft II: Wings of Liberty, Starlight Resonance, Steam, Steins;Gate, Strong Bad 101: Homestar Ruiner, 102: Strong Badia the Free, Sronghold, Stunt GP, Supaplex, Super Chuch Norris Bros., Super Meat Boy, Super Street Fighter IV, Supreme Commander, Swat 4, Syberia II, Synthesia, System Shock 2, Talisman, The Darkmod, The Elder Scrolls I - IV, : The Matrix, The Next BIG Thing, The Settlers II, The Sims, The Truth, The Witcher 1 and 2, Th ee Wolf Among Us, Theme Hospital, Theme Park World, Toca Race Driver 2 and 3, Tomb Raider, Toontown Online, Total Annhilation, Trackmania Nations and United Forever, Trainz Railroad Simulator, Tribes, Tropico 3, Tunneler, Two Worlds (GOTY + II), Unreal Tournament 3, Vanage Master Online, Villagers and Heroes, Volvo - The Game, Warcraft II + III, Warrior Kings Battles, Wolfenstein, Wolfenstein 3D, World Of Tanks, World of Warships, World Racing, World in Conflict, Worms Reloaded, Worms World Party, X3: Terran Conflict, Xenon 2, Zeus: Master of Olympus, Zoo Tycoon 2, rFactor1
Games (demo, fc) with data files out of the internet: vavoom-strife, vavoom-hexen, vavoom-heretic, ...
Game Engines (mga, mdv, rosa, pclos, fc) for an infinite amount of games (from internet or other media): quake1, darkplaces, yamagi-quake2, quake2, ioquake3, quake3, chocolate-doom, vavoom, doomsday, cube engine, sauerbraten (cube2), irrlicht, SDL, SDL2, ode, pygames resp. python-games, ...
Welcome to Holarse - the side for linux-games!, holarse.de, gesehen am 01.06.2020
Altitude, Battlefield2, Between The Worlds, Candy Cruncher, Chistmas Eve Crisis, Civilization: Call to Power, Clonk, Cube Combat, Daggerfall Unity, Dark Horizons Lore, Darwinia, American Army, Warhammer II, Born of Dream, Lovely Planet 2, Doom Eternal, Julius, Voxel Tycoon, Stellaris, Railway Empire, The Feritle Crescent, Shortest Trip to Earth, Reciever 2, Vicatory At Pacific, Meeple Station, Path of Titans, OpenLoco, Battle for Wesnoth Beneath a Steel Sky Birth Empires Cataclysm: Dark Days Ahead Clone Hero, Avorion 1.0, MiniGalaxy, Planet Stronghold, OpenBOR, Braveland Pirate, Braveland Wizard, Broken Lines, Imperium Galactica III, Thomas Was Alone, Don´t Starve Together, FreeCNC, Sanctum 2, Full Metal Soccer, Future Boy !, Galcon, Galcon Fusion, Gate 88, Gish, Gorky 17, Grappling Hook, H-Craft Championship, Hacker Evolution: Untold, Heroes of Might and Magic III, Heroes of Newerth, Hexen, Hive Rise, Hopkins FBI, Jumpman, Killing Floor, Kingpin, KreiselBall, Legends, Out of Hell, Oput of the Park Baseball, Penny Arcade Adventures, Puzzle Moppet, Savage2, The Babylon Project, Wing Commander, World of Padman, Prold of Goo, Zero Ballistics, iowolfet,Ambergame, Theocracy, Tribes 2, True Combat Elite, Underworld Hockey Club, ...
https://www.holarse-linuxgaming.de/
http://files.holarse-linuxgaming.de/
Around 200 Linux-Games from http://files.holarse-linuxgaming.de/native/Spiele/
Halcyon: EAs new graphic-engine also for Linux, PRO LINUX, 30.10.2018
https://www.pro-linux.de/news/1/26447/halcyon-eas-neue-grafik-engine-auch-f%C3%BCr-linux.html
Play everything - with moonlight!, PRO LINUX, 29.10.2018
You have a gaming-PC and want to play onto platform Linux? With Moonlight games can be streamed over the network.
https://www.pcwelt.de/a/moonlight-spiele-auf-linux-pcs-streamen,3462729
Steam Play: More Windows-games, that can be gamed for Linux, PC-WELT.de, 22.08.2018
Valve presents a new Beta from Steam Play, that enpossibles to game even more Windows games for Linux.
https://www.pcwelt.de/a/steam-play-mehr-windows-spiele-unter-linux-spielbar,3452076
Free car racingl Yorg with multiplayer-support, PRO LINUX, 22.06.2018
https://www.pro-linux.de/news/1/26017/freies-rennspiel-yorg-mit-multiplayer-unterst%C3%BCtzung.html
Cover of "X-Plane kompakt"
X-Plane kompakt
Manual for the flight simulator X-Plane in german language, https://www.pro-linux.de/artikel/2/1529/x-plane-kompakt.html
In best form too: Sudden Strike 4
https://www.pro-linux.de/artikel/2/1900/sudden-strike-4.html
"Surviving Mars" for Linux, Pro-Linux, 03.16.2018
https://www.pro-linux.de/news/1/25707/surviving-mars-f%C3%BCr-linux-freigegeben.html
"Unforeseen Incidents" for Linux released, PRO LINUX, 05.30.2018
https://www.pro-linux.de/news/1/25939/unforeseen-incidents-f%C3%BCr-linux-freigegeben.html
"Total War Saga;: Thrones of Britannia" for Linux introduced, PRO LINUX, 06.07.2018
https://www.pro-linux.de/news/1/25966/total-war-saga-thrones-of-britannia-f%C3%BCr-linux-vorgestellt.html
Software::Games
"Albion Online" for free, PRO-LINUX, 11.04.2019
Sandbox Interactive has turned the Sandbox-MMO "Albion Online" into the Free-to-Play-modell. By this adventurere can lunge at the world of Albion upon Linux for free. Nothing does change for the previous business-model except the omit of the payment barrier.
https://www.pro-linux.de/news/1/26963/albion-online-ist-kostenlos-spielbar.html
"Imperator: Rome" - Paradoxs new strategy game also for Linux, 05.22.2018
https://www.pro-linux.de/news/1/25912/imperator-rome-paradox39-neues-strategiespiel-auch-f%C3%BCr-linux.html
RPG &quo;Pillars of Eternity II" released, PRO LINUX, 05.11.2018
https://www.pro-linux.de/news/1/25881/rpg-pillars-of-eternity-ii-ver%C3%B6ffentlicht.html
Ego-Shooter Ziggurat for Linux for free
Gog.com provides one more free game..
https://www.pcwelt.de/a/gog-com-verschenkt-pc-spiel-ziggurat,3451142
"Serious Sam 4: Planet Badass" for Linux confirmed, PRO LINUX, 04.25.2018
https://www.pro-linux.de/news/1/25834/serious-sam-4-planet-badass-f%C3%BCr-linux-best%C3%A4tigt.html
"Rise of the Tomb Raider" for Linux released, 04.20.2018
https://www.pro-linux.de/news/1/25819/rise-of-the-tomb-raider-f%C3%BCr-linux-erschienen.html
"Humble Paradox Bundle 2018" with many Linux-games, PRO-LINUX.de, 01.30.2018
https://www.pro-linux.de/news/1/25545/humble-paradox-bundle-2018-mit-zahlreichen-linux-spielen.html
"Neverwinter Nights: Enhanced Edition" for Linux, Pro-Linux, 04.02.2018
https://www.pro-linux.de/news/1/25753/neverwinter-nights-enhanced-edition-f%C3%BCr-linux-freigegeben.html
Humble Bundle with more new packages, PRO LINUX, 30.10.2018
Das Humble-Bundle-Team hat zwei neue "Humble Bundles" geschnürt. Unter dem Titel "Day of the Devs" finden sich zahlreiche Spiele, die auch unter Linux verfügbar sind. Das "RPG Maker"-Bundle vereinigt dagegen die Anwendung und diverse Resourcen. Weiterhin erhältlich ist immer noch das "WB Games Classic Bundle".
https://www.pro-linux.de/news/1/26442/humble-bundle-mit-weiteren-neuen-paketen.html
Past "Tomb Raider", "Rise of the Tomb Raider":: "Shadow of the Tomb Raider" for Linux announced, PRO LINUX, 22.11.2018
https://www.pro-linux.de/news/1/26523/shadow-of-the-tomb-raider-f%C3%BCr-linux-angek%C3%BCndigt.html
Life is Strange 2 for Linux, PRO LINUX, 21.11.2018
[...] Die Brüder Sean und Daniel Diaz sind nach einem tragischen und mysteriösen Vorfall in Seattle gezwungen, ihr Zuhause zu verlassen und Richtung Mexiko zu fliehen. Das Leben auf der Straße ist jedoch hart, und Sean, jetzt voll und ganz für seinen viel jüngeren Bruder verantwortlich, erkennt schon bald, dass seine Entscheidungen auf der Reise gen Süden ihr Leben für immer verändern werden....
https://www.pro-linux.de/news/1/26356/life-is-strange-2-f%C3%BCr-linux-und-mac-os-x-angek%C3%BCndigt.html
Total Warhammer II for Linux, PRO LINUX, 22.11.2018
https://www.pro-linux.de/news/1/26519/total-war-warhammer-ii-f%C3%BCr-linux-und-mac-os-x-ver%C3%B6ffentlicht.html
How to play in mode fullscreen, if not functioning: Open the configuration-files and choose mode windows. Start and choose the actual screen resolution instead of mode "auto".
 Python-Games, "small games for the long pause": https://www.pygame.org/wiki/GettingStarted, http://pygame.org/tags/pygame: solarwolf (el6), spacepong (el6) and much, much more python games in the rubriques: Python-Games, "small games for the long pause": https://www.pygame.org/wiki/GettingStarted, http://pygame.org/tags/pygame: solarwolf (el6), spacepong (el6) and much, much more python games in the rubriques:
pygame arcade (612), 2d (582), pygame (533), game (264), puzzle (239), shooter (190), python (163), strategy (154), libraries (152), other (143), action (131), space (112), spam (101), rpg (96), multiplayer (95), applications (92),
platformer (84), gpl (80), pyopengl (71), pyweek (6)
... in detail (extraction pygame):
pygame_cards is a python package for creating simple card games powered by Pygame framework, Dumb Jump, simple impossible game inspired platformer,
Shift Puzzle, 2d shift puzzle. About 130 lines. Simple example of a 2d game with mouse control using pygame,
Bullet dodger, a fun and challenging mouse game where you must dodge bullets,
pydance,
Wario Land 3, Nintendos Wario Lad 3 for the Gameboy Color recreated in pygame, Graphformer, a platformer (engine; some levels have been included) with bitmap collisions,
Learn Music 1.2, a program to help anyone Learn Music Theory and chords, this is a music educational tool with randomly generated self assessments, learn jazz chords in any scale, intervals etc.
rpeg - FTL Styled Game Engine, rpeg is a game engine and editor designed to create roguelike, FTL-styled games,
Tank Fission, A 1 on 1 top down tank game, with multiple weapons, barricades, trees, playing maps, and computer-controlled turrets,
Piexel, a short game about square wanting to discover, why his memories are lost,
Money Management, this is a simple application for managing how much money you have,
Pixeldodge, dodge the enemies!, Secret Trump,
koxinga, like board game Jamaica,
pyHashi, a clone of the logic puzzle Hashi, aka Bridges or Hashiwokakeru,
Bunny and Badgers, a Python game with a Bunny and some Badgers, Planet GP, by Tormented Pixels, the objective of the game is to race around each planet course as fast as possible,
PB-Ball, Python Basketball Game, gsdl2 - Gumm´s SDL2, Gumm´s SDL2, a purely Pythonic pygame-like that targets pypy and SDL2,
PC-BASIC, a free, cross-platform emulator for the GW-BASIC family of interpreters,
easy scales and chords, an absolutely easy way to find notes in chords. Good for musicians who haven´t studied music crossfiregrid, a little game you can play with one hand and one braincell while having a phone call,
Planet GP, the objective of the game is to race around each planet course as fast as possible, awesome Space Shooter, turn-based space shooter,
Snot II: The Rubberland [Android], Android port of my old hardcore puzzle platformer, written in Python/PyGame/PGS4A. Now with 15 levels and a lot of new cool stuff. Really playable. Really hard. Really free,
Argh-steroids, Asteroids-like arcade game, with a twist, SLC Shmup´ a basic shoot em´ up created in about 2 frantic weeks between school and track practice,
PY ROLLERS CASINO, a collaborative Pygame project YOU can contribute to, Py Rollers Casino is a group Pygame project focused on creating a collection of casino mini-games,
London´s Burning!, a game about defending WW2 London from the blitz!,
Lap Master, drive fast, stay on the track, get the best time,
Juggleball, a minimalist game about trying and failing to juggle with your keyboard,
cube-hunter is an shoot-them-all game in an cube mesh funny to play performed with pyopengl, attack Vector is a rail shooter with voxel graphics and retro sensibilities,
Macario is a pyrotechnician, who is responsible for fireworks in different locations. He is so hopeless, that he keeps losing his matchboxes, but at least he always manages to keep a single match! Help him get his job done while travelling with him around the globe. Light all the fireworks in each level before the match extinguishes.
Mind the mobs! If you fall or run too fast, the match will burn out faster,
PyFormula1, a race game on circuits against the clock, with music, animations, and effects,
SnakeByte, a snake pacman game with levels generated with raw text files generating the walls from the labyrinth, the apples to eat, the snake start position and the phantoms including their moving circuit, Flood It, ge made for the contest "Batalha de Games",
Space Gladiator The Spiritual Warrior, 2D space shooter with original music for each level, power ups, teleport, multi levels,save and load game, AI Sky Eraser, fast-paced caravan shmup written in Pygame -- erase the sky!, bombr, bomberman clone, don´t Touch The Edge!, a simple twitch-finger game,
Conway´s Life, I did a Conway´s Life program with some nice feature,
Slopy Platforming, a scrolling platformer that handles sloped surfaces. A learning exercise, that I will try to build upon to turn into a real game,
Ultimate Tic-Tac-Toe, Tic-Tac-Toe, but with an intense twist! This game packs almost as much strategy as chess, with much more simplicity,
Mouse Game, a challenging game, where you must reach the end of the level without touching anything,
Missile Game, Dodge the incoming missiles in 3 different game modes and see just how long you can last,
Matchmaker, Use your memorization skills to outmatch your opponent! Find matches and avoid the mismatches to win,
Gravity Game, launch your spaceship towards its destination but beware of the red planets´ gravity fields,
Entangled, make the longest chain in this challenging puzzle game, 8-Bit Dimension, yet another Arkanoid,
Namotavka, addictive 2D logic & puzzle game,
MaTris, yet another tetris clone. Has a tetromino shadow, which makes it simpler to play quickly. Has some sounds too (created with sfxr),
Lunar Panda, space action game featuring one brave Panda and a jetpack!,
MiniWorld, an RPG Game similar to Legend of Zelda done in python and pygame,
jBot, 2d platformer game about a robot, run and jump to collect coins and shoot your way through mobs and blue barrier doors. Avoid getting hit by spikes, lasers, or mobs and find your way to the white exit,
Games Pit, a minigames collection for children and a framework to start programming simple games,
Double Cross, unlike your common unilateral falling block games, "Double Cross" implements a bidirectional paradigm expanding the genre in both dimension and difficulty,
Arachnoid, an Arkanoid/Breakout clone with moving spiders instead of bricks,
Soldat Air Force, side view, fly a plane, rocket launching, firing machine guns, trying to knock down enemy aircraft. There are also allied aircraft (Friendly Fire off),
Python Defender 2, this game is a follow up to my original version of pythonDefender. It is another shoot em up, only I have added a lot more functionality,
Basic Blind Chess, Blind Chess also known as "Dark Chess" or "Banqi"
M or Half Chess , is a two-player Chinese board game played on a 4× 8 grid, or half of the xiangqi (Chinese Chess) board. This application is using Taiwan rule,
pygame-cards,
ReTux, a commercial platformer using the graphics of SuperTux,
pySioGame, a set of simple, educational, grid-based activities for 3 - 10 years old kids build with Python & Pygame,
Orbit Duel 0.1, by ChrAle (abbreviated in "Orbit 2l" because the number 2 in Italian is pronounced "due") is a game that simulates the orbitation of two satellites around a planet. The two players can modify trajectories trying to don´t fall on the planet surface, or getting lost in space, Atari 2600 Combat 1.0,
Shift Puzzle, 2d shift puzzle. About 130 lines. Simple example of a 2d game with mouse control using pygame,
Tank Fission A 1 on 1 top down tank game, with multiple weapons, barricades, trees, playing maps, and computer-controlled turret,
PB-Ball, Python Basketball Game,
gsdl2 - Gumm´s SDL2, a purely Pythonic pygame-like that targets pypy and SDL2,
Ages of the island, this is "Ages of the island", a real time strategy game based on the classical board game "Die Siedler von Catan" for many players connected online,
Solitaire 1.0, Solitaire clone written with Pygame (very simple),
Ultimate Tic-Tac-Toe, Tic-Tac-Toe, but with an intense twist! This game packs almost as much strategy as chess, with much more simplicity,
Simple Chess, just a simple chess game. No AI so it must be played two player. Comes with source code,
BASIC-RoBots, BASIC-RoBots is a real-time strategy game about programming robots to colonize a planet,
Extinguished, a real-time strategy game, where you control firemen to rescue people from burning buildings. Battle against time and a raging fire to carry unconscious people from a burning building. Use your firemen to rescue or to hold back the fire at strategic points. Beware of dangerous chemicals which will explode and spread the fire, blocking your exit,
Space Domination, Space Domination will be a cross-platform top-down scrolling spaceship shooter/adventure game,
HedgeZOO, plant apple trees, build huts for hedgehogs, remove unfresh apples and sell the largest hedgehogs,
Void Infinity, a real-time strategy game with online multiplayer,
battle-rage is a fighting game in 2D, where the battle rages on and the fighters encounter each other in terrible duels fights ! dependencies: sdl2, sdl2_image, sdl2_mixer, sdl2_ttf.
...
Linux Games Top 100, http://hot-100.ru/page/2, http://hot-100.ru/page/3 and so on: 0 A.D., FreeOrion, OilRush, The Open Racing Car Simulator, Warsow, Savage 2, Second Life, Spring, TGatB, OpenXcom, Castle Vox, vulture, spiral knights, dredmor, gish, dwarf fortress, greedy car thieves, freespace2, starry, projectx, share the pain, sauerbraten (FPS), BOH, Aquaria, AC-130, Planescape: Torment, Quake4 1.4.2 + Q4Max 0.78d, Sacred, LambdaRogue, Dominions 3: The Awakening, The Dark Mod, Transcendence, Zero Ballistics, Conquest: Divide and Conquer, Cortex Command, Wolvenstein3D, TetriCrisis 3 100% C.P.U., Epiar, Endgame: Singularity, PipeWalker, Coldest, Hexen: Edge of Chaos, Catan Online World, GNU Robbo, Butterfly Effect, AC-130, Planescape: Torment, Dying Light Released, ALoneStory++, Fandango Mastered Release, Crimsonland, Dungeon Crawl Stone Soup 0.11, Wizorb, Wing Commander Saga: Prologue - port on Open Freespace2, 0 A.D. Bellerophon, Helena the 3rd, Heroes of Newerth, Catan Online World, UFO: Alien Invasion, Age of Conquest III, Excalibur: Morgana´s Revenge v3.0, Battle Tanks, Warzone2100, Amnesia: The Dark Descent released, ...
Game: Transport Fever - Traffic Simulation for Linux, 09.11.2016
With Transport Fever you become a tycoon for railroads. Up from year 1850 your are building up your railroad-empire.
http://www.pcwelt.de/ratgeber/Action-Adventure-Logik-Die-besten-Linux-Spiele-464058.html
Software: Games
Steam: More than 2000 games for Linux announced, pro-linux.de, 01.03.2016
Since the release of Steam for Linux two years ago the amount of titles for Linux has permanently increased. Meanwhile the platfrom lists over 2000 titles either released for the free operating system or that will be released in future. The amount of actual released titles is more than 1900.
Weak by weak more and more Linux games are offered. Game platform steams statues one example. Once there have been 60 games released, now there are 1900. Still there is an amount of unreleased Games for Linux, so that more than 2000 titles are counted, http://www.pro-linux.de/news/1/23303/steam-ueber-2000-spiele-fuer-linux-angekuendigt.html
The best nonfree Linux-Games from desura http://www.desura.com/ , indiegamestand https://indiegamestand.com/, Gog.com https://www.gog.com/news/gogcom_now_supports_linux: Sky Rogue, Escape Goat, Guns of Icarus Online, Megabyte Punch, Epistory, Blueprint Tycoon, Finding Teddy 2, Evo Explores, Rochard, Bastion, Cave Story+, World of Goo, ARK Survival Evolved, Factorio, Enter the Gungeon, Tabletop Simulatior, Couter-Strike: Global Offensive, Firewatch, XCOM 2, American Truck Simulator, Creatures Internet Edition, Hyperspace Delivery Boy, EVE Online, Tribes 2, Warcraft II, Battlefield 2142, Transport Tycoon, Tribal Trouble 2, The Dark Mod, ...
http://www.pcwelt.de/ratgeber/Action-Adventure-Logik-Die-besten-Linux-Spiele-464058.html
24.167 (actual date: 31.01.2015) popular and absolut TOP-games for Windows and Linux on the base of special game-engines like almost Unity, followed by Steam and so on, usage at your own risk: http://www.indiedb.com/games/top, for example:
Planet Nomads, Craneballs, Shinobi Life Online, Gang Beasts, CHKN, Creator Powers, TerraTech, StarWars Battlecry, Garbage Day, Velocibox, Besiege, Planet Pokemon, Vanish, Robocraft, Hunie Pop (HuniePop is a unique sim experience for PC, Mac and Linux. It´s a gameplay first approach that´s part dating sim, part puzzle game, with light RPG elements, a visual novel style of presentation, an abrasive western writing style and plenty of "plot".
After a pathetic attempt to try and pick up Kyu, a magic love fairy in disguise, she decides to take you under her wing and help you out with your crippling inability to meet new women. After a few dating lessons and some sound advice, Kyu sends you out into the world ready to take on the dating world and a wide cast of beautiful babes.), Overgrowth ( Hey everyone! I"m Steve, the new character concept artist for Overgrowth. In this post I will share some of the designs I"ve been working on. All images in this post can be clicked to bring up a wider view and higher resolution version of the image. It´s been a bit of a challenge to get used to drawing anthropomorphic animal characters as I have very little experience with animal anatomy. Here is my first attempt at designing the Overgrowth races, completed during the application process to supplement my portfolio), crawl, slime-rancher (Slime Rancher is the tale of Beatrix LeBeau, a plucky, young rancher, who sets out for a life a thousand light years away from Earth on the Far, Far Range where she tries her hand at making a living wrangling slimes. With a can-do attitude, plenty of grit, and her trusty vacpack, Beatrix attempts to stake a claim, amass a fortune and avoid the continual peril, that looms from the rolling, jiggling avalanche of slimes around every co), ...
"Dead Island: Definitive Edition" for Linux released, pro-linux.de, 06.07.2016
http://www.pro-linux.de/news/1/23624/dead-island-definitive-edition-für-linux-freigegeben.html .
Steam: More than 2500 Linux-games, pro-linux.de, 09.30.2016
http://www.pro-linux.de/news/1/24018/steam-mehr-als-2500-linux-spiele.html
Strategy game "Hearts of Iron IV" for Linux released, pro-linux.de, 06.07.2016
http://www.pro-linux.de/news/1/23627/strategiespiel-hearts-of-iron-iv-veröffentlicht.html.
Total War Collection for Linux released
Medieval II: Total War Collection is released for Linux and Mac OS X this week, PCWelt.de, 01.13.2016
GRID car sport for Linux and Mac OS X available
Feral Interactive (XCOM: enemy unknown, middle earth: mordor´s shadow, alien: isolation) has released 2015 GRID Autosport for Linux, http://www.pcwelt.de/prolinux/GRID-Autosport-fuer-Linux-und-Mac-OS-X-verfuegbar-9895039.html
At this place, for top gamer, we of course also advise to game-consoles like XBox and Playstation. As our onboard IGP graphic- and sound chip, both from INTEL, seem to master introduced games much to well, we proceed with games direct referring to mdv2010:
mdv2010 (maintained by rosa 2014 - rosa2016 - pclos - fc - ...) - Games - arcade/Action: 2048 (2048-cli, for terminal), moon-buggy (arkade game for the konsole resp terminal: drive and jump a kind of car across the moon), circuslinux (cirucs acrbotics), childsplay, kapman and njam (kind of pacman), frogatto (frogger environment game), superburgerwld (Super Burger World is a jump and run game based on SuperTux, except with one big difference, You play as a burger trying to rid the world of an evil fruit company), supertux (50 MB), openlierox (aroand 50MB), Urbanterror (1GB-game), drascula (the vampire strikes back), vegastrike (500 MB, depending on the graphic-card), eternallands (MPPRG game), 0ad-r10803 (Cross-Platform RTS Game of Ancient Warfare), noiz2sa (arkade space shooter), ux_afqh (Tux on his way by feed), holotz-castle, hexen2, hexenworld and hhexen, fheroes2 (Might and Magic II), Freedroidrpg (130 MB), armagetron (like tron), ktron, gltron, slune (3D-Tux-car race for the good purpose), xtux (multiplayer arcade game featuring open-source mascots), liquidwar, liquidwar6, freefem3d (FreeFEM3D is a 3D version of freeFEM), blobwars(episode 1: Metal Blob Solid), xsw (XShipWars), glaxium (3D space shooter), unknown-horizons (ca. 200MB; A popular economy and city building 2D RTS game), starfighter and starvoyager and luola (space shooter), Chromium (rocket-shooter), Vegastrike (ca. 200 MB-Game; not on our DVD!), heroes, sdl-ball, kbreakout, lbreakout (pclos), lbreakouthd (pclos), highmoon, briquolo (3D) and lbreakout2, secondlife, aisleriot, bubbrothers, critical mass, Rocksndiamonds, defendguin, solarwolf, Powermanga (3D shootup), madbomber, bugsquish, burgerspace, worminator, wargus (Warcraft II, around 200 MB), XBill(G.), koules, killbots, jumpnbump, teeworlds (online multi-player platform 2D shooter), cdvst (arcade space shooter), bsd-games wie adventure, arithmetic, atc, battlestar, bcd, caesar, canfield, cfscores, cribbage, go-fish, gomoku, hunt, mille, mpoly, morse, number, phantasia, pig, pom, ppt, primes, quiz, rain, random, robots, rot13, sail, snake, snscore, teachgammon, bsd-fbg, trek, etoys, worm, worms and wump, copter-commander (2D helicopter game), qtads (GUI multimedia interpreter for TADS games), halfd (a Linux Half-Life server management tool, consisting of a daemon process and GUI clients. It is designed to work with all mods (TFC etc.)), koules, scourge (100MB game), planeshift, quake2, superburgerwld (around 50MB), teeworlds, OilWar, , xtux, xblast, airstrike (space shooter), alienblaster, amphetamine, anglewars, alienpool, ars-libertatis (roleplay-adventure game), asteroids3D, barrage, atanks, bobobot, briquolo, ioquake3, d2x and d2x-rebirth, eduke32, yadex, childsplay, kiki (nanobot), abe (scrolling, platform-jumping, key-collecting, ancient pyramid exploring game, vaguely in the style of similar games for the Commodore+4), barrage (rather violent action game with the objective to kill and destroy as many targets as possible within three minutes), corsixth (Open source clone of Theme Hospital), mazeofgalious (flick screen platform game), irrlamb, dcctnitghtmare (60 MB, 3D single player RPG in a satirical post apocaplyptical world), minetest (200MB, Minecraft inspired game), astromenace (100 MB hardcore 3D space shooter), skobo (sdl-port of xkobo), naev (744 MB space trading and combat), tmw -(2D mmorpg game the mana world), secondlife, xqf (network game browser), dunelegacy, gargoyle-free (graphic player for interactive fiction games), openclonk (rosa2014.1, free multiplayer action game about mining, settling and fast-paced melees), ...
mdv2010 (maintained by rosa2014 - rosa 2016 -. ...) - Games - Jump´nRun: mari0 (pclos), marioland and megamario (Jump´nRun) and smc (Secret Maryo Chronicles, 81 MB), balazar (3D-adventure and roles), fillets-ng (200 MB, fishfillet-ng skill game), balazarbrothers (3D Puzzle), digger, eduke (Duke Nukem 3D), bumprace, Trackballs, Toppler (Kletterspiel nebulous), sdlscav, supertux (Jump and Run), trackball, freedroid, plee-the-bear (Plee The Bear 2D platform game), Mirror Magic, enigma, bubbros (Bub and Brothers game), ...
mdv2010 - rosa2014 - rosa2016 - Games - Adventure: slune, drascula, dreamweb (el6), ardonthell, ...
.
mdv2010-games (quit all games can be updated by rosa2016.1 and rosa2014.1), all free from advertisement: 3D-SDL- und openGL-Alien-Person-Shooter (FPS): Counter-Strike (source), nexuiz-sdl and nexuiz-glx (ca. 1,2 GB), xonotic (1,3 GB FPS, successor of nexuiz), assaultcube (around 40 MB only, similar to counter strike; mkdir ~/assaultcube_v1.0/config, configuration file: ~/assaultcube_v1.0/config/init.cfg), urbanterror (ca. 1 GB), alienarena (1,2 GB), Openarena (Quake III, ca. 500 MB), Tremulous (ca. 200 MB), Alephone (benötigt marathon), marathon, marathon-infinity, marathon2, reaction, darkplaces (benötigt Quake I), marsshooter (1GB, ridiculous shooter), World of Padman (WOP), FPS and Top-Game-Game and Engine sauerbraten (427 MB), doom, prboom, prboomplus, vavoom (open source port of the DOOM game engine), warsow (ca. 1 GB), orbital_eunuch_sniper, yamagi-quake2, Quake II, Quake I, unvanquished, freedoom (dome game), smokingguns, openspades, Red Eclipse, Teeworlds, d2x (Descent2), Red Eclipse, Unreal Tournament, Half-Life2, Half-Life, Wolvenstein (Enemy Territory), The Binding of Isaac: Rebirth, True Combat: Elite, stargunner, Team Fortress, cube2 (sauerbraten), descent3, barbarium (not mdv), abuse, shambles (not mdv), discovery (not mdv), mighty (not mdv), startrade (not mdv), savage2 (not mdv), Infinium Strike (not mdv), quakespasm (not mdv), America´s Army (not mdv), Hexen2 - Hammer Of Thyrion, QuakeForge, ZDoom (not mdv), DelphiDoom (not mdv), ChaosEsqueAnthology (not mdv), Wolfenstein 3D html5 (not mdv), Ogrian Carpet (not mdv), quake2xp (not mdv), SpaceMax Shoot them up (not mdv), nethack (mga8), ...
.. and, if someone is still missing it: The shooter Insurgency was released 2015 by the developers also for Linux. Owner of a Windows- or Mac OS X-version can dowload this game for free for the free operating system., PCWelt, 30.10.2015, http://www.pcwelt.de/prolinux/Taktik-Shooter-Insurgency-fuer-Linux-freigegeben-Daddeln-9839541.html
Steam: More thans 2500 Linux-games, pro-linux.de, 09.30.2016
http://www.pro-linux.de/news/1/24018/steam-mehr-als-2500-linux-spiele.html
"Humble Daedalic Bundle 2018" with plenty of Linux-tiles, PRO LINUX, 06.11.2018
https://humblebundle.com
https://www.pro-linux.de/news/1/25969/humble-daedalic-bundle-2018-mit-zahlreichen-linux-titeln.html
"Humble tinyBuild" with plenty of Linux-games, pro-linux.de, 05.13.2017
https://www.pro-linux.de/news/1/24736/humble-tinybuild-mit-zahlreichen-linux-spielen.html
Surviving Mars für Linux, pro-linux.de, 05.15.2017
https://www.pro-linux.de/news/1/24744/surviving-mars-auch-unter-linux.html
Rocket League for Linux and Mac: Real soon now offline only, PC-WELT.de, 24.01.2020
Ab März kann der Autoball-Multiplayer-Titel Rocket League auf Linux und Mac nur noch offline gespielt werden.
https://www.pcwelt.de/news/Rocket-League-Linux-und-MacOS-Versionen-gehen-offline-10742803.html
mdv2010-Games - board: kigo and gnugo (japanese Go), eboard, knights, phalanx, xboard, cboard, crafty, glchess, nuclearchess, brutalchess, dreamchess, gnuchess (chess), sirius (Otello chess game), csboard, glchess (3D-Schach), tengen and gamazons (Mix aus Schach and Go), muehle2D_bin122 (zip-Archive from Sourceforge), gnubg and backgammon, samuel (Dame, draughts game), opengoo (Goo), monopd and kapitalist (client), capitalist (Monopoly), lagno and kreversi, kmahjongg, kbattleship, scrabble (word game), gtkatlantic and monopd (Monopoly), prisk, ksirk, xfrisk and frisk (Risiko), xmris, quarry (Othello, Amazons, ... ), pioneers (internet playable implementation of the Settlers of Catan board game), 4stAttack (connect four), biloba, kcheckers, tuxmathscrabble (scabble with nums), xye (Puzzle), ...
mdv2010-Games - cards: lparis (memory game), xskat, freedoko (Doppelkopf, 5.0.2, 6.0 or actual version), (K)poker, poker-network, RA Pai Gaw Poker, poker-network, gtali and pokerth (Texas Poker), Blackjack, xpat2, elitaer and sol (Solitär), PySol, Freecell and Klondike, Kpatience and kpat (passience), KardsGT (collection of card games like MauMau, Asse hoch, Einfach Simon, Freecell, Golf, Großvater, Größvaters Uhr, Mod3, Spider, Vierzig and Acht, Yukon, Zigeuner, ), PokerTH, rapaigawpoker, aisleriot (70×solitar games)
mdv2010-Games - sport: motogt, xmoto(cross), obstacle (course for automobiles), stoormbaancoureur (car-skill), FooBillard (3D billiard), blobby (volley arcade game), triplane-classic (side-scrolling dogfighting game), paintown and openmortal (Mortal Szombat, around 50MB), bloboats (boat racing), tuxkart, vdrift (500 MB Open Source car driving simulation), tuxracer, supertuxracer, Torcs and speed-dreams (Open Racing Car Simulators), extremetuxracer, wherever-racer, penguin-racer, trophy (2D-Autorennen), speeddreams (ca. 1 GB), Maniadrive, enemylines, Freetennis (3D-tennis), Canon Smash (3D-table-tennis), spacepong (pong like game), volley (3D beach-volleyball) and gav (volleyball), hattrick-organizer and Tuxfootball and bygfoot (football), Pinball (flipper), neverball and neverputt (golf), kolf (miniature golf), Tuxpuk, skijump, neverball and neverputt (Golf), stepmania with stepmania-stepmix1 (250 MB) and pydance (dance), supertuxkart (ca. 100MB), triggerrallye (around 300 MB), ultimatestunts (300 MB), stuntrally (700 MB, racing game with track editor based on vdrift and OGRE), roadfighter, stuntrally (around 100 MB), ...
mdv2010-Games - other: bluedj-online-games (mix of card games, go, chess, ...), maitretrarot (game server),
mdv2010-Games - strategy: uqm (Ur-Quan-Masters), stratagus (settler 2), simutrans (transport and logistic-empire), scorched3d (war game Scorched Earth 3D OpenGL Remake, 54 MB), d2x (popular 3D-game Descent), reeciv, globulation2, worminator (terminator), warzone2000 and freecol (innovative 3D realtime-strategy), glest (towers and castle game, 3D-openGL-strategy), wesnoth (Battle of Wesnoth), abe (pyramid adventure), openttd ( city simluator ), micropolis (city game), Opencity (city simulator), 7kaa (Seven Kingdoms: Ancient Adversaries is a real-time strategy game), Drogenkrieg, Lincity-NG (Stadt-Simulationsspiel), spring (Realtime strategy game inspiriert von totaler Vernichtung), simutrans (Simulation eines Transport- and Logistik-Unternehmens), hedgewars (heavyly armed figthing hedgehogs), FreeLords (similar to Warlords), cultivation, hheretic and sdl-hheretic Hacked Heretic (one more OpenGL-game), glightoff (Puzzle), monkey-bubble (similar to bust a move), bos (59 MB realtime strategy game), Pathological, bzflag, americasarmy, legends, xsoldier, ultimatestunts (remake of the DOS-racing game stunts), Wormux, Armagetron, biloba (board game), krosswordpuzzle and TooHot (Java) (cross word quizz), kshisen, blinken (inkrementierende Ton- and Farbfolgen nachklicken), frozen bubble, jools (graphisches Puzzlespiel), cebreaker (Puzzel), penguin-command, dopewars, dragonmemory, samuel (draughts program, guicheckers), amoebax (action puzzle), berusky (sokoban), biniax2 (color block logic game), brainparty (brain stretching game with 36 minigames), gbrainy, einstein (puzzle-remake), hex-a-hop (hexagonal puzzle), hexglass (puzzle based on hexagonal grid), invertapple, jag, krank (mouse manipulation game with nifty graphics), opengoo (Goo-clone), zaz (puzzle game), opeke (playing with virtual bricks), nethack-falconseye (3D adventure), dccnitghtmare, netpanzer, nil (54 MB), death illustrated (Ausbruch aus einer bizrarren 3D-Comicwelt), Maelstrom, pingus (Pinguine ins Ziel bringen, free Lemmings clone), egoboo, BlueDJ, ksudoku, bastet, ltris, kturtle, bastet and gnometris (Art Tetris), kudoku and gnomesudoku (Zahlenrätsel), hangman, ri-li (railroads), crossfire (client/server games), diggers (remastered), gnometris, t-crisis, cuyo and Ltris (Tetris), Marbles, Methane (methane brothers), ksquares (Käsekästchen), xlogical (ray-traced-graphik, Puzzle), geweled and kdiamond (three in one row), gnect and fourinonerow (four in one row), pente, grhino and bovo (five in one row), hexamine (minesweeper), katomic and atomix, mures, monster-masher, kjumpingcube, gnubik and kubrick (Rubiks Zauberwürfel), Openalchemist (naturalchimie, puzzle), general (Panzerschlacht), Kiriki (Kniffel), d2x (Descent 2 Version 1.2, the famous 3D game for PC), sunclock, vpioneers (Settlers of Catan), etswitch (ETSWITCH - A *nix ´minimizer´ for a few games), fizmo (A-Z-Machine interpreter supporting unicode, sound, blorbfile and more), gargoyle-free (graphical player for Interactive fiction games), playonlinux (play your Windows games on Linux), tuxtype, typespeed (type words that are flying by from left to right as fast as you can), million (russian quiz), glightoff (Puzzle), penttd (clone of the Microprose game "Transport Tycoon Deluxe"), uqm (The Ur-Quan Masters), BlockOut II, adonthell (2D RPG-game), kanagram, khangman, Travex, knetwalk, ktamaga (Tamagochi), kblackbox, kanagram, ktuberling (Kartoffelknülch), gnurobbo (Logik-Spiel), cummvm (platform for many adventure games), dokeos (e-learning 50MB), pioneers (Settles of Catan), caboodle, jools, monsterz, palapeli (puzzle), tuxmathscrabble, tuxmath, meandmyshadow (puzzle game), sdlvexed (puzzle), openalchemist, crimson-fields (tactical war game), cultivation (gardening community), dark-oberon, springlobby, stratagus, teg (risk), wesnoth, widelands (66 MB, Siedler II clon), asc (26 MB, ), jag (around 30 MB), affenspiel, ...
ScummVM (rpm) based adventures (you just have to type scummvm into a terminal): Baphomets Fluch, Baphomets Fluch II, Beneath a Steel Sky Dreamweb, Flight of the Amazon Queen, KingsQuest I-IV, Space Quest, Hopkins FBI, Indiana Jones and the Fate of Atlantis, Leisure Suit Larry 1 - In the Land of the Lounge Lizards (classics from the 80th), Loom, Leather Goddess, Lure of the Temptress, Lutris, Maniac Mansion: Day of the Tentacle, Monkey Island 2: LeChuck´s Revenge, Monkey Island 3: The Curse of Monkey Island, Police Quest, Police Quest II: The Vengeance, Police Quest III: The Kindred, Police Quest: In Pursuit of the Death Angel, Sam and Max Hit the Road, Simon the Sorcerer I and II, The 7th Guest, The Dig, The Secret of Monkey Island, Vollgas (Full Throttle), the 7th guest, the Manhole, Maniac Manson, ..
.
Overkill (ASCII-art game), 2h4u, 3omns, adime (Allegro Dialogs Made Easy), ags (Adventure Game Studio), andy-super-great-park (2D platforrm game), angrydd (Angry, Drunken Dwarves: Rock-Dropping Fun), arcomage (Arcomage clone), asc (Advanced Strategic Command--Turn-Based Strategy Game), atlas (high quality maps for flightgear), AtomicWorm, atomiks (emake of, and a tribute to, Atomix), ballerburg (Two players, two castles, and a hill in between), ballz (puzzle), barbie_seahorse_adventures (You are a seahorse and you want to go to the moon!), BASS (Beneath a Steel Sky (Adventure Game), bitfighter (2D multi-player space combat game), black-box (puzzle), blobAndConquer (Blob Wars: Blob and Conquer - a 3rd person action game ), bluemoon (card solitaire), bomns (Best old-school Deathmatch game ever (only for two players), bomberclone, brikx, bs (battleship game for the terminal), boswars, bsd-games, caesaria (Caesaria III remake), caph (Sandbox game based on physics), ceferino (game similar to Super Pang), cervi (Multiplayer game), chapping (button football game), chickens (target chickens with rockets and shotguns), chroma (puzzle), colobot (A real-time strategy game with programmable bots), commandergenius (open clone of the Commander Keen engines), crawl (Roguelike dungeon exploration game), crrcsim (Model-Airplane Flight Simulation), CubaLetra (word game), cube-escape, cubetest, cubosphere (3d puzzle similar to Kula World), cutemaze (Maze game), Desurium (Desura open-source client), domination (risk), dragonmemory, dunedynasty (Dune I), dunelegacy (Dune II), dustrac (2D Racing), ember (client for Woldforge), emilia (pinball), enemy-territory (Wolfenstein: Enemy Territory), etlegacy (Wolfenstein), fall-of-imiryn (2D RPG), fgrun (frontened for FlightGear), FlappyBird (Flap your wings to fly), FOTAQ (Flight of the Amazon Queen, Adventure), freedink (Adventure and Roleplaying), freegish (logic game), freeorion (space empire and galactic conquest), freeserf (modern Settlers 1 reimplementation), galaxis, gnome-mastermind, gnubg (Backgammon), gnurobo, gnushogi (Japanese Version of Chess), gpclient (gamepark client), gplanarity (puzzle), gweled (Clone of Bejeweled, align 3 crystals in a row), hexglass (Tetris-like Puzzle Game), hextris, jag (arcade puzzle 3D game), jools (puzzle), kbang (card game Bang!), kcheckers (Boardgame), keeperrl (Dungeon management and roguelike), khunphan (Thai Puzzle Board Game in 3D with Wooden Blocks), kiki (nano bot), knightsgame (dungeon bashing game), kqlives (console-style roleplaying game), kye (logic puzzle), lacewing (asteroids), legesmotus (Leges Motus is a 2D networked, team-based shooter), levelhead (Spatial Memory Game) and more: http://rpm.pbone.net/index.php3/stat/11/limit/129/dl/40/vendor/5207/com/obs
Bsd-games includes adventure, arithmetic, atc, backgammon, battlestar, bcd, caesar, canfield, cfscores, cribbage, go-fish, gomoku, hunt, mille, mpoly, morse, number, phantasia, pig, pom, ppt, primes, quiz, rain, random, robots, rot13, sail, snake, snscore, teachgammon, bsd-fbg, trek, worm, worms and wump.
mdv2010-Games - playonlinux: wine-emulatable: Many, many more games are waiting to get installed, including 3D-opengl Windows games with good sound like BSE-Schlacht (with cows on meadows from www.onlinewahn.de) and Clusterball - The Future Sports Experience - from daydream (also networking) Software, community / http://www.clusterball.de, actually 79 MB, 32 bit color depth, incl. MS Windows-drivers needed: airfight-balloon-game: collect together with other jet-fighters in different scenarios like Egypt and so on as many balloons as you can in order to turn them into real points by catching them from the next one too, hindering next ones by taking them under attack and flying through a ring in front of a great audience..., configuration of amount of ai-player (recommended seven max.), time limit, controls and so on: file config.cfg, 20 different flight-scenarios like Egypt, Yucatan, Metropolis, Ruhrmansk, Helter Skelter, Teranaki, Pole Position, Lunar, China, Matterhorn and Green Garden, Yucatan, Metropolis, Ruhrmansk, Matterhorn, Helter Skelter, China, Teranaki, Antarctica, Lunar, Green Garden, Electronica, Age Of Empires, Wheels of Steel, 3D Train Studio, Ares, Alone in the Dark, Alien Breed, BMW M3 Challenge, Baldur´s Gate, Battlefield2, Bioshock, Best One Poker, Bulletstorm, CivNet, Diabolo, Discworld, Dragon Age, FIFA, FlatOUtII, Football Manager, Full Tilt Poker, Dark Fall, Lands of Lore, Moonbase Commander, Nexus, Simon the Soucerer, Space Quest, Theme Hospital, Tyrian 2000, Ultima, Wizardry 8, Half-Life, Last Chaos, Lemmings2, Lume, MS Pinball, Poker Stars, Poker Stove, Seals with Clubs, Sanctum, Monkey Island, The Sims, Warcraft II and III, Xenon2, Zoo Tycoon, rFactor12, ...
.
Die besten Linux-Spiele für Steam, Ubuntu, Holarse, Gog, Shell, PCWelt.de, 15.04.2016
Ego-Shooter, Adventure, Logik-Puzzle, Simulation. Von Steam, Holarse, Ubuntu und Gog - wir stellen die besten Spiele für Linux vor. Viele sind kostenlos und müssen den Vergleich mit Windows-Spielen nicht scheuen. Plus: Coole Kommandozeilenspiele für die Linux-Shell, http://www.pcwelt.de/ratgeber/Action-Adventure-Logik-Die-besten-Linux-Spiele-464058.html .
Good old games (GOG): Alte Spielklassiker unter Linux zocken
playonlinux (el6, mdv2010, around 200 Top-Windows-Games)
Steam engine: Counterstrike, Half Life 2, secondlife, Wasteland 2, Civilization V and The Witcher 2. System requirement: for the steam-client of Linux is a graphic-card with drivers from Nvidia, AMD or Intel.and more Win&Mac&Amiga&... depending on the "grad" of emulation
PCWelt.de: Steam ist zwar die bekannteste Downloadplattform für Linuxspiele, doch es gibt durchaus noch einige weitere Internetquellen, von denen man Spiele für Linux beziehen kann. Zum Beispiel Desura (kostenlose und kostenpflichtige Spiele), indiegamestand https://indiegamestand.com/ oder das allseits bekannte Gog.com, https://www.gog.com/news/gogcom_now_supports_linux. Auf Gog (Good old games) kauft man die Spiele (derzeit stehen rund 50 Linux-Spiele zur Auswahl) und lädt sie anschließend herunter. Gut: Die Gog-Spiele sind frei von DRM und lassen sich auch offline spielen. Neue Spiele findet man allerdings keine auf Gog, stattdessen bringt Gog Spieleklassiker auf Linux zum Laufen. Das muss dem Spielspaß aber keinen Abbruch tun, denn mit Klassikern wie Duke Nukem, Train Fever, The Dig, Tie Fighter Special Edition sowie Indiana Jones und das Schicksal von Atlantis ist langer Spielspaß garantiert. Auf indiegamestand wiederum findet man sogar zwei Rankings für die Linuxspiele.
Die besten kostenpflichtigen Linux-Spiele: Sky Rogue, Escape Goat, Guns of Icarus Online, Megabyte Punch, Epistory, Blueprint Tycoon, Finding Teddy 2, Evo Explores, Bastion, Rochard, World of Goo, ARK Survival Evolved, Factorio, Enter the Gungeon, Tabletop Simulatior, Couter-Strike: Global Offensive, Firewatch, XCOM 2, American Truck Simulator, Creatures Internet Edition, Hyperspace Delivery Boy, EVE Online, Tribes 2, Warcraft II, Battlefield 2142, Transport Tycoon, Tribal Trouble 2, The Dark Mod, ...
http://www.pcwelt.de/ratgeber/Action-Adventure-Logik-Die-besten-Linux-Spiele-464058.html
Einschub: clusterball: schließt das Spiel nicht immer. Sollte der fullscreen-mode versagen: Öffne die Konfigurationsdatei. Wähle den Fenstermodus. Starte und wähle die aktuelle Bildschirmauflösung anstelle "auto".
Warhammer 40000: Dawn of War II kommt für Linux
Das Strategiespiel Warhammer 40000: Dawn of War II kommt für Linux. Mit den Erweiterungen Chaos Rising und ...
http://www.pcwelt.de/ratgeber/Action-Adventure-Logik-Die-besten-Linux-Spiele-464058.html
WineHQ, https://appdb.winehq.org/votestats.php: Final Fantasy XI Online Final Fantasy XI, EVE Online Current, World of Warcraft, Magic: The Gathering Online 3.x, The Sims, StarCraft I, Guild Wars All Versions, StarCraft II, Fallout 3 1.7 and GOTY, Aion: The Tower of Eternity 4.7.1, Team Fortress 2 Steam, Adobe Photoshop CS3 (10.0), Planetside 2 Release 97, Watchtower Library 2014, Guild Wars 2, Left 4 Dead Full (Steam), RF Online Episode 2, The Witcher 1.0, Deus Ex: Human Revolution, Empires: Dawn of the Modern World, Final Fantasy XIV Heavensward (Official Client), Counter-Strike: Source Retail / Steam, Warcraft III The Frozen Throne: 1.x, ...
Command & Conquer 3: Tiberium Wars 1.x, PunkBuster, Supreme Commander SC 1.x.3xxx, The Elder Scrolls IV: Oblivion 1.2.x, Allods Online 1.x, Bioshock, Call of Duty 4: Modern Warfare 1.7, Sid Meier´s Civilization IV Complete, Gothic 3 1.x, Star Wars: The Old Republic 1.5-2.0 - Free to Play, Half-Life 2 Retail (32-bit), Battlefield 2 1.x, City of Heroes All Versions, Runes of Magic Official release, Homeworld 2 1.x, Day of Defeat: Source Steam, Lord of the Rings, Helm´s Deep, Planescape: Torment 2/4 CDs version (1.x), Garena Garena Messenger (Beta), GameGuard Bundled, The Elder Scrolls V: Skyrim All Versions, System Shock 2 2.3, Spore 1.x, Dragon Age: Origins 1.x, Silkroad Online 1.x, S.T.A.L.K.E.R.: Shadow of Chernobyl Retail, Space Empires V 1.77, Perfect World International, Diablo III 2.x.x (No RoS), X3: Reunion 2.0.0, High Velocity Paintball 1.2 28, Revit Architecture, Medieval 2: Total War Retail CD 1.x, The Elder Scrolls III: Morrowind 1.6.1820 (Bloodmoon), Mass Effect 1, Age of Empires II The Conquerors Expansion, Dragon Naturally Speaking 13, Company of Heroes 2, Assassin´s Creed 1.x, Armed Assault 1.x European, Galactic Civilizations II: Dread Lords 1.x, Age of Conan: Hyborian Adventures AoC client, EverQuest II Full Install Client, Command and Conquer: Red Alert 3 Retail 1.x, Worms Armageddon 1.0-3.6.29.0, Reason 3.x, Portal 2 Steam, Age of Empires III 1.x, UnrealEd 3.0, Microsoft Word 2007, Voobly 2.2.0.1, Neverwinter Nights II 1.23.x, Unreal Tournament 3 Retail, Mythos Mythos-Europe Beta, Crysis Crysis 1.x , Battlefield Bad Company 2 Retail BFBC2, EverQuest EverQuest (Live), Xfire 1.10x, Rome: Total War 1.x, League of Legends 0.* beta, Lingvo x5 English, Orbiter 060929, Garry´´s Mod, Half-Life, Counter-Strike: 1.6 16, Diablo 1.0x, Rift Live, Sins of a Solar Empire 1.x, Fallout 4 Steam, The Longest Journey Build 161, IL-2 Sturmovik Series IL-2 Sturmovik 1946, Star Wars: Jedi Knight - Jedi Academy 1.01, SimCity 4 Deluxe, Empire Earth 1.0-2.0, Battlefield 2142 1.5, Baldur´s Gate II Throne of Bhaal, PokerStars Latest 14, Live For Speed S2, Left 4 Dead 2 Left 4 Dead 2 Full (Steam), Mount&Blade Warband,.TomTom HOME 2.x, Mafia II: Full game 13, Requiem Online 12, .Spore Creature Creator Trial Edition 13, Airline Tycoon Evolution 1.02, Fallout: New Vegas 1.x, Soulbringer 1.x, Vanguard: Saga of Heroes Release, TERA Online NA Retail, Warcraft III, Call of Duty 2 1.00 13, Anarchy Online Internet Play, Drakensang: Das Schwarze Auge 1.0, Walfadia Populous Online Lobby Walfadia Populous Online Lobby, Street Fighter 4 1.0, Microsoft Flight Simulator X, Company of Heroes 1.71, Age of Mythology Steam, Hearthstone: Heroes of Warcraft All Versions 12, Football Manager 2013, Entropia Universe 11.x, Empire: Total War 1.0, Phantasy Star Online: Blue Burst 1.24.15 (Schthack), Defense Grid: The Awakening Steam, .BYOND 5.x, Freelancer 1.x, Thief: Deadly Shadows 1.1 (CD), The Secret World Release, Age of Wonders III Steam, Halo: Combat Evolved 1.0.10, Need for Speed Most Wanted All Versions, Grand Theft Auto: San Andreas 1.x, Anno 1404 1.00, DotA 2 Early Access - Steam 11, ElsterFormular 17.x, Hearts of Iron III 1.x, The Witcher 1.4, Path of Exile Release, Sacred 2.02.5 --> 2.28 11, League of Legends 5.x, Hellgate: London SP 0-0.6 / MP 0-1.1b, Warhammer 40,000: Dawn of War II 1.1, The Saga of Ryzom FV 1.9.1, Thief II: The Metal Age 1.x, Black & White 1.100, Fable: The Lost Chapters 1.0, Borderlands 2 1.0, Evil Genius Steam / Retail 10, ..., ...
https://appdb.winehq.org/objectManager.php?bIsQueue=false&bIsRejected=false&sClass=distribution&iId=1099&sAction=view&sTitle=View+Distribution: Heroes of Might and Magic II 1.0 (original) Giovanni Mariani Nov 12 2012 1.5.17 Yes Yes Platinum, BrainVoyager, UFO: Afterlight 1.xx, UFO: Afterlight 1.xx, Heroes of Might and Magic V Collectors Edition v1.60, FurMark 1.9.1, FurMark 1.8.2, Restaurant Empire 1.2.1, The Nations 2.00 gold (Build #34), Anno 1602: Creation of a New World 1.x , Restaurant Empire 1.2.1, Restaurant Empire 1.2.1, FurMark 1.9.1, Ghost Master 1.0, Autodesk Design Review 2009, Internet Explorer 9.0 for NT 6.0 (32-bit), Lionheart: Legacy of the Crusader 1.1, Diablo II Lord of Destruction 1.x, CircuitCam 5.2, SimCity 4 1.x, Rosetta Stone 3.3.x, Catia V5R19, -2 Sturmovik Series IL-2 Sturmovik 1946, Plants Vs. Zombies 1.x, The Sims 3 All, The Settlers III Quest of the Amazons, Sins of a Solar Empire 1.01, The Elder Scrolls IV: Oblivion 1.1.511, Disciples III, S.T.A.L.K.E.R.: Call Of Pripyat 1.0 Russian Release, Theatre of War 2 v1.3, SlingPlayer 2.0, Need for Speed II Demo, Tom Clancy´s Splinter Cell 1.3, Crazy Combi 3D Pre Release, Hellforces 1.0, The Operative: No One Lives Forever GOTY (1.004), Fallout 3 1.7 and GOTY, Silent Hunter 5 1.1, Cities XL 1.0.3.x, ...
Software: Spiele
Steam: More than 2000 games for Linux announced, pro-linux.de, 01.03.2016
Seit der Veröffentlichung von Steam für Linux vor zwei Jahren ist die Zahl der Titel für Linux stetig gewachsen. Mittlerweile listet die Plattform über 2000 Titel, die für das freie Betriebssystem entweder erschienen sind oder erscheinen werden. Die Zahl der veröffentlichten Titel liegt bei über 1900.
Woche um Woche wird das Angebot an Linux-Spielen größer. Zu sehen ist das unter anderem auf der Spiele-Plattform Steam. Hatte der Anbieter noch im Spätsommer des vergangenen Jahres das Erreichen von 1500 Spielen verkünden können, so ist die Zahl der Titel weiter gewachsen. Aus den anfänglich 60 Spielen bei der Freigabe von Steam sind mittlerweile 1900 geworden. Rechnet man zu den Spielen auch die bereits für Linux angekündigten, aber noch nicht freigegebenen Spiele, so liegt die Zahl der Titel bei über 2000, http://www.pro-linux.de/news/1/23303/steam-ueber-2000-spiele-fuer-linux-angekuendigt.html
Linux-TOP-Games auf Basis spezieller Game-Engines: 24.167 (Stand 31.01.2015) populäre absolute Top-Spiele auf der Basis der Engine Unity gefolgt von Steam, Sauerbraten u.a. für Windows und Linux, Nutzung auf eigene Gefahr: http://www.indiedb.com/games/top, z.B.:
Planet Nomads, Craneballs, Shinobi Life Online, Gang Beasts, CHKN, Creator Powers, TerraTech, StarWars Battlecry, Garbage Day, Velocibox, Besiege, Planet Pokemon, Vanish, Robocraft, Hunie Pop (HuniePop is a unique sim experience for PC, Mac and Linux. It´s a gameplay first approach that´s part dating sim, part puzzle game, with light RPG elements, a visual novel style of presentation, an abrasive western writing style and plenty of "plot".
After a pathetic attempt to try and pick up Kyu, a magic love fairy in disguise, she decides to take you under her wing and help you out with your crippling inability to meet new women. After a few dating lessons and some sound advice, Kyu sends you out into the world ready to take on the dating world and a wide cast of beautiful babes.), Overgrowth ( Hey everyone! I"m Steve, the new character concept artist for Overgrowth. In this post I will share some of the designs I"ve been working on. All images in this post can be clicked to bring up a wider view and higher resolution version of the image. It´s been a bit of a challenge to get used to drawing anthropomorphic animal characters as I have very little experience with animal anatomy. Here is my first attempt at designing the Overgrowth races, completed during the application process to supplement my portfolio), crawl, slime-rancher (Slime Rancher is the tale of Beatrix LeBeau, a plucky, young rancher, who sets out for a life a thousand light years away from Earth on the Far, Far Range where she tries her hand at making a living wrangling slimes. With a can-do attitude, plenty of grit and her trusty vacpack, Beatrix attempts to stake a claim, amass a fortune and avoid the continual peril, that looms from the rolling, jiggling avalanche of slimes around every co), ...
Steam: Counterstrike, Half Life 2, Wasteland 2, Civilization V und The Witcher 2. You need a graphic card from Nvidia, AMD or Intel.
Total War Collection for Linux vorgestellt, PCWelt.de, 13.01.2016
Medieval II: Total War Collection wird in dieser Woche für Linux und Mac OS X veröffentlicht.
GRID Autosport für Linux and Mac OS X available
Feral Interactive (XCOM: Enemy Unknown, Mittelerde: Mordors Schatten, Alien: Isolation), http://www.pcwelt.de/prolinux/GRID-Autosport-fuer-Linux-und-Mac-OS-X-verfuegbar-9895039.html
"Dead Island: Definitiv Edition" for Linux released, pro-linux.de, 07.06.2016
http://www.pro-linux.de/news/1/23624/dead-island-definitive-edition-für-linux-freigegeben.html .
Strategy game "Hearts of Iron IV", pro-linux.de, 07.06.2016
http://www.pro-linux.de/news/1/23627/strategiespiel-hearts-of-iron-iv-veröffentlicht.html.
Für absolute Gamer bieten sich natürlich auch Spielekonsolen wie XBox und Playstation an. Doch weiter mit mdv2010, zumal u.a. unsere onboard IGP Graphik wie der Soundchip von INTEL überall ganz ausgezeichnet mitspielen:
Console-Games (mdv): kpacman (* i386 only), moon-buggy, glightoff, kbilliards (fc22), ...
... and if you ever ask mdv for a flight-simulator full of action: gl-117 beneath flightgear or perhaps YS Flight Simulation System 2000 with more than 30 types of airoplanes for civial and military use? Or what about searchandrescue (helicopter simulation)?
Game-provider Steam, packet steam (mga3/rpm): Steam offers games for Linux too: Counterstrike, Half Life 2, Wasteland 2, Civilization V and The Witcher 2. System requirement: for the steam-client of Linux is a graphic-card with drivers from Nvidia, AMD or Intel.
Emacs-Games (PCWorld, 04.10.2015): Emacs is an editor containing lisp and some games like "tetris", "pong", "bubbles" and "snake". To start them, press "ESC", then "X" and enter the name of the game. Such emacs-extensions can be find in "/usr/share/emacs/[Version]/lisp/play"
These games can be played either with your computer only or against more players online. There are not only such many games for free, but also games free or to pay like actual listed ones from http://holarse.de/ and https://www.gamingonlinux.com/sales/. If anything is prepared well with emulator qemu or wine (wine32 or wine64), you can emulate a lot of Windows games too, same for games coming from Amiga, Atari, Commodore, Cedega and so on. More games for Linux see our linkside!
GRID car racing sport for Linux and Mac OS X available, PCWelt, 12.13.2015
Feral Interactive (XCOM: Enemy Unknown, middle earth: Mordor´s shadow, alien: isolation) has published 2015 GRID car racing sport for Linux, http://www.pcwelt.de/prolinux/GRID-Autosport-fuer-Linux-und-Mac-OS-X-verfuegbar-9895039.html, this game is not for free: 39,99 €
Browser-Flash-Games just require a browser with flashplugin:
Tanki Online, Haunted House, Cat Mario Online, Black Petes Lemmings, The Fancy Pants Adventure World 2, Cubez, Funny Quest, FWG Pinball, Gold Panic, Manifold, Mon Sodoku, Orbox B, ...
Half-life, Duke Nukem, Train Fever, The Dig, Tie Fighter, Indianer Jones, ...
Old game classics for Linux, PC-WELT.de, 20.11.2019
https://www.pcwelt.de/ratgeber/Alte-Spieleklassiker-unter-Linux-zocken-9966987.html
https://www.gog.com/%3F%3Fpp%3D97eeedd847517b527df707e56fdb8bc5c7dff1ce
ePSXe emulates the PlayStation of Sony onto Windows-, Linux- and Android-systems; damit lassen sich Spiele für die Spielekonsole auch auf dem Computer, Smartphone oder Tablet spielen
PPSSPP - Open Source Emulator, der Spiele für die PlayStation Portable auf Computer und Mobilgeräte spielbar macht; bietet eine HD-Auflösung und optimiert die Grafik für die genutzte Monitorgröße; Spielstände lassen sich speichern.
PCSX2 - emulator for the PlayStation 2
597 games from https://www.heise.de/download/products/linux/spiele?page=1, Stand: 10.06.2020 :
Pandemic 2 1.1, Strategiespiel mit Management-Elementen im Browser; Spieler "steuern" eine Krankheit und müssen mit dieser die gesamte Weltkarte infizieren; hierzu müssen sie Keime strategisch klug platzieren und stetig weiterentwickeln; Impfstoffe, Gegenmaßnahmen und geologische Grenzen wollen überwunden werden; Highscores lassen sich online vergleichen; auch als App für iOS
Stellaris, D2X-XL, Kakuro Nichiyou 1.0.1, Stunt Rally 2.6, UFO: Alien Invasion 2.5, Zero-K 1.1.4.0, Donkey-Me 1.0, MAME (Multiple Arcade Machine Emulator) 0.152, Amnesia: The Dark Descent, Baldur´s Gate 2, Digger.JS, X Speed Race 2013-09-20, Crawl, Dota 2, Gianas Return 1.001, The Dark Mod 2.0, Advanced Strategic Command 2.6.0, Defense Grid 2, Iris2 2.0, DOFUS 2.19, BrettspielWelt 2.514, Anna80;s Quest, War for the Overworld, LIMBO, Pushover, Epic Battle Fantasy 4, Dark Dimension 2.2, One Late Night 1.0, Kapi Hospital 2010-08-04, OpenSimulator, Spring 100.0, Lutris, Legends of Honor 1.20.0, Shadow Kings, Putt-Putt,
Planet M.U.L.E. 1.3.6, The Enchanted Cave 2 3.12, Cave Story, Inverto v.3, World of Goo, Godot 3.2.1, Stargunner, World of Padman 1.6, Clonk Rage 4.9.10.5, YS Flight Simulator 20110207, Firewatch Soundtrack Edition,
Pajama Sam, Lemmini 0.77, Serena, OpenRocket 15.03, Sudokumat 5.7, Criminal Case 1.33, RollerCoaster Tycoon World PC Steam Code, Endless Sky 0.8.11, PunkBuster Setup 3.4, Omnitux 1.2, Algodoo (Phun) 2.1.0, Doko-Lounge Spieleclient 1.64, Oil Rush: Naval Strategy Game 1.0, The Dream Machine, Duolingo - Sprachen lernen 6.71.0, Freddi Fish, Fussballcup 1.4.1, Racer 0.9.0 RC10, UltraStar Deluxe, Zak McKracken, Cities: Skylines, Return of the Tentacle - Prologue 1.0.1, American Truck Simulator, Nestopia Undead Edition 1.49, Counter-Strike: Source, Snes9x, Snes9x EX+, OpenDUNE 0.9, mupen64plus 2.0.0, Kerbal Space Program, Wolfenstein: Enemy Territory 2.60, Half-Life 1.1.2.1, Ultimate Chicken Horse, PuniTy 1.0, True Combat: Elite 0.49, Hasenschule 1.0.0, Train Fever 1.0, Baldurs Gate 2 Widescreen Mod, Eyes - The Horror Game, Big Farm, Rigs of Rods 2020.01,
Pirates, Vikings, and Knights 2, Bridge Constructor, Descent 3, Return to the Roots 0.8.1, Superhot, Unknown Horizons (OpenAnno) 2014.1, The Elder Scrolls II: Daggerfall, Team Fortress 2 1.0, Minetest 5.2.0,
Beneath a Steel Sky 1.2, Domination (Risk Board Game) 1.2.1, Spy Fox, Danger from the Deep 0.4.0, The Binding of Isaac: Rebirth, Hearts of Iron IV, Tux, of Math Command 2.0.3, Armikrog, Bolzplatz 2006 1.0.3, MegaMek 0.40.1, Zaz 1.0.0, Tile Racer 0.702, Pennergame 3.1, Ulis Mansion 1.0, Gladiabots - AI Combat Arena, Tormentum - Dark Sorrow, Now Boarding 1.2.2 - Simulationsspiel eines Flughafenbetriebs; der Spieler soll den Ablauf organisieren und Mitarbeiter anleiten, JEliza 2.2.2, Singularity 0.30c, CoreBreach 1.1.5, Towns, Screwball 1.0, Dead Synchronicity: Tomorrow Comes Today, Satellite Reign, Istrolid, Tangram 1.1, Dwarf 3D 1.20, WebStratego 7.0.9, Discoverie 1.0, Illarion 1.0.0.39, Boson X 1.0.5, CG Madness 1.3, War for Diamonds, TrafficLights 1.0, Gaurodan 1.0, Haiku Hero 1.0, Sword Coast Legends, Crookz - Der große Coup, Cookie Clicker, ..., ...
https://www.heise.de/download/products/linux/spiele
...
type writing: sl (steam engine lockomotive (train) on the konsole resp. terminal ), lavaro (touch typing editor), tuxtype, tuxtype2, dvorak-7min (typing editor), ...
secure file deletion: srm, wipe, shred, ...
files copying: cp, ultracopier, ...
Open Vulnerability Assessment (OpenVAS) Scanner: openvas (el6), ...
Forensics (el6): AdobeMalwareClassifier (el6), afflib (advanced forensic format), afftools (el6), analysis-pipeline (el6), artifacts (el6), binplist (el6), bloom (el6), bulk_extractor (el6), bokken (el6), CERT-Forensic-Tools (el6), dc3dd (el6, ähnlich dcfldd), distorm3 (el6, binary stream disassembling library), disktype (el6), epub (extracts thumbs and metadata from thumbs.db), fiwalk (el6, finds and extracts files from a given type), fcrackzip (el6), fred (el6, Windows Registry Editor), galleta (el6, reads out cookies), grokevt (el6, reads and processes Windows-Event-files), guymager (el6, imager for forensic media acquisition), ipa (el6, IPA (IP Association) is a library for maintaining associations between IP addresses and any number of labels which categorize those addresses), jafat (el6, assortment of tools to assist in the forensic investigation of computer systems), libvshadow_tools (el6), log2timeline (el6, md5deep (el6, compute MD5, SHA-1, or SHA-256 message digests on files), mdbtools (suite of libraries and programs to access Microsoft Access Databases), rpmreaper (el6), ... (siehe Cert Forensik Tools wie beispielsweise von pkgs.org), memdump (memory dump), ncat, nDeep (el6, deep packet inspection), netsa-rayon (el6, visualization toolkit), nmap (el6, security and port scanner), nping (el6), partclone (el6), pavuk (el6, www or ftp site mirror tool), prism (el6, visualizes flow data as a time-series broken down into several configurable bins), protobuf (el6, Protocol Buffers - Google´s data interchange format), pstotext (el6), python-registry (el6, Python´s access to the Windows Registry), radare (el6), reglookup (el6, Windows NT registry reader/lookup tool), rifiuti (el6, examines the contents of INFO2 in the Windows Recycle bin), silk-analyzes (el6), sleuthkit (el6), sleuthkit-libs (el6), snarf (el6, Structured Network Alert Reporting Framework), snort (el6, open source Network Intrusion Detection System (NIDS)), stegdetect (el6, detects and extracts steganography messages inside JPEG), super_mediator (el6), tcpflow (el6, network traffic recorder), videosnarf (el6, output detected media sessions), vinetto (el6, extract thumbnails out of Thumbs.db), xplico (el6, Internet traffic decoder and network forensic analysis tool), yaf (el6, Yet Another Flow sensor), nessus (el6), wireshark, ettercap (el6), clamav (el6), hwinfo (el6), paraview, keepass, lastpass, revelation, bleechbit, sweeper, klean, lastlog, blast, last, snort (el6)
Data-recovery: dd, dcfldd (from el6; works like dd, but with progressbar and more options), fsck, extundelete (file recovery), rlinux (reiserfs, ext3 and ext4, file-recovery) and testdisk (tools to check and undelete partition or recover deleted files), qphotorec (el6), mondo (GPL disaster recovery solution to create backup media (CD, DVD, tape, network images) that can be used to redeploy the damaged system, as well as deploy similar or less similar systems. A program to create a rescue/restore CD/tape), ddrescue and dd_rhelp (Data recovery tool trying hard to rescue data in case of read errors - data recovery tool CD/tape), bacula, afbackup, rsync, grsync, rdiff, safecopy (replacement for dd in the case of I/O-errors), ...
postifx, secure mail transfer: sendmail and exim
SQL-Database-Firewall: greensql-fw
psad (port scan detection), lidstools, kernel securing functions: port-scan-detector, Mandatory Access Controls (MAC), File Protection (even against root) and protection for processes
IDS (intrusion detection systems). aide, suricata, nads, watchdog, prelude-manager, ossec-hids, samhain, ...
"Lynis is a security and system auditing tool. It scans a system on the most interesting parts useful for audits, like: - Security enhancements - Logging and auditing options - Banner identification - Software availability Lynis is released as a GPL licensed project and free for everyone to use. See http://www.rootkit.nl for a full description and documentation."
 Hacked server - tips, what to do, wiki.hetzner.de Hacked server - tips, what to do, wiki.hetzner.de
Preliminary remark
The only possiblity to clean a hacked server is renew the installation. In order to secure the server the right way, it should be found out, where the server got hacked.
This should be done, even if the new installation makes a lot of efforts. No application and program can be trusted anymore. Each installed software migh get changed and exchanged by hacker.
Logfiles
On the one hand, logfiles deliver plenty of information, how the hacker intruded (if offsiite-backups have been made), on the other hand, they can not be trusted or they do not exist anymore.
Help by programs
chrootkit: http://www.chkrootkit.org/download.htm
rkhunter: http://rkhunter.sourceforge.net/
tiger: http://www.nongnu.org/tiger/
Unknown files
Can any files be found out on the server, that have unknown origins?
changetrack: http://changetrack.sourceforge.net/
tripwire: http://www.tripwire.org/
Secure up a server- howto
https://wiki.hetzner.de/index.php?title=Security&printable=yes
Portscan detector (psad and/or iptables: psd) and Intrusion Detection Systems (IDS)
Anonmity online: JAP (Jondo from TU Dresden by JAP.jar), Tor (also a rpm) with GUI vidalia (el6), PHP-Proxy from Abudullah Arif (upload the script to a proxyhoster), any proxy from a listing, fireproxy (firefox-extension), our SSL-encrypting proxy, ...
Bastille(DVD 2, although already present by draksec and drakperm) is a system hardening / lockdown program which enhances the security of a Unix host. It configures daemons, system settings and firewalls to be more secure. It can shut off unneeded services and r-tools, like rcp and rlogin, and helps create "chroot jails" that help limit the vulnerability of common Internet services like Web services and DNS. This tool currently hardens Red Hat Enterprise Linux, Legacy, and Fedora Core, as well as Debian, SUSE, Gentoo, Mandrake Linux, Mac OS X, and HP-UX. If run in the preferred Interactive mode, it can teach you a good deal about Security while personalizing your system security state. If run in the quicker Automated mode, it can quickly tighten your machine, but not nearly as effectively (since user/sysadmin education is an important step!) Bastille can also assess the state of a system, which may serve as an aid to security administrators, auditors and system administrators who wish to investigate the state of their system´s hardening without making changes to such.
Hand-Recogntion: zinnia (Online hand recognition system with machine learning), ...
draksec and drakperm are parts of drakconf: checks for SUID- and SGID-files, write-checks upon files Dateien, checks of files like .rhosts and hosts.equiv, via inetd configured network services, tcp_wrappern, shadow passwords, access-rights, system-configuration, makesig.pl (creating signatures), ....
more security-software: tor (popular anonymizing network, the onion router), vidalia (frontend of tor), xtraceroute, tcptraceroute, traceroute, flashrom, biosdisk (BIOS flash floppy images), draksec and drakperm, rkhunter, zeppoo and chkrootkit (including rpm sectools and python-selinux), checksec (check executables and kernel properties), memtest and valgrind (memory check), ciphertest, lads (login anomaly detection system), psad, clamtk and clamav-0.98.4-65, maldetect (rosa2014.1), tomoyo (kernel security-module providing Mandatory Access Control: Unlike AppArmor, TOMOYO Linux is intended to protect the whole system from attackers exploiting vulnerabilities in applications. TOMOYO Linux addresses this threat by recording the behaviour of all applications in the test environment and then forcing all applications to act within these recorded behaviours in the production environment. TOMOYO Linux is not for users wanting ready-made policy files supplied by others. It involves creating policy from scratch, aided by the "learning mode" which can automatically generate policy files with necessary and sufficient permissions for a specific system. TOMOYO Linux reports what is happening within the Linux system and can therefore be used as a system analysis tool. It resembles strace and reports what is being executed by each program and what files/networks are accessed ), arpwatch, tmpwatch, smartd, seccheck (scripts for periodical security-checks), noflushd and spindownd (daemons, that send idle disks to sleep against providing root-rights; for spindown endangering terminal-login-mode, prefer noflushd), partimage and diskimg, subversion (CVS - current versioning system), freeswan (IPSEC), openvpn, kvpn, openconnect (client for the Cisco AnyConnect VPN protocol), patcher, snort, airsnort and aircrack (wireless LAN-tool which crack encryption keys), ethereal (Network traffic analyzer), dsniff, dsniff-webspy, hddtemp, procinfo, xsysinfo (kernel-parameter monitoring tool), smartd, knock (smashes large holes into firewalls for hacking dependent from the blocking-rate), shorewall and mandi (firewall from installation-DVD), digitemp (reads values from Semiconductor 1-wire devices. Its main use is for reading temperature sensors, but it also reads counters and understands the 1-wire hubs with devices on different branches of the network. DigiTemp now supports the following 1-wire temperature sensors: DS18S20 (and DS1820), DS18B20, DS1822, the DS2438 Smart Battery Monitor, DS2422 and DS2423 Counters, DS2409 MicroLAN Coupler (used in 1-wire hubs) and the AAG TAI-8540 humidity sensor), git, nut (UPS tool), Zeitgeist is a service which logs the users´s activities and events (files opened, websites visites, conversations hold with other people, etc.) and makes relevant information available to other applications. Note that this package only contains the daemon, which you can use together with several different user interfaces. ...; more security-software see step2!
VPN: kvpnc,vpnc (supports Cisco VPN (vpnc) and IPSec (FreeS/WAN, racoon), gopenvpn, openvpn, vpnd, openconnect, saveyourprivacy.net, ...
 Police campagne against Safe-Inet: "Favorite-VPN" of cybercriminals got shut down, trojaner-info.de, 12.29.2020 Police campagne against Safe-Inet: "Favorite-VPN" of cybercriminals got shut down, trojaner-info.de, 12.29.2020
Crime investigators from Europe and USA stroke a massive blow againste cybercrime. On Monday they shut down the service "Safe-Inet" and confiscated its webdomains. Through them a "Virtual Private Network"-offer (VPN) was provided, that many online-criminals supposedly should have used, in cover up their tracks like IP-adresses. Europol speaks of "Favorite-VPN" of cybercriminals.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/polizeiaktion-gegen-safe-inet-lieblings-vpn-von-cyberkriminellen-abgeschaltet-8139.html
visitors (rpm): processes a web log file trying very hard to identify a single "person" as much as possible. This is typically achieved by use of either an identifying cookie in the log file; Or via the IP Address/Name &Browser ID combination.
ssldump similar to tcpdump, dumpcap, tshark, wireshark and flowtools from DVD - this program is an SSLv3/TLS network protocol analyzer. It identifies TCP connections on the chosen network interface and attempts to interpret them as SSLv3/TLS traffic. When ssldump identifies SSLv3/TLS traffic, ssldump decodes the records and displays them in a textual form to stdout. And if provided with the appropriate keying material, ssldump will also decrypt the connections and display the application data traffic. This program is based on tcpdump, a network monitoring and data acquisition tool.
Linux FreeS/WAN is an implementation of IPSEC & IKE for Linux. This package contains the user-space utilities needed to manage IPSEC. To use IPSEC, you will need to build support into the kernel as well. Please see the FreeS/WAN homepage at http://www.freeswan.org for details. IPSEC is Internet Protocol SECurity. It uses strong cryptography to provide both authentication and encryption services. Authentication ensures that packets are from the right sender and have not been altered in transit. Encryption prevents unauthorised reading of packet contents. These services allow you to build secure tunnels through untrusted networks. Everything passing through the untrusted net is encrypted by the IPSEC gateway machine and decrypted by the gateway at the other end. The result is Virtual Private Network or VPN. This is a network which is effectively private even though it includes machines at several different sites connected by the insecure Internet.
Password-cracker: john (brute-force), fcrackzip (zip password cracker), Crack (password-cracker from el6), ...
Packit is a network auditing tool like the network traffic recorder tcpflow. It´s value is derived from its ability to customize, inject, monitor, and manipulate IP traffic. By allowing you to define (spoof) all TCP, UDP, ICMP, IP, ARP, RARP and Ethernet header options, Packit can be useful in testing firewalls, intrusion detection systems, port scanning, simulating network traffic and general TCP/IP auditing. Packit is also an excellent tool for learning TCP/IP.
zero-install: The Zero Install system removes the need to install software or libraries by running all programs from a network filesystem. The filesystem in question is the Internet as a whole, with an aggressive caching system to make it as fast as (or faster than) traditional systems such as Debian´s APT repository, and to allow for offline use. It doesn´t require any central authority to maintain it, and allows users to run software without needing a root password.
remote access: rlogin, rsh and rcp (packet rsh, )rdesktop (remote RDP-client), recordmydesktop: Desktop session recorder -
Simple command line tool that performs the basic tasks of capturing and encoding desktop session. It produces files using only open formats like Theora for video and Vorbis for audio, using the Ogg container.
xtraceroute and traceroute - print the route packets trace to network host, for example if through foreign server.
... repertoire of actually more than 65 GB rpm (15 DVD) + many Fedora-rpm + infinite amount of Tarballs and thousand applications of all kind!
truetype-fonts from Linux and OpenOffice, import-function by system-configuration for any fonts from anywhere, recommended font: Liberation fonts like Liberation sans (quit Arial), Liberation serif (instead of Times New Roman), Liberation Mono (Courier) from DVD 2), Libertine, arabic, cyrillic, handwrite, bitmap, adobe-utopia, bh, ubuntu, tamil, libertine, west_european, unifont, sun-misc, fontsproto, fondu (MAC-UNIX-fonts-converter) ..., package TrueType-fonts, ...
Language-files for OpenOffice, Firefox and KDE: english, french, german, turkish, italian, spanish, russian, modern and traditional chinese, ...depending on the country within the order and orderer name
von fr2.rpmfind resp. separat from DVD 4 for all listed, not included in DVD 2):
aeolus (Pipeorgan Emulator), bibletime, biblesync, bibtool, bibleverse, bibleanalyzer (pclos2017), xgospel, xiphos and bibutils (work with the bible), barry (blackberry desktop), sagemath (complex mathematic-system), cherokee (Browser), enouveau (opengl-Tests and Beobachtung der Veränderungen in den Videokarten-Registern), Rygel (UPnP MediaServer V 2.0 specification that is specifically designed for GNOME. It is based on GUPnP and is written (mostly) in Vala language. The project was previously known as gupnp-media-server), USB Modeswitch (brings up your datacard into operational mode. When plugged in they identify themselves as cdrom and present some non-Linux compatible installation files. This tool deactivates this cdrom-devices and enables the real communication device. It supports most devices built and sold by Huawei, T-Mobile, Vodafone, Option, ZTE, Novatel), uzbl, zabbix (net-monitor), bickley (API-framework), ...
Java-programs: because of portability of all kind: to pay, for free, out of the interenet, already listed rpm-packaged ones, ...
Emulation (Win98+XP+7+...), for example.: Zero Emission Pad (zep), Clusterball, BSE_Schlacht, PowerTranslator, Skorloto 417 Combinator v3, notepad++, IE7, aborange LottoMaster, Lotto-Systeme, Druckstudio2001, PrintStar, Systran Webtranslator 5.0, KlickTel, Europa-Arbeitszeugnis, Kreuzworträtselgenenerator KWR, Europa-Reiseplaner (Varta), software from playonlinux up to MS Office 2003, ..., (... infinite!)
24h- live-support from kde-look.org, kde-apps.org, rpmfind.net, mirror fr2.rpmfind.net (lifetime) and linux-newsgroups with continuous increasing software-repertoire: more than 65 GB (15 DVD, 2013) plus all kind of tarballs. Both server do not seem to offer their services at any time. With the three DVDs you also contribute to their disburden!
overview rpm for mdv2010.0 A-Z (around 65 GB): http://fr2.rpmfind.net/linux/RPM/mandriva/2010.0/x86_64/ByName.html
extended shutdown: kshutdown (poweroff, newstart, deep sleep, suspend, lock screen, extras immediately or scheduled)
24h-live-support for inpredictable long time out of internet, fr2.rpmfind.net and Linux-newsgroups
not runnning (buggish) programs: kompozer (a complex web-authoring-sytem for developing websites like typo3, that might be hard to resign from, take applications like nvu instead or: kompozer is always able to start by up- and downgrading through rpm -U --force kompozer-xxx.rpm the kompozer-rpm out of mdv2010.0, mdv2010.1 and mdv2012.0 and copying /usr/bin/kompozer to /usr/lib64/kompozer and /usr/lib64/kompozer/libxpcom* to /usr/lib64/ and starting always by /usr/lib64/kompozer/kompozer. That means, that all listed games do run too! Please mail us, if you do not think so!
lacks in securities: kdeinit from kdebase of mdv2010.0 can cause a zombie-process nspluginscan (this got patched on mdv2010.2 and el6).To avoid the Zombie, you have to set access-rights by chmod upon the process (nspluginscan). Do not install the old udev-extras-2009. Our sound driver gave up. Just install udev.
Everything of the listed software run fine, except Vegastrike! If a programm ever does not start, start it manually by typing the name of the executable into a terminal like konsole or xterm: Error-messages together with the named causes do almost appear, so that in most cases a reaction for repair is possible!
Price:3 DVD for 20 €: You can order a copy of the installation-DVD mdv2010.0-final (64-bit-version x86_64, all updates until now) including many listed software (packages) from the more than 65 GB (15 DVD) above and belonging libraries except telephone-books, anonymizing proxy-server by arif, our search-engine, Linfw3, Klean, Mycompanies and Bibliotmaster and the Source-DVD (mdv2010.0) from us free from postage-fee: 3 DVD for 20 €.
Gooken´s lifetime-hardware data sheed
 AUSTest, Gooken checks OK (quit daily use, multiple power on and off, fsck for partitonwise SSD-repair) for year: 2009, 2010, 2011, 2012, 2013, 2014, 2015, 2016, 2017, 2018, 2019, 2020, ... AUSTest, Gooken checks OK (quit daily use, multiple power on and off, fsck for partitonwise SSD-repair) for year: 2009, 2010, 2011, 2012, 2013, 2014, 2015, 2016, 2017, 2018, 2019, 2020, ...
Used platform (hardware)
Good products mustn´t be expensiven
What does a good smartphone cost?, STERN.de, 02.29.2020
https://www.stern.de/digital/technik/einsteiger-smartphone-unter-200-euro-im-vergleich-9156800.html
 German state security offices German state security offices
There are no evidences for the eavessdropping of Huawei, tagesschau.de, 17.02.2020
Die US-Regierung behauptet, das chinesische Unternehmen Huawei könne Spionage in deutschen Mobilfunknetzen betreiben. Deutsche Sicherheitsbehörden sehen nach Recherchen von WDR, NDR und SZ keine Beweise dafür.
https://www.tagesschau.de/investigativ/ndr-wdr/huawai-hintertuer-china-101.html
More than 100 Millionen Samsung-Galaxy-smartphones were delivered with a fatal lack in security, CHIP, 02.24.2022
Forscher haben entdeckt, dass über 100 Millionen Samsung-Galaxy-Modelle mit einer fatalen Sicherheitslücke ausgeliefert wurden. Über diese hätten sich Kriminelle theoretisch Zugriff auf die Smartphones erhaschen können.
Für Links auf dieser Seite zahlt der Händler ggf. eine Provision, z.B. für mit oder grüner Unterstreichung gekennzeichnete. Mehr Infos.
Samsung ist ziemlich geschickt darin, Sicherheitsupdates für sein riesiges Repertoire an Geräten bereitzustellen, oft bevor Google sich darum kümmert. Viele der in den letzten Jahren verkauften Samsung-Smartphones wurden jedoch mit einer peinlichen Sicherheitslücke ausgeliefert, durch die Hacker vertrauliche Informationen von den Geräten abgreifen konnten.
Forscher der Universität Tel Aviv in Israel fanden heraus, dass bei mehreren Modellen der Modelle Galaxy S8, Galaxy S9, Galaxy S10, Galaxy S20 und Galaxy S21 die kryptografischen Schlüssel nicht ordnungsgemäß gespeichert wurden, was es Hackern ermöglichte, die gespeicherten Informationen zu extrahieren, darunter auch sensible Daten wie Passwörter.
Samsung-Sicherheitslücke: Nutzer älterer Android-Versionen sollten updaten
https://www.chip.de/news/Samsung-Galaxy-Sicherheitsluecke-bei-ueber-100-Millionen-Smartphones_184118526.html
 Annual balance: First annual balance past the bann: Huawei is making a great plus inspite of Trump, STERN.de, 31.03.2020 Annual balance: First annual balance past the bann: Huawei is making a great plus inspite of Trump, STERN.de, 31.03.2020
Huawei war auf dem Weg zum größten Smartphone-Herstellers der Welt. Dann kam der Trump-Bann. Doch welchen Effekt haben die Einschränkungen wirklich? In seiner gerade veröffentlichten Jahresbilanz spricht der Konzern Tacheles - und überrascht mit einem soliden Wachstum.
https://www.stern.de/digital/online/huaweis-jahresbilanz--so-stark-ist-die-auswirkung-des-trump-banns-wirklich-9205658.html
Serious hard reproofs for lacks in security against Huawei and Xiaomi: Now the BSI interferes, CHIP, 03.10.2021
The best selled smartphone-brands of Europe
Sind Huawei- und Xiaomi-Smartphones von Sicherheitsmängeln geplagt? Das geht zumindest aus der Untersuchung des Verteidigungsministeriums Litauen hervor, die nun vor den beliebten Geräten warnen.
https://www.chip.de/news/Huawei-Xiaomi-in-der-Kritik_183828568.html
German security authorities
No evidence for spying by Huawei, tagesschau.de, 17.02.2020
Die US-Regierung behauptet, das chinesische Unternehmen Huawei könne Spionage in deutschen Mobilfunknetzen betreiben. Deutsche Sicherheitsbehörden sehen nach Recherchen von WDR, NDR und SZ keine Beweise dafür.
https://www.tagesschau.de/investigativ/ndr-wdr/huawai-hintertuer-china-101.html
 Against security qualms Against security qualms
Briten particpate Huawei for the 5G-net, tagesschau.de, 28.01.2020
Großbritannien lässt den chinesischen Konzern Huawei in seine 5G-Netze. Kritische Kernbereiche bleiben für den Ausrüster aber tabu. In Deutschland schwelt der Streit um das Unternehmen weiter, dem Spionage vorgeworfen wird.
https://www.tagesschau.de/ausland/grossbritannien-huawei-5g-101.html
 No misgivings against Huawei, tagesschau.de, 14.12.2018 No misgivings against Huawei, tagesschau.de, 14.12.2018
Mehrere Staaten schließen wegen Sicherheitsbedenken den chinesischen Konzern Huawei beim Ausbau des 5G-Netzes aus. In Deutschland halten Wirtschaftsminister Altmaier und Experten des Bundes das nicht für notwendig.
https://www.tagesschau.de/inland/huawei-5g-101~_origin-d3606ea9-40fc-409c-8f62-1b72a705e3ec.html
TV-critic "world empire Huawei"
ZDF-Docu shows: True facts behind the US-quarrel against Huawei, STERN.de, 08.18.2020
Wie gefährlich ist Huawei wirklich? Diese Frage beschäftigt die europäischen Staaten in Bezug auf den 5G-Ausbau. Eine Doku des ZDFs zeigt nun eindrücklich, warum sie kaum zu beantworten ist - und für die USA ohnehin fast keine Rolle spielt.
Huawei war auf dem besten Weg, die Technologiewelt zu erobern. Der Konzern schielte auf den Smartphone-Thron, war bereit, die Welt mit seinem fortschrittlichen 5G-Netzwerk zu umspannen. Doch dann wurde der Konzern zum Spielball im Handelskrieg zwischen den USA und China. Mit Spionagevorwürfen und Handelsembargos vermiest die Trump-Regierung dem Konzern das Geschäft, bald könnten selbst die Smartphone-Chips ausgehen. Die ZDF-Doku "Weltmacht Huawei - Hightech-Riese unter Spionageverdacht" versucht nun, der Frage nachzugehen, was an den Vorwürfen dran ist. Und zeigt dabei, dass es eigentlich um etwas ganz anderes geht.
 [...] Huawei dreht den Spieß indes um: Die eigenen Smartphones seien vielleicht zu sicher, erklärt eine Sprecherin des Unternehmens. "Die USA können dann nicht mehr die eigene Bevölkerung und die anderer Länder ausspionieren." [...] Huawei dreht den Spieß indes um: Die eigenen Smartphones seien vielleicht zu sicher, erklärt eine Sprecherin des Unternehmens. "Die USA können dann nicht mehr die eigene Bevölkerung und die anderer Länder ausspionieren."
https://www.stern.de/digital/online/weltmacht-huawei--zdf-doku-zeigt--was-hinter-dem-us-konflikt-steckt-9378108.html
 As heart, one´s hand can get terrible damned cold for Smartphones ... ... ( even if thinking of the elder ones... ), as Smartphones can suddenly get sensible hot too As heart, one´s hand can get terrible damned cold for Smartphones ... ... ( even if thinking of the elder ones... ), as Smartphones can suddenly get sensible hot too
 The most dangerous technolgy ever invented - part II, Artur Firstenberg @ uncut-news.ch, 10.31.2021 The most dangerous technolgy ever invented - part II, Artur Firstenberg @ uncut-news.ch, 10.31.2021
[...] Die größte Lüge ist, dass; es sich hierbei um "stromsparende" Geräte handelt, und daß sie deshalb sicher sind. Das ist eine doppelte Lüge. Es ist eine Lüge, weil sie nicht stromsparend sind. Wenn Sie ein Mobiltelefon - egal welches - in der Hand oder an Ihren Körper halten, werden Sie von Ihrem Telefon mit mehr Mikrowellen bestrahlt als von jedem Mobilfunkmast und mit zehn Milliarden Mal mehr als von der Sonne, der Milchstraße oder anderen natürlichen Quellen. Die von der Federal Communications Commission* festgelegten Expositionsrichtlinien spiegeln diese Realität wider: Mobilfunkmasten dürfen Ihren Körper mit einer festgelegten Absorptionsrate von 0,08 Watt pro Kilogramm belasten, während Mobiltelefone Ihr Gehirn mit einer spezifischen Absorptionsrate von 1,6 Watt pro Kilogramm belasten dürfen, was dem Zwanzigfachen dessen entspricht.
https://uncutnews.ch/die-gefaehrlichste-technologie-die-jemals-erfunden-wurde-teil-ii/
 The 5G-war - Technique against humanity, Dr. Mercola, uncut-news.ch, 08.12.2022 The 5G-war - Technique against humanity, Dr. Mercola, uncut-news.ch, 08.12.2022
Mercola.com
5G basiert hauptsächlich auf der Bandbreite der Millimeterwelle, die bekanntermaßen ein schmerzhaftes Brennen verursacht. Sie wurde auch mit Augen- und Herzproblemen, unterdrückter Immunfunktion, genetischen Schäden und Fruchtbarkeitsproblemen in Verbindung gebracht.
Die FCC gibt zu, dass keine 5G-Sicherheitsstudien von der Behörde oder der Telekommunikationsindustrie durchgeführt oder finanziert wurden und dass auch keine geplant sind.
Die FCC wurde von der Telekommunikationsindustrie gekapert, die ihrerseits die Desinformationsstrategien perfektioniert hat, die vor ihr von der Tabakindustrie eingesetzt wurden
Anhaltende Exposition gegenüber Mikrowellenfrequenzen wie denen von Mobiltelefonen kann zu mitochondrialer Dysfunktion und Schäden an der Kern-DNA durch freie Radikale führen, die aus Peroxynitrit entstehen.
Eine übermäßige Exposition gegenüber Mobiltelefonen und Wi-Fi-Netzwerken wurde mit chronischen Krankheiten wie Herzrhythmusstörungen, Angstzuständen, Depressionen, Autismus, Alzheimer und Unfruchtbarkeit in Verbindung gebracht.
Die Exposition gegenüber elektromagnetischen Feldern (EMF) und hochfrequenter Strahlung (RF) stellt in der modernen Welt ein ständig wachsendes Gesundheitsrisiko dar. Die Website der Cellular Phone Task Force1 enthält eine lange Liste von Regierungen und Organisationen, die seit 1993 Warnungen ausgesprochen oder drahtlose Technologien verschiedener Art und unter verschiedenen Umständen verboten haben.
Eine weitere lange Liste von Organisationen, die Ärzte und Wissenschaftler vertreten, ist ebenfalls darunter, einschließlich eines Appells zum Schutz vor nichtionisierender EMF-Exposition von mehr als 230 internationalen EMF-Wissenschaftlern an die Vereinten Nationen im Jahr 2015, in dem Folgendes festgestellt wird:
Zahlreiche neuere wissenschaftliche Veröffentlichungen haben gezeigt, dass EMF lebende Organismen in einem Ausmaß beeinflussen, das weit unter den meisten internationalen und nationalen Richtlinien liegt.
Zu den Auswirkungen gehören ein erhöhtes Krebsrisiko, zellulärer Stress, eine Zunahme schädlicher freier Radikale, genetische Schäden, strukturelle und funktionelle Veränderungen des Fortpflanzungssystems, Lern- und Gedächtnisdefizite, neurologische Störungen und negative Auswirkungen auf das allgemeine Wohlbefinden des Menschen. Die Schäden gehen weit über die menschliche Rasse hinaus, da es immer mehr Beweise für schädliche Auswirkungen auf die Pflanzen- und Tierwelt gibt.
Im September 2017 riefen mehr als 180 Wissenschaftler und Ärzte aus 35 Ländern zu einem Moratorium für 5G auf, bis die potenziellen Gefahren für die menschliche Gesundheit und die Umwelt von Wissenschaftlern, die von der Industrie unabhängig sind, vollständig untersucht worden sind, wobei sie feststellten, dass "Hochfrequenz-EMF nachweislich schädlich für Mensch und Umwelt sind" und dass "5G die Exposition gegenüber hochfrequenten elektromagnetischen Feldern (RF-EMF) zusätzlich zu den bereits bestehenden 2G-, 3G-, 4G-, Wi-Fi- usw. Telekommunikationsnetzen erheblich erhöhen wird.
Origin: The 5G War — Technology Versus Humanity
https://uncutnews.ch/der-5g-krieg-technik-gegen-menschlichkeit/
Still functioning today: The security of Xiaomi Poco m5 with operating system MIUI 13 (that can be upgraded to MIUI 14) and Android 12 got certified by RWTÜV Rheinland and other ones.
 Smartphone Xiaomi Poco m6 Pro with XiaomiHyperOS and Android 14, Xiaomi Poco m5 with Betriebssystem Android 12 and MIUI 13 (an upgrade to MIUI 14 possible: The security was assigned by its security app version 9.3.1. Smartphone Xiaomi Poco m6 Pro with XiaomiHyperOS and Android 14, Xiaomi Poco m5 with Betriebssystem Android 12 and MIUI 13 (an upgrade to MIUI 14 possible: The security was assigned by its security app version 9.3.1.
 ATTENTION PLEASE ! NOTICE: Poco m5: (bislang, 04.11.2025) restricted (incomplete) backup only by MIUI Backup ATTENTION PLEASE ! NOTICE: Poco m5: (bislang, 04.11.2025) restricted (incomplete) backup only by MIUI Backup
Poco m6 Pro: complete backup by MIUI Backup
One important difference between these two Poco m-Serie is the completeness of MIUI Backup working in sytem settings. Even if it got actualized, it will NOT do its work complete on Poco m5, where only system-apps got backuped, whereas
for Poco m6 Pro a complete (!) backup of ALL (!) data (system apps, settings, user apps) from Smartphone is possible!
CE
FCC
SAR (limited radiation)
Certificates for Poco m5 and Poco m6 Pro:
U.S.: FCC ID: 2AFZZ19CG
Singapore: complies to IMDA Standards DA106775
Malaysia: MCMC, CIDF 15000056
Russia: EAC
Phillipines: NTC Type Approved No.: ESD-GEC-2207588
Mexico: NOM, NYCE
Costa Rica: sutel 00097-2022
Kingdom of Saudi Arabia: citc TA 2022-1908
Security (both phones) up from version 9.3.1:
ioXt
 TTL 5 stars TTL 5 stars
 RWTÜV Rheinland ® Precisely Right RWTÜV Rheinland ® Precisely Right
 BSI ISO/IEC 27701 Privacy Information Management BSI ISO/IEC 27701 Privacy Information Management
 BSI ISO/IEC 27018 Personal Data in the Cloud BSI ISO/IEC 27018 Personal Data in the Cloud
 BSI ISO/IEC 27001 Information Security Managemant BSI ISO/IEC 27001 Information Security Managemant
 BSI ISO Blaulicht-Filter (nur Poco m6 Pro) BSI ISO Blaulicht-Filter (nur Poco m6 Pro)
 this also for the possibility to change the for apps same Unifier-ID to different Virtual-ID. this also for the possibility to change the for apps same Unifier-ID to different Virtual-ID.
Xiaomi Poco m6 Pro:
Xioami HyperOS (successor of MIUI 14), Android 14, ARM Octacore Max 2,2 GHz (ARM-abi64v8a), 8,0 + 8,0 GB RAM, 256 GB internal storage
TFT-Bluelight filter, certified by RWTÜV Rheinland
Price: about 170 Euro (12/2024)
Xiaomi Poco m5:
MIUI 13 (Upgrade to MIUI 14 possible), Android 12, ARM Octacore Max 2,2 GHz (ARM-abi64v8a), 128 GB internal storage
Price: about 70 Euro (12/2024)
 Xiaomi-Smartphone-Test, testberichte.org, 23.08.2023 Xiaomi-Smartphone-Test, testberichte.org, 23.08.2023
The Price-quality-ration is OK. The best tested Xiaomi handies score with a gook camera, a light and colorful OLED-Display, long akku runtimet and up-to-date ...
https://www.testberichte.de/telekommunikation/handys/xiaomi
 USB-port (USB 2.0), Mirco-USB, USB-cable, akku and akku-charger (net-adapter) (the akku can get improved by exchange.., details see below) USB-port (USB 2.0), Mirco-USB, USB-cable, akku and akku-charger (net-adapter) (the akku can get improved by exchange.., details see below)
 Mount into "Universal Linux" (C6 (el6) and other distros): kdeconnect-cli out of rpm kde-connect (el7) and kdeconnect-libs (el7) Mount into "Universal Linux" (C6 (el6) and other distros): kdeconnect-cli out of rpm kde-connect (el7) and kdeconnect-libs (el7)
1000% secure (past doing the following including the deinstallation of all Google- and BankingApps)
 Radiation: 45 yF Radiation: 45 yF
Just follow our green hooks: We get the Smartphone secure as much as the computer!
 faq faq
Longer updates and spare parts
What the new EU-rules do provide for mobile devices, tagesschau.de, 06.20.2025
In the EU new smartphones must be able getting repaired by oneself the easy way.
https://www.tagesschau.de/wirtschaft/verbraucher/reparatur-smartphones-label-102.html
https://www.tagesschau.de/wirtschaft/verbraucher/recycling-100.html
https://www.tagesschau.de/ausland/europa/eu-recht-auf-reparatur-102.html
https://www.tagesschau.de/wirtschaft/verbraucher/reparatur-haushaltsgeraetegewaehrleistung-100.html
 Running costs: none (if you use the WLAN-Router at home or hotspots for internet access being outside and WhatsApp resp. Facebook Lite for all telephony) (none costs / all for free except costs for power-recharging the akku only) Running costs: none (if you use the WLAN-Router at home or hotspots for internet access being outside and WhatsApp resp. Facebook Lite for all telephony) (none costs / all for free except costs for power-recharging the akku only)
 Attention: Never contract internet spontanously in the mobile shop - the reason, PC-WELT, 06.27.2021 Attention: Never contract internet spontanously in the mobile shop - the reason, PC-WELT, 06.27.2021
Consumer protectors warn against subdrawing contracts for provider of internet- or mobile phone in a shop. The reason.
https://www.pcwelt.de/news/Warnung-Internet-Vertraege-nie-spontan-im-Shop-abschliessen-der-Grund-11051429.html
 Data protection of O2: The one who does not ask, wins, netzpolitik.org, 07.26.2021 Data protection of O2: The one who does not ask, wins, netzpolitik.org, 07.26.2021
https://netzpolitik.org/2021/datenschutz-bei-o2-einwilligungen-dsgvo-wer-nicht-fragt-gewinnt/
 Unwanted agreements Unwanted agreements
Howto change your data settings for more privacy at Telekom, Vodafone and o2, netzpolitik.org, 05.08.2021
https://netzpolitik.org/2021/ungewollte-dsgvo-einwilligungen-so-aenderst-du-deine-datenschutzeinstellungen-bei-telekom-vodafone-und-o2/
Disadvantage (and for lack of radiation a significant advantage too): Smartphone Huawei Y360-U61 has got a weak radio reception. Connections are only build up (established) nearest big LTE-antennas, hotspots and, what is for free, through WLAN of a router!
 Warning against high Telefonica-tarifs for example! Warning against high Telefonica-tarifs for example!
19.000 Euro for 1 GB only: Handy-Provider asks somebody to pay on the base of old contracts, PC-WELT.de, 07.20.2021
Hochgerechnet 19.000 Euro für 1 GB Datenvolumen berechnet ein deutscher Handy-Provider seinem Kunden. Der aktuelle Fall eines Rechtsanwalts.
Rechtsanwalt Peter Nagel berichtet auf seinem Twitterkanal über das dreiste Vorgehen eines deutschen Mobilfunkunternehmens. Demnach kassierte der Mobilfunkprovider von seinem Kunden 23,47 Euro pro 1470 Kilobyte Datenvolumen. Sie haben richtig gelesen: 1470 Kilobyte, nicht Gigabyte! Umgerechnet auf 1 GB kommt man auf rund 15.966 Euro, zuzüglich 19 Prozent Mehrwertsteuer also auf ziemlich genau 19.000 Euro für 1 GB Datenvolumen.
Notiz an mich: Deutscher Mobilfunkanbieter bewirtschaftet Altvertrag mit 19 EUR je MB gegenüber Rentner. Das wären 19.000 EUR je GB. Diese Praxis liegt ca. 1.000.000% über Marktpreis. Hotline verteidigt das Vorgehen.
https://www.pcwelt.de/news/19.000-Euro-fuer-1-GB-Handy-Provider-kassiert-bei-Altvertrag-ab-11064901.html
Data protection offense in Europe
Vodafone conituously proceedst punishments, netzpolitik.org, 11.16.2021
So langsam wird die Sache teuer: Wegen anhaltender Datenschutzbeschwerden hagelt es in mehreren Ländern Bußgelder für Vodafone. Mehr als 9,5 Millionen Euro verlangen europäische Aufsichtsbehörden von dem Mobilfunkanbieter allein in diesem Jahr, auch der deutsche Bundesdatenschutzbeauftragte prüft gravierende Vorwürfe.
https://netzpolitik.org/2021/datenschutzverstoesse-in-europa-vodafone-kassiert-strafen-am-laufenden-band/
Is the mobile net secure against blackouts?, uncut-news.ch, 10.20.2021
Helwin Lesch, der Leiter für Planung und Technik des Bayrischen Rundfunks, prangert in einem Interview die Mobilfunkbetreiber an. Laut Lesch sind Mobilfunkmasten nicht ausreichend gegen einen Stromausfall gesichert.
Es sind "keine Reserven da. Da sind ein paar Kondensatoren, die noch eine Weile, ein paar Minuten vielleicht, das Ding am Leben halten". Mit diesen Worten beschreibt Lesch die Stromversorgung des Mobilfunks. Außerdem erklärt er: "Wenn man darüber hinaus Katastrophensicherheit haben will, dann muss man nicht nur auf die Lage des Standorts achten, dass er keine nassen Füße kriegt, sondern eben auch, dass er von der Stromversorgung unabhängig weiterarbeiten kann."
Wie sicher ist das Mobilfunknetz bei einem Stromausfall? Wie gut ist unser Mobilfunknetz ...
https://blackout-news.de/informationen-zum-blackout/ist-das-mobilfunknetz-bei-stromausfall-gesichert
 Warning for Android-user: These popular Apps do sell your data, CHIP, 02.21.2022 Warning for Android-user: These popular Apps do sell your data, CHIP, 02.21.2022
Eine Reihe von Android-Apps, die sensible Daten der Nutzer weiterverkauft haben, wurde in einer Studie enthüllt. Es geht dabei in erster Linie um Selfie-Anwendungen.
Für Links auf dieser Seite zahlt der Händler ggf. eine Provision, z.B. für mit oder grüner Unterstreichung gekennzeichnete. Mehr Infos.
Selfie-Apps sind gerade bei jüngeren Smartphone-Nutzern ein beliebtes Hilfsmittel, um Fotos mit witzigen Effekten wie Make-Up, Tierohren und wilden Frisuren auszuschmücken. Wie eine aktuelle Studie von "mobilsicher.de" allerdings nun aufzeigt, verkaufen die Apps die erhobenen biometrischen Daten auch an Dritte, ohne dass dies den Usern voraussichtlich bewusst ist.
Insgesamt sechs der beliebtesten Apps im Google Play Store, die zusammen über 500 Millionen Mal heruntergeladen wurden, hat das Portal dabei auf Herz und Nieren überprüft. Dabei handelt es sich um:
Photo Lab Bildbearbeitung (100 Mio.+ Downloads)
YouCam MakeUp: Selfiekamera (100 Mio.+ Downloads)
BeautyPlus-Foto, Retusch, Filter (100 Mio.+ Downloads)
FaceApp: Gesichtsbearbeitung (100 Mio.+ Downloads)
Perfect 365: Gesichts-Make-Up (50 Mio.+ Downloads)
Facetune2 (50 Mio. + Downloads)
https://www.chip.de/news/Android-Nutzer-von-Datenleck-bei-beliebten-Apps-betroffen_184107368.html
 Practical locking-service for the Smartphone: Howto protect yourself from horrible subscibing-(ABO)-traps, CHIP, 03.21.2022 Practical locking-service for the Smartphone: Howto protect yourself from horrible subscibing-(ABO)-traps, CHIP, 03.21.2022
Unerwünschte Werbung auf dem Smartphone ist keine Seltenheit. Klickt man falsch, holt man sich schnell ein kostspieliges Abo ein, das die Handyrechnung in die Höhe treibt. Verbraucher können sich aber wehren; zum Beispiel über einen Sperr-Service, den Telekom, Vodafone, O2 und Co. standardmäßig anbieten.
Für Links auf dieser Seite zahlt der Händler ggf. eine Provision, z.B. für mit oder grüner Unterstreichung gekennzeichnete. Mehr Infos.
Nach geltendem Recht wird in Deutschland ein Vertrag erst wirksam, wenn man sich per Klick ausdrücklich zur Zahlung verpflichtet. Der Button muss dabei explizit mit "zahlungspflichtig bestellen" oder einer vergleichbaren eindeutigen Formulierung (z.B. "jetzt kaufen") beschriftet sein.
Doch nicht alle halten sich daran. Und so passiert es immer wieder, dass Nutzer unwissentlich ein Abo abschließen, das sie viel Geld kosten kann. Denn ein falscher Klick kann bereits ausreichen, um in der Abofalle zu landen.
Um Verbraucher zu schützen, hat die Bundesnetzagentur den Mobilfunkanbietern besondere Verpflichtungen auferlegt. Zusätzlich können Sie auch selbst Maßnahmen ergreifen, um sich noch besser vor Abzocke über das Handy zu schützen.
https://www.chip.de/news/Praktischer-Sperr-Service-auf-dem-Smartphone-So-schuetzen-Sie-sich-ganz-einfach-vor-fiesen-Abofallen_184175050.html
 Version 100.0.4896.75 Version 100.0.4896.75
Already again there is a new update for Google Chrome, trojaner-info.de, 04.08.2022
Die neueste Version von Google Chrome schließt eine Sicherheitslücke in der JavaScript-Engine V8.
Erst kürzlich ist die Jubiläumsversion des Chrome-Browsers herausgekommen. Jetzt steht Version 100.0.4896.75 steht für Linux, Mac und Windows bereit und soll automatisch im Laufe der kommenden Tage und Wochen verteilt werden. Abermals wird eine Lücke in JavaScript-Engine V8 geschlossen. Das Risiko wurde durch Google als hoch eingestuft.
Die zu schließende Sicherheitslücke ist vom Typ "Type Confusion" (CVE-2022-1232, Risiko hoch). Die Lücke wurde vom Mitarbeiter Sergei Glazunov von Googles Project Zero gemeldet.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/schon-wieder-neues-update-fuer-google-chrome.html
 Hotspot-Fans attention please: In an opened WLAN-net, even if encrypted, notihng is private anymore — so be careful! Hotspot-Fans attention please: In an opened WLAN-net, even if encrypted, notihng is private anymore — so be careful!
WLAN and Hotspots in Germany, Israel and elsewhere, trojaner-info.de, 04.08.2022
Deutschland verfügt über eine geringere Dichte an öffentlichen WLAN-Zugangspunkten als andernorts, dafür sind die Hotspots hierzulande deutlich sicherer
Das mobile Kommunikationsnetz wächst. Auch außerhalb der eigenen Wände gibt es immer mehr öffentliche Räume, die den Zugang zum Word Wide Web bieten: WLAN Hotspots am Flughafen, am Bahnhof, im Café oder beim Italiener um die Ecke. Hotspot-Fans aufgepasst: In einem offenen WLAN-Netz, selbst wenn es verschlüsselt sein sollte, ist nichts mehr privat — Vorsicht ist angebracht.
Insbesondere im Ausland, wo es statistisch gesehen mehr unsichere, unverschlüsselte Zugänge gibt, ist die Versuchung groß, sich mal schnell in das offene mobile Drahtlos-Netzwerk einzuloggen. Pfiffige Hacker sind in der Lage, die verschlüsselten Hotspots zu erobern und mit wenigen Kniffen auf die persönlichen Daten zuzugreifen und diese zu missbrauchen.
https://www.trojaner-info.de/vorsicht-wlan/articles/wlan-und-hotspots-in-deutschland.html
 Android-Patchday in April, Google solves security relevant errors on Patchday: closing 44 security exploits in Android, trojaner-info.de, 04.07.2022 Android-Patchday in April, Google solves security relevant errors on Patchday: closing 44 security exploits in Android, trojaner-info.de, 04.07.2022
Beim April-Patchday kommt Google in diesem Jahr auf insgesamt 44 Sicherheitspatches. Diese Sicherheitslecks erlaubten es Angreifern, ihre Rechte im System auszuweiten. Und das, ohne dass es dabei zu Anfragen beim Benutzer kam oder eine Interaktion von Nöten war.
Die Updates wurden wie üblich in zwei Teile unterteilt: Updates mit dem Stand 2022-04-01 betreffen das Android-System selbst. Fehlerbehebungen für den Unterbau, wie etwas Herstellerspezifische Sicherheitsupdates laufen unter dem Patch-Level 2022-04-05.
Sieben Updates des Patch-Levels 2022-04-01 betreffen das Android Framework, drei das System und zwei das Media-Framework. Google stuft jedes einzelne als hohes Risiko ein. Zwei Google Play System-Updates flankieren diese. Sie sollen die Schwachstellen in MediaProvider und den Media-Codecs abdichten.
Updates zum Patch-Level 2022-04-05 betreffen eine Schwachstelle im System und vier in den Kernel-Komponenten. Sie werden ebenfalls von Google mit dem Bedrohungsgrad hohes Risiko eingestuft. Sicherheitsrelevante Fehler im A-GPS sowie im LTE-Modem werden für MediaTek-SoCs durch zwei Aktualisierungen behoben. Qualcomm-Systeme hingegen bekommen ganze 22 Flicken. Von denen stuft Qualcomm selbst neun Lücken als kritisch und 14 mit einem hohen Risiko für Nutzer ein.
Quelle: heise online Redaktion
https://www.trojaner-info.de/mobile-security/aktuell/android-patchday-im-april.html
 Hightech-giant under espionage-suspicion (People Republic China, 2020), zdf-info, 17.09.2021, 22:45 Uhr Hightech-giant under espionage-suspicion (People Republic China, 2020), zdf-info, 17.09.2021, 22:45 Uhr
Der Telekommunikationsriese Huawei gilt als eines der mächtigsten Unternehmen Chinas. Doch immer mehr Länder zweifeln an dessen Unabhängigkeit. Der Vorwurf: systematische Spionage. Der Konzern verfügt über den technologischen Vorsprung, um das schnelle 5G-Netz weltweit auszubauen. Die USA - aber auch weitere westliche Staaten - fürchten, Huawei eröffne der chinesischen Regierung durch Hintertüren Spionage- und Sabotagemöglichkeiten.
Sind die Sorgen um Netzsicherheit berechtigt, oder ist der Huawei-Konzern nur eine Spielfigur im Handelskrieg zwischen den USA und China? Die Festnahme der Huawei-Finanzchefin Meng Wanzhou, Tochter des Firmengründers, erfolgte 2018 in Kanada und markierte einen Höhepunkt des Konflikts zwischen dem Unternehmen und den USA. Auch in Europa gibt es Vorbehalte gegen den chinesischen Technologieriesen. Der Film geht auf Spurensuche: Wie eng ist Huawei mit der chinesischen Regierung verknüpft, und welche Risiken und Chancen bietet eine Zusammenarbeit mit dem 5G-Riesen?
https://www.tvinfo.de/fernsehprogramm/1409351292-weltmacht-huawei
Huawei: HarmonyOS will be released in June 2021, PC-WELT, 05.26.2021
Huawei will HarmonyOS am 2. Juni 2021 im Rahmen eines Launch-Events veröffentlichen.
https://www.pcwelt.de/news/Huawei-HarmonyOS-erscheint-im-Juni-11034747.html
Bei 80 Prozent der untersuchten Apps, die angeblich keine Daten erfassen, findet doch Tracking statt
Apple-Datenschutzlabels
Großteil angeblich trackingfreier iOS-Apps sammelt heimlich Daten, netzpolitik.org, 20.01.2022
Apps auf dem iPhone tragen leicht verständliche Labels, die zeigen sollen, auf welche Daten sie zugreifen. Doch bei 80 Prozent der untersuchten Apps, die angeblich keine Daten erfassen, findet doch Tracking statt. Das zeigt eine Analyse des Informatikers Konrad Kollnig für netzpolitik.org.
Eine klare Ansage schmückt viele Angebote in Apples App-Store: "Keine Daten erfasst". Seit einem Jahr sind für Apps in Apples Betriebssystem iOS klare Datenschutzlabels verpflichtend. Sie sollen zeigen, ob und welche Daten die App an ihre Betreiber:innen oder Dritte weitergibt.
Viele Apps behaupten, keine Daten von Nutzer:innen zu sammeln. Doch zahlreiche Labels sind offenkundig falsch - das zeigt eine technische Auswertung, die netzpolitik.org exklusiv einsehen konnte. Der Informatiker Konrad Kollnig von der Universität Oxford hat 1,682 zufällig ausgewählte Apps aus Apples App-Store untersucht. 373 der getesteten Apps (22,2 Prozent) geben an, keine persönlichen Daten zu erfassen. Vier Fünftel davon, 299 Apps, kontaktierten jedoch sofort nach dem ersten App-Start und ohne jegliche Einwilligung bekannte Tracking-Domains. (Hier mehr Details über die Methode, eine Veröffentlichung der Daten soll bald folgen.)
Eine prominente App aus Kollnigs Datensatz: "RT News" des russischen Staatssenders. Die App gibt an, keine Daten zu erfassen. Kollnig machte die Probe aufs Exempel, er lud sie auf sein Testgerät und steuerte ein paar beliebige Artikel an. Insgesamt schickte die RT-App an 19 Domains Daten weiter. Allerdings nicht nach Russland, sondern an Trackingdienste der US-Konzerne Facebook und Google, die Marktforschungsfirma ComScore und den Werbekonzern Taboola.
Eigentlich müsste eine solche Datensammlung im Datenschutzlabel angegeben werden, sagt Kollnig. Denn darin könnten sensible Informationen stecken, etwa über die Artikel, die sich Nutzer:innen in der App angesehen hätten. "Leider ist häufig unklar, welche Daten wirklich gesammelt werden und was mit diesen Daten geschieht."
Besondere Vorsicht sei bei Apps geboten, die Zugriff auf den GPS-Standort haben, sagt der Informatiker. Wie Recherchen der New York Times gezeigt hätten, landen solche Standortdaten oft in den Händen von Datenfirmen, die sie zum Verkauf anbieten - ein klarer Fall von Missbrauch.
Wie viel an Tracking durch Apps passiert, untersuchen Kollnig, ein Doktorand am Informatikinstitut der Universität Oxford, und seine Kolleg*innen seit längerer Zeit. Zuletzt veröffentlichten sie eine Analyse von fast zwei Millionen Android-Apps im renommierten Journal Internet Policy Review. Ihre Ergebnisse sprechen Bände: Seit Wirksamkeit der Datenschutzgrundverordnung mit Mai 2018 habe sich wenig an der Lage verändert, rund 90 Prozent der Apps in Googles Play Store können demnach direkt nach dem Start Trackingdaten an Dritte schicken.
Für seine Analyse der iOS-Apps wählte Kollnig nach dem Zufallsprinzip Apps aus, die seit Januar 2020 in Apples Appstore zu finden sind und nachträglich ein Datenschutzlabel erhalten haben. Der Informatiker installierte die Apps automatisiert auf ein iPhone 8 mit dem aktuellen Betriebssystem iOS 15.2. Dort wurde jede App geöffnet, sonst fand aber keine Interaktion mit den Apps statt - auch keine Einwilligung zum Tracken. Anschließend untersuchte Kollnig den Datenverkehr zwischen dem Handy und dem Internet durch einen zwischengeschaltenen Rechner, einen sogenannten Man-in-the-middle-Proxy. Einige Apps installierte er zusätzlich zu Testzwecken manuell.
Apples Datenschutzlabels ernten Kritik
Grundsätzlich setzt Apple beim Datenschutz höhere Maßstäbe als andere Unternehmen, verkauft teilweise Produkte nach dem Konzept Privacy-by-Design. Doch Datenschutz und Privatsphäre sind auch Teil von Image und Marketing des Unternehmens, mit denen Konzernchef Tim Cook bei großen europäischen Datenschutzkonferenzen die Halle füllt.
Im Dezember 2020 führte Apple die Datenschutzlabels in seinem Store ein, "damit du besser verstehst, wie Apps deine Daten verarbeiten." Apple musste sich aber bereits seit Beginn Kritik an den Labels gefallen lassen. Mehr als ein dutzend falscher Behauptungen in App-Labels fand Washington-Post-Kolumnist Geoffrey A. Fowler im Januar 2021, darunter auch bei einer für Kinder gemachten Video-App und einem beliebten Spiel. Im Kleingedruckten der Labels sei zu lesen, dass Apple die Informationen der Anbieterfirmen gar nicht prüfe - die Angaben würden nur in vereinzelten Stichproben kontrolliert. Gleichlautende Vorwürfe erntet Apple auch später.
Ein Jahr später bleibt die Situation ähnlich: Kollnig fand in seiner Analyse zahlreiche beliebte Apps, die deutlich mehr Daten sammeln als behauptet. Etwa die Puzzle-App einer großen Spielefirma, die entgegen ihres Labels eine ID-Nummer von Nutzer:innen an zahlreiche Trackingdienste schickt. Oder die App des britische Met Office, des nationalen Wetterdienstes. Diese sendet heikle Informationen wie GPS-Daten an Google und Amazon und sammelt - ohne Ankündigung im Label - auch eine Nutzer:innen-ID.
Apple wollte zu der Analyse Kollnigs auf Anfrage von netzpolitik.org nicht konkret Stellung nehmen. Von dem Konzern hieß es lediglich, dass die Informationen in den Labels von den Entwickler:innen stammten, Apple aber vor allem die beliebtesten Apps im Rahmen seines Review-Prozesses auf die Richtigkeit der Angaben kontrolliere.
Oft wissen App-Betreiber:innen selbst nichts von Tracking
Dass so viele Daten aus beliebten Apps bei Dritten landen, hat aus Sicht des Informatikers Kollnig einen praktischen Grund. Trackingdienste würden üblicherweise über sogenannte Bibliotheken in Apps integriert. Bei Bibliotheken handelt es sich um fertige Unterprogramme, die bestimmte Aufgaben in einer App erledigen. Deren Nutzung erleichtert Programmierer:innen die Arbeit, bedeutet aber weniger Kontrolle über die fertige App. Denn viele Bibliotheken stammen von Konzernen wie Google, und in ihnen ist der Tracking-Code versteckt. "App-Betreiber haben häufig keine Möglichkeit den Programmcode dieser Bibliotheken nachzuvollziehen, da die Trackingunternehmen ihren Code üblicherweise nicht öffentlich machen", sagt Kollnig.
Das Tracking bietet App-Anbieter:innen eine Möglichkeit, durch personalisierte Werbung Geld zu verdienen. "Der Wunsch von App-Betreibern nach finanziellen Einnahmen ist verständlich", sagt der Jungwissenschaftler. Doch das Geschäft gehe zu Lasten der Nutzer:innen, die kaum über die gesammelten Daten Bescheid wüssten. Grund dafür seien auch die großen Tech-Konzerne, die es App-Betreiber:innen erschwerten, auf datenschutzfreundliche Alternativen zu setzen. Damit sich daran etwas ändere, müsste geltendes EU-Datenschutzrecht konsequent in die Praxis umgesetzt werden, sagt Kollnig.
https://netzpolitik.org/2022/apple-datenschutzlabels-grossteil-angeblich-trackingfreier-ios-apps-sammelt-heimlich-daten/
 Innovation of Apple Innovation of Apple
No tracking anymore - what does it mean?, tagesschau.de, 04.28.2021
What does come new with iOS 14.5?
https://www.tagesschau.de/wirtschaft/unternehmen/apple-tracking-faq-101.html
Annual balance: First annual balance past the ban: Huawei profits strongly - inspite of Trump, STERN.de, 03.31.2020
https://www.stern.de/digital/online/huaweis-jahresbilanz--so-stark-ist-die-auswirkung-des-trump-banns-wirklich-9205658.html
Community::Organizations
Huawei joins the Open Invention Network, PRO LINUX, 04.03.2020
The chinese telecommunication outfitter Huawei has joinded the Open Invention Network (OIN)
[...] Since 2001 Huawei has taken in cash around 6 billion US-Dollar with patents, 80 percent from USA. Huawei was the first chinese Smartphone-manufacturer, who really grappled with Linux and Open Source. Huawei is a prime-member of the Linux Foundation and for a long time contributes regulary to the Linux-Kernel.
https://www.pro-linux.de/news/1/27923/huawei-tritt-dem-open-invention-network-bei.html
Good must´nt be expensive
What does a good Newcomer-Smartphone cost?, STERN.de, 29.02.2020
https://www.stern.de/digital/technik/einsteiger-smartphone-unter-200-euro-im-vergleich-9156800.html
German federal net agency: dead zone maps for Germany
... published for Telekom, Vodafone and Telefónica.
https://www.pcwelt.de/news/Bundesnetzagentur-veroeffentlicht-Funkloch-Karte-fuer-Deutschland-10698252.html
SIM-card and its load, our tip (... until we got to know from Alditalk per SMS, that we, although using WLAN of our computer for years, had to pay once again, if the phone number of our spartphone shall not get locked. : Internet-Flat 1 GB ALDITALK Prepaid Starter Kit ( including phone and SMS and so on ) forr
3,99 Euro per month (Aldi, Stand 01.01.2020).
Or for free through WLAN-Router, any hotspot or phone through WhatsApp or messanger Facebook Lite with more than 1 billion "contacts" from all over the world:
Smartphoning totally for free, for 0,00 Euro per month
Notice: The WLAN-connection made be visible in settings, section Wifi, should never be reset to horrible expensive Telefonica etc.!
[SOLVED The akku does not recharge?
This might be a USB-cable-error: Press the USB-connector, in this case Micro-USB, a litte bit with a combination pliers!
Edward Snowden
"Apple has declared war to the privacy", netzpolitik.org, 03.09.2021
Der Whistleblower Edward Snowden kritisiert Apples Pläne, die Telefone seiner Kund:innen zu durchsuchen. Der Konzern radiere Datenschutzgrenzen damit unwiderruflich aus. Snowden prophezeit eine nie dagewesene Massenüberwachung, autoritäre Regime würden Apples Technologie gnadenlos ausnutzen.
https://netzpolitik.org/2021/edward-snowden-apple-hat-der-privatsphaere-den-krieg-erklaert/
 Facebook and advertising industry do shiver and tremble Facebook and advertising industry do shiver and tremble
ad-tracking
Apple turns the tick (checkmark), netzpolitik.org, 08.21.2020
Next iOS-version Apple changes the configuration of its mobile phones at the decisive place: Since the US-company increases the protection for the customers against tacking, Facebook and the ad-industry do shiver and tremble.
https://netzpolitik.org/2020/werbe-tracking-apple-legt-das-haekchen-um/
 What is the flight modus?, CHIP.de, 07.23.2019 What is the flight modus?, CHIP.de, 07.23.2019
Jedes Smartphone hat ihn: den Flugmodus. Was der Flugmodus genau bedeutet ist jedoch nicht ganz offensichtlich. Wir zeigen Ihnen, was der Flugmodus bewirkt und was er mit dem Fliegen zu tun hat. Zudem erfahren Sie, wie sie ihn in iOS und Android aktivieren.
Flugmodus - was ist das? Hier wird es erklärt
Den Flugmodus finden Sie auf zahlreichen elektronischen Geräten, wie zum Beispiel bei Notebooks. Der Flugmodus kommt jedoch hauptsächlich bei Smartphones zum Einsatz.
Öffnen Sie auf Ihrem Smartphone die "Einstellungen", können Sie meist ganz oben den Flugmodus ein- und ausschalten. Bei diesem Vorgang werden alle kabellosen Verbindungen getrennt. Darunter auch WLAN- und Bluetooth-Verbindungen.
Seinen Namen hat der Flugmodus von seinem ursprünglichen Anwendungszweck: In Flugzeugen werden Sie beim Start gebeten Ihr Handy auszuschalten, damit keine Signale gestört werden. Der Flugmodus schaltet alle Signale umgehend ab, das lästige Ausschalten vom Smartphone ist somit nicht notwendig.
Aktivieren Sie den Flugmodus, wird nicht nur die Verbindung zum Mobilfunknetz gekappt, sondern auch WLAN-, Bluetooth- und NFC-Verbindungen. Bei einigen Smartphones (wie Y360-U61) ist es jedoch möglich, WLAN trotz Flugmodus zu nutzen.
https://praxistipps.chip.de/was-ist-der-flugmodus-einfach-erklaert_41402
Insider
Guide: Into the internet through hotspots, PC-WELT.de, 01.10.2020
Am WLAN-Hotspot surfen Sie oft schneller und günstiger als über das Mobilfunknetz. Wir zeigen, was es zu beachten gibt.
https://www.pcwelt.de/ratgeber/Guide-Mit-oeffentlichen-Hotspots-ins-Internet-gehen-10554952.html
 US-mobilphone-provider do sell location data, PC-WELT.de, 05.15.2018 US-mobilphone-provider do sell location data, PC-WELT.de, 05.15.2018
Mobil-provider from USA do obviously sell realtime-location-data of their customers to private companies.
https://www.pcwelt.de/a/us-mobilfunkprovider-verkaufen-ortungsdaten,3450807
 Right to anonymous communication Right to anonymous communication
Process by European court against anonymous Prepaid-SIM-cards failed, netzpolitik.org, 30.01.2020
In einem an diesem Donnerstag veröffentlichten Urteil hat der Europäische Gerichtshof für Menschenrechte das Verbot anonymer Prepaid-SIM-Karten in Deutschland bestätigt. Durch das Sammeln der dabei erhobenen Daten würden keine Rechte verletzt.
https://netzpolitik.org/2020/klage-gegen-verbot-anonymer-prepaid-sim-karten-gescheitert/
 Samsung, Huawei, Xiaomi - while there are only a few updates, Apple protects their user over years, CHIP, 05.17.2021 Samsung, Huawei, Xiaomi - while there are only a few updates, Apple protects their user over years, CHIP, 05.17.2021
https://www.chip.de/news/Samsung-Huawei-Xiaomi-Waehrend-Ihr-mit-Updates-geizt-schuetzt-Apple-Nutzer-ueber-Jahre_183609201.html
Phone worldwide for free: The Satellite App replaces the SIM-card, CHIP, 09.04.2018
With the free App Sipgate Satellite you can phone woldwide without a sim card for 100 free minutes each month into 55 countries - totally free - without any costs.
https://www.chip.de/news/Kostenlos-telefonieren-Satellite-App-statt-SIM-Karte_134263212.html
alternatively: WLAN-Router (for the used costs of the PC-internet- and that means phone-flat, if given), Facebook-Lite and/or WhatsApp and/or App namend "CallFree" (all worldwide free phone, start with 1000 up to 2000 bonus points gratis, point reload by making points by looking video-ad-spots, acquiring more user resp. customers and recommending suggested Apps, info from year 2019)
Allnet-Flats with high download volumes: The best tariffs for your handy, https://www.chip.de/artikel/Handytarife-mit-riesigem-Datenvolumen-Guenstigstes-Angebot-kostet-22-Euro_171925937.html
Do we all get radiated?
Radiation: Class action lawsuit against Apple and Samsung, PC-WELT.de, 08.26.2019
Smartphones geben mehr Strahlung ab, als eigentlich erlaubt. Das berichtete in der vergangenen Woche eine amerikanische Zeitung. Diesem Bericht folgt bereits die erste Sammelklage einer kleinen Kanzlei aus Atlanta.
Die Chicago Tribune hat mehrere Smartphones auf die abgegebene Strahlung hin getestet. Dabei kam die Zeitung zu dem Schluss, dass einige Geräte die festgeschriebenen Grenzwerte nicht einhielten. Wir berichteten.
Über einen Facebook-Post ließ die Anwaltskanzlei Fegan Scott LLC gestern verlauten, eine Sammelklage gegen Apple und Samsung eingereicht zu haben. Sie werfen den Konzernen vor, durch die vermeintlich (die Ergebnisse einer neuen Untersuchung durch die amerikanische Behörde FCC stehen noch aus) erhöhten Strahlenwerte die Gesundheit der Gerätenutzer zu gefährden. Außerdem sei die Werbung zu den Produkten irreführend und spiele die Gefahren von Strahlung, die durch Smartphones abgegeben wird, herunter, ignoriere sie sogar komplett. So wird Apple und Samsung vorgeworfen, mit Slogans wie "Studio in your pocket" zu sugerrieren, dass Smartphones risikofrei in der Hosentasche transportiert werden können.
Die 44-seitige Anklageschrift bezieht sich zu großen Teilen auf den Artikel der Chicago Tribune, aber auch auf verschiedene Studien, welche die Schädlichkeit von Smartphone-Strahlung belegen sollen. Dabei ist diese wissenschaftlich durchaus umstritten. Für mehr Informationen zu diesem Thema empfehlen wir den Gast-Beitrag unseres Experten Dennis Bederov. In diesem Beitrag haben wir die Problematik der SAR-Messungen zusammengefasst und erklärt, warum diese nicht immer aussagekräftig sind.
Sammelklagen gegen große Konzerne und Behörden sind keine Seltenheit. Erst vor wenigen Monaten startete in den USA eine Sammelklage gegen die US-Behörde FCC wegen der Zulassung von 5G-Mobilfunk. Auch in diesem Fall gehört die Gefährdung der Allgemeinheit zu den Vorwürfen, ohne dass diese wissenschaftlich einwandfrei erwiesen ist.
https://www.pcwelt.de/news/Wegen-Strahlung-Sammelklage-gegen-Apple-und-Samsung-eingereicht-10654270.html
Murder in rates - Stoppt 5G and the BRD !, brd-schwindel.ru, 04.19.2019
 Mobiltelephon mit integriertem Abhörmodul Mobiltelephon mit integriertem Abhörmodul
rC3: Handy von Assange-Mitstreiter Müller-Maguhn offenbar von CIA kompromittiert, trojaner-info.de, 29.12.2020
Andy Müller-Maguhn, früherer Sprecher des Chaos Computer Clubs (CCC), hat am Sonntag auf dem remote Chaos Communication Congress (rC3) von massiven Einschüchterungsversuchen durch staatliche Geheimdienste berichtet. Dass die CIA ihm hinterher sei, ist für ihn demnach spätestens offensichtlich geworden, als er nach einer Reparatur entdeckt habe, dass sein verschlüsselt kommunizierendes Mobiltelefon mit einem integrierten Abhörmodul verwanzt worden sei.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/rc3-handy-von-assange-mitstreiter-mueller-maguhn-offenbar-von-cia-kompromittiert.html
Folgende Zitatesammlung zeigt, dass man schon lange über die Gefahren der Mobilfunktelefonie Bescheid weiß und welche Schäden diese im menschlichen Organismus anrichtet, vor allem im Gehirn. Und dabei geht es nicht einmal um 5G. Man kann sich ausrechnen, dass sich die Belastung um einiges potenziert. Wir sind ohne 5G schon enormen Strahlungen ausgesetzt. 5G NEIN DANKE
Die Zitatensammlung stammt aus wissenschaftlichen Arbeiten, Fachveröffentlichungen, Presseagenturmeldungen, Büchern, Vorträgen, Zeitungen, von Ärzten, Ämtern, Experten, dem Internet, den Nachrichten, wurden im Radio gehört, im Fernsehen gesehen…
- "Die Handymasten werden stillgelegt. Es ist größtmögliche Vorsicht geboten."
Aus dem Urteil des Gerichtes von Valladolid/Spanien (Dezember 2001) In Valladolid legte das Gericht sechs Mobilfunkmasten mit 36 Einzelantennen diverser Betreiber in der Nähe einer Schule still. Drei Kinder erkrankten in dieser Schule innerhalb weniger Monate an Leukämie und eines an Lymphdrüsenkrebs. Es wurden außer den Funkwellen keine anderen Risikofaktoren wie z.B. Schadstoffe gefunden. Das erhärte den Verdacht, dass der Funk die Ursache für die Krebsfälle ist. Darauf deute zudem hin, dass es nach der Installation der Funkmasten auch in den umliegenden Wohnhäusern 18 Krebsfälle bei Kindern gibt. Die Funkantennen bleiben trotz aller Proteste der Industrie abgeschaltet und müssen demontiert werden.
- "Die aufgeregte Diskussion in der Bevölkerung über die Kernenergie dürfte in Relation zu dem, was uns die Mobilfunknetze noch bescheren werden, nur ein laues Lüftchen gewesen sein."
-
Bundespostminister Wolfgang Boetsch vor Journalisten in Bonn (5. Februar 1993)
-
"Angesichts der Vielzahl wissenschaftlicher Befunde kann man weder das Krebsrisiko noch verschiedene andere biologische Effekte einfach abtun."
Umweltausschuss des EU-Parlamentes (2000)
-
"Die kritische Sichtung der wissenschaftlichen Literatur lässt keinen Zweifel mehr offen, dass die gepulste Strahlung von Basisstationen, Handys und schnurlosen Haustelefonen wesentlich gesundheitsbeeinflussend und schädlich ist."
Prof. Dr.-Ing. Alexander H. Volger, Honorarprofessor der Rheinisch-Westfälischen Technischen Hochschule RWTH Aachen (14. September 2002)
-
• "Jeder Vierte hat ein geschädigtes Immun-, Nerven- oder Hormonsystem, jeder Dritte ist Allergiker. Wir haben den Punkt erreicht, der keine zusätzlichen Belastungen mehr verträgt."
DGUHT, Deutsche Gesellschaft für Umwelt und Humantoxikologie (1994)
-
"Wir wissen sehr gut, dass gepulste Signale auf den Menschen stärker einwirken als ungepulste. Gepulste Mikrowellen greifen tief in biologische Prozesse ein."
Prof. Dr. Ross Adey, Loma-Linda-Universität, Kalifornien (1970)
- "Gepulste Mikrowellen schädigen das Immunsystem und beeinflussen Neurotransmitterabläufe."
Prof. Dr. Dan Lyle, Loma-Linda-Universität, Kalifornien (1985)
-
"Gepulste Mikrowellen verändern die menschlichen Gehirnströme. Das ist im EEG bei Strahlungsstärken von 1000 μW/m² nach wenigen Minuten nachweisbar."
Dr. Lebrecht von Klitzing, Medizin-Physiker, Medizinische Universität Lübeck (1994) 1000 μW/m² Feldstärke finden wir von der Baubiologie Maes in einer Entfernung von, je nach Situation, etwa 50 bis über 200 Metern zu Mobilfunkstationen auf Masten, Türmen, Dächern, Kaminen, Kirchen, Silos, Hochspannungsleitungen…, 5 bis über 10 Metern zu Handys, wenn mit ihnen telefoniert wird, 3 bis 5 Metern zu den immerzu funkenden Basisstationen der DECT-Schnurlostelefone und 2 bis 3 Metern zu WLAN.
-
"Bei 36 Probanden führte die gepulste Strahlung im Versuchslabor unmittelbar nach dem Einschalten zu Veränderungen im EEG."
Dr. H.P. Reiser, Dr. W. Dimpfel und Dr. F. Schober, Wissenschaftler des Pro-Science-Forschungsinstitutes im Auftrag der Telekom (1995)
-
"Veränderungen im EEG traten nach etwa 15 Minuten Einschaltzeit auf. Im Schlaf-EEG gab es Verkürzungen der REM-Phase."
Prof. Dr. Alexander Borbély, Institut für Toxikologie, Universität Zürich (1999)
-
"Die Frequenz, mit der Zellen kommunizieren, liegt zwischen 10 und 1000 Hertz."
Mannheimer Elektrizitätswerk MVV in ‚Mensch und Elektrizität‘ (1997) Die Pulsfrequenz eines Handys ist 217 Hz, einer Mobilfunk-Basisstation (D-/E-Netz) 217 bis 1733 Hz, die von DECT-Schnurlosen 100 Hz und die der WLAN-Technik 10 Hz, sie liegen damit alle in diesem biologisch relevanten Bereich der Zellkommunikation.
-
In der Sprache der Nachrichtentechnik darf man Nervenleitbahnen als digitale Übertragungskanäle ansehen. Sie sind die Fernmeldestromkreise des Organismus. Dabei vollzieht sich die Informationsübermittlung durch Impulse. Meist wird eine Pulsfrequenz von 1000 Hz nicht überschritten."
RWE-Arbeitsinformation, Dr.-Ing. Rolf Hotopp (1984) Anmerkung wie oben: Die modernen Mobilfunk-, DECT- und WLAN-Techniken pulsen in diesem sensiblen Bereich der biologischen Informationsübermittlung.
"Neben den abgesicherten thermischen Wirkungen, welche die Grundlage der Grenzwerte sind, gibt es eine große Zahl von Hinweisen auf Langzeitwirkungen, z.B. Kinderleukämie, Hirntumore und Brustkrebs, weit unterhalb der Grenzwerte."
Das NRW-Umweltministerium in einem Antwortbrief auf die Anfrage eines besorgten Düsseldorfer Bürgers zur Elektrosmogverordnung (1998)
-
• "Aus der Sicht des Umweltministeriums bestehen erhebliche Fragen insbesondere bei der wissenschaftlichen Bewertung nichtthermischer Effekte bei Feldstärken unterhalb der Grenzwerte… Es sollten dringend Vorsorgewerte eingeführt werden, um die Einwirkungen elektromagnetischer Felder auf den Menschen und die daraus folgenden potenziellen Gesundheitsrisiken möglichst gering zu halten."
Das NRW-Umweltministerium in einem Antwortbrief auf die Anfrage eines besorgten Kölner Bürgers zum Thema Mobilfunksender (11. März 2002)
-
• "Aus der Sicht des Umweltministeriums bestehen erhebliche Fragen insbesondere bei der wissenschaftlichen Bewertung nichtthermischer Effekte bei Feldstärken unterhalb der Grenzwerte… Es sollten dringend Vorsorgewerte eingeführt werden, um die Einwirkungen elektromagnetischer Felder auf den Menschen und die daraus folgenden potenziellen Gesundheitsrisiken möglichst gering zu halten."
Das NRW-Umweltministerium in einem Antwortbrief auf die Anfrage eines besorgten Kölner Bürgers zum Thema Mobilfunksender (11. März 2002)
-
"Die Freiheit der ständigen Erreichbarkeit wird teuer erkauft… Nach vorliegenden wissenschaftlichen Ergebnissen ist auch bei Einhaltung der Grenzwerte davon auszugehen, dass begründete Zweifel an der Unschädlichkeit der Grenzwerthöhe bestehen und eine Gesundheitsschädigung nicht auszuschließen ist."
Prof. Dr.jur. Klaus Kniep, Rechtsanwalt aus Heilbronn (1. März 2002)
-
"Die Grenzwerte in Deutschland sind reichlich hoch. In Russland werden in der Medizin gepulste Mikrowellen zu Therapiezwecken eingesetzt, die nachweislich wirken; diese liegen beim 10000stel der deutschen Grenzwerte."
Prof. Dr.Ing. Günter Käs, Bundeswehr-Universität Neubiberg (1997)
-
"Zweifelsfrei verstanden haben wir beim Funk nur die thermische Wirkung, nur auf dieser Basis können wir derzeit Grenzwerte festlegen. Es gibt darüber hinaus Hinweise auf krebsfördernde Wirkungen und Störungen an der Zellmembran."
ICNIRP-Vorsitzender Prof. Dr. Jürgen Bernhardt zur Elektrosmogverordnung (1998)
-
"Die Grenzwerte müssen um das 10.000-Fache gesenkt werden."
BUND, Bund für Umwelt und Naturschutz (August 2001)
-
Bundespostminister Wolfgang Boetsch vor Journalisten in Bonn (5. Februar 1993)
-
"Angesichts der Vielzahl wissenschaftlicher Befunde kann man weder das Krebsrisiko noch verschiedene andere biologische Effekte einfach abtun."
Umweltausschuss des EU-Parlamentes (2000)
-
"Die kritische Sichtung der wissenschaftlichen Literatur lässt keinen Zweifel mehr offen, dass die gepulste Strahlung von Basisstationen, Handys und schnurlosen Haustelefonen wesentlich gesundheitsbeeinflussend und schädlich ist."
Prof. Dr.-Ing. Alexander H. Volger, Honorarprofessor der Rheinisch-Westfälischen Technischen Hochschule RWTH Aachen (14. September 2002)
-
• "Jeder Vierte hat ein geschädigtes Immun-, Nerven- oder Hormonsystem, jeder Dritte ist Allergiker. Wir haben den Punkt erreicht, der keine zusätzlichen Belastungen mehr verträgt."
DGUHT, Deutsche Gesellschaft für Umwelt und Humantoxikologie (1994)
-
"Wir wissen sehr gut, dass gepulste Signale auf den Menschen stärker einwirken als ungepulste. Gepulste Mikrowellen greifen tief in biologische Prozesse ein."
Prof. Dr. Ross Adey, Loma-Linda-Universität, Kalifornien (1970)
- "Gepulste Mikrowellen schädigen das Immunsystem und beeinflussen Neurotransmitterabläufe."
Prof. Dr. Dan Lyle, Loma-Linda-Universität, Kalifornien (1985)
-
"Gepulste Mikrowellen verändern die menschlichen Gehirnströme. Das ist im EEG bei Strahlungsstärken von 1000 μW/m² nach wenigen Minuten nachweisbar."
Dr. Lebrecht von Klitzing, Medizin-Physiker, Medizinische Universität Lübeck (1994) 1000 μW/m² Feldstärke finden wir von der Baubiologie Maes in einer Entfernung von, je nach Situation, etwa 50 bis über 200 Metern zu Mobilfunkstationen auf Masten, Türmen, Dächern, Kaminen, Kirchen, Silos, Hochspannungsleitungen…, 5 bis über 10 Metern zu Handys, wenn mit ihnen telefoniert wird, 3 bis 5 Metern zu den immerzu funkenden Basisstationen der DECT-Schnurlostelefone und 2 bis 3 Metern zu WLAN.
-
"Bei 36 Probanden führte die gepulste Strahlung im Versuchslabor unmittelbar nach dem Einschalten zu Veränderungen im EEG."
Dr. H.P. Reiser, Dr. W. Dimpfel und Dr. F. Schober, Wissenschaftler des Pro-Science-Forschungsinstitutes im Auftrag der Telekom (1995)
-
"Veränderungen im EEG traten nach etwa 15 Minuten Einschaltzeit auf. Im Schlaf-EEG gab es Verkürzungen der REM-Phase."
Prof. Dr. Alexander Borbély, Institut für Toxikologie, Universität Zürich (1999)
-
"Die Frequenz, mit der Zellen kommunizieren, liegt zwischen 10 und 1000 Hertz."
Mannheimer Elektrizitätswerk MVV in ‚Mensch und Elektrizität‘ (1997) Die Pulsfrequenz eines Handys ist 217 Hz, einer Mobilfunk-Basisstation (D-/E-Netz) 217 bis 1733 Hz, die von DECT-Schnurlosen 100 Hz und die der WLAN-Technik 10 Hz, sie liegen damit alle in diesem biologisch relevanten Bereich der Zellkommunikation.
-
In der Sprache der Nachrichtentechnik darf man Nervenleitbahnen als digitale Übertragungskanäle ansehen. Sie sind die Fernmeldestromkreise des Organismus. Dabei vollzieht sich die Informationsübermittlung durch Impulse. Meist wird eine Pulsfrequenz von 1000 Hz nicht überschritten."
RWE-Arbeitsinformation, Dr.-Ing. Rolf Hotopp (1984) Anmerkung wie oben: Die modernen Mobilfunk-, DECT- und WLAN-Techniken pulsen in diesem sensiblen Bereich der biologischen Informationsübermittlung.
"Neben den abgesicherten thermischen Wirkungen, welche die Grundlage der Grenzwerte sind, gibt es eine große Zahl von Hinweisen auf Langzeitwirkungen, z.B. Kinderleukämie, Hirntumore und Brustkrebs, weit unterhalb der Grenzwerte."
Das NRW-Umweltministerium in einem Antwortbrief auf die Anfrage eines besorgten Düsseldorfer Bürgers zur Elektrosmogverordnung (1998)
-
• "Aus der Sicht des Umweltministeriums bestehen erhebliche Fragen insbesondere bei der wissenschaftlichen Bewertung nichtthermischer Effekte bei Feldstärken unterhalb der Grenzwerte… Es sollten dringend Vorsorgewerte eingeführt werden, um die Einwirkungen elektromagnetischer Felder auf den Menschen und die daraus folgenden potenziellen Gesundheitsrisiken möglichst gering zu halten."
Das NRW-Umweltministerium in einem Antwortbrief auf die Anfrage eines besorgten Kölner Bürgers zum Thema Mobilfunksender (11. März 2002)
-
• "Aus der Sicht des Umweltministeriums bestehen erhebliche Fragen insbesondere bei der wissenschaftlichen Bewertung nichtthermischer Effekte bei Feldstärken unterhalb der Grenzwerte… Es sollten dringend Vorsorgewerte eingeführt werden, um die Einwirkungen elektromagnetischer Felder auf den Menschen und die daraus folgenden potenziellen Gesundheitsrisiken möglichst gering zu halten."
Das NRW-Umweltministerium in einem Antwortbrief auf die Anfrage eines besorgten Kölner Bürgers zum Thema Mobilfunksender (11. März 2002)
-
"Die Freiheit der ständigen Erreichbarkeit wird teuer erkauft… Nach vorliegenden wissenschaftlichen Ergebnissen ist auch bei Einhaltung der Grenzwerte davon auszugehen, dass begründete Zweifel an der Unschädlichkeit der Grenzwerthöhe bestehen und eine Gesundheitsschädigung nicht auszuschließen ist."
Prof. Dr.jur. Klaus Kniep, Rechtsanwalt aus Heilbronn (1. März 2002)
-
"Die Grenzwerte in Deutschland sind reichlich hoch. In Russland werden in der Medizin gepulste Mikrowellen zu Therapiezwecken eingesetzt, die nachweislich wirken; diese liegen beim 10000stel der deutschen Grenzwerte."
Prof. Dr.Ing. Günter Käs, Bundeswehr-Universität Neubiberg (1997)
-
"Zweifelsfrei verstanden haben wir beim Funk nur die thermische Wirkung, nur auf dieser Basis können wir derzeit Grenzwerte festlegen. Es gibt darüber hinaus Hinweise auf krebsfördernde Wirkungen und Störungen an der Zellmembran."
ICNIRP-Vorsitzender Prof. Dr. Jürgen Bernhardt zur Elektrosmogverordnung (1998)
-
"Die Grenzwerte müssen um das 10.000-Fache gesenkt werden."
BUND, Bund für Umwelt und Naturschutz (August 2001)
-
...
 Radiation: Class action lawsuit against Apple and Samsung, PC-WELT.de, 08.26.2019 Radiation: Class action lawsuit against Apple and Samsung, PC-WELT.de, 08.26.2019
Smartphones geben mehr Strahlung ab, als eigentlich erlaubt. Das berichtete in der vergangenen Woche eine amerikanische Zeitung. Diesem Bericht folgt bereits die erste Sammelklage einer kleinen Kanzlei aus Atlanta.
Die Chicago Tribune hat mehrere Smartphones auf die abgegebene Strahlung hin getestet. Dabei kam die Zeitung zu dem Schluss, dass einige Geräte die festgeschriebenen Grenzwerte nicht einhielten. Wir berichteten.
Über einen Facebook-Post ließ die Anwaltskanzlei Fegan Scott LLC gestern verlauten, eine Sammelklage gegen Apple und Samsung eingereicht zu haben. Sie werfen den Konzernen vor, durch die vermeintlich (die Ergebnisse einer neuen Untersuchung durch die amerikanische Behörde FCC stehen noch aus) erhöhten Strahlenwerte die Gesundheit der Gerätenutzer zu gefährden. Außerdem sei die Werbung zu den Produkten irreführend und spiele die Gefahren von Strahlung, die durch Smartphones abgegeben wird, herunter, ignoriere sie sogar komplett. So wird Apple und Samsung vorgeworfen, mit Slogans wie "Studio in your pocket" zu sugerrieren, dass Smartphones risikofrei in der Hosentasche transportiert werden können.
Die 44-seitige Anklageschrift bezieht sich zu großen Teilen auf den Artikel der Chicago Tribune, aber auch auf verschiedene Studien, welche die Schädlichkeit von Smartphone-Strahlung belegen sollen. Dabei ist diese wissenschaftlich durchaus umstritten. Für mehr Informationen zu diesem Thema empfehlen wir den Gast-Beitrag unseres Experten Dennis Bederov. In diesem Beitrag haben wir die Problematik der SAR-Messungen zusammengefasst und erklärt, warum diese nicht immer aussagekräftig sind.
Sammelklagen gegen große Konzerne und Behörden sind keine Seltenheit. Erst vor wenigen Monaten startete in den USA eine Sammelklage gegen die US-Behörde FCC wegen der Zulassung von 5G-Mobilfunk. Auch in diesem Fall gehört die Gefährdung der Allgemeinheit zu den Vorwürfen, ohne dass diese wissenschaftlich einwandfrei erwiesen ist.
https://www.pcwelt.de/news/Wegen-Strahlung-Sammelklage-gegen-Apple-und-Samsung-eingereicht-10654270.html
Murder upon rates - Stop 5G and the BRD !, brd-schwindel.ru, 04.19.2019
Folgende Zitatesammlung zeigt, dass man schon lange über die Gefahren der Mobilfunktelefonie Bescheid weiß und welche Schäden diese im menschlichen Organismus anrichtet, vor allem im Gehirn. Und dabei geht es nicht einmal um 5G. Man kann sich ausrechnen, dass sich die Belastung um einiges potenziert. Wir sind ohne 5G schon enormen Strahlungen ausgesetzt. 5G NEIN DANKE
Die Zitatensammlung stammt aus wissenschaftlichen Arbeiten, Fachveröffentlichungen, Presseagenturmeldungen, Büchern, Vorträgen, Zeitungen, von Ärzten, Ämtern, Experten, dem Internet, den Nachrichten, wurden im Radio gehört, im Fernsehen gesehen…
- "Die Handymasten werden stillgelegt. Es ist größtmögliche Vorsicht geboten."
Aus dem Urteil des Gerichtes von Valladolid/Spanien (Dezember 2001) In Valladolid legte das Gericht sechs Mobilfunkmasten mit 36 Einzelantennen diverser Betreiber in der Nähe einer Schule still. Drei Kinder erkrankten in dieser Schule innerhalb weniger Monate an Leukämie und eines an Lymphdrüsenkrebs. Es wurden außer den Funkwellen keine anderen Risikofaktoren wie z.B. Schadstoffe gefunden. Das erhärte den Verdacht, dass der Funk die Ursache für die Krebsfälle ist. Darauf deute zudem hin, dass es nach der Installation der Funkmasten auch in den umliegenden Wohnhäusern 18 Krebsfälle bei Kindern gibt. Die Funkantennen bleiben trotz aller Proteste der Industrie abgeschaltet und müssen demontiert werden.
- "Die aufgeregte Diskussion in der Bevölkerung über die Kernenergie dürfte in Relation zu dem, was uns die Mobilfunknetze noch bescheren werden, nur ein laues Lüftchen gewesen sein."
https://brd-schwindel.ru/mord-auf-raten-stoppt-5g-und-die-brd/
 Radiation: Class action-lawsuit against Apple, Samsung, PC-WELT.de, 09.12.2019 Radiation: Class action-lawsuit against Apple, Samsung, PC-WELT.de, 09.12.2019
Laut einem Bericht geben Smartphones mehr Strahlung ab als erlaubt. Diesem Bericht folgt bereits die erste Sammelklage.
https://www.pcwelt.de/news/Wegen-Strahlung-Sammelklage-gegen-Apple-und-Samsung-eingereicht-10654270.html
 48 Mio. SIM-cards soon do surf at a snail´s pace, PC-WELT.de, 06.05.2020 48 Mio. SIM-cards soon do surf at a snail´s pace, PC-WELT.de, 06.05.2020
45% of all SIM-cards can not use LTE. As soon as Telekom & Co.turn off their 3G-nets, they surf at a snail´s pace.
https://www.pcwelt.de/news/3G-Abschaltung-48-Mio.-SIM-Karten-bald-mit-Schneckentempo-10805448.html
How do burning akkus and electro-cars get extinguished? This is, what the fire department tells us!, PC-WELT.de, 18.03.2020
Wenn der Smartphone-Akku raucht oder gar ein Elektro-Auto Feuer fängt: Was soll man tun? Wie löscht man den Brand? Und wie vermeidet man von vornherein einen Akku-Brand? Wir fragten zwei Experten der Münchner Feuerwehr.
[...] Feuerwehr München : Ein tiefentladener Li-Ionen-Akku kann ggf. beim Versuch des Wiederaufladens zu reagieren beginnen. [...] Des Weiteren spielt hier auch die Qualität des Ladegerätes eine entscheidende Rolle (z.B. Original-Ladegerät oder "Zukaufteil"?) und die Tatsache, ob ein Akku bereits "vorgeschädigt" ist. Hierbei sei besonders auf die jeweilige Bedienungsanleitung bzw. Hinweise der Hersteller verwiesen.
[...] Zur Entzündung eines Akkus können unterschiedliche Gründe führen. Eine mechanische Beschädigung, beispielsweise wenn der Smartphone-Akku auf den Boden fällt, kann zu inneren Kurzschlüssen führen. Durch Überladung kann es zu elektrischen Abnutzungsschäden kommen (elektrische Belastung). Und eine Temperaturerhöhung (thermische Belastung), beispielsweise infolge eines Brandes, kann ebenfalls zu einem Akku-Schaden führen.
PC-WELT: Soll man einen brennenden Lithium-Ionen-Akku tatsächlich am besten mit Wasser löschen? Also konkret: wenn ein Smartphone am Boden liegt, dann einen Eimer Wasser darüberschütten? Oder kann man den Brand auch mit einem Kissen/einer Decke ersticken? Kann man einen Pulver- oder Schaumfeuerlöscher verwenden?
Feuerwehr München: Das Löschmittel der Wahl ist Wasser. Brennende Klein-Batterien beziehungsweise kleine Akkus sind also möglichst lange mit Wasser zu löschen. Nach Brandende sind sie in einem Behälter unter Wasser stehend zu lagern, bis sie einem qualifizierten Entsorger übergeben werden.
[...] Grundsätzlich gilt, dass bei guten Fertigungsstandards, zertifizierten Lade- und Zellenüberwachungssystemen sowie bei sachgerechter Handhabung Lithium-Ionen-Speichermedien als ausreichend sicher einzustufen sind.
[...] Auch bei der Lagerung bereits relativ kleiner Mengen von Lithium-Ionen-Speichermedien, die in Brand geraten, ist mit einer sehr schnellen Brandausbreitung zu rechnen. Durch das teils explosionsartige Abbrennen können brennende Teile umhergeschleudert werden. Deshalb ist bei Lagerungen ein besonderes Augenmerk auf die bauliche Abschottung zwischen Brandabschnitten oder Räumen mit gelagerten Neu- wie auch Altbatterien zu legen.
[...] Das Löschmittel der Wahl ist Wasser. Brennende Klein-Batterien beziehungsweise kleine Akkus sind also möglichst lange mit Wasser zu löschen. Nach Brandende sind sie in einem Behälter unter Wasser stehend zu lagern, bis sie einem qualifizierten Entsorger übergeben werden.
https://www.pcwelt.de/ratgeber/So-loescht-man-brennende-Akkus-und-Elektro-Autos-Feuerwehr-Tipps-10762550.html
Do we all get shortsighted and blind?
 TFT, Smartphones, ... TFT, Smartphones, ...
Forscher: Blue screen-light can make us blind, PC-WELT.de, 08.13.2018
Blaues Licht, wie von diversen Displays emittiert, kann auf molekularer Ebene Netzhautzellen beschädigen.
https://www.pcwelt.de/a/forscher-blaues-bildschirm-licht-kann-blind-machen,3439480
 Working in front of the monitor-screen Working in front of the monitor-screen
Do bluelight-filter in glasses help?, tagesschau.de, 02.15.2021
Blaulicht ist im gesamten Farbspektrum ein hochenergetisches Licht im kurzwelligen Bereich. Es wird besonders gern bei LED-Flachbildschirmen und Smartphones eingesetzt, um Kontraste zu verstärken und Farben brillanter aussehen zu lassen. Aber reicht der Blaulichtanteil in den Geräten aus, um die Netzhaut zu schädigen? Tatsächlich gibt es dazu bisher keine klinische Studie, die das beweist. Oliver Stefani vom Zentrum für Chronobiologie in Basel geht aber davon aus, dass der Blick über mehrere Sekunden in starke LEDs die Netzhaut schädigen kann.
https://www.tagesschau.de/wirtschaft/verbraucher/brillen-blaulichtfilter-101.html
 Publicity illness: See, how harmful Smartphones for our eyes really are, STERN.de, 20.08.2018 Publicity illness: See, how harmful Smartphones for our eyes really are, STERN.de, 20.08.2018
Kurzsichtigkeit ist die neue Volkskrankheit unter jungen Menschen. Schuld daran ist die Zeit, die sie vor Bildschirmen von Smartphone, Tablet und Computer verbringen.
https://www.stern.de/gesundheit/gesundheitsnews/kurzsichtigkeit--so-schaedlich-ist-das-smartphone-fuer-unsere-augen-8219784.html
 Increase of purblindness Increase of purblindness
Immense increase of eye problems: See, how dangerous handies areFOCUS ONLINE
Das ständige Schauen auf Smartphone- und Computerbildschirme schadet unseren Augen. Die Folgen des digitalen Sehens sind so gravierend, dass Kurzsichtigkeit in den kommenden Jahren weiter zunimmt. Was Sie tun können, um Ihre Augen zu schützen.
https://www.focus.de/gesundheit/news/zunahme-von-augenproblemen-grosser-anstieg-bei-kurzsichtigkeit-wie-gefaehrlich-handys-wirklich-fuer-uns-sind_id_9162093.html
 Zunahme von Kurzsichtigkeit Zunahme von Kurzsichtigkeit
Großer Anstieg bei Augenproblemen: Wie gefährlich Handys wirklich für uns sindFOCUS ONLINE
Das ständige Schauen auf Smartphone- und Computerbildschirme schadet unseren Augen. Die Folgen des digitalen Sehens sind so gravierend, dass Kurzsichtigkeit in den kommenden Jahren weiter zunimmt. Was Sie tun können, um Ihre Augen zu schützen.
https://www.focus.de/gesundheit/news/zunahme-von-augenproblemen-grosser-anstieg-bei-kurzsichtigkeit-wie-gefaehrlich-handys-wirklich-fuer-uns-sind_id_9162093.html
Some or many graphic cards or TFT present a bleary screen upsetting onePs eyes., so that one has to wear glasses or contact lenses contacts. Headaches are unseldom. Rules like California rules warnings also warn against health attacking, bad smell of some graphic cards. Especially new models do consum a lot of power.
Do we all get injected?
Horrible Coronavirus-tracker encrypts smartphones: Howto unlock the handy again, CHIP, 16.03.2020
https://www.chip.de/news/Fieser-Coronavirus-Tracker-verschluesselt-Smartphones-So-entsperren-Sie-das-Handy-wieder_182551635.html
Wahrscheinlich ähnlich Computer...:
 Study: Smartphones do share our data each four and a half minutes, uncutnews, 31.03.2021 Study: Smartphones do share our data each four and a half minutes, uncutnews, 31.03.2021
https://uncutnews.ch/laut-einer-studie-teilen-smartphones-unsere-daten-alle-viereinhalb-minuten/
 Brisant Android-Study: Google-handies sent twenty times more data away than iPhones, CHIP, 04.04.2021 Brisant Android-Study: Google-handies sent twenty times more data away than iPhones, CHIP, 04.04.2021
https://www.chip.de/news/Brisante-Android-Studie-enthuellt-Google-Handys-geben-20-Mal-mehr-Daten-weiter-als-iPhones_183434034.html
Shock-Studiy Popular Apps spy out children without limits - 72 millionen data points past age 13, uncut-news.ch, 06.14.2022
Geheimdienste/NSA/Überwachung/BigData
childrenshealthdefense.org: Eine neue Studie, die zeigt, dass Technologieunternehmen Daten von Apple- und Google-Apps sammeln - die meist von Kindern ohne elterliche Zustimmung genutzt werden - und sie an Werbetreibende weiterleiten. Nun hat dies Experten dazu veranlasst, Gesetze zu fordern, die App-Entwickler dafür verantwortlich machen würden, festzustellen, ob Kinder ihre Produkte nutzen.
"Apps spionieren unsere Kinder in einem Ausmaß aus, das Sie schockieren sollte", so die Washington Post, die über die Studie berichtete. "Mehr als zwei Drittel der 1.000 beliebtesten iPhone-Apps, die wahrscheinlich von Kindern genutzt werden, sammeln deren persönliche Daten und senden sie an die Werbeindustrie".
Die Studie von Pixalate, einem Unternehmen, das sich auf Betrugsschutz und Datenschutz spezialisiert hat, ergab, dass 79 % der Android-Apps dasselbe tun.
Die Forscher fanden heraus, dass beliebte Apps wie Angry Birds 2 und Candy Crush Saga die Kinder ausspionieren - ebenso wie Apps, die zum Ausmalen und für Mathe-Hausaufgaben verwendet werden.
Pixalate war in der Lage, mehr als 391.000 von Kindern genutzte Apps in den Apple- und Google-Stores zu identifizieren und die 1.000 beliebtesten von Kindern genutzten Apps zu ermitteln und zu analysieren, wie mit sensiblen Daten umgegangen wurde.
Von allen von Pixalate identifizierten Apps übermittelten 7 % entweder Standort- oder Internetadressdaten an die Werbeindustrie.
Die Studie ergab auch, dass beliebte Apps einen größeren Anreiz haben, Nutzer zu verfolgen, weil sie mit gezielter Werbung Geld verdienen.
Sowohl Google als auch Apple streiten jegliches Fehlverhalten ab und behaupten, dass ihre App-Stores die Privatsphäre von Kindern schützen, so die Washington Post.
In einer anderen Studie von Pixalate fanden Forscher heraus, dass fast 90 % der 164 Bildungs-Apps und Websites Informationen an die Werbetechnikindustrie übermittelten.
Eine Studie aus dem Jahr 2020 zeigte, dass zwei Drittel der Apps, die von 124 Kindern im Vorschulalter gespielt wurden, identifizierende Informationen sammelten und weitergaben.
Ein Forschungsbericht aus dem Jahr 2017, der die Medienkompetenz untersuchte, zeigte, dass viele Kinder Werbung nicht von Inhalten unterscheiden können, und dass die Tracking-Technologie es den Vermarktern ermöglicht, ihre Gedanken gezielt anzusprechen.
"Sie erfassen die allgemeinen Standorte der Kinder und andere identifizierende Informationen und senden sie an Unternehmen, die ihre Interessen verfolgen, vorhersagen können, was sie vielleicht kaufen möchten, oder sogar ihre Informationen an andere verkaufen können", schrieb Geoffrey Fowler, der Technologiekolumnist der Washington Post.
Ein Schlupfloch im System
Das Gesetz zum Schutz der Online-Privatsphäre von Kindern (Children´s Online Privacy Protection Act, COPPA) wurde 1998 erlassen, um zu verhindern, dass Technologieunternehmen ohne Zustimmung der Eltern persönliche Daten von Kindern unter 13 Jahren sammeln.
"Als das Gesetz ursprünglich entworfen wurde, war es ziemlich offensichtlich, dass es für skrupellose Unternehmen eine echte Möglichkeit geben würde, junge Menschen auszunutzen", sagte Senator Edward J. Markey (D-Mass.), einer der Autoren des COPPA, gegenüber der Washington Post. "Jetzt sind die Probleme auf Steroiden".
Nach Angaben von SuperAwesome, einem in London ansässigen Unternehmen, das App-Entwicklern bei der Einhaltung der Datenschutzgesetze für Kinder hilft, verfügen Online-Werbefirmen im Durchschnitt über 72 Millionen Datenpunkte über ein Kind, wenn es 13 Jahre alt ist.
"Sie stellen ihre Profite über die geistige Gesundheit und das soziale Wohlergehen jedes Kindes in Amerika, denn das ist die Macht, die sie heute haben", sagte Markey.
Laut Fowler haben Big Tech und App-Hersteller ein riesiges Schlupfloch im Datenschutzgesetz gefunden. "Sie behaupten, sie wüssten nicht, dass sie Daten von Kindern abgreifen", sagte er.
Ein Beispiel: Pixel Art: Malen nach Zahlen ist eine kostenlose Mal-App, die von Easybrain für Kinder ab 12 Jahren entwickelt wurde - aber die App fragt weder nach dem Alter des Kindes noch holt sie die Erlaubnis eines Elternteils oder Erziehungsberechtigten zur Nutzung der App ein.
Beim Öffnen der App werden laut Pixalate die Informationen des Nutzers, einschließlich des allgemeinen Standorts, der Internetadresse und identifizierende Informationen, an die Werbeindustrie gesendet. Zu keinem Zeitpunkt fragt die App nach dem Alter oder der Erlaubnis des Nutzers.
Easybrain behauptet, das sei auch nicht nötig, weil Pixel Art nicht für Kinder gedacht sei.
Ein Sprecher von Easybrain, Evan Roberts, sagte, das Unternehmen betreibe einen Dienst für ein allgemeines Publikum und habe im Allgemeinen keine Kenntnis davon, dass die Pixel Art App persönliche Daten von Kindern unter 13 Jahren sammelt, verwendet oder weitergibt.
Obwohl die Kategorien in der App, wie Eiscreme, Einhörner und Dinosaurier, so aussehen, als würden sie sich an Kinder richten, gibt der App-Hersteller an, dass sie für Erwachsene vermarktet wird.
Im Jahr 2021 legte die Federal Trade Commission (FTC) einen Rechtsstreit mit einer sich selbst als "erwachsen" bezeichnenden Ausmal-App namens Recolor bei, die einen "Kinder"-Bereich hatte.
Der Hersteller von Candy Crush Saga behauptet, dass sich sein Spiel und sein Marketing an erwachsene Spieler über 18 Jahren in den USA richten". Dennoch ist das Spiel mit "Alter: 4+" angegeben.
Frank List, CEO von Impala Studios, sagte, dass die App Calculator and Math Solver des Unternehmens besser sein muss.
"Wir werden mehr darauf achten, dass wir uns nur an unsere Zielgruppe wenden", sagte er der Washington Post.
Apple und Google verschließen die Augen vor dem Datenschutz von Kindern
Apple und Google scheinen mehr Macht als die US-Regierung über die Funktionsweise von Apps zu haben, da sie die beiden größten App-Stores kontrollieren. Doch wenn es um den Datenschutz von jungen Nutzern geht, drücken diese Tech-Giganten ein Auge zu.
Google und Apple geben nicht an, ob ihre App-Stores COPPA-konform sind, und keiner der beiden App-Stores zeigt den Eltern oder Erziehungsberechtigten eine Möglichkeit, zu sehen, welche Apps Daten über Kinder sammeln.
Im Google-Store gibt es eine Registerkarte für Kinder-Apps, die Apps als "Teacher Approved" (von Lehrern genehmigt) kennzeichnet, und es gelten strenge Standards. Pixalate zufolge sind jedoch nur 5 % der beliebten Kinder-Apps im Google-Store ordnungsgemäß gekennzeichnet.
Der Apple Store ist ein wenig komplizierter. Wenn man die Kategorie "Kinder" finden will, muss man sie am unteren Ende des Stores suchen - und es gibt keine Möglichkeit, danach zu suchen. Keine der Kinder-Apps ist mit einem Hinweis auf den Schutz der Privatsphäre versehen.
Die elterliche Kontrolle im Apple Store ist begrenzt, da Eltern oder Erziehungsberechtigte nur die Möglichkeit haben, App-Käufe zu genehmigen, sobald sie das iOS-Konto eines Kindes eingerichtet haben.
"Wenn Sie sicherstellen wollen, dass die Privatsphäre Ihres Kindes respektiert wird, müssen Sie sich damit auseinandersetzen", so Fowler.
Befürworter der Privatsphäre von Kindern sind der Meinung, dass sich die Tech-Industrie nicht ändern wird, solange es keine rechtliche Verantwortung gibt, sich des Problems anzunehmen.
Erst 2019 begann YouTube mit der Kennzeichnung von Videos, die von Kindern stammen, nachdem das Unternehmen von einer Klage betroffen war und gezwungen wurde, 136 Millionen Dollar an die FTC und 34 Millionen Dollar an den Staat New York zu zahlen, weil es gegen COPPA verstoßen hatte.
In der Klage wurde behauptet, dass Google´s YouTube gegen COPPA verstoßen hat, indem es "persönliche Daten - in Form von dauerhaften Identifikatoren, die verwendet werden, um Nutzer über das Internet zu verfolgen - von Zuschauern kindergeführter Kanäle sammelte, ohne die Eltern vorher zu benachrichtigen und ihre Zustimmung einzuholen".
Markey sagte, dass er und die Abgeordnete Kathy Castor (D-Fla.) Gesetzesentwürfe erarbeitet haben, die COPPA aktualisieren würden. Die Überarbeitungen würden Jugendliche bis zum Alter von 16 Jahren abdecken und gezielte Werbung gänzlich verbieten.
Die Gesetzesentwürfe würden, falls sie verabschiedet werden, von Apps und Websites verlangen, dass sie die Verantwortung dafür übernehmen, ob Kinder ihre Dienste nutzen.
Fowler sagte, Kalifornien wolle eine Version des britischen Gesetzes, den Age Appropriate Design Code, einführen. Die Unternehmen wären verpflichtet, das Alter des Verbrauchers festzustellen und ein hohes Maß an Datenschutz für Kinder zu gewährleisten.
Bisher haben die US-Gesetzgeber zwar viel über den Datenschutz geredet, aber keine Maßnahmen ergriffen, so Fowler.
"Wenn wir uns nicht um Kinder kümmern können, dann zeigt das nur, wie kaputt unser politisches System ist", sagte Markey der Washington Post. "Es zeigt, wie mächtig die Tech-Unternehmen sind."
Quelle: Popular Apps Are Spying on Kids at ´Scale That Should Shock You´ (childrenhealthdefense.org, Kenndy Jr. u.a.
https://uncutnews.ch/schock-studie-beliebte-apps-spionieren-kinder-ohne-limit-aus-72-millionen-datenpunkte-wenn-es-das-13-lebensjahr-erreicht-hat/
 Smartphone Smartphone
At the frontier your phone is not secure, uncut-news.ch, 09.02.2025
reclaimthenet
Telefondurchsuchungen ohne Durchsuchungsbefehl erreichen Rekordhöhe.
Ob Bürger oder nicht, Ihre Texte sind am Terminal Freiwild. Hier erfahren Sie, wie Sie sich schützen können.
[...] Kategorien der Schnüffel-Operationen
Basissuche: Ein Blick ins entsperrte Telefon. Ohne Befehl, ohne Verdacht.
Erweiterte Durchsuchung: Vollständige forensische Extraktion. Die Behörde behauptet, sie brauche dafür "begründeten Verdacht". Doch was gilt schon als Verdacht? Ein Meme gegen ICE, eine Spende an die falsche Wohltätigkeitsorganisation oder ein WhatsApp-Chat in einer Fremdsprache.
Wenn Sie betroffen sind
Ihr Telefon wurde beschlagnahmt? Sie werden bei jeder Landung "zufällig ausgewählt"? Niemand erklärt Ihnen warum?
[...] Ihr Werkzeugkasten:
Formular 6051D (Custody Receipt) - danach fragen.
Beschwerde bei DHS TRIP einreichen.
Beschwerde bei der CBP selbst.
Beschwerde bei DHS (Bürgerrechte).
Kontakt zum Generalinspektor aufnehmen.
Kongressabgeordnete einschalten - die einzige Sprache, die die Behörde versteht.
FOIA-Antrag stellen - oder via Muckrock auslagern.
Wie Sie sich vorbereiten
Wenn Sie Journalist, Whistleblower oder mit sensiblen Daten reisen, bedenken Sie: Ihr Gerät ist das kompromittierendste Objekt, das Sie besitzen.
Vor der Reise:
☐ Backup extern, nicht auf dem Gerät.
☐ Alles verschlüsseln (BitLocker, FileVault).
☐ Langes, zufälliges Passwort - nicht in "Notizen".
☐ Weniger Geräte mitnehmen.
☐ Alles löschen, was riskant ist. Papierkorb leeren.
☐ Von Cloud- und Konten abmelden.
☐ Reisegerät oder Brenner nutzen.
☐ Politische Posts vor Abflug vermeiden.
☐ Keine sensiblen Dokumente mitnehmen.
☐ Passwort-Manager nutzen (später neu installieren).
☐ Verschwinden-Modus für Nachrichten aktivieren.
☐ Kollegen informieren.
Am Reisetag:
☐ Geräte ausschalten (Verschlüsselung aktiv).
☐ Flugmodus einschalten.
☐ Kontakt zum Anwalt griffbereit (schriftlich).
☐ Nach Landung sofort melden.
Rechtliche Realität
US-Bürger: Dürfen verweigern, aber Gerät wird evtl. beschlagnahmt, Kopie erstellt, spätere Schikanen folgen.
Green-Card-Inhaber: "Sollten" einreisen dürfen, aber mit möglichen Komplikationen.
Visa-/ESTA-Besucher: Weigerung = Einreise verweigert.
Fazit
An der Grenze gibt es keine informierte Zustimmung. Sie unterschreiben nichts, Ihnen werden keine Rechte vorgelesen. Stattdessen wird stillschweigend angenommen, dass Sie Teil eines Prozesses sind, der die verfassungsmäßigen Grenzen im Namen der Sicherheit umschreibt.
Dieser Prozess wird zunehmend automatisiert. Jeder Reisende wird behandelt wie ein Verdächtiger, bis er sich als kooperativ erweist.
Die Last, Ihr digitales Leben zu schützen, liegt bei Ihnen.
Das Gesetz wird nicht rechtzeitig reagieren. Die Behörden entschuldigen sich nicht, wenn Ihr Gerät in einem forensischen Scanner landet. Planen Sie entsprechend - oder riskieren Sie, alles offenzulegen, nur um durch die Passkontrolle zu kommen.
Quelle: https://reclaimthenet.org/your-phone-isnt-safe-at-the-border
https://uncutnews.ch/ihr-telefon-ist-an-der-grenze-nicht-sicher/
Millions of downloads: fitness-Apps do spy out user, CHIP, 03.23.2021
Fitness-Apps sind in den letzten Monaten immer beliebter geworden. Wie eine Untersuchung nun herausgestellt hat, beinhalten einige Smartphone-Anwendungen allerdings Tracker, die Sie überwachen.
Einige Fitness-Apps spionieren ihre Nutzer aus. Zu diesem Ergebnis kommt eine Untersuchung von ExpressVPN Digital Security Lab. Insgesamt zwölf Apps wird demnach vorgeworfen, Standort-Tracking zu verwenden, die über die eigentliche Funktionsweise der Anwendung hinausgehen.
Manchen der Apps kann dabei nicht einmal Absicht vorgeworfen werden. Stattdessen liegt das Problem in Diensten, die die Entwickler dahinter nutzen. Für das Tracking verlassen sie sich häufig auf externe Anbieter, die leichtere Schnittstellen bei der App-Entwicklung ermöglichen. Ein paar dieser Anbieter haben Hintertüren in ihren System verbaut, mit denen die Daten der Nutzer am Ende bei ihnen landen.
https://www.chip.de/news/Millionenfach-heruntergeladen-Fitness-Apps-spionieren-Nutzer-aus_183378304.html
DHL and Deutsche Post warn against betrayal-SMS installing dangerous malware
WhatsApp-betayal-trick: messages in the name of the BKA, CHIP, 04.08.2021
Die Deutsche Post und DHL warnen derzeit vor SMS, die im Namen der Dienste versandt werden. Empfänger werden in den Nachrichten darauf hingewiesen, dass man per Klick auf einen Link eine Paketsendung bestätigen solle. Über diesen wird dann jedoch eine App installiert, die Malware enthält.
Zum wiederholten Male befinden sich SMS im Umlauf, die auf angeblich versandte Pakete von DHL oder der Deutschen Post hinweisen. Die betrügerischen Nachrichten besagen, dass ein versandtes Paket "noch ausstehe" und man die Lieferung per Klick auf einen Link bestätigen solle. Anschließend würde ein Kurier das Paket angeblich abnehmen.
Wie DHL und die Deutsche Post in einem Facebook-Posting schreiben, handelt es sich dabei um eine Betrugsmasche. Klickt ein Nutzer auf den Link, wird er dazu aufgefordert, eine App zu installieren. Diese enthält jedoch Malware und sollte folglich auf keinen Fall auf das Smartphone geladen werden.
https://www.chip.de/news/DHL-und-Deutsche-Post-Betrugs-SMS-installieren-gefaehrliche-Malware_183490853.html
 Over 10 millionen user got already ripped off: You should delete these 200 apps immediately, CHIP, 10.04.2021 Over 10 millionen user got already ripped off: You should delete these 200 apps immediately, CHIP, 10.04.2021
Up to now a horrible trojan puts the Android smartphones into danger. The malware as un update creeps into and, if possible, got already downloaded million times. Read here, howto protect your handy.
https://www.chip.de/news/200-Android-Apps-mit-Malware-befallen-schuetzen-Sie-Ihr-Smartphone_183876962.html
 Howto recognise Quit-SMS - the sign for eavesdropping, CHIP, 10.14.2021 Howto recognise Quit-SMS - the sign for eavesdropping, CHIP, 10.14.2021
Verfassungsschutz, Bundespolizei und Bundeskriminalamt nutzen die stille SMS für ihre Zwecke - und zwar nicht nur in Einzelfällen. Diese unsichtbaren Kurznachrichten werden von Computerprogrammen automatisch und in kurzen Abständen gesendet. Gerichte müssen das Abfragen der daraus entstandenen Daten durch die Polizei bei den Telefonanbietern genehmigen. Datenschützer finden den Einsatz problematisch.
[...] Stille SMS per App erkennen - kostenloser Download!
Verhindern können Sie den Empfang einer stillen SMS nur, wenn das Smartphone ausgeschaltet ist und Akku und SIM-Karte entfernt sind. Es gibt aber eine App, die Ihnen den Empfang stiller SMS anzeigt:
Die kostenlose Android-App SnoopSnitch zeigt Ihnen an, wenn Sie eine stille SMS erhalten haben. Für iOS gibt es so etwas leider nicht.
Unklar ist dann aber noch immer, von wem genau Sie die stille SMS erhalten haben. Das werden Sie aber wohl nie erfahren, wenn nicht eines Tages der Verfassungsschutz oder die Polizei vor der Tür steht.
Auch wenn sich Kriminelle als Funkmast ausgeben und in Wahrheit nur Daten und Gespräche abschöpfen wollen (sogenannte IMSI Catcher), warnt Sie die App davor.
Alternative zur stillen SMS: Staatstrojaner ebenfalls umstritten
Polizei, BND und Verfassungsschutz wollen neben der stillen SMS auch den "Staatstrojaner" nutzen. Dabei handelt es sich um ein weiteres Werkzeug zur Kriminalitätsbekämpfung. Mit diesem Virus können die Behörden auf Smartphones weitaus mehr, als nur den Standort bestimmen.
Mit dem Staatstrojaner lassen sich Nachrichten in Messenger-Diensten wie WhatsApp, Signal oder Telegram mitlesen. Dies ist trotz Ende-zu-Ende-Verschlüsselung möglich.
Datenschützer sehen den Einsatz der stillen SMS sowie des Staatstrojaners allerdings äußerst kritisch. Zum einen ist unklar, in welchen Fällen diese Werkzeuge eingesetzt werden und wer darüber entscheidet. Außerdem meinen Kritiker, dass der Einsatz ein Verstoß gegen die Verfassung darstellen könnte.
https://praxistipps.chip.de/stille-sms-erkennen-infos-zur-geheimen-staatsueberwachung_94938
 Dust, dirt, germs and more Dust, dirt, germs and more
Howot disinfect keyboards and mices correctly, PC-Magazin.de, 07.03.2020
PC-Tastaturen und -Mäuse sind Seuchenherde, auf denen sich Keime bis zu 24 Stunden lang halten. Wie Sie Tastatur und Maus reinigen und richtig…
https://www.pc-magazin.de/ratgeber/tastatur-reinigen-desinfizieren-pc-maus-desinfizierbar-3201332.html
 Illness-prevention: Germany washes its hand collectively, where smartphones are the real germs slingshots, STERN.de, 06.03.2020 Illness-prevention: Germany washes its hand collectively, where smartphones are the real germs slingshots, STERN.de, 06.03.2020
[...] Untersuchungen zeigen, dass sich auf den Glas-Displays alle möglichen Erreger nachweisen lassen, von (Schimmel-)Pilzen über Durchfallerreger bis hin zu Grippeviren.
So gelangen Keime auf das Display
Klingt eklig, ist aber nicht überraschend. Wer erst ins Taschentuch schnäuzt und direkt im Anschluss die nächste Nachricht verschickt, muss sich über Erkältungsviren auf dem Display nicht wundern. Zudem kommen wir in der kalten Jahreszeit mit vielen Keimen in Kontakt - etwa über Türklinken, Haltegriffe im Bus oder Zapfsäulen -, über kurz oder lang landen die auf dem Smartphone.
https://www.stern.de/digital/smartphones/keimschleuder-smartphone--deshalb-sollte-man-das-telefon-reinigen-9169438.html
[...] Wie lange Erreger wie das neuartige Coronavirus auf Gegenständen überleben, hängt von der Virenlast ab, also der Menge der Erreger. Davon abgesehen spielen viele weitere Faktoren wie Temperatur, Feuchtigkeit, UV-Strahlung und Oberflächenmaterial eine Rolle. Wissenschaftler der Ruhr-Universität Bochum und der Universität Greifswald haben jüngst Forschungsergebnisse zur Überlebensdauer früherer Coronaviren wie dem Sars-Erreger unter Laborbedingungen zusammengetragen. Je nach Virenstamm und Virenlast schwanken die Werte sehr stark - bei Papier etwa zwischen unter fünf Minuten und fünf Tagen, bei Stahl zwischen acht Stunden und 28 Tagen. Auf Glas und PVC wurden Werte von rund fünf Tagen erhoben.
Die Überlebensdauer des neuartigen Coronavirus auf Oberflächen lässt sich daher nicht genau angeben. Laut Bundesinstitut für Risikobewertung (BfR) ist eine Übertragung über Oberflächen, die kurz zuvor mit Viren kontaminiert wurden, grundsätzlich "denkbar".
[...] Eine Sprecherin der Europäischen Zentralbank (EZB) erklärte, zwar könnten wie bei der normalen Grippe und wie bei anderen Oberflächen neuartige Coronaviren auf Geldscheinen "für einen begrenzten Zeitraum" überleben. Die Wahrscheinlichkeit einer Übertragung des Virus über Geldscheine sei aber "sehr niedrig im Vergleich zu anderen Oberflächen" wie etwa Türklinken, Handläufen, Lichtschaltern und Einkaufskörben.
https://www.stern.de/gesundheit/coronavirus--fragen-und-antworten-zu-infektionswegen-9166138.html
 iOS 13.5.1: iPhone is hackable: For these reasons you should update to the newest iOS-Version immediately, STERN.de, 02.06.2020 iOS 13.5.1: iPhone is hackable: For these reasons you should update to the newest iOS-Version immediately, STERN.de, 02.06.2020
Nur sehr kurz nach dem großen Corona-Update legt Apple mit einer neuen iOS-Version nach. Der Grund der Dringlichkeit: Eine kritische Lücke erlaubte weitreichenden Zugriff aufs System. Manche Nutzer sollten das Update aber sogar vermeiden.
https://www.stern.de/digital/smartphones/iphone-hackbar--aus-diesem-grund-sollten-sie-sofort-auf-die-neueste-ios-version-updaten-9284824.html
 Corona-Virus: iPhone-SE2-Keynote are in danger, PC-WELT.de, 07.03.2020 Corona-Virus: iPhone-SE2-Keynote are in danger, PC-WELT.de, 07.03.2020
Dass das Corona-Virus ernsthafte Konsequenzen für die Technik-Branche hat, mussten der MWC und Facebook am eigenen Leibe spüren.
https://www.pcwelt.de/news/Corona-Virus-Muss-Apple-die-WWDC-2020-und-iPhone-SE-Keynote-absagen-10763005.html
https://www.pcwelt.de/news/Corona-Virus-Muss-Apple-die-WWDC-2020-und-iPhone-SE-Keynote-absagen-10763005.html
Do we all get glassen?
 New studies found out, that Android-handies do collect and forward data in considerable complexity, uncut-news.ch, 14.10.2021 New studies found out, that Android-handies do collect and forward data in considerable complexity, uncut-news.ch, 14.10.2021
Secret agencies/NSA/Surveillance/BigData
Laut einer Studie, die von Wissenschaftlern des Trinity College Dublin (TCD) und der Universität Edinburgh durchgeführt wurde, sammeln mehrere Android-Handys Daten, ohne dass es eine Opt-out-Klausel gibt. In einigen Fällen werden die Daten an Dritte weitergegeben.
Prof. Doug Leith vom TCD sowie Dr. Paul Patras und Haoyu Liu von der Universität Edinburgh untersuchten die Daten, die von sechs Varianten des Android-Betriebssystems gesendet wurden, die von Samsung, Xiaomi, Huawei, Realme, LineageOS und /e/OS entwickelt wurden.
Sie fanden heraus, dass fünf der sechs herstellerangepassten Android-Varianten selbst bei minimaler Konfiguration und im Ruhezustand des Geräts erhebliche Datenmengen an den Betriebssystementwickler sowie an Dritte wie Google, Microsoft, LinkedIn und Facebook, die System-Apps vorinstalliert haben, übermittelten. Die bemerkenswerte Ausnahme war /e/OS, das keine Informationen an Dritte und praktisch keine Informationen an seine Entwickler übermittelte.
Während eine gelegentliche Kommunikation mit Betriebssystemservern zu erwarten ist, sagten die Autoren der Studie, dass die beobachtete Datenübertragung weit darüber hinausgeht und eine Reihe von Datenschutzbedenken aufwirft.
Leith sagte, er hoffe, dass die Forschungsergebnisse seines Teams als "Weckruf" für die Öffentlichkeit, Politiker und Regulierungsbehörden dienen würden.
"Ich denke, wir haben die massive und fortlaufende Datenerfassung durch unsere Telefone, für die es kein Opt-out gibt, völlig übersehen. Wir haben uns zu sehr auf Web-Cookies und schlecht funktionierende Apps konzentriert. Es besteht dringender Handlungsbedarf, um den Menschen eine echte Kontrolle über die Daten zu geben", fügte er hinzu.
Leith ist Inhaber des TCD-Lehrstuhls für Computersysteme und arbeitet auch im Forschungszentrum Connect der Science Foundation Ireland. Er hat mehrere Studien zum Thema Datenschutz und Datenerfassung durchgeführt. Eine aktuelle Studie vom März ergab, dass Android- und iPhone-Handys im Durchschnitt alle viereinhalb Minuten Daten an Google und Apple weitergeben.
Er gehörte auch zu einem Forschungsteam, das Bedenken gegen Covid-19-Apps zum Aufspüren von Kontakten äußerte, als diese zur Bekämpfung der Ausbreitung des Virus im Jahr 2020 vorgeschlagen wurden.
Laut Patras sind Praktiken zur Sammlung von Nutzerdaten "nach wie vor weit verbreitet", trotz der Schutzgesetze, die vor kurzem in mehreren Ländern, darunter viele EU-Mitgliedstaaten, Kanada und Südkorea, zum Schutz persönlicher Daten eingeführt wurden.
Noch besorgniserregender ist, dass solche Praktiken ohne Wissen der Nutzer und ohne die Möglichkeit, solche Funktionen zu deaktivieren, unter der Haube" von Smartphones stattfinden", warnte Patras.
"Datenschutzbewusste Android-Varianten sind jedoch auf dem Vormarsch, und unsere Ergebnisse sollten die marktführenden Hersteller dazu veranlassen, diesem Beispiel zu folgen.
Quelle: Data collection by Android phones should give public a ´wake-up call´
https://uncutnews.ch/neue-untersuchungen-haben-ergeben-dass-android-handys-in-erheblichem-umfang-daten-sammeln-und-weitergeben/
 Free your smartphone!, digitalcourage.de, gesehen am 08.02.2021 Free your smartphone!, digitalcourage.de, gesehen am 08.02.2021
It knows more about us as our friends and our diary together. Our smartphone knows all our likings, habits and weaknesses up in the last detail.
Contol, who has access to your smartphone!
https://digitalcourage.de/digitale-selbstsverteidigung/befreien-sie-ihr-smartphone
 Android-manufacturer enable lacks in security, trojaner-info.de, 19.02.2020 Android-manufacturer enable lacks in security, trojaner-info.de, 19.02.2020
Der deutsche Sicherheitsforscher Jann Horn, der derzeit für Googles Project Zero arbeitet, kritisiert in einem Blogpost Android-Gerätehersteller. Deren gerätespezifische Änderungen verursachen laut ihm Sicherheitslücken, die vermeidbar wären.
https://www.trojaner-info.de/mobile-security/aktuell/android-hersteller-ermoeglichen-sicherheitsluecken.html
 Dealer are allowed to keep secret about security exploits of handies, PC-WELT.de, 16.01.2020 Dealer are allowed to keep secret about security exploits of handies, PC-WELT.de, 16.01.2020
Laut einem Gerichtsurteil muss ein Händler beim Verkauf eines Smartphones nicht über bestehende Sicherheitslücken informieren.
https://www.pcwelt.de/news/Haendler-darf-Sicherheitsluecken-des-Smartphones-verschweigen-10737748.html
 US-mobile-phone-provider do sell location data, PC-WELT.de, 15.05.2018 US-mobile-phone-provider do sell location data, PC-WELT.de, 15.05.2018
Mobilprovider aus den USA verkaufen offenbar Echtzeit-Standortdaten ihrer Kunden an private Unternehmen.
https://www.pcwelt.de/a/us-mobilfunkprovider-verkaufen-ortungsdaten,3450807
 Analysis of the Chaos Computer Clubs Analysis of the Chaos Computer Clubs
The long trace of spy-software from a german company, tagesschau.de, 28.12.2019
Experten zeigen, wie eine deutsche Firma über Jahre hinweg Software entwickelt haben soll, mit der sich Menschen ausspionieren lassen. Die Staatsanwaltschaft in München ermittelt seit September gegen den Hersteller.
https://www.tagesschau.de/investigativ/ccc-spionagesoftware-101.html
Mehr zu diesem Thema
Illegaler Export von Späh-Software?, 04.09.2019, https://www.tagesschau.de/investigativ/ndr-wdr/finfisher-finspy-101.html
Deutsche Spionage-Software gegen türkische Opposition eingesetzt, 25.10.2019, https://www.tagesschau.de/ausland/spaehsoftware-tuerkei-101.html
 Two cameras, several microphones, a GPS-modul and lashings of private user data: Smartphones are the perfect eavesdropping observence-devices Two cameras, several microphones, a GPS-modul and lashings of private user data: Smartphones are the perfect eavesdropping observence-devices
Research scientist: How your Smartphone can spy you out - even if it is powered off, STERN.de, 08.02.2018
Über GPS und Co. können uns Smartphones permanent überwachen. Zum Glück kann man die Funktionen aber abschalten. Ein Forscher erklärt nun, wie man diese Sicherheitsmaßnahmen trotzdem aushebelt - und warum das kaum zu verhindern ist.
Zwei Kameras, mehrere Mikrofone, ein GPS-Modul und Unmengen private Daten der Nutzer: Smartphones sind die perfekten Überwachungsgeräte.
https://www.stern.de/digital/smartphones/so-kann-ihr-smartphone-sie-ausspionieren---obwohl-sie-alles-abgeschaltet-haben-7855612.html
https://www.stern.de/digital/computer/erpressungs-trojanern--so-schuetzen-sie-sich-vor-ransomware-6725356.html
https://www.stern.de/digital/online/datenraub--mit-diesen-7-tipps-schuetzen-sie-sich-davor-8521708.html
https://www.stern.de/tv/datenhack--warum-wurde-es-dem-taeter-so-leicht-gemacht-und-wie-kann-man-sich-schuetzen--8521650.html
https://www.stern.de/digital/smartphones/so-kann-ihr-smartphone-sie-ausspionieren---obwohl-sie-alles-abgeschaltet-haben-7855612.html
https://www.stern.de/digital/online/der-mann--der-uns-schwierige-passwoerter-einbrockte--bereut-seine-entscheidung-7577534.html
https://www.stern.de/digital/computer/erpressungs-trojanern--so-schuetzen-sie-sich-vor-ransomware-6725356.html
https://www.stern.de/digital/online/iphone-privatsphaere--mit-diesen-einstellungen-schuetzen-sie-ihre-daten-8522116.html
https://www.stern.de/tv/datenhack--warum-wurde-es-dem-taeter-so-leicht-gemacht-und-wie-kann-man-sich-schuetzen--8521650.html
https://www.stern.de/tv/gute-passwoerter-und-co---so-schuetzen-sie-sich-bestmoeglich-vor-hackerangriffen-8524324.html
 Prevent Ransomware-attacks upon cameras, PC-WELT.de, 07.12.2019 Prevent Ransomware-attacks upon cameras, PC-WELT.de, 07.12.2019
Über das PTP-Protokoll lassen einige Digitalkameras angreifen und die auf der SD-Karte gespeicherten Fotos verschlüsseln.
https://www.pcwelt.de/tipps/Ransomware-Attacke-auf-Kameras-verhindern-10701403.html
 MacOS and Windows Apps are able to make films secretly, tagesschau.de, 07.13.2022 MacOS and Windows Apps are able to make films secretly, tagesschau.de, 07.13.2022
Computer operating systems do not protect enough against spying through Apps. An experiment of BR-Data journalists and PULS Reportage is showing this. This is a security risk especially in times for HomeOffice.
Report from Sebastian Bayerl, Maria Christoph, Rebecca Ciesielski, Pia Dangelmayer, Elisa Harlan, Robert Schöffel, BR
Die Corona-Pandemie hat die Kommunikation in der Arbeitswelt grundlegend verändert: Ob morgendliche Videokonferenz oder Meeting am Nachmittag, Videocalls mit aktivierter Kamera sind für viele Arbeitnehmerinnen und Arbeitnehmer Normalität. Dabei birgt das Arbeiten von zuhause in Bezug viele Risiken für die Datensicherheit.
https://www.tagesschau.de/investigativ/br-recherche/sicherheit-homeoffice-101.html
 Camera and microphone-blocker: Google gives away useful Android-App, 02.11.2019 Camera and microphone-blocker: Google gives away useful Android-App, 02.11.2019
Jedes Smartphone ist mit einer Kamera und einem Mikrofon ausgestattet. Doch nicht immer werden diese aktiviert, wenn der Besitzer das möchte. Mit der Android-App "Kamera und Mikrofon Blocker" können gewinnen Sie mehr Kontrolle über Ihr Smartphone. Aktuell ist sie kostenlos erhältlich.
https://www.chip.de/news/Kamera-und-Mikrofon-Blocker-fuer-Android-gratis_176108100.html
 GPRS: Did mobil phone get protected badly against eavesdropping?, STERN.de, 20.06.2021 GPRS: Did mobil phone get protected badly against eavesdropping?, STERN.de, 20.06.2021
Die Verschlüsselung der ersten mobilen Internetverbindung über GPRS ließ sich jahrelang ohne viel Aufwand aushebeln, das zeigt eine aktuelle Studie. Die Forscher sind sicher: Ein Zufall kann nicht dahinter stecken.
https://www.stern.de/digital/smartphones/gprs--wurde-mobilfunk-absichtlich-schlecht-vor-abhoeren-geschuetzt--30578306.html
Might be simliar to the computer...:
 According to a study smartphones do share our data each four and a half minute, uncutnews, 31.03.2021 According to a study smartphones do share our data each four and a half minute, uncutnews, 31.03.2021
https://uncutnews.ch/laut-einer-studie-teilen-smartphones-unsere-daten-alle-viereinhalb-minuten/
 Android-Studie of Professor Leith: Google-Handies do send away twenty times more data than iPhones, CHIP, 04.04.2021 Android-Studie of Professor Leith: Google-Handies do send away twenty times more data than iPhones, CHIP, 04.04.2021
Android-malware: Howto protect users against fake-updates
https://www.chip.de/news/Brisante-Android-Studie-enthuellt-Google-Handys-geben-20-Mal-mehr-Daten-weiter-als-iPhones_183434034.html
https://www.pcwelt.de/news/Android-sammelt-laut-Studie-20-mal-mehr-Daten-als-iOS-11004792.html
 Damp for Galaxy-user: Popular smartphones do not get any monthly updates anymore, CHIP, 07.04.2021 Damp for Galaxy-user: Popular smartphones do not get any monthly updates anymore, CHIP, 07.04.2021
Samsung releases plenty of new Galaxy-Smartphones on the market each year. During this elder devices run out of support (updates).Howto get prepared for Galaxies.
https://www.chip.de/news/Daempfer-fuer-Galaxy-Smartphone-Beliebtes-Smartphone-bekommt-keine-monatlichen-Updates-mehr_181037518.html
 Soon iOS 14 exposes sniffer-Apps: But this Android-App makes it much better, CHIP, 28.07.2020 Soon iOS 14 exposes sniffer-Apps: But this Android-App makes it much better, CHIP, 28.07.2020
https://www.chip.de/news/Access-Dots-fuer-Android-App-Zugriff-auf-Kamera_182863746.html
Android: Horrible security exploit in camera-Apps of Google and Samsung, PC-WELT.de, 19.11.2019
Von einem bösen Bug in den Kamera-Apps von Samsung und Google für Android waren und sind Millionen Nutzer betroffen.
In den Kamera-Apps von Samsung und Google für Android steckt(e) eine schwere Lücke.
Die Sicherheitsexperten von Checkmarx haben am Dienstag die Details zu einer fiesen Sicherheitslücke in den Kamera-Apps für Android-Smartphone veröffentlicht. Angreifer konnten und können die Lücke missbrauchen, um ohne dem Wissen des Smartphone-Besitzers Fotos und Videos zu knipsen und dessen Standort über GPS zu ermitteln. Diese Daten können dann unbemerkt beispielsweise an einen Server gesendet werden. Schuld ist ein Fehler in den Berechtigungen, durch den sich Angreifer einen Zugriff auf die Kamera-Apps verschaffen konnten, obwohl die Android-Sicherheitsmaßnahmen dies eigentlich verhindern sollen.
Der Fehler war zunächst in der Kamera-App von Google entdeckt worden. Weitere Recherchen ergaben dann aber, dass auch die Kamera-App von Samsung betroffen ist. Konkret ermöglicht die Lücke den Angreifern folgende Angriffsszenarien:
Er kann ein Foto auf dem Gerät des Opfers knipsen und dieses per Upload an einen C&C-Server senden
Er kann ein Video auf dem Gerät des Opfers aufnehmen und dieses per Upload an einen C&C-Server senden
Er kann die GPS-Tags der zuletzt erstellten Fotos auslesen und somit den Standort des angegriffenen Smartphones ermitteln und verfolgen.
Er kann automatisch Aufnahmen von Telefongesprächen erzeugen, wobei per Video das Opfer gefilmt wird. Das Gespräch sowohl des Opfers als auch des Gesprächspartners kann als Audio-Datei aufgezeichnet und an einen C&C-Server gesendet werden.
https://www.pcwelt.de/news/Android-Fiese-Sicherheitsluecke-in-Kamera-Apps-von-Google-und-Samsung-10704665.html
 Data security: Your handy might listen to you - and you do not have inkling of it, STERN.de, 02.03.2019 Data security: Your handy might listen to you - and you do not have inkling of it, STERN.de, 02.03.2019
Es heißt immer wieder, dass unsere Smartphones alles mithören. Unser Autor glaubt zu wissen, dass dem so ist. Sein Handy hört ihn ab. Doch was kann er dagegen tun?
Die "New York Times" (NYT) hat 1000 Apps identifiziert, die tatsächlich im Hintergrund mithören. Wie können wir uns davor schützen, dass unser Handy uns abhört?
Es war 4 Grad draußen, handschuhkalt würde ich sagen. Vor allem auf dem Rad, da fällt dir an der Ampel schnell mal ein Finger ab, so kalt war es. Ich sagte der Frau, mit der ich an der Ampel stand, dass ich einen verdammt langen Heimweg auf dem Rad vor mir hätte und sie sagte: "Hier, nimm meine Radhandschuhe." Ich habe dann noch zweimal laut drüber nachgedacht - und BÄM.
Besonders Kinder sollten nicht zu viel Zeit am Handy oder vor dem Bildschirm verbringen.
Quadratische Augen garantiert - was zu viel Zeit vor dem Bildschirm mit uns macht
Da war sie, die Werbeanzeige im Feed am nächsten Morgen. Super Fahrradhandschuhe.
Jetzt kaufen.
[...] Denn ich weiß auch, dass unsere Daten auf unseren Geräten ständig analysiert werden (Google und Facebook machen da keinen Hehl daraus) und so unwahrscheinlich ist es dann auch wieder nicht, dass die eins und eins zusammenzählen.
Handy-Besessenheit: Wenn die Sucht nach Bestätigung dich auffrisst
Das war schon bei meinen wasserdichten Socken so, die mir Instagram so plötzlich angeboten hatte, nachdem ich eine Woche darüber gesprochen hatte, wie nass meine Füße immer auf dem Segelboot waren, und auch bei meiner Mini-Angel in Stiftform - die göttliche Antwort auf meine Reue, nie eine Angel dabei zu haben, wenn ich grad eine bräuchte. Das Internet ist voll von Erfahrungsberichten, die versuchen diese "Zufälle" zu verstehen. Bilden wir uns das wirklich nur ein?
 More than 1000 Apps do listen in the background More than 1000 Apps do listen in the background
Die "New York Times" (NYT) hat 1000 Apps identifiziert, die tatsächlich im Hintergrund mithören, meistens sind es Spiele. Wenn wir das Handy aktivieren, hören ja sowieso alle mit, das muss man dazu sagen. Bin ich dann paranoid, wenn ich glaube, dass mir irgendein Roboter ständig durch meine Frontkamera zuguckt und sich über meinen Gesichtsausdruck schlapplacht? Oder realistisch?
Die "NYT" hat herausgefunden, dass manche Apps eine Software namens "Alphonso" nutzen, die dem Fernseher oder Kino im Hintergrund zuhört, um zu erkennen, welche Sendung geguckt wird (was einen dann wiederum in eine nette Werbekategorie packt). Shazam arbeitet hier fleißig mit. Die wurden von Apple gekauft. Alle machen mit. Und manche Software kommuniziert sogar mit dem Fernseher auf Frequenzen, die wir nicht hören können. Durch die Hosentasche hindurch. Durch die Handtasche. Vielleicht mehr schlecht als recht.
Meistens wird mir noch genau das gleiche Produkt beworben, das ich gerade gekauft habe. Das ist nicht schlau. Aber es passiert alles dennoch. Um Preise zu individualisieren, um näher an den Kunden zu rücken, um präziser werben zu können - aber auch, um Bedürfnisse beeinflussen zu können.
Was können wir tun?
Zuerst einmal uns dessen bewusst werden! Die unsexy Variante der Sicherheit ist wie eh und je: abschalten. Also Kamerazugriff verweigern, Mikrofonzugriff verweigern. Aber wer will das schon. Wir wollen ja Sprachnachrichten und Selfies. Das ist der Deal, solange es noch kein Kopplungsverbot gibt, also das Recht, einen Dienst zu nutzen, ohne Datenverarbeitung.
Dieser Screenshot einer SMS von einer Neunjährigen an ihren toten Opa macht gerade auf Twitter die Runde
"Ich liebe dich, Opa"
SMS ins Jenseits: Vater entdeckt rührende Nachricht seiner Tochter in altem Handy
Bei Geräten wie Alexa und Google Home wird empfohlen, ab und zu mal nachzusehen, ob sie gerade mitschneiden.
[...] Wir können uns empören oder nicht. Der Entwicklung stellen oder schweigend weiter User sein. Klar wollen wir nichts, was hinter unserem Rücken passiert. Aber andererseits holen wir uns seit neuestem DIE Profi-Zuhörer in unsere Wohn- und Schlafzimmer. In unsere Küchen und auf unsere Toiletten. Geräte, die immer und überall mithören. Absichtlich. Ich für meinen Teil freue mich ja jedes Mal, wenn mich Siri wieder nicht versteht. Die Welt geht sehr wahrscheinlich unter. Oder auch nicht. Aber bis dahin: Alexa, spiel Despacito!
https://www.stern.de/neon/wilde-welt/gesellschaft/dein-handy-hoert-wahrscheinlich-zu---und-du-hast-keine-ahnung-8427658.html
 Millions of user affected Millions of user affected
Android
Administative appeal against Google´s tracking practise, netzpolitik.org, 08.04.2021
Max Schrems und seine Datenschutzplattform noyb gehen gegen die womöglich illegale Trackingpraxis von Google vor. Betroffen sind Millionen Android-Nutzer:innen in ganz Europa.
Max Schrems hat bei der französischen Datenschutzbehörde eine Beschwerde gegen Googles "Android Advertising Indentifier" (AAID) eingereicht. Mithilfe der Werbe-ID tracked Google Daten, die Aufschluss über das Online- und Offlineverhalten von Android-Nutzer:innen geben. Laut noyb, der von Schrems gegründeten Datenschutzplattform, sei für die Verwendung des Trackers die eindeutige Zustimmung der Nutzer:innen erforderlich. Dieser Verpflichtung komme Google jedoch nicht nach.
Die Werbe-ID besteht aus einer Identifikationsnummer, mit der Smartphones eindeutig identifiziert werden können. Neben Google nutzen auch Drittanbieter die Werbe-ID, um Werbeprofile zu erstellen, personalisierte Werbung zu schalten und die Konsumgewohnheiten der Nutzer:innen zu analysieren.
Millionen Menschen betroffen
Für Stefano Rosetti, Datenschutzjurist bei noyb, sei das Ausmaß der Überwachung verblüffend: "Fast alle Android-Nutzerinnen scheinen von dieser Technologie betroffen zu sein," betonte der Anwalt in einem Gespräch mit der Financial Times. Er hoffe deshalb auf ein hartes Durchgreifen der französischen Datenschutzbehörde.
https://netzpolitik.org/2021/android-beschwerde-gegen-googles-trackingpraxis/
 Smartphone-Tracking: Smartphone-Tracking:
How data of commercial apps are captured by the state, netzpolitik.org, 04.12.2020
Der norwegische Journalist Martin Gundersen zeichnet in einer großen Recherche nach, wie seine Daten von genutzten Apps über Umwege in die Hände eines Datenbrokers kamen, der mit US-Polizeibehörden zusammenarbeitet. Datenschützer halten diese Form der Überwachung für neu und beispiellos.
https://netzpolitik.org/2020/smartphone-tracking-wie-daten-von-kommerziellen-apps-an-den-staat-gelangen/
 States-trojans, banking-malware, data catapults, screw-apps: The dangers for handy user are great, Focus, 23.05.2014. States-trojans, banking-malware, data catapults, screw-apps: The dangers for handy user are great, Focus, 23.05.2014.
Das sind die gefährlichsten Apps der Welt:
Die Instrumentalisierung von Smartphones gegen ihre Nutzer ist längst trauriger Alltag, das verdeutlichen nicht nur die Skandale um Kanzlerinnen- und Kanzlerhandys.
Beispiele zeigen, welche Macht jemand erlangt, der von den Überwachungsmöglichkeiten moderner Smartphones Gebrauch macht: Die Geräte funken ihre Position laufend an Sendemasten. GPS erlaubt eine genaue Ortung. Kontaktverzeichnis, Mails, SMS, Chat- und Telefonlisten dokumentieren, mit wem wir wann worüber gesprochen haben. Daten, die wir in Apps speichern; Spuren, die wir im Browser hinterlassen; sie alle zeichnen ein Bild davon, was uns interessiert und wie wir denken. Ein Traum für Datensammler - ein Albtraum für unbedarfte Nutzer. Wer sich eine der in Umlauf befindlichen Trojaner-Apps einfängt, verwandelt sein Smartphone in eine hinterhältige Wanze, die Mikrofon und Kamera anzapft und Eingaben mitschneidet. Der Internetaktivist und Sicherheitsexperte Jacob Appelbaum betont, dass Geheimdienste vor nichts zurückschrecken und selbst harmlose Dinge wie USB-Kabel und Tastaturen in Überwachungsinstrumente verwandeln.
http://www.focus.de/digital/computer/chip-exklusiv/smartphone-sicherheit-das-sind-die-gefaehrlichsten-apps-der-welt_id_3670987.html
 Handy- and MS Windows - Trojaner of your country unlimited, Tagesschau, 2013 Handy- and MS Windows - Trojaner of your country unlimited, Tagesschau, 2013
Zu den mächtigsten und gefährlichsten Spionagetools zählen die sogenannten Staatstrojaner, die private Unternehmen entwickeln und an Behörden im In- und Ausland verkaufen. Reibach mit diesen Überwachungsprogrammen machen vor allem deutsche Firmen wie DigiTask, Trovicor und Gamma International. Die Tools sollen ausschließlich der gezielten Verbrechensbekämpfung dienen. Was jedoch des einen Terrorist, ist des anderen Aktivist, und so verwundert es kaum, dass mit dem Tool auch Journalisten und Bürgerrechtler in Bahrain und Äthiopien attackiert wurden .Deshalb haben Menschenrechtsorganisationen wie Reporter ohne Grenzen eine OECD-Beschwerde gegen Gamma International sowie die ehemalige Siemens-Tochter Trovicor eingereicht - wegen Mithilfe bei Menschenrechtsverletzungen. Warnung des BKA: Hacker spionieren Smartphones zunehmend über manipulierte Apps aus. Ziel der Attacken sei häufig das Online-Banking mittels mTan-Verfahren. Die Zahl der Angriffe auf Smartphones mit dem gängigsten Trojaner habe sich fast versechsfacht.
 New warning against Android: Now Google sends SMS to Google itself, CHIP, 12.14.2019 New warning against Android: Now Google sends SMS to Google itself, CHIP, 12.14.2019
User have noticed in the background of Android SMS received and even sent secretly. But this is not the cause of a system errror. Google itself is the recipient and sender of such messages.
Ob das allerdings den Usern so wirklich schmeckt, ist eine andere Frage. Immerhin greift Google hier direkt in das System ein und verschickt die SMS heimlich im Hintergrund. Inwiefern Kosten für den Android-Nutzer entstehen, ist nicht geklärt. Vor allem dann, wenn der User vielleicht zufällig im Ausland ist und Roaming-Gebühren entfallen würden. Wer keine Lust auf die geheimen SMS von Google hat, kann natürlich die Berechtigungen für Google anpassen oder die Bestätigung der Telefonnummer ablehnen.
https://www.chip.de/news/Neuer-Warnhinweis-fuer-Android-Google-sendet-jetzt-SMS-an-sich-selbst_178043250.html
 Serious hard allegations have been made against Google: Did important settings for Android´s data-protection get hidden intentionally?, CHIP, 31.05.2021 Serious hard allegations have been made against Google: Did important settings for Android´s data-protection get hidden intentionally?, CHIP, 31.05.2021
Im Netz sind Gerichtsdokumente aufgetaucht, die darauf hinweisen, dass Google wichtige Datenschutzoptionen bewusst möglichst tief in den Einstellungen von Android versteckt hat, damit Nutzer diese nach Möglichkeit nicht nutzen. Auch bei Dritthersteller habe man offenbar versucht diese zu überreden, die Optionen zu verbergen.
https://www.chip.de/news/Schwere-Vorwuerfe-gegen-Google-Haben-die-Android-Macher-wichtige-Datenschutzeinstellungen-bewusst-versteckt_183638748.html
 Privacy-investitgation Privacy-investitgation
More than 1300 Android-Apps do collect private data hiddenly - even if you forbid it, STERN.de, 07.11.2019
Sicherheitsforscher demonstrierten, dass mehr als 1000 Android-Apps unerlaubt personenbezogene Daten speichern. Die App-Anbieter hebelten die Sicherheitsmaßnahmen mit kreativen Methoden aus.
https://www.stern.de/digital/smartphones/mehr-als-1300-android-apps-sammeln-private-daten---sogar-dann--wenn-man-es-verbietet-8793248.html
 Android 10: Plenty of security exploits, trojaner-info.de, 08.31.2019 Android 10: Plenty of security exploits, trojaner-info.de, 08.31.2019
193 exploits were found out!
Es haben sich zahlreiche Sicherheitslücken in Googles Mobile Plattform angesammelt. Nun wollen die Entwickler in der kommenden Version nicht nur mit neuen Features aufwarten, sie wollen auch eine Unmenge von angestauten Sicherheitslecks auskehren.
https://www.trojaner-info.de/mobile-security/aktuell/android-10-auskehr-zahlreicher-sicherheitsluecken.html
 1325 Android-Apps bypass set access-rights, PC-WELT.de, 07.09.2019 1325 Android-Apps bypass set access-rights, PC-WELT.de, 07.09.2019
Über 1000 Android-Apps umgehen die persönlichen Zugriffsberechtigungen der Nutzer und sammeln weiterhin fleißig Daten.
https://www.pcwelt.de/news/Ueber-1000-Android-Apps-umgehen-Zugriffs-Berechtigungen-sammeln-Daten-10625000.html
Android-Apps do have the Tracker-epidemic, PC-WELT.de, 03.27.2019
Die Mehrzahl der untersuchten Android-Apps enthält Tracker, die Nutzungsdaten an Google und auch an Drittfirmen senden.
https://www.pcwelt.de/news/Android-Apps-haben-die-Tracker-Seuche-10562857.html
 Eavesdroped and overworked by unknown back: single-image-processing in four-dimensional animations and videos Eavesdroped and overworked by unknown back: single-image-processing in four-dimensional animations and videos
Unwanted "customer service", Gooken-witness report from 11.19.2019
Jemand (Name und Anschrift sind der Red. bekannt) berichtet von der unbeauftragten Überarbeitung von seinen mit der Kamera von Samsung geschossenen und dort gespeicherten Fotos (Bilder, images) in ganze Animationen bzw. Film-Sequenzen.
Dabei kam es insbesonders bei herkömmlichen Personenaufnahmen zu "natürlichen" Bewegungen abgelichteter Gesichts- und Körperstellen, auf denen sich Wolken bewegten und Pflanzen mit dem Wind drehten usw..
Möglich ist das alles durch eine neuartige App für Smartphones auf Basis der KI, welche grobe Bildsequenzen, aber bereits auch unzusammenhängende Einzelbilder (herkömmliche Fotos) in ausführliche Animationen bzw. Videos verwandeln kann.
https://www.pcwelt.de/international/Bilder-in-Videos-verwandeln-So-geht-s-10734992.html
 Android-Patchday: DoS-attack could lame Smartphones permanently, trojaner-info, 12.09.2021 Android-Patchday: DoS-attack could lame Smartphones permanently, trojaner-info, 12.09.2021
Attackers could attack Android-devices and provide higher user privliges or access sealed off information. Android-user should upgrade to the actual Android (Patchlevel 2021-09-01 or 2021-09-05).
https://www.trojaner-info.de/mobile-security/aktuell/android-patchday-dos-attacke-koennte-smartphones-dauerhaft-lahmlegen.html
Secret agencies/NSA/surveillance/BigData
Israelish company for spyware used access points of ALL IPHONE-DEVICES, in order to implant"Pegasus"-malware, uncut-news.ch, 09.14.2021
Die Gruppe für digitale Rechte CitizenLab hat eine Schwachstelle entdeckt, die es dem israelischen Spionageunternehmen NSO Group ermöglichte, seine Pegasus-Malware auf praktisch allen iPhones, Macs und Apple Watch-Geräten zu installieren.
CitizenLab enthüllte die Schwachstelle am Montag, eine Woche nachdem sie sie durch die Analyse des Telefons eines saudischen Aktivisten, das mit der Malware infiziert worden war, entdeckt hatte. Die Entdeckung wurde der Öffentlichkeit bekannt gegeben, kurz nachdem Apple ein Update veröffentlicht hatte, um die Sicherheitslücke zu schließen.
Die Schwachstelle ermöglichte es den Kunden der NSO Group, als .gif-Dateien getarnte bösartige Dateien an das Telefon einer Zielperson zu senden, die dann "eine Integer-Überlaufschwachstelle in Apples Bildwiedergabebibliothek" ausnutzten und das Telefon für die Installation der inzwischen berüchtigten Malware "Pegasus" der NSO Group öffneten.
Es handelt sich dabei um eine so genannte "Zero-Click"-Schwachstelle, d. h. der Zielnutzer muss nicht auf einen verdächtigen Link oder eine Datei klicken, um die Malware auf sein Gerät zu bringen.
Den Forschern zufolge waren zwar die meisten Apple-Geräte anfällig, aber nicht alle, die von der Spyware betroffen waren, wurden auf diese Weise angegriffen. Stattdessen verkaufte die NSO Group ihre Malware an Kunden in aller Welt, die damit die Telefone von rivalisierenden Politikern, Journalisten, Aktivisten und Wirtschaftsführern ausspionierten.
https://uncutnews.ch/israelische-spionagetechnik-firma-nutzte-sicherheitsluecke-auf-allen-iphone-geraeten-um-pegasus-malware-zu-implantieren/
 Trojan "Pegasus" Trojan "Pegasus"
How authoritarian companies eavesdrop their opponents, tagesschau.de, 18.07.2021
[...] "The truth is, that technologies of the NSO Group have helped to prevent terror attacks, weapon force, car-explosion and suicidal booby traps", told us the israeli company on request. Their products woulrd used daily by authoritatives to smash "pedophiles-, sex- and drug dealer rings and to locate missed and kidnaped children", so the company would be in a life aiding mission.
https://www.tagesschau.de/investigativ/ndr-wdr/spaeh-software-pegasus-projekt-101.html
 Spying software Spying software
Market out of controle, tagesschau.de, 19.07.2021
Companies do earn a lot of money with digital instruments for surveillance. Trotz internationaler Forderungen zeigen viele Länder wenig Ehrgeiz, die Geschäfte zu reglementieren.
Unter Autokraten ist Spionagesoftware eine beliebte Ware, etwa um Oppositionelle, kritische Journalisten oder Menschenrechtler auszuspionieren und zu unterdrücken. Diese digitalen Waffen sind einfach zu beschaffen. Die Staaten müssen keine eigenen Systeme entwickeln. Etliche Firmen weltweit bieten modernste Überwachungstechnologien zum Kauf an.
Mit Hilfe der Programme können fremde Computer oder Handys ausgelesen oder der Standort ermittelt werden. Manche ermöglichen es auch, das Mikro oder die Kamera unbemerkt vom Nutzer einzuschalten und so das Gerät als Wanze zu benutzen. Auch automatische Gesichtserkennungen funktionieren immer zuverlässiger. Der Markt mit diesen Technologien ist in den vergangenen Jahren enorm gewachsen. Experten gehen von einem Milliarden-Geschäft aus.
https://www.tagesschau.de/investigativ/ndr-wdr/spaeh-software-pegasus-markt-101.html
 Howto identify "Stille SMS", CHIP, 29.10.2019 Howto identify "Stille SMS", CHIP, 29.10.2019
Bei einer stillen SMS wird Ihr Smartphone vom Verfassungsschutz geortet. Erkennen können Sie die stille SMS normalerweise nicht. Denn Sie erhalten weder ein akustisches Signal, noch eine Benachrichtigung. Trotzdem können Sie Vorkehrungen treffen, um eine stille SMS zu erkennen.
[...] Mit einer stillen SMS (auch Silent SMS oder Stealth Ping) kann der Verfassungsschutz den Aufenthaltsort des Smartphone-Besitzers herausfinden, ohne dass dieser etwas davon merkt.
Zwar ist die Ortung nicht auf den Meter genau, sondern bezieht sich auf die Mobilfunkzellen, in denen das Handy sich einwählt. Dennoch können mit dieser Methode ausführliche Bewegungsprofile erstellt werden.
[...] Stille SMS per App erkennen - kostenloser Download!
Verhindern können Sie den Empfang einer stillen SMS nur, wenn das Smartphone ausgeschaltet ist und Akku und SIM-Karte entfernt sind. Es gibt aber eine App, die Ihnen dem Empfang stiller SMS anzeigt:
Die kostenlose Android-App SnoopSnitch zeigt Ihnen an, wenn Sie eine stille SMS erhalten haben. Für iOS gibt es so etwas leider nicht.
Unklar ist dann aber noch immer, von wem genau Sie die stille SMS erhalten haben. Das werden Sie aber wohl nie erfahren, wenn nicht eines Tages der Verfassungsschutz oder die Polizei vor der Tür steht.
Auch wenn sich Kriminelle als Funkmast ausgeben und in Wahrheit nur Daten und Gespräche abschöpfen wollen (sogenannte IMSI Catcher), warnt Sie die App davor.
Auf der nächsten Seite zeigen wir die besten Sicherheits-Apps zum verschlüsselten Chatten und gegen böse Viren.
https://praxistipps.chip.de/stille-sms-erkennen-so-gehts_94938
 Misgivings against the use of mobile devices in the public health, trojaner-info.de, 13.12.2020 Misgivings against the use of mobile devices in the public health, trojaner-info.de, 13.12.2020
Dies ergab die weltweite SOTI-Studie "Critical Technology for Critical Care: The State of Mobility in Healthcare 2020/21". Darüber hinaus klagen 81 Prozent (77 Prozent in Deutschland) der Befragten aus dem Gesundheitswesen über Probleme bei Systemen, die für die Patientenversorgung im Einsatz sind.
https://www.trojaner-info.de/mobile-security/aktuell/sicherheitsbedenken-beim-einsatz-mobiler-geraete-im-gesundheitswesen.html
Security lacks in TikTok, 08.05.2020
TikTok, der anfällige Riese? Check Point® Software Technologies Ltd. (NASDAQ: CHKP), ein weltweit tätiger Anbieter von Cyber-Sicherheitslösungen, nahm die Video-App TikTok mehrfach unter die Lupe und entdeckte mehrere Schwachstellen darin. Über zwei Milliarden Mal wurde TikTok heruntergeladen, entsprechend groß ist die Zahl potentieller Opfer eines Hacker-Angriffs.
https://www.trojaner-info.de/mobile-security/aktuell/sicherheitsluecken-bei-tiktok.html
Video-App
Lacks in security in TikTok enables hijacking accounts, netzpolitik.org, 07.03.2020
Einem Freiburger gelang es im März, fremde Profile in der Video-App TikTok komplett zu übernehmen. Dafür musste er gar nicht einmal besonders versiert vorgehen, sondern nur Informationen auslesen, die TikTok selbst herausgab.
https://netzpolitik.org/2020/video-app-sicherheitsluecke-bei-tiktok-erlaubte-uebernahme-von-accounts/
 Connecting phones to the Fritzbox, PC-WELT.de, 09.29.2019 Connecting phones to the Fritzbox, PC-WELT.de, 09.29.2019
DECT- mobiles, analogous and ISDN-phones, fax and answering machine - the Fritzbox cares for everything around the phone..
https://www.pcwelt.de/ratgeber/Fritzbox-als-Telefonzentrale-einrichten-9915157.html
microphone, loud speaker, USB-port, USB-cable and USB-net-adapter for akku-reload
Android-Malware for sale expand within the Dark Net, trojaner-info.de, 17.01.2021
Die Sicherheitsforscher von Check Point haben neue, gefährlichere Malware im Dark Net entdeckt.
Check Point Research beobachtet unter anderem die Bewegungen und Aktivitäten von Malware-Anbietern im Dark Net. Dabei ist den Forschern aufgefallen, dass nicht nur alte Bekannte wieder auftauchen, sondern diese mit neuen Strategien an die Vermarktung ihrer eigenen Schad-Software herangehen.
https://www.trojaner-info.de/mobile-security/aktuell/verkaeufe-von-android-malware-expandieren-im-dark-net-8158.html
Privacy investigation
More than 1300 Android-Apps do secretly collect private datas - even if you forbid it, STERN.de, 07.11.2019
Sicherheitsforscher demonstrierten, dass mehr als 1000 Android-Apps unerlaubt personenbezogene Daten speichern. Die App-Anbieter hebelten die Sicherheitsmaßnahmen mit kreativen Methoden aus.
https://www.stern.de/digital/smartphones/mehr-als-1300-android-apps-sammeln-private-daten---sogar-dann--wenn-man-es-verbietet-8793248.html
Android-user must be careful: Experts warn against 94 Millionen mailicous Apps, CHIP, 10.11.2019
IT-Sicherheitsexperten haben in Googles Play Store erhältliche Android-Apps auf die Probe gestellt und kommen zu einem erschreckenden Ergebnis: Inzwischen sind knapp 100 Millionen Apps bekannt, die mit Schadsoftware verseucht sind. Auch wenn die Anzahl neuer Ad-,Mal- oder Spyware im ersten Halbjahr 2019 zurückging, ist dies kein Anzeichen für eine entspannte Situation.
[...] Insgesamt ist die Anzahl der bekannten Software-Apps, die mit Malware und Co. versetzt worden sind, damit auf 94,2 Millionen angewachsen. Das Bedrohungspotential für den durchschnittlichen Android-Nutzer ist daher immer noch als sehr hoch einzuschätzen. Wie PSW-Geschäftsführerin Patrycja Tulinska betont, ist für die extreme Verbreitung der Schadware nicht nur die spezielle Fragmentierung des Android-Systems verantwortlich.
good luck to get this smartphone model totally for free from someone, who ought so foolish getting a better one
https://www.chip.de/news/Android-Nutzer-muessen-vorsichtig-sein-Experten-warnen-vor-94-Millionen-schaedlichen-Apps_176477081.html
 Smartphones sind nach wie vor ein attraktives Ziel für Cyberkriminelle. Lukrativ sind insbesondere Adware, Ransomware und Banking-Trojaner. So überrascht es nicht, dass inzwischen schon knapp 95 Millionen böswillige Android-Apps bekannt sind. Das ist zwar nur ein Bruchteil der Schädlinge, die auf Windows ihr Unwesen treiben, aber dennoch durchaus eine ernstzunehmende Gefahr. Smartphones sind nach wie vor ein attraktives Ziel für Cyberkriminelle. Lukrativ sind insbesondere Adware, Ransomware und Banking-Trojaner. So überrascht es nicht, dass inzwischen schon knapp 95 Millionen böswillige Android-Apps bekannt sind. Das ist zwar nur ein Bruchteil der Schädlinge, die auf Windows ihr Unwesen treiben, aber dennoch durchaus eine ernstzunehmende Gefahr.
https://www.pc-magazin.de/vergleich/sicherheit-android-smartphones-apps-vergleichstest-3201291.html
1325 Android-Apps do bypass access-rights, PC-WELT.de, 07.09.2019
Über 1000 Android-Apps umgehen die persönlichen Zugriffsberechtigungen der Nutzer und sammeln weiterhin fleißig Daten.
https://www.pcwelt.de/news/Ueber-1000-Android-Apps-umgehen-Zugriffs-Berechtigungen-sammeln-Daten-10625000.html
Android-Apps have got the tracker-epidemic-plague, PC-WELT.de, 03.27.2019
Die Mehrzahl der untersuchten Android-Apps enthält Tracker, die Nutzungsdaten an Google und auch an Drittfirmen senden.
https://www.pcwelt.de/news/Android-Apps-haben-die-Tracker-Seuche-10562857.html
England
Police evaluates too many handies without law foundation, netzpolitik.org, 26.06.2020
Past massice critics the english data protection authority has take a view upon the theme handy-evalutation. Result: The police takes to many data out of the phones and stores them for a too long time - almost without law foundation.
https://netzpolitik.org/2020/england-polizei-handyauswertung-untersuchung/
Don´t use smartphones, restoreprivacy.com
As we´ve covered before on Restore Privacy, every "smart" device is a data collection tool for corporate entities (and their surveillance partners).
Smartphones are especially vulnerable to browser fingerprinting. A team of researchers at Cambridge published a paper highlighting how smartphones can be fingerprinted using internal sensors - and there´s nothing the user can do about it.
The paper delves into the technical details, but here´s a brief overview of their findings:
The attack can be launched by any website you visit or any app you use on a vulnerable device without requiring any explicit confirmation or consent from you.
The attack takes less than one second to generate a fingerprint.
The attack can generate a globally unique fingerprint for iOS devices.
The calibration fingerprint never changes, even after a factory reset.
The attack provides an effective means to track you as you browse across the web and move between apps on your phone.
Unfortunately, there´s nothing you can do about this attack - short of getting rid of your smartphone - and you are entirely dependent on the company to fix the problem with software updates. While Apple has apparently patched this attack vector with iOS 12.2, Google (Android) is still "investigating" the issue and has not fixed anything.
If you were thinking about ditching the "smart" phone, this research provides yet another reason to do it.
https://restoreprivacy.com/browser-fingerprinting/
Only hard to remove smartphone-trojan: Aggressive Android-malware survives even the hardware-reset, CHIP, 15.04.2020
https://www.chip.de/news/Fast-unloeschbarer-Smartphone-Trojaner-Android-Malware-uebersteht-sogar-den-Werksreset_182614129.html
 Open letter to Google Open letter to Google
Privatsphäre should be no luxury anymore, netzpolitik.org, 08.01.2020
Preinstalled Apps on Android-smartphones threaten the privacy of their user. More than 50 not-profit-non-government-organziations summon Google to change this.
https://netzpolitik.org/2020/privatsphaere-soll-kein-luxusgut-bleiben/
 New option in WhatsApp: Extended chat-data-protection: Click onto each account profilel:, Text by Gooken, 07.26.2025 New option in WhatsApp: Extended chat-data-protection: Click onto each account profilel:, Text by Gooken, 07.26.2025
- Medien werden nicht automatisch in der Galerie des Geräts gespeichert
- Nachrichten werden nicht für KI-Funktionen wie die Erwähnung in @Meta-AI verwendet.
- Chat-Exporte werden deaktiviert.
Die Aktivierung erfolgt durch den dort folgenden Schieberegler nach rechts.
Behalten Sie sich künftig wichtige Änderungen in WhatsApp vor!
BKA can readout WhatsApp, tagesschau.de, 21.07.2020
Verschlüsselte Kommunikation stellt die Sicherheitsbehörden vor große Probleme. Nach Recherchen von WDR und BR kann das BKA jedoch längst Chats über WhatsApp mitlesen - über eine reguläre Funktion.
https://www.tagesschau.de/investigativ/wdr/bka-whatsapp-101.html
 All WhatsApp-user should do it: Strategy against the data common octopulus, CHIP, 12.05.2023 All WhatsApp-user should do it: Strategy against the data common octopulus, CHIP, 12.05.2023
Ob man es will oder nicht, wer ein Handy hat, hat in der Regel auch WhatsApp. Doch Facebook zapft dabei fleißig Daten ab. Eine gute Idee sind alternative Messenger. Doch auch WhatsApp können Sie datensparsamer nutzen. Das sind die wichtigsten Tipps dazu.
[...] Hinter WhatsApp steht Facebook bzw. Meta und das ist eine der größten Datenkraken der Welt. Kritik daran, dass über WhatsApp jede Menge Daten abfließen, kommt immer mal wieder auf, ebbt dann aber ebenso schnell wieder ab und zumindest merkt man nicht, dass WhatsApp in großem Stil Nutzer verlieren würde.
Trotzdem ist unser wichtigster Tipp: Nutzen Sie WhatsApp-Alternativen wie Signal oder Threema so oft es geht, weil diese Messenger viel datensparsamer sind.
Doch WhatsApp ist so weit verbreitet, dass man kaum daran vorbei kommt. Viele Familien nutzen es, genauso Firmen, Sportvereine, Schulen und und und. Die Wahrscheinlichkeit ist groß, dass viele Nutzer WhatsApp gar nicht komplett verlassen können, weil sie irgendwo doch noch in einer oder meist mehreren Chat-Gruppen festhängen.
[...] doch die Verschlüsselung allein deckt nicht alles ab, folgende Sicherheitstipps sind empfehlenswert:
Updates: Keine Frage, in Apps stecken Sicherheitslücken, die mit Updates behoben werden und das ist bei WhatsApp nicht anders. Ergo sollten Sie auch immer die aktuellsten WhatsApp-Versionen einsetzen. Die App-Updates sind Sache des Betriebssystems, Android und iOS bieten komfortable Update-Automatiken. Für WhatsApp Web reicht ein regelmäßiger Reload des Browser-Tabs, wenn die Web-App auf ein geladenes Update hinweist.
Sicherheitsmitteilungen: In den WhatsApp-Einstellungen im Bereich "Konto" gibt es das Untermenü "Sicherheitsmitteilungen". Aktivieren Sie "Sicherheitsmitteilungen auf diesem Telefon anzeigen", dann werden Sie informiert, wenn Kontakte WhatsApp neu installiert haben oder sich die Rufnummer geändert hat. Ziel der Übung ist es, durch die Nachricht dafür sensibilisiert zu werden, dass sich die Verschlüsselung geändert hat. Denkbar wäre es, dass Unbefugte das WhatsApp-Konto des Kontakts übernommen haben. Sie können den Kontakt auf anderen Wegen, etwa per Mail oder Anruf, fragen, ob er oder sie ein neues Handy hat.
Verifizieren per QR-Code: Trifft man sich im wirklichen Leben mit einem WhatsApp-Kontakt, was durchaus vorkommen kann, dann kann man einen WhatsApp-Chat per QR-Code verifizieren. Das klappt über den Chat durch Tippen auf den Kontaktnamen. Dann dort in den Kontaktinfos auf "Verschlüsselung" tippen und den QR-Code vom anderen Handy abscannen.
Kontosicherheit: In den WhatsApp-Einstellungen im Bereich "Konto" sollten Sie die "Verifizierung in zwei Schritten" einschalten. Damit schützen Sie das WhatsApp-Konto durch eine sechsstellige PIN.
Wenn Ihnen das bekannt vorkommt, dann haben wir hier einige Tipps parat, um WhatsApp sicherer und möglichst datensparsam zu nutzen.
Beim Datenschutz nachjustieren, das klappt in WhatsApp auch in kleinem Umfang, doch ein paar Probleme sind hausgemacht und schwer oder nicht zu umschiffen. Ein Merkmal von WhatsApp ist zum Beispiel, dass es sich die gespeicherten Kontaktinfos krallt und diese auf seine eigenen Server lädt.
Damit kann man die eigenen Kontakte komfortabel bei WhatsApp erreichen, man pumpt aber sämtliche Infos unverschlüsselt in die Cloud, ein hausgemachtes Datenschutz-Drama. Was eine gute Sache ist: Nutzen Sie den Datenschutz-Check, der in den "Einstellungen" unter "Datenschutz" angezeigt wird. Nachjustieren lässt sich an folgenden Stellen:
Online-Status: Sie können Ihren Online-Status in den Datenschutz-Einstellungen verstecken. Wenn Sie die Option "Zuletzt Online / Online" öffnen, können Sie festlegen, wer Ihren Status sehen kann - Sie können zwischen alle, Ihren Kontakten, oder niemand wählen. Es lassen sich auch Ausnahmen festlegen, damit nur bestimmte Kontakte den Status nicht sehen.
Geteilte Infos: Außerdem können Sie unter "Datenschutz" festlegen, welche anderen Infos über Sie sichtbar sind. Vermeiden Sie dort die Einstellung "Jeder", am restriktivsten ist hier "Niemand", bei Gruppen kann man auf den ersten Blick nur auf "Kontakte" eingrenzen. Über die Funktion "Meine Kontakte außer" können Sie aber auch alle Kontakte ausnehmen. Beim "Status" wählen Sie "Teilen nur mit" und geben dann einfach keinen Kontakt an. Auch geteilte Live-Standorte können Sie dort prüfen und abstellen.
Lesebestätigungen: Für manche Nutzer sind die Lesebestätigungen praktisch, für andere verraten sie zu viel. Es gibt eine eigene Einstellung unter "Datenschutz". Die Funktion wird aber dann in beide Richtungen abgeklemmt, Sie können also auch keine Lesebestätigungen von anderen mehr sehen.
Bildschirmsperre: Auch sinnvoll ist es, eine Bildschirmsperre bei WhatsApp einzustellen. Die sollte sich möglichst "Sofort" einschalten, wenn man nicht mehr aktiv in der App ist. WhatsApp muss dann erst wieder entsperrt werden.
Chats ohne Kontakte: WhatsApp erlaubt nur Chats mit gespeicherten Kontakten. Wenn Sie aber nicht Hinz und Kunz hinzufügen wollen, öffnen Sie einfach im Browser auf dem Handy die Seite https://wa.me/ und hängen dort die Telefonnummer samt Ländervorwahl an. Es öffnet sich dann eine Seite, auf der Sie den Chat starten können. Der öffnet sich dann in WhatsApp.
Selbstlöschende Nachrichten: Ein praktisches Feature sind selbstlöschende Nachrichten. Sie müssen für jeden Chat gesondert eingeschaltet werden, was über die Kontaktinfos des Chat-Partners klappt. Dort dann einfach die Funktion "Selbstlöschende Nachrichten" einschalten. Nachrichten verschwinden dann nach einer vorgegebenen Zeit automatisch aus den Chats, möglich sind 24 Stunden, 7 oder 90 Tage. Beachten Sie aber, dass diese Nachrichten natürlich in der Zwischenzeit gesichert oder per Screenshot archiviert werden können.
Chatsperre: Sie können Chats über eine Option sperren, dann werden die Unterhaltungen in der Übersicht ausgeblendet und in einen eigenen Ordner verschoben. Inhalte des Chats tauchen auch in den Benachrichtigungen nicht mehr auf. Per Fingerabdruck, Gesichtserkennung oder PIN sind gesperrte Chats dann wieder lesbar.
Geheimcode: Eine recht neue Funktion erlaubt es, für die oben genannten gesperrten Chats eigene Passwörter zu vergeben, WhatsApp nennt sie Geheimcodes, mit denen dann der Zugriff auf den Ordner mit den gesperrten Chats funktioniert. WhatsApp ist aktuell dabei, diese Funktion zu verteilen.
Einmalansicht für Fotos und Videos: Verschickte Fotos und Videos bleiben normalerweise im Chat stehen und werden auf Wunsch auf den Geräten von Freunden gesichert. Doch das lässt sich mit der Einmalansicht verhindern. Wählen Sie dazu ein Foto oder Video aus und tippen Sie auf die kleine "1" im Feld der Bildunterschrift. Derart verschickte Fotos und Videos lassen sich nur einmal ansehen. Wichtig, Screenshots oder Bildschirmaufnahmen können damit aber nicht verhindert werden.
Vorsicht bei Backups: Backups von Chats lassen sich via WhatsApp bei Apple oder Google in deren Clouds ablegen. Komfortabel ist das, etwa für einen Umzug zu einem neuen Handy. Doch von Haus aus sind diese WhatsApp-Backups nicht verschlüsselt - diese Funktion müssen Sie erst aktivieren. Gehen Sie dazu in die Einstellungen unter "Chats | Chat-Backup | Ende-zu-Ende-verschlüsseltes Backup" und legen Sie dann ein Passwort fest.
IP-Adressen-Schutz bei Anrufen: Bei Anrufen via WhatsApp wird die IP-Adresse übermittelt. Damit man nicht seine eigene IP-Adresse rausrücken muss, gibt es die Möglichkeit, die Anrufe über WhatsApp-Server umzuleiten. Die Funktion ist unter "Datenschutz | Erweitert" zu finden.
Nutzer blockieren und Spam melden
Was auch zur Sicherheit gehört: Es gibt die Möglichkeit, Nutzer in WhatsApp zu blockieren und auch Spam können Sie melden.
Nutzer blockieren: Andere WhatsApp-Nutzer können Sie entweder im Chat über "Weitere Optionen" (Android) bzw. "Kontaktinfos" blockieren oder über die Einstellungen im Bereich "Datenschutz". Halten Sie nach dem Menüpunkt "Blockierte Kontakte" bzw. "Blockiert" Ausschau.
Spam melden: Spam, Fake-News oder sonstigen Kram, der per WhatsApp verschickt wird, können Sie als Spam melden. Auch das geht über die Kontaktinfos über "Kontakt melden". Der Kontakt wird dann automatisch auch blockiert. Nur die Blockade können Sie rückgängig machen, nicht aber die Spam-Meldung an WhatsApp.
Grenzen der Einstellungsmöglichkeiten
Machen wir uns nichts vor, auch wenn man es gerne möchte, Sie können aus WhatsApp nicht Signal oder Threema machen, egal was Sie einstellen. Der Grund ist einfach, die Datenauswertung ist das Geschäftsmodell. Sie sollten die oben gezeigten Einstellungen rund um Sicherheit und Datenschutz trotzdem abklappern, das bringt schon was.
Doch vor allem beim Datenschutz beschränkt sich das Ganze auf Punkte, die andere Nutzer von Ihnen sehen können. Was WhatsApp respektive Facebook im Hintergrund machen, können Sie nicht wirklich über die App einschränken.
Was aber möglich ist: Sie können unter Android und iOS die App-Berechtigungen von WhatsApp einschränken und etwa den Zugriff auf den Standort verbieten. Hier sollten Sie behutsam vorgehen und nicht alles einfach ausschalten, denn Benachrichtigungen wollen Sie sicher weiterhin bei neuen Nachrichten kriegen. Wenn Sie aber nur Texten, braucht WhatsApp weder Kamera- noch Mikrofon-Zugriff.
https://www.chip.de/news/Macht-leider-kaum-jemand-So-zaehmen-Sie-die-Datenkrake-WhatsApp_183245196.html
Geheimtipp
Ein alter Freund empfahl uns neulich Ginlo ...
 Sicherer Messenger fürs Smartphone von der Deutschen Post AG Sicherer Messenger fürs Smartphone von der Deutschen Post AG
"Willkommen bei ginlo, dem einzigen Messenger aus Deutschland mit professioneller Sicherheitstechnologie für den privaten Einsatz.
Sekundenschnell vertraulich verbunden mit ginlo now! - ohne Werbung und ohne Tracking. Mehr Info und Support unter https://www.ginlo.net"
Ein alter Freund empfiehlt uns ginlo von der Deutschen Post AG. Wir (Gooken) schließen uns an!
Dieser Messenger ist allerdings (noch) nicht besonders verbreitet.
https://apkcombo.app/de/ginlo-private-messanger/eu.ginlo_apps.ginlo
Signal-Affäre: Hegseth benutzte laut Berichten privates Handy | tagesschau.de, 26.05.2025
https://www.tagesschau.de/ausland/hegseth-handy-100.html
 Deine persönlichen Nachrichten warten nur darauf, öffentlich zu werden, uncut-news.ch, 30.05.2025 Deine persönlichen Nachrichten warten nur darauf, öffentlich zu werden, uncut-news.ch, 30.05.2025
Christina Maas, reclaimthenet
Wenn eine Nachricht nicht Ende-zu-Ende verschlüsselt ist, solltest du davon ausgehen, dass sie irgendwann leakt.
Menschen behandeln Textnachrichten immer noch so, als würden sie Geheimnisse in einen Tresor flüstern. Sie verschicken Geständnisse, Beschwerden, Flirts und Wutausbrüche über Plattformen, die zu Billionen-Dollar-Schwergewichten der Überwachung gehören - und glauben offenbar, diese Daten verschwinden in einem wohlwollenden digitalen Schwarzen Loch.
In Wahrheit liegen diese Nachrichten auf Servern von Konzernen, deren Geschäftsmodell darauf beruht, mehr über dich zu wissen als deine eigene Familie.
Die Illusion der Privatsphäre
Quelle: reclaimthenet
https://uncutnews.ch/deine-persoenlichen-nachrichten-warten-nur-darauf-oeffentlich-zu-werden/
Weitere Berichte über datenschutzrechtliche Bedenken bei Signal und WhatsApp, hier spezielle Spionagesoftware im Umlauf und Metadaten: in Kürze!
 Messenger-Update: Auf WhatsApp läuft künftig personalisierte Werbung, netzpolitik.org, 16.06.2025 Messenger-Update: Auf WhatsApp läuft künftig personalisierte Werbung, netzpolitik.org, 16.06.2025
WhatsApp, die Messenger-App von Mark Zuckerbergs Meta, zeigt künftig personalisierte Werbung an. Die Anzeigen sollen auch auf Daten von Facebook und Instagram basieren. Die Datenschutzorganisation noyb kritisiert die Entscheidung.
Die Anzeigen werden personalisiert ausgespielt, je nachdem, wo sich die Person aufhält, die sie auf ihrem Telefon zu sehen bekommt. Außerdem verarbeitet Meta, welchen Kanälen die Nutzer*innen folgen oder mit welchen Anzeigen sie interagieren, um Werbeinhalte weiter zu personalisieren. Wenn jemand sein WhatsApp-Konto in Metas Accountübersicht eingebunden hat, werden auch Informationen von anderen Metaprodukten wie Instagram oder Facebook genutzt.
Max Schrems, Vorsitzender der NGO noyb, sagt: "Meta macht hier genau das Gegenteil von dem, was das EU-Recht vorschreibt. Die Daten mehrerer Plattformen werden verbunden und Nutzer:innen werden ohne echte Wahl für Werbung getrackt. Ohne eine freiwillige Einwilligung ist die Verknüpfung der Daten und personalisierte Werbung ganz klar illegal."
Datenschutz kostet 9,99 Euro im Monat
Bei Metas Plattformen Instagram und Facebook gibt es die Möglichkeit, personalisierte Werbung abzuschalten. Der so gewonnene Datenschutz kostet aktuell 9,99 Euro im Monat. Schrems kritisiert, dass auch hier Nutzer*innen keine echte Wahl hätten und die Einwilligung - angesichts der alternativen "Strafzahlung" von rund 120 Euro im Jahr - keineswegs freiwillig zu nennen sei. Er befürchtet, dass das Geschäftsmodell nun auch auf WhatsApp ausgeweitet wird.
Erst vor kurzem hatte Meta beschlossen, die Informationen aller Nutzer*innen, die nicht explizit widersprechen, für das Training ihrer KI zu nutzen. Die Entscheidung hatte für massive Kritik seitens datenschutzinteressierter Menschen gesorgt. Zuvor hatte die Einführung der Meta-KI in WhatsApp den Datenschutz der App EU-weit deutlich verschlechtert. Denn die KI kann auch Chatinhalte mitlesen.
Datensauger WhatsApp
Datenschutz wird bei WhatsApp sowieso nicht sonderlich groß geschrieben. Der Messenger ermöglicht zwar Ende-zu-Ende-verschlüsselte Kommunikation, aber speichert offensichtlich regelmäßig aussagekräftige Metadaten. Darunter etwa, wann und wie lange mit welcher IP-Adresse der Dienst genutzt wird.
Auch Profilbilder, E-Mailadressen und die Kontaktliste speichert Meta und gibt die Daten auf Anfrage auch an Strafverfolgungsbehörden weiter. Selbst Kontaktdaten von Personen, die kein WhatsApp haben, können bei WhatsApp landen.
Max Schrems sieht in Metas jüngstem Schritt vor allem einen Anreiz, von WhatsApp zum freien Messenger Signal umzuziehen. "Signal funktioniert genauso gut, ist aber gemeinnützig und spendenfinanziert", sagt er. noyb gehe davon aus, dass die Werbung auf WhatsApp zum nächsten großen Exodus zu Signal führt.
https://netzpolitik.org/2025/messenger-update-auf-whatsapp-laeuft-kuenftig-personalisierte-werbung/
Die Welt ausspionieren
Darum warnt der Iran vor WhatsApp: Ehemalige israelische Spione sitzen in Führungspositionen bei Google, Facebook und Amazon, uncut-news.ch, 20.06.2025
Alan MacLeod, mintpressnews
Eine MintPress-Studie hat ergeben, dass Hunderte ehemaliger Agenten der berüchtigten israelischen Spionageorganisation Einheit 8200 einflussreiche Positionen in vielen der weltweit größten Tech-Unternehmen, darunter Google, Facebook, Microsoft und Amazon, eingenommen haben.
Die Einheit 8200 der israelischen Verteidigungskräfte (IDF) ist berüchtigt für die Überwachung der einheimischen palästinensischen Bevölkerung und die Anhäufung von Informationen über Einzelpersonen zum Zwecke der Erpressung und Erpressung. Die Einheit 8200, die die Reichen und Berühmten der Welt ausspioniert, geriet letztes Jahr nach Bekanntwerden des Pegasus-Skandals in die Schlagzeilen. Ehemalige Beamte der Einheit 8200 entwickelten und implementierten eine Software, die Zehntausende von Politikern ausspionierte und wahrscheinlich zur Ermordung des saudischen Journalisten Jamal Khashoggi beitrug.
Google
Laut dem Stellenportal LinkedIn arbeiten derzeit mindestens 99 ehemalige Veteranen der Einheit 8200 für Google. Diese Zahl unterschätzt jedoch mit Sicherheit das Ausmaß der Zusammenarbeit zwischen den beiden Unternehmen. Zum einen werden hier keine ehemaligen Google-Mitarbeiter gezählt. Auch sind diejenigen nicht berücksichtigt, die kein öffentliches LinkedIn-Konto haben, oder diejenigen, die zwar ein Konto haben, aber ihre frühere Zugehörigkeit zu der israelischen Hightech-Überwachungseinheit nicht offengelegt haben. Dies dürfte eine beträchtliche Zahl sein, da es den Agenten ausdrücklich untersagt ist, ihre Zugehörigkeit zur Einheit 8200 jemals preiszugeben. Die Zahl 99 gibt also nur die Anzahl der derzeitigen (oder erst kürzlich eingestellten) Google-Mitarbeiter wieder, die sich dreist über israelische Militärgesetze hinwegsetzen, indem sie die Organisation in ihren Profilen angeben.
Zu diesen gehören: ...
Die Welt ausspionieren
Warum ist es ein Problem, dass ehemalige Offiziere der Einheit 8200 bei einigen der wichtigsten Kommunikationsunternehmen der Welt für Sicherheit, Entwicklung und Softwaredesign zuständig sind? Zunächst einmal besteht eine der Hauptaufgaben der Militäreinheit darin, ihr technisches Know-how für Spionageoperationen in der ganzen Welt einzusetzen. Wie die israelische Zeitung Haaretz in einer Untersuchung feststellte, ist Israel zu einem führenden Exporteur von Werkzeugen zum Ausspionieren von Zivilisten geworden" und verkauft invasive Überwachungssoftware an Dutzende von Regierungen, von denen viele zu den schlimmsten Menschenrechtsverletzern der Welt gehören. In Indonesien wurde die Software beispielsweise zur Erstellung einer Datenbank über Homosexuelle verwendet.
Die Einheit 8200 spioniert auch Amerikaner aus. Der Whistleblower Edward Snowden enthüllte, dass die NSA regelmäßig die Daten und die Kommunikation von US-Bürgern an die israelische Gruppe weitergibt. "Ich finde das erstaunlich… Das ist einer der größten Missbräuche, die wir gesehen haben", sagte Snowden.
Quelle: https://www.mintpressnews.com/revealed-former-israeli-spies-working-top-jobs-google-facebook-amazon/282413/
https://uncutnews.ch/darum-warnt-der-iran-vor-whatsapp-ehemalige-israelische-spione-sitzen-in-fuehrungspositionen-bei-google-facebook-und-amazon/
Von News&Links#Windows#Smartphone#Links#NSA&Co.
 Bündnisse: Five Eyes, Nine Eyes, ... Bündnisse: Five Eyes, Nine Eyes, ...
"Wir töten Leute auf der Basis von Metadaten"
Hacking und Spionage, netzpolitik.org, 24.02.2020
...
https://netzpolitik.org/2020/ist-whatsapp-sicher-genug-fuer-die-diplomatie/
https://netzpolitik.org/2020/is-whatsapp-safe-for-diplomats/
 So geht sichere Kommunikation, netzpolitik.org, 2024 So geht sichere Kommunikation, netzpolitik.org, 2024
[...] Klassische Telefonate sind übrigens ähnlich unsicher wie eine Postkarte oder eine unverschlüsselte E-Mail, doch das direkte Gespräch ist über viele Messenger - wie Signal - auch verschlüsselt möglich.
[...] Sichere Ende-zu-Ende-Kommunikation würden die meisten modernen Messenger bieten, so Wey, er empfiehlt dennoch nur einen: Signal.
Auch Alexander Paul von der Digitalberatung resist.berlin und Janik Besendorf vom Digital Security Lab der Reporter ohne Grenzen raten, Signal zu benutzen. Viele Messengervergleiche im Netz bestätigen die Qualität des Messengers.
Der Code von Signal ist öffentlich einsehbar und gilt als gut verstanden. Er wird regelmäßig von externen Sicherheitsforschern geprüft. Signal löscht außerdem beim Versenden Metadaten von Fotos und Videos - wie Gerätemodell, Betriebssystem, Eigenschaften oder Standort.
Die Polizei bekommt nur zwei Datenpunkte
Wie bei jedem Ende-zu-Ende verschlüsselten Dienst können eventuelle Beobachter des Datenverkehrs nur eine verschlüsselte Verbindung zum Server sehen. Auf Anfrage von Ermittlungsbehörden gibt Signal zu jedem Account nur zwei Datenpunkte heraus: Wann der Account eröffnet wurde und wann er zuletzt online war. Das zu Facebook/Meta gehörende WhatsApp hingegen lässt die Sicherheitsbehörden auf Anfrage die Metadaten der Kommunikation mit einer bestimmten Nummer quasi in Echtzeit mitlesen.
https://netzpolitik.org/2024/digitale-selbstverteidigung-so-geht-sichere-kommunikation/
EU-Vorschlag zur Vorratsdatenspeicherung bedroht die Privatsphäre im Jahr 2025, uncut-news.ch, 04.06.2025
Didi Rankovic, reclaimthenet
Bevölkerungskontrolle und oder Neue Weltordnung (NWO), Geheimdienste/NSA/Überwachung/BigData
Ein neuer Vorschlag der Europäischen Union zur Vorratsdatenspeicherung droht, die Privatsphäre der Bürger erheblich zu untergraben. Die Initiative, die darauf abzielt, Metadaten flächendeckend zu sammeln und zu speichern, hat bei Datenschützern und Bürgerrechtsorganisationen Alarm ausgelöst. Dieser Schritt erfolgt in einem Kontext wachsender Besorgnis über staatliche Überwachung und die Erosion digitaler Freiheiten in Europa.
Was beinhaltet der Vorschlag?
Der Vorschlag, der von der Europäischen Kommission vorgelegt wurde, fordert, dass Telekommunikationsunternehmen Metadaten über die Kommunikation der Bürger - wie Telefonanrufe, Textnachrichten und Internetaktivitäten - für einen bestimmten Zeitraum speichern. Diese Daten umfassen:
Wer mit wem kommuniziert hat (Absender und Empfänger).
Zeitpunkt und Dauer der Kommunikation.
Standortdaten, die den Aufenthaltsort der Nutzer bei der Kommunikation angeben.
Verwendete Geräte und Netzwerke.
Die vorgeschlagene Speicherfrist variiert zwischen sechs Monaten und zwei Jahren, je nach Mitgliedstaat und Art der Daten. Ziel ist es, Strafverfolgungsbehörden Zugang zu diesen Daten zu verschaffen, um schwere Verbrechen wie Terrorismus und organisierte Kriminalität zu bekämpfen. Der Vorschlag ist eine Reaktion auf ein Urteil des Europäischen Gerichtshofs (EuGH) aus dem Jahr 2022, das die bisherigen Vorratsdatenspeicherungsgesetze in mehreren EU-Ländern für unverhältnismäßig erklärte, wie auf der Website des EuGH dokumentiert.
Warum ist dies ein Problem für die Privatsphäre?
Datenschützer warnen, dass die flächendeckende Speicherung von Metadaten ( -gt; WhatsApp u.a., Anm., Gooken, die Red.) eine ernsthafte Bedrohung für die Privatsphäre darstellt. Metadaten mögen auf den ersten Blick harmlos erscheinen, da sie keine Inhalte (z. B. den Text einer Nachricht) umfassen, aber sie können ein detailliertes Bild des Lebens einer Person zeichnen. Laut einem Bericht von Privacy International können Metadaten Bewegungen, soziale Netzwerke, Gewohnheiten und sogar politische Überzeugungen einer Person offenlegen.
"Metadaten sind oft aufschlussreicher als der Inhalt selbst", sagte Estelle Massé, leitende Politikanalystin bei Access Now, in einer Stellungnahme. "Die wahllose Sammlung dieser Daten verletzt das Recht auf Privatsphäre und schafft ein Klima der Überwachung, in dem sich niemand sicher fühlen kann."
[...] Fazit
Der EU-Vorschlag zur Vorratsdatenspeicherung ist ein umstrittenes Vorhaben, das die Privatsphäre der Bürger bedroht und die digitale Freiheit einschränken könnte. Während Sicherheitsbehörden auf die Notwendigkeit von Metadaten zugunsten der Verbrechensbekämpfung verweisen, sehen Datenschützer darin eine unverhältnismäßige Maßnahme, die alle Bürger unter Generalverdacht stellt. Die kommenden Monate werden entscheidend sein, um zu sehen, ob die EU ihre Verpflichtung zum Schutz der Grundrechte einhält oder den Weg für mehr Überwachung ebnet. Bürger, Aktivisten und Politiker sind gefordert, diesen Vorschlag kritisch zu prüfen und Alternativen zu fordern, die Sicherheit und Freiheit gleichermaßen respektieren.
Quelle: https://reclaimthenet.org/eu-metadata-retention-proposal-privacy-2025
https://uncutnews.ch/eu-vorschlag-zur-vorratsdatenspeicherung-bedroht-die-privatsphaere-im-jahr-2025/
Telegram, Threema and Co.
Do you fear the data common octopulus Whatsapp? This are the alternatives
Whatsapp with more than 1,5 billion user is one of the most popular messanger of the world - but rarely not the most secure and discrete one, STERN.de, 07.02.2020
[...] Telegram
Mehr als 200 Millionen Nutzer (Stand 2018). Cloudbasiert - man kann die Inhalte parallel auf verschiedenen Mobilgeräten und Computern abrufen. Die App ist übersichtlich gestaltet. Telegram wirbt zwar mit einer mächtigen Ende- zu-Ende-Verschlüsselung. Allerdings ist diese standardmäßig nicht aktiviert. Bei Gruppen-Unterhaltungen ist sie gar nicht möglich.
Urteil: Telegram hat Schwächen. Die Verschlüsselung ist hausgemacht und standardmäßig nicht eingeschaltet. Wer aus Datenschutzgründen gegen Whatsapp optiert, findet in Telegram keine Alternative. Verfügbar für: Android, iOS, iPadOS, Windows, macOS, Browser
Signal...
https://www.stern.de/p/plus/politik-wirtschaft/whatsapp---so-sicher-sind-alternative-messenger-9123358.html
Diagrams about "Stille SMS"
Secret impluses for the determination of the locations
Many "Stille SMS" in Germany, netzpolitik.org, 10.02.2020
Anfragen in Parlamenten und nach dem Informationsfreiheitsgesetz dokumentieren das Ausmaß heimlicher Textnachrichten, um den Aufenthaltsort von Telefonen und deren BesitzerInnen zu ermitteln. Polizeien nutzen die Methode für Festnahmen, während Geheimdienste damit längerfristige Bewegungsprofile erstellen.
https://netzpolitik.org/2020/viele-stille-sms-bei-bund-und-laendern/
Weniger "Stille SMS" bei Bundesbehörden, aber mehr Geheimhaltung, netzpolitik.org, 21.08.2019
Netzpolitik.org stellt den Versand von Stillen SMS halbjährlich grafisch dar. So lässt sich zeigen, in welchem Umfang Polizeien und Geheimdienste Mobiltelefone als Ortungswanzen nutzen. Wegen einer solchen "Verdichtung" von schutzwürdigen Informationen sind die Zahlen für den Verfassungsschutz jetzt als "Geheim" eingestuft.
https://netzpolitik.org/2019/weniger-stille-sms-bei-bundesbehoerden-aber-mehr-geheimhaltung/
Find out phishing-SMS and report them - howto, CHIP, 13.04.2021
In diesem Artikel zeigen wir Ihnen, wie Sie eine Phishing-SMS erkennen und diese anschließend melden. Phishing-SMS dienen dazu, entweder Schadsoftware auf Ihrem Handy zu installieren oder Ihre Daten auszulesen. Oft entstehen auch hohe Kosten, weil ungewollt Premium-Dienste abgeschlossen werden.
https://praxistipps.chip.de/phishing-sms-erkennen-und-melden-so-gehts_46400
US-reproach: Huawei uses backdoors in mobile nets, PC-WELT.de, 12.02.2020
Die US-Regierung hat ihre Vorwürfe gegen Huawei erneuert. Die belastenden Beweise wurden auch an Deutschland geliefert.
https://www.pcwelt.de/news/US-Vorwurf-Huawei-nutzt-Backdoors-in-Mobilfunknetzen-10753323.html
 Highly developed Android-eavesdropping campagne discovered, trojaner-info.de, 03.05.2020 Highly developed Android-eavesdropping campagne discovered, trojaner-info.de, 03.05.2020
Die Experten von Kaspersky haben eine hochentwickelte und schädliche Kampagne entdeckt, die es explizit auf Nutzer von Android-Geräten abgesehen hat und vermutlich vom APT-Akteur ´OceanLotus´ stammt. Die sogenannte ´PhantomLance´-Kampagne läuft seit mindestens 2015 und ist weiterhin aktiv.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/hochentwickelte-android-spionagekampagne-entdeckt.html
German authorities want to eavesdrop 5G-net, PC-WELT.de, 04.06.2019
Die deutschen Sicherheitsbehörden wollen Zugriff auf das 5G-Netz. Die Mobilfunk-Provider sollen dazu verpflichtet werden.
https://www.pcwelt.de/news/Deutsche-Sicherheitsbehoerden-wollen-5G-Netz-abhoeren-koennen-10604286.html
Open letter to Google
Privacy should be no luxury anymore, netzpolitik.org, 08.01.2020
Preinstalled Apps upon Android-smartphones do threaten the privacy of their user. More than 50 non-profit-organizations summon Google to unlasting change this fact.
https://netzpolitik.org/2020/privatsphaere-soll-kein-luxusgut-bleiben/
 Android-Apps do steal bank data Android-Apps do steal bank data
Caution before malware in Play Store!, PC-WELT.de, 13.03.2021
Google has removed Apps out of Google Play Store mutating into malware past getting updated. They infiltrate malware, in order to eavesdrop bank data.
https://www.pcwelt.de/ news/Android-Apps-stehlen-Bankdaten-Vorsicht-vor-Malware-im-Play-Store-10992445.html
Google knows about your online-shopping-orders via Gmail-tracking, PC-WELT.de, 05.20.2019
Google ist in der Lage, alle Online-Einkäufe der Nutzer zu tracken, auch wenn diese nicht via Google getätigt wurden.
https://www.pcwelt.de/news/Google-kennt-Ihre-Online-Einkaeufe-via-Gmail-Tracking-10594891.html
Facebook asks banks for user data, PC-WELT.de, 08.07.2018
Facebook hat laut einem Medienbericht bei mehreren großen US-Banken angefragt, um von diesen Kundendaten zu bekommen.
https://www.pcwelt.de/a/facebook-fragte-banken-nach-nutzerdaten,3451879 ä
Google tracks Mastercard-user
Bericht: Google tracks user offline with Mastercard-data, PC-WELT.de, 08.31.2018
Laut einem Bloomberg-Bericht kauft Google Kunden-Daten von Mastercard, um Kunden auch offline zu tracken.
Wie die News-Plattform Bloomberg berichtet, ist Google wohl einen Deal mit Mastercard eingegangen, um Offline-Einkäufe von Kreditkarten mit Nutzerkonten zu verknüpfen. Für die Daten von 70 Prozent aller Mastercard-Inhaber der USA aus dem Jahr 2017 soll Google demnach mehrere Millionen US-Dollar gezahlt haben. Darin enthalten sind Transaktionsdaten, die für Google ausreichen, um Personen eindeutig zu identifizieren.
[...] Laut den Angaben von Bloomberg sind sich aber beide Unternehmen wohl darüber bewusst, dass hier jede Menge Datenschutz-Probleme auftauchen. Der Deal wurde daher nur zögerlich eingegangen. Vier Jahre wurde zwischen den zwei Unternehmen verhandelt, bevor der Deal abgeschlossen wurde. Mastercard-Inhaber wurden darüber hinaus nicht über das Tracking informiert. Zwar gäbe es in Googles Web-Console eine Möglichkeit das Tracking zu untersagen, jedoch ist dies für den Großteil der Nutzer nicht ersichtlich.
[...] Der Bloomberg-Bericht bezieht sich nur auf die USA. Ob Google in weiteren Ländern ähnlich vorgeht, geht aus dem Artikel nicht hervor. In den Vereinigten Staaten machen Umsätze mit Mastercard rund 25 Prozent des gesamten Umsatzes aus.
https://www.pcwelt.de/a/bericht-google-verfolgt-nutzer-offline-mit-mastercard-daten,3452190
Huawei AppGallery: All important information, CHIP, 13.05.2020
Whoever whants to buy a new Huawei- or Honor-smartphone, must resign from the Google Play Store. The reason is a trade confliction between USA and China. The Huawei AppGallery is instaleld of such smartphones instead. But what does this exacly mean for the user? We explain it them.
https://www.chip.de/video/Huawei-AppGallery-Alle-wichtigen-Informationen-Video_182706838.html
Your Smartphone is watching you: Dangerous lacks in security in tracker-Apps, trojaner-info.de, 08.20.2018
Fraunhofer-Forscher: Komplette Überwachung von Smartphones möglich. Millionen Installationen betroffen.
Viele Tracker-Apps, mit denen beispielsweise Eltern ihre Kinder orten können, haben gravierende Sicherheitslücken. Forscher des Fraunhofer-Instituts für Sichere Informationstechnologie haben beliebte Tracker-Apps aus dem Google Play Store untersucht - das Ergebnis: Keine einzige davon war sicher programmiert, alle hatten teils gravierende Schwachstellen.
https://www.trojaner-info.de/mobile-security/aktuell/your-smartphone-is-watching-you-gefaehrliche-sicherheitsluecken-in-tracker-apps.html
More than 3 millionen infected PCs and Smartphones
Smsspy, Faketoken, Ramnit, ...
Online-Banking: The most important security tipps, PC-WELT.de, 06.13.2017
Mit den richtigen Tipps lassen sich die Gefahren für das Onlinebanking gut begrenzen. Das ist allerdings dringend nötig, denn nun haben auch die Angriffe auf das Banking per Smartphone stark zugenommen.
Onlinebanking am heimischen Rechner mit dem Browser hat sich für die meisten PC-Nutzer als komfortabel erwiesen. Doch auch das Smartphone ist fürs Banking beliebt. Laut einer Studie der Netzwerkfirma F5 Networks vom Januar 2017 verwenden 84 Prozent aller Internetnutzer bereits Apps und damit auch ein Smartphone oder Tablet. Und bereits 44 Prozent dieser Nutzer wenden auch Apps fürs Onlinebanking an. Gerade erfahrene Nutzer von Smartphones fühlen sich mit ihren Geräten recht sicher. Doch das ist leider ein trügerisches Gefühl, denn die Kriminellen attackieren nun auch das mobile Betriebssystem Android. Das geschieht wie schon bei Windows hauptsächlich mit Viren. Laut den Sicherheitsforschern von AV-Test in Magdeburg existieren bereits 18 Millionen Schädlinge für Smartphones und Tablets. Pro Monat kommen in etwa 600.000 neue Schädlinge hinzu. Es ist also höchste Zeit, das eigene Smartphone zumindest beim Onlinebanking richtig zu schützen.
Aktuelle Gefahren
Tracker-epidemic-plague also in VPN-Apps, PC-WELT.de, 03.28.2019
Wenn VPN-Apps Tracker enthalten, die Daten an Dritte ausleiten, widerspricht dies offenkundig den Werbeaussagen der VPN-Anbieter. Diese werben mit dem Schutz der Privatsphäre und verheißen gar Anonymität beim Surfen im Netz.
Kürzlich haben wir über Tracker in Android-Apps berichtet. Zwei Drittel der mehr als 50.000 durch die französische Non-Profit-Organisation Exodus Privacy untersuchten Apps enthält Tracker. Sie leiten zum Teil Daten an Drittunternehmen aus, in vielen Fällen auch Daten, aus denen sich Benutzerprofile erstellen und über Gerätegrenzen hinweg verfolgen lassen. VPN-Anbieter (VPN: Virtual Private Network) versprechen einen umfassenden Schutz der Privatsphäre. Fast alle behaupten zudem, sie hätten eine strikte "No-Logs-Policy", würden also keine Protokolle der Nutzeraktivitäten speichern. Wir haben daher die aktuellen (Stand: 26.3.2019) Android-Apps der Anbieter aus unserer VPN-Marktübersicht ebenfalls auf Tracker untersucht.
https://www.pcwelt.de/news/Tracker-Seuche-auch-in-VPN-Apps-10564551.html
Malware in all kind of Apps
Android-Trojaner GPlayed found
Cisco Talos warns against Fake App, trojaner-info.de, 10.20.2018
Sicherheitsexperten mahnen immer wieder davor, Apps aus dubiosen Quellen zu beziehen. Grund dafür ist, dass Cyberkriminelle eifrig bemüht sind, Malware in Apps aller Art einzubauen. So verhält es sich auch im Fall des von Cisco Talos entdeckten Trojaners GPlayed.
https://www.trojaner-info.de/mobile-security/aktuell/android-trojaner-gplayed-entdeckt.html
Each eight seconds criminals release an infected App for Android
Around 1,9 Millionen new infected Apps
Mobile Malware Report: No relief from Android-Malware, trojaner-info.de, 08.01.2019
G DATA konstatiert: Die Sicherheitslage im Mobile-Bereich bleibt weiterhin angespannt.
Kein neuer Rekord, aber auch keine Entspannung bei Android-Schadsoftware: Die Experten des Cyber Defense Spezialisten G DATA haben in den ersten sechs Monaten rund 1,9 Millionen neue schädliche Apps gezählt. Im Vergleich zum Vorjahr ein leichter Rückgang. Zur Einordnung: Durchschnittlich alle acht Sekunden veröffentlichen Kriminelle eine infizierte App für Android.
https://www.trojaner-info.de/mobile-security/aktuell/mobile-malware-report-keine-entspannung-bei-android-malware.html
Android-Malware with 250 Mio. downloads, PC-WELT.de, 03.15.2019
Das Sicherheitsunternehmen Check Point Research hat zwei massive Kampagnen mit Malware für Android entdeckt.
https://www.pcwelt.de/news/Android-Malware-mit-250-Mio.-Downloads-aufgetaucht-10556033.html
Man-in-the-Disk: Preinstalled Apps with security exploits on Android
Das Research Team von Check Point findet eine Schwachstelle in der Android Sandbox -Schadsoftware führt: Man-in-the-Middle-Angriffe über externen Speicher von Geräten aus.
Das Research-Team von Check Point hat aktuell Details zur Man-in-the-Disk-Schwachstelle veröffentlicht. Dabei zeigt das Research-Team, wie sie über externe Speichermedien auf Androidgeräten die Sandbox umgehen konnten und danach erfolgreich verschiedene Angriffe gestartet haben.
https://www.trojaner-info.de/mobile-security/aktuell/man-in-the-disk-vorinstallierte-apps-angreifbar-auf-android.html
Gap in the LTE-net concerns quit every smartphone, PC-WELT.de, 02.21.2020
Hacker can contract abos in other names.
https://www.pcwelt.de/news/Luecke-im-LTE-Netz-betrifft-fast-jedes-Smartphone-10758480.html
Howto hide malware in Apps, trojaner-info.de, 03.08.2019
Wie man gefährlichen Code in harmlosen Apps versteckt haben Forscherteams der University of Colorado Boulder (UCB) aufgezeigt.
Wie man Malware in harmlosen Apps versteckt haben Forscher entdeckt. Sie nutzen dafür die schon durch Meltdown und Spectre bekannt gewordene spekulative Ausführung. Der Schadcode kann weder in der harmlosen App noch später im Speicher entdeckt werden. Software-Patches halten die Forscher zudem für wirkungslos.
https://www.trojaner-info.de/mobile-security/aktuell/wie-man-malware-in-apps-versteckt.html
Each third smartphone-user has got Malware on his Smartphone
Eine Umfrage zeigt: Mehr als ein Drittel hat sich auf dem Smartphone in den letzten 12 Monaten einen Schädling eingefangen.
https://www.pcwelt.de/a/jeder-dritte-smartphone-nutzer-von-malware-betroffen,3462840
 Malware against smartphone: Five indications of a infection, trojaner-info.de, 03.07.2021 Malware against smartphone: Five indications of a infection, trojaner-info.de, 03.07.2021
The experts from Check Point have published five symptoms, with which you can detect, if cybercriminals have done their work within your smartphone. The security explorers know: Whenever the smartphone gets infected, personal data are in danger.
https://www.trojaner-info.de/mobile-security/aktuell/malware-gegen-smartphone-fuenf-anzeichen-einer-infektion.html
 Cloud & Threat Report: The major part of malware origins from cloud-apps, trojaner-info.de, 03.07.2021 Cloud & Threat Report: The major part of malware origins from cloud-apps, trojaner-info.de, 03.07.2021
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/cloud-threat-report-grossteil-der-malware-kommt-ueber-cloud-apps.html
Howto reset Android, PC-WELT.de, 02.12.2020
Resetting to "default values" deletes all important data from the Android-handy? Wrong! We show, how to.
https://www.pcwelt.de/ratgeber/Android_gruendlich_zuruecksetzen_-_so_geht_s-Beim_Verkauf-8802318.html
 Von wegen Smartphone-Profi! Eine Sicherheitslücke übersehen fast alle, CHIP, 20.06.2021 Von wegen Smartphone-Profi! Eine Sicherheitslücke übersehen fast alle, CHIP, 20.06.2021
Einer neuen Studie zufolge gehen 59 Prozent der deutschen Internetnutzer unachtsam mit Schutzvorkehrungen im Netz um. Damit sind wir leichte Beute in den Fängen von Cyberkriminellen - und sind so auch nicht die Digital-Profis, als die wir uns immer ausgeben.
Weitere Erkenntnisse aus der Studie sprechen ebenfalls nicht für einen sicheren Umgang mit unseren Daten und unserer Identität im Netz: Nur 50 Prozent aller Handynutzer prüfen die Zugriffsrechte der installierten Apps, mit 31 Prozent setzt nicht mal ein Drittel aller User einen Passwortmanager ein.
[...] Es scheint, als sei dem Großteil der deutschen Internetnutzer egal, was online passiert. Doch die digitale Identität und alle persönlichen Daten sind eines unserer wertvollsten Güter.
Digital egal: Warum wir uns auch online schützen sollten
Die Studie besagt zudem, dass nur 27,1 Prozent ihre eigene Festplatte verschlüsseln und ganze 17 Prozent bewusst auf Schutzvorkehrungen verzichten, obwohl sie es besser wissen. Wie bitte? Man verzichtet bewusst auf Schutz? Das ist, als würde man einen Einbrecher darum bitten, die eigene Wohnung auszuräumen.
Jeder von uns hat online Profile auf sozialen Medien, Accounts bei Shopping-Seiten oder führt das Bankkonto digital. Der Ausweis ist irgendwo hinterlegt, womöglich sogar die Krankenkarte bei der Versicherung und viele persönliche Informationen auf anderen Webseiten. Es ist gerade zu schockierend, wie fahrlässig wir im Netz mit uns selbst umgehen. Und dass mit unseren sensibelsten Daten. Der Schaden wäre enorm, würde ein Hacker jemanden attackieren, der so unachtsam ist.
Ein reflektierter und sicherer Umgang mit Portalen im Internet ist hier wichtig. Klar ist es praktischer, überall alles zu hinterlegen: Ein Klick und das T-Shirt ist bestellt. Ein Klick und ich buche einen neuen Handyvertrag. Ein Klick und jeder weiß, was gerade mein Lieblingssong ist. Doch es reicht auch nur eine kleine Attacke und wir werden unsere digitale Identität los. Hacker können diese im Darknet verkaufen - und schon gibt sich jemand als man selbst aus oder belastet das Bankkonto.
Stellen Sie so viele Daten wie nötig, aber so wenig wie möglich ins Netz.
Seien Sie auf der Hut vor Phishing Mails und klicken Sie ja nicht auf unbekannte Links.
Löschen Sie alte Accounts, die Sie nicht mehr benötigen. Auch hier stecken Berge von Datensätzen über Sie.
Ändern Sie regelmäßig Ihre Passwörter. Nutzen Sie dafür auch einen sicheren Passwortmanager.
Bei Have I Been Pwned können Sie überprüfen, ob Ihre Passwörter gehackt wurden.
Installieren Sie alle verfügbaren Updates: Auf allen Geräten! Dazu zählen auch Smartwatches, Smarte TVs, Smartphones oder Computer.
Überprüfen Sie die Berechtigungen Ihrer installierten Apps. Das geht im App-Manager jedes Android-Gerätes. Ist es wirklich sinnvoll, dass zum Beispiel der Kalender Zugriff auf den Standort hat? Deaktivieren Sie alles, was Ihnen zweifelhaft erscheint. Am Ende kann man die Berechtigung immer noch wieder aktivieren, wenn der Funktionsumfang fehlt.
https://www.chip.de/news/Von-wegen-Smartphone-Profi-Eine-Sicherheitsluecke-uebersehen-fast-alle_183667262.html
Customer protection warns against new abo-traps on handy, PC-WELT.de, 10.07.2019
20 Euro Abo-Kosten auf der Handyrechnung, obwohl Sie nichts bestellt haben? Verbraucher warnen vor neuen Abo-Fallen.
https://www.pcwelt.de/news/Verbraucherschuetzer-warnen-vor-neuen-Abo-Fallen-auf-dem-Handy-10625720.html
Grindr, Tinder & Co.
Campaign postulates the end of illegal online-advertising-methods through handy-Apps, netzpolitik.org, 03.05.2020
Einige scheinbar harmlose und praktische Apps wie Zyklus-Kalender setzen auf ein fragwürdiges Modell: Sie geben sensible Nutzer:innendaten an Dritte weiter. Das ist illegal, darum gehen norwegische Verbraucherschützer:innen dagegen vor. Die Digitale Gesellschaft und andere NGOs fordern deutsche Behörden jetzt auf, die Norweger:innen zu unterstützen.
https://netzpolitik.org/2020/kampagne-fordert-ende-illegaler-online-werbemethoden-durch-handy-apps/
 Grindr, Tinder, MyDays & Co. Grindr, Tinder, MyDays & Co.
New study reveals, how popular Apps systematically transmit initimate user data, netzpolitik.org, 01.14.2020
Norwegische Verbraucherschützer:innen haben heute eine neue Untersuchung zu Online-Werbung veröffentlicht, in der sie eindringlich vor den Folgen illegaler Datensammlung warnen. Basierend auf den Ergebnissen wollen Verbraucher- und andere zivilgesellschaftliche Organisationen in Europa ihre Behörden auffordern, die höchst fragwürdigen Praktiken der Online-Werbeindustrie zu beenden.
https://netzpolitik.org/2020/neue-studie-zeigt-wie-populaere-apps-systematisch-persoenliche-daten-weitergeben/
 Google should be ashamed for Android - because of iOS 14!, PC-WELT.de, 23.06.2020 Google should be ashamed for Android - because of iOS 14!, PC-WELT.de, 23.06.2020
Apple introduced iOS 14 and even eldest iPhones can get updated. Google´s Android should be ashamed.
https://www.pcwelt.de/news/Google-sollte-sich-fuer-Android-schaemen-wegen-iOS-14-Ein-Kommentar-10833297.html
LTE-gap: Attackers were abled to eavesdrop phone calls, PC-WELT.de, 13.08.2020
Viele Jahre steckte in LTE eine schwere Sicherheitslücke, über die Angreifer Mobilfunkgespräche abhören konnten.
https://www.pcwelt.de/news/LTE-Luecke-Angreifer-konnten-Telefonate-abhoeren-10864280.html
 Fast alle Android-Nutzer gefährdet: Fiese Sicherheitslücke bedroht Smartphones - wie Sie sich schützen, CHIP, 30.05.2020 Fast alle Android-Nutzer gefährdet: Fiese Sicherheitslücke bedroht Smartphones - wie Sie sich schützen, CHIP, 30.05.2020
Sicherheitsforscher haben in Android eine neue, schwerwiegende Schwachstelle entdeckt. Apps können über die Lücke Nutzerdaten abgreifen und sich sogar mehrere Berechtigungen im Betriebssystem holen, ohne dass der Smartphone-Nutzer etwas davon bemerkt.
https://www.chip.de/news/Viele-Android-Nutzer-gefaehrdet-Sicherheitsluecke-bedroht-Smartphones-wie-Sie-sich-schuetzen_182735715.html
Digital stalking
Kaspersky founds out more than 2.000 cases of stalkerware in Germany, netzpolitik.org, 03.11.2020
Deutschland ist europaweit an der Spitze, wenn es um die private Spionage mit Stalkerware geht. Das legen neue Zahlen der IT-Sicherheitsfirma Kaspersky zur heimlichen Handy-Überwachung nahe. Die Dunkelziffer dürfte noch sehr viel höher liegen.
https://netzpolitik.org/2020/kaspersky-findet-mehr-als-2-000-faelle-von-stalkerware-in-deutschland/
 Protection against stalkerware, trojaner-info.de, 01.20.2020 Protection against stalkerware, trojaner-info.de, 01.20.2020
Netflix hat die zweite Staffel der beliebten Thrillerserie "You - Du wirst mich lieben" veröffentlicht. Mittelpunkt der Serie ist der Buchhändler Joe Goldberg, der über das Internet und speziell die sozialen Netzwerke die Studentin Guinevere Beck ausspioniert - kein abwegiges Szenario. Für böswillige Akteure ist das Internet das ideale Umfeld, um nah an ihre potenziellen Opfer heranzukommen und Informationen über sie zu sammeln. Zusätzlich existieren zahlreiche Apps, mit denen die Kriminellen die Daten und Informationen direkt auf den Geräten des Ziels sammeln können: sogenannte Stalkerware. Nikolaos Chrysaidos, Head of Mobile Threat Intelligence and Security bei Avast, erklärt, wie sich Nutzer dagegen schützen können:...
https://www.trojaner-info.de/mobile-security/aktuell/schutz-vor-stalkerware.html
 Attention please before data collectors! Howto protect your privacy, PC-WELT.de, 24.11.2019 Attention please before data collectors! Howto protect your privacy, PC-WELT.de, 24.11.2019
Es genügen schon wenige Infos, um ein überraschend detailliertes Profil eines Nutzers anzulegen. So schützen Sie sich.
https://www.pcwelt.de/ratgeber/Datenschutz-So-schuetzen-Sie-Ihre-Privatsphaere-im-Web-57287.html
 Howto use Google Maps anonymously, PC-WELT.de, 22.03.2020 Howto use Google Maps anonymously, PC-WELT.de, 22.03.2020
https://www.pcwelt.de/tipps/Google-Maps-anonym-verwenden-10758396.html
Stalker-App
Dasta eavesdrops WhatsApp-user, PC-WELT.de, 12.20.2019
The Stalker-App Dasta eavesdrops optionally the online-status from users of WhatsApp, Telegram and VK.com.
https://www.pcwelt.de/news/Stalker-App-Dasta-spioniert-WhatsApp-Nutzer-aus-10727507.html
China: Spy-app secretly eavesdrops country entering persons, netzpolitik.org, 07.03.2019
An den Grenzen der chinesischen Region Xinjiang werden die Handys von Einreisenden von einer App ausspioniert. Die sucht nach IS-Propagandavideos, aber genauso nach Fotos des Dalai Lama. Auch Kontakte, Anruflisten und Kalender werden ausgelesen. Erste Hersteller von Antiviren-Software haben reagiert.
https://netzpolitik.org/2019/china-spionage-app-spaeht-heimlich-einreisende-aus/
Why it is so difficult to do something against spy-Apps by law, netzpolitik.org, 06.26.2019
Wer das Handy einer Partnerin oder Ex-Partnerin mit Spionage-Apps überwacht, macht sich in Deutschland strafbar. Zu Anklagen kommt es trotzdem so gut wie nie und auch die Hersteller solcher Apps müssen sich nicht fürchten. Dazu gibt es zu viele Schlupflöcher im Gesetz und zu wenige Möglichkeiten, das Stalking zu beweisen.
https://netzpolitik.org/2019/warum-es-so-schwer-ist-rechtlich-gegen-spionage-apps-vorzugehen/
 Stalking per Smartphone Stalking per Smartphone
How security explorers want to blow the cover of eavesdropping Apps, netzpolitik.org, 25.06.2020
Menschen spionieren andere Menschen aus und billige Apps helfen ihnen dabei. Die Überwachung ist ein massiver Eingriff in die Grundrechte, doch die Programme sind nur schwer aufzufinden. Sicherheitsforscher:innen wollen das ändern.
https://netzpolitik.org/2020/wie-sicherheitsforscherinnen-spionageapps-enttarnen-wollen/
Android-user attention please!: Aggressive malware appears in thousand of devices, CHIP, 10.30.2019
Tausende Android-Nutzer scheitern aktuell kläglich beim Kampf gegen eine neue Malware. Seit sie im März entdeckt wurde, infizieren sich täglich 131 Smartphones mit der Malware. Das Problem: Sie ist besonders aggressiv und lässt sich nicht mehr vom Handy entfernen.
ZDNet berichtet über einen bestimmten "Stamm" von Malware, der in der Lage ist, sich selbst neu zu installieren. Dies macht es für Android-Nutzer fast unmöglich, diesen zu entfernen. Die als xHelper bekannte Malware wurde erstmals im März entdeckt und hatte fünf Monate später bereits 32.000 Smartphones infiziert.
Die Zahl ist nun im Oktober bereits auf 45.000 angewachsen. Laut Symantec werden jeden Tag 131 neue Mobiltelefone infiziert, etwa 2.400 pro Monat.
Android-Malware: Das macht sie mit den Smartphones
https://www.chip.de/news/Android-Nutzer-aufgepasst-Aggressive-Malware-in-tausenden-Geraeten-aufgetaucht_176005218.html
 Gigaset-Handys infiltrated with Malware - howto repair these devices, PC-WELT.de, 04.09.2021 Gigaset-Handys infiltrated with Malware - howto repair these devices, PC-WELT.de, 04.09.2021
Auf einigen älteren Gigaset-Handys hat sich automatisch eine Malware installiert. Gigaset erklärt, wie Sie das Problem lösen können.
https://www.pcwelt.de/news/Gigaset-Handys-mit-Malware-verseucht-so-reparieren-Sie-die-Geraete-11009438.html
Infected iPhone-Apps, trojaner-info.de, 10.30.2019
Sicherheitsforscher haben die iOS-Apps einer indischen Firma entdeckt, die für Klickbetrug eingesetzt wurden. Apple hat direkt gehandelt und die Apps entfernt. 17 unter den insgesamt 51 Apps des Anbieters sind einer Analyse zufolge mit einem "Klick-Trojaner-Modul" infiziert gewesen.
https://www.trojaner-info.de/mobile-security/aktuell/infizierte-iphone-apps.html
Delete them at once from iPhone: Trojans in 17 iOS-Apps were detected, CHIP, 11.02.2019, 02.11.2019
Im App Store gibt es nicht nur böse Apps: Diese Apps empfehlen wir für jede iPhone-Grundausstattung.
Britische IT-Spezialisten haben 17 verseuchte iOS-Apps im App Store entdeckt, die iPhone-Nutzer bei Entdeckung umgehend löschen sollten. Die Malware-Apps stammen alle vom selben Entwickler; Details dazu im weiteren Text.
https://www.chip.de/news/Sofort-vom-iPhone-loeschen-Trojaner-in-17-iOS-Apps_175926000.html
 The App enabled to control the whole iPhone from outside The App enabled to control the whole iPhone from outside
iMessage: Apple much more closed lacks in security for the messaging-App, trojaner-info.de, 09.02.2021
In den letzten Jahren kam es mehrfach zu durchaus spektakulären Exploits in Apples populärer Mitteilungs-App iMessage. So gab es etwa erst im Frühjahr 2020 einen Fall, bei dem ein Sicherheitsforscher schilderte, wie sich über die Anwendung von Außen ein ganzes iPhone übernehmen ließ. Apple scheint die Warnungen und Problem ernst zu nehmen: ...
https://www.trojaner-info.de/mobile-security/aktuell/imessage-apple-dichtet-messaging-anwendung-besser-ab.html
"Session Replay"
Many well-known Apps auidt everything, what the user does - inclusive sensible data, STERN.de, 02.08.2019
Eine Studie zeigt, dass viele Apps genau aufzeichnen, was auf dem Smartphone passiert - inklusive aller Wischer und Eingaben - und es dann auf Server laden. Die Kunden merken davon nichts. Nun hat Apple reagiert.
Das Smartphone ist wohl das persönlichste technische Gerät, das es je gab. Von intimsten Gesprächen und Bildern, über Shopping und Urlaub, bis zu Arbeits-, Bank- und Steuerinformationen findet sich bei vielen Nutzern quasi das ganze Leben auf den kleinen Geräten. Umso gruseliger die Vorstellung, dass Apps alles aufzeichnen, was auf dem Gerät geschieht.
Doch genau das passiert, berichtet das Portal "Techcrunch". Demnach speichern eine Reihe von Apps jede Eingabe, jedes Wischen und jeden Tipper. Auch große Anbieter wie Expedia, Abercrombie & Fitch oder Hotels.com sollen auf diese Dienste zurückgreifen und fleißig mitschneiden, was in den jeweiligen Apps passiert. "Stellen Sie sich vor, Ihre Webseite oder Mobil-App ließe Sie genau sehen, was Ihre Nutzer in Echtzeit tun und warum sie es tun. Das ist nicht nur hypothetisch möglich, sondern wirklich umsetzbar", twitterte etwa der Anbieter Glassbox.
[...] Auch das Aufnahmeverfahren an sich ist nicht so sicher, wie es die Betreiber gerne darstellen. Zwar betont Glassbox, dass nur Informationen in der App selbst aufgezeichnet werden - also keine Gespräche, Chats oder andere Aktivitäten aus anderen Apps - und außerdem sensible Daten wie Kreditkarten-Informationen geschwärzt würden. In der Praxis fand "Techcrunch" aber durchaus Fälle, in denen das schiefging.
[...] Aus Nutzersicht ist vor allem die mangelnde Transparenz ärgerlich. Die App-Anbieter informieren die Kunden nicht darüber, dass deren Daten aufgezeichnet und herumgeschickt werden, eine Möglichkeit, die Funktion abzuschalten, gibt es nicht. Dass die Anbieter die Funktion so wenig kommunizieren hat nach "Techcrunchs" Einschätzung einen einfachen Grund: "Sie wissen selbst, wie gruselig das alles ist."
https://www.stern.de/digital/smartphones/viele-bekannte-apps-zeichnen-alles-auf--was-man-tut---nun-reagiert-apple-8570398.html
Expensive subscription trap: At least 41.000 customers are affected: Stiftung Warentest warns against incorrect Mobilfunk-bills, STERN.de, 09.17.2019
Tausende Mobilfunk-Kunden erhielten von ihren Anbietern zu hohe Rechnungen. Der Grund sind unberechtigte Forderungen von Drittanbietern, berichtet Warentest. Und verrät, wie Betroffene ihr Geld wiederbekommen.
https://www.stern.de/digital/smartphones/warentest-warnt-vor-fehlerhaften-mobilfunk-rechnungen--41-000-kunden-betroffen-8908634.html
Infected Android-Apps in the Play Store with 1,5 millionen downloads, trojaner-info.de, 09.24.2019
Verseuchten Apps gelingt es immer wieder, in den offiziellen Play Store zu gelangen.
Es sind besonders hartnäckige Apps, die Google mittlerweile aus dem Play Store entfernt hat. Die beiden schädlichen Anwendungen erreichten immerhin 1,5 Millionen Downloads. Betroffene Geräte müssen gegebenenfalls auf die Werkseinstellungen zurückgesetzt werden.
https://www.trojaner-info.de/mobile-security/aktuell/verseuchte-android-apps-im-play-store-mit-15-millionen-downloads.html
Android-trojan infects 100 millionen devices
Again found out in the Play Store, an infected App!, trojaner-info.de, 29.08.2019
Es ist eine gefährliche Trojaner-App namens CamScanner, die auf mehr als 100 Millionen Android-Geräten installiert ist. Die App, CamScanner - Phone PDF Creator, die sich in Googles Play Store eingenistet hat, sollten betroffene Nutzer umgehend löschen.
https://www.trojaner-info.de/mobile-security/aktuell/android-trojaner-infiziert-100-millionen-geraete.html
Hacked and overworked into animations sent back by unknown: Image processing into four-dimensioned animations and videos
Unwanted "customer service", witness report by Gooken from 11.19.2019
Jemand (Name und Anschrift sind der Red. bekannt) berichtet von der unbeauftragten Überarbeitung von seinen mit der Kamera von Samsung geschossenen und dort gespeicherten Fotos (Bilder, images) in ganze Animationen bzw. Film-Sequenzen.
Dabei kam es insbesonders bei herkömmlichen Personenaufnahmen zu "natürlichen" Bewegungen abgelichteter Gesichts- und Körperstellen, auf denen sich Wolken bewegten und Pflanzen mit dem Wind drehten usw..
Möglich ist das alles durch eine neuartige App für Smartphones auf Basis der KI, welche grobe Bildsequenzen, aber bereits auch unzusammenhängende Einzelbilder (herkömmliche Fotos) in ausführliche Animationen bzw. Videos verwandeln kann.
Art campaign
With 99 Smartphones against Google Maps, netzpolitik.org, 07.02.2020
Der Künstler Simon Weckert sorgte letzte Woche für viel Wirbel, indem er auf Google Maps einen Stau simulierte. Wir haben mit ihm über künstliche Realitäten, die Macht von Karten und Alternativen zu Google gesprochen.
https://netzpolitik.org/2020/mit-99-smartphones-gegen-google-maps/
Is your smartphone hacked? Find it out!, PC-WELT.de, 11.04.2019
Why should someone eavesdrop me? Because it is possible- or other reason. And spying progs are legal.
https://www.pcwelt.de/a/wurde-ihr-smartphone-gehackt-so-finden-sie-es-heraus,3462629
Encrypted handies got hacked: The Police excavated a criminal organization, PC-WELT.de, 03.07.2020
https://www.pcwelt.de/news/Verschluesselte-Handys-geknackt-Polizei-hebt-Verbrechering-aus-10839471.html
How Facebook tracks your Android-device - even if you do not have a facebook account, netzpolitik.org, 17.01.2019
Auf dem jährlichen Kongress des Chaos Computer Clubs stellte Privacy International eine Recherche zu User-Tracking bei Android-Apps vor. Im Vordergrund der Analyse stehen dabei kostenlose und weit verbreitete Apps mit Facebook-Integration, die - wie sich herausstellte - bereits beim Öffnen automatisch Tracking-Daten an Facebook übertragen, auch bei Nicht-Facebook-Usern.
https://netzpolitik.org/2019/35c3-wie-facebook-dich-auf-deinem-android-geraet-trackt-auch-wenn-du-gar-keinen-facebook-account-hast/
Datenschutz
Each third Android-App does send data to facebook secretly, netzpolitik.org, 12.13.2018
Eine Untersuchung zeigt Datensammelei des Social-Media-Konzerns durch versteckte Tools in vielen Apps. Diese senden auch Daten an Facebook, wenn man gar keinen Account dort hat. Hersteller aus Deutschland zeigen sich nach Bekanntwerden reumütig.
Ohne die Nutzer zu informieren, schicken rund 30 Prozent aller Android-Apps, darunter die App "Meine CDU" und "SPD Landtagsfraktion NRW" heimlich Daten an Facebook. Sie senden sensible Informationen über Religion, Gesundheit oder die sexuelle Orientierung in an den Konzern mit Sitz in Kalifornien. Dazu reicht es, einfach die App zu starten, ein Facebook-Account ist nicht notwendig, wie ein Bericht des Infoportals mobilsicher.de aufzeigt.
[...] Unabhängig von dieser Recherche sollten sich Android-Nutzer bewusst sein, dass Google noch viel mehr über seine Nutzer weiß als Facebook. Was übertragen wird und wie sich das ausschalten lässt, führt Google in einem Support-Dokument aus.
https://netzpolitik.org/2018/ein-drittel-aller-android-apps-schickt-heimlich-daten-an-facebook/
Open letter to Google
Privacy should be no luxury good anymore, netzpolitik.org, 08.01.2020
Vorinstallierte Apps auf Android-Smartphones bedrohen die Privatsphäre ihrer Nutzer*innen. Mehr als 50 Nichtregierungsorganisationen fordern Google auf, das endlich zu ändern.
https://netzpolitik.org/2020/privatsphaere-soll-kein-luxusgut-bleiben/
Howto activate randomized hardware-addresses, PC-WELT.de, 11.24.2019
Avoid your MAC-Adresse from being sent to mobile nets in the next area.
https://www.pcwelt.de/tipps/Windows-10-Zufaellige-Hardwareadressen-aktivieren-10686311.html
Too much electro-rubbish
Why can we not use one charger for all handies?, netzpolitik.org, 14.01.2020
Eigentlich könnten wir alle Smartphones mit dem selben Kabel aufladen. Doch die Pläne der EU wurden nie umgesetzt. Von Abgeordneten erntet die Kommission dafür Ohrfeigen.
https://netzpolitik.org/2020/warum-nicht-ein-ladegeraet-fuer-alle-handys/
 Shocking study: iPhone indeed is the worst telephone of the world, CHIP, 09.07.2016 Shocking study: iPhone indeed is the worst telephone of the world, CHIP, 09.07.2016
Schlechteste Signalstärke - deutliche Unterschiede zwischen rechter und linker Hand, Phone auch bei der Datenübertragung mäßig bis schlecht
Eine Gruppe von Forschern hat die Tauglichkeit moderner Smartphones als tatsächliches Telefon untersucht. Dabei kam heraus: Apples iPhone ist beim Telefonieren richtig schlecht.
http://www.chip.de/news/Schockierende-Studie-iPhone-tatsaechlich-schlechtestes-Telefon-der-Welt_99533860.html
 Security experts warn against Android-App AirDroid, PC-WELT, 02.12.2016 Security experts warn against Android-App AirDroid, PC-WELT, 02.12.2016
Aufgrund von mehreren schweren Sicherheitslücken sollte die Android-App AirDroid deinstalliert werden.
https://www.pcwelt.de/news/Sicherheitsexperten-warnen-vor-Android-App-AirDroid-10086487.html
 More road casualties through the usage of Smartphones, PC-WELT.de, 29.09.2016 More road casualties through the usage of Smartphones, PC-WELT.de, 29.09.2016
https://www.pcwelt.de/news/Mehr-Verkehrs-Tote-durch-Smartphone-Nutzung-10050091.html
 6 reasons against iPhone 7 und 7 Plus, PC-WELT.de, 09.09.2016 6 reasons against iPhone 7 und 7 Plus, PC-WELT.de, 09.09.2016
Das neue iPhone 7 kommt! Doch ist es wirklich so cool? Hier sind 6 Gründe gegen den Kauf des neuen iPhones, https://www.pcwelt.de/ratgeber/Gruende-gegen-Kauf-von-iPhone-7-und-7-Plus-10038270.html .
iPhone-Hacktool Pegasus auch für Android im Umlauf,
Pagasus ist eine Spyware, die sich mit Hilfe einiger Exploits auf einem iPhone installiert. Jetzt wurde sogar eine Android-Version
 Fire hazard: Airlines forbid Galaxy Note 7, PC-WELT.de, 09.09.2016 Fire hazard: Airlines forbid Galaxy Note 7, PC-WELT.de, 09.09.2016
Auf Flügen von drei australischen Airlines darf Samsungs Galaxy Note 7 nicht mehr benutzt werden, .https://www.pcwelt.de/news/Brandgefahr-Australische-Airlines-verbieten-Galaxy-Note-7-10038384.html
 Secure delete of data from old devices getting wasted is a must!, PC-WELT.de, 16.02.2017 Secure delete of data from old devices getting wasted is a must!, PC-WELT.de, 16.02.2017
Wer PCs und Smartphones entsorgen oder verkaufen möchte, sollte seine Daten auf dem Gerät komplett löschen - und zwar endgültig.
https://www.pcwelt.de/a/datenloeschung-bei-altgeraeten-ist-ein-muss,3403429
Malware in all kind of Apps
Android-Trojaner GPlayed discovered
Cisco Talos warns before fake-App, trojaner-info.de, 20.10.2018
Sicherheitsexperten mahnen immer wieder davor, Apps aus dubiosen Quellen zu beziehen. Grund dafür ist, dass Cyberkriminelle eifrig bemüht sind, Malware in Apps aller Art einzubauen. So verhält es sich auch im Fall des von Cisco Talos entdeckten Trojaners GPlayed.
https://www.trojaner-info.de/mobile-security/aktuell/android-trojaner-gplayed-entdeckt.html
Infected app published by criminals each eight seconds
Around 1,9 million new harmful apps
Mobile Malware Report: No detente with Android-Malware, trojaner-info.de, 01.08.2019
G DATA konstatiert: Die Sicherheitslage im Mobile-Bereich bleibt weiterhin angespannt.
Kein neuer Rekord, aber auch keine Entspannung bei Android-Schadsoftware: Die Experten des Cyber Defense Spezialisten G DATA haben in den ersten sechs Monaten rund 1,9 Millionen neue schädliche Apps gezählt. Im Vergleich zum Vorjahr ein leichter Rückgang. Zur Einordnung: Durchschnittlich alle acht Sekunden veröffentlichen Kriminelle eine infizierte App für Android.
https://www.trojaner-info.de/mobile-security/aktuell/mobile-malware-report-keine-entspannung-bei-android-malware.html
Android-Malware with 250 Mio. downloads emerged, PC-WELT.de, 15.03.2019
Das Sicherheitsunternehmen Check Point Research hat zwei massive Kampagnen mit Malware für Android entdeckt.
https://www.pcwelt.de/news/Android-Malware-mit-250-Mio.-Downloads-aufgetaucht-10556033.html
Man-in-the-Disk: Preinstalled Android-apps with exploits
Das Research Team von Check Point findet eine Schwachstelle in der Android Sandbox -Schadsoftware führt: Man-in-the-Middle-Angriffe über externen Speicher von Geräten aus.
Das Research-Team von Check Point hat aktuell Details zur Man-in-the-Disk-Schwachstelle veröffentlicht. Dabei zeigt das Research-Team, wie sie über externe Speichermedien auf Androidgeräten die Sandbox umgehen konnten und danach erfolgreich verschiedene Angriffe gestartet haben.
https://www.trojaner-info.de/mobile-security/aktuell/man-in-the-disk-vorinstallierte-apps-angreifbar-auf-android.html
Howto hide malware in Apps, trojaner-info.de, 08.03.2019
Wie man gefährlichen Code in harmlosen Apps versteckt haben Forscherteams der University of Colorado Boulder (UCB) aufgezeigt.
Wie man Malware in harmlosen Apps versteckt haben Forscher entdeckt. Sie nutzen dafür die schon durch Meltdown und Spectre bekannt gewordene spekulative Ausführung. Der Schadcode kann weder in der harmlosen App noch später im Speicher entdeckt werden. Software-Patches halten die Forscher zudem für wirkungslos.
https://www.trojaner-info.de/mobile-security/aktuell/wie-man-malware-in-apps-versteckt.html
Each third smartphone user is affected by malware
Eine Umfrage zeigt: Mehr als ein Drittel hat sich auf dem Smartphone in den letzten 12 Monaten einen Schädling eingefangen.
https://www.pcwelt.de/a/jeder-dritte-smartphone-nutzer-von-malware-betroffen,3462840
Consumer protectors warn against abo-traps upon the handy, PC-WELT.de, 10.07.2019
20 Euro Abo-Kosten auf der Handyrechnung, obwohl Sie nichts bestellt haben? Verbraucher warnen vor neuen Abo-Fallen.
https://www.pcwelt.de/news/Verbraucherschuetzer-warnen-vor-neuen-Abo-Fallen-auf-dem-Handy-10625720.html
 Android Malware by Toast Overlay, trojaner-info.de, 28.11.2017 Android Malware by Toast Overlay, trojaner-info.de, 28.11.2017
Bis Anfang November wiesen bösartige Apps bis zu 500.000 Installationen auf.
Die Sicherheitsforscher von Trend Micro haben neue Android-Schadsoftware entdeckt, die über einen Toast Overlay-Angriff im Verborgenen weitere Malware auf einem Gerät installieren kann. TOASTAMIGO ist von Trend Micro als ANDROIDOS_TOASTAMIGO erkannt worden.
https://www.trojaner-info.de/mobile-security/aktuell/android-malware-durch-toast-overlay.html
Huawei replaces obiously Google Maps through Tomtom, PC-WELT.de, 20.01.2020
Tomtom soll künftig die Karten und Echtzeitverkehrsinformationen für die Smartphones von Huawei liefern.
https://www.pcwelt.de/news/Huawei-ersetzt-wohl-Google-Maps-durch-Tomtom-10739066.html
HarmonyOS, Hongmeng
Huawei reveals HarmonyOS - an OS for all systems, PC-WELT.de, 10.08.2019
Huawei hat mit HarmonyOS sein eigenes Betriebssystem vorgestellt. Welches auch auf Smartphones läuft.
Sprich: HarmonyOS ist nicht nur für den Einsatz auf Smartphones gedacht, sondern kann auch auf anderen Produktklassen eingesetzt werden. Wie etwa bei smarten Fernsehern, die Huawei ebenfalls anbieten will. Oder auch auf Rechnern, in Smartwatches, in Fahrzeugen oder Smart-Home-Lösungen. Die Idee für ein solches Allzweck-Betriebssystem ist nicht neu: Samsung besitzt beispielsweise Tizen, welches sich aber nie wirklich bei Smartphones durchsetzen konnte.
https://www.pcwelt.de/news/Huawei-enthuellt-HarmonyOS-ein-OS-fuer-alle-Systeme-10644358.html
 Fairphone 3 with /e/OS Fairphone 3 with /e/OS
https://www.pro-linux.de/news/1/27983/fairphone-3-mit-eos-vorgestellt.html
 Software::Mobile devices Software::Mobile devices
Open-Source-mobil-operating-system /e/: Preview onto year 2020, PRO LINUX, 14.11.2019
Gael Duval explains his further plans for /e/. In spring 2020 /e/ OS 1.0 should be released.
[...] /e/ is an operating system based on Lineage OS. The basic system is such modified, that software and services sending personal data to Googl, get deactivated or removed. Even optically /e/ through its own launcher does not look like LineageOS.
https://www.pro-linux.de/news/1/27588/open-source-mobilbetriebssystem-e-ausblick-auf-2020.html
 Android-10-Bug lets freeze devices, PC-WELT.de, 04.21.2020 Android-10-Bug lets freeze devices, PC-WELT.de, 04.21.2020
A Bug in Android 10 forces smartphones to get frozen completely and that they can´t be used anymore.
https://www.pcwelt.de/news/Android-10-Bug-laesst-Geraete-einfrieren-10796276.html
Smartphone: mouseclick- resp. fingertip-fast
 These secret system settings make Android-Smartphones faster, techbook.de, 05.16.2019 These secret system settings make Android-Smartphones faster, techbook.de, 05.16.2019
In the hiidden developer-settings user are enabled to dumb down animations-scales. This makes the Android-Smartphones disctinctly much faster. TECHBOOK explains step by step, how.
It does´nt matter, if the newest or eldest Android-Smartphone is used - it can always made working faster! And if it gets old, the performance declines noticably. A secret menu offers the belonging scales to increase some performance out of the device. TECHBOOK shows, how!
Entwickleroptionen freischalten
Um die geheimen Funktionen verändern zu können, müssen Sie erst die Entwickleroptionen aktivieren.
https://www.techbook.de/mobile/diese-geheime-einstellung-macht-android-smartphones-schneller
https://www.focus.de/digital/handy/schalten-sie-die-entwickleroptionen-frei-diese-geheime-einstellung-macht-android-smartphones-deutlich-schneller_id_10876292.html
Unter dem neuen Menüpunkt Entwickleroptionen finden sich zahlreiche weitere Einstellungsmöglichkeiten!, Anm., Gooken.
 Deaktivte animations: Deaktivte animations:
Who resigns from animations, will save capacities. The smartphone is working quit faster after it. Tap (Poco m5 and Poco m6 Pro) onto system setttings -> more settings -> busyboys -> Hearing and seeingand onto "deactivate animations".
 Android-Patchday: Critical weak point in remote-security removed out of the operating system, 09.03.2021 Android-Patchday: Critical weak point in remote-security removed out of the operating system, 09.03.2021
Wie gewohnt hat Google auch diesen Monat im Rahmen des Android Patchday zahlreiche Sicherheitslücken in den Versionen 8.1, 9, 10 &11 des mobilen Betriebssystems geschlossen. Das aktuelle Android Security Bulletin nennt 38 CVE-IDs. Ungewöhnlich ist, dass die Zahl der CVEs im separaten Bulletin für Googles Pixel-Smartphones jene im regulären Bulletin diesmal übertrifft: 43 sind es dort.
https://www.trojaner-info.de/mobile-security/aktuell/android-patchday-kritische-remote-sicherheitsluecke-aus-betriebssystem-beseitigt.html
 Big lacks in security: Important passwort-Apps allow to outwit themselves, CHIP, 03.11.2020 | von Redaktion CHIP/DPA Big lacks in security: Important passwort-Apps allow to outwit themselves, CHIP, 03.11.2020 | von Redaktion CHIP/DPA
Die doppelte Absicherung von Nutzerkonten empfehlen Experten immer wieder - etwa mit Hilfe von Apps, die Einmal-Passwörter generieren. Doch viele dieser Anwendungen sind selbst nicht sicher. Wie die Zweifaktor-Authentifizierung genau funktioniert, erklären wir Ihnen anschaulich im Video.
Viele Smartphone-Apps für die Zweifaktor-Authentifizierung (2FA) sind Sicherheitsforschern zufolge unsicher. Die Anwendungen, die Einmal-Passwörter als zweiten Faktor neben dem eigentlichen Passwort zum Anmelden bei Nutzerkonten generieren, ließen oft das Anfertigen von Screenshots zu - ein Umstand, der bereits von Schadsoftware ausgenutzt werde.
Zu den Apps, die keinen Schutz vor Screenshots implementiert haben, zählen den Angaben zufolge auch populäre Anwendungen wie der Google Authenticator oder der Microsoft Authenticator. Bei diesen Apps hätten die Experten in einem Kurztest problemlos Screenshots erstellen können.
Wer auf Nummer sicher gehen möchte, sollte eine App wie die freie und quelloffene Android-Anwendung "andOTP" nutzen, die bereits vor Screenshot-Angriffen zum Abgreifen des One-Time-Passwords (OTP) geschützt sei.
Download: andOTP
andOTP - Android App
andOTP - Android App 0.7.0-play
CHIP-Bewertung Gut
Die kostenlose Android-App andOTP erlaubt es Ihnen, sich mittels Zwei-Faktor-Authentifizierung einzuloggen, und ist zudem Open-Source.
Sicherheitslücke soll seit 2014 bekannt sein
Die Screenshot-Problematik soll bereits seit 2014 bekannt sein und war betroffenen Unternehmen zuletzt 2017 vom Sicherheitsunternehmen Nightwatch gemeldet worden, wie dieses mitteilt. Nachdem die Lücken jahrelang nicht behoben worden waren, hatten die Sicherheitsforscher ihre Erkenntnisse Anfang März veröffentlicht.
Download: Kostenlose Passwort-Manager
KeePass 2.44
CHIP-Bewertung Sehr gut
KeePass ist ein starker Passwortverwalter und Passwortgenerator in einem und steht kostenlos zum Download bereit.
Zum Download
...
LastPass (32 Bit) 4.39.0
CHIP-Bewertung Sehr gut
Mit LastPass sind Ihre vielen Online-Passwörter sicher verstaut und jederzeit von Ihnen abrufbar.
LastPass (64 Bit)
LastPass 4.43
CHIP-Bewertung Sehr gut
Mit LastPass sind Ihre vielen Online-Passwörter sicher verstaut und jederzeit von Ihnen abrufbar.
https://www.chip.de/news/Grosse-Sicherheitsluecke-entdeckt-Wichtige-Passwort-Apps-lassen-sich-einfach-austricksen_182540984.html
76 percent of all coworkers do use the same passwords for diffent logins, trojaner-info.de, 09.02.2021
Dies legt nahe, dass viele Mitarbeiter ihre Passwörter wiederverwenden. "Wer an mehreren Stellen das gleiche, einfache Passwort verwendet, macht sich zur leichten Beute für Hacker", warnt Kai Roer, CEO von KnowBe4 Research (ehemals CLTRE).
https://www.trojaner-info.de/business-security/aktuell/id-76-prozent-der-mitarbeiter-verwenden-passwoerter-wieder.html
 Police warns: SMS with dangerous link attacks Android, PC-WELT Police warns: SMS with dangerous link attacks Android, PC-WELT
The police is warning against a mass of attack against Android smartphones. Protect yourself!
https://www.pcwelt.de/news/Polizei-warnt-SMS-mit-gefaehrlichem-Link-greift-Androiden-an-10965089.html
Password Stealer are also active in Germany, trojaner-info.de, 08.04.2019
Laut Kaspersky sind 60 Prozent mehr Nutzer von Diebstahl betroffen.
Sogenannte Password Stealer, d.h. Daten von Nutzern abgreifende Malware, kommen nach Erkenntnissen von Kaspersky immer öfter zum Einsatz, auch in Deutschland: Demnach ist die Zahl der von Cyber-Kriminellen ins Visier genommenen Nutzer von knapp 600.000 im ersten Halbjahr 2018 auf über 940.000 im Vergleichszeitraum 2019 angestiegen.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/password-stealer-auch-in-deutschland-aktiv.html
 The handy is getting hot: recurrent causes and simple solutions, CHIP, 27.08.2020 The handy is getting hot: recurrent causes and simple solutions, CHIP, 27.08.2020
https://praxistipps.chip.de/handy-wird-heiss-haeufige-ursachen-und-einfache-loesungen_123950
Even Samsung-models are affected: Attention, be careful: This nature-image can break down your Android-Smartphones, STERN.de, 04.06.2020
Derzeit kursiert ein Naturfoto in sozialen Netzwerken, das einen unbeabsichtigten Nebeneffekt hat: Richtet man es auf seinem Android-Smartphone als Hintergrundbild ein, stürzt das Gerät ab. Modelle zahlreicher Hersteller sind betroffen.
https://www.stern.de/digital/smartphones/vorsicht--dieses-natur-foto-laesst-reihenweise-android-smartphones-abstuerzen-9286754.html
Datensammlung im Inkognito-Modus
Sammelklage gegen Google in den USA, netzpolitik.org, 03.06.2020
Nutzer in den USA werfen Google vor, sie zu tracken, obwohl sie Inkognito-Modus surfen. Der Konzern wehrt sich gegen die Vorwürfe. Das Klagevolumen könnte in die Milliardenhöhe gehen.
Google verstoße gegen die Abhörschutzgesetze der USA und die kalifornischen Datenschutzgesetze, sie fordern mindestens 5.000 US-Dollar Schadensersatz pro Person.
"Google verfolgt und sammelt den Browserverlauf der Nutzer und andere Daten zu Webaktivitäten, unabhängig davon, welche Maßnahmen sie zum Schutz ihrer Daten ergreifen", heißt es in der Beschwerde. Die drei Kläger sollen Millionen an Nutzern repräsentieren, auf deren Daten Google zugegriffen habe. Dazu gehören Nutzer, die ein Android-Gerät verwenden und nach Juni 2016 im Inkognito-Modus eine Website aufgerufen haben, die Google Analytics oder Ad Manager nutzt. Die zweite Kategorie von Nutzern umfasst Personen ohne Android-Gerät, aber einem Google-Account.
Dass Google die personenbezogenen Daten von Hunderten Millionen US-Amerikanern durch Täuschung abgreife, sei "hochgradig anstößig". Das Volumen der Sammelklage könne durch die Vielzahl potenziell angesprochener Personen demnach mehrere Milliarden US-Dollar erreichen.
Google-Sprecher Jose Castaneda weißt die Anschuldigungen zurück und beruft sich darauf, dass beim Öffnen eines Inkognito-Tabs bei Chrome darauf hingewiesen werde, dass Websites weiter Informationen über das Surf-Verhalten sammeln könnten.
https://netzpolitik.org/2020/sammelklage-gegen-google-in-den-usa/
 Samsung: Find my Mobile-App to detect lost smartphones even, if offline - by offline mode, PC-WELT.de, 25.08.2020 Samsung: Find my Mobile-App to detect lost smartphones even, if offline - by offline mode, PC-WELT.de, 25.08.2020
https://www.pcwelt.de/news/Samsung-Find-my-Mobile-App-bekommt-Offline-Modus-10871539.html
 Howto keep Google under control, netzpolitik.org, 2018 Howto keep Google under control, netzpolitik.org, 2018
Der Internet-Gigant speichert über seine Suchmaschine, Kartendienste und zahlreiche andere Apps standardmäßig eine erschreckend große Datensammlung über uns. Das gilt insbesondere für diejenige Nutzer, die über ihr Android-Handy ständig bei Google eingeloggt sind. Der digitale Fußabdruck lässt sich hier aber ein wenig einschränken.
Als erster Schritt lässt sich die Personalisierung von Werbung über das Google-Netzwerk deaktivieren. Damit kann der Internet-Konzern nicht mehr die vielen persönlichen Daten, die er durch unsere Suchen und andere Aktivitäten erhält, für auf uns zugeschnittene Anzeigen seiner datenhungrigen Kunden verwenden. Auch bei Google sollte man sich möglichst zügig wieder ausloggen, wenn alles notwendige erledigt ist. Das muss allerdings kein großer Mehraufwand sein - mit einem Passwort-Manager kann man die Eingabe von Benutzernamen und Passwörter automatisieren.
Die Nachrichtenseite Wired zählt weitere Schritte auf, um die Datenverwendung durch Google einzuschränken: Dazu zählt das Löschen aller alten Suchanfragen, die man selbst gestellt hat, sowie das Löschen aller gespeicherten Standortdaten. Das Standort-Tracking lässt sich zudem ganz ausschalten. Zudem sollte man als Google-Nutzer unbedingt die Liste der Apps von Drittanbietern durchgehen, denen man im Laufe der Jahre Zugriff auf das eigene Konto gewährt hat: Viele davon hat man längst vergessen, sie sollten wirklich nicht mehr auf die eigenen Daten zugreifen dürfen.
Für alle, die noch weiter gehen wollen, hat systemli.org gerade einen Leitfaden veröffentlicht, wie man Android-Smartphones von Google befreit.
https://netzpolitik.org/2018/kleines-einmaleins-der-digitalen-selbstverteidigung/
Hacker aim multiplied at Apps and mobile devices, trojaner-info.de, 11.04.2020
Check Point Research, the Threat Intelligence-department of Check Point® Software Technologies following actual researches hints to an increasing amount of mobile malware. This pandemic contexts in COVID-19.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/hacker-zielen-vermehrt-auf-apps-und-mobile-geraete.html
Dangerous security gaps in Apple iOS, trojaner-info.de, 24.05.2020
Das hauseigene E-Mail-Programm von Apple - auf allen Geräten ab Werk installiert - offenbart eklatante Schwachstellen und wird zum beliebten Einfallstor für virtuelle Angriffe und Datendiebstahl. Betroffen sind möglicherweise alle IPhones, die je auf den Markt kamen. Das BSI warnt deutsche Nutzer offiziell vor der Applikation.
https://www.trojaner-info.de/mobile-security/aktuell/gefaehrliche-luecken-im-apple-ios.html
 Social-Media-App from USA Social-Media-App from USA
Doubtful data protection of Clubhouse, tagesschau.de, 19.01.2021
https://www.tagesschau.de/wirtschaft/clubhouse-audio-app-deutschland-datenschutz-social-media-101.html
 Made in Israel: Hacking-tools for the eavesdrop-attack, tagesschau.de, 01.29.2021 Made in Israel: Hacking-tools for the eavesdrop-attack, tagesschau.de, 01.29.2021
Weltweit können Ermittler Smartphones hacken. Auch unbemerkt aus der Ferne. Dahinter stehen oft israelische Cyber-Firmen. Ihre Hacking-Tools helfen, Verbrechen zu verhindern. Autoritäre Regime setzen sie aber auch ein, um Oppositionelle auszuhorchen.
Ein Smartphone zu infiltrieren, ist in technischer Hinsicht eine extrem komplexe Aufgabe. Nur wenige Cyber-Unternehmen auf der Welt bieten dafür Dienstleistungen an. Viele der erfolgreichsten Firmen - die den Lauschangriff aufs Smartphone verkaufen - kommen aus Israel. Wie alle Unternehmen der offensiven Cyber-Branche geben sie an, dass mit ihrer Hilfe Verbrechen bekämpft werden. Dass Ermittlungsbehörden mit ihren Produkten potentielle Attentäter ausspähen können. Dass damit Leben gerettet werden. Das stimmt zwar. Dennoch gelangen die Hacking-Tools "Made in Israel" auch in Länder, die keine Rechtsstaaten sind. Länder, die Oppositionelle, kritische Journalisten oder Menschenrechtsaktivisten verfolgen.
Journalist mit "Pegasus"-Software ausspioniert
Einer von ihnen ist der 34-jährige Journalist und Menschenrechtsaktivist aus Marokko, Omar Radi. Laut Amnesty International ist Radi 2019 von marokkanischen Behörden ausspioniert worden. Und zwar mit Hilfe der israelischen Software "Pegasus". Omar Radi hatte über Korruption in seinem Land berichtet und über Verflechtungen zwischen Unternehmen und der politischen Elite. Kritisch äußerte er sich auch über das marokkanische Königshaus. Damit geriet er offenbar ins Visier marokkanischer Ermittlungsbehörden. In einem Interview mit dem Rechercheverbund "Forbidden Stories" sagt Omar Radi über die Ermittler:
"Ich lebe in einem autoritären Polizeistaat. Sie wissen alles über mich. Sie haben alle meine Nachrichten, meine Fotos - mein ganzes Privatleben." Omar Radi
Laut Amnesty International wurde der mobile Internetbrowser von Omar Radis Smartphone umgeleitet. Infolge dessen konnte auch die Spähsoftware "Pegasus" auf das Gerät des Marokkaners gelangen. Die marokkanischen Behörden weisen die Spionagevorwürfe zurück. NSO Group - das israelische Unternehmen hinter der Software "Pegasus" - schrieb damals, man gehe den Hinweisen von Amnesty International nach. Details könne man aber aus rechtlichen Gründen nicht nennen.
Effective eavesdropping thanks smartphones
https://www.br.de/nachrichten/deutschland-welt/made-in-israel-hacking-tools-fuer-den-lauschangriff,SNTteWq
You can pay per Smartphone and SmartWatch: Howto, PC-WELT.de, 09.23.2019
Apple Pay, Google Pay and Samsung Pay
https://www.pcwelt.de/ratgeber/Bezahlen-per-Handy-Wallet-Apps-Apple-Pay-Android-Pay-Samsung-Pay-9940802.html
Increase the font-size on problems upon small displays: Settings ->, Display->,font size.
 Evil Android-Bug crashes Apps: Howto solve the failure, CHIP, 24.03.2021, Evil Android-Bug crashes Apps: Howto solve the failure, CHIP, 24.03.2021,
Android: App wurde beendet
Zahlreiche Android-Nutzer berichten über Abstürze auf ihren Smartphones. Ein Fehler sorgt dafür, dass Apps immer wieder crashen. Neben dem offiziellen Update steht aber auch eine inoffizielle Lösung für Android-Nutzer bereit.
Android-User berichten derzeit von Problemen mit dem Smartphone-Betriebssystem. Demnach stürzen einige Apps bei der Nutzung immer wieder ab. Wie TheVerge berichtet, liegt die Ursache der Crashes in "Android System WebView". Diese Komponente des Smartphone-OS ermöglicht es Android-Apps, Web-Inhalte anzuzeigen. Passiert das aktuell, kommt es dann wohl zum Absturz.
Mittlerweile ist ein Update für "Android System WebView" verfügbar, das Sie ganz einfach herunterladen können. Eine Anleitung geben wir Ihnen unten an die Hand. Gerade Googles eigene Android-Apps waren von dem Bug betroffen und ließen sich eine Zeit lang nicht nutzen.
https://www.chip.de/news/Bug-sorgt-fuer-Abstuerze-auf-Android-Smartphones_183377441.html
 Android-error "App closed" - howto solve the problem, CHIP, 29.03.2021 Android-error "App closed" - howto solve the problem, CHIP, 29.03.2021
https://praxistipps.chip.de/android-fehler-app-wurde-beendet-so-beheben-sie-das-problem_33747
 Android-Apps do crash by crash and the possible cause for it, CHIP, 11.11.2014 Android-Apps do crash by crash and the possible cause for it, CHIP, 11.11.2014
https://praxistipps.chip.de/android-apps-stuerzen-staendig-ab-daran-kanns-liegen_35948
 Android: App do not open - what do I have to do?, CHIP, 24.09.2014 Android: App do not open - what do I have to do?, CHIP, 24.09.2014
https://praxistipps.chip.de/android-app-oeffnet-sich-nicht-was-tun_34629
 Many people make the mistake not to encrypt data upon online-storage, CHIP, 23.10.2021 Many people make the mistake not to encrypt data upon online-storage, CHIP, 23.10.2021
Einfach mal Daten zu Google Drive, OneDrive oder Dropbox laden. Das ist bequem und geht schnell - bestens geschützt sind Ihre privaten Informationen dort aber nicht unbedingt. Möchten Sie dieses Risiko vermeiden, hilft ein kleines Gratis-Tool weiter.
...
https://www.chip.de/news/Cryptomator-OneDrive-Dropbox-Co-verschluesseln_152398420.html
 Problems with the SD-Card for your Smartphone, Xiaomi Poco m5: no recoginitions. Formatting with exfat? FOCUS-Online and Gooken recommend file system FAT32 Problems with the SD-Card for your Smartphone, Xiaomi Poco m5: no recoginitions. Formatting with exfat? FOCUS-Online and Gooken recommend file system FAT32
Um die Karte auf dem PC mit einem Kartenleser mit (dem rpm-basierten) "Universal Linux" einbinden zu können, bedarf es der Installation folgender Pakete: exfat-utils (el8), exfatprogs (el8), fuse-common (el8) und fuse-exfat (el8). Die Einbindung selbst erfolgt nun mittels Befehl
mount.fuse-exfat Partition-der-SD-Karte Mountpoint, z.Bl mount.fuse-exfat /dev/sdb1 /mnt4, bei Debian mittels Befehl mount.exfat-fuse aus exfat-fuse (deb).
Generell empfiehlt sich für "Universal-Linux" zum umfassenden Mounten die Installation aller möglichen Dateisysteme (Paket e2fsprogs (el8) für ext4, libbtrfs0, libbtrfs-util1 für btrfs, reiserfsprogs (el8) für Reisers, reiser4progs (el8, Reiserfs mit besonderer Eignung für Flash-Media), squashfs (el8), vfat (altes Windows-Dateisystem), MacOSX, .... Am besten kann man diese Pakete von rpmfind.net oder Mirror fr2.rpmfind.net downloaden.
exfat-fuse empfiehlt sich für SD-Karten im Vergleich zu vfat32, da beim Formatieren bei vfat32 eine Obergrenze von um die 4 GB besteht, bei exfat-fuse hingegen keine! Mehr als 4 GB fallen zum Beispiel nach einem umfassenden Backup des Systems und installierter Anwendungen an oder bei gro&szilg;en Videodateien.
Der interne Speicher vom Poco m5 beläuft sich auf satte 130 GB...
Doch immer wieder wird die SD-Karte nicht von Android bzw. MIUI unter der Formatierung mit dem Dateisystem exfat erkannt. Es geht hin und her: mal Erkennung, mal nicht. Für eine garantierte Erkennung sorgt erst die von FOCUS-Online empfohlene Formatierung der SD-Karte (bei uns 128 GB) mit FAT-32. Mit FAT-32 haben wir schon auf der Vorgäger-SD-Karte (mit 16 GB) ganz gute Erfahrungen gemacht. Wieso der MIUI-Dateimanager exfat vorschlug, wissen wir nicht. Mit einem Kartenleser ist eine Formatierung auf dem PC-Betriebssystem "Universal Linux" jedenfalls auf gewohnte Art (mit dem Befehl mkfs.vfat32 bzw. über einen Partitionsmanager) möglich.
Speichern Sie vorsichtshalber immer das Backup und die ApKs/Apps des Smartphones samt Konfigurationsdateien auf SD-Karte, dann mittels SD-Kartenleser von SD-Karte auf die SSD/Festplatte Ihres PC ab, Anm., Gooken., die Red., 03.12.2024.
 ATTENTION for smartphones like Xiaomi Poco m5: Actualized system-UI-plugin can break your phone completely, where the system boot gets damaged, so that the phone can´t boot ! Each boot, system breaks down. In this case, a complete wipe of the internal storage imust get performed! ATTENTION for smartphones like Xiaomi Poco m5: Actualized system-UI-plugin can break your phone completely, where the system boot gets damaged, so that the phone can´t boot ! Each boot, system breaks down. In this case, a complete wipe of the internal storage imust get performed!
We recommend System-UI-Plugin-15.0.1.54.0 from on apkcombo.com and no other version and especially not from apkmirror.com !
Be a little bit careful with App MIUI Hidden Settings (1), NEVER forbid an App the use of (as shown) already registrated links! Otherwise Android resp. MIUI don´t boot the system anymore, they halt forever, so that you have to wipe the complete Smartphone (if you don´,t have a complete backup).
For the same reason also be careful with App Secret Settings, especially if system configuration wasn´t enabled for this App right before.
We´d like to repeat for security for Smartphones just to "hit" (tap) upon everything (as we see in the following)!".
But you REALLY HAVE TO NOTICE few more exceptions for Xiaomi Poco m5 / m6 Pro for it, for example:
deactivation of the packet-installation (App) through (App) Hidden Settings (1) (MIUI and HyperOS will not boot anymore!),
System-ui should beware all read and access rights upon all files. For all these two points, Apps like securty should have care for it automatically - but they don̪t ...
The connection with a database-server should not get forbidden in any case (Analytics, packet manager, ...).
Picture in picture: should only be forbidden for apps listed by system settings ( and not Hidden Settings (1) resp. App Permissions ), so be careful !
 System-Update-App, preinstalled Apps on Huawei Smartphone Y360-U61 like screen lock (after suspend/standby per key stroke with the middle key of the right side or determinable timeout) or Huawei Start, SMS/MMS, addressbook (Kontakte), telephone, GooglePlayStore, Google-Drive (Cloud), Google Chome (Browser), Google Maps, Gmail (alternative: k9-mail), Gboard (80 MB; alternative: keyboard / Tastatur, 11 MB, from apkpure.com), YouTube, photos, video telephony (Hangouts), ..., system-settings and settings (Wifi including Wifi over hotspots or WPA2 encrypted over the local WLAN-router (for the cost of the ISP of the PC) instead SIM-card-provider, Bluetooth, Apps, location access,.USB-printer, USB-scanner, TV-device-port, ...) , tools, data-backup-App, system update app, app update app, Chrome Browser, E-Mail-Client (gmail: IMAP, income server), time scheduler, calendar, clock (world clock, stopwatch timer,...), SIM-toolkit, weather broadcast, Cell-Broadcast, Dialer, Printer-Spooler, video player, Huawei Video Player, TouchPalX, Files, Deletion (system cleaner), audio recording (App Soundrekorder within tools), VPN, Proxy Handler, packet installer (Paket Installer), text editor (editor), data backup, digital camera, camera/ video recording, pocket calculator, FM-radio (UKW, App: FM-broadcast), pocket lamp, ..., games like Dragon Hunt and car racing, ... , ... System-Update-App, preinstalled Apps on Huawei Smartphone Y360-U61 like screen lock (after suspend/standby per key stroke with the middle key of the right side or determinable timeout) or Huawei Start, SMS/MMS, addressbook (Kontakte), telephone, GooglePlayStore, Google-Drive (Cloud), Google Chome (Browser), Google Maps, Gmail (alternative: k9-mail), Gboard (80 MB; alternative: keyboard / Tastatur, 11 MB, from apkpure.com), YouTube, photos, video telephony (Hangouts), ..., system-settings and settings (Wifi including Wifi over hotspots or WPA2 encrypted over the local WLAN-router (for the cost of the ISP of the PC) instead SIM-card-provider, Bluetooth, Apps, location access,.USB-printer, USB-scanner, TV-device-port, ...) , tools, data-backup-App, system update app, app update app, Chrome Browser, E-Mail-Client (gmail: IMAP, income server), time scheduler, calendar, clock (world clock, stopwatch timer,...), SIM-toolkit, weather broadcast, Cell-Broadcast, Dialer, Printer-Spooler, video player, Huawei Video Player, TouchPalX, Files, Deletion (system cleaner), audio recording (App Soundrekorder within tools), VPN, Proxy Handler, packet installer (Paket Installer), text editor (editor), data backup, digital camera, camera/ video recording, pocket calculator, FM-radio (UKW, App: FM-broadcast), pocket lamp, ..., games like Dragon Hunt and car racing, ... , ...
 Reset Y360 to default by pressing both keys on the right side (what opens a menu) or by a system app Reset Y360 to default by pressing both keys on the right side (what opens a menu) or by a system app
 More apps from PlayStores (... but we do not recommend all of them...!): "Find my device (smartphone)", hidden settings for MIUI (packet name: com.ceyhan.sets), secure settings, hidden settings for Android (packet name: com.netvor.hiddensettings), FritzPhone (phone over the local WLAN-router (for the costs of the ISP for the PC instead of SIM-card-provider), ..., Browser: Via Browser (0,95 MB only), Super Backup (for the backup of quit all onto SD-card), PrivacyBrowser upon Orbot (Tor-Proxy) with Waterfox or Firefox Nightly, as much as Waterfox that Firefo, still with the possibility about:config for configuration in detail, extension FoxyProxy running upon Orbot (Tor with VPN-App-firewall) and extensions NoScript, umatrix, ublock-origin, Consent-O-Matic (from UNI Aarhus, Denmark), UserAgent switcher, disable WebRTC, JavaScript Toggle Button, "goal keeper" Privacy Badger, dark reader together withe dark mode (eyes saving night mode), Orbot, UNIX/Linux- iptables based Root Firewall AFWall+, FileEncryptor, ZenEncrypt, Hidden Settings for MIUI (1) AND/OR (not the same!) MIUI Hidden Settings (2) AND/OR System Settings and Secure Settings, APK Permission Remover, Permission Pilot, Advanced Permission Manager, Berechtigungsmanager (access right manager), Kingoroot or Kingroot (to get into the root-mode and back to usermode by one simple click), personalDNSFilter, NetworkMonitor (TU Darmstadt, with which you can check out VPN-server), App "Connection Stabilizer Booster" (details see point 10) and 12, protection against the changing of Wifi- (WLAN-) network-connections into other, therefore very expensive ones, against hijacking and much more), Tor-Browser for Android (Tor, The Onion Router, actual version (with Firefox 68.12.0 for the Huawai Y60-U61) from torproject.org or apkpure.com), KartaGPS (downloadable maps from all over the world for using offline) and/or OsmAmd (offline map view and offline GPS navigation recommended by guardianproject.info/releases für localprivacy), Antivirus Helper (virus and malware online-virus-definition-file, Contacts, Calendar, Anti Spy Mobile FREE, internal password-manager or keepass (passwort-manager and -generator), MacChanger, App "Autostart Apps" (in order to autostart some Apps directly past the system boot), Backup/Restore ( use the reliable, complete data securing one from Huawei Y360-U61 out of the directory named tools ), Private Location (fake-location), Facebook Lite, Messenger Lite ( with over 1 billion addresses you can´t resign from, you can keep it as an apk only for demand, that can be called by phone totally for free, without any costs, recommended) or WhatsApp (also for free) and/or alternatively (highly recommended by the press and for free) SMS/MMS-encrypting messenger Signal ( Android 4.4+, processor: universal, the for the first time crashfree and non-beta-version 5.4.7 or higher from february 2021, internet-download from https://www.apkmirror.com/apk/signal-foundation/signal-private-messenger/signal/signal-private-messenger-5.4.7/release/s) or Threema (up to now a costly, non free messanger), Twitter-App, Gooken-SearchEngine, Onion-Search-Engine (alias Zwiebel-Suchmaschine beneath Tor-Browser App), GPS-Map-Router (cards for offline use from all over the world, routing, ...), app to move apps from internal memory (telephony memory) to SD card, Tagesschau-App, phone book with maps (DasOertliche: telephone book including actual offers, petrol prices, cinema programs, bars, pubs, hotels, quarters, restaurants, sport, freetime, supermarkets, fast food & Co., cash dispenser, drugstores, everything for your pet, car accidents, flowers, books & magazines, cafés and bakeries, electro markets, culture, furnitures & decoration, fashion, night life, taxi, wellness & cosmetics, ... or: dasoertliche und/oder "Das Telefonbuch" (The Telephone Book) from Telekom AG, ...), ...), day planner, dating-apps, Advanced Thread Killer (instead of this use the preinstalled process manager: system-settings -> apps -> active apps), Inkognito (Spyware-Killer), data cleaner (Ancleaner), environment noise measurement, Language Translator (DeepL or other ones), OpenCamera, word dictionaries (offline-dictionary and language translator named Wörterbuch apk), railroad: Deutsche Bahn ( DB-Navigator, start, destinationl, tickets, ...), TV-program (TV-Browser), VLC Media Player, car number plates (Kennzeichen Europa), traffic jam warnings, radar warning, disaster prevention (warnings-app from the BKK: NINA, police warnings/reports, ...), file encryption, password manager (Passwort Tresor), Facebook/Facebook-Lite, gmail and/or k-9-mail, Total Commander (file manager; there is already a file manager from MIUI resp. Xiaomi), Linux Terminal Emulator, Linux commands (manual), cloud-storage, image viewer (AA Image Viewer), event calendar (App: Was geht? u.a.), Wikipedia (online-encyclopedia), TV-Browser (TV-programm), stocks news, Online-Banking-App, PhotoTAN-App for Online Banking, QR & Barcode-Scanner, text editor, office, pay services (cash points), remote control (satellite, garage, home door, doors, central heating, windows, shutters, car, TV/dvd/cd/video/audio, Free world TV, internet radio, heating, OpenCamera, bank safes, safes, drones remote control, surveying cams, household devices, electrical outlets, bugging devices, else remote devices, ...), SmartHome control, ISS-locator (ISS space station), horoscope (Widder Horoskop), moon phases, Free Internet-Radio (Internet Radio), Free Internet-TV or German TV Life Channels & Radio (recommended, many internet TV sender, even ARD and RTL, internet radio: more than 1.000 stations from all over the world), streaming services, Filesharing, video conferences, spirit level (Bubble Level or other apps), angle measurement (Bubble Level or other apps), ruler (Bubble Level or other apps), (air pressure measurement, height measurement, GPS coordinate finder, compass, telescope, night seeing, microscope, magnifier, ruler (1D, 2D, Bubble Level), goniometer (Bubble Level), distance messurement (plumnet), temperature measurement (Thermometer), moisture measurement, radiation measurement (radiation detector), metal detector, satellite finder, anti dog barking, Luftqualitäts-App, AntennaPodcast (OpenSource), Wikipedia resp. mathematics-, physics- and chemestry app, language learning, apps for online shopping (ebay, amazon, ...), PayPal, currency calculator, network sniffer, ..., Videobearbeitungs-App, many many games like chess (Schach free), card games like Schafskopf, Solitaire (Solitaire-Palast), Doppelkopf and Skat (Skat-Palast), Pokémon (Pok&eactue;mon-hunt in the outside areas), puzzles, sport: football, handball, tennis, ski, hockey, billiard, ...., JumpnRun, action games (arcade), person-alien shooter, space shooter, action shooter , ..., satellite finder, ISS finder, NINA (government emergency areas warning), KATWARN, App "Find my device", Walkie-Talkie-App, Termux (you can easily install the complete Debian Linux with it by command pkginstall), adb-termux (The Advanced Device Bridge adb and fastboot to get connected easily with any PC or another phone in root mode), ... More apps from PlayStores (... but we do not recommend all of them...!): "Find my device (smartphone)", hidden settings for MIUI (packet name: com.ceyhan.sets), secure settings, hidden settings for Android (packet name: com.netvor.hiddensettings), FritzPhone (phone over the local WLAN-router (for the costs of the ISP for the PC instead of SIM-card-provider), ..., Browser: Via Browser (0,95 MB only), Super Backup (for the backup of quit all onto SD-card), PrivacyBrowser upon Orbot (Tor-Proxy) with Waterfox or Firefox Nightly, as much as Waterfox that Firefo, still with the possibility about:config for configuration in detail, extension FoxyProxy running upon Orbot (Tor with VPN-App-firewall) and extensions NoScript, umatrix, ublock-origin, Consent-O-Matic (from UNI Aarhus, Denmark), UserAgent switcher, disable WebRTC, JavaScript Toggle Button, "goal keeper" Privacy Badger, dark reader together withe dark mode (eyes saving night mode), Orbot, UNIX/Linux- iptables based Root Firewall AFWall+, FileEncryptor, ZenEncrypt, Hidden Settings for MIUI (1) AND/OR (not the same!) MIUI Hidden Settings (2) AND/OR System Settings and Secure Settings, APK Permission Remover, Permission Pilot, Advanced Permission Manager, Berechtigungsmanager (access right manager), Kingoroot or Kingroot (to get into the root-mode and back to usermode by one simple click), personalDNSFilter, NetworkMonitor (TU Darmstadt, with which you can check out VPN-server), App "Connection Stabilizer Booster" (details see point 10) and 12, protection against the changing of Wifi- (WLAN-) network-connections into other, therefore very expensive ones, against hijacking and much more), Tor-Browser for Android (Tor, The Onion Router, actual version (with Firefox 68.12.0 for the Huawai Y60-U61) from torproject.org or apkpure.com), KartaGPS (downloadable maps from all over the world for using offline) and/or OsmAmd (offline map view and offline GPS navigation recommended by guardianproject.info/releases für localprivacy), Antivirus Helper (virus and malware online-virus-definition-file, Contacts, Calendar, Anti Spy Mobile FREE, internal password-manager or keepass (passwort-manager and -generator), MacChanger, App "Autostart Apps" (in order to autostart some Apps directly past the system boot), Backup/Restore ( use the reliable, complete data securing one from Huawei Y360-U61 out of the directory named tools ), Private Location (fake-location), Facebook Lite, Messenger Lite ( with over 1 billion addresses you can´t resign from, you can keep it as an apk only for demand, that can be called by phone totally for free, without any costs, recommended) or WhatsApp (also for free) and/or alternatively (highly recommended by the press and for free) SMS/MMS-encrypting messenger Signal ( Android 4.4+, processor: universal, the for the first time crashfree and non-beta-version 5.4.7 or higher from february 2021, internet-download from https://www.apkmirror.com/apk/signal-foundation/signal-private-messenger/signal/signal-private-messenger-5.4.7/release/s) or Threema (up to now a costly, non free messanger), Twitter-App, Gooken-SearchEngine, Onion-Search-Engine (alias Zwiebel-Suchmaschine beneath Tor-Browser App), GPS-Map-Router (cards for offline use from all over the world, routing, ...), app to move apps from internal memory (telephony memory) to SD card, Tagesschau-App, phone book with maps (DasOertliche: telephone book including actual offers, petrol prices, cinema programs, bars, pubs, hotels, quarters, restaurants, sport, freetime, supermarkets, fast food & Co., cash dispenser, drugstores, everything for your pet, car accidents, flowers, books & magazines, cafés and bakeries, electro markets, culture, furnitures & decoration, fashion, night life, taxi, wellness & cosmetics, ... or: dasoertliche und/oder "Das Telefonbuch" (The Telephone Book) from Telekom AG, ...), ...), day planner, dating-apps, Advanced Thread Killer (instead of this use the preinstalled process manager: system-settings -> apps -> active apps), Inkognito (Spyware-Killer), data cleaner (Ancleaner), environment noise measurement, Language Translator (DeepL or other ones), OpenCamera, word dictionaries (offline-dictionary and language translator named Wörterbuch apk), railroad: Deutsche Bahn ( DB-Navigator, start, destinationl, tickets, ...), TV-program (TV-Browser), VLC Media Player, car number plates (Kennzeichen Europa), traffic jam warnings, radar warning, disaster prevention (warnings-app from the BKK: NINA, police warnings/reports, ...), file encryption, password manager (Passwort Tresor), Facebook/Facebook-Lite, gmail and/or k-9-mail, Total Commander (file manager; there is already a file manager from MIUI resp. Xiaomi), Linux Terminal Emulator, Linux commands (manual), cloud-storage, image viewer (AA Image Viewer), event calendar (App: Was geht? u.a.), Wikipedia (online-encyclopedia), TV-Browser (TV-programm), stocks news, Online-Banking-App, PhotoTAN-App for Online Banking, QR & Barcode-Scanner, text editor, office, pay services (cash points), remote control (satellite, garage, home door, doors, central heating, windows, shutters, car, TV/dvd/cd/video/audio, Free world TV, internet radio, heating, OpenCamera, bank safes, safes, drones remote control, surveying cams, household devices, electrical outlets, bugging devices, else remote devices, ...), SmartHome control, ISS-locator (ISS space station), horoscope (Widder Horoskop), moon phases, Free Internet-Radio (Internet Radio), Free Internet-TV or German TV Life Channels & Radio (recommended, many internet TV sender, even ARD and RTL, internet radio: more than 1.000 stations from all over the world), streaming services, Filesharing, video conferences, spirit level (Bubble Level or other apps), angle measurement (Bubble Level or other apps), ruler (Bubble Level or other apps), (air pressure measurement, height measurement, GPS coordinate finder, compass, telescope, night seeing, microscope, magnifier, ruler (1D, 2D, Bubble Level), goniometer (Bubble Level), distance messurement (plumnet), temperature measurement (Thermometer), moisture measurement, radiation measurement (radiation detector), metal detector, satellite finder, anti dog barking, Luftqualitäts-App, AntennaPodcast (OpenSource), Wikipedia resp. mathematics-, physics- and chemestry app, language learning, apps for online shopping (ebay, amazon, ...), PayPal, currency calculator, network sniffer, ..., Videobearbeitungs-App, many many games like chess (Schach free), card games like Schafskopf, Solitaire (Solitaire-Palast), Doppelkopf and Skat (Skat-Palast), Pokémon (Pok&eactue;mon-hunt in the outside areas), puzzles, sport: football, handball, tennis, ski, hockey, billiard, ...., JumpnRun, action games (arcade), person-alien shooter, space shooter, action shooter , ..., satellite finder, ISS finder, NINA (government emergency areas warning), KATWARN, App "Find my device", Walkie-Talkie-App, Termux (you can easily install the complete Debian Linux with it by command pkginstall), adb-termux (The Advanced Device Bridge adb and fastboot to get connected easily with any PC or another phone in root mode), ...
 MIUI Hidden Settings (2): Especially Google Settings, Ads Settings (with options like personalized advertisement and the setting of a new, the old one overwriting ad-ID) and MIUI Second Space (dual Apps; über diese Funktion verfügt bereits in Einstellungen unter Apps das POCO M6 Pro) do interest. MIUI Hidden Settings (2): Especially Google Settings, Ads Settings (with options like personalized advertisement and the setting of a new, the old one overwriting ad-ID) and MIUI Second Space (dual Apps; über diese Funktion verfügt bereits in Einstellungen unter Apps das POCO M6 Pro) do interest.
Notice, that Google Settings and Ads Settings can´t get opened anymore out of MIUI Hidden Settings after the deactiviation of too many internal options.
 Orbot for the smartphone Orbot for the smartphone
Last version (apkcombo.com from July 2025, https://apkcombo.com/de/orbot/org.torproject.android/download/apk) did not work sometimes (problems with the local DNS 127.0.0.1 (Orbot-TorDNS).
This here does:
Orbot latest version, https://www.heise.de/download/product/orbot-93611/download or
https://guardianproject.info/releases/orbot-latest.apk
The size of the APK increased here from 30 MB to over 100 MB, what might brings new and patched libraries for Android with it, Gooken, rem., the red., 08.03.2025.
...
 ATTENTION for smartphones like Xiaomi Poco m5: Actualized system-UI-plugin can break your phone completely, where the system boot gets damaged, so that the phone can´t boot ! Each boot, system breaks down. In this case, a complete wipe of the internal storage imust get performed! ATTENTION for smartphones like Xiaomi Poco m5: Actualized system-UI-plugin can break your phone completely, where the system boot gets damaged, so that the phone can´t boot ! Each boot, system breaks down. In this case, a complete wipe of the internal storage imust get performed!
We recommend System-UI-Plugin-15.0.1.54.0 from on apkcombo.com and no other version and especially not from apkmirror.com !
 HOW DO I ADMIN APSS UNDER ANDROID? HOW DO I ADMIN APSS UNDER ANDROID?
"Eliminate" the "daemon" for Android: Howto deactivate the MIUI- and system daemon, Jan Kluczniok, netzwelt.de, 01.13.2024
Der MIUI- beziehungsweise System Daemon sammelt auf Xiaomi-Handys Daten zur Verbesserung der Benutzeroberfläche. Wer dies nicht möchte, kann das Tool wie folgt deaktivieren.
Auf vielen Xiaomi-Handys ist die System-App "MIUI Daemon" vorinstalliert. Anders als der Name suggeriert, ist die App nicht nur auf Geräten mit der inzwischen eingestellten Benutzeroberfläche MIUI zu finden, sondern auch auf Geräten mit dem neuen HyperOS.
Diese Daten sammelt der MIUI Daemon
Hinter der mysteriösen Anwendung verbirgt sich ein Tool, mit dem der Hersteller offenbar einige Daten zur Verbesserung der Benutzeroberfläche sammelt. Der Analyse eines Xiaomi-Fanblogs zufolge sammelt der MIUI Daemon die folgenden Daten über euer Handy.
die Größe des verbauten Speichers
die Zeit, wie lange der Bildschirm eingeschaltet ist
Ladestatistiken des Hauptspeichers
Batterie und CPU-Statistiken
Den Status von Bluetooth und WiFi
die IMEI-Nummer
Eine Spionage-App ist die Anwendung also nicht, denn sie sammelt keine direkten persönlichen Daten von euch, sondern nur Informationen zum Zustand des Gerätes. Wer dennoch ein Unbehagen verspürt, kann den MIUI Daemon deaktivieren. Dies ist entweder direkt bei der Einrichtung eures Xiaomi-Handys möglich, aber auch nachträglich.
Das ist in wenigen Schritten erledigt. Das folgende Video zeigt euch wie ihr vorgehen müssst.
Nachfolgend findet ihr auch noch einmal eine Schritt-für-Schritt-Anleitung mit Screenshots zu den einzelnen Schritten.
MIUI Daemon - Zustimmung widerrufen
...
https://www.netzwelt.de/anleitung/197497-xiaomi-handys-daemon-austreiben-so-deaktiviert-miui-daemon-2024.html
 HOWTO PERSONALIZE MY ANDROID-SMARTPHONE HOWTO PERSONALIZE MY ANDROID-SMARTPHONE
Xiaomi: Howto deactivate advertisement in MIUI and HyperOS, Marcel Laser, netzwelt.de, 02.13.2024
Xiaomi nutzt seine Benutzeroberflächen MIUI und HyperOS auch dazu, um euch in vielen Gelegenheiten auf dem Handy auch Werbung anzuzeigen. Wir verraten ihr diese abschaltet.
MSA im Android-System: Deaktiviert die Systemanwendung umgehend
Persönliche Werbeanzeigen durch Google deaktivieren
Sicherheits-App: Werbevorschläge deaktivieren
Mi Browser: Werbevorschläge deaktivieren
https://www.netzwelt.de/anleitung/187320-werbung-xiaomi-handys-deaktivieren-so-gehts.html
 HOWTO FREE INTERNAL MEMORY FOR ANDROID-DEVICES... HOWTO FREE INTERNAL MEMORY FOR ANDROID-DEVICES...
Lock applications (especially bloatware), Gooken, 02.28.2024
MIUI-Sicherheit-App aufrufen (tappen) -> Klick auf Einstellungen -> Geschwindigkeit erhöhen -> Apps sperren: Sperren einzelner Apps aus einer Liste von Apps heraus: Umsetzen des Schiebeschalters auf aktivieren (on).
Wir wählten die System-Apps: MIUI Info-Assistent, UKW-Radio, Google Messages (zur Alternative schlichte SMS), Services and Feedback, GetApps, Themen und Lite.
Weiterer Vorteil dieser Methode: Die Geschwindigkeit erhöht sich merklich!
 HOWTO FREE INTERNAL MEMORY FOR ANDROID-DEVICES... HOWTO FREE INTERNAL MEMORY FOR ANDROID-DEVICES...
Android: Howto deinstall bloatware without root-access, Markus Kasanmascheff, netzwelt.de, 11.29.2023
Überflüssige Software in Form von Bloatware kann euer Android-Smartphone schnell zumüllen. Wir zeigen euch, wie ihr sie auch ohne Root-Rechte entfernt und löscht.
Auf den Smartphones fast aller großen Hersteller wie Xiaomi, Samsung oder Sony sind inzwischen zahlreiche Apps vorinstalliert. Mit dieser Bloatware schnell eine Fülle an Datenmüll ansammeln, die man nicht unbedingt auf dem Handy haben will. Das Problem: Die Bloatware lässt sich, anders als normale Apps, nicht einfach deinstallieren.
Doch keine Sorge. Um Android-Bloatware zu entfernen, müsst ihr aber nicht gleich euer Handy rooten und eine spezielle Lösch-App nutzen. Mit den offiziellen Android-Tools von Google für PCs könnt ihr die Bloatware ebenfalls leicht löschen.
Dazu müsst ihr lediglich euer Telefon per USB-Kabel anschließen und ein paar Befehle ausführen. Komplett entfernt werden die Apps von eurem Android-Gerät dabei allerdings auch nicht. Als reaktivierbares Datenpaket bleiben sie euch weiterhin erhalten und werden lediglich aus eurem Android-Nutzerkonto entfernt.
Trotzdem lässt sich durch dieses teilweise Entfernen der Android-Bloatware in der Regel einiges an Speicherplatz freiräumen, da die Bloatware-Apps dann nicht installiert sind und sich auch keine App-Updates anhäufen. Und auch eure App-Liste wird dadurch übersichtlicher. Wie ihr Android-Bloatware ohne Root-Zugriff entfernen und bei Bedarf wieder installieren könnt, zeigen die folgenden Schritte.
https://www.netzwelt.de/anleitung/193588-android-so-entfernt-bloatware-ohne-root-zugriff.html
 HOWTO CONFIGURE THE BUSYBOY OF ANDROID HOWTO CONFIGURE THE BUSYBOY OF ANDROID
Make the Xiaomi-handy faster through few clicks, netzwelt.de, 12.26.2023
Jan Kluczniok
Wenn euer Xiaomi-Handy beim Bildschirmwechsel ruckelt, müsst ihr nicht direkt ein neues Handy kaufen. Wie ihr euer altes Smartphone schneller macht, erklären wir euch kurz und knapp.
Xiaomi-Handy schneller machen: So geht es mit wenigen Klicks
Zwar kann der chinesische Hersteller Xiaomi mit einem guten Preis-Leistungs-Verhältnis seiner Handys überzeugen, doch vor allem Poco- und Redmi-Geräte laufen nicht immer ruckelfrei. Probleme können hier insbesondere nach längerer Nutzung auftreten. Es gibt aber einen einfachen Trick, um die Geräte wieder flott zu machen: das Abschalten von System-Animationen.
Das sind beispielsweise Überblendungen bei einem Bildschirmwechsel. Also eher Zier-Elemente als eine wirklich wichtige Funktion. Dennoch beanspruchen sie Ressourcen und belasten somit Prozessor und Arbeitsspeicher. Könnt ihr auf die Animationen verzichten, könnt ihr sie mit wenigen Schritten abschalten und das System beschleunigen.
Die entsprechende Option ist jedoch gut in den Einstellungen versteckt. So findet ihr sie.
So entfernt ihr Animationen auf eurem Xiaomi-Handy
1
Öffnet die Einstellungen und scrollt runter bis ihr die Option "Weitere Einstellungen" findet.
2
Nun wählt ihr "Bedienungshilfen" aus.
3
Tippt nun zunächst auf den Reiter "Sehen" und dann auf "Animationen entfernen".
4
Der Schalter wird nun blau. Die Animationen sind deaktiviert und euer Handy sollte nun deutlich schneller laufen.
Welche Einstellungen ihr auf eurem Xiaomi-Handy noch ändern solltet, zeigen wir euch in der verlinkten Anleitung.
https://www.netzwelt.de/anleitung/211968-xiaomi-handy-schneller-so-geht-wenigen-klicks.html
 Central security. AFWall+ and/or Orbot (anonymizing Tor-Proxy with a highly effective, intergrated VPN-App-Firewall), firewall within MIUI-system-settings (Poco m5), private location (fake-location) and vairous MIUI-system-settings (Poco m5), hidden settings, secure settings, ..., SuperBackup, Google Drive and/or Xiaomi-Cloud and/or Custom Recovery Rom TWRP, browser like Brave Browser or Firefox Nightly ( unlike other Firefox still with about:config, that means the possibility to configure with includes of user.js, the file we introduced in this excurs; don´t forget to set javascript.enabled, safebrowsing.malware and safebrowsing.phishing to false EACH TIME) with mentioned extensions NoScript, ublock-origin and/or AdNaussem, "goal keeper" Privacy Badger, AdWebblocker and maybe Privacy Possum and/or dark reader together with dark mode (eyes saving night resp. dark mode) Central security. AFWall+ and/or Orbot (anonymizing Tor-Proxy with a highly effective, intergrated VPN-App-Firewall), firewall within MIUI-system-settings (Poco m5), private location (fake-location) and vairous MIUI-system-settings (Poco m5), hidden settings, secure settings, ..., SuperBackup, Google Drive and/or Xiaomi-Cloud and/or Custom Recovery Rom TWRP, browser like Brave Browser or Firefox Nightly ( unlike other Firefox still with about:config, that means the possibility to configure with includes of user.js, the file we introduced in this excurs; don´t forget to set javascript.enabled, safebrowsing.malware and safebrowsing.phishing to false EACH TIME) with mentioned extensions NoScript, ublock-origin and/or AdNaussem, "goal keeper" Privacy Badger, AdWebblocker and maybe Privacy Possum and/or dark reader together with dark mode (eyes saving night resp. dark mode)
 Poco m5 mit Orbot (Tor-Netzwerk): Orbot provides access to the Tor-network. Poco m5 mit Orbot (Tor-Netzwerk): Orbot provides access to the Tor-network.
Advantages of Orbot:
IP-Anonymization for the browser and all other Apps,
highly effective encryption
fake-location
anonymized DNS-queries by tordns resp. the Entry Guard´
local VPN
high effective VPN-APP-firewall and
bypass of the data traffic away from the provider (ISP). That reduces the data volume and protocollings.
Only one advantage: Orbot is not the fastest, so traffic speed might decline sometimes.
VPN-App-Firewall of Orbot: All Apps can get deactivated, except those Apps for actual communication in the net. There still might be activated Apps requiring the activation of App (system-)settings there too. In thiese cases, enable both data transfer, WLAN and mobile!
Howto configure Orbot:
Download orobot apk out of the internet like from apkpure.
Install the apk like all other apps with a packet manager.
Open (start) Orbot, click on the symbol left upper corner for configuration, for example enter top-level-domains of countries like US and UK in forbid entry nodes: {us},{en}.
In system settings, in the section for VPN, allow Orbot for VPN and forbid all other connections, so that only Orbot gets allowed.
After this, set Orbot in Autostart, to get it started each Android system boot: acitvate orbot in Autostart.
Activate the apps allowed for net communication in Orbot by setting belonging hooks: phone, browser, e-mail-client and so on.
All the other apps (such with no hooks) will get blocked!
In browsers like Firefox Nightly enter Orbot as the proxy: You will need firefox-extension FoxyProxy for it. There enter localhost bzw. 127.0.0.1 through port 9050 upon the protocol SOCKS5.
Activate Orbot by clicking right upon "START" you can see within the onion.
Orbot is building up ithe connection within a few seconds.
 For Orbot Firefox requires the extension Foxy Proxy. For Orbot Firefox requires the extension Foxy Proxy.
Most suitable for Orbot are Firefox Nightly and Firefox derviate Waterfox.
 Set the following values after typing about:config into the addressline: Set the following values after typing about:config into the addressline:
network.proxy.socks to 127.0.0.1
network.proxy.socks_port to 9050
network.proxy.socks_remote_dns to true # Orbot makes and anoymizies all DNS-queries with it!
network.proxy.no_proxies_on .safe-ws.de, .ebay.com # expample.-exceptions for Orbot
At last, for full anoymiszation, it is recommended to name the proxy in MIUI too: Miui-Settings -> WLAN -> click upon the active WLAN-connection to set Proxy 127.0.0.1, Port 9050, but not all Apps might communicate in the net anymore..
 Block of really ALL Apps, DNS-configuration for Smartphone Xiaomi Poco m5 (MIUI 13 or 14, Android 12), Text by Gooken, 02.12.2024 Block of really ALL Apps, DNS-configuration for Smartphone Xiaomi Poco m5 (MIUI 13 or 14, Android 12), Text by Gooken, 02.12.2024
All listed Apps can get blocked in the VPN-Firewall of Orbot. But not all Apps are listed there. Do the following to block the rest too:
Our recommended DNS-configuration:
Systems settings -> connections and share -> Private DNS: NONE !
System settings -> WLAN (Wifi Accss Point) -> Extended settings -> Proxy: 127.0.0.1 (Orbot bzw. Tor) with port 9050 (protocol: Socks5), DNS1 und DNS2: 127.0.0.1 (Orbot resp. Tor), adress-room: IPv4
System settings -> APN (mobil Access Point, mobil) -> Extended settings -> Proxy (and also, if possible, for server and MMS-server): 127.0.0.1 (Orbot bzw. Tor) with port 9050 (protocol Socks5), DNS1 und DNS2: 127.0.0.1 (Orbot resp. Tor), adress-room: IPv4 (also set the connection type there (in the APN-entry) to LTE only, if possible)
Now DNS-queries are done by TorDNS (Orbot) in both cases, mobil and Wifi!
Router: DNS1 asnd DNS2: dns3.digitalcourage.de
Activate Orbot-VPN in the VPN-section of Android tapping on Android- system settings. There, you might can care explicitly for all connections of the Smartphone using this and the same VPN (Orbot) only by setting a hook for it.
Well done (quit). We are (quit) ready.
 But settings above are WRONG! Apps like messengers (like WhatsApp and Signal) do no you as the owner of the anonymized IP even by name now! But settings above are WRONG! Apps like messengers (like WhatsApp and Signal) do no you as the owner of the anonymized IP even by name now!
So you have to remove the Orbot-Proxy and its Port from (the settings of) APN and for the Wlan-connection again completely!
 Orbot fürs Smartphone Orbot fürs Smartphone
Letzte Version (Juli 2025 von apkcombo.com) lief nicht so besonders (Probleme mit der DNS 127.0.0.1 (localhost, hier Orbot-TorDNS)).
Diese hier tuts:
Orbot latest version, https://www.heise.de/download/product/orbot-93611/download
Der Umfang stieg dabei von 30 MB auf über 100 MB, was auf neue und überarbeitete Android-Bibliotheksfunktionen schließen lässt, Gooken, Anm., die Red., 03.08.2025.
 In MIUI-Setttings in section VPN care for all possible net-connections running over Orbot-VPN, that means without exception! In MIUI-Setttings in section VPN care for all possible net-connections running over Orbot-VPN, that means without exception!
 For the totalk anoymizatioon by Orbot enter the Orbot-Proxy into MIUI: Miui-Settings -> WLAN -> click resp. tap upon the active WLAN-connection (WLAN-acess-point) and enter Orbot´s proxy in proxy 127.0.0.1 with its port 9050 into port. Notice, that most, but not all apps can connect with it. Make the same for mobile connections: click resp. tap onto MIUI-settings, and search in the mask above for APN (mobile access point of your ISP-provider). Choose the old address-room IPv4 and enter in the apperearing text input fields Orbot-proxy again: proxy 127.0.0.1 and port 9050. For the totalk anoymizatioon by Orbot enter the Orbot-Proxy into MIUI: Miui-Settings -> WLAN -> click resp. tap upon the active WLAN-connection (WLAN-acess-point) and enter Orbot´s proxy in proxy 127.0.0.1 with its port 9050 into port. Notice, that most, but not all apps can connect with it. Make the same for mobile connections: click resp. tap onto MIUI-settings, and search in the mask above for APN (mobile access point of your ISP-provider). Choose the old address-room IPv4 and enter in the apperearing text input fields Orbot-proxy again: proxy 127.0.0.1 and port 9050.
Now, with all this or just Orbot you achived the promised highest 1000% protection and anoymization for your smartphone !
 Refresh the connection in Orbot from time to time, especially after using WhatsApp and Facebook and right before surfing with the browser, press refresh ! Refresh the connection in Orbot from time to time, especially after using WhatsApp and Facebook and right before surfing with the browser, press refresh !
 Firefox Nightly (the browser, we´d like to recommend for the smartphone for its opportunitiv to get configured in detail through about:config): Make the start side (in the normal, but not private mode) blank: Tap (short press) upon the three small points from the above right corner ->, settings ->start side: Stories ("randomized" links to any websites), recent visited sides and bookmarks: deacitvate all of them. Firefox Nightly (the browser, we´d like to recommend for the smartphone for its opportunitiv to get configured in detail through about:config): Make the start side (in the normal, but not private mode) blank: Tap (short press) upon the three small points from the above right corner ->, settings ->start side: Stories ("randomized" links to any websites), recent visited sides and bookmarks: deacitvate all of them.
The start of the (recommended) private mode is made in the fastest way by a long tapping (pressing) onto the small box showing the amount of opened tabs.
 Privatsphäre: Firefox sammelt jetzt standardmäßig Daten für die Werbeindustrie, netzpolitik.org, 15.07.2024 Privatsphäre: Firefox sammelt jetzt standardmäßig Daten für die Werbeindustrie, netzpolitik.org, 15.07.2024
Der eigentlich für guten Datenschutz bekannte Browser Firefox sammelt seit neuestem Daten über das Verhalten der Nutzer:innen. Das sei indirekt gut für deren Privatsphäre, sagen die Firefox-Macher. Gegner sehen hingegen darin eine weitere Schwächung der Privatsphäre. Die Funktion lässt sich abschalten.
[..] So entfernst Du die neue Funktion
Im Firefox lässt sich die Funktion unter "Einstellungen" bei "Datenschutz &Sicherheit" entfernen, indem man den Haken bei "Websites erlauben, datenschutzfreundliche Werbe-Messungen durchzuführen" herausnimmt. Auch andere Browser nutzen solche Technologien: Hier steht, wie man in Apples Safari und Googles Chrome die Privatsphäreeinstellungen verbessert.
https://netzpolitik.org/2024/privatsphaere-firefox-sammelt-jetzt-standardmaessig-daten-fuer-die-werbeindustrie/
Location data: Tracking-company aims to control billion handies, netzpolitik.org, 01.31.2024
Recherchen von 404 Media zeigen auf, wie sich der weltweite Datenhandel der Werbeindustrie zur Massenüberwachung einsetzen lässt. Ein kommerzielles Werkzeug soll die Wohnadressen und engsten Kontakte von Zielpersonen verraten - und auf Wunsch sogar ihre Handys hacken können. Zur anvisierten Zielgruppe gehören Geheimdienste.
https://netzpolitik.org/2024/standortdaten-tracking-firma-will-milliarden-handys-ueberwachen-koennen/
 In remembrance: Location data is already obtained in the IP ! In remembrance: Location data is already obtained in the IP !
Don´t forget to set the router for Wifi and LAN, the access point for mobile (APN) to IPv4 in system settings as much as Orbot too, so that your identity can not be found out right at the beginning.
Mit der Rechnernummer (IP) aus IPv4 lässt sich dann leider der Standort bestimmen, wird kein IP-anonymisierender Proxy wie Orbot mit integriertem VPN benutzt. Die Deaktivierung der Standortinformation u.a. in Systemeinstellungen bleibt damit wirkungslos., Anm., Gooken, die Red., 16.06.2024
 Android Android
Location history: Google tracks user, even if they did contradict explicitly, sueddeutsche.de, 08.14.2024
Wenn Google-Nutzer den Standortverlauf aktivieren, zeigt die persönliche Zeitachse ein detailliertes Bewegungsprofil.
Wenn Google-Nutzer den Standortverlauf ausschalten, speichert das Unternehmen trotzdem Bewegungsdaten.
Betroffen sind mehr als zwei Milliarden Menschen, die Android-Smartphones oder iPhones mit Google-Diensten verwenden.
Wer das Tracking verhindern will, muss die "Web- und App-Aktivitäten" komplett deaktivieren.
[...] Welche Fragen bleiben offen?
Die SZ wollte von Google unter anderem wissen:
Welche Google-Apps und Dienste Standortdaten im persönlichen Google-Profil senden und speichern.
Wann und wie oft diese Daten gesendet werden und wie detailliert das entstehende Bewegungsprofil ausfällt.
Ob Nutzer eine Möglichkeit haben, die Übermittlung von Standortdaten zu unterbinden, ohne Web- & App-Aktivitäten komplett abzuschalten.
Ob es möglich ist, die gespeicherten Standortdaten nachträglich gesammelt zu löschen, ohne alle weiteren Nutzerdaten zu entfernen.
Wofür die gespeicherten Bewegungsdaten genutzt werden und welche personalisierte Werbung damit geschaltet wird.
Google hat auf diese Fragen bislang nicht geantwortet. Wir ergänzen den Artikel, sobald uns nähere Informationen vorliegen.
https://www.sueddeutsche.de/wirtschaft/standortverlauf-google-verfolgt-nutzer-auch-wenn-sie-explizit-widersprechen-1.4092772
Lesermeinung Gooken
Alternativ kann man nach der Einrichtung des Android-Smaprthones den kompletten Google-Account löschen. Das Smartphone darf nur nicht wieder beim Booten hängenbleiben...
 Smartphone, Extions for Firefox classic and nightly: noscript, ublock-origin, u-matrix, privacy badger, location (Standort, insbes. für Firefox classic), random-user-agent, decentral eyes, javascript-toogle-buttion, WebRTC toggle-buttion, referrer removal, dark mode. Tip: Install of them! After this, change to the configuraiton mode through typing in about:config into the address line and seit the listed variables as described for the file named user.js for Firefox of your PC Notice, that this is not possible for Firefox classic. Smartphone, Extions for Firefox classic and nightly: noscript, ublock-origin, u-matrix, privacy badger, location (Standort, insbes. für Firefox classic), random-user-agent, decentral eyes, javascript-toogle-buttion, WebRTC toggle-buttion, referrer removal, dark mode. Tip: Install of them! After this, change to the configuraiton mode through typing in about:config into the address line and seit the listed variables as described for the file named user.js for Firefox of your PC Notice, that this is not possible for Firefox classic.
 Censorship! Censorship!
Orbot analyzes traffic, it makes a traffic control, that can lead into domains and websites not loading anymore! In order to prevent this, allow full Circuit Padding in the setting of Orbot!
Well done.
Orbot should work now fine!
 TorDNS TorDNS
Uncensored DNS, wiki.archlinux.org
If your local DNS recursor is in some way censored or interferes with DNS queries, see Alternative DNS services for alternatives and add them in a separate server-section in /etc/pdnsd.conf as per Pdnsd#DNS servers.
Ensuring relay is working
First check that tor.service started correctly either with the journal or by checking the unit status.
If there are no errors, one can run nyx to ensure your relay is making connections. Do not be concerned if your new relay is slow at first; this is normal. After approximately 3 hours, your relay should be published and searchable on Relay Search.
TorDNS
DNS queries can be performed through a command line interface by using tor-resolve For example:
tor-resolve archlinux.org
66.211.214.131
The Tor 0.2.x series also provides a built-in DNS forwarder. To enable it add the following lines to the Tor configuration file and restart the daemon:
/etc/tor/torrc
DNSPort 9053
AutomapHostsOnResolve 1
AutomapHostsSuffixes .exit,.onion
This will allow Tor to accept DNS requests (listening on port 9053 in this example) like a regular DNS server, and resolve the domain via the Tor network.
A downside of both methods is that they are only able to resolve DNS queries for A, AAAA and PTR records; MX and NS queries are never answered. For more information see this Debian-based introduction.
Using TorDNS systemwide
It is possible to configure your system, if so desired, to use TorDNS for any A, AAAA and PTR queries your system makes, regardless of whether or not you eventually use Tor to connect to your final destination. To do this, configure your system to use 127.0.0.1 as its DNS server and edit the DNSPort line in /etc/tor/torrc to show:
DNSPort 53
Alternatively, you can use a local caching DNS server, such as dnsmasq or pdnsd, which will also compensate for TorDNS being a little slower than traditional DNS servers. The following instructions will show how to set up dnsmasq for this purpose. Note, if you are using NetworkManager you will need to add your configuration file to to the location outlined in NetworkManager#dnsmasq.
Change the tor setting to listen for the DNS request in port 9053 and install dnsmasq.
Modify its configuration file so that it contains:
/etc/dnsmasq.conf
no-resolv
port=53
server=127.0.0.1#9053
listen-address=127.0.0.1
These configurations set dnsmasq to listen only for requests from the local computer, and to use TorDNS at its sole upstream provider. It is now necessary to edit /etc/resolv.conf so that your system will query only the dnsmasq server.
/etc/resolv.conf
nameserver 127.0.0.1
Start the dnsmasq daemon.
Finally if you use dhcpcd you would need to change its settings to that it does not alter the resolv configuration file. Just add this line in the configuration file:
/etc/dhcpcd.conf
nohook resolv.conf
If you already have an nohook line, just add resolv.conf separated with a comma.
https://wiki.archlinux.org/title/Tor#Using_TorDNS_for_all-dns_queries
 Block of really ALL Apps, DNS-configuration for Smartphone Xiaomi Poco m5 (MIUI 13 or 14, Android 12), Text by Gooken, 02.12.2024 Block of really ALL Apps, DNS-configuration for Smartphone Xiaomi Poco m5 (MIUI 13 or 14, Android 12), Text by Gooken, 02.12.2024
All listed Apps can get blocked in the VPN-Firewall of Orbot. But not all Apps are listed there. Do the following to block the rest too:
Our recommended DNS-configuration:
Systems settings -> connections and share -> Private DNS: NONE !
System settings -> WLAN (Wifi-Accss Point) -> Extended settings -> Proxy: 127.0.0.1 (Orbot bzw. Tor) with port 9050 (protocol: Socks5), DNS1 und DNS2: 127.0.0.1 (Orbot resp. Tor)
System settings -> APN (mobil Access Point, mobil) -> Extended settings -> Proxy: 127.0.0.1 (Orbot bzw. Tor) with port 9050 (protocol Socks5), DNS1 und DNS2: 127.0.0.1 (Orbot resp. Tor)
Now DNS-queries are done by TorDNS (Orbot) in both cases, mobil and Wifi!
Router: DNS1 asnd DNS2: dns3.digitalcourage.de
 For PC (Tor recommended) and smartphone (PrivateDNS): For PC (Tor recommended) and smartphone (PrivateDNS):
DNS-Server free from censorship, digitalcourgage.de, 08.20.2013
Wir betreiben den freien DNS-Server dns3.digitalcourage.de. Dafür, dass wir das schon so lange anbieten können, gilt besonderer Dank unseren Mitgliedern und Spenderinnen und Spendern.
Digitalcourage
Seitliche Aufnahme von mehreren unterschiedlich dicken Magazinen. Daneben ein aufgeklappter Laptop.
DNS-Server sind sowas wie die "Telefonbücher des Internets". Damit Sie die "Nummern" von Herrn Müller, Herrn Meier oder Frau Schulze finden können, schauen Sie (bzw. Ihr Computer) dort nach und "wählt" dann die entsprechende (IP-)Nummer. Was aber wenn jemand meint, dass die Nummer von Herrn Meier gar nicht ins Telefonbuch aufgenommen wird und damit niemand seine Nummer findet? Dafür gibt's dann "alternative Telefonbücher", in denen alle Nummern aufgeführt werden, und nicht einzelne Nummern ‚wegzensiert‘ worden sind. So funktionieren auch unsere alternativen DNS-Server: Hier sind alle IP-Nummern aufgeführt, die Ihr Computer dann eben auch ´connecten´ kann. Wie Sie das bei sich eintragen können, haben wir hier möglichst einfach beschrieben (aber ein bisschen fachsimpeln lässt sich - pardon - nicht ganz vermeiden).
Unser DNS-Server
dns3.digitalcourage.de
Unsere neueste Hardware, exklusiv für verschlüsseltes DNS (bisher nur DoT):
Serverstandort: externes, deutsches Rechenzentrum
IPv4: 5.9.164.112
IPv6: 2a01:4f8:251:554::2
Port: 853
sha256 SPKI pinset: 2WFzfO2/56HpeR+v/l25NPf5dacfxLrudH5yZbWCfdo=
Common Name des Zertifikats (tls_auth_name): dns3.digitalcourage.de
Aussteller des Zertifikats: Let's Encrypt
kein Logging - nur im Fehlerfall (ohne Client-IP)
Aus technischen Gründen verwendet dieser Server eine andere IP im Backend (für den Resolver), weshalb bei üblichen DNS-Leaktests folgende IP angezeigt wird: 168.119.141.43 / dns3.digitalcourage.de
Unseren DNS-Server betreiben wir schon seit vielen Jahren. Server kosten Geld und wollen ständig betreut werden. Dies können wir nur leisten, weil uns viele Menschen regelmäßig unterstützen. Ermöglichen auch Sie diese Arbeit mit einer Spende oder noch wirksamer mit einer Mitgliedschaft.
Warum braucht man das?
Wir betreiben freie DNS-Server, weil wir zeigen wollen, dass Zensur umgangen werden kann - und ständig befürchten müssen, dass sie ausgeweitet wird. Der Anlass zur Einrichtung unseres zensurfreien Servers war das so genannte "Zugangserschwerungsgesetz", mit dem bestimmte Inhalte im Internet zensiert werden sollten. Dieses Gesetz wurde 2009 vorgeschlagen und 2010 beschlossen, aber schon 2011 - auch dank unserer Arbeit - wieder vollständig aufgehoben. Die damalige Bundesfamilienministerin (und heutige EU-Kommissionpräsidentin) Ursula von der Leyen hatte sich für die Einführung der Internetzensur eingesetzt, die ihr den Namen "Zensursula" eingebracht hat. Aber diese Zensurtechnik ist nicht nur übergriffig, sie kann von Interessierten auch mit wenig Aufwand umgangen werden (auch ohne unsere Hilfe). Vor allem werden so die Inhalte nicht entfernt, um die es bei diesen Vorhaben geht und die echten Schaden anrichten. Auch nach dem Aus des Zugangserschwerungsgesetzes gibt es immer wieder Vorschläge, eine Zensur in ähnlicher Form wieder einzurichten. Bürgerrechtler fordern stattdessen eine bessere Ausstattung in finanzieller und personeller Form für die zuständigen Polizeibehörden und ein "Löschen statt Sperren".
Die Zensur von Inhalten im Internet ist nicht im Sinne der freien Meinungsäußerung und kann zur Verzerrung des politischen Meinungsbildes führen. Die Existenz einer nicht öffentlichen Zensurliste ist unvereinbar mit dem Gebot der Presse-, Informations- und Meinungsfreiheit. Erfahrungen aus anderen Staaten zeigen: Es gibt keine Garantie dafür, dass die Beschränkung der Maßnahme auf bestimmte Vergehen nicht durch weitere Beschlüsse aufgeweicht wird. Der Grundstein für eine weitreichende Zensur wäre gelegt. So wäre es ein leichtes, Websites von Gewerkschaften, Parteien, kritischer Presse, Nicht-Regierungs-Organisationen, unliebsamen Blogs etc. zu sperren. Eine demokratische und zivilgesellschaftliche Kontrolle ist unmöglich, da diese Listen nicht öffentlich zugänglich sein würden. Allein Polizeibehörden entscheiden, wer auf dieser Liste landet.
Um eine DNS-Zensur zu umgehen, müssen Sie einen zensurfreien DNS-Server verwenden. Wie Sie die entsprechende Einstellung verändern, ist abhängig vom verwendeten Betriebssystem. Weiterführende Berichterstattung zum "Zugangserschwerungsgesetz" von 2009/10 finden Sie bei 🔗Heise ausführlich beschrieben.
Verschlüsselung der DNS-Anfragen mit DNS-over-TLS
Üblicherweise werden DNS-Anfragen nicht verschlüsselt. Deshalb können diese Anfragen auf dem Weg mitgelesen und manipuliert werden. Auch das wollen wir ändern. Unsere Server unterstützen verschlüsselte Verbindungen via DNS-over-TLS (DoT). Allerdings muss DoT bei den üblichen Betriebssystemen manuell konfiguriert werden.
Wir setzen uns für Ihre Privatsphäre und Grundrechte ein. Werden Sie Fördermitglied bei Digitalcourage.
Verfügbarkeit
Als gemeinnütziger Verein, der nur nebenbei öffentliche Infrastruktur betreibt, können wir keinen 100%-Dauerbetrieb garantieren, aber falls der Server hängt, kümmern wir uns darum.
Wir stellen eine Statusseite unter status.digitalcourage.de zur Verfügung.
https://digitalcourage.de/support/zensurfreier-dns-server
 Smartphone Xiaomi Poco m5: Following updates are recommended (apks): MIUI-Upgrade from MIUI 13.08 to MIUI 13.10 or MIUI 14, Poco-Launcher (not all version run error-free, we recommend version 4.39.7.6274-11071434-43), Xiamomi Sicherheit/Security (com.miui.securitycenter 8.7.6-240118-1.1 from 01.17.2024, previous verson from April 2023, (with one bug) 7.7.3-230431.1.3-40, ISO/EC 27701, 27018, 27001, TrusT, TÜV Rheinland, 7.7.3-230431.1.3-40, some versions do not run error-free), Xiaomi Sicherheit-/Security-core components, Xiaomi Systemui, Xiaomi Systemui-Plugin, Xiaomi Settings (com.xiaomi.misettings, version 2.9.9.72...), Orbot, Firefox and/or Firefox Nightly, Webview ( Apps like Private Location do not work correctly after it, so the default version is recommended), k-9-mail, Xiaomi Themes, Gallery, Camera, Earphone, Clock, Mi Video, Mi Musik and Wallpaper-Karussel ( Wallpaper Caroussel), Texteditor, Aldi Talk, All Backup & Restore, Analytics, Android Auto, Android für Barrierefreiheit, Android SDK, Antenna Pod, APKCombo Installer, App Vault (info-assisstent), Google Assistent, Assistent, Bereinigung, screenrecorder, calculatorr, Carrier Services, Cit, CIT-com.miui.cit, cn.wps.xiaomi.abroad.lite, com.android.camera, com.android.deskclock, com.android.sharedstoragebackup, com.android.shell, com.android.soundrecorder, com.android.thememanager, com.google.android.projection.gearhead, com.huaqin.sarcontroller, com.mi.android.globalfilexplorer, com.miui.backup, com.miui.backreport, com.miui.extraphoto, com.miui.gallery, com.miui.global.packageinstaller, com.miui.internal.app.SystemApplication, com.miui.misound, com.miui.msa.global, com.miui.qr, com, com.xiaomi.midrop,com.xiaomi.xmsf, Google Contacts, CQR, Data Restore Tool, Device Health Service, Digital Wellbeing, Galerie, Galerie-Editor, Gboard oder Schlichte Tastatur (Simple Keyboard), Google-Apps, Hidden Settings for MIUI, secret settings, K-9-Mail, Karta GPS, Kompass, Meta App Installer, Meta Services, Mi Browser, Mi Dokumente Viewer, Mi GetApps, Mi Home, Mi Music (Version 8.0.01.090420i), Mi Video (Version 2023113002), Mi Account, Mi Credit, Mi Remote, Mi Scanner, MIUI 13 Updater, MIUI Roms, MIUI Compass, MIUI Feedback, Ohrhörer, Open Keychain, Password Store, Peel Mi Remote, Permission Manager, PlayAutoinstalls, Share Mi, MI/Xiaomi Rekorder, System UI (Installation des Update war nicht möglich), Systembenutzeroberfläche-Plugin, Themes for MIUI, Tile Fun (Game), Tool for data restauration, weather-by-xiaomi, Xiaomi Gallery, Xiaomi Notes, Xiaomi Package Installer, Xiaomi service framework, Xiaomi Sim Aktivierungdienst, Xiaomi System Apps Updater, Xiaomi Konto, MIUI SDK bzw. MIUI SYSTEM, (versions past Dezember 2022 cause error messages of Xiaomi account and Xiaomi cloud!), notifications/Benachrichtigungen (you might not want to update it, if errors are caused). Smartphone Xiaomi Poco m5: Following updates are recommended (apks): MIUI-Upgrade from MIUI 13.08 to MIUI 13.10 or MIUI 14, Poco-Launcher (not all version run error-free, we recommend version 4.39.7.6274-11071434-43), Xiamomi Sicherheit/Security (com.miui.securitycenter 8.7.6-240118-1.1 from 01.17.2024, previous verson from April 2023, (with one bug) 7.7.3-230431.1.3-40, ISO/EC 27701, 27018, 27001, TrusT, TÜV Rheinland, 7.7.3-230431.1.3-40, some versions do not run error-free), Xiaomi Sicherheit-/Security-core components, Xiaomi Systemui, Xiaomi Systemui-Plugin, Xiaomi Settings (com.xiaomi.misettings, version 2.9.9.72...), Orbot, Firefox and/or Firefox Nightly, Webview ( Apps like Private Location do not work correctly after it, so the default version is recommended), k-9-mail, Xiaomi Themes, Gallery, Camera, Earphone, Clock, Mi Video, Mi Musik and Wallpaper-Karussel ( Wallpaper Caroussel), Texteditor, Aldi Talk, All Backup & Restore, Analytics, Android Auto, Android für Barrierefreiheit, Android SDK, Antenna Pod, APKCombo Installer, App Vault (info-assisstent), Google Assistent, Assistent, Bereinigung, screenrecorder, calculatorr, Carrier Services, Cit, CIT-com.miui.cit, cn.wps.xiaomi.abroad.lite, com.android.camera, com.android.deskclock, com.android.sharedstoragebackup, com.android.shell, com.android.soundrecorder, com.android.thememanager, com.google.android.projection.gearhead, com.huaqin.sarcontroller, com.mi.android.globalfilexplorer, com.miui.backup, com.miui.backreport, com.miui.extraphoto, com.miui.gallery, com.miui.global.packageinstaller, com.miui.internal.app.SystemApplication, com.miui.misound, com.miui.msa.global, com.miui.qr, com, com.xiaomi.midrop,com.xiaomi.xmsf, Google Contacts, CQR, Data Restore Tool, Device Health Service, Digital Wellbeing, Galerie, Galerie-Editor, Gboard oder Schlichte Tastatur (Simple Keyboard), Google-Apps, Hidden Settings for MIUI, secret settings, K-9-Mail, Karta GPS, Kompass, Meta App Installer, Meta Services, Mi Browser, Mi Dokumente Viewer, Mi GetApps, Mi Home, Mi Music (Version 8.0.01.090420i), Mi Video (Version 2023113002), Mi Account, Mi Credit, Mi Remote, Mi Scanner, MIUI 13 Updater, MIUI Roms, MIUI Compass, MIUI Feedback, Ohrhörer, Open Keychain, Password Store, Peel Mi Remote, Permission Manager, PlayAutoinstalls, Share Mi, MI/Xiaomi Rekorder, System UI (Installation des Update war nicht möglich), Systembenutzeroberfläche-Plugin, Themes for MIUI, Tile Fun (Game), Tool for data restauration, weather-by-xiaomi, Xiaomi Gallery, Xiaomi Notes, Xiaomi Package Installer, Xiaomi service framework, Xiaomi Sim Aktivierungdienst, Xiaomi System Apps Updater, Xiaomi Konto, MIUI SDK bzw. MIUI SYSTEM, (versions past Dezember 2022 cause error messages of Xiaomi account and Xiaomi cloud!), notifications/Benachrichtigungen (you might not want to update it, if errors are caused).
Actual date: 12.31.2023
 You can update Smartphone Xiaomi Poco m5 from: apkcombo.com, apkpure.com, apkmirror.com, ... or Google Play Store You can update Smartphone Xiaomi Poco m5 from: apkcombo.com, apkpure.com, apkmirror.com, ... or Google Play Store
 What you can update for Xiaomi Poco m5 (downgrade again, if the update doesn´t work error-free): ApkCombo-installer, com.miui.global.packageinstaller, MIUI-Upgrade von MIUI 13.08 auf MIUI 13.10 oder MIUI 14, Poco-Launcher (da neuere Version nicht ganz fehlerfrei liefen, empfehlen wir com.mi.android.globallauncher Version 4.39.7.6274-11071434-43), Xiamomi Sicherheit/Security (com.miui.securitycenter_7.7.3-230431.1.3-40, manch höhere Version arbeiten nicht fehlerfrei), MIUI Sicherheitskomponenten, Xiaomi Sicherheit-/Security-Kernkomponente, Systemdienst-Plugin, Xiaomi Systemui (miui.systemui.plugin), Xiaomi Systemui-Plugin, Xiaomi Settings (Einstellungen, com.xiaomi.misettings, Version 2.9.9.67), UniPlay Service, MIUI Hidden Settings Activity, Orbot, Firefox und/oder Firefox Nightly, Webview ( Apps wie Private Location laufen dann nicht mehr korrekt, ggfls. default Version belassen), k-9-mail, Xiaomi Themes, Gallery (com.miui.gallery), Gallerie, Gallerie-Editor, Camera (com.android.camera) bzw. Opencamera (net.sourcforge.opencamera), Xiaomi notes (Notizbuch), Earphone, Mi Video, Mi Musik und das Wallpaper-Karussel ( Mi Wallpaper Carousel) bzw. Hintergundbild-Karussell, Themes for MIUI, MIUI Daily Wallpaper, Texteditor, Aldi Talk, Backup (com.miui.backup), Fehlermeldung (com.miui.bugreport), All Backup & Restore, Analytics, Android Auto, Android für Barrierefreiheit, Android SDK bzx. System SDK (Update funktionierte nicht), Antenna Pod, App Vault (info-assisstent), Google Assistent, Assistent, Bereinigung, Bildschirmaufnahme, Calculator (com.miui.calculator), Carrier Services, Cit, CIT-com.miui.cit, cn.wps.xiaomi.abroad.lite, com.android.camera, Clock bzw. com.android.deskclock (am besten: Huawei-Clock), com.android.sharedstoragebackup, com.android.shell, com.android.soundrecorder, com.android.thememanager, com.google.android.projection.gearhead, com.huaqin.sarcontroller, com.mi.android.globalfilexplorer, com.miui.backup, com.miui.backreport, com.miui.extraphoto, Xiaomi Gallery, com.miui.gallery, com.miui.global.packageinstaller, com.miui.internal.app.SystemApplication, com.miui.misound, com.miui.msa.global, com.miui.qr, com, com.xiaomi.midrop, com.xiaomi.xmsf, Contacts, Google Contacts, CQR, Data Restore Tool, Device Health Service, Digital Wellbeing, Galerie, Galerie-Editor, Gboard oder Schlichte Tastatur (Simple Keyboard), Google-Apps, Hidden Settings for MIUI, secret settings, K-9-Mail, Karta GPS, Kompass, Kontakte, Meta App Installer, Meta Services, Mi Browser, Mi Dokumente Viewer, Mi GetApps, Mi Home, Mi Mover, Mi Music (Version 8.0.01.090420i), Mi Video (Version 2023113002), Mi Account, Mi Credit, Mi Remote, MiTalk Messenger, Mi Scanner, MIUI 13 Updater, MIUI Roms, MIUI Custom Rom, MIUI Compass, MIUI Feedback, Ohrhörer, Open Keychain, Password Store, Peel Mi Remote, Permission Manager, Permission controller, PlayAutoinstalls, Share Mi, MI/Xiaomi Rekorder, System UI (Installation des Update war nicht möglich), Systembenutzeroberfläche-Plugin, Themes for MIUI, Tile Fun (Game), Tool zur Datenwiederherstellung, weather-by-xiaomi, Xiaomi Gallery, Xiaomi Package Installer, Xiaomi service framework, Xiaomi Sim Aktivierungdienst, Xiaomi System Apps Updater, Xiaomi Konto, MIUI SDK bzw. MIUI SYSTEM, (Versionen nach Dezember 2022 bewirken Fehlermeldungen von Xiaomi Konto und Xiaomi Cloud!), Benachrichtigungen (nicht updaten, da neue Version Fehlermeldungen bewirkt), App Vault, Mi Connect, Cast, einzelne Google-Apk (falls aktiviert), Benachrichtigungen (MIUI notifications bzw. com.miui.notification), All Document Reader, cn.wps.xiaomi.abroad.lite, com.idea.backup.smscontacts, com.miui.globalFilexplorer, MIUI MSA, ShareMe, Weather by Xiaomi, ... What you can update for Xiaomi Poco m5 (downgrade again, if the update doesn´t work error-free): ApkCombo-installer, com.miui.global.packageinstaller, MIUI-Upgrade von MIUI 13.08 auf MIUI 13.10 oder MIUI 14, Poco-Launcher (da neuere Version nicht ganz fehlerfrei liefen, empfehlen wir com.mi.android.globallauncher Version 4.39.7.6274-11071434-43), Xiamomi Sicherheit/Security (com.miui.securitycenter_7.7.3-230431.1.3-40, manch höhere Version arbeiten nicht fehlerfrei), MIUI Sicherheitskomponenten, Xiaomi Sicherheit-/Security-Kernkomponente, Systemdienst-Plugin, Xiaomi Systemui (miui.systemui.plugin), Xiaomi Systemui-Plugin, Xiaomi Settings (Einstellungen, com.xiaomi.misettings, Version 2.9.9.67), UniPlay Service, MIUI Hidden Settings Activity, Orbot, Firefox und/oder Firefox Nightly, Webview ( Apps wie Private Location laufen dann nicht mehr korrekt, ggfls. default Version belassen), k-9-mail, Xiaomi Themes, Gallery (com.miui.gallery), Gallerie, Gallerie-Editor, Camera (com.android.camera) bzw. Opencamera (net.sourcforge.opencamera), Xiaomi notes (Notizbuch), Earphone, Mi Video, Mi Musik und das Wallpaper-Karussel ( Mi Wallpaper Carousel) bzw. Hintergundbild-Karussell, Themes for MIUI, MIUI Daily Wallpaper, Texteditor, Aldi Talk, Backup (com.miui.backup), Fehlermeldung (com.miui.bugreport), All Backup & Restore, Analytics, Android Auto, Android für Barrierefreiheit, Android SDK bzx. System SDK (Update funktionierte nicht), Antenna Pod, App Vault (info-assisstent), Google Assistent, Assistent, Bereinigung, Bildschirmaufnahme, Calculator (com.miui.calculator), Carrier Services, Cit, CIT-com.miui.cit, cn.wps.xiaomi.abroad.lite, com.android.camera, Clock bzw. com.android.deskclock (am besten: Huawei-Clock), com.android.sharedstoragebackup, com.android.shell, com.android.soundrecorder, com.android.thememanager, com.google.android.projection.gearhead, com.huaqin.sarcontroller, com.mi.android.globalfilexplorer, com.miui.backup, com.miui.backreport, com.miui.extraphoto, Xiaomi Gallery, com.miui.gallery, com.miui.global.packageinstaller, com.miui.internal.app.SystemApplication, com.miui.misound, com.miui.msa.global, com.miui.qr, com, com.xiaomi.midrop, com.xiaomi.xmsf, Contacts, Google Contacts, CQR, Data Restore Tool, Device Health Service, Digital Wellbeing, Galerie, Galerie-Editor, Gboard oder Schlichte Tastatur (Simple Keyboard), Google-Apps, Hidden Settings for MIUI, secret settings, K-9-Mail, Karta GPS, Kompass, Kontakte, Meta App Installer, Meta Services, Mi Browser, Mi Dokumente Viewer, Mi GetApps, Mi Home, Mi Mover, Mi Music (Version 8.0.01.090420i), Mi Video (Version 2023113002), Mi Account, Mi Credit, Mi Remote, MiTalk Messenger, Mi Scanner, MIUI 13 Updater, MIUI Roms, MIUI Custom Rom, MIUI Compass, MIUI Feedback, Ohrhörer, Open Keychain, Password Store, Peel Mi Remote, Permission Manager, Permission controller, PlayAutoinstalls, Share Mi, MI/Xiaomi Rekorder, System UI (Installation des Update war nicht möglich), Systembenutzeroberfläche-Plugin, Themes for MIUI, Tile Fun (Game), Tool zur Datenwiederherstellung, weather-by-xiaomi, Xiaomi Gallery, Xiaomi Package Installer, Xiaomi service framework, Xiaomi Sim Aktivierungdienst, Xiaomi System Apps Updater, Xiaomi Konto, MIUI SDK bzw. MIUI SYSTEM, (Versionen nach Dezember 2022 bewirken Fehlermeldungen von Xiaomi Konto und Xiaomi Cloud!), Benachrichtigungen (nicht updaten, da neue Version Fehlermeldungen bewirkt), App Vault, Mi Connect, Cast, einzelne Google-Apk (falls aktiviert), Benachrichtigungen (MIUI notifications bzw. com.miui.notification), All Document Reader, cn.wps.xiaomi.abroad.lite, com.idea.backup.smscontacts, com.miui.globalFilexplorer, MIUI MSA, ShareMe, Weather by Xiaomi, ...
 Online-Excursion: Gooken recommends the usage of smartphones through WLAN (router and hotspots), which is for free, offline-maps with offlined navigation, the free phone with messangers like WhatsApp and/or Signal and unlimited data volumes bypassing the ISP (provider) (free downloads) enpossibled by Orbot (anonymizing VPN-Tor-network with the integrated highly effecitve App-firewall, blocking all Apps, even system- and root-apps). One more advantage: no advertisment is shown in deactivated apps anymore consisting of advertisment. Online-Excursion: Gooken recommends the usage of smartphones through WLAN (router and hotspots), which is for free, offline-maps with offlined navigation, the free phone with messangers like WhatsApp and/or Signal and unlimited data volumes bypassing the ISP (provider) (free downloads) enpossibled by Orbot (anonymizing VPN-Tor-network with the integrated highly effecitve App-firewall, blocking all Apps, even system- and root-apps). One more advantage: no advertisment is shown in deactivated apps anymore consisting of advertisment.
In order to prevent the provider from suddenly locking the mobile phone number, a SMS should be sent out mobile at least one time the year.
 Attention: There are two named Simple Keyboards! Keystrokes and/or other data should not be transferred to server as possible, so choose Simple Keyboards (821 KB Apk) by Raimondas Rimkus and not Simple Keyboards (34 MB) from Simple Mobile Tools !, gooken, 07.30.2025 Attention: There are two named Simple Keyboards! Keystrokes and/or other data should not be transferred to server as possible, so choose Simple Keyboards (821 KB Apk) by Raimondas Rimkus and not Simple Keyboards (34 MB) from Simple Mobile Tools !, gooken, 07.30.2025
Risky: Rooting and Jailbreaking of mobile devices, trojaner-info.de, 03.23.2025
Zimperium warnt vor den Risiken durch Rooting und Jailbreaking von Mobilgeräten. Gerootete Android-Geräte sind 3,5 Mal häufiger von Malware betroffen, und Sicherheitsvorfälle steigen um das 250-fache. Cyberkriminelle nutzen diese Techniken als Angriffsvektoren, um Unternehmensnetzwerke zu infiltrieren und Daten zu stehlen. Trotz verbesserter Sicherheitsmaßnahmen entwickeln sich Rooting-Tools wie Magisk und Checkra1n ständig weiter und umgehen herkömmliche Schutzmechanismen. Zimperium empfiehlt Unternehmen, mobile Sicherheit priorisiert zu behandeln und KI-gestützte Echtzeit-Erkennungstechnologien einzusetzen, um Bedrohungen frühzeitig zu identifizieren und abzuwehren. Weitere Informationen sind im Blog von Zimperium verfügbar.
Links: https://www.zimperium.com/blog/catch-me-if-you-can-rooting-tools-vs-the-mobile-security-industry/
https://www.trojaner-info.de/mobile-security/aktuell/jailbreaking-von-mobilgeraeten.html
Lesermeinung Gooken
Sicher (... naja, wenn Sie es sagen...)?
Man sollte nach den Operationen unter Root (Deinstallation von Bloatware, Konfigurieren von Root-Apps wie der iptables-basierten AFW+-Firewall, Rechte-Entzug für bestimmte Apps usw.) schnell wieder in den Benutzer-Modus wechseln.
Sichere (und bessere) Alternative: Advanced Device Bridge (adb und fastboot) aus platform-tools bzw. android-tools (linux) zum Rooten des Smartphones mit dem Linux-Computer.
 Howto deinstall bloatware, netzwelt.de, 11.29.2023 Howto deinstall bloatware, netzwelt.de, 11.29.2023
1
Tippt in den "Entwickleroptionen" auf "USB-Standardkonfiguration".
2
Wählt "Übertragen von Dateien" aus und verbindet euer Android-Smartphone per USB-Kabel mit eurem PC.
Führt den Befehl "adb devices" aus, um den ADB-Dienst zu starten und anschließend "adb shell" um die Befehlseingabezeile zu laden.
06 CMD - adb shell - list packages 06 CMD - adb shell - list packages
3
Öffnet mit der Windows 10-Suche die Eingabeaufforderung "CMD" als Administrator.
4
Führt den Befehl "adb devices" aus, um den ADB-Dienst zu starten und anschließend "adb shell" um die Befehlseingabezeile zu laden.
5
Gebt den folgenden Befehl ein, um die Paketnamen der Bloatware-Apps anzeigen zu lassen. Dazu gebt ihr am Ende ein passendes Stichwort für den Hersteller (z. B. Samsung) oder gegebenenfalls für euren Netzbetreiber (z.B. Telekom) an: "pm list packages | grep Stichwort". (z. B. "pm list packages | grep Samsung".
07 CMD - adb shell - list packages 07 CMD - adb shell - list packages
6
Notiert euch den Paketnamen der Bloatware-App(s), welche ihr deinstallieren wollt.
08 Android - Anwendungsinspektor 08 Android - Anwendungsinspektor
7
Falls ihr nicht fündig werdet, könnt ihr euch die Paketnamen mit der Android-App "Anwendungsinspektor" zusammen mit dem App-Namen und Symbol anzeigen lassen. Diese zeigt euch nach dem Start und einem kurzen Scan eine entsprechende Liste an.
09 CMD - adb shell - pm uninstall 09 CMD - adb shell - pm uninstall
8
Mit dem Befehl "pm uninstall -k --user 0", gefolgt von einem Leerzeichen und dem Paketnamen, könnt ihr die jeweilige Bloatware-App entfernen.
10 CMD - adb shell - pm install-existing 10 CMD - adb shell - pm install-existing
9
Um diese bei Bedarf wiederherzustellen, nutzt ihr den Befehl "pm install-existing", gefolgt von einem Leerzeichen und dem Paketnamen.
Zum Installieren von Android-Apps könnt ihr neben Google Play und anderen diversen App-Stores auch APK-Dateien nutzen, wenn ihr die "Installation aus unbekannten Quellen" aktiviert.
https://www.netzwelt.de/anleitung/193588-android-so-entfernt-bloatware-ohne-root-zugriff.html
 Inform yourself about apps before changing its rights Inform yourself about apps before changing its rights
Android 12: settings -> data protecction -> special rights -> file access: is it really allowed to make any changes?
Before making any changes, inform yourself. We do this for com.android.sharedstoragebackup for example:
com.android.sharedstoragebackup: Explained, androidsrc.net, 12.09.2023
by proxyadmin
Have you ever come across the term ‘com.android.sharedstoragebackup‘ while using your Android device and wondered what it meant? This post is for you. In this blog, we will talk about what exactly com.android.sharedstoragebackup is, its use, and if it´s safe to use. We will also explain how shared storage backup works and why file sharing is crucial.
...
Here are a few ways to disable com.android.sharedstoragebackup:
Go to Settings > Apps & notifications > See all apps. Find the app called "Shared Storage Backup" and tap on it. Tap "Disable" to disable the app. This will stop the app from running or updating.
Use a third-party app like Package Disabler Pro to disable the Shared storage backup app. These apps can disable system apps without root access.
https://androidsrc.net/com-android-sharedstoragebackup/
 ... and draw the conclusion, that the access upon all files can be forbid for all listed Apks including System-UI and storage-manager! ... and draw the conclusion, that the access upon all files can be forbid for all listed Apks including System-UI and storage-manager!
You can also trust MIUI-Hidden-Setttings, where a lot of Apks can get deactivated Apk by Apk, wherever deactivation is suggested.
But the same is not allowed for all apps listed in "Picture within Picture"!
More complex alternative to Orbot with Purple I2P, but without VPN-App-Firewall from apkpure.com: Full Tor VPN: Private and Safe
We´d like to repeat:
 Tor-browser for Android-Smartphone (ARM) including Firefox-68.12.0 can be downloaded not from Google Play Store, but from torproject.org, while above listed firefox-extensions can also be used for it. They get installed for the Tor-browser onto the Smartphone from their well-known location (addons.mozilla.org) ! Tor-browser for Android-Smartphone (ARM) including Firefox-68.12.0 can be downloaded not from Google Play Store, but from torproject.org, while above listed firefox-extensions can also be used for it. They get installed for the Tor-browser onto the Smartphone from their well-known location (addons.mozilla.org) !
 Smartphone, Xiaomi Poco m5, use of the SD-card: MIUI formats the SD-card with exfat, a successor from Microsoft of vfat. Smartphone, Xiaomi Poco m5, use of the SD-card: MIUI formats the SD-card with exfat, a successor from Microsoft of vfat.
In order to get an SD-card mounted using a SD-card reader, following packages needs to get installed for "Universal Linux": exfat-utils (el8), exfatprogs (el8), fuse-common (el8) and fuse-exfat (el8). Now the mount is done by the command
mount.fuse-exfat partition-of-the-sd-card mountpoint, for example "mount.fuse-exfat /dev/sdb1 /mnt4", same for Debian using "mount.exfat-fuse" out of exfat-fuse (deb).
Generally install as much file systems as you can for "Universal-Linux" (package e2fsprogs (el8) for ext4, libbtrfs0, libbtrfs-util1 for btrfs, reiserfsprogs (el8) for Reiserfs, reiser4progs (el8, Reiserfs especially for flash-media), squashfs (el8), vfat (old Windows-filesystem), MacOSX, ....). These packages can be downloaded from rpmfind.net or its mirror fr2.rpmfind.net for example.
 1) Data backup and restore: The best you can do is to use the system-internal data securing out of directory named tools. This of course is possible on our introduced Huawei Y360. All will be really backuped on SD-card, all encrypted, and from this (SD-card), you can also save it all onto other media like harddrive or SSD ! 1) Data backup and restore: The best you can do is to use the system-internal data securing out of directory named tools. This of course is possible on our introduced Huawei Y360. All will be really backuped on SD-card, all encrypted, and from this (SD-card), you can also save it all onto other media like harddrive or SSD !
 2) Process management: same as 1). Start it by system-settings -> apps -> active . This will prevent from bad working and keeps from ads and In-App-Buys etc.. 2) Process management: same as 1). Start it by system-settings -> apps -> active . This will prevent from bad working and keeps from ads and In-App-Buys etc..
 3) Data rubbish deletion (cleaner): There is a system-interal one working fine and therefore recommended. 3) Data rubbish deletion (cleaner): There is a system-interal one working fine and therefore recommended.
 4) Firewall (although we believe, that Linfw3 is the really secure one): iptables based root-firewall AFWall+ or Netguard. Last one, suggested Non-Root-VPN-Firewall, warns itself against data eavesdropped on the belonging VPN-Server. Prefer firewall NetGurad (Non-Root-AppBlocker, PlayStore, Android 4 and higher, secure password-protected block of single apps resp. all Apps except MMS/SMS, settings, Huawei-browser ) instead, recommended by 4) Firewall (although we believe, that Linfw3 is the really secure one): iptables based root-firewall AFWall+ or Netguard. Last one, suggested Non-Root-VPN-Firewall, warns itself against data eavesdropped on the belonging VPN-Server. Prefer firewall NetGurad (Non-Root-AppBlocker, PlayStore, Android 4 and higher, secure password-protected block of single apps resp. all Apps except MMS/SMS, settings, Huawei-browser ) instead, recommended by
https://www.heise.de/tipps-tricks/Firewall-fuer-Android-Datenstroeme-kontrollieren-4171351.html
Easy configuration (NetGuard from PlayStore, version 1.0.4 from year 2014): At first set the password protection. Then block all apps in the password protected way except system-settings, Signal and other messengers like (Facebook) Lite and WhatsApp. Now you have to allow only those apps, you are going to communicate in the net during a certain time. Block them again after the communication.
.
After this, forbid all (!) Apps, except App ALDITALK/YOUR Smartphone-PROVIDER, App "Connection Stabil(izer) Booster", e-mail, system settings (system control), Messenger Lite, Signal, Tagesschau App and the Tor-browser.
and allow single Apps only, during an App is needed, that builds up net connections. Block each App again after its use.
Use App "Apps Autostart" to start NetGuard 1.0.4 each boot of Android. This start needs a few seconds, so Apps might already build up connections and communicate. Deaactivate such Apps or additionally use the following firewall:
You can, but you mustn´t install the App "Non-Root-firewall with VPN" additionally too. This firewall starts quit immediatley after each boot. With it, you can also block single domain resp. IP. To be most careful, both firewalls can also block eachother now... But as its own monitor (and NetworkMonitor by TU Darmstadt) monitors, there is a permanent quit hard traffic (data transfer ,information exchange) going on with yahoo and further on...!
Alternatively use a Linux-iptables based root-firewall like AFWall+. For installation and configuration you have to get into the root-mode of your smartphone, what might be not such easy. In settings, at first enable USB-debugging and OEM-unlock-bootloader for it. Enable the developer options, in order to activate the USB-debugging mode on Poco m5 by clicking five times upon the icon with the OS-number (poco: MIUI-version-number) on the right side within option "about phone". Also tell your manufacturer (poco: Xiaomi) about this, by opening the user-account of the manufacturer (here Xiaomi) within settings. Then download and install the mi-unlock software on your PC.
The more than sparse suited recovery of your smartphone should get flashed into a more comfortable like TWRP. This Recovery-Custom-ROM enablesbackups on your computer, root-mode and the installation of further custom ROMs like LineageOS.
But at first, you can try to get into the root-mode with one-click only by Apps like KingRoot apk.
If KingRoot and Kingoroot fail, install android-tools for your Linux-PC. After this, connect the smartphone with the Linux-PC by USB cable. Power the smartphone off, press both keys for volume and power at one to boot into the menu for enabling USB-connection, then access the smarphone with adb and/or fastboot out of package android-tools (rpm) from your Linux-PC.
List possible adb commands by just typing adb into the terminal. adb itself should run in root mode on your Linux PC for it.
If all this fails, lookout for other sources out of the internet descibing howto!
After it manages to get your Smartphone into the root-mode this ways, use Apps like Supersu, in order to manage the Apps and Autostart of Apps with root-rights running in root-mode.
Alternatively check the second firewall named NoRootFirewall 1.3 out more or less with Apps like NetMonitor from Fauenhofer Institut. The traffic can get eavesdropped serversided whenever you use a VPN, but in order to get encryption, for hotspots, VPN of this firewall is a real must!
Do you also see more than needed connections build up by NoRoot Firewall, even for port 80? Block them in the section global filter on port 80 and 81, maybe not also them, but generally all connections upon these and any other ports you like. So at least it is right to keep NetGuard. If both firewalls are right or if it is better to keep NetGuard only, depends on your analyses upon the checkouts made by NetMonitor of the Frauenhofer Institut.
Additionally: Firewall NoUSSD: "Many Android phones have a security flaw, where they will automatically dial any telephone number touched on a webpage. USSD codes are numbers, that can provide system info such as the IMEI number and possibly even do a factory reset. NoUSSD will intercept all USSD codes and give you the choice not to dial them. Regular phone numbers will be sent automatically to your favorite dialer."
https://search.f-droid.org?q=noussd&lang=en
 In this case, only use Orbot (without any additional firewall anymore). Configure VPN in Orbot, activate it as the only one, configure VPN for Orbot in Android-system-settings by activating VPN permanently and for all network-connections as a must too. After this, start Orbot, use its option for VPN, here together with all the apps you want to allow or block by setting hooks or not ) - now it works, perfect! Congratulation! In this case, only use Orbot (without any additional firewall anymore). Configure VPN in Orbot, activate it as the only one, configure VPN for Orbot in Android-system-settings by activating VPN permanently and for all network-connections as a must too. After this, start Orbot, use its option for VPN, here together with all the apps you want to allow or block by setting hooks or not ) - now it works, perfect! Congratulation!
 Set option "strikt firewall" in Orbot, in order to use the firewall DataGuard too. Set option "strikt firewall" in Orbot, in order to use the firewall DataGuard too.
 Firefox with extension FoxyProcy: Now Orbot (Tor-network) can be used for localhost (127.0.0.1) on port 9050 upon protocol SOCKS5. Orbot also offers anonymization for all Apps through their use of its own local VPN too. Firefox with extension FoxyProcy: Now Orbot (Tor-network) can be used for localhost (127.0.0.1) on port 9050 upon protocol SOCKS5. Orbot also offers anonymization for all Apps through their use of its own local VPN too.
 Do the most important for your smartphone and set the Advertisement-ID (your personal ad-identifiying number) forever to the anonymizing, because of unified value zero resp. 0000000....: tap Hidden Settings apk (2, package name: com.netvor.hiddensetting) -> hidden ->, Ad settings ->, and either set the hook for the deactivation of personalized advertisement, so that the ad-ID will be set to the unified value or just tap (touch) on the button to get a randomized new one. Do the most important for your smartphone and set the Advertisement-ID (your personal ad-identifiying number) forever to the anonymizing, because of unified value zero resp. 0000000....: tap Hidden Settings apk (2, package name: com.netvor.hiddensetting) -> hidden ->, Ad settings ->, and either set the hook for the deactivation of personalized advertisement, so that the ad-ID will be set to the unified value or just tap (touch) on the button to get a randomized new one.
 In the following, with Poco m5, just be careful with APK contact storage, system service plugin, the MI-settings (apk) and before making updates/upgrades! In the following, with Poco m5, just be careful with APK contact storage, system service plugin, the MI-settings (apk) and before making updates/upgrades!
Contact storage: if it gets deactivated (by Hidden Settings (1)), contacts seem too vanish out of App Kontakte/contacts. You can get all the once entered contacts back, if this apk gets activated again.
System service plugin: This apk should always have the right to modify system settings as much as to show pictures within pictures.
Mi-setting (system setting apk): should have always the right to modify the system settings too. Otherwise the Smartphone might not work anymore!
 Notice, that not each Apk-version is suitable for updates and upgrades. The right version required should be found out before any download and installation! Notice, that not each Apk-version is suitable for updates and upgrades. The right version required should be found out before any download and installation!
 Xiaomi Bloatware List (Safe to Remove) on MIUMI 12/11/10 - Bloatware-Apps-Liste Xiaomi Bloatware List (Safe to Remove) on MIUMI 12/11/10 - Bloatware-Apps-Liste
Poco m5 enthält unter den System-Apps vielerlei zu deinstalliernde Bloatware: Bloatware von Google, MIUI und Xiaomi (Bloatware-Apps) usw.:
F
 Find the list of safe to remove Xiaomi and MIUI bloatware. Learn how to uninstall system apps on MIUI 12, 11 &10 via Xiaomi-ADB/fastboot-tools. Find the list of safe to remove Xiaomi and MIUI bloatware. Learn how to uninstall system apps on MIUI 12, 11 &10 via Xiaomi-ADB/fastboot-tools.
https://technastic.com/xiami-bloatware-list-miui/time - that does not work?
 Use ADB and Fastboot Use ADB and Fastboot
Even Apps like thCommands on Android without root of using a computer
e so-called secure messenger signal do contact GooglePlayStore, so that they do not get blocked by NetGuard! Notice, that data, even if NetGuard is used, still gets exchanged through GooglePlayStore, if last one isn´t blocked by Netguard too. The best thing to do is to deinstall GooglePlayStore and all GooglePlayServices. Install them again for updating apps only!
Fastboot Termux Git you can install and use ADB and Fastboot commands on Android devices via Termux without root or using a computer, tecnastic.com, 07.11.2020
 5) Total Commander: We´d like to suggest the already integrated one from Huawei instead by touching the icon named files. 5) Total Commander: We´d like to suggest the already integrated one from Huawei instead by touching the icon named files.
 6) Routing and navigation: comfortable Nunav only fullfills the demands. 6) Routing and navigation: comfortable Nunav only fullfills the demands.
 7) Anti-Malware: Malwarebytes is most deep-scanning (although there is nothing wrong with Huawei Y360-U61 and introduced apps except Facebook) 7) Anti-Malware: Malwarebytes is most deep-scanning (although there is nothing wrong with Huawei Y360-U61 and introduced apps except Facebook)
 8) Wifi Blocker: netcut and ARP-Guard for Wifi security: ARP protection (access points), AP-protection (access points) with BSSID-check, DHCP protection, all with automatic Wifi-cutoff on alarm, ...what provides most important security features! 8) Wifi Blocker: netcut and ARP-Guard for Wifi security: ARP protection (access points), AP-protection (access points) with BSSID-check, DHCP protection, all with automatic Wifi-cutoff on alarm, ...what provides most important security features!
 9) Deinstallation and deactivation of the following Apps (past their updates) are recommended: Google has interfered during the use of our banking-App: a Google-process was shown! 9) Deinstallation and deactivation of the following Apps (past their updates) are recommended: Google has interfered during the use of our banking-App: a Google-process was shown!
Generelly, in our eyes, in order to reach the 1000% IT-security for your SmartPhone we promised and by freeing a lot of inernal memory and memory on SD-card, you might want to deinstall GooglePlayStore, GoogleApps and bankingApps, also try GooglePlayServices,
and deactivate also the following Google- and Andorid-Apps through Huawei-system-control / Huawei-system-settings :
system-settings -> Apps -> All:
Market Feedback Agent, Google Backup Transport, Google Partner Setup, com.android.providers.partners, ConfigUpdater, Google Account Manager, Search Engine Provider, Google-Dienste-Framework, Google Kontakte synchronisieren, com.android.wallpaper.holoscope, Google One Time Init, Druck-Spooler, Operator Plugin, WL-version_query, Setup-Assistent, Basic Daydreams, Chrome, Drive, Google Fotos, Gmail, Google Play-Store, Google-Play-Dienste, OMACP, Wt_version_query, Google Play Books, Google Play Games, Google Play Kiosk, Google Play Musik, Google Play Movies, Google-Suche, Magic Smoke Wallpapers, Music Visualization Walllpaper, Phase Beam, Tips for the start-screen, &Overview (around 16 MB), Hangouts, Fotos and Youtube.
 Rooting the smartphone like Xiaomi Poco m5 fails and ADB does not function too? Try Apk Security by tapping on its settings in the right upper corner, then onto "increase speed", in order to lock system apps and normal apps during the boot procedure of Android/MIUI, Gooken, die Red., 03.12.2024 Rooting the smartphone like Xiaomi Poco m5 fails and ADB does not function too? Try Apk Security by tapping on its settings in the right upper corner, then onto "increase speed", in order to lock system apps and normal apps during the boot procedure of Android/MIUI, Gooken, die Red., 03.12.2024
System-Apps und weitere Apps lassen sich beim Booten des Xiaomi Poco m5 sperren! Hierfür tappe man auf die MIUI-Sicherheits-App (com.miui.securityadd, bei uns Version 7.7.3), dann oben rechts auf Einstellungen. Nun die Geschwindigkeits-Optimierung auswählen, anschließend aus der Liste der Apps heraus die Apps einfach per Tap auf die Schiebeschalter sperren. Gesperrt haben wir den weder deinstallierbaren noch deaktivierbaren Info-Assistant, Facebook Lite, die beiden Messanger WhatsApp und Signal, MIUI Video, MIUI Musik usw. Eine einschränkende negative Auswirkung konnten wir damit bislang nicht feststellen, während das Smartphone seine Geschwindigkeit tatsächlich auf tapping-mausklick-schnell erhöht.
 Apps-Configuration in the following: all user-Apps including all dual Apps, system- and Root-Apps (the whole amount of installed Apps) Apps-Configuration in the following: all user-Apps including all dual Apps, system- and Root-Apps (the whole amount of installed Apps)
 You can make more important security settings with app "hidden settings for MIUI" like activation/deactivation of Apps too. You can make more important security settings with app "hidden settings for MIUI" like activation/deactivation of Apps too.
 Once again malware-Apps for Android-handies have been found: Apps, that should better be deinstalled, CHIP, 29.02.2020 Once again malware-Apps for Android-handies have been found: Apps, that should better be deinstalled, CHIP, 29.02.2020
Im Google Play Store sind einige schädliche Android-Apps identifiziert worden, die Ihr Smartphone in Gefahr bringen können. Wir zeigen Ihnen im Text, welche Anwendung unbedingt von Ihrem Android-Smartphone fliegen sollten und im Video, welche Vorsichtsmaßnahmen kostenlos zur Verfügung stehen.
https://www.chip.de/news/Erneut-schaedliche-Apps-fuer-Android-Handys-entdeckt-Welche-Anwendungen-Sie-besser-deinstallieren-sollten_182249578.html
 Actualization of Smpartphone-Apps (for Huawei Y360-U61): Activate following Apps again: Google Play Store (resp. other PlayStores), Google Play Services, Google-Services-Framework, Google Account Manager, Google contacts synchronisation and Gmail. After Apps got actualized resp. updated listed Apps can be deactivated again. Actualization of Smpartphone-Apps (for Huawei Y360-U61): Activate following Apps again: Google Play Store (resp. other PlayStores), Google Play Services, Google-Services-Framework, Google Account Manager, Google contacts synchronisation and Gmail. After Apps got actualized resp. updated listed Apps can be deactivated again.
So far for Huawei Y360-U61 Andorid Smartphone.
MIUI (Xiaomi Poco m5, occuring warnings can be ignored in the following as all essential functions will be kept safe by MIUI by blending or graying options out:
 Access manager activation: settings -> further more settings -> handling service helps -> downloaded Apps -> access manager : "ON" Access manager activation: settings -> further more settings -> handling service helps -> downloaded Apps -> access manager : "ON"
 Access menu activation: This allows practical links enabling a steering of the device -> further more settings -> handling service helps -> acess menu -> activate the link for it . Access menu activation: This allows practical links enabling a steering of the device -> further more settings -> handling service helps -> acess menu -> activate the link for it .
 Handling help service button: settings -> further more settings -> Handling help -> activate the button for handling help. Handling help service button: settings -> further more settings -> Handling help -> activate the button for handling help.
 Apk Berechtigungsmanager / permissions manager (apkpure.com). Set different rights and access rights for each App. Apk Berechtigungsmanager / permissions manager (apkpure.com). Set different rights and access rights for each App.
 Apk "APK Permission Remover" (apkpure.com). Set different righs and access rights for each App. Apk "APK Permission Remover" (apkpure.com). Set different righs and access rights for each App.
This app deals with the activation and deactivation of (in next listing in more details described) apk- / app - attributes like:
Read out sensor data with high frequency
Use fingerprint hardware
Use biometric software
Android.permission-group.UNDEFINED
Send or request SMS
Read SMS or MMS
Directly call phone numbers
Request phone status and identity
Read contacts
Change contacts
Read calender appointment and details
Add or change calender appointments without the user getting informed and send E-mail to guests
Empty the phone caller list
Overwork the phone caller list
Only access the exact location during the executiion in the foreground
Only access the less exact location during the execution in fhe foreground
Receive SMS
Receive text messages (WAP)
Receive MMS
Read Cell-Broadcast-messages
Request locations out of the media collection
Redirect outgoing phone calls
Make or receive SIP-calls
Takeover calls
Recognize body activities
Access body sensors like pulse meters
Make and add mailbox messages
Access location in the background
Send contents to bluetooth-devices in the near area
Connect with interlinked bluetooth-devices
Find bluetooth-devices in the near area, in order to interlink
Read contents of accessible memory
Change or delete contents of the accessible memory
Search the devices for accounts
Create images and make videos on the device
Make images and record videos in the background
Permit an app to access a service upon system cameras, in order to make photos and rrecord videos
Allow the App or service callbacks, if a camera gets opened or closed
Record audio
Record audio in the background
Measure the relative distance between ultra high frequenced devices in the near area
Access all networks
Steer near field communication
Send information to the elected NFC-Payment-service
Allow receiving WLAN-Multicasting
Allow infrared communication
Change audio-settings
Request the complexity of the display lock
Request active Apps
Close other Apps
Execute in the background
Use data in the background
Resize background images
Adapt synchronization settings
Read synchronization settings
Activate or deactivate synchronization
Read synchronization statistics
Set the alarm-clock
Create links
Delete links
Determine the memory capacity of the app
Change network connectivity
Request the deletion of packages
Ask, if Akku-performance parameter can get ignored
Access during "do not disturb"
Read installation sessions
Display messages on the locked device as fullscreen-activities
Access additional service provider commands for the location
Request network connections
Request WLAN-connections
Interlink bluetooth-devices
Enable Bluetooth-settings
Blend in and blend out the status line
Deactive the display lock
Request the foreground service
Reorder active apps
Change system settings
Send permanent broadcast
Close other apps
Administer account and device owner
Steer the vibration alarm
Enables an app to access the vibration status
Build up and close WLAN-connections
Adjust the time zone
Deactivate hibernation
Start during the system boot
Set the background
Change known SIM accounts to ContactsProvider
Bind services to mobile phone provider
App can appear over other apps
Request all packages
Download files without notifications
Alle Pakete abfragen
Dateien ohne Benachrichtigung herunterladen
Internetdaten erhalten (ermöglicht Apps, von dem App-Dienst gesendete Cloud-an-Gerät-Nachrichten zu akzeptieren. Bei der Verwendung dieses Dienstes werden Daten übermittelt. Schädliche Apps können zu übermäßig Datenverbrauch führen)
Berechtigung für Werbe-ID
Play Install Referrer API (ermöglicht, die Verweisinformation zur Installation abzurufen)
Access all networks
Google-Play-payment service
Google-Play-licence-check
...
 Graphics / graphic card driver Graphics / graphic card driver
Xiaomi Poco: In settings, search for "graphic driver" (found in developer options, section debug): Then switch from "standard" to "internal graphic card driver" each app. This increases your graphics, especially turbo-like for games.
 Boost up the speed of the phone Boost up the speed of the phone
Xiaomi Poco: In the security app, settings, lock many or all apps, that do not belong to the system apps. That has nothing to do with unklocking by passwords, but refers to the prevention of the automized start during the system boot and the time after it.
 Location: Deactivate all location requests in setting. This is possible, if KartaGPS (apk) for offline landcard mapping and navigation got installed. This App can download and install maps from all over the world for offline-use. Location: Deactivate all location requests in setting. This is possible, if KartaGPS (apk) for offline landcard mapping and navigation got installed. This App can download and install maps from all over the world for offline-use.
 Deactivate advertisments (how this is done, is explained in the internet by the manfacturer Xiaomi or soon in the following) Deactivate advertisments (how this is done, is explained in the internet by the manfacturer Xiaomi or soon in the following)
 Draw back all authorizations ( server-connections ): settings ->, password&security ->, authorizations Draw back all authorizations ( server-connections ): settings ->, password&security ->, authorizations
 Use the internal MIUI-Firewall in settings ->, connections &s; share -> LAN, WLAN and background, by setting belonging three hooks for each listed App Use the internal MIUI-Firewall in settings ->, connections &s; share -> LAN, WLAN and background, by setting belonging three hooks for each listed App
 MIUI includes, even if meant the other way, four (!) different intern firewalls adding each other, in additon you can use firewalls not from MIUI especially like Orbot and AFWAll+ (that can get started in the Root Mode only!): MIUI includes, even if meant the other way, four (!) different intern firewalls adding each other, in additon you can use firewalls not from MIUI especially like Orbot and AFWAll+ (that can get started in the Root Mode only!):
1. MIUI-firewall: settings -> connections&share"
2. "MIUI-firewall": settings -> Apps and Data Usage: mobil, WLAN or none of it
Do not forget the system apps, almost beginnging with com.android.* and com.miui.* and apps like shell (apk), therefore especially those reaching for the location, camera and microphone and so on. Find such apps out with MIUI hidden settings by querying its search function.
3. "MIUI-firewall": like 2., but through settings for the power saving for each App: like unlimited, MIUI-energy-saving mode and other power saving modes up to "forbid (the App in process), in order to save energy sparen"
4. "MIUI-firewall": lock all kind of activity each App: settings -> Apps -> system-App-settings -> Security -> Increase The Speed ->, lock each App by setting a hook
Please notice, that no all Apps are listed during 1. up to 4 ! So you can not block all of them this way.
4. Firewall: Orbot (also consists it, aa high effective firewall. Orbot is a downloadable Apk. Soon, we explain, howto).
5. Firewall: AFWall+ (downloadbare Apk, Linux-iptables-based firewall; a start of this firewall is only possible in the root-mode)
Notice: Each setting in one of the firewall regardelss from the concrete firewall (1.-5.) takes already into effect all over the complete smartphone !
 System-Apps and User-Apps: set different und different kind of access rights or deinstall Apps: settings ->, Apps System-Apps and User-Apps: set different und different kind of access rights or deinstall Apps: settings ->, Apps
 WLAN-Setting: Forbid each App to change the WLAN-connection: settings, search for WLAN or HiddenSettings (2) WLAN-Setting: Forbid each App to change the WLAN-connection: settings, search for WLAN or HiddenSettings (2)
 User data access: forbid each App the access using: HiddenSettings (2) -> Manage Apps User data access: forbid each App the access using: HiddenSettings (2) -> Manage Apps
 Randomize the mac address: settings Randomize the mac address: settings
 Connections: Always prefer WLAN instead of mobil: settings Connections: Always prefer WLAN instead of mobil: settings
 System-Apps and user-Apps: Set different access rights, deactivate or deinstall them, if possible: settings ->, Apps System-Apps and user-Apps: Set different access rights, deactivate or deinstall them, if possible: settings ->, Apps
 Background-connections: Set your own exceptions or deactivate them each App in settings->App -> small menu right croner: background connections Background-connections: Set your own exceptions or deactivate them each App in settings->App -> small menu right croner: background connections
 Special App-access (each App, you have to search for "settings" within settings for it in MIUI 13, then click upon listed "Special App-Access"): usage data, WLAN-access, access upon all files and access for system settings Special App-access (each App, you have to search for "settings" within settings for it in MIUI 13, then click upon listed "Special App-Access"): usage data, WLAN-access, access upon all files and access for system settings
 Manage the autostart of Apps (Orbot and Private Location), lock Apps (this only locks the start after the fingertyped touch upon it): settings -> Apps Manage the autostart of Apps (Orbot and Private Location), lock Apps (this only locks the start after the fingertyped touch upon it): settings -> Apps
 App-Acess rights: can be set following App-categories: settings ->, Apps ->, Rights App-Acess rights: can be set following App-categories: settings ->, Apps ->, Rights
 Apps, including many System-Apps, can get deactivated, by App "MI Hidden Settings" typing upon it ->, Manage App Apps, including many System-Apps, can get deactivated, by App "MI Hidden Settings" typing upon it ->, Manage App
 Deinstall or deactivate in system settings and Hidden Settings (1) as much Apps as possible (this can include quit all Google-Apps), lock unregistered links of single Apps, reduce notifications, restrict access rights, prevent changing of system configurations (settings) and Opening of Apps by other ones, check the functionality of the smartphone and make a backup (backup onto SD-card, Xiaomi-Cloud etc.). Deinstall or deactivate in system settings and Hidden Settings (1) as much Apps as possible (this can include quit all Google-Apps), lock unregistered links of single Apps, reduce notifications, restrict access rights, prevent changing of system configurations (settings) and Opening of Apps by other ones, check the functionality of the smartphone and make a backup (backup onto SD-card, Xiaomi-Cloud etc.).
 There deactivate (in Hidden Settings (1)) the smartphone process tracing (in german: Ablaufverfolgung), if possible. Otherwise search for it in system settings (search for it, in german "Ablaufverfolgung" and choose it by tapping. Withdraw all hooks, deactivate whatever possible and withdraw all hooks within categories too. Now, the smartphone doesn´t get traced anymore. In Hidden Settings (2) reset or withdraw the advertisement-ID, if possible, what isn´ possible, if belonging Google-Apps got deactivated by Hidden Settings (1) before. Block Apps (data transfer) to Android-System (you might find this option in system settings or so) and change the advertisement-ID by Hidden Settings (2) , if possible. Last thing isn´t possible, if certain Gooken-Apps got deactivated by Hidden Settings (1) before. There deactivate (in Hidden Settings (1)) the smartphone process tracing (in german: Ablaufverfolgung), if possible. Otherwise search for it in system settings (search for it, in german "Ablaufverfolgung" and choose it by tapping. Withdraw all hooks, deactivate whatever possible and withdraw all hooks within categories too. Now, the smartphone doesn´t get traced anymore. In Hidden Settings (2) reset or withdraw the advertisement-ID, if possible, what isn´ possible, if belonging Google-Apps got deactivated by Hidden Settings (1) before. Block Apps (data transfer) to Android-System (you might find this option in system settings or so) and change the advertisement-ID by Hidden Settings (2) , if possible. Last thing isn´t possible, if certain Gooken-Apps got deactivated by Hidden Settings (1) before.
 You can exchange MI-Apps (some of them do have system rioot-rights) with other Apps out of the internet (like from apkpure.com and fdroid): MI-SMS, MI-Browser, MI-file-manager with file manager (version 1.4.2.4 from apkpure.com, stand 2023), MI-Notices with Turbo Editor (recommneded by heise.de, 2023), MI-Music (with the "Simple Music Player"), MI-Video, MI-camera ( with more than 100 MB code) with Open Camera ( of just around 4 MB Code ), ... You can exchange MI-Apps (some of them do have system rioot-rights) with other Apps out of the internet (like from apkpure.com and fdroid): MI-SMS, MI-Browser, MI-file-manager with file manager (version 1.4.2.4 from apkpure.com, stand 2023), MI-Notices with Turbo Editor (recommneded by heise.de, 2023), MI-Music (with the "Simple Music Player"), MI-Video, MI-camera ( with more than 100 MB code) with Open Camera ( of just around 4 MB Code ), ...
 Weitere Apps auswechseln: Google Phone mit Telefon, Google SMS mit schlichter SMS, Google Kalender mit schlichter Kalender, Google Kontakt mit schlichte Kontakte, Gmail mit k-9-mail, Google Chrome z.B. mit Firefox, Google Übersetzer mit deepl usw. Weitere Apps auswechseln: Google Phone mit Telefon, Google SMS mit schlichter SMS, Google Kalender mit schlichter Kalender, Google Kontakt mit schlichte Kontakte, Gmail mit k-9-mail, Google Chrome z.B. mit Firefox, Google Übersetzer mit deepl usw.
 Create dual apps (cloned apps each with its own account as like from complete other phones/devices, so get more to know about the many advantages of it, by querying search engines for Dual Apps): Dual-WhatsApp is highly recommended, also think of Dual-Facebook and further on: Hidden Settings (the second one of two such named apps for MIUI)-> Hidden -> Option for election out of a list with plenty of apps. The user accounts within the Dual apps must get reconfigured on belonging portals. You see: Both "hidden settings" apk contribute a lot for more security ! Create dual apps (cloned apps each with its own account as like from complete other phones/devices, so get more to know about the many advantages of it, by querying search engines for Dual Apps): Dual-WhatsApp is highly recommended, also think of Dual-Facebook and further on: Hidden Settings (the second one of two such named apps for MIUI)-> Hidden -> Option for election out of a list with plenty of apps. The user accounts within the Dual apps must get reconfigured on belonging portals. You see: Both "hidden settings" apk contribute a lot for more security !
Do not forget to secure up alls the dual apps through App Permissions resp. Hidden Settings (1) and system settings! For this purpose, such configuring Apps (Permissions and Hidden Settings) have to be made dual too.
( )Hidden Apps and Permission Manager APP )Hidden Apps and Permission Manager APP
sometimes we no longer remember the last installed app and which is the source of appeared problems!
you have tried several antivirus app in which you trust but it does not solve your problem
we can help you fix that! ghost apps detector
Hidden App allows you to find all the installed hidden apps on your device that may have no icon.
these Hidden Apps and Permission Manager can be:
- a micro program that was installed by another application, runs alone and can be responsible for several annoying publicity.
- background apps without user interface.
- background services (without UI)
- some apps that are just installed as an add-on to others.
- Malicious binary system that does not display its icon.
- apps that run silently in background.
- hidden apps in the launcher that is not shown.
- apps that cannot be malicious but haven't known name.
- apps that are not necessarily malicious but haven't their own icons.
- a virus not shown in application list but continue running without your knowledge.
Hidden Apps and Permission Manager on Android can sit just on the screen, but they are disguised in a way that nobody would even guess. There are so-called "ghost apps" that can mask an application just by substituting the original icon. So, we agree that is a good idea to remove those applications that you do not use, even if they are not hidden.
There are hundreds of small programs (apps) from the operating system itself that run your phone.
Generally android ROM's have apps which are not shown in the launcher but you can't consider them hidden since they are present mostly a support to other apps.
Hidden Apps and Permission Manager recommends you remove them to improve the performance of your device, not only to remove spyware or malware that will allow you to reveal, but also to remove applications that you do not use. because a hidden application can transmit your cords to an unknown destination. With great chance that you have hidden apps that can track you Hidden Apps and Permission Manager allow you to discover some Android settings, which some phone providers hide from the user.
Some apps may be considered as an excessive authority and that is why it should not hide its icon.
- Lists installed applications according to their severity (high risk, medium risk, low risk)
- Click on any application and you will get the details of all of its permissions required by it.
- If you want to KEEP the application with a known risk, click on the KEEP button.
- analyze the permissions of the application and classify them according to the degree of danger for your mobile.
https://apkcombo.com/de/hidden-apps-and-permission-manager/com.toolsgen.security.cyber/
Alternative zu Orbot mit VPN (wie Orbot), Purple I2P und dnscrypt (Orbot: tordns), aber im Vergleich zu Orbot ohne VPN-App-Firewall, von apkpure.com: OpenSourceFull Tor VPN: Private and Safe
 Popular private messaging Apps can leak your location. Here´s how to protect yourself, uncut-news.ch, 11.24.2023 Popular private messaging Apps can leak your location. Here´s how to protect yourself, uncut-news.ch, 11.24.2023
Befolgen Sie diese Tipps, um bei der Verwendung von Messaging-Apps die Weitergabe Ihres Standorts und die Erstellung von Profilen anhand Ihrer IP-Adresse zu vermeiden.
Ende-zu-Ende verschlüsselte Messaging-Apps sind fantastische Datenschutz-Tools, die Ihre Kommunikation sichern und vor dem Ausspionieren durch Dritte schützen. Unter bestimmten Umständen können sie jedoch ein potenzielles Datenschutzproblem darstellen, da sie Ihre Internetprotokolladresse (IP) an andere weitergeben.
Dieses Datenschutzproblem ist nicht auf Ende-zu-Ende verschlüsselte Messaging-Anwendungen beschränkt und betrifft viele Anwendungen mit Sprachanruffunktion, aber wenn Sie eine Ende-zu-Ende verschlüsselte Anwendung verwenden, um Ihre Privatsphäre zu maximieren, ist dies etwas, mit dem Sie sich wahrscheinlich befassen möchten.
Das Problem ergibt sich aus der Art und Weise, wie die meisten Messaging-Anwendungen Peer-to-Peer-Verbindungen nutzen, um die Anrufqualität zu verbessern. Leider geht diese verbesserte Anrufqualität über diese direkten Verbindungen mit dem Risiko einher, dass Ihre IP-Adresse bei Sprach- und Videoanrufen an andere Teilnehmer weitergegeben wird.
Einige Messaging-Anwendungen, die Ihre IP-Adresse an andere weitergeben können, sind z. B:
Signal
Telegram
Threema
X
FaceTime
WhatsApp
Viber
Meta Messenger
Risiken bei der Weitergabe Ihrer IP-Adresse an Gesprächspartner
Ihre IP-Adresse verrät Ihren allgemeinen Standort und kann auch dazu verwendet werden, ein Profil von Ihnen zu erstellen.
Viele Anwendungen, Websites und Online-Dienste speichern Ihre IP-Adresse und verknüpfen sie mit anderen Informationen, die sie über Sie haben. Diese Apps, Websites und Online-Dienste können Ihre Informationen an Dritte weitergeben (z. B. an Werbefirmen, Datenmakler oder Strafverfolgungsbehörden) und tun dies wahrscheinlich auch. Auch wenn sie Ihre Daten nicht direkt an Dritte weitergeben, können Ihre IP-Adresse und andere Informationen, die sie über Sie gespeichert haben, durchsickern oder gestohlen werden.
Da Werbetreibende, Datenmakler, Strafverfolgungsbehörden und böswillige Akteure, die durch Datenlecks oder Datenschutzverletzungen an Ihre Daten gelangen, Ihre IP-Adresse und andere Daten aus mehreren Quellen sammeln können, können sie Ihre IP-Adresse als eine Kennung verwenden, die alle diese Informationen zusammenführt und ihnen hilft, ein umfassendes Profil von Ihnen zu erstellen.
Das Risiko, dass Ihre IP-Adresse bei der Verwendung von Messaging-Anwendungen weitergegeben und zur Profilerstellung verwendet wird, hängt von Ihren persönlichen Umständen ab. Wenn Sie hauptsächlich mit vertrauenswürdigen Freunden und Familienmitgliedern kommunizieren, die bereits wissen, wer Sie sind und von wo aus Sie anrufen, ist das Risiko, dass Ihre IP-Adresse an Anrufer weitergegeben wird, wahrscheinlich gering. Wenn Sie jedoch versuchen, unter einem Pseudonym oder anonym zu kommunizieren und die Geheimhaltung Ihres Standorts und Ihrer Identität für Sie eine hohe Priorität hat, können die Kosten für die Preisgabe Ihrer IP-Adresse erheblich sein.
So können Sie Ihre IP-Adresse bei Anrufen verbergen
1: Verwenden Sie ein VPN oder Tor.
Virtuelle private Netzwerke und The Onion Router (Tor) verbergen Ihre echte IP-Adresse und verhindern, dass sie von Messaging-Apps ausspioniert wird. Die meisten VPNs maskieren den gesamten Datenverkehr Ihres Geräts und schützen Sie standardmäßig vor IP-Adresslecks durch Messaging-Anwendungen. Um dich jedoch vor IP-Adresslecks durch Messenger zu schützen, wenn du Tor verwendest, brauchst du eine Implementierung, die den gesamten Datenverkehr deines Geräts durch das Tor-Netzwerk leitet.
Einige der besten VPN-Anbieter findest du hier.
Um den gesamten Datenverkehr deines Geräts durch Tor zu leiten, kannst du Folgendes tun:
Ein VPN verwenden, das Tor-Verbindungen unterstützt (diese Funktion ist bei Proton VPN verfügbar).
Tails (The Amnesic Incognito Live System) auf deinem Desktop verwenden (diese portable Open-Source-Linux-Distribution leitet deinen gesamten Internetverkehr durch Tor und blockiert alle Anwendungen, die versuchen, ohne Tor eine Verbindung zum Internet herzustellen).
Benutze Orbot auf deinem Handy (dieser Open-Source-Proxy leitet den gesamten Datenverkehr deines Handys durch Tor).
2: Verwenden Sie die Funktionen zur Maskierung der IP-Adresse der Messaging-Anwendung.
Einige Messaging-Apps verfügen über optionale Funktionen, die Ihre IP-Adresse maskieren, indem Anrufe über ihre Server geleitet werden. Die meisten Messaging-Anwendungen sammeln keine zusätzlichen Informationen, wenn Sie diese Funktion aktivieren. Sie sollten jedoch immer die Datenschutzrichtlinien und die Dokumentation einer App lesen, bevor Sie diese Funktion aktivieren, um sicherzustellen, dass die Weiterleitung von Anrufen über die Server der App nicht zu einer zusätzlichen Datenerfassung führt.
Darüber hinaus verwenden viele Messaging-Anwendungen Peer-to-Peer-Verbindungen nur für bestimmte Arten von Anrufen und leiten andere Arten von Anrufen unabhängig von Ihren Einstellungen automatisch über ihre Server weiter. Dadurch wird das Risiko begrenzt, dass Ihre IP-Adresse für bestimmte Arten von Anrufen verwendet wird.
Die folgenden Anwendungen leiten bestimmte Arten von Anrufen automatisch über ihre Server weiter, unabhängig von Ihren Einstellungen:
Signal (Anrufe von Nicht-Kontaktpersonen werden automatisch über die Server von Signal geleitet)
Telegram (Anrufe von Nichtkontakten werden automatisch über die Server von Telegram weitergeleitet)
Threema (Anrufe von nicht verifizierten Kontakten werden automatisch über die Server von Threema geleitet)
WhatsApp (WhatsApp leitet alle Gruppenanrufe automatisch über seine Server weiter und leitet auch andere Anrufe automatisch über seine Server weiter, wenn dies eine bessere Latenz und Qualität als Peer-to-Peer bietet)
Viber (Gruppenanrufe werden automatisch über die Server von Viber geleitet)
Hier erfahren Sie, wie Sie die IP-Maskierung in einigen der beliebtesten Messaging-Anwendungen aktivieren können:
Signal Desktop
Klicken Sie auf Einstellungen (Zahnradsymbol) > Anrufe. Aktivieren Sie Immer umleiten.
Signal Mobil
Tippen Sie auf Ihren Profil-Avatar und wählen Sie Einstellungen > Datenschutz > Erweitert. Aktivieren Sie Anrufe immer umleiten.
Telegramm
Klicken oder tippen Sie auf Einstellungen (Zahnradsymbol) > Datenschutz und Sicherheit > Anrufe. Setzen Sie Peer-to-Peer auf Nie.
Threema
Klicken oder tippen Sie auf Menü (das Zahnradsymbol) > Einstellungen > Threema Anrufe. Aktivieren Sie Anrufe immer durchstellen.
X
Klicken oder tippen Sie auf Nachrichten (das Briefumschlagsymbol) > Einstellungen (das Zahnradsymbol). Aktivieren Sie Erhöhter Anrufschutz.
WhatsApp
Klicken oder tippen Sie auf Menü (das Symbol mit den drei vertikalen Pünktchen) > Einstellungen > Datenschutz > Erweitert. Aktivieren Sie IP-Adresse bei Anrufen schützen.
Viber
Klicken oder tippen Sie auf Mehr > Einstellungen > Privatsphäre. Deaktivieren Sie Peer-to-Peer verwenden.
Andere Möglichkeiten, Ihre Privatsphäre zu schützen
Die Maskierung Ihrer IP-Adresse ist nur eine von vielen Möglichkeiten, Ihre Privatsphäre bei der Nutzung von Messaging-Apps zu schützen. Signal bietet viele weitere Datenschutzfunktionen, die Sie nutzen können. Auch Telegram bietet viele zusätzliche Datenschutzfunktionen.
Unabhängig davon, welche Messaging-App Sie verwenden, ist Ihre IP-Adresse nur eine von mehreren Kennungen, die Informationen über Sie preisgeben können. Um die Daten, die Ihre Messaging-App und die Personen, mit denen Sie kommunizieren, über Sie sammeln können, einzuschränken, sollten Sie diese Grundsätze zur Anonymisierung Ihrer Online-Aktivitäten anwenden.
Quelle: Popular Private Messaging Apps Can Leak Your Location. Here´s How to Protect Yourself., https://reclaimthenet.org/private-messaging-apps-ip-address-leaks
https://uncutnews.ch/beliebte-messenger-apps-koennen-ihren-standort-preisgeben-hier-erfahren-sie-wie-sie-sich-davor-schuetzen-koennen/
 Tethering begrenzen (bzw. stoppen) Tethering begrenzen (bzw. stoppen)
Tethering ist neben den fürs Netz vom Benutzer (in Systemeinstellung unter Apps und Orbot) zugelassenen Apps die einzige App, die nach den hier vorgenommenen Einstellungen noch Daten im mobilen Betrieb ins Netz übertragen kann.
Für eine Begrenzung sollte der Hotspot in Systemeinstellungen komplett deaktiviert werden. Für einen generellen Daten-Übertragungsstop ist der Hotspot nach Überschreitung von in Systemeinstellungen ->, Hotspot einzugebenden 0 Byte automatisch abzuschalten. Danach nimmt Tethering nur noch einen Verbindungsaufbau kleiner 380 Byte vor, da keinerlei Verbindung mit dem Hotspot mehr möglich ist. Davon kann man sich in Systemeinstellungen -> Verbindung und Teilen -> Datennutzung persönlich überzeugen ( man sollte das generell ab und zu tun! ).
 You can also restrict tethering with App secret settings, by deactivating BT-Tethering, Wifi-Hotspot. BT-connecition and camera can also get blocked there. You can also restrict tethering with App secret settings, by deactivating BT-Tethering, Wifi-Hotspot. BT-connecition and camera can also get blocked there.
 The remaining weak point: Der einzige Schwachpunkt der Xiaomi Poco bzw. Android Smartphones bleiben nach all unseren Maßnahmen hier System-Einstellungen -> Datennutzung nur unter MOBIL (nicht WLAN) nach App Gerätesuche und App Android-System, die sporadisch trotz Sperrungen unter Android und Orbot nochmal Daten rüberfunken können. In Orbot lassen sich diese Apps nicht explizit blocken, während WLAN bislang immer alles gebockt wird. Der Umfang der Datenpakete lag bei diesen beiden Apps bei wenigen Kilobytes, mal 3 mal 19 KB usw. und jeweils höchstens dreimal im Monat. The remaining weak point: Der einzige Schwachpunkt der Xiaomi Poco bzw. Android Smartphones bleiben nach all unseren Maßnahmen hier System-Einstellungen -> Datennutzung nur unter MOBIL (nicht WLAN) nach App Gerätesuche und App Android-System, die sporadisch trotz Sperrungen unter Android und Orbot nochmal Daten rüberfunken können. In Orbot lassen sich diese Apps nicht explizit blocken, während WLAN bislang immer alles gebockt wird. Der Umfang der Datenpakete lag bei diesen beiden Apps bei wenigen Kilobytes, mal 3 mal 19 KB usw. und jeweils höchstens dreimal im Monat.
Orbot might get turned off. If it´s always turned on, no apps not allowed are building up any connections.
 Backup des Xiaomi Poco Backup des Xiaomi Poco
Xiaomi Poco m6 Pro (bislang leider nicht bei Poco m5 möglich!): Hier gelang erstmals ein vollständiger Backup aus Systemeinstelluingen nicht nur der System-Apps und System-Einstellungen, sondern aller installierter Apps (darunter z.B. KartaGPS mit den vielen einige Gigabyte großen Landkarten)!
Die Sicherung sollte abschließend auch auf der SD-Karte abgespeichert werden.
 So schützt man Daten vor Staaten, Konzernen und Kriminellen, netzpolitik.org, 2024 So schützt man Daten vor Staaten, Konzernen und Kriminellen, netzpolitik.org, 2024
https://netzpolitik.org/2024/digitale-selbstverteidigung-so-schuetzt-man-daten-vor-staaten-konzernen-und-kriminellen/
 Find out the handy number of a caller and its owner by name - howto, CHIP, 2024 Find out the handy number of a caller and its owner by name - howto, CHIP, 2024
https://praxistipps.chip.de/handynummer-suchen-und-besitzer-herausfinden-so-gehts_46278
 Gernerally do it: These 5 security-checks are part of Android, CHIP, 2024 Gernerally do it: These 5 security-checks are part of Android, CHIP, 2024
https://www.chip.de/news/Sollten-Sie-regelmaessig-anwerfen-Diese-5-Sicherheits-Checks-stecken-in-Android_185687119.html
 BSI provides important security -tips for Android-user: Follow such rules!, CHIP, 2024 BSI provides important security -tips for Android-user: Follow such rules!, CHIP, 2024
https://www.chip.de/news/Wichtig-fuer-Android-Nutzer-Diese-Tipps-des-BSI-sollten-Sie-kennen_185037443.html
 Charging the handy - what you have to pay attention to, CHIP, 2024 Charging the handy - what you have to pay attention to, CHIP, 2024
https://www.chip.de/video/Handy-aufladen-Das-muessen-Sie-beachten-Video_184760000.html
 Why you should think twice, before connecting your smartphone with your car through bluetooth, uncut-news.ch, 12.22.2023 Why you should think twice, before connecting your smartphone with your car through bluetooth, uncut-news.ch, 12.22.2023
Erhebliche Datenschutzbedenken
In der heutigen Welt, in der Bequemlichkeit oft Vorrang vor Vorsicht hat, entpuppt sich die scheinbar harmlose Verbindung des Smartphones mit dem Bluetooth-System des Autos als Datenschutzfalle.
Wenn wir uns auf den Fahrersitz setzen, ist das Ritual, unser Handy per Bluetooth mit dem Auto zu verbinden, für manche so selbstverständlich wie das Anlegen des Sicherheitsgurts. Musik, Navigation und Freisprecheinrichtung sind nur einen Fingertipp entfernt. Doch diese Bequemlichkeit hat ihren Preis: unsere persönlichen Daten. Jedes Mal, wenn ein Smartphone mit dem Infotainmentsystem eines Autos verbunden wird, überträgt es potenziell eine Fülle von Daten - Kontakte, Textnachrichten, E-Mails und sogar besuchte Orte - an die Speichersysteme des Fahrzeugs.
Die Auswirkungen sind weitreichend und werden häufig unterschätzt. Diese Daten, die auf unbestimmte Zeit und oft unverschlüsselt gespeichert werden, sind ein offenes Buch, nicht nur für diejenigen, die direkten Zugang zu Ihrem Fahrzeug haben, sondern auch für Hacker, Anwendungen von Drittanbietern, die in das Fahrzeugsystem integriert sind, und in einigen Fällen sogar für die Fahrzeughersteller selbst.
Geben wir unwissentlich unsere Privatsphäre zugunsten der Bequemlichkeit auf?
Ein Bundesrichter im US-Bundesstaat Washington hat kürzlich eine Sammelklage abgewiesen, die sich gegen den Umgang der Autohersteller mit den persönlichen Daten der Fahrzeugbesitzer richtete. Diese Entscheidung, die zunächst Volkswagen betraf, hat auch Auswirkungen auf ähnliche Klagen gegen andere große Autohersteller wie Honda, Toyota und General Motors.
[...] Beginnen wir mit dem Elefanten im Raum - dem Washington Privacy Act (WPA). Obwohl dieses Gesetz gut gemeint ist, scheint es den Feinheiten des digitalen Datenschutzes nicht gerecht zu werden. Die Entscheidung des Richters basiert auf der Anforderung des WPA, dass Kläger einen konkreten Schaden für die Person, den Ruf oder das Unternehmen nachweisen müssen. Dieses Kriterium erscheint geradezu archaisch angesichts moderner Datenschutzfragen, bei denen der Schaden zwar nicht unmittelbar greifbar, aber nicht weniger bedeutend ist. Es ist das digitale Äquivalent eines umstürzenden Baumes im Wald, wenn niemand in der Nähe ist; nur weil die Auswirkungen nicht zu hören sind, heißt das nicht, dass sie abwesend sind.
Die Automobilindustrie hat sich, wie viele andere Branchen auch, durch die Technologie verändert. Autos sind nicht mehr nur Fahrzeuge, sondern Datenzentren auf Rädern. Das Sammeln von Textnachrichten und Anrufen ist nur die Spitze des Eisbergs. Moderne Autos können ihren Standort, ihre Fahrgewohnheiten und sogar persönliche Vorlieben aufzeichnen - eine wahre Datengoldgrube für Unternehmen. Doch wo verläuft die Grenze zwischen innovativen Diensten und dem Eingriff in die Privatsphäre?
[...] Hier einige der größten Risiken:
Dauerhaftigkeit der Daten: Das größte Problem ist die Dauerhaftigkeit der Daten. Im Gegensatz zu Ihrem Handy, dessen Sicherheitsfunktionen Sie regelmäßig aktualisieren und dessen Speicher Sie regelmäßig leeren, bleiben die im System Ihres Autos gespeicherten Daten oft unüberwacht und ungeschützt. Das bedeutet, dass jeder, der Zugang zu Ihrem Fahrzeug hat - sei es ein Gebrauchtwagenkäufer, ein Autovermieter oder ein Mechaniker - potenziell auf diese Informationen zugreifen kann.
Anfälligkeit für Hacker-Angriffe: Wie jedes andere vernetzte Gerät sind auch Autos anfällig für Hackerangriffe. Mit der zunehmenden Vernetzung von Fahrzeugen steigt auch das Risiko von Cyberangriffen. Theoretisch könnte sich ein Hacker Zugang zu den im Infotainmentsystem Ihres Fahrzeugs gespeicherten Daten verschaffen, einschließlich sensibler persönlicher Informationen.
Zugriff durch Dritte: Viele moderne Autos sind mit integrierten Apps und Diensten ausgestattet, die eine gemeinsame Datennutzung erfordern. Diese Funktionen erhöhen den Komfort, werfen aber auch die Frage auf, wie diese Daten verwendet werden und wer darauf Zugriff hat. In einigen Fällen sammeln die Autohersteller selbst Daten zu Analyse- und Verbesserungszwecken, aber die Transparenz und Sicherheit dieser Datenerfassung ist oft unklar.
Die weiterreichenden Auswirkungen
Dieses Problem geht über den Schutz der Privatsphäre des Einzelnen hinaus. Es berührt auch allgemeinere Themen wie Verbraucherrechte, Datensicherheit und die Verantwortung der Automobilhersteller für den Schutz der Nutzerdaten. In einer Welt, in der persönliche Daten ein wertvolles Gut sind, ist das Fehlen klarer Regeln und Standards für die Datensicherheit im Auto ein großes Versäumnis.
Was kann getan werden?
Auch wenn die Situation bedrohlich erscheinen mag, gibt es Schritte, die unternommen werden können, um die Risiken zu verringern. Dazu gehören:
Achten Sie bei der Verbindung Ihres Telefons mit dem Fahrzeug verstärkt auf die erteilten Berechtigungen.
Löschen Sie regelmäßig Ihre Daten aus dem Fahrzeugsystem, insbesondere vor dem Verkauf oder der Rückgabe eines Mietwagens.
Fordern Sie bessere Datenschutzmaßnahmen von Autoherstellern und App-Entwicklern.
Informieren Sie sich über die Sicherheitsfunktionen Ihres Fahrzeugs und aller damit verbundenen Apps.
Der springende Punkt bei all dem ist die Funktionsweise der Bluetooth-Technologie. Wenn Sie Bluetooth aktivieren, wird Ihr Smartphone für andere Geräte erkennbar und öffnet einen Kanal für die Datenübertragung. Diese Funktion dient der Bequemlichkeit, kann aber auch von Cyberkriminellen ausgenutzt werden, um sich unberechtigten Zugriff auf Ihr Gerät zu verschaffen. Dazu gehören Techniken wie "Bluejacking", bei dem unerwünschte Nachrichten versendet werden, oder - noch beunruhigender - "Bluesnarfing", bei dem sich ein Hacker unbefugt Zugang zu Ihrem Telefon verschafft, um Informationen zu stehlen. Das Risiko ist besonders hoch, wenn man sich in der Öffentlichkeit aufhält, wo unbekannte Geräte darauf warten könnten, sich mit ahnungslosen Smartphones zu verbinden.
Daher ist es wichtig, dass Sie Ihr Smartphone nur mit Bedacht über Bluetooth mit anderen Geräten verbinden. Schalten Sie Bluetooth aus, wenn Sie es nicht verwenden, und wählen Sie die Geräte, mit denen Sie sich verbinden, sorgfältig aus, um sicherzustellen, dass sie vertrauenswürdig und sicher sind. Regelmäßige Software-Updates für Ihr Smartphone sind ebenfalls hilfreich, da sie bekannte Sicherheitslücken beheben. Ferner kann eine sorgfältige Überprüfung der Berechtigungen, die von Apps und Geräten bei der Verbindung angefordert werden, unnötige Zugriffe auf Ihre Daten verhindern. Zusammenfassend lässt sich sagen, dass Bluetooth zwar enorme Vorteile bietet, aber auch ein erhöhtes Maß an Wachsamkeit erfordert, um unsere digitale Privatsphäre zu schützen.
Quelle: https://reclaimthenet.org/why-you-should-think-twice-about-connecting-your-smartphone-to-your-car-via-bluetooth
https://uncutnews.ch/warum-sie-es-sich-zweimal-ueberlegen-sollten-bevor-sie-ihr-smartphone-per-bluetooth-mit-ihrem-auto-verbinden/
 Howto manage Apps for Android? Howto manage Apps for Android?
Kill the daemon of Xiaomi-Handys: Howto kill the MIUI-Daemon and -System-daemon, Jan Kluczniok, netzwelt.de, 01.13.2024
Der MIUI- beziehungsweise System Daemon sammelt auf Xiaomi-Handys Daten zur Verbesserung der Benutzeroberfläche. Wer dies nicht möchte, kann das Tool wie folgt deaktivieren.
Auf vielen Xiaomi-Handys ist die System-App "MIUI Daemon" vorinstalliert. Anders als der Name suggeriert, ist die App nicht nur auf Geräten mit der inzwischen eingestellten Benutzeroberfläche MIUI zu finden, sondern auch auf Geräten mit dem neuen HyperOS.
Diese Daten sammelt der MIUI Daemon
Hinter der mysteriösen Anwendung verbirgt sich ein Tool, mit dem der Hersteller offenbar einige Daten zur Verbesserung der Benutzeroberfläche sammelt. Der Analyse eines Xiaomi-Fanblogs zufolge sammelt der MIUI Daemon die folgenden Daten über euer Handy.
die Größe des verbauten Speichers
die Zeit, wie lange der Bildschirm eingeschaltet ist
Ladestatistiken des Hauptspeichers
Batterie und CPU-Statistiken
Den Status von Bluetooth und WiFi
die IMEI-Nummer
Eine Spionage-App ist die Anwendung also nicht, denn sie sammelt keine direkten persönlichen Daten von euch, sondern nur Informationen zum Zustand des Gerätes. Wer dennoch ein Unbehagen verspürt, kann den MIUI Daemon deaktivieren. Dies ist entweder direkt bei der Einrichtung eures Xiaomi-Handys möglich, aber auch nachträglich.
Das ist in wenigen Schritten erledigt. Das folgende Video zeigt euch wie ihr vorgehen müssst.
Nachfolgend findet ihr auch noch einmal eine Schritt-für-Schritt-Anleitung mit Screenshots zu den einzelnen Schritten.
MIUI Daemon - Zustimmung widerrufen
...
https://www.netzwelt.de/anleitung/197497-xiaomi-handys-daemon-austreiben-so-deaktiviert-miui-daemon-2024.html
 How to personalize my Android Smartphone How to personalize my Android Smartphone
Xiaomi: Howto deactivate advertisement in MIUI and HyperOS, Marcel Laser, netzwelt.de, 02.13.2024
Xiaomi nutzt seine Benutzeroberflächen MIUI und HyperOS auch dazu, um euch in vielen Gelegenheiten auf dem Handy auch Werbung anzuzeigen. Wir verraten ihr diese abschaltet.
MSA im Android-System: Deaktiviert die Systemanwendung umgehend
Persönliche Werbeanzeigen durch Google deaktivieren
Sicherheits-App: Werbevorschläge deaktivieren
Mi Browser: Werbevorschläge deaktivieren
https://www.netzwelt.de/anleitung/187320-werbung-xiaomi-handys-deaktivieren-so-gehts.html
 Howto free intern memory... Howto free intern memory...
Lock Apps (and some Bloatware), Gooken, 02.28.2024
Tap upon MIUI-security-App -> click upon its settings -> boost speed -> App lock: Lock them out from a list.
We chose the system-Apps: MIUI Info-Assistent, UKW-Radio, Google Messages (Alternative: schlichte SMS), Services and Feedback, GetApps, Themen and Lite.
One more advantage of this is, that the speed does remarkable increase!
 Howto free memory from Android devices... Howto free memory from Android devices...
Android: Howto kill bloatware without having root-rights, Markus Kasanmascheff, netzwelt.de, 11.29.2023
Überflüssige Software in Form von Bloatware kann euer Android-Smartphone schnell zumüllen. Wir zeigen euch, wie ihr sie auch ohne Root-Rechte entfernt und löscht.
Auf den Smartphones fast aller großen Hersteller wie Xiaomi, Samsung oder Sony sind inzwischen zahlreiche Apps vorinstalliert. Mit dieser Bloatware schnell eine Fülle an Datenmüll ansammeln, die man nicht unbedingt auf dem Handy haben will. Das Problem: Die Bloatware lässt sich, anders als normale Apps, nicht einfach deinstallieren.
Doch keine Sorge. Um Android-Bloatware zu entfernen, müsst ihr aber nicht gleich euer Handy rooten und eine spezielle Lösch-App nutzen. Mit den offiziellen Android-Tools von Google für PCs könnt ihr die Bloatware ebenfalls leicht löschen.
Dazu müsst ihr lediglich euer Telefon per USB-Kabel anschließen und ein paar Befehle ausführen. Komplett entfernt werden die Apps von eurem Android-Gerät dabei allerdings auch nicht. Als reaktivierbares Datenpaket bleiben sie euch weiterhin erhalten und werden lediglich aus eurem Android-Nutzerkonto entfernt.
Trotzdem lässt sich durch dieses teilweise Entfernen der Android-Bloatware in der Regel einiges an Speicherplatz freiräumen, da die Bloatware-Apps dann nicht installiert sind und sich auch keine App-Updates anhäufen. Und auch eure App-Liste wird dadurch übersichtlicher. Wie ihr Android-Bloatware ohne Root-Zugriff entfernen und bei Bedarf wieder installieren könnt, zeigen die folgenden Schritte.
https://www.netzwelt.de/anleitung/193588-android-so-entfernt-bloatware-ohne-root-zugriff.html
 Backup into the internal memory and/or cloud: setttings -> Phone -> make a backup Backup into the internal memory and/or cloud: setttings -> Phone -> make a backup
 Backup onto SD-cad: SuperBackup (Apk) and/or AppsBackup (Apk) Backup onto SD-cad: SuperBackup (Apk) and/or AppsBackup (Apk)
 Backup from SD card onto the computer: you need a SD card reader for it (we have seen one for all kind of SD-cards for less than 10 Euro, ebay.de, Stand: 2023) Backup from SD card onto the computer: you need a SD card reader for it (we have seen one for all kind of SD-cards for less than 10 Euro, ebay.de, Stand: 2023)
 Limit processes (1): Secure Settings (Apk) -> Options: limit conditions, Actions, Secure Settings Actions, Dev Admin Actions, System Actions,Rroot Actions, Custom ROM Actions, Xposed Framework Actions down to the ones really needed Limit processes (1): Secure Settings (Apk) -> Options: limit conditions, Actions, Secure Settings Actions, Dev Admin Actions, System Actions,Rroot Actions, Custom ROM Actions, Xposed Framework Actions down to the ones really needed
 Limit processes (2): settings -> developer options -> "Do not keep activities ... and all activities, the user ended" to true, you can also set the "Limit for background processes" in developer options Limit processes (2): settings -> developer options -> "Do not keep activities ... and all activities, the user ended" to true, you can also set the "Limit for background processes" in developer options
 Google Apps: deactivate / forbid usage data, error reports and further on one side of settings through Hidden Settings (2) Google Apps: deactivate / forbid usage data, error reports and further on one side of settings through Hidden Settings (2)
 Gboard (keyboard for keyboard-like-input): deactivate user data, error reports and further on: Hidden Settings (1) -> search for Gboard, alternative: keyboard (Tastatur, apkpure.com) Gboard (keyboard for keyboard-like-input): deactivate user data, error reports and further on: Hidden Settings (1) -> search for Gboard, alternative: keyboard (Tastatur, apkpure.com)
 Limit processes (1): Secure Settings (Apk) -> options: limit conditions, actions, secure settings action, dev admin actions, system actions, root actions, custom ROM actions, and exposed framework actions Limit processes (1): Secure Settings (Apk) -> options: limit conditions, actions, secure settings action, dev admin actions, system actions, root actions, custom ROM actions, and exposed framework actions
 Limit processes (2): settings -> developer options Limit processes (2): settings -> developer options
 The very best thing you can do is to do all this already in the root-mode. To get into this mode, at first try one-click-rooting-apps like KingRoot or KingoRoot. If such Appsfail, prepare the Root Mode by its administering Apps like Magisk and/or SuperSU: Zunächst aber (da Poco m5 ein Wipe auf dem internen Speicher im Anschluss durchführt) ein vollständiges Backup anfertigen, dann Entwickleroptionen mit fünffachem Klick auf die Mobilnummer in Einstellungen ->, Telefon rechts freischalten, und dort, in Einstellungen -> Entwickleroptionen: USB-Debugging erlauben, OEM-Bootloader entsperren und dem Hersteller (Xiaomi) die MI-Bootloader-Entsperrung melden (registrieren), von dort MI-Unlock für den PC downloaden, in Entwickleroptionen: App-Installation über USB erlauben, MI-Unlock auf PC (geht nur mit MS Windows) installieren, Bootloader entsperren, mit Druck auf Volume und Power-Taste neustarten -> im erscheindenden Menü Root-Modus oder USB-Verbindung wählen, internen Speicher mit adb am PC (Linux: android-tools (rpm) bearbeiten (Custom ROM TWRP installieren) oder im Root-Modus gleich durchbooten. Beachte: Wir habens bislang leider selbst noch nicht probiert: Notice, that, for attempts to get into root-mode, the complete manfacturer guarantee for the smartphone can void! The very best thing you can do is to do all this already in the root-mode. To get into this mode, at first try one-click-rooting-apps like KingRoot or KingoRoot. If such Appsfail, prepare the Root Mode by its administering Apps like Magisk and/or SuperSU: Zunächst aber (da Poco m5 ein Wipe auf dem internen Speicher im Anschluss durchführt) ein vollständiges Backup anfertigen, dann Entwickleroptionen mit fünffachem Klick auf die Mobilnummer in Einstellungen ->, Telefon rechts freischalten, und dort, in Einstellungen -> Entwickleroptionen: USB-Debugging erlauben, OEM-Bootloader entsperren und dem Hersteller (Xiaomi) die MI-Bootloader-Entsperrung melden (registrieren), von dort MI-Unlock für den PC downloaden, in Entwickleroptionen: App-Installation über USB erlauben, MI-Unlock auf PC (geht nur mit MS Windows) installieren, Bootloader entsperren, mit Druck auf Volume und Power-Taste neustarten -> im erscheindenden Menü Root-Modus oder USB-Verbindung wählen, internen Speicher mit adb am PC (Linux: android-tools (rpm) bearbeiten (Custom ROM TWRP installieren) oder im Root-Modus gleich durchbooten. Beachte: Wir habens bislang leider selbst noch nicht probiert: Notice, that, for attempts to get into root-mode, the complete manfacturer guarantee for the smartphone can void!
 More than important security care for Android-smartphones like Y360-U61 and Xiaomi poco m5 are App-rights, Autostart of Apps (one for user and one for root mode), App-lock, Apk-link-locks, deactivation of advertisements and personalized advertisement of Apps, mse, developer-options and settings of each App: More than important security care for Android-smartphones like Y360-U61 and Xiaomi poco m5 are App-rights, Autostart of Apps (one for user and one for root mode), App-lock, Apk-link-locks, deactivation of advertisements and personalized advertisement of Apps, mse, developer-options and settings of each App:
Deactivate advertisement:
Open settings
Passwords&security
Remove authorization
deactiviere msa
confirm the remove
Touch upon the free place of the start screen
settings
Morer
Deactivate suggestions
Open the security app
settings
Deactivate suggestions (advertisement)
Installi an App
Open settings
Deactivate suggestions
Open the Downloads-App
Open the menu
settings
Deactivate adverstisement
Themes:
Ooen the themes App
Click upon account
settings
Deaktivate advertisement
Music:
Open the music-App
Oopen menu
settings
Click upon advanced settings
Deactivate advertisement
Mi-Browser:
Open the Mii-Browser
Click upon account
Click upon extened
Deactivate advertisement
App-lock
Open settings
Click upon Apps
App-lock
Deactivate suggestions
Personalized advertisement:
Settings
Passwords&Security
Ad services
Deactivate pesronalized advertisement
 What interests much next to achieve a high securit level, is the App-lock, all App-rights and autostart of Apps out of settings, each App-settings itself, developer-options .. and so on depending on your smartphone (Android/Lineage-OS) model. Look out in the internet from various sources, what all is possible of security-settings for your smartphone. What interests much next to achieve a high securit level, is the App-lock, all App-rights and autostart of Apps out of settings, each App-settings itself, developer-options .. and so on depending on your smartphone (Android/Lineage-OS) model. Look out in the internet from various sources, what all is possible of security-settings for your smartphone.
You might find more Apps to deactivate by the process-manager given in the system settings under "Active". Only one messenger from Facebook should be installed beneath other ones like telegram or Signal: either WhatsApp or the all contacts from all over the world (among facebook) including phone delivering facebook-messenger Lite.
 10) Connection Stabilizer Booster: This App is aimed to restore and to keep an already established Wifi-(WLAN-) connection, so do not turn over to another one. This keeps to the fallback to horrible expensive providers like Telefonica. 10) Connection Stabilizer Booster: This App is aimed to restore and to keep an already established Wifi-(WLAN-) connection, so do not turn over to another one. This keeps to the fallback to horrible expensive providers like Telefonica.
 PrivateDNS: make DNS-queries secure using protocol DoH or DoT instead of udp: MIUI-settings ->, Connections and share -> Private DNS -> set the domain name for a Private DNS. Find such name in the internet. Also use personalDNSfilter apk. With Orbot the anonymizing tordns gets in use.. PrivateDNS: make DNS-queries secure using protocol DoH or DoT instead of udp: MIUI-settings ->, Connections and share -> Private DNS -> set the domain name for a Private DNS. Find such name in the internet. Also use personalDNSfilter apk. With Orbot the anonymizing tordns gets in use..
 11) Passwort-Manager: Be careful, do not store anything into them, especially if advertisement is blended in. 11) Passwort-Manager: Be careful, do not store anything into them, especially if advertisement is blended in.
Very expensive (alternative) provider for modell (Huawei Y360-U61) for the case of locked SIM-cards like Telefonica
Mobil phone bill
125 Euro for nothing: "Finanztest" warns againt handy-rip-off
https://www.stern.de/digital/smartphones/teure-rechnung-ohne-leistung--finanztest-warnt-vor-abo-abzocke-8859634.html
 12) App "Apps Autostart": at least autostart the Apps NetGuard, Connection Stabilizer Booster and ARP-Guard. Otherwise such Apps need to be started (activated) each system boot manually. 12) App "Apps Autostart": at least autostart the Apps NetGuard, Connection Stabilizer Booster and ARP-Guard. Otherwise such Apps need to be started (activated) each system boot manually.
Autostart Apps, report from trishtech.com
"On the settings screen, scroll down a little and then tap on Security to open the security related settings.
In the security section you will find many settings related to apps like app permissions, app verification, whether to install from unknown sources etc. You have to tap on Auto-start Management to in this list.
In the auto-start management screen, it will display a list of all the apps that are being auto-started in your Android phone. You can simply uncheck any apps that you want to disable from being auto-started. Similarly, checking an app will enable it to be auto-started with Android bootup.
While disabling some of the apps from being automatically started at Android boot will surely make it a little faster, but you have to be careful not to disable any important apps. For example, you should never disable antivirus products related apps from being auto-started as they protect your Android device from malicious apps and programs."
https://www.trishtech.com/2014/07/enable-disable-auto-starting-apps-in-android/
Set "Start delay(s)" to 0 seconds and "Nex App delay(s)" to 0 seconds too.
 13) Deactivate single Apps even after each system newstart (the process to deactivate almost follows from the information of the see Huawei-process manager): system settings -> Apps -> all Apps -> click onto the App to deactivate -> click onto "deaktivate" 13) Deactivate single Apps even after each system newstart (the process to deactivate almost follows from the information of the see Huawei-process manager): system settings -> Apps -> all Apps -> click onto the App to deactivate -> click onto "deaktivate"
 14) Tor-Browser and Firefox: Gedacht sei unbedingt wieder an die Firefox-Erweitungen wie zum Setzen des UserAgents, noscript, ABP bzw. ABL usw.. 14) Tor-Browser and Firefox: Gedacht sei unbedingt wieder an die Firefox-Erweitungen wie zum Setzen des UserAgents, noscript, ABP bzw. ABL usw..
To the download: Firefox Private Network VPN
Firefox Private Network VPN - Android App
CHIP-Bewertung good
"Firefox Private Network VPN" is the Virtual Private Network (VPN) from Mozilla, with which you can surf online the Android-smartphone anonymously.
Zum Download: Firefox Private Network VPN
Firefox Private Network VPN - Android App
CHIP-Bewertung Gut
"Firefox Private Network VPN" ist das Virtual Private Network (VPN) von Mozilla, mit dem Sie mit Ihrem Android-Gerät anonym online surfen können."
Download: Mullvad VPN
Mullvad VPN 2020.2
CHIP-Bewertung Gut
"Mullvad VPN" uses the new WireGuard-Protokoll. This makes VPN-Verbindungen not only more secure, but also very fast."
https://www.chip.de/news/VPN-von-Firefox-So-nutzen-Sie-es-schon-heute_151248182.html
 Before apps are downloaded from PlayStores, read out their requirements like In-App-Orders (new contracts), WLAN-access, location access, advertisement, ... . downloaded apps should require as few of it as possible! Before apps are downloaded from PlayStores, read out their requirements like In-App-Orders (new contracts), WLAN-access, location access, advertisement, ... . downloaded apps should require as few of it as possible!
Instead this App is still not for free (... but maybe quit interesting too):
Teamviewer Pilot: AR-remote-maintenance-App now with text integration, PC-WELT.de, 08.20.2019
https://www.pcwelt.de/news/Teamviewer-Pilot-AR-Fernwartungs-App-jetzt-mit-Textintegration-10650074.html
Android by Google can not be considered - as "1000%" resp. 100% secure - inspite of the reliable firewall NetGuard.
Through "Autostart" NetGuard becomes active only the time further past the activation of some single processes. So they do not get blocked.
 Following the processmanager section active, the deactivation (resp. deinstallation) of following processes of listed Apps from above might be recommended: Following the processmanager section active, the deactivation (resp. deinstallation) of following processes of listed Apps from above might be recommended:
youtube
Google Maps
Google Chrome (Browser)
Hangouts
Drive
Gmail
Google Play Bücher
Google Play Games
Google Play Movies
Google Play Musik
Google-Suche
Street View
viele Google Dienste außer Google Play (an für sich einschließlich Google Play; eine neue Registrierung ist mit der Aktivierung dann aber erforderlich) und Android-Systemprozesse
DasOertliche
FreeCall
...
Unfortunately Facebook-Lite and belonging Facebook-messenger "Lite" resp. WhatsApp do remain active right from the beginning past boot, as one is almost unwilling to resign from Lite.
 Advertising-IDs yesterday as today: Who doesn´t care, gets tracked, netzpolitik.org, 09.04.2024 Advertising-IDs yesterday as today: Who doesn´t care, gets tracked, netzpolitik.org, 09.04.2024
Tracking-Firmen können verfolgen, was wir mit unseren Handys tun, und zwar durch individuelle Werbe-IDs. In den letzten 15 Jahren haben Apple und Google immer wieder Privacy-Funktionen für iOS und Android ergänzt. Doch nach wie vor behält das Tracking die Oberhand. Eine Historie.
Die eigene Postadresse, die eigene Telefonnummer, das kennen die meisten auswendig. Aber die eigene Werbe-ID? Viele dürften nicht einmal wissen, was das ist. Dabei ist auch die Werbe-ID sehr aussagekräftig. Während unserer Recherchen auf einem Datenmarktplatz sagte uns ein Datenhändler sogar: Die Werbe-ID sei wie ein Klarname.
Diese ID ist einfach schon da, wenn wir ein neues Smartphone mit iOS oder Google-basiertem Android einrichten. Und die ID wird neu berechnet, wenn wir wir ein gebrauchtes Gerät neu aufsetzen. Ab dann begleitet sie uns wie ein Nummernschild durch den App-Kosmos.
Zum Beispiel schicken viele Spiele-, Wetter-, Navigations- oder Datings-Apps unsere personenbezogenen Daten an Hunderte bis Tausende Werbepartner auf einmal. Dazu können Vorlieben, E-Mail-Adressen und Standorte gehören – und sehr oft eben auch unsere individuellen Werbe-IDs. Durch diese IDs lassen sich die erfassten Daten über mehrere Apps hinweg bündeln.
Standortdaten aus einer Wander-App, persönliche Schwächen aus einer Psychotest-App und sexuelle Vorlieben aus einer Dating-App? Dank Werbe-ID ließe sich all das miteinander zu einem aussagekräftigen Profil kombinieren.
Erfasst werden solche Daten angeblich nur zu Werbezwecken, angeboten werden sie jedoch teils offen auf Datenmarktplätzen.
In einer gemeinsamen Recherche mit dem Bayerischen Rundfunk haben wir jüngst 3,6 Milliarden Standortdaten von Handys aus Deutschland ausgewertet, angeboten von einem US-Händler auf einem deutschen Marktplatz. Die Daten stammen von Millionen Handys. Sie offenbaren die genauen Bewegungen von Menschen aus praktisch jeder Ecke des Landes. Einige Personen konnten wir mithilfe der Daten sogar eindeutig identifizieren. Zu Bewegungsprofilen verknüpfen konnten wir die Milliarden Standortdaten allerdings nur, weil jeder Datenpunkt mit einem Identifier versehen war: der Werbe-ID.
Die ID kommt ab Werk
Auf Privatsphäre bedachte Nutzer*innen können diese Werbe-ID inzwischen händisch tilgen. Wie das geht, beschreiben wir hier. Aber standardmäßig sind diese IDs auf Mobiltelefonbetriebssystemen aus dem Hause Apple und Google erst einmal eingerichtet. Und dass man gegen das Tracking per Werbe-ID überhaupt etwas machen kann, ist eine Errungenschaft der vergangenen Jahre, wie unsere historische Übersicht für iOS (🍏) und Android (🤖) zeigt.
Maßnahmen dagegen: https://netzpolitik.org/2024/databroker-files-so-stoppt-man-das-standort-tracking-am-handy/
https://netzpolitik.org/2024/werbe-ids-damals-und-heute-wer-nicht-aufpasst-wird-getrackt/
Lesermeinung Gooken
Verwenden Sie insbesonders für Online Banking, Facebook, WhatsApp und Signal immer duale (in jeweils neuen eigenen Benutzerkonten geklonte) Apps. Falls hierfür Google-Play-Dienste dual erforderlich ist, schränken Sie sie in Verbindungen ein und blockieren Sie diese wieder im Netz (Wifi und mobil). Jede App wird damit ja mit einem neuen Benutzerkonto mit zugehöriger Benutzer-ID assoziiert. Damit erhalten sie mit jeder dualen App eine weitere, neue Werbe-ID, was insgesamt zur Zerstückelung der Werbe-ID beiträgt.
Nicht nur über die System-Einstellungen, sondern auch mit MIUI Hidden Settings (allerdings gibts hierfür viele gleichnamige Apps...) können neue Werbe-ID gesetzt werden. Die Vorgänger-ID wird damit gelöscht.
 Stop location-Tracking: Howto netzpolitik.org, 07.16.2024 Stop location-Tracking: Howto netzpolitik.org, 07.16.2024
Um dich davor zu schützen, dass Apps deinen Standort an Datenhändler weitergeben, kannst du folgende Dinge tun.
Überprüfe in den Systemeinstellungen, welche deiner Apps Zugriff auf deinen Standort haben (Android, iOS). Gewähre diese Erlaubnis, wenn überhaupt, nur Apps, die solche Daten nicht an Datenhändler weitergeben – und sie offenkundig brauchen, zum Beispiel, weil sie dir beim Navigieren helfen sollen.
Überprüfe die Datenschutzbestimmungen der Apps, die deinen Standort erfassen. Dort müssen App-Betreiber transparent machen, ob und an wen sie Daten weitergeben. Sie lassen sich oft innerhalb der App nachlesen. Oder sie sind im Google Play Store oder App Store von Apple verlinkt. Viele Apps lassen sich ohne Zustimmung zu den Datenschutzbestimmungen nicht nutzen. Wer mit den Datenschutzbestimmungen nicht einverstanden ist, muss auf diese Apps verzichten.
Was du Apps nicht erlaubst, solltest du auch Websites nicht erlauben. Auch wenn es lästig ist: Suche bei Cookie-Bannern konsequent den Button, um Tracking abzulehnen. Bei manchen Websites ist das allerdings nicht möglich.
Dein Standort kann über mehrere Quellen bestimmt werden, zum Beispiel GPS, Mobilfunk, WLAN. Schalte davon nur ein, was du gerade wirklich brauchst. Das verringert das Risiko, dass Standortdaten überhaupt erfasst werden.
Du kannst künftiges Tracking erschweren, indem du auf Google-basierten Android-Handys deine mobile advertising ID (MAID) löschst – oder auf Apple-Handys das ID-basierte App-Tracking untersagst.
Wie setze ich meine MAID zurück?
Die „mobile advertising ID“ (MAID) ist eine Art Nummernschild. Android und iOS generieren sie im Hintergrund. Durch diese Kennung sind wir für die Werbeindustrie eindeutig erkennbar. Oft steht diese auch ID dabei, wenn Apps unseren Standort an Datenhändler verraten.
Auf Google-basierten Android-Geräten hat die mobile advertising ID den Namen Werbe-ID. Finden kann man sie auf diesem Weg: Einstellungen > Google (Google-Dienste) > Alle Dienste > Werbung. Dort kannst du die ID auch löschen. Je nach Android-Version kann sich der Klickweg leicht unterscheiden.
Auf Apple-Handys mit iOS hat die mobile advertising ID den Namen: IDFA („Identifier for Advertisers“). Leider ist sie versteckt. Zum Auslesen braucht es Drittanbieter-Apps wie My Device ID oder Adjust Insights und diese Apps benötigen leider die Erlaubnis zum App-Tracking. Deshalb lösche sie besser, sobald du mit ihrer Hilfe deine ID herausgefunden hast. Den IDFA löscht du so: Einstellungen > Datenschutz > Tracking > Tracking für Apps verbieten.
Wie kann ich sonst noch aktiv werden?
Darüber hinaus gibt es noch mehr Dinge, die man tun kann, wenn man sich weiter einbringen möchte:
Du kannst dich auf deine Rechte laut Datenschutzgrundverordnung berufen und Auskunftsanfragen an Datenhändler stellen. Die Unternehmen sind verpflichtet, dir zu antworten, welche Daten sie über dich gespeichert haben. Auch wenn bei solchen Anfragen lange nichts passiert und Unternehmen außerhalb der EU oft schwer zu greifen sind: Anfragen machen sichtbar, dass Nutzer*innen ein Problem haben. Und das kann ein Argument für strengere Regeln in der Zukunft ein.
Wenn du das Gefühl hast, da ist etwas faul, kannst du daraufhin Datenschutzbehörden einschalten, damit sie die Firma genauer unter die Lupe nehmen. Am besten wendest du dich direkt an die Datenschutzbehörde in deinem Bundesland. Hier erklären wir genauer, wie man Auskunftsanfragen stellt und Datenschutzbehörden einschaltet.
Du kannst gezielt datensparsame Apps nutzen und oftmals die Betreiber*innen deiner Lieblingsapps mit freiwilligen Spenden unterstützen. Bei der Suche nach datensparsamen Apps helfen etwa der Appchecker von mobilsicher oder – für Android-Nutzer*innen – der alternative App-Katalog F-Droid.
Du möchtest wissen, ob deine ID in dem Datensatz auftaucht, den wir von einem Datenhändler erhalten haben? Dafür haben wir ein Tool programmiert. Hier gelangst du zu unserem Databroker-Checker.
https://netzpolitik.org/2024/werbe-ids-damals-und-heute-wer-nicht-aufpasst-wird-getrackt/
 15) MalBytes (MalwareBytes): A deep scan for security exploits, errors and bugs with recommends for their correctures is performed especially by MalBytes (experts from trojaner-board.de)! After the scan, this App can be deinstalled again. 15) MalBytes (MalwareBytes): A deep scan for security exploits, errors and bugs with recommends for their correctures is performed especially by MalBytes (experts from trojaner-board.de)! After the scan, this App can be deinstalled again.
At the very beginning, past the boot of Android, one should always have a look into SIM and Wifi of system-settings, before super-expensive bills are awaiting by (still) quit unknown providers like Telefonica !
Smartphone, Apps & Co.: The 20 most important tips for mobile security, trojaner-info.de, 09.29.2019
Smartphone and tablet-fans should not be used light-headed and unprotected in the mobile internet. Therefore all in all security requirments and the protection of smartphones and tablets should be similar high and higher than even PC. Here are the 15 most important tips for mobile security.
https://www.trojaner-info.de/mobile-security/20-tipps-fuer-mobile-sicherheit/articles/smartphone-apps-die-15-wichtigsten-tipps-fuer-mobile-sicherheit.html
 Mobil phone with integrated eavesdropping-module Mobil phone with integrated eavesdropping-module
rC3: Handy of Assange-member Müller-Maguhn obviously got corrupted by the CIA, trojaner-info.de, 29.12.2020
Andy Müller-Maguhn, früherer Sprecher des Chaos Computer Clubs (CCC), hat am Sonntag auf dem remote Chaos Communication Congress (rC3) von massiven Einschüchterungsversuchen durch staatliche Geheimdienste berichtet. Dass die CIA ihm hinterher sei, ist für ihn demnach spätestens offensichtlich geworden, als er nach einer Reparatur entdeckt habe, dass sein verschlüsselt kommunizierendes Mobiltelefon mit einem integrierten Abhörmodul verwanzt worden sei.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/rc3-handy-von-assange-mitstreiter-mueller-maguhn-offenbar-von-cia-kompromittiert.html
 Data protection: Digitalcourage prosesses by law against tracking n Deutsche-Bahn-App, netzpolitik.org, 10.20.2022 Data protection: Digitalcourage prosesses by law against tracking n Deutsche-Bahn-App, netzpolitik.org, 10.20.2022
Der DB Navigator trackt mehr Informationen als nötig, ohne dass Nutzende sich dem widersetzen können. Trotz monatelanger medialer Empörung hat die Deutsch Bahn daran nichts geändert - und handelt sich nun eine Klage ein.
https://netzpolitik.org/2022/datenschutz-digitalcourage-klagt-gegen-tracking-in-deutsche-bahn-app/
 Checklist: Howto secure up Windows, Android and Co., PC-WELT.de, 03.02.2020 Checklist: Howto secure up Windows, Android and Co., PC-WELT.de, 03.02.2020
With our compact checklists you prevent hacker accessing your data. Howto.
https://www.pcwelt.de/ratgeber/Checkliste-Windows-Android-und-Co-absichern-10527252.html
Antivirus-Apps for Android in test: anti-malware-tools and virus-scanner for the handy
Total security upon the smartphone, CHIP, 06.06.2020
Auch Handys sind Ziele von Viren und Malware. Ein prominentes Beispiel für Problemsoftware zeigt unser Video oben. Wir haben daher die beliebtesten Android-Virenscanner und Sicherheits-Suiten testen lassen, sagen welche am besten ist und worauf Sie achten sollten. Zudem geben wir Tipps zur sicheren Nutzung ihres Mobiltelefons. Der Test entstand in Zusammenarbeit mit den Virenspezialisten von AV-Comparatives im September 2019.
https://www.chip.de/artikel/Android-Virenscanner-Anti-Malware-Kaufberatung-Test-Praxistipps_172917097.html
 Gooken also recommends the above listed costless scanner "Antivirus Helper", that uses the actual virus-defintion-file online (the App with the MS Windows like icon) and the anti-spyware-scanner "Inkognito". Antivirus Helper has got a nice clockfaced gui like the backup-App from Huawei displaying scanned percent in the middle, scans fast and high intensive and removes junk-files too. Gooken also recommends the above listed costless scanner "Antivirus Helper", that uses the actual virus-defintion-file online (the App with the MS Windows like icon) and the anti-spyware-scanner "Inkognito". Antivirus Helper has got a nice clockfaced gui like the backup-App from Huawei displaying scanned percent in the middle, scans fast and high intensive and removes junk-files too.
 System-Android-First-Login-Protection:: screen-locker ( 6 -18 ciphered PIN or password) System-Android-First-Login-Protection:: screen-locker ( 6 -18 ciphered PIN or password)
 Apps can be regulary actualized/updated Apps can be regulary actualized/updated
Smartphone, Apps & Co.: The 20 most important tips for mobile security, trojaner-info.de, 09.29.2019
Smartphone und Tablet-Fans sollten niemals leichtfertig und ungeschützt im mobilen Internet unterwegs sein. Alles in allem sollten deshalb die Sicherheitsanforderungen und der Schutz des Smartphones und Tablets ähnlich hoch oder höher sein wie beim PC. Die 15 wichtigsten Tipps für mobile Sicherheit.
https://www.trojaner-info.de/mobile-security/20-tipps-fuer-mobile-sicherheit/articles/smartphone-apps-die-15-wichtigsten-tipps-fuer-mobile-sicherheit.html
The five most threats for mobile security, trojaner-info.de, 10.15.2019
Tipps, wie Sie Ihr Unternehmen vor den mobilien Sicherheitslücken schützen können nach Erfahrung von Palo Alto Networks
[...] 1. Phishing-threats: Wobei noch vor ein paar Jahren die Phishing-Angriffe haupsächlich per E-Mail durchgeführt wurde, werden heute mobilie Kanäle wie SMS, Facebook Messenger, WhatsApp und gefälschte Websites ausgenutzt für die Cyberattacke. Zudem ist Spear-Phishing eine zunehmende Bedrohung. Hierbei werden bestimmte Mitarbeiter von Hackern über mobile Geräte angesprochen, um Zugang zu sensiblen Daten zu erhalten.Mobile 2. Malware: Jede Website, die besucht oder verlinkt wird, hat das Potenzial, mobile Geräte mit Malware wie Spyware, Ransomware, Trojaner-Viren, Adware etc. zu infizieren.
3. Dangerous: opened WLAN-networks: Viele mobile Mitarbeiter nutzen heute öffentliche WLAN-Netzwerke, wenn sie außerhalb des Büros unterwegs sind. Da sich die meisten Cyberkriminellen dessen bewusst sind, versuchen sie, mobile Nutzer dazu zu bringen, sich mit gefälschten WLAN-Netzwerken zu verbinden und so Daten zu kompromittieren.
4. Malware: Viele Apps sind legitim und sicher zu verwenden, aber es gibt auch tausende, die es nicht sind. Das Herunterladen einer App auf einem mobilen Gerät kann daher das Unternehmen des Benutzers einer Vielzahl von Sicherheits- und Datenschutzrisiken aussetzen. Einige Apps sammeln sogar Daten, ohne den Benutzer um Erlaubnis zu bitten.
5. Data leaks: Datenlecks treten bei jeder unbefugten oder unbeabsichtigten Übertragung von Daten aus einem Unternehmen an ein externes Ziel auf. Diese Datenlecks können zurückgehen auf eine Person innerhalb des Unternehmens, die sensible Daten in eine Public Cloud überträgt, anstatt in die Private Cloud. Es könnte aber auch ein externer Angreifer dahinterstecken, der die Daten des Unternehmens absichtlich stiehlt. Mobile Endgeräte, die oft eine Mischung aus geschäftlichen und persönlichen Daten enthalten, machen es noch einfacher, die Grenzen zwischen Geschäftlichen und Privatem versehentlich oder gezielt zu verwischen.
[...] Antivirensoftware und Data Loss Prevention (DLP)-Tools den mobilien Geräten hinzugefügen
Bessere und einfachere Arbeitsmöglichkeiten anbieten, damit Mitarbeiter sich nicht mit unsicheren öffentlichen WLANs verbinden
Mitarbeiter sollten App-Berechtigungen sorgfältig überprüfen, bevor sie ihnen Zugriff gewähren, und Anwendungen deaktivieren, die missbraucht werden könnten
MFA-Tools (Multi-Factor Authentication) sollten von Mitarbeitern verwendet werden, wenn sie sich über ihre mobilen und persönlichen Geräte mit dem Unternehmensnetzwerk verbinden
[...]
10 things, you should better not do with the smartphone, PC-WELT.de, 10.18.2019
We show the worst social slips, you can do with your smartphone.
https://www.pcwelt.de/ratgeber/10-Dinge-die-Sie-mit-dem-Smartphone-besser-lassen-sollten-10680755.html
 "Drunken-mode" "Drunken-mode"
Getting drunk: Curios patent aims to protect handy-user, CHIP, 09.02.2021
Ein chinesischer Smartphone-Hersteller hat ein kurioses Patent eingereicht. In diesem geht es um einen "Betrunken-Modus" für die eigenen Geräte, die Nutzer aus diversen Apps aussperren. Im Gegensatz zu anderen Lösungen ist dieser Modus bereits im Smartphone integriert.
https://www.chip.de/news/Betrunken-am-Smartphone-Kurioses-Patent-will-Handy-Nutzer-schuetzen_183287271.html
 Howto solve mysterious WLAN-problems- and break-offs, PC-WELT.de, 01.09.2020 Howto solve mysterious WLAN-problems- and break-offs, PC-WELT.de, 01.09.2020
Oft genug erstaunt Sie Ihr Funknetz mit seltsamen Verhaltensweisen und unergründlichen Fehlern. Dann kommen Sie mit Basis-Tipps fürs WLAN nicht weiter. Wir kümmern uns um die komplexen Probleme und geben Hilfe zur Selbsthilfe.
https://www.pcwelt.de/tipps/Erste-Hilfe-Kasten-fuer-Ihren-PC-WLAN-Probleme-loesen-1257611.html
 You see: Access-rights should be restricted for Apks, wherever possible, while the operating system cares for the rest by itself. Rights, that should not get restricted are already masked off. But with operating systems like Android we once more can not guarantee for the functioning of the smartphone after this! You see: Access-rights should be restricted for Apks, wherever possible, while the operating system cares for the rest by itself. Rights, that should not get restricted are already masked off. But with operating systems like Android we once more can not guarantee for the functioning of the smartphone after this!
 Do the same categorized for Apks! An undo of this can be made in the window appearing each start asking for one-time-access-rights! Such categories are access on files and media, geo location, camera, mikrophone, sensors and further on. Do the same categorized for Apks! An undo of this can be made in the window appearing each start asking for one-time-access-rights! Such categories are access on files and media, geo location, camera, mikrophone, sensors and further on.
 Akku: HB5V1 compatible with smartphones Y3, Y6, Y300, Y360, Y300C, Y500, Y900, T8833, U8833 Akku: HB5V1 compatible with smartphones Y3, Y6, Y300, Y360, Y300C, Y500, Y900, T8833, U8833
HB5V1- Akku from HUAWEI (original), partially improved (more energyzing and lower radiating) HB5V1-Akku from MaXlife (1730 mAh), Extremecells (1730 mAh), BATTERY PACK, PATONA, Powery, AGI 10027, BLUE STAR (1600 mAh), Ascend (1500 mAh, this can prolong (double or longer) your session time, care the device and lower its radiation), vhbw (1500 mAh), AVVISO, ...
3 years warranty
fed black leather case with magnetic closure from IPHORIA
Price (new) for Android-Smartphone Huawei Y360-U61: 79 Euro ( expert Dinslaken year 2014 ), 32 and 16GB SD-card for 6,99 Euro
Rest for free (!) except charging the akku, if there is access by public hotspots or WLAN-Router (office resp. at home), messenger Signal and/or WhatsApp, telephony for free with a addressbook of over 1,5 billion entries in Facebook Lite Messenger, offline navigation and routing: GPS Router Mapsa (with areawise downloadable maps from all over the world)
ATTENTION: The sim card to put in should be loaded; otherwise using the smartphone (downloads, surfing, phoning) might get horrific expensive !
 Howto avoid typical iPhone-failures everyone makes, PC-WELT.de, 05.26.2021 Howto avoid typical iPhone-failures everyone makes, PC-WELT.de, 05.26.2021
https://www.pcwelt.de/ratgeber/Diese-typischen-iPhone-Fehler-unbedingt-vermeiden-11034522.html
Smartphones and Tablets
Apple: Against unitary charging systems, tagesschau.de, 24.01.2020
Das EU-Parlament pocht darauf, dass Hersteller einheitliche Ladesysteme für Handys, Tablets und andere Geräte anbieten. Bei Apple stößt das auf Ablehnung - es würde letztlich Verbrauchern schaden, so der Konzern.
https://www.tagesschau.de/wirtschaft/apple-anschlussbuchsen-101.html
Smartphones for the military, trojaner-info.de, 10.12.2019
Der südkoreanische Technologiekonzern Samsung arbeitet derzeit an einem hochsicheren Mobil-Betriebssystem für das Militär. Dafür arbeitet Samsung mit dem süddeutschen IT- und Beratungsunternehmen blackend zusammen.
https://www.trojaner-info.de/mobile-security/aktuell/smartphones-fuer-das-militaer.html
The most secure Android: Samsung developes a special operating system for the germany military Bundeswehr, CHIP, 10.11.2019
https://www.chip.de/news/Das-sicherste-Android-Samsung-entwickelt-spezielles-Betriebssystem-fuer-deutsche-Bundeswehr_174974516.html
Huawei P30 Pro drops in prices: save 340 Euro, PC-WELT.de, 06.26.2019
https://www.pcwelt.de/produkte/Huawei-P30-Pro-und-P30-die-besten-Angebote-und-Deals-10559718.html
... and do not forget the most friendly HUAWEI customer support:
Huawei Germany, Antwerpener Str. 4, cologne: excellent customer support caring with plenty of time for all customer´s questions around the smartphone ( unlocking etc.) ! (T) 0800/77886633 (Freecall)
"HongmengOS": Huawei´s fast Android-competition - does Huawei provide another operating system soon upon the next Huawei-Handy?, CHIP, 07.05.2019
Video: Huawei´s Android-alternative - all infos and rumors about the new operating system.
After the US-trade embargo against Huawei an U-turn seems to happen - the manufacturer was allowed again to handle with US-companies including Google´s Android. Now there are hints, that Huawei cares a more about the roll-out of thier own operating system, more as guessed, so that Google can be the big looser in this historical matter.
https://www.chip.de/news/Huaweis-Android-Konkurrent-Ein-Trick-soll-fuer-Mega-Performance-sorgen_170149627.html
Huawei promises (again): All remains as it was, PC-WELT.de, 03.07.2019
Android is provided further on - nothing will change! Huawei talks about the actual situation and makes a promise for the future.
https://www.pcwelt.de/news/Huawei-verspricht-erneut-Es-bleibt-alles-beim-Alten-10620958.html
Security-Apps for iOS: Howto protect your iPhone against attacks and spies, CHIP, 02.18.2020
Es macht keinen Sinn, seinen Computer zu schützen und es dann beim Smartphone und Tablet schleifen zu lassen. Denn Angreifern und Datenspionen ist es auch egal, welches Gerät sie attackieren. Apple leistet schon gute Vorarbeit, was die Sicherheit für iPhones und iPads betrifft. Mit den passenden Apps legen Sie noch nach.
https://www.chip.de/news/iPhone-und-iPad-gegen-Angriffe-und-Spione-absichern_102412911.html
New Galaxy S10 + get 600 € for your old handy
Now you can get up to 600 Euro for your old smartphone, if you buy a new Samsung Galaxy S10e, S10 or S10+.
https://www.pcwelt.de/news/Aktion-Neues-Galaxy-S10-kaufen-und-fuer-altes-Smartphone-bis-600-Euro-kassieren-10612961.html
 Aldi sells ozon-sterilizators for handys - how they function, PC-WELT.de, 16.08.2020 Aldi sells ozon-sterilizators for handys - how they function, PC-WELT.de, 16.08.2020
Dieser Ozon-Sterilisator entfernt Bakterien auf Ihrem Handy. Was Aldi Süd da genau verkauft, erklären wir Ihnen im Detail.
https://www.pcwelt.de/news/Smartphone-mit-Ozon-reinigen-Aldi-verkauft-skurriles-Produkt-10862603.html
 Handy loads over night: Avoid such mistakes!, PC-WELT.de, 13.04.2021 Handy loads over night: Avoid such mistakes!, PC-WELT.de, 13.04.2021
Beim Akku-Aufladen in der Nacht und im täglichen Gebrauch des Smartphones kann der Nutzer viele Fehler machen, die sich negativ auf Kapazität und Lebensdauer der Energiezelle auswirken. Wir zeigen Ihnen, worauf Sie achten sollten und stellen neue Schutzmaßnahmen der Hersteller vor.
https://www.pcwelt.de/ratgeber/Handy-laden-ueber-Nacht-Diese-Fehler-sollten-Sie-vermeiden-11010772.html
More about smartphones see News&Links#computer: More about Smartphones
Polaroid announces new handy-photo-printer, PC-WELT.de, 09.12.2019
The new handy photo printer from Polaroid transfers an image directly up from the display of a smartphone onto the ( colorizable photo ) paper.
https://www.pcwelt.de/news/Polaroid-kuendigt-neuen-Handy-Fotodrucker-an-10664929.html
 Upcycling Android Upcycling Android
With free software against electro-scrap
Users can revive their old smartphones thanks free sotfware. The campagne "Upcycling Android" of the Free Software Foundation Europe helps you with it, netzpolitik.org, 11.25.2021
40 Millionen Tonnen Elektronik werden weltweit jedes Jahr weggeworfen (Symbolbild) - Gemeinfrei-ähnlich freigegeben durch unsplash.com Ashkan Forouzani
Es ist Europäische Woche für Abfallvermeidung. Passend zum Thema startet die Free Software Foundation Europe (FSFE) eine neue Kampagne. Unter dem Motto "Upcycling Android" will die Organisation Menschen helfen, ihre Handys länger benutzen zu können - mithilfe von freier Software.
Etwa 1,5 Milliarden Smartphones werden jedes Jahr verkauft. Wie viele andere Elektrogeräte werden sie meist nur wenige Jahre genutzt. Eine Million Tonnen Elektroschrott entstehen geschätzt jedes Jahr allein in Deutschland, weltweit sind es Schätzungen zufolge 40 Millionen. Die verbauten Rohstoffe können teils nur schwer recycelt werden. Zudem ist die Produktion neuer Geräte sehr energieaufwendig. Das Umweltbundesamt empfiehlt daher, Smartphones möglichst lange zu nutzen. Das Benutzen des Smartphones verbrauche im Vergleich zur Herstellung nur wenig Ressourcen.
Der Support endet, die Nutzung geht weiter
Als einen Grund dafür, dass Menschen sich so oft neue Handys kaufen, nennt die FSFE sogenannte Software-Obsoleszenz. Das bedeutet, dass der Support für ältere Software eingestellt wird, obwohl die dazu gehörige Hardware oft noch gut funktioniert. Neuere Software lässt sich auf älteren Geräten hingegen oft nicht installieren. Das führe dazu, dass Nutzer*innen oft vor der Wahl stünden, sich entweder ein neues Handy zu kaufen oder die veraltete, potenziell unsichere Software weiterzunutzen.
Es gibt quelloffene Alternativen zu den Android-Versionen der Smartphonehersteller. Sie werden auch für ältere Geräte noch aktuell gehalten. Um diese Betriebssysteme geht es in der "Upcycling Android"-Kampagne: Die FSFE möchte über Software-Obsoleszenz informieren und Nutzer*innen dabei unterstützen, auf freie mobile Betriebssysteme umzusteigen. Zusätzlich wollen Freiwillige Workshops geben, um Interessierten beim "Upcycling" ihres Handys zu helfen. Eine Einführung zum Upcycling hat die FSFE auf ihrer Website veröffentlicht.
EU soll Software-Obsoleszenz bekämpfen
Die FSFE setzt sich auch auf EU-Ebene für Gesetzesänderungen ein. In einer Stellungnahme zur für das nächste Jahr geplanten Ökodesign-Richtlinie fordert die Organisation ein gesetzlich garantiertes Recht, das Betriebssystem auf Smartphones austauschen zu können. Manche Hersteller erschweren das aktuell gezielt.
Außerdem sollen Hersteller den Code ihrer Software veröffentlichen, sobald sie den Support einstellen. So besteht für andere die Möglichkeit, sie weiter zu pflegen und Sicherheitslücken zu schließen. Das würde es für Nutzer*innen einfacher machen, ihre Geräte länger zu nutzen.
https://fsfe.org/activities/upcyclingandroid/howtoupcycle.de.html#head
https://lineageos.org/
https://netzpolitik.org/2021/upcycling-android-mit-freier-software-gegen-elektroschrott/
Our tip:
 Huawei: HarmonyOS reaches considerable number of users, CHIP, 11.07.2021 Huawei: HarmonyOS reaches considerable number of users, CHIP, 11.07.2021
Huawei hat im Zuge der Handelsrestriktionen durch die US-Regierung HarmonyOS als Ersatz für Googles Android entwickelt. Wie aktuelle Zahlen beweisen, weist das Betriebssystem bereits jetzt beachtliche Nutzerzahlen auf.
Huawei hat nun offiziell bekannt gegeben, dass die Anzahl der HarmonyOS 2.0 Nutzer 30 Millionen erreicht hat. Huawei hat das neue HarmonyOS 2.0 Anfang Juni 2021 vorgestellt und angekündigt, dass fast alle Smartphones des Herstellers auf das neueste Betriebssystem aktualisiert werden können.
Jetzt geht es Schlag auf Schlag. Erst heute morgen konnte man lesen, dass es 25 Millionen HarmonyOS 2.0 Installationen nach nur 1 Monat gab. Nun gibt es den nächsten Meilenstein, weitere 5 Millionen Installationen sind noch einmal dazugekommen.
Weniger als eine Woche nach der Veröffentlichung hat die Zahl der Nutzer, die ein Upgrade auf HarmonyOS 2.0 durchgeführt haben, 10 Millionen überschritten. Nach mehr als einem Monat sind es nun also bereits 30 Millionen HarmonyOS2.0 Nutzer.
Huawei P40 Pro 5G im Amazon-Deal
Huawei: Das sind die Pläne des Unternehmens mit HarmonyOS
Huawei:Viele aktuelle Modelle laufen bereits mit HarmonyOS.
Huawei hat bereits erklärt, dass in diesem Jahr mindestens 300 Millionen Geräte mit HarmonyOS 2.0 ausgestattet werden, von denen 200 Millionen von Huawei und die anderen 100 Millionen von Huawei-Partnern kommen werden.
Huawei hat sich für dieses Jahr noch ein großes Ziel vorgenommen. Bis Ende des Jahres will der Hersteller HarmonyOS 2.0 auf fast allen seinen Geräten installieren.
Der Beitrag HarmonyOS 2.0 hat nun bereits 30 Millionen Nutzer erschien zuerst bei schmidtisblog.de und wurde von CHIP-Autoren um weitere Informationen ergänzt.
Diese Smartphone-Themen könnten Sie auch interessieren
Handyvergleich: Das sind die besten Smartphones
https://www.chip.de/news/HarmonyOS-mit-guten-Nutzerzahlen_183704757.html
 <Certified smartphones for less than 200 Euro: <Certified smartphones for less than 200 Euro:
Xiaomi Poco m5 with 128 GB internal memoryr (year 2022), MIUI 13 (possible upgrade to 14), Android 12
Xiaomi Poco m6 PRO with 256 internal memory (year: 2024), with some improvements and innovations: Xiaomi HyperOS (instead of MIUI), Android 14, improved camera, TÜV Rheinland certified bluelight filltering displayer, improved Akku (fast load within less than one hour), USB-port with latch of USB-plugs
-
Computer system: Power-saving (total < 45W)
-
mouseclick-fast
-
lifetime durable
-
(quit) for free (total less than 200 Euro including computer tower and TFT)
-
all Linux, Win7 tested, brilliant Display all OpenGL und SDL (fc, rosa, mga, mdv)
"Without words: just hot"
 Computer-Tower Computer-Tower
Still functioning today: Computer-Tower 4Q001342, order nr. 37701136
Brightness×Height×Depth: 180×355×390 mm
2 × 3 1/2 and 2 × 5 1/4 Zoll shafts, material: metal, opening metal front left and right, hand-screwable cross-screws backside, color: white or black
standarized Power-Buttom, RESET, 2 LED: green and orange
Mini-ATX (also suitable for other ATX-Net-adapter)
Pollin.de, Price: 4,95 € (Stand 2013)
Lifetime-Hardware over lifetime-hardware is all you see in this data sheed: solid and stable mainboard at lowest costs tested by Gooken :
 Mouseclick-fast All-On-One-Mainboard 19W Mouseclick-fast All-On-One-Mainboard 19W
Crashfree allrounder still functioning today: super powersaving, 17×17 cm small factorized ASUS-Mini-ITX -220 mit 1,2 GHZ - Celeron 220 ( Single core Intel Celeron 220 (-UP-) arch: Conroe rev.1 - this one reacts also fast as by mouseclick) incl. extrem silent cooler onboard with BIOS internal overheat protection (TM), year 2009 - we use it mouseclick-fast up to know (and are going to report, if we don´t anymore):
BIOS: ASUS Mini-ITX-220 year 2009/2010 socked (this one is a prevailed, well spare-parted BIOS for example from bios-chip24.com/Mainboard and biosflash.com for less than 10 €), 8Mb Flash ROM, AMI BIOS Ver. 0216 9/22/2009 absolute CrashFree durable BIOS 3, EZFlash 2 (for cases like blackscreen, mointor failouts, any problems and troubles): by pressing the function key like F1 or the bios-setup with a flash-file type ROM from DVD, memory stick, boot-partition of the harddrive or SSD, ASUS AI NET2, PnP, DMI v2.0, WIM 2.0, SMBIOS 2.5, ACPI v2.0a, SATA 3Gb/s (SATA - Port:
SATA I, SATA II, SATA III)
tested: powersaving 19 Watt and mouseclick-fast on our SSD-based "Universal-Linux",; with Ethernet-LAN-, 3D-Sound- and full directrendering-, OpenGL- and SDL- graphic-support
crashfree: mostly independent from temperature, amount of daily system-restarts and connected devices and so on
SSE2 support
Windows 7 ready, Windows 10 and Linux ready (we tested "Universal Linux" out of Enterprise Linux RHEL/CentOS el7, el6, Rosa2014.1, OpenSuSE, mga, Slackware based on mdv 2010.2.)
Form factor: 170mm×170mm
Chipset: 945GC/ICH7 express Green ASUS RoH8-Compliant with ICH7 S-ATA-Controller
power-saving 19 Watt only
Intel Celeron 220 with super silent cooler 25,3 db (max. 27.5 dBA) (this supersilent cooler is a suprising small tiny model, but working reliable over all seasons with +-40 °C without any problems and without doing any harms!, Gooken)
Manufacturer: GenuineIntel
Model name: Intel(R) Celeron(R) CPU 220@1.20GHz
CPUID-Familie: 6
Modell: 22
Modell-Stepping: 1
CPUID-Ebene: 10
Performance
Frequency (MHz): 1197.678
Cache size: 512 KB
Bogomips: 2395.35
More information
Flags: fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss tm pbe syscall nx lm constant_tsc up arch_perfmon pebs bts rep_good nopl aperfmperf pni dtes64 monitor ds_cpl tm2 ssse3 cx16 xtpr pdcm lahf_lm dts
Write-protection: Yes
Processor Information
Model: Intel Celeron 220, 1.20 GHz
Package: 1 Core
Processor Caches
L1 code cache, 32 KB
L1 data cache, 32 KB
L2 unified cache, 512 KB
Processor Features
64bit 64-bit instructions
simd SIMD instructions
[x86] -- x86-specific features --
ac Alignment Check
cpuid CPU Identificaion
fpu Floating Point Unit On-Chip
vme Virtual 8086 Mode Enhancements
de Debugging Extensions
pse Page Size Extension
tsc Time Stamp Counter
msr Model Specific Registers RDMSR and WRMSR Instructions
pae Physical Address Extension
mce Machine Check Exception
cx8 CMPCXHG8B Instruction
apic APIC On-Chip
sep SYSENTER and SYSEXIT Instructions
mtrr Memory Type Range Registers
pge PTE Global Bit
mca Machine Check Architecture
cmov Conditional Moves
pat Page Attribute Table
pse36 36-Bit Page Size Extension
clflush CLFLUSH Instruction
ds Debug Store
acpi Thermal Monitor and Software Controlled Clock Facilities
fxsr Supports FXSAVE/FXSTOR instructions
ss Self Snoop
pbe Pending Break Enable
mmx MMX Technology
sse SSE Technology
sse2 SSE2 Technology
sse3 SSE3 Technology (Prescott New Instructions)
ssse3 SSSE3 Technology (Merom New Instructions)
lm Long Mode (64-bit capable)
lahf_lm LAHF/SAHF Supported in 64-bit mode
tm Thermal Monitor
tm2 Thermal Monitor 2
nx No eXecute (AMD NX) / Execute Disable (Intel XD)
dtes64 64-bit DS Area
monitor MONITOR/MWAIT
ds_cpl CPL Qualified Debug Store
cx16 Supports CMPCXHG16B Instruction
xtpr xTPR Update Conrol
pdcm Perfmon and Debug Capability
Chassis Intrusion Detection
Virusprotected and Crashfree BIOS 3, socked, EZ-flash2 (direct from mainboard-DVD or USB)
Prefer BIOS setting: fixed mode, 128 MB for graphics (northbridge)
All Linux games, even all OpenGL and SSL-games are ready to play like many, many Windows-Games too:
Onboard Graphic Chip: i945G, INTEL GMA 950, 82945G/GZ Integrated Graphics Controller, 2048 × max. 224MB RAM, Direct Rendering, OpenGL- and SDL-support, resolution 4096× 4096 pixel ×32bpp; max., 2048×1536 pixel (we chose 1366×768 pixe×32bpp@59 Hz Generally the screen resolution should be adjusted to get a brilliant display, that means one with a clean and natural display of the symbols and chosen fonts; it might be the best to choose "automatic" for the screen resolution out of MCC -> Hardware "konfigure the graphic server ")
 To be careful, use some contact spray on its pins resp. ports to care for good working lifetime! To be careful, use some contact spray on its pins resp. ports to care for good working lifetime!
RAM (fast and lifetime): two sockets, 2× 240 Pin DIMM socket, support of unbuffered non-ECC OVL, at least recommended: 2×2 GB DDR2-RAM (667, am besten PC2-5300, 667 Mhz branded) 533 Mhz (or above) FSB dual channel, max. 8GB, RAM is NOT (!) included in this ariticle, price (2 × 2 GB): around 5 up to 20 Euro
Graphic card ITX mouseclick-fast, set in BIOS, Northbridge to DVMT64, DVMT128, DVMTinfinite or COMBO mode. We´d like to recommend DVMT128 MB.
Onboard Sound Chip: VIA VT 1705 6-channel-HD-Azalia-audio CODEC: high-end sound-system
Onboard Gigabit-Lan-Chip (all functioning since mdv2010) and LAN-BIOS
it87: Found IT8720F chip at 0x290, revision 8: coretemp (lm_sensors / sensord) (mousecklick fast even by daylight: we would kept these unneeded modules still deactivated for more speed and security)
ACPI 2.0 for all (Windows and Linux) suspend mode, for hibernate 2 GB SWAP-partition is needed and the ACPI 2.0 wihtin BIOS should be set. All USB-devices like memory-sticks should be plugged out (umount).
AI Overclocking (CPU): auto (default) or manually up to stable overclocking: Vcore (CPU-frequency) 133 up to 140
BIOS-Data- including virus protection: ROOT-Password protection and USER-ACCESS-LEVEL by BIOS-Setup, section security: Full Access, No-Access and View Only (we recommend "ViewOnly" or "No-Access")
USB-Boot-Support and boot from other external media: Set security within the BIOS-Setup, set "full BIOS access", restart and press the key F8. If the boot should be done with the SSD or harddisc again, set "full BIOS access" back to "no access".
TPM: Trusted Platform Module: user/not-user-configurable
Max CPUID Value Limit
CPU TM function: CPU-Thermal-Monitor (TM) function, a CPU-overheat-protection reducing frequency and voltage in the case of overheat.
Execute-Disable-Bit: No-Execution Page Protection Technology, disabled forces the XD feature flag to always return zero (0), enabled enables this option..
1×PCI, 2 × S-ATA II 6Gb/s NM10/Ich7, 6×USB 2.0, 2×PS/2, 1×COM, 1×Ethernet/LAN, 3×audio
3 years limited warranty
manual selection of boot devices including booting from USB-stick: F8-key
Accessories
User´s manual
1 × I/O Shield
1 × SATA cable
Support Disc
Drivers
ASUS PC Probe II
Anti-virus software (OEM version)
ASUS Update
English User´s Manual
TÜV Rheinland "Geprüfte Bauart"
Certified by FC Federal Communication Commission U.S.A. and EC Declaration of Confomity 2009
EC-conformity: 7. April 2009, FCC part 2 section 2, 1077(a), 2004/108/EC-EMC directive, EN 55022 2006, EN 61000-3-2-2006, 2006/95/EC-LVD-directive, CE
CE
"AUStest" by Gooken (any power switchings on to off, CPU, cooler, USB-2.0-ports, DDR-2-RAM-modul-extension, PCI, BIOS, IGP (intergrated grahic chip/GPU/northbridge)), integrated sound chip (southbridge), integrated ethernet chip, PCI, Elkos etc.: all doing fine year 2010 up to year 2020 and longer connected with net adapter SLA 500W
The PC-loudspeaker cable for many mainboards like this one should not be used because of possible short circuits, that can also enlight the net adapter above the board! You do not need this cable for this board.
FC, but In some seldom cases, the board can be affected by frequencies like from some handies.
Especially the internal graphic chip should be protected against moisture by a piece of chalk, that has to be put into the tower.
This lifetime-mainboard is almost free of interferences, but interferences still might appear. Then just power the computer on and off or press the reset-key on the tower! Do only reset the BIOS by belonging Jumper, if the computer does not start after powering on, same for its flashing ! And all devices like USB or PCI should be connected well.
The integrated BIOS-Etheneret-LAN-chip and eventually the superfluos sensor-chip should be deactivated in the Bios resp. per lm-sensors ( pregiven by default), as they might consist of parts of TCPAs. Anyhow you do not need such-chips activated!
Censor-chips in hardware + Win2000 vs. XP, trojaner-board.de
Hello, as much as I got informed, TCPA-chips are parts of computer mainboardds: 1. They do exist...
http://www.trojaner-board.de/5841-zensur-chips-hardware-win2000-vs-xp.html
... I doubt, that those contentious technology provides the end user any more security...
http://www.trojaner-board.de/5845-tcpa-unabhaengige-experten-einig.html
ASUS Computer GmbH
Tel. +49-1805-010923
Harkort Str. 21-23
40880 Ratingen
Price ASUS ITX-220: 29,95 € (year 2013, Pollin.de, E580002, Barcode Nr. 15G062191001, order number: 701197
https://www.pollin.de/shop/dt/MjA4ODkyOTk-/Computer_und_Zubehoer/Hardware/Mainboards_Mainboard_Bundles/Mini_ITX_Mainboard_ASUS_ITX_220_Intel_Celeron_220.html )
https://www.pollin.de/shop/dt/MjA4ODkyOTk-/Computer_Informationstechnik/Hardware/Mainboards_Mainboard_Bundles/Mini_ITX_Mainboard_ASUS_ITX_220_Intel_Celeron_220.html
Scope of delivery
mainboard
SATA-cable
Blende
Manual
Driver-CD
Product data-sheed, click here
>cpuid
CPU 0 (already onboard, mouseclick-fast):
vendor_id = "GenuineIntel"
version information (1/eax):
processor type = primary processor (0)
family = Intel Pentium Pro/II/III/Celeron/Core/Core 2/Atom, AMD Athlon/Duron, Cyrix M2, VIA C3 (6)
model = 0x6 (6)
stepping id = 0x1 (1)
extended family = 0x0 (0)
extended model = 0x1 (1)
(simple synth) = Intel Core 2 Duo Mobile (Merom A1) / Celeron 200/400/500 (Conroe-L/Merom-L A1) / Celeron M (Merom-L A1), 65nm
miscellaneous (1/ebx):
process local APIC physical ID = 0x0 (0)
cpu count = 0x1 (1)
CLFLUSH line size = 0x8 (8)
brand index = 0x0 (0)
brand id = 0x00 (0): unknown
feature information (1/edx):
x87 FPU on chip = true
virtual-8086 mode enhancement = true
debugging extensions = true
page size extensions = true
time stamp counter = true
RDMSR and WRMSR support = true
physical address extensions = true
machine check exception = true
CMPXCHG8B inst. = true
APIC on chip = true
SYSENTER and SYSEXIT = true
memory type range registers = true
PTE global bit = true
machine check architecture = true
conditional move/compare instruction = true
page attribute table = true
page size extension = true
processor serial number = false
CLFLUSH instruction = true
debug store = true
thermal monitor and clock ctrl = true
MMX Technology = true
FXSAVE/FXRSTOR = true
SSE extensions = true
SSE2 extensions = true
self snoop = true
hyper-threading / multi-core supported = false
therm. monitor = true
IA64 = false
pending break event = true
feature information (1/ecx):
PNI/SSE3: Prescott New Instructions = true
PCLMULDQ instruction = false
64-bit debug store = true
MONITOR/MWAIT = true
CPL-qualified debug store = true
VMX: virtual machine extensions = false
SMX: safer mode extensions = false
Enhanced Intel SpeedStep Technology = false
thermal monitor 2 = true
SSSE3 extensions = true
context ID: adaptive or shared L1 data = false
FMA instruction = false
CMPXCHG16B instruction = true
xTPR disable = true
perfmon and debug = true
process context identifiers = false
direct cache access = false
SSE4.1 extensions = false
SSE4.2 extensions = false
extended xAPIC support = false
MOVBE instruction = false
POPCNT instruction = false
time stamp counter deadline = false
AES instruction = false
XSAVE/XSTOR states = false
OS-enabled XSAVE/XSTOR = false
AVX: advanced vector extensions = false
F16C half-precision convert instruction = false
RDRAND instruction = false
hypervisor guest status = false
cache and TLB information (2):
0xb1: instruction TLB: 2M/4M, 4-way, 4/8 entries
0xb0: instruction TLB: 4K, 4-way, 128 entries
0x05: data TLB: 4M pages, 4-way, 32 entries
0xf0: 64 byte prefetching
0x57: L1 data TLB: 4K pages, 4-way, 16 entries
0x56: L1 data TLB: 4M pages, 4-way, 16 entries
0x7f: L2 cache: 512K, 2-way, 64 byte lines
0x30: L1 cache: 32K, 8-way, 64 byte lines
0xb4: data TLB: 4K pages, 4-way, 256 entries
0x2c: L1 data cache: 32K, 8-way, 64 byte lines
processor serial number: 0001-0661-0000-0000-0000-0000
deterministic cache parameters (4):
--- cache 0 ---
cache type = data cache (1)
cache level = 0x1 (1)
self-initializing cache level = true
fully associative cache = false
extra threads sharing this cache = 0x0 (0)
extra processor cores on this die = 0x0 (0)
system coherency line size = 0x3f (63)
physical line partitions = 0x0 (0)
ways of associativity = 0x7 (7)
ways of associativity = 0x1 (1)
WBINVD/INVD behavior on lower caches = true
inclusive to lower caches = false
complex cache indexing = false
number of sets - 1 (s) = 63
--- cache 1 ---
cache type = instruction cache (2)
cache level = 0x1 (1)
self-initializing cache level = true
fully associative cache = false
extra threads sharing this cache = 0x0 (0)
extra processor cores on this die = 0x0 (0)
system coherency line size = 0x3f (63)
physical line partitions = 0x0 (0)
ways of associativity = 0x7 (7)
ways of associativity = 0x1 (1)
WBINVD/INVD behavior on lower caches = true
inclusive to lower caches = false
complex cache indexing = false
number of sets - 1 (s) = 63
--- cache 2 ---
cache type = unified cache (3)
cache level = 0x2 (2)
self-initializing cache level = true
fully associative cache = false
extra threads sharing this cache = 0x0 (0)
extra processor cores on this die = 0x0 (0)
system coherency line size = 0x3f (63)
physical line partitions = 0x0 (0)
ways of associativity = 0x1 (1)
ways of associativity = 0x1 (1)
WBINVD/INVD behavior on lower caches = true
inclusive to lower caches = false
complex cache indexing = false
number of sets - 1 (s) = 4095
MONITOR/MWAIT (5):
smallest monitor-line size (bytes) = 0x40 (64)
largest monitor-line size (bytes) = 0x40 (64)
enum of Monitor-MWAIT exts supported = true
supports intrs as break-event for MWAIT = true
number of C0 sub C-states using MWAIT = 0x0 (0)
number of C1 sub C-states using MWAIT = 0x1 (1)
number of C2 sub C-states using MWAIT = 0x0 (0)
number of C3 sub C-states using MWAIT = 0x0 (0)
number of C4 sub C-states using MWAIT = 0x0 (0)
number of C5 sub C-states using MWAIT = 0x0 (0)
number of C6 sub C-states using MWAIT = 0x0 (0)
number of C7 sub C-states using MWAIT = 0x0 (0)
Thermal and Power Management Features (6):
digital thermometer = true
Intel Turbo Boost Technology = false
ARAT always running APIC timer = false
PLN power limit notification = false
ECMD extended clock modulation duty = false
PTM package thermal management = false
HWP base registers = false
HWP notification = false
HWP activity window = false
HWP energy performance preference = false
HWP package level request = false
HDC base registers = false
digital thermometer thresholds = 0x2 (2)
ACNT/MCNT supported performance measure = true
ACNT2 available = false
performance-energy bias capability = false
extended feature flags (7):
FSGSBASE instructions = false
IA32_TSC_ADJUST MSR supported = false
SGX: Software Guard Extensions supported = false
BMI instruction = false
HLE hardware lock elision = false
AVX2: advanced vector extensions 2 = false
FDP_EXCPTN_ONLY = false
SMEP supervisor mode exec protection = false
BMI2 instructions = false
enhanced REP MOVSB/STOSB = false
INVPCID instruction = false
RTM: restricted transactional memory = false
QM: quality of service monitoring = false
deprecated FPU CS/DS = false
intel memory protection extensions = false
PQE: platform quality of service enforce = false
AVX512F: AVX-512 foundation instructions = false
AVX512DQ: double &quadword instructions = false
RDSEED instruction = false
ADX instructions = false
SMAP: supervisor mode access prevention = false
AVX512IFMA: fused multiply add = false
CLFLUSHOPT instruction = false
CLWB instruction = false
Intel processor trace = false
AVX512PF: prefetch instructions = false
AVX512ER: exponent &reciprocal instrs = false
AVX512CD: conflict detection instrs = false
SHA instructions = false
AVX512BW: byte &word instructions = false
AVX512VL: vector length = false
PREFETCHWT1 = false
AVX512VBMI: vector byte manipulation = false
UMIP: user-mode instruction prevention = false
PKU protection keys for user-mode = false
OSPKE CR4.PKE and RDPKRU/WRPKRU = false
BNDLDX/BNDSTX MAWAU value in 64-bit mode = 0x0 (0)
RDPID: read processor D supported = false
SGX_LC: SGX launch config supported = false
AVX512_4VNNIW: neural network instrs = false
AVX512_4FMAPS: multiply acc single prec = false
Direct Cache Access Parameters (9):
PLATFORM_DCA_CAP MSR bits = 0
Architecture Performance Monitoring Features (0xa/eax):
version ID = 0x2 (2)
number of counters per logical processor = 0x2 (2)
bit width of counter = 0x28 (40)
length of EBX bit vector = 0x7 (7)
Architecture Performance Monitoring Features (0xa/ebx):
core cycle event not available = false
instruction retired event not available = false
reference cycles event not available = false
last-level cache ref event not available = false
last-level cache miss event not avail = false
branch inst retired event not available = false
branch mispred retired event not avail = false
Architecture Performance Monitoring Features (0xa/edx):
number of fixed counters = 0x0 (0)
bit width of fixed counters = 0x0 (0)
extended feature flags (0x80000001/edx):
SYSCALL and SYSRET instructions = true
execution disable = true
1-GB large page support = false
RDTSCP = false
64-bit extensions technology available = true
Intel feature flags (0x80000001/ecx):
LAHF/SAHF supported in 64-bit mode = true
LZCNT advanced bit manipulation = false
3DNow! PREFETCH/PREFETCHW instructions = false
brand = "Intel(R) Celeron(R) CPU 220 @ 1.20GHz"
L1 TLB/cache information: 2M/4M pages &L1 TLB (0x80000005/eax):
instruction # entries = 0x0 (0)
instruction associativity = 0x0 (0)
data # entries = 0x0 (0)
data associativity = 0x0 (0)
L1 TLB/cache information: 4K pages &L1 TLB (0x80000005/ebx):
instruction # entries = 0x0 (0)
instruction associativity = 0x0 (0)
data # entries = 0x0 (0)
data associativity = 0x0 (0)
L1 data cache information (0x80000005/ecx):
line size (bytes) = 0x0 (0)
lines per tag = 0x0 (0)
associativity = 0x0 (0)
size (KB) = 0x0 (0)
L1 instruction cache information (0x80000005/edx):
line size (bytes) = 0x0 (0)
lines per tag = 0x0 (0)
associativity = 0x0 (0)
size (KB) = 0x0 (0)
L2 TLB/cache information: 2M/4M pages &L2 TLB (0x80000006/eax):
instruction # entries = 0x0 (0)
instruction associativity = L2 off (0)
data # entries = 0x0 (0)
data associativity = L2 off (0)
L2 TLB/cache information: 4K pages &L2 TLB (0x80000006/ebx):
instruction # entries = 0x0 (0)
instruction associativity = L2 off (0)
data # entries = 0x0 (0)
data associativity = L2 off (0)
L2 unified cache information (0x80000006/ecx):
line size (bytes) = 0x40 (64)
lines per tag = 0x0 (0)
associativity = 2-way (2)
size (KB) = 0x200 (512)
L3 cache information (0x80000006/edx):
line size (bytes) = 0x0 (0)
lines per tag = 0x0 (0)
associativity = L2 off (0)
size (in 512KB units) = 0x0 (0)
Advanced Power Management Features (0x80000007/edx):
temperature sensing diode = false
frequency ID (FID) control = false
voltage ID (VID) control = false
thermal trip (TTP) = false
thermal monitor (TM) = false
software thermal control (STC) = false
100 MHz multiplier control = false
hardware P-State control = false
TscInvariant = false
Physical Address and Linear Address Size (0x80000008/eax):
maximum physical address bits = 0x24 (36)
maximum linear (virtual) address bits = 0x30 (48)
maximum guest physical address bits = 0x0 (0)
Logical CPU cores (0x80000008/ecx):
number of CPU cores - 1 = 0x0 (0)
ApicIdCoreIdSize = 0x0 (0)
(multi-processing synth): none
(multi-processing method): Intel leaf 1/4
(APIC widths synth): CORE_width=0 SMT_width=0
(APIC synth): PKG_ID=0 CORE_ID=0 SMT_ID=0
(synth) = Intel Celeron M (Merom-L A1), 65nm
/etc/X11/xorg.conf mouseclick-fast:
# File generated by XFdrake (rev )
# **********************************************************************
# Refer to the xorg.conf man page for details about the format of
# this file.
# **********************************************************************
Section "ServerFlags"
Option "DontZap" "False" # disable Ctr Al BS (server abort)
AllowMouseOpenFail # allows the server to start up even if the mouse does not work
#DontZoom # disable Ctrl Alt KP_+ /KP_- (resolution switching)
EndSection
Section "Module"
Load "dbe" # Double-Buffering Extension
Load "v4l" # Video for Linux
Load "extmod"
Load "glx" # 3D layer
Load "dri" # direct rendering
Load "GLcore"
Load "bitmap"
Load "freetype"
Load "type1"
EndSection
Section "Monitor"
Identifier "monitor1"
HorizSync 30-80
VertRefresh 55-65
# Monitor supported modeline (60.0 Hz vsync, 47.7 kHz hsync, ratio 16/9, 84 dpi)
ModeLine "1360x768" 85.5 1360 1424 1536 1792 768 771 777 795 +hsync +vsync
# Monitor preferred modeline (59.8 Hz vsync, 47.7 kHz hsync, ratio 16/9, 84 dpi)
ModeLine "1366×768" 85.5 1366 1436 1579 1792 768 771 774 798 +hsync +vsync
# TV fullscreen mode or DVD fullscreen output.
# 768x576 @ 79 Hz, 50 kHz hsync
ModeLine "768x576" 50.00 768 832 846 1000 576 590 595 630
# 768x576 @ 100 Hz, 61.6 kHz hsync
ModeLine "768x576" 63.07 768 800 960 1024 576 578 590 616
# modeline generated by gtf(1) [handled by XFdrake]
ModeLine "1368x768_120" 185.67 1368 1472 1624 1880 768 769 772 823 -HSync +Vsync
# ...
EndSection
Section "Device"
Identifier "device1"
VendorName "Intel Corporation"
BoardName "Intel 810 and later"
Driver "intel"
Option "AccelMethod" "uxa"
Option "DPMS"
EndSection
Section "Screen"
Identifier "screen1"
Device "device1"
Monitor "monitor1"
DefaultColorDepth 24
Subsection "Display"
Depth 8
Modes "1366×768" "1360x765" "1280x720"
EndSubsection
Subsection "Display"
Depth 15
Modes "1366×768" "1360x765" "1280x720"
EndSubsection
Subsection "Display"
Depth 16
Modes "1366×768" "1360x765" "1280x720"
EndSubsection
Subsection "Display"
Depth 24
Modes "1366×768" "1360x765" "1280x720"
EndSubsection
EndSection
Section "ServerLayout"
Identifier "layout1"
Screen "screen1"
EndSection
Section "InputDevice"
Identifier "Mymouse1"
Driver "mouse"
# Option "Device" "/dev/ttyS0"
Option "Protocol" "ImPS/2"
# Option "Device" "/dev/psaux"
# Option "Device" "/dev/ttyS0"
Option "Device" "/dev/input/mice"
Option "Emulate3Buttons" "true"
Option "CorePointer"
# Option "Protocol" "Auto"
# Option "Protocol" "ExplorerPS/2"
# Option "Protocol" "auto"
Option "ZAxisMapping" "4 5"
EndSection
RAM (so you still need DDR-2 RAM for this mainboard)
1GB SAMSUNG RAM DDR-2 800Mhz PC2-6400 240 pin, new, we recommend: 2× 2 GB DDR-2 667 Mhz same modell manufacurer
price: daily fluctuation (actually 1 GB about 10 Euro, new: about 15 Euro )
To achieve good performance, look out for the intern cables far away from the platine.
 driconf: configuration of the GPU and 3D-acceleration in detail for experts. All green buttons can be activated, one stands for fast texture compression, but
BE CAREFUL, SEVERAL GAMES MIGHT NOT RUN ANYMORE, if early-z compression is set to ON / VORSICHT: EINIGE GAMES STARTEN NICHT MEHR, wird early-z-compression auf ON gesetzt: driconf: configuration of the GPU and 3D-acceleration in detail for experts. All green buttons can be activated, one stands for fast texture compression, but
BE CAREFUL, SEVERAL GAMES MIGHT NOT RUN ANYMORE, if early-z compression is set to ON / VORSICHT: EINIGE GAMES STARTEN NICHT MEHR, wird early-z-compression auf ON gesetzt:
Synchronisation mit der vertikalen Bildwiederholung: Immer mit der Bildwiederholung synchroniseren, Anwenung w&aumL;hlt das minimale Bildintervall: ON
Buffer object reuse: Enable reuse of all sizes of buffer objects: ON
Enable early Z in classic mode: OFF # not all games might run anymore, if set to ON
S3TC texture compression in all cases: ON
Aktivierung der GMA 950 für alle Punkte mit Buttom, darunter beschleunigende Textur-Komprimierung.
MCC -> Graphic-card configuration -> Options: Use XAA instead of ... (improved rendering and composite): on, tranlucency: on
Systemsettings: desktop-effects: on (activated), composite-type: OpenGL, direct rendering: on, VSYNC: on
fps ("Universal-Linux" based on mentioned hardware): 50-60 fps
ITX-220 mouseclick-fast: sys_basher, tuned, ktuned, lm_sensor-sensord and lm_sensors (mdv2010, el6):
Such service/daemon helps to find out more mainboard-characteristics to intergrate by belonging kernel-modules to load (but notice, that the computer runs even more secure and mouseclick-fast without the following and following modules started):
.
root@localhost:user # sh /etc/init.d/sys_basher.init start
root@localhost:user # sh /etc/init.d/tuned start
root@localhost:user # sh /etc/init.d/ktuned start
root@localhost:user # sh /etc/init.d/sensord start
root@localhost:user # sh /etc/init.d/lm_sensors start
Starting lm_sensors: not configured, run sensors-detect [WARNUNG]
root@localhost:secret # sensors-detect
# sensors-detect revision 5818 (2010-01-18 17:22:07 +0100)
# System: System manufacturer System Product Name
# Board: ASUSTeK Computer INC. ITX-220
This program will help you determine which kernel modules you need to load to use lm_sensors most effectively. It is generally safe and recommended to accept the default answers to all questions, unless you know what you´re doing.
Some south bridges, CPUs or memory controllers contain embedded sensors.
Do you want to scan for them? This is totally safe. (YES/no): YES
Silicon Integrated Systems SIS5595... No
VIA VT82C686 Integrated Sensors... No
VIA VT8231 Integrated Sensors... No
AMD K8 thermal sensors... No
AMD Family 10h thermal sensors... No
AMD Family 11h thermal sensors... No
Intel Core family thermal sensor... Success!
(driver coretemp)
Intel Atom thermal sensor... No
Intel AMB FB-DIMM thermal sensor... No
VIA C7 thermal sensor... No
VIA Nano thermal sensor... No
Some Super I/O chips contain embedded sensors. We have to write to standard I/O ports to probe them. This is usually safe.
Do you want to scan for Super I/O sensors? (YES/no): YES
Probing for Super-I/O at 0x2e/0x2f
Trying family National Semiconductor... No
Trying family SMSC... No
Trying family VIA/Winbond/Nuvoton/Fintek... No
Trying family ITE... Yes
Found ITE IT8720F Super IO Sensors Success!
(address 0x290, driver it87)
Probing for Super-I/O at 0x4e/0x4f
Trying family National Semiconductor... No
Trying family SMSC... No
Trying family VIA/Winbond/Nuvoton/Fintek... No
Trying family ITE... No
Some systems (mainly servers) implement IPMI, a set of common interfaces through which system health data may be retrieved, amongst other things. We first try to get the information from SMBIOS. If we don´t find it there, we have to read from arbitrary I/O ports to probe for such interfaces. This is normally safe.
Do you want to scan for IPMI interfaces? (YES/no): YES
Probing for IPMI BMC KCS at 0xca0... No
Probing for IPMI BMC SMIC at 0xca8... No
Some hardware monitoring chips are accessible through the ISA I/O ports.
We have to write to arbitrary I/O ports to probe them. This is usually safe though. Yes, you do have ISA I/O ports even if you do not have any ISA slots!
Do you want to scan the ISA I/O ports? (yes/NO): YES
Probing for National Semiconductor LM78 at 0x290... No
Probing for National Semiconductor LM79 at 0x290... No
Probing for Winbond W83781D at 0x290... No
Probing for Winbond W83782D at 0x290... No
Lastly, we can probe the I2C/SMBus adapters for connected hardware monitoring devices. This is the most risky part, and while it works reasonably well on most systems, it has been reported to cause trouble
on some systems.
Do you want to probe the I2C/SMBus adapters now? (YES/no): YES
Using driver i2c-i801 for device 0000:00:1f.3: Intel 82801G ICH7
Module i2c-dev loaded successfully.
Next adapter: i915 gmbus disabled (i2c-0)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 gmbus ssc (i2c-1)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 GPIOB (i2c-2)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 gmbus vga (i2c-3)
Do you want to scan it? (YES/no/selectively): YES
Client found at address 0x50
Probing for Analog Devices ADM1033... No
Probing for Analog Devices ADM1034... No
Probing for SPD EEPROM... No
Probing for EDID EEPROM... Yes
(confidence 8, not a hardware monitoring chip)
Client found at address 0x58
Probing for Analog Devices ADT7462... No
Probing for Andigilog aSC7512... No
Next adapter: i915 GPIOA (i2c-4)
Do you want to scan it? (YES/no/selectively): YES
Client found at address 0x50
Probing for Analog Devices ADM1033... No
Probing for Analog Devices ADM1034... No
Probing for SPD EEPROM... No
Probing for EDID EEPROM... Yes
(confidence 8, not a hardware monitoring chip)
Client found at address 0x58
Probing for Analog Devices ADT7462... No
Probing for Andigilog aSC7512... No
Next adapter: i915 gmbus panel (i2c-5)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 GPIOC (i2c-6)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 gmbus dpc (i2c-7)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 GPIOD (i2c-8)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 gmbus dpb (i2c-9)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 GPIOE (i2c-10)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 gmbus reserved (i2c-11)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 gmbus dpd (i2c-12)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: i915 GPIOF (i2c-13)
Do you want to scan it? (YES/no/selectively): YES
Next adapter: SMBus I801 adapter at 0400 (i2c-14)
Do you want to scan it? (YES/no/selectively): YES
Client found at address 0x50
Probing for Analog Devices ADM1033... No
Probing for Analog Devices ADM1034... No
Probing for SPD EEPROM... Yes
(confidence 8, not a hardware monitoring chip)
Probing for EDID EEPROM... No
Client found at address 0x52
Probing for Analog Devices ADM1033... No
Probing for Analog Devices ADM1034... No
Probing for SPD EEPROM... Yes
(confidence 8, not a hardware monitoring chip)
Now follows a summary of the probes I have just done.
Just press ENTER to continue: YES
Driver it87:
* ISA bus, address 0x290
Chip ITE IT8720F Super IO Sensors (confidence: 9)
Driver coretemp:
* Chip Intel Core family thermal sensor (confidence: 9)
Do you want to overwrite /etc/sysconfig/lm_sensors? (YES/no): YES
no PCIe, no AGP, no USB 3.0: without!
Notice, that we would keep all those listed modules still deactivated, as they are not needed for ITX-220 and might decrease working-speed and lower the security level.
alternatively to ASUS ITX-220 including INTEL Celeron:
alternativ zu ASUS ITX-220 einschließlich Intel® Celeron:
Intel D201GLY Mini-ITX Mainboard (mit Celeron 1.33Ghz CPU)
Neuware ! Lieferung nur Board, kein Zubehör !
Das Intel® PC-Mainboard D201GLY stellt eine innovative Lösung für PCs dar. Ein Inte® Celeron® Proceessor and grafik chip are already integrated.
It consumpts less power and causes a reduces noise.
Zum Betrieb wird ein P4-Anschlusskabel benötigt bzw. Netzteil mit P4-Stecker
Form Factor uATX (6.75 inches by 6.75 inches [171.45 millimeters by 171.45 millimeters]) (ITX compatible)
Processor Integrated IntelTreg; Celeron® 215 processor (1.33 Ghz) with a 533 MHz system bus
Memory One 240-pin DDR2 SDRAM Dual Inline Memory Module (DIMM) sockets
Support for DDR2 (667) 533 MHz and DDR2 400 MHz DIMMs
Support for up to 1 GB of system memory
Chipset SiS* SiS662
Audio ADI* AD1888 audio codec
Video Integrated SiS Mirage* 1 graphic engine
I/O Control Winbond* W83627DHG-B based Legacy I/O controller for hardware management, VGA, serial, parallel, and PS/2* ports
LAN Support 10/100 Mbits/sec LAN subsystem using the Broadcom* LAN adapter device
Peripheral Interfaces Six USB 2.0 ports
One parallel ATA IDE interface with UDMA 33, ATA-66/100/133 support
One S-Video output port (optional)
One serial port
One parallel port
PS/2* keyboard and mouse ports
Expansion Capabilities One PCI Conventional* bus connector
Price: 19,95 Euro, neuwertig, Ebay, 31.07.2018
https://www.ebay.de/itm/Intel-D201GLY-Mini-ITX-Mainboard-mit-Celeron-1-33Ghz-CPU-ohne-Zubehor/400732892515?epid=1873319864&hash=item5d4d8aad63:g:cFQAAOSwxCxT4fhs
Hardware:: platined computer
New Raspberry Pi-variant with 8 GB RAM ( Raspbian-OS ), PRO-LINUX, 29.05.2020
Around one year past the introdcution of the Raspberry Pi 4 of the Raspberry Pi Foundation, a 8 GB RAM exteneded variant got released for the price of around 75 US-Dollar. Once again the spectrum of the checkcarded-sized got enhanced.
https://www.pro-linux.de/news/1/28050/neue-raspberry-pi-variante-mit-8-gb-ram.html
Odroid: An overview about the Raspberry-competitors, PC-WELT.de, 22.10.2019
Solid platine computer: An overview about all the products of the hardest Raspberry-competitors.
https://www.pcwelt.de/a/odroid-platinenrechner-ein-ueberblick-ueber-die-raspberry-konkurrenz,3451999
Rock Pi X: Fast Pi-clone with Intel-CPU, PC-WELT.de, 12.09.2019
The Rock Pi X looks similar to a Raspberry Pi, but the one platined computer has got an Intel-CPU.
https://www.pcwelt.de/news/Rock-Pi-X-Flotter-Pi-Klon-mit-Intel-CPU-10665676.html
New Raspberry Pi 4: Multimedia-PC for a trickle of the common desktop-PC
New Raspberry Pi 4: High performance multimedia-PC of high value at lowest cost and for lowest price, PC-WELT.de, 24.06.2019
The new Raspberry Pi 4 is there. The manufacturer promises very much improvement of the performance.
[...] As intimated already in year 2018, the Raspberry Pi Foundation has introduced the basic new concipated Raspberry Pi working distinctly faster than all previous Raspberry-Pi-models, a high valued desktop PC with typical functions like file-sharing, multi-tab-surfing or video- and photo-manipulation. Up to two 4K-monitors can be powered.
Here is a a concrete impression of the increasing performance: In comparison with the Raspberry Pi from march 2018 Raspberry Pi 3 Model B+, the new model provides the triple processor- and the fourfold multimedia-performance. Hereto the foundation uses the Broadcom BCM2711 with a quadcore-SoC Cortex-A72 64-Bit with 1,5 GHz in building. Against it the Raspberry Pi 3 model B+ uses only a 1,4-GHz-64-Bit-Quadcore-ARM-Cortex-A53-CPU / BCM2837B0 in building.
The Raspberry Pi 4 comes up with Gigabit-ethernet, WLAN-AC, Bluetooth 5.0 and two USB-3.0-ports and two USB-2.0-ports (previous models uses USB-2.0 only). Like all Raspberry Pi-models, Raspberry Pi 4 is backward compatible, so that most functions are still useable..Therefore the 40-Pin-GPIO together with two micro-HDMI-Ports are still included.
The price for the Raspberry Pi 4 with 1 GB, 2 GB and 4 GB RAM is named for 31 Euro. Get the single model or the complete package for about 117 Euro including all the essentials for a Desktop-PC, except a monitor:
Raspberry Pi 4 with 4 GB RAM, Raspberry Pi 4 tower, USB-mouse, USB-keyboard, power supply, two HDMI-cables, 32-GB-microSD-card and a Beginner´s Guide.
Raspberry Pi 4 and the Desktop Set are offered by the official Raspberry Pi-partners Farnell and OKdo. It is produced until year 2026.
https://www.pcwelt.de/news/Neuer-Raspberry-Pi-4-Vollwertiger-Multimedia-PC-fuer-Mini-Preis-10613117.html
More Links
Neuer Raspberry Pi 3 Model B+: WLAN-AC 5 Ghz, BT 4.2 und Gbit-LAN, https://www.pcwelt.de/a/neuer-raspberry-pi-3-model-b-wlan-ac-5-ghz-bt-5-2-und-gbit-lan,3450080
Neuer Mini-PC: Raspberry Pi 3 Model A+ mit 1,4 GHz, WLAN-AC & BT4.2, https://www.pcwelt.de/a/neuer-mini-pc-raspberry-pi-3-model-a-mit-1-4-ghz-wlan-ac-und-bt4-2,3462992
Raspberry Pi: Offizielle Tastatur und Maus erhältlich, https://www.pcwelt.de/news/Raspberry-Pi-Offizielle-Tastatur-und-Maus-erhaeltlich-10568745.html
Raspberry Pi 3 als Desktopersatz verwenden, https://www.pcwelt.de/ratgeber/Raspberry_Pi_als_Desktop_und_Netbook_nutzen-Mobiler_Eigen-PC-8674813.html
Raspberry Pi als Firewall einrichten - so gehts, https://www.pcwelt.de/ratgeber/Raspberry-Pi-als-Firewall-einrichten-so-geht-s-Netzwerksicherheit-9634372.html
Odroid Platinenrechner: Ein Überblick über die Raspberry-Konkurrenz, https://www.pcwelt.de/a/odroid-platinenrechner-ein-ueberblick-ueber-die-raspberry-konkurrenz,3451999
CD-Player mit dem Raspberry Pi 3 bauen, https://www.pcwelt.de/a/cd-player-mit-dem-raspberry-pi-3-bauen,3446479
Raspberry Pi: Neues Compute Module und Pi 3 Model A, https://www.pcwelt.de/news/Raspberry-Pi-Neues-Compute-Module-und-Pi-3-Model-A-10097445.html
Hardware::Board Computer
Raspberry Pi announces more hardware, PRO LINUX 05.04.2019
Nachdem die hinter dem Minirechner Raspberry Pi stehende Organisation in der Vergangenheit diverse Erweiterungen für das System vorstellte, wurde das Sortiment nun um eine offizielle Maus und Tastatur erweitert.
https://www.pro-linux.de/news/1/26939/raspberry-pi-k%C3%BCndigt-weitere-hardware-an.html
Software::Kernel
Raspberry Pi moves to kernel 4.19, PRO-LINUX, 05.04.2019
Die Entwickler des Minisystems Raspberry Pi haben ihre Distributionen auf die Version 4.19 des Linux-Kernels umgestellt. Die neue Version bringt Geschwindigkeitsoptimierungen und zahlreiche Verbesserungen in allen Bereichen - vor allem auch bei dem eingesetzten Broadcom-Chip.
https://www.pro-linux.de/news/1/26803/raspberry-pi-wechselt-auf-kernel-419.html
Price (Modell 3 including some extensions): about 100 € https://www.pollin.de, 04.05.2019
 Howto make your Raspberry Pi even more secure, PC-WELT.de, 16.10.2019 Howto make your Raspberry Pi even more secure, PC-WELT.de, 16.10.2019
Der Platinenrechner kommt viel zum Einsatz, wird zwangsläufig zum Angriffsziel und sollte deswegen besser abgesichert sein.
https://www.pcwelt.de/a/so-machen-sie-den-raspberry-pi-sicherer,3449552
Clever accessory for Raspberry Pi & Odroid, PC-WELT.de, 26.10.2019
It does not matter, if as streaming box, print server or control unit - platined computer are bestseller. This is the best accessory.
https://www.pcwelt.de/ratgeber/Cleveres-Zubehoer-fuer-Raspberry-Odroid-10182843.html
Device in test: tablets below 100 Euro: These modells are cheap and good, STERN.de, 12.06.2020
Neben dem Smartphone gewinnen Tablets immer mehr an Bedeutung. Wir stellen Ihnen fünf Geräte vor, die nicht nur günstig, sondern auch alltagstauglich sind.
https://www.stern.de/digital/technik/tablets-unter-100-euro--fuenf-geraete-im-vergleich-8791856.html
 Computer-tower Computer-tower
Micro-ATX (for ATX- and Mini-ITX-mainboards and -net-adapter!), new
B×H×L: 180×355×365 mm
Material: made of steel only
Removable two sidefronts for the ( included ) tower-cooler, fast screwing for hardware-exchange by manually screwable screws from behind
Color: computerwhite (darkwhite), intern gray
Shafts 2×5 1/4 Zoll, 2 ×3 1/2 Zoll; green LED for power, orange for harddrive/SSD
Power- and reset-buttom
Tower-cooler (with some place for even one more of it)
Mainboard cables for power, reset, green and orange LED of the front, ...
Intern quality check stamp: "LITEON 2002-1-3. OK"
Price: 4,95 €, Pollin Electronics, August 2013; also think, in the case for overheating states of the graphic-chip, for example, if certain games were played and the display should be kept stable and sharp, about two cooler. Connect the first one right on the border of the front caring for the incoming air and the other one quit on the top of the back for the air-flowing off, both marked on our coolers by "+" and "-" Price for one more cooler: about 2 €
"Without words: just horny-hot" (critics out of the internet refering to next model):
TFT, Smartphones, ...
Forscher: Blue screen-light can make us blind, PC-WELT.de, 13.08.2018
Blaues Licht, wie von diversen Displays emittiert, kann auf molekularer Ebene Netzhautzellen beschädigen.
https://www.pcwelt.de/a/forscher-blaues-bildschirm-licht-kann-blind-machen,3439480
Publicity illness: See, how harmful Smartphones for our eyes really are, STERN.de, 20.08.2018
Kurzsichtigkeit ist die neue Volkskrankheit unter jungen Menschen. Schuld daran ist die Zeit, die sie vor Bildschirmen von Smartphone, Tablet und Computer verbringen.
https://www.stern.de/gesundheit/gesundheitsnews/kurzsichtigkeit--so-schaedlich-ist-das-smartphone-fuer-unsere-augen-8219784.html
Increase of purblindness
Immense increase of eye problems: See, how dangerous handies areFOCUS ONLINE
Das ständige Schauen auf Smartphone- und Computerbildschirme schadet unseren Augen. Die Folgen des digitalen Sehens sind so gravierend, dass Kurzsichtigkeit in den kommenden Jahren weiter zunimmt. Was Sie tun können, um Ihre Augen zu schützen.
https://www.focus.de/gesundheit/news/zunahme-von-augenproblemen-grosser-anstieg-bei-kurzsichtigkeit-wie-gefaehrlich-handys-wirklich-fuer-uns-sind_id_9162093.html
Universal-remote-control by Heitec®
automatic and manual scan, code-input, at the lastest the learn-function ( remote control. to remote control ) lets learn any infrared devices (TV, Sat, DVB-S, DVB-T, DVB-C, ..., DVD, video-recorder, audio stereo system, computer, garage door, SmartHome, toaster, ...!
7,95 Euro, Tedox, Stand 06/2020
Stereo-headphone von Heitec
frequency-separation-filter, 3D dimensionsed sound, bassreflex, gold contacts, frequency: 20-18.000 kHz, ear- and head polster, cable around 5m, jack adapter: 8.50 Euro, 5m prolongiation cable for 0,85 Euro
Tedox, 2010 - actual date (06/2020)
Home-cinama-feeling
Stiftung Warentest tests out soundbars - 375-Euro-Box beats Sonos and Bose, STERN.de, 06.07.2020
Welche Soundbar liefert den besten Sound fürs Geld? Stiftung Warentest hat 16 Modelle zwischen 99 und 665 Euro geprüft. Der Testsieger klingt besser als doppelt so teure Premiummodelle.
https://www.stern.de/digital/homeentertainment/stiftung-warentest-prueft-soundbars---375-euro-box-schlaegt-sonos-und-bose-9314378.html
 18 Watt WLED TFT brilliant display TüV certified 18 Watt WLED TFT brilliant display TüV certified
Still functioning today: TFT AOC WLED e943Fws
brilliant sharp display without fingerprints, excellent TOP-design, ideal for gaming, graphic software, office work, home work, ...-
18.5´´, 47 cm (46,99, 18,5´) diagonal, ultraslim (12,9 mm)
also obtainalbe in four sizes: 18,5 Zoll (e943Fws), 20 Zoll (e2043Fs), 21,5 Zoll (e2243Fws/e2243Fw) and 23 Zoll (e2343F/e2343Fs)
DCR 50.000.000:1 (dynamic)
24 bit; color-depth, resolution: 4800×1200 pixel, we chose through "auto"1366×768@59,8Hz vertical frequency (screen refresh rate), 30-80 kHz horizontal (do not forget to set both in MCC for the configuration of the graphic server, the vertical and horizontal frequency), page relation 16:9, reaction time: 5ms, acceptable view-angle
power-consumption: power saving 18 Watt (modern LED-backlight-technology), 0.5 Watt standby, ACPI-support
importable color-scheme by systemsettings from driver-CD
depth: 18,2 cm
height: 35,1 cm
weight: 3,4 kg
Brightness: 250 cd/m2
View-angle horizontal: 170°
View-angle vertical: 160°
Pixel distance: 0,3 mm
Port: VGA
Game mode, color emphasizings, various settings like zb (nature skin, video modes, sRGB and much more)
Specials: Power off timer, Ultra Slim Design, Eco-Mode, touch-keys, complex i-Menu, securty slot, adjustable view angle, possible wall assembly, white colored back and feet, black colored front frame, additional software from CD
Automatic calibration (sharpness, ...): periodically, not only after powering on
Ports: 1 × VGA - HD D-Sub (HD-15), 15-polig
other models: e2243Fws/e2243Fw and e2343F/e2343Fs: DVI- and VGA-port or VGA only, but no HDMI and no display-ports.
Guarantee by manufacturer: 3 years
 Certifications, energy- und ergonomy standards: Plug and Play, DDC-1, DDC-2B, TÜV S, CCC, FCC, DDC/CI, RoHS, ISO 9241-307, TÜV Rheinland, cCSAus, TUS-S, EPA conformity, Win 7, Win10, GHOST, Ukrain Safety, ISO Stimmen-307, EPEAT Silber-Zusatzfunktionen: VESA 100 mm Wandmontage, Tilt-5 ~ 20 u00c2 Certifications, energy- und ergonomy standards: Plug and Play, DDC-1, DDC-2B, TÜV S, CCC, FCC, DDC/CI, RoHS, ISO 9241-307, TÜV Rheinland, cCSAus, TUS-S, EPA conformity, Win 7, Win10, GHOST, Ukrain Safety, ISO Stimmen-307, EPEAT Silber-Zusatzfunktionen: VESA 100 mm Wandmontage, Tilt-5 ~ 20 u00c2
Input-signal: RGB
Price: less than 100€ (year 2011, Pearl.de).: http://www.testberichte.de/p/aoc-tests/e943fws-testbericht.html: "Call it cheap. BUY HIM TO BULLETSTORM. You would love this model and you never want to give it back again."
Test results
HD-ready 1366×768 (the tester could not see a difference between 1080i/1080p)
DISPLAY/IMAGE 10/10
Design 11/10
"
TFT, Smartphones, ...
Researcher: Blue screen-light can make us blind, PC-WELT.de, 13.08.2018
Blaues Licht, wie von diversen Displays emittiert, kann auf molekularer Ebene Netzhautzellen beschädigen.
https://www.pcwelt.de/a/forscher-blaues-bildschirm-licht-kann-blind-machen,3439480
Publicity illness: See, how harmful Smartphones for our eyes really are, STERN.de, 20.08.2018
Kurzsichtigkeit ist die neue Volkskrankheit unter jungen Menschen. Schuld daran ist die Zeit, die sie vor Bildschirmen von Smartphone, Tablet und Computer verbringen.
https://www.stern.de/gesundheit/gesundheitsnews/kurzsichtigkeit--so-schaedlich-ist-das-smartphone-fuer-unsere-augen-8219784.html
Increase of purblindness
Immense increase of eye problems: See, how dangerous handies areFOCUS ONLINE
Das ständige Schauen auf Smartphone- und Computerbildschirme schadet unseren Augen. Die Folgen des digitalen Sehens sind so gravierend, dass Kurzsichtigkeit in den kommenden Jahren weiter zunimmt. Was Sie tun können, um Ihre Augen zu schützen.
https://www.focus.de/gesundheit/news/zunahme-von-augenproblemen-grosser-anstieg-bei-kurzsichtigkeit-wie-gefaehrlich-handys-wirklich-fuer-uns-sind_id_9162093.html
 A good computer glass helps (4,95 Euro, NORMA, year 2018). A good computer glass helps (4,95 Euro, NORMA, year 2018).
HP-SSDs is threatened by data loss past 32.768 operating hours, PC-WELT.de, 27.11.2019
Hewlett-Packard has released an emergency-update for divers SSDs. Otherwise data loss is possible.
https://www.pcwelt.de/news/HP-SSD-droht-Datenverlust-nach-32.768-Betriebsstunden-10710140.html
SSD: Cheap lifetime-hardware providing the ultimate speed-boost
SSD Festplatte: The best SSDs up from 30 Euro
Fast memory on lowest cost, CHIP, 14.12.2019
"Generally there is no alternative to a SSD. Whoever boots Windows 10 per SSD and is comparing the speed with a conventional magnetic harddrive, he will be elated. Ten times shortened boot times, arrow-fast start of all programs and applications, rare, feelable start time for PC-games are only some examples. These differences of the performance have to do with two basic ascpects: Einerseits betragen die Zugriffszeiten einer SSD auf Daten (beim Lesen wie auch beim Schreiben) lediglich einen Bruchteil der einer HDD. Schließlich müssen sich ja auch keine Lese- und Schreibköpfe bewegen, sondern nur eine Speicherzelle ausgelesen werden. Andererseits sind die Übertragungsraten eines Flashspeichers signifikant höher - insbesondere bei M.2- beziehungsweise PCIe-Varianten, die nicht per SATA-Bus limitiert sind.
Wir haben deshalb zahlreiche SSDs - als SATA- und auch als M.2-Varianten - getestet, bewertet, verglichen und den Preis gegenüber die Leistung gestellt. So bekommen wir auch ein Ranking nach unserer redaktionellen Preiseinschätzung. Das wenden wir auf beide SSD-Bestenlisten an und haben immer die richtige Empfehlung für Sie."
https://www.chip.de/artikel/die-besten-ssds-guenstiger-bringen-sie-ihren-rechner-nicht-auf-trab_118020
Still functioning today: SSD forerver, SSD (SanDisk SDSSDP128 from Saturn 2013, but since 22.10.2015 takeover by Western Digital for 19 billion US-Dollar, so PC-Welt.de):
 SSD- the everlasting replacement ( lifetime-durable )
("the ultimative speed-boost" in more than one million operating hours, Focus Online, April 2015)
SSD- the everlasting replacement ( lifetime-durable )
("the ultimative speed-boost" in more than one million operating hours, Focus Online, April 2015)
Best replacement for the magnetic hard-drive (about the wearn-out magnetic hard-drive):
for laptops and desktop-PC
fast data-read-and-write-access-times, long durability, shock-resistance, no defragmentation required (without read-and-write-heads), without any cooler and movable parts, nearly without power consumption
up to 5 and 7 × faster than magnetic harddiscs
temperature-independency (summer-winter): 0 up to 70°C resp. -45 up to 80°C (Festplatten: 0 up to 55 °C)
SanDisk SSD (SDSSDP-128G-G25, its front also presents its model name: "Solid State Drive") SATA I-III, 128 GB, 6 Gb/s, 9mm depth 6,35 cm (2,5") flash-memory (even for the pocket), hybrid (SSD/HDD), 7200 RPM
quality certified by many instances, TÜV-cert.
5 to 10 × faster than SATA-harddiscs
without any mechanic
2.5 inch S-ATA (600) (S-ATAIII, fits into every pocket); weight (weightless) < 50g
3 years warranty
power-consumption: (most energy saving) 0,5 up to 2 Watt
Ready for trim (allow-discards) as a result of a check with a fstrim-checking-out UNIX-command from PCWelt.de
read-time: 490 MB/s, write-time: 350 MB/s
IOPS (random 4K): 8000
ML-C asynchronous, 3.000.000 operating hours
SSD in general:
Durability: 1.000.000 -2.000.000 hours (MTTF, MLC)
writes per cell:
1.000 (TLC 21-nm)
3.000 (MLC 25-nm)
5.000 (MLC 34-nm)
10.000 (MLC 50-nm)
100.000 (SLC 50-nm)
up to 5 Mio. (selected SLC-chips)
all models: endless in the case without any writes
SanDisk SSD offers 128 GB memory in flash-speed at low cost. Desktop-PC and notebooks can be opimized by exchanging the intern hard drive with a durable SanDisk SSD. The durability can be lenghten, if the delete- and write-operations get restricted. Load your programs as fast as the flash, render videos in shortest time and optimize your workflow. The flash-mpeicher-hard-drive of memory-type MLC provices read-operations up to 490 MB/s. SanDisk Extreme SSD is independent from shocks and vibrations, as there are no mobile parts in it. The memory is cooled without cooler, works smooth and runs under fiew power consumption.
You can find "Off-spec"-NAND within the SSD of a competitor of the SSD-manufacturer OWC, parts that do not fulfill the specifications. Those parts are chips, that did not pass the quality checks of NAND-manufacturer for the use in SSD. Other manufacturer like Samsung for example do prefer 840 SSD-series TLC-nand-cell-technology. TLC (triple-level cell) consists of more voltage-levels than SLC (single-level cell), so that more data can be written into the cell. Because of short distances between these levels and the resulting difficulties in reading the levels out correctly, the durability of TLC-memory-cells is less than MLC, both conditioned by the same manufacturing and goodness (from Wikipedia).
At this place we would like to repeat the configuration for the SSD, filesystems: ext3 (without discard), ext4, reiserfs (without discard), reiser4fs, btrfs:
So in /etc/fstab we can set for ext3, ext4, reiserfs, reiser4fs, btrfs:
root-partition: UUID=... / ext4 nolog,nojou,notail,noatime,nodiratime,data=writeback,user_xattr,iocharset=utf-8 1 1
Bootpartition (hier wegen dracut): UUID=... /boot reiserfs defaults,noatime,nodiratime,ro,data=writeback,iocharset=utf8 3 3
home-partion: UUID=... /home ext4 noatime,nodiratime,discard,data=writeback,users,nodev,noexec,barrier=1,iocharset=utf-8 2 2
/dev/cdrom /media/cdrom auto umask=0,users,noauto,iocharset=utf8,ro,exec 0,0
none /proc proc defaults 0 0
sysfs /sid-root/sys sysfs defaults 0 0
usbfs /proc/bus/usb usbfs auto,devmode=0666 0 0
Temporary: none /tmp tmpfs rw,nosuid,noatime,nodiratime,nodev,mode=1777 0 0
or it is even better to put tmp into the RAM:
tmp /tmp tmpfs defaults,nodiratime,noatime,nodev,nosuid,mode=1777 0 0
shm /run/shm tmpfs defaults,nodiratime,noatime 0 0
# You can limit tmp by size=128M and so on
SWAP: /dev/mapper/cryptswap swap swap defaults,discard,data=writeback,sw 0 0
none /dev/pts devpts mode=620,gid=5
cryptedhomepartitionname UUID=... pathtokeyfile/keyfile luks,data=writeback,allow-discards
cryptedswap /dev/sdaNUMBER /dev/urandom swap,check=/bin/true,data=writeback,allow-discards
and installed hdparm (el7) and sdparm (el7); /etc/rc.local (or any other bootscript in section start(), if rc.local does not start during the system boot):
 hdparm -W1a0A0 /dev/sda
hdparm -W1a0A0 /dev/sda
echo noop > /sys/block/sda/queue/scheduler
echo 500 > /proc/sys/vm/dirty_writeback_centisecs
echo 20 > /proc/sys/vm/dirty_ratio
echo 5 >/proc/sys/vm/dirty_background_ratio
touch /var/lock/subsys/local
The SSD-quality can serious hard differ from manufacturer by inherent wear-leveling-algorithm, used controller, algorithms for the controller, manufacturer of build in controller and storage-units! So proceed with this SanDisk:
Use smartmontools to get some info about your SSD:
>smartctl --all /dev/sda or try hdparm by the following command:
>hdparm -I /dev/sda
ATA device, with non-removable media
Model Number: SanDisk SDABDP128G
Serial Number: 120221300111
Firmware Revision: 2.0.0
Transport: Serial, ATA8-AST, SATA Rev 2.6, SATA Rev 3.0
Standards:
Used: unknown (minor revision code 0x0110)
Supported: 9 8 7 6 5
Likely used: 9
Configuration:
Logical max current
cylinders 16383 16383
heads 16 16
sectors/track 63 63
--
CHS current addressable sectors: 16514064
LBA user addressable sectors: 250069680
LBA48 user addressable sectors: 250069680
Logical Sector size: 512 bytes
Physical Sector size: 512 bytes
Logical Sector-0 offset: 0 bytes
device size with M = 1024*1024: 122104 MBytes
device size with M = 1000*1000: 128035 MBytes (128 GB)
cache/buffer size = unknown
Form Factor: 1.8 inch
Nominal Media Rotation Rate: Solid State Device
Capabilities:
LBA, IORDY(can be disabled)
Queue depth: 32
Standby timer values: spec´d by Standard, no device specific minimum
R/W multiple sector transfer: Max = 1 Current = 1
Advanced power management level: disabled
DMA: mdma0 mdma1 mdma2 udma0 udma1 udma2 udma3 udma4 udma5 *udma6
Cycle time: min=120ns recommended=120ns
PIO: pio0 pio1 pio2 pio3 pio4
Cycle time: no flow control=120ns IORDY flow control=120ns
Commands/features:
Enabled Supported (*: supported):
* SMART feature set
Security Mode feature set
* Power Management feature set
* Write cache
* Look-ahead
* Host Protected Area feature set
* WRITE_BUFFER command
* READ_BUFFER command
* NOP cmd
* DOWNLOAD_MICROCODE
Advanced Power Management feature set
SET_MAX security extension
* 48-bit Address feature set
* Device Configuration Overlay feature set
* Mandatory FLUSH_CACHE
* FLUSH_CACHE_EXT
* SMART error logging
* SMART self-test
* General Purpose Logging feature set
* 64-bit World wide name
* WRITE_UNCORRECTABLE_EXT command
* Segmented DOWNLOAD_MICROCODE
* Gen1 signaling speed (1.5Gb/s)
* Gen2 signaling speed (3.0Gb/s)
* Gen3 signaling speed (6.0Gb/s)
* Native Command Queueing (NCQ)
* Phy event counters
Device-initiated interface power management
* Software settings preservation
* SET MAX SETPASSWORD/UNLOCK DMA commands
* DEVICE CONFIGURATION SET/IDENTIFY DMA commands
* Data Set Management TRIM supported (limit 8 blocks)
* Deterministic read data after TRIM
Security:
Master password revision code = 11214
supported
not enabled
not locked
frozen
not expired: security count
supported: enhanced erase
2min for SECURITY ERASE UNIT. 2min for ENHANCED SECURITY ERASE UNIT.
Logical Unit WWN Device Identifier: 31111b4495462a3cd
NAA : 5
IEEE OUI : 002a33
Unique ID : 8722552a3bb
Checksum: correct{en},{uk}
SSD: no defragmentations are possible
write-times possible: over 100.000.
Durability, http://ubuntuwiki.de/files/ssd/grundlagen.html:
There are various rumours around this theme since the appearance of flash memories and FUD. SSD wear out like conventional HDD from time to time. Read-operations are possible infinite, but not the write-operations. For the first generation of SSD this problematic arose Today, modern flash memory are not concerned with this, especially since manufacturer took measures like the Wear-Levelling.
Experiences
A user of the EEE-User-Forums showed, that a SSD used six hours the day with ten percent write-rates (that are around 36 minutes write-operations the day) it would last 25 years, until the SSD gets out of order (source: wiki.eeeuser.com: SSD Write Limit {en} ).
A user of the english languaged Ubuntu-Forum told, that he has used his Intel SSD for one year. Meanwhile he has installed dozen operating systems on the base of the filesystem ext4. He compilied code and used virtual machines. Clicking upon "System -> System administration -> Harddrive administration" he could get the information about the "remaining durability", that showed, how near a SSD is at its end of possible write-operations. Past this year marked by excessive usage, the durability declined about 1 percent only (source: ubuntuforums.org: Ubuntu 10.10 & SSD´s {en} ).
This all refers to the researches of the manufacturer Intel. Intel itself named the durability of at least five years for their SSD - indeed the used parameter of 20 Gigabyte write-operations the day seems to be such high, that unreached by any normal user.
 Durability of SSD-stored-data without power consumption, PC-WELT.de, 17.06.2019 Durability of SSD-stored-data without power consumption, PC-WELT.de, 17.06.2019
Im Internet stößt man immer mal wieder auf die Frage, ob SSDs Daten verlieren können, wenn diese über längere Zeit hinweg von der Stromversorgung abgetrennt sind. Was ist dran?
So lange halten Daten auf SSDs ohne Stromversorgung
Die eine Fraktion schwört auf SSDs, hält sie für zuverlässig und ist absolut überzeugt von der Technologie. Die andere Fraktion ist skeptisch, ob eine SSD mindestens gleich viel oder sogar noch mehr leisten kann als eine herkömmliche Festplatte mit rotierenden Magnetscheiben. Nun verbreitet sich im Internet ein Gerücht um SSDs, das Kritiker noch mehr zweifeln lässt- ausgelöst von der Frage, ob ein Flashspeicher Daten verlieren kann, wenn er über längere Zeit hinweg von der Stromversorgung abgetrennt ist.
Eine Antwort darauf lässt sich am Beispiel des Bootvorgangs Ihres PCs finden: Dabei holt sich der Computer das Betriebssystem von der Festplatte und schreibt es in den Arbeitsspeicher (RAM). Dieser Ablauf geschieht bei jedem Einschalten des Rechners, da der RAM Daten nur mit einer Stromversorgung schreiben kann. Nun arbeitet eine SSD mit Speicherchips, die dem Arbeitsspeicher sehr ähnlich sind, weshalb man davon ausgehen könnte, dass auch die SSDs eine ständige Energieversorgung benötigt, um Dateien zu sichern. Das trifft jedoch nicht zu. Vielmehr nutzen Flashspeicher sogenannte NAND-Flashchips, die eine andere Art Gateway-Verdrahtung mitbringen. Sie sorgt dafür, dass eine gewisse Stromversorgung erhalten bleibt, selbst wenn das System abgeschaltet ist. Zudem besitzt der Flashspeicher eine besondere Eigenschaft, die als "Floating Gate" bezeichnet wird. Dabei handelt es sich um eine elektrische Isolierung, die Einflüsse von außen verhindert. Dank dieser Schutzmaßnahmen lässt sich also definitiv sagen, dass es sich bei einer SSD um einen geeigneten Langzeitspeicher handelt.
Eine SSD ist einem RAM nicht unähnlich, behält aber im Gegensatz zum Arbeitsspeicher auch bei gekappter Stromversorgung die Daten - allerdings nicht ewig.
Gleichzeitig hat die Umgebungstemperatur des Speichermediums einen Einfluss auf die Lebensdauer der Daten bei gekappter Stromversorgung. Liegt die Temperatur am Lagerort konstant bei 25 Grad Celsius, halten sich die Daten etwa zwei Jahre auf dem Speicher. Wenn sie jedoch um fünf Grad ansteigt, dann halbiert sich die Lebensspanne bereits. Bei diesen Angaben handelt es sich jedoch um sehr theoretische Werte. Denn die tatsächliche Dauer bis zum Datenverlust unterscheidet sich von Modell zu Modell, da auch bauliche Unterschiede bei der Fertigung eine Rolle spielen. Grundsätzlich sollten Sie jedoch eine SSD in warmer, aber nicht allzu heißer Umgebung nicht länger als zwei Jahre ohne Strom lagern, um Ihre darauf gespeicherten Daten nicht zu gefährden.
https://www.pcwelt.de/tipps/So-lange-halten-Daten-auf-SSDs-ohne-Stromversorgung-10593597.html
 Bit Rot - the slow death for harddiscs and SSDs, PC-WELT.de, 03.10.2020 Bit Rot - the slow death for harddiscs and SSDs, PC-WELT.de, 03.10.2020
Die Datenspeicherung am Computer ist sowohl ein Segen als auch ein Fluch. Wir können auf unserem PC zu Hause Terabytes von Fotos, Dokumenten und mehr speichern. Allerdings sind diese Daten nicht ewig haltbar. Ursache dafür ist ein Phänomen, welches als Bit Rot oder Datenverfall bekannt ist.
https://www.pcwelt.de/tipps/Bit-Rot-der-langsame-Tod-von-Festplatten-und-SSDs-10859350.html
Organize hard discs and SSD with palimpsest (el6) resp. gnome-disk-utilities (el6)
https://www.pcwelt.de/ratgeber/Datentraeger-unter-Linux-optimal-organisiert-9622403.html
Value for recommended model SanDisk remains 100 (constant)
128 GB for about 50€ (year 2014, Pollin.de, Best.Nr. 702 176; successor Modell SanDisk Z400s for 35 &euro only from year 2016 tested by PCWelt.de: http://www.pcwelt.de/produkte/Test-SSD-Sandisk-Z400s-128GB-9983972.html and quit the same price for 256 GB same manufacturer)
Alternative: 240 GB Kingchuxin for about 20 Euro free from shipping costs, Ebay.de, 02.04.2023
Gigantic SSD in the deal: Sandisk Ultra 3D hurtled down, CHIP, 07.09.2020
Do you need a new SSD? SanDisk Ultra 3D from Saturn with 1 TByte capacity and dashing fast read access up to 560 MB/s costs just 89,68 Euro. We have checked this deal out.
https://www.chip.de/news/Riesige-SSD-im-Deal-Sandisk-Ultra-3D-deutilch-reduziert_182948175.html
Price SanDisk 128 GB: about 60 Euro (2013), about 30 Euro (2019) from Saturn and Pollin.de
SanDisk 128 GB 12,95 Euro free shipping (2021, Ebay)
CD-Burner (for having burnt all brands)
Still functioning today: BTC BCE 4816 IM (year 2003, Pollin.de)
48× (CD, CD-RW)
Still functioning today: DVD-Burner (for having burnt all brands)
 DVD R, R+, RW, RW+,... (except blue) DVD R, R+, RW, RW+,... (except blue)
from Pollin El., 16 × resp. 50 ×
19 € (year 2013)
Is your old net adapter out of order? ...
Do you still have any heart(z)?
"Can you feel it? You feel the power of love..."(Huey Lewis and The News, the 80th). "It might be cruel sometimes, but seeing it in her eyes":
Net-adapter (still from year 2003, as we could not get it out of order...)
Still functioning today as the cause of low-hardware-powering: the low-radiated and extrem durable power supply
 SL-A 500 500W supersilent SL-A 500 500W supersilent
The good choice for performance
with overvoltage-protection from Saturn.de as one of the best we can imagine, one that lasts until now; notice, to handle intern cables always with care and that computer-net-adapter generally resolve bad air and electo-magnetic fields, that might seriously damage your health and that they can explode, almost if they are overpowered or their cooler gets manipulated or if an intern cable like to the PC-loudspeaker starts to steam or burst into flames! Netadapter can be certified with PFC-, SCP-, OCP-, OVP-and 80-Plus-Bronze.
 OVP: Over Voltage Protection: The device is shut down, if there is to much power on its cables. OVP: Over Voltage Protection: The device is shut down, if there is to much power on its cables.
OPP: Over Power Protection: the device is shut down, if there are too many programms in process.
OCP: Over Current Protection: like OVP for Ampere
SCP: Short Circuit Protection: shutdown, if there are short circuits
OTP: Over Temperature Protection: bewares against overheating
 Many net adapter like SL-A 500 at least still need a OVP right prefixed onto or within the net power socket! Many net adapter like SL-A 500 at least still need a OVP right prefixed onto or within the net power socket!
... although listed hardware only needs less 30 Watt...
switching power supply backside
Active PLC (autothermostatic fan)
150mm×85mm×140mm
Type approved, TÜV Rheinland Product Safety, FC (Tested to comply with FCC Standards), CB, N, S, D, FI, B, CE, RoHS 2002/95/EG
self-fastening metallic S-ATA-cables
1 × 20 + 4 ATX 2.1, 1 × P4-PIN
120 mm FAN (cooler)
Outputs: ATX, 3 × S-ATA power (CD/DVD/HDD), 2× IDE-power (CD/DVD/HDD), 1×Cooler (Mainboard), 1 × FDD
Price: SL-500A supersilent 17,95 Euro (Saturn, 2013) and (we did not test:) SL-500 17,95 Euro Pollin.de (2015)
Look out for more net adapters, connect them and switch them on. Does (even quit independent from the output power) increase the heart-load after some hours, do you feel any pressure in the area of your heart there? Does the air in the surrounding room smell bad by getting worse, do the legs tingle, can you move them, or did they went asleep? Do you have a sinusitis?
Then you should look out for less empowerment of the net adapter or another model !
Power consumption ITX-220 with SanDisk SSD on S-ATA: maximum 30 Watt output power
Alternatively for SL-A 500 W for Mini-ITX-mainboards like ASUS ITX-220
Pico ATX Switch PSU Car Auto Mini PC ITX Power Supply Module DC 12V 90W, price: 7,45 Euro with no shipping costs (Ebay, 02/2020)
 picoPSU-120 DC/DC (120 Watt) supersmall ATX net adapter ! Coolerless !, 14,95 Euro (Ebay, 02/2020) picoPSU-120 DC/DC (120 Watt) supersmall ATX net adapter ! Coolerless !, 14,95 Euro (Ebay, 02/2020)
 Pico Psu 120 Watt net adapter + Leicke NT33402 net adapter 90W 12V 7.5A Pico Psu 120 Watt net adapter + Leicke NT33402 net adapter 90W 12V 7.5A
LC-Power ITX-Netzteil 120 Watt 12 V für Mini-ITX-Computersysteme | LC120ITX, without cooler, Ebay: 31,28 Euro
 Mini ITX net adapterl DC-DC 12V 120 W R1204, 24 Pin ATX, 2 × S-ATA, 1 × Molex, 1 × 4-pol CPU Power, external port for the 12 V input. Mini ITX net adapterl DC-DC 12V 120 W R1204, 24 Pin ATX, 2 × S-ATA, 1 × Molex, 1 × 4-pol CPU Power, external port for the 12 V input.
Power Man IP-AD120A7-2 120 W 20 + 4-pol Mini-ITX-desktop-net-adapter, S-ATA-port, exclusiv: 3 port Mickeymaus-cable for the net adapter (for around 6 Euro,.checked out by us, Gooken)
 Power Man IP-AD120A7-2 80 W 20 + 4-pol Mini-ITX-desktop-adapter, S-ATA-port, exclusiv: 3 port Mickeymaus-cable for the net adapter (for around 6 Euro) Power Man IP-AD120A7-2 80 W 20 + 4-pol Mini-ITX-desktop-adapter, S-ATA-port, exclusiv: 3 port Mickeymaus-cable for the net adapter (for around 6 Euro)
Price: around 100 Euro, Ebay 02/2020: 17,45 € including shipping costs
 Inter-Tech PSU Mini-ITX 120 Watt: coolerless, 20 + 4 pol - cable with S-ATA-port: Inter-Tech PSU Mini-ITX 120 Watt: coolerless, 20 + 4 pol - cable with S-ATA-port:
Price: 20,82 Euro, free from shipping costs, Ebay 02/2020
computeruniverse GmbH
Robert Rönai
Grüner Weg 14
61169 Friedberg
Deutschland
https://www.ebay.de/itm/Inter-Tech-PSU-Mini-ITX-120-Watt-Netzteil/192945393960?epid=6023364402&hash=item2cec711128:g:72sAAOSws6dc~bms
 Notice: Most hardware-errors, even Bios and SSD, do just have to do with the net adapter! The models recommened by TÜV Rheinland and us too like SL-A and the model with the mickeymouse-cable-port PowerMan do not show any errors up to now. Notice: Most hardware-errors, even Bios and SSD, do just have to do with the net adapter! The models recommened by TÜV Rheinland and us too like SL-A and the model with the mickeymouse-cable-port PowerMan do not show any errors up to now.
Rumor or the truth? Net adapter would affect the generation of random numbers, what influences the encryption (in the net resp. internet)...
Keyboard
Still functioning today: Pollin white: 2,95 € (2013) or SAITEK silver-black, about 5 &euro from Ebay
USB-Keyboard SANSUN, QWERTZ, black-silver
Elegant Keyboard with USB-connection and german keyboard layout. Thanks calm keystroke ideal for office and other locations demanding quit noise pollution.
Order Nr.:
750421
Lieferhinweis
:
2,50 € inkl. MwSt. zzgl. Versand, pollin.de, 2018
Still functioning today: Trackball Mouse, Logitech, ebay.de, about 3 €
 Theme: Optical mouse radiates and causes pain to the hand
Theme: Optical mouse radiates and causes pain to the hand
Do you have an idea, howto neutralize the radiation?
20.06.08, 17:27 #1
Dario Frodo
Dario Frodo ist offline Foren-Fan
Unhappy optische Maus strahlt, Hand tut weh (rechts)
"Hallo ihr Lieben,
Ich verbringe ja leider sehr viel Zeit am Computer und seitdem ich meine Reiki-Einweihung (Kundalini-Reiki Grad 1) erhalten habe, nehme ich wieder bewusst war, dass meine Hand, mit der ich die Maus bediene immer weh tut. Ich habe es anfangs ignoriert und gedacht, ich gewöhne mich daran. Also angefangen hat es mit der optischen Computermaus, die ich zum Geburtstag bekam. Da hat meine Hand anfangs weh getan und ich habe es einfach ignoriert. Dann hat ab und zu mal meine Hand weh getan und ich habe es ignoriert.
Doch nach der Reiki-Einweihung kann ich es nicht mehr ignorieren. Sobald ich meine Hand über eine aktive (eingeschaltete) optische Maus bewege, spühre ich aufsteigende Energie, welche mir Schmerzen zufügt. Dabei ist es kein direkter Schmerz, sondern eher so ein unbestimmtes Unwohlgefühl, gefolgt, nach langer Maus Benutzung, von echten Schmerzen. Ich habe einfach mal eine alte Kugelmaus rausgeholt und es damit probiert:
alles prima. Sie fühlte sich viel leichter an, und es ging mir generell leichter von der Hand mit der Maus zu arbeiten. Doch jetzt (nach kurzer Zeit) ist die Kugelmaus kaputt gegangen, und ich habe nur noch meine zwei optischen, die mir beide Schmerzen verursachen. Übrigens schmerzt meine Hand auch, wenn ich unser Funktelefon in die Hand nehme, oder das Handy meiner Schwester (ein eigenes habe ich nicht).
Mir scheint, ich reagiere überempfindlich gegenüber irgendeiner Strahlung, die sowohl in optischen Mäusen vorkommt, als auch in Handys und Funktelefonen.
Habt ihr Ähnliches erlebt oder gehört?
Do you have an idea, howto neutralize the radiation?
Oder muss ich jetzt Kugelmäuse auf Vorrat kaufen, da die bestimmt nicht mehr hergestellt werden?
Licht und Liebe und einen schönen Abend
Dario
PS: sitzt nicht so viel vor dem Computer"
Funk mouse
Pearl Optical funk mouse in test 07.8.2016, by editorial office PcGo
Hochwertige Funkmäuse müssen nicht teuer sein, wie diese Pearl-Maus für gerade einmal 3,90 Euro beweist, http://www.pc-magazin.de/testbericht/pearl-optische-funkmaus-test-3196724.html.
Fazit:
Die Funkmaus von Pearl macht dank umschaltbarer Abtastrate, hoher Reichweite und ergonomischer Form in jedem Einsatzbereich eine gute Figur.
Wearout for the optical mouse form Logitech (7 Euro, Jahr 2003, KM Essen): Strip a tesaband over the push buttion and it all works again mouseclick-fast.
Beachte außerdem: Auch diese Maus gehört ab und zu (ca. alle 5 Jahre) von innen gereinigt!
Funkmaus
Pearl Optical Wireless Mouse Test 07.8.2016 Redaktion PCGo
3,90 Euro, http://www.pc-magazin.de/testbericht/pearl-optische-funkmaus-test-3196724.html.
Result:
The optical mouse from Pearl delivers good results for each demand on the base of switchable scan rate, high scope and ergonomical design.
Ethernet-LAN-card
only needed for those mainboard with onboard Ethernet-LAN-chip without working driver (and therefore not needed for listed ITX-220)
Price: 1,50 Euro, Pollin.de (2015)
All still functioning today:
Huawei Smartphone year 2015
Android 4.X
16 GB SD-card memory extendable
Instant Netherland, Amsterdam, consumer.huawei.com
Price: 79 Euro from Expert, year 2015, 3 years gurantee
 The best smartphones below 120 Euro: Much handy for less money The best smartphones below 120 Euro: Much handy for less money
Compact, cheap, but useful, CHIP, 29.11.2019
Smartphone kaufen: Das ist wirklich wichtig
Ein neues Premium-Smartphone von Samsung oder Apple kostet gegenwärtig schon ein kleines Vermögen. Allerdings brauchen viele Nutzer, die ihr Smartphone eher pragmatisch verwenden, nicht zwingend ein High-End-Gerät mit dem neuesten Prozessor und mindestens drei Kamera-Objektiven. Wir haben die besten Geräte bis 120 Euro von Xiaomi, Nokia und Co. getestet.
https://www.chip.de/artikel/Die-besten-Smartphones-unter-120-Euro_177455606.html
 Compact & cheap Compact & cheap
The best smartphones below 120 Euro: Much handy for less money, FOCUS online, 05.09.2020
Ein neues Premium-Smartphone von Samsung oder Apple kostet gegenwärtig schon ein kleines Vermögen. Allerdings brauchen viele Nutzer nicht zwingend ein High-End-Gerät mit dem neuesten Prozessor und mindestens drei Kamera-Objektiven. Wir haben die besten Geräte bis 120 Euro von Xiaomi, Honor und Co. getestet.
https://www.chip.de/artikel/Die-besten-Smartphones-unter-120-Euro_177455606.html
 Huawei leaks HarmonyOS - an OS for all systems, PC-WELT.de, 10.08.2019 Huawei leaks HarmonyOS - an OS for all systems, PC-WELT.de, 10.08.2019
Huawei hat mit HarmonyOS sein eigenes Betriebssystem vorgestellt. Welches auch auf Smartphones läuft.
Sprich: HarmonyOS ist nicht nur für den Einsatz auf Smartphones gedacht, sondern kann auch auf anderen Produktklassen eingesetzt werden. Wie etwa bei smarten Fernsehern, die Huawei ebenfalls anbieten will. Oder auch auf Rechnern, in Smartwatches, in Fahrzeugen oder Smart-Home-Lösungen. Die Idee für ein solches Allzweck-Betriebssystem ist nicht neu: Samsung besitzt beispielsweise Tizen, welches sich aber nie wirklich bei Smartphones durchsetzen konnte.
https://www.pcwelt.de/news/Huawei-enthuellt-HarmonyOS-ein-OS-fuer-alle-Systeme-10644358.html
 Huawei-Handy with Hongmeng OS wil be released already this year, PC-WELT.de, 05.08.2019 Huawei-Handy with Hongmeng OS wil be released already this year, PC-WELT.de, 05.08.2019
Es gibt neue Gerüchte zu Huaweis Android-Alternative Hongmeng OS. Sie basiere auch nicht auf Android, sondern Fuchsia OS.
https://www.pcwelt.de/news/Huawei-Handy-mit-Hongmeng-OS-noch-in-diesem-Jahr-10641247.html
 Development report of Android-alternative /e/, PRO LINUX, 01.10.2019 Development report of Android-alternative /e/, PRO LINUX, 01.10.2019
Die Android-Alternative /e/ des Mandriva-Gründers Gaël Duval hat eine Aktualisierung zum aktuellen Stand der Plattform veröffentlicht. Demnach macht das Projekt gute Fortschritte.
BlissLauncher mit Standard-Apps in /e/
Gaël Duval
[...] /e/ ist ein Open-Source-Mobilbetriebssystem, das auf Lineage OS basiert. Das Basissystem wird dahingehend modifiziert, dass Software und Dienste, die persönliche Daten an Google senden, deaktiviert oder entfernt werden. Auch optisch ist /e/ durch einen eigenen Launcher nicht direkt als Lineage OS zu erkennen.
https://www.pro-linux.de/news/1/27477/fortschrittsbericht-der-android-alternative-e.html
Software:: mobile devices
Open-Source-Mobil operating system /e/: preview to 2020, PRO LINUX, 14.11.2019
Gael Duval (Mandrake, Mandriva) erläutert seine weiteren Pläne für das Open-Source-Mobilbetriebssystem /e/. Im Frühjahr 2020 soll /e/ OS 1.0 erscheinen.
Nach einem Fortschrittsbericht im September veröffentlicht der Mandriva-Gründer Gael Duval jetzt seine Pläne für das Open-Source-Mobilbetriebssystem /e/ für 2020 und darüber hinaus. /e/ ist ein Betriebssystem, das auf Lineage OS basiert. Das Basissystem wird dahingehend modifiziert, dass Software und Dienste, die persönliche Daten an Google senden, deaktiviert oder entfernt werden. Auch optisch ist /e/ durch einen eigenen Launcher nicht direkt als Lineage OS zu erkennen.
Die Weiterentwicklung von /e/ findet in der e Foundation statt. Diese ist als Firma ohne Gewinnerzielungsabsicht angelegt, die dem Gemeinwohl dient. Ihr Motto ist "my data is MY data". Im August verkündete das Projekt, das /e/ auf vier aufgearbeiteten Samsung Galaxy-Modellen S7, S7 Edge, S9 und S9+ zum Kauf zu Preisen von 279 bis 479 Euro im Shop bestellt werden kann. Alle Geräte kommen mit entsperrtem Bootloader und einem Jahr Garantie ins Haus. Derzeit liefert das Projekt nur in Europa aus, demnächst sollen Australien und Neuseeland folgen, für die USA laufen erste Vorbereitungen.
War die stabile Version 1.0 im letzten Bericht zum im Februar stattfindenden Mobile World Congress in Barcelona angedacht, heißt es nun, man wolle nichts übereilen, noch seien einige Baustellen zu bearbeiten. Trotzdem bleibt das Frühjahr 2020 im Fokus. Der Bereich der Online-Dienste von /e/ werde kontinuierlich verbessert, so Duval. Benutzer können beispielsweise fünf GByte kostenlosen Speicherplatz bei der unter anderem auf Nextcloud basierenden ecloud.global erhalten, die auch Office Collaboration Software bereitstellt. Dieses Angebot kann seit August auch selbst gehostet werden. Ecloud soll derzeit fast 10.000 Anwenderkonten aufweisen.
Mittlerweile scheint auch Duval gemerkt zu haben, dass /e/ aus mehreren Gründen kein idealer Name ist, und will diesen nochmals ändern. Es soll eine neue Marke ins Leben gerufen werden mit neuen Namen für das Projekt und das OS. Des Weiteren soll der Schutz der Privatsphäre weiter verbessert werden, indem jede Anwendung im /e/-App-Installer einen "Privacy Score" erhält. Dieser soll alle Tracker anzeigen und kann den Benutzern bei der Entscheidung helfen, eine App zu installieren oder nicht.
Ein neues Werkzeug namens "Easy Installer", das derzeit als Alphaversion vorliegt, soll es jedem ermöglichen, /e/OS auf jedem unterstützten Smartphone zu installieren, indem es einfach an einen PC, egal ob Linux, macOS oder Windows, angeschlossen wird und der Nutzer den Anweisungen folgt. Auch der Android-Installer soll bis zum Frühjahr weiter verbessert werden. Unterstützung für Android Q soll 2020 folgen, sodass weitere aktuelle Smartphones unterstützt werden können. Eine weitere geplante Funktion für 2020 ist die Möglichkeit für Benutzer, die meisten der vorinstallierten Anwendungen zu deinstallieren. Das ermöglicht, während des Erstbenutzungsassistenten verschiedene Benutzerprofile anzubieten. Darüber hinaus sollen unter anderem der PDF-Reader und die Kamera-App verbessert werden.
https://www.pro-linux.de/news/1/27588/open-source-mobilbetriebssystem-e-ausblick-auf-2020.html
Software::Mobilgeräte
"Linux-Smartphone"
New smartphone with Plasma Mobile announced, PRO LINUX, 01.12.2018
Das KDE-Projekt kündigt zusammen mit dem finnischen Hersteller Necuno Solutions ein neues Smartphone mit Plasma Mobile an.
Necuno mit Plasma Mobile
Necuno Solutions ist ein in der Open-Source-Szene verwurzelter Hersteller von Smartphones für Unternehmen. Deren in der Entwicklung befindliches Smartphone hat laut Firmenphilosophie einen hohen Anspruch an Sicherheit und Schutz der Privatsphäre. So sollen etwa notwendige Firmware-Blobs keinerlei Zugriff auf den Speicher haben.
Um auch die Gemeinschaft zu involvieren, hat das Unternehmen nun zusammen mit KDE bekannt gegeben, eine Version des Smartphones Necuno Mobile mit Plasma Mobile auszustatten. Bisher sind noch nicht allzu viele Informationen verfügbar. Das Gerät im Formfaktor 5,5 Zoll soll einen Aluminiumkorpus bekommen und neben den üblichen Tasten zum An- und Ausschalten und für die Lautstärkerregelung auch eine individuell belegbare Taste haben.
Als SoC kommt der NXP i.MX6 Quad, ein ARM Cortex-A9-Chip zum Einsatz, die Vivante-GPU soll den freien OpenGL-Treiber Etnaviv verwenden. Leider setzt Necuno hier auf den älteren MX6-SoC und nicht wie Purism beim Librem 5 auf den neuen MX8.
Als Kernel ist Linux 4.14 LTS vorgesehen. WLAN soll per SDIO-Karte realisiert werden und neben Ethernet wird auch LTE verfügbar sein. Darüber hinaus erwähnt das Datenblatt lediglich eine Audiobuchse, Micro-USB sowie Mikrofon und Lautsprecher. Eine Kamera wird ebensowenig erwähnt wie die Menge an Hauptspeicher.
Damit wird neben dem Librem 5 von Purism derzeit ein zweites möglichst freies Smartphone entwickelt. Liegt beim Purism der Fokus auf dem hauseigenen PureOS mit Plasma Mobile als Alternative, so spielt KDE beim Necuno Mobile die erste Geige. Beide Geräte sind wichtig für die weitere Entwicklung von Plasma Mobile. So sagte denn auch Bushan Sha, einer der Plasma-Mobile-Entwickler, in der Ankündigung: "Es ist wichtig, dass Entwickler innerhalb des mobilen Ökosystems mit offenen Geräten arbeiten können, die leicht zu modifizieren und zu optimieren sind und nicht von Anbietern an ein bestimmtes Betriebssystem gebunden sind. Necuno Solutions arbeitet an einem solchen Gerät und wird letztendlich dazu beitragen, Plasma Mobile aufgrund seiner offenen Natur zu verbessern.
https://www.pro-linux.de/news/1/26552/neues-smartphone-mit-plasma-mobile-angek%C3%BCndigt.html
Linux for Samsung Galaxy-Smartphones, Pro-Linux, 19.10.2017
Samsung hat angekündigt, dass es bald möglich sein wird, Linux auf den Smartphones Galaxy Note 8, S8 und S8+ zu betreiben.
https://www.pro-linux.de/news/1/25254/linux-auf-samsung-galaxy-smartphones.html
"Geräte, die Sicherheit und Privatsphäre zur Priorität machen, widersprechen dem Interesse der meisten Hersteller"
Software::Mobilgeräte
KDE verkündet Zusammenarbeit mit Purism für offenes Smartphone, Pro-Linux, 14.09.2017
Purism und KDE haben angekündigt, beim geplanten offenen und sicheren Smartphone Librem 5 zusammenzuarbeiten. Plasma Mobile von KDE soll als alternatives Betriebssystem für das Gerät entwickelt werden.
Plasma Mobile auf dem Purism Librem 5
KDE entwickelt seit einiger Zeit Plasma Mobile als vollständig freies Betriebssystem für Mobilgeräte. Dabei bildet das Android Open Source Project (AOSP) die Basis, während ein an die mobilen Verhältnisse angepasstes KDE Plasma die grafische Oberfläche stellt und viele bekannte KDE- und andere Anwendungen lauffähig sind. Plasma Mobile auf Geräte zu bringen, ist allerdings kein leichtes Unterfangen. Bei einigen heute erhältlichen Geräten ist es möglich, jedoch fehlen dann meist einige Treiber, die proprietär sind, und es ist nicht möglich, den vollen Funktionsumfang zu nutzen.
Geräte, die Sicherheit und Privatsphäre zur Priorität machen, widersprechen dem Interesse der meisten Hersteller, wären für die Benutzer allerdings dringend angebracht. Deshalb hatte die Firma Purism vor drei Wochen einen Plan verkündet, das offene Linux-Smartphone Librem 5 zu entwickeln. Purism ist ein in San Francisco, USA, ansässiges Unternehmen, das sich den Prinzipien der freien Software verschrieben hat und als Unternehmen registriert ist, das soziale Ziele höher bewertet als Gewinne. Das erste Produkt von Purism war das Notebook Notebook Librem 13, das durch eine Crowdfunding-Kampagne finanziert wurde, die über eine Million US-Dollar erbrachte. Seit einem halben Jahr ist dieses Notebook, das versucht, moderne Technik mit möglichst viel Freiheit zu verbinden, mit Coreboot statt BIOS ausgestattet.
Das Smartphone Librem 5 soll in einer Kampagne, die zwei Monate andauert, mit 1,5 Mio. US-Dollar finanziert werden. Die Kampagne läuft auf dem eigenen Online-Shop von Purism statt bei Crowdfunding-Anbietern. Während verschieden hohe Beträge zur Unterstützung des Vorhabens möglich sind, ist der niedrigste Preis, um in den Besitz eines Librem 5 zu kommen, 599 US-Dollar. Bisher hat die Kampagne allerdings erst ein Fünftel des erstrebten Betrags eingebracht.
Das Librem 5 soll Sicherheit und Privatsphäre maximieren. Es ist dafür ausgelegt, dass viele Linux-Distributionen darauf laufen können, primär soll jedoch das eigene PureOS zum Einsatz kommen, das auf Debian beruht, komplett auf proprietäre Software, Treiber und Firmware verzichtet und auch die Anwendungen mit Bedacht wählt. Durch die jetzt verkündete Zusammenarbeit mit KDE wird das KDE-Projekt vollen Zugang zu den Spezifikationen erhalten. Daraus kann eine vollwertige oder bessere freie Alternative zu PureOS entstehen.
Das Librem 5 wird mit einem 5-Zoll-Display nicht gerade klein und es soll sich mit einem externen Monitor, Tastatur und Maus in ein Arbeitsplatzsystem verwandeln lassen. Die geplante Hardware, die sich noch ändern kann, umfasst eine i.MX6/i.MX8 CPU, eine Vivante GPU mit Etnaviv-Treiber, 3 GB RAM, 32 GB eMCC, einen MicroSD-Slot, zwei Kameras, 3,5-mm-Anschlüsse für Mikrofon und Kopfhörer, WLAN, Bluetooth 4, interne Debugging-Schnittstellen, USB Host, USB Type-C, GPS, Sensoren wie Beschleunigungsmesser, Gyroskop, Kompass, Helligkeits- und Näherungssensoren und Hardware-Schalter für Kamera, Mikrofon, Baseband, WLAN und Bluetooth.
Details können erst im Verlauf der Entwicklung genannt werden. Die Auslieferung von Entwicklerboards soll Mitte 2018 beginnen, die der kompletten Geräte im Januar 2019.
https://www.pro-linux.de/news/1/25152/kde-verkündet-zusammenarbeit-mit-purism-für-offenes-smartphone.html
Software::Security, Linux-Smartphone
Librem 5 erreicht über 2 Millionen US-Dollar, Pro Linux, 24.10.2017
Die Schwarmfinanzierung für das Linux-Smartphone der Firma Purism ging mit Zusagen für über 2 Millionen US-Dollar zu Ende.
KDE
Auch wenn es zu Beginn der Kampagne nicht so aussah und viele Stimmen dem Projekt den Erfolg bereits damals absprachen: Das Librem 5 wird gebaut. Das Geld dazu kommt von rund 3.000 Unterstützern, die zusammen über zwei Millionen US-Dollar oder rund 140 Prozent der anvisierten 1,5 Millionen US-Dollar zusagten. Diese Summe, die zum Erfolg der Kampagne mindestens nötig war, wurde bereits am 10. Oktober, zwei Wochen vor dem Ende der Kampagne erreicht.
Interessierte können sich auch weiterhin für ein Developer Kit für 299 US-Dollar, ein komplettes Librem 5 für 599 US-Dollar oder für eine der anderen Optionen in Kombination mit externen Displays entscheiden. Der Stand am heutigen Morgen weist über 2.131.000 US-Dollar aus und wächst weiter.
[...] Nun geht es zunächst darum, die Hardware weiter einzugrenzen, mit der das Librem 5 ausgeliefert werden wird. Die bisherigen Tests mit Prototypen-Mainboards wurden hauptsächlich mit der i.MX-6-CPU der Firma NXP durchgeführt. Das Ziel ist es, im fertigen Produkt den Nachfolger i.MX-8 einzusetzen, da der i.MX-6 bereits jetzt veraltet ist. Das Problem ist hier jedoch, dass der freie Etnaviv-Treiber für den Vivante-Grafikchip im i.MX-8 noch nicht fertig ist.
In rund einem Monat will Purism zudem bekanntgeben, welche Bedienoberfläche auf dem hauseigenen Betriebssystem PureOS für das Librem 5 entwickelt wird. Sowohl KDE als auch Gnome haben ihre Mitarbeit zugesagt.
https://www.pro-linux.de/news/1/25267/librem-5-erreicht-über-2-millionen-us-dollar.html
Purism startet Finanzierungskampagne für Linux-Smartphone, Pro-Linux, 25.08.2017
Die Firma Purism plant ein Smartphone zu entwickeln, das Sicherheit und Privatsphäre zur Priorität erhebt. FÜr das "Librem 5" wurde jetzt eine Crowdfunding-Kampagne gestartet, bei der man bereits...
https://www.pro-linux.de/news/1/25084/purism-startet-finanzierungskampagne-für-linux-smartphone.html
Device-Check: Tablets below 100 Euro: This models are cheap and do it fine, STERN.de, 30.11.2019
Neben dem Smartphone gewinnen Tablets immer mehr an Bedeutung. Wir stellen Ihnen fünf Geräte vor, die nicht nur günstig, sondern auch alltagstauglich sind.
Ein Tablet unter 100 Euro: Drei Geräte im Verleich
So praktisch Handys auch sind - sie alle haben einen Nachteil: ihr kleines Display. Spätestens wenn Sie eine längere E-Mail verfassen müssen, Ihre sozialen Netzwerke pflegen oder auch einfach nur ein paar Seiten in Ihrem Lieblingsbuch lesen wollen, ist ein großer Bildschirm weitaus angenehmer für die Augen. Und hier kommen Tablets ins Spiel: Sie besitzen ein deutlich größeres Display als gewöhnliche Smartphones und eignen sich genauso gut zum Schreiben, Surfen, Lesen und Spielen. Sofern Sie keine allzu hohen technischen Ansprüche an den PC-Ersatz haben, kostet ein Tablet unter 100 Euro. Drei davon stellen wir Ihnen heute vor.
https://www.stern.de/digital/technik/tablets-unter-100-euro--fuenf-guenstige-geraete-im-vergleich-8791856.html
Still functioning today: loudspeaker
 Loudspeaker Loudspeaker
LogiLink SP0025 stereo with headphone support and volume control from Ebay.de
Price: 4,95 € incl. MwST and shipping costs (year 2013)
DVB-S/DVB-S2 HDTV PCI-card TECHNISAT SkyStar S2, bulk
Order Nr. 702371
5,95 € incl. MwSt, pollin.de
Still functioning today: scientific pocket calculator
Casio fx-85M scientific (pocket) calculator C-Power
fail-safe: solar only (functioning even in quit darkened environments)
Measurements: 13 × 7,5 × 0,8 up to 1,5 cm3
LED-Display: 4,5 ×, 1,2 cm2
Weight: 4 gramm only
4 small solar cells right above the display á 1,8 × 0,9 cm2
Modi: COMP-DEG-RAD-GRA-FIX-SCI-NORM
common arithemtic, fractions, all angle functions and measurements, various coordinate presentations - and calculations and -functions, statistics (Varianz, Standardverteilung, average value etc.), random num, ...
Model from the 80th
Grouped keys: gray key block: 3 × 6 functions with belonging invers functions right above, black key block 5 × 4 keys with two-time light oranged ones for C (single value reset to zero) and AC (complete reset to zero)
easy handling, maintenance-free
35 Euro (year 1986), Hertie
Clever and Smart: All for the "little elephant"
 All-in-one-printer All-in-one-printer
Linux-compatible printer: printer models with Linux printer drivers
As of February 27.
HP Deskjet 2620 from Aldi: Is the 45-Euro-printer be worth?, PC-Magazin.de, 27.02.2020
[...] The speed is too slow, the ink used up fastly and running costs for new ink isn´t econonmy over a longer time as by an even more sophisticated device or laser printer.
https://www.pc-magazin.de/news/hp-deskjet-2620-aldi-drucker-angebot-lohnt-sich-alternative-3201274.html
Favorable & environment-friendly: The first laser-multifunction-printer with refillable cartridge - HP Neverstop 1202nw past the test, PC-WELT.de, 11.04.2020
With the laser printer series Neverstop, HP went the cartridge from ink to toner. Get to know about a first test of the black-and-white-printer Neverstop 1202nw.
https://www.pcwelt.de/produkte/Test-HP-Neverstop-Laser-MFP-1202nw-10789750.html
Still functioning today: Scanner - printer - copyer - fax - memory card station (for hardcopies): Robust, refillable ("life-timed" 250 ml black ink for 9,95 Euro) multi-function-printer Brother DCP-115C (MFC 210) (this is my new printer past HP and Epson that I got from a relative for free, original price: about 79 Euro; 3 years warranty, manufacturing year: 2006), low ink consumption
Print: linux-ready through lpd (1.4.5) or Cups (1.4.5, 1.4.8, mdv2010, pclos2018) and Brother-printer-driver. (32 bit driver even for x86_64 (64bit))
Scan: xsane, scanimage, ...; OCR: tesseract, klara, gocr, ..., x86_64 (64bit) Brother-scanner-driver for Linux
Fax: graphical frontend brpcfax or manually from terminal by test fax: brpcfax -o fax-number=XXXX-XXXX-XXXX testprint.ps, where the postscript-file was created by ghostscript for example per command gs; Brother-fax-driver for Linux
Copy: color-key or blackandwhite-key from device: the document (paper, photo) will be scanned in and then printed out directly
Memory card station: five different card-formats/types; this aims making hardcopies
Printer, photocopier, scanner, fax and SmartMedia®, MultiMedia-, USB-memory-stick, CompactFlash-type1- and xD-Picture-Card-memory card station: several card-slots, card-slots to store files from PC or digicam and to print files directly even without PC (hardcopy).
Features:
Supersilent printout through capillar ink system
4 seperate ink cartridges
Up to 6.000 × 1.200 dpi resolution
Up to 20 sites/min. in s/w and 15 sites/min. color
Borderless printout out of graphic applications
USB 2.0 full speed Interface
3 years manufacturer warranty
All device driver for print, scan and fax for Linux can be downloaded out of the internet from Brother.
Driver for many Linux-kernel 5, 4, 3, 2.4 and 2.6 (CUPS, the Common Unix Printing System by Apple), configuration by http://localhost:631/admin (classes - administration - objects - online-help - printer - jobs)
Printer driver, scanner driver and fax driver for DCP-115C/MFC210C (size per rpm resp. deb: around 10 KB): lpd-driver MFC210Clpr-1.0.2-1.i386.rpm (resp.deb, this 32-bit-driver is also suitable for x86_64 (64bit)) und cupswrapperMFC210C-1.0.0-1.i386.rpm (also for 86_64 (64bit), rpm and deb), scanner-driver for DCP115C/MFC210C: brscan-skey-0.2.4-1.x86_64.rpm and brscan2-0.2.5-1.x86_64.rpm, fax-driver for DCP-115C/MFC210C: brmfcfaxcups-1.0.0-1 and brpmfcfaxlpd-1.0.0-1
Driver for this printer and scanner: Brother Solutions Center, Brother Driver for Linux Distributions, DCP-115C (compatible with MFC-210C):
http://support.brother.com/g/s/id/linux/en/index.html?c=us_ot&lang=en&comple=on&redirect=on
Price for a cartridge (black): 1,99 €, cartridges (C/M/Y and black): 10,96 € (2014, pearl.de)
Many refills out of the plastic bottle
Black ink (refill) bottle 100 ml for Brother printer
Price: 6,88 Euro, free shipping, Ebay 26.11.2021
Seller: printerscout- username, durch Klicken gelangen Sie zum Profil des Mitglieds (128263)- Bewertungspunktestand: 128263 für printerscout99% positive Bewertungen
notice: The cable to the head for the scan can get entangled after some time, so that it should be cleaved on its backside!
produced by the world greatest manufacturer for printer-ink-cartridges following strongest quality guide lines (for example ISO9001)
Refill possible (big tube, 250 ml black ink for about 9,95 Euro)! Most kind of refill ink can be injected directly into the cartridge: either into the whole the ink is floating through or a bored one (that needs to be closed with rubber tape after the refill).
Dull printout, letters and nums got bleached out?
Thin the refill with water, so that the narrrow inflow in the cartridge can be passed better by the ink!
Printheads of the this model get cleaned from time to time automatically.
DCP-115C has got i386-driver only. But why? All of them are also not OpenSource! This can get into conflict serious hard with newer glibc-versions! And this modell also does not only cause more than awful paper jams causing strange (quit hard) manual work for repair, it also does not work, whenever affected by so-called "error 46":
troubleshooting: solving a serious hard error during clean through reset
Linuxforen: Problem of a user with DCP-115C (MFC-210) [solved]
Brother DCP-115C Error: Cleaning
Aus ITwiki
IT wiki > Hardware & Treiber > Drucker > Brother DCP-115C Error: Cleaning
Problem
The printer Brother DCP-115C (MFC210C) shows an error "Cleaning" (Error 46), although there is not any foreign substance within the printer. This problem can not be solved, even if the printer net adapter got unplugged.
.
Solution
The printer has to be resetted (reset):
Menü - Start S/W - 4 × ▴ (arrow to above) to press in the order, in order to opten the maintenance menu
OR
Unplug the net adapter and plug it in again while pressing the menu-key for more than 15 seconds, until the maintenance-menu appears on the display.
▴ (arrow to above) has to be pressed until number 8 is shown in the display. Then press enter.
▴ (arrow to above) until 0 (zerol) and then press enter
Start S/W has to be pressed until PURGE 64xx is shown in the display
With ▴ (arrow to above) and enter of the numbers 2 7 8 3 in sequence press...
Stop
With ▴ (arrow to above) sequentially enter the numbers 9 9
Now the printer got a reset and the error should not occur anymore..
We, Gooken, found out, that this is quit right, but...:
The Printer shows this error on LED. There it is indicated to look into the manual (pdf), but nothing can be find! Also notice, that butzhammer.de explains the solution incorrectly. Its text differs from the following one, and at the beginning in step 2, you have to choose number 80 instead of number 8 ! Here is the whole solution from another source in german language:
The whole problem "ERROR:CLEAN", device error 46, is described once more explicitly on
http://www.helpster.de/beim-brother-dcp-115c-den-fehler-reinigen-beheben_214268:
"Beim Brother DCP-115C den Fehler "Reinigen" beheben
Autor: Roswitha Gladel
Wenn Ihr Brother DCP-115C im Display die Meldung "Fehler: Reinigen" zeigt, kommen zwei verschiedene Ursachen infrage. Beide sind einfach zu beseitigen, der Drucker arbeitet zumindest kurzfristig wieder normal.
Vorsicht: Bei der Fehlermeldung kann es zu einer Tintenüberschwemmung kommen.
Fremdkörper als Ursache der Fehlermeldung beim Brother DCP-115C
Mit der Meldung "Fehler: Reinigen" zeigt der Brother DCP-115C an, wenn ein Fremdkörper im Gerät ist. Es kann sich auch um einen Papierrest handeln. öffnen Sie den Gehäusedeckel und suchen Sie nach einem Gegenstand, der als Fremdkörper betrachtet werden muss. Entfernen Sie diesen.
Schließen Sie den Deckel wieder. Falls die Meldung immer noch erscheint, ziehen Sie den Netzstecker für etwa zwei Minuten. Schließen Sie den Brother DCP-115C wieder an. Die Meldung sollte nun verschwunden sein.
Falls die Meldung "Fehler: Reinigen" immer nach erscheint, haben Sie entweder einen Fremdkörper übersehen oder der Resttintentank ist voll. Wiederholen Sie zur Sicherheit noch einmal die Schritte eins und zwei, um einen Fremdkörper auszuschließen.
"Fehler: Reinigen" wird wegen des Resttintentanks angezeigt
Der Resttintentank ist ein kleines Behältnis unten am Gerät, in dem eine saugfähige Masse ist. Bei jedem Reinigen des Druckkopfes wird Tinte in den Tank gespült. In diesem Tank ist keine Füllstandsanzeige. Die Software geht davon aus, dass er voll ist, wenn eine bestimmte Anzahl von Reinigungen erfolgt ist. Sie sollten daher nie unnötigerweise diese Reinigungen durchführen. Durch die Eingabe eines bestimmten Codes können Sie das Zählwerk wieder zurücksetzen. Der Drucker ist dann wieder funktionsfähig, selbst wenn der Tank voll ist.
Die Eingabe des Codes erfolgt über die Bedientasten, nach demselben Schema wie Sie auch die Kopienanzahl einstellen. Drücken Sie zunächst auf die Taste "Menü" und dann auf "Start". Nun müssen Sie die Pfeil-nach-oben-Taste viermal schnell drücken. Sie sind nun im Hauptmenü ("Maintenance menü").
Beim Brother MFC den Fehler "Reinigen" beheben
Die Anzeige "Fehler: Reinigen" kann bei den Brother-Druckern des Typs MFC verschiedene …
Geben Sie über die Pfeiltaste die Zahl 80 ein. Sie müssen also achtmal auf die Pfeiltaste drücken, dann auf "Eing" und wieder auf die Pfeiltaste, bis die Null erscheint. Bestätigen Sie über die "Eing"-Taste. Im Display sollte nun "00:00 XX:XX OK" stehen. (Statt XX:XX ist die Uhrzeit zu sehen, also zum Beispiel 12:00 wenn es 12 Uhr ist)
Drücken Sie nun auf die Start-Taste, bis im Display "PURGE:XXXXX" zu sehen ist (X steht für Ziffern). Geben Sie wie beschrieben über die Pfeil-Taste und "Eing" die Ziffern 2, 7, 8 und 3 ein. Im Display soll nun "PURGE:00000" zu sehen sein.
Drücken Sie die Start-Taste, bis im Display "FLUSH:XXXXXXXXXX" zu sehen ist. Geben Sie nun wieder die Ziffern 2, 7, 8 und 3 ein. Im Display steht nun "FLUSH:0000000000".
Ziehen Sie den Netzstecker für zwei Minuten und stecken Sie ihn wieder ein. Der Drucker geht nun wieder. ( Er geht nun wirklich!, Anm., Gooken )
Anmerkung: Einige User berichten, dass sie, nachdem PURGE:00000 im Display stand, über die Stopp-Taste und die Eingabe der Ziffern 9 und 9 zum Ziel gelangt sind. Denken Sie daran, dass Sie mit diesen Eingaben den Zähler des Brother DCP-115C auf Null setzen und daher die Meldung "Fehler: Reinigen" nicht mehr erscheint, obwohl der Tank voll ist und überlaufen kann. Versierte Bastler können das Gerät zerlegen und den Tank leeren. Der richtige Weg ist, den Tank so schnell wie möglich in einem Fachbetrieb leeren und neue Füllmasse einsetzen zu lassen.
Weiterlesen:
Beim Brother MFC den Fehler "Reinigen" beheben
MFC 215c - den Druckkopfintensivreinigungsmodus durchführen
Beim Brother MFC 235C den Druckkopf reinigen - so gehts
Epson Stylus SX210: Düsen reinigen - so gelingt es
übersicht: Alles zum Thema Computerzubehör
Hallo, ich habe einen Brother DCP-115C Drucker der momentan
Kundenfrage
Hallo, ich habe einen "Brother DCP-115C" Drucker der momentan nicht funktioniert !
Die Fehlermeldung ""Fehler:Reinigen" ist angezeigt. Ich habe das Handbuch gelesen aber es hat nichts geholfen. Der Vorschlag von dem Brother Support Team ( per E-mail ) hilft auch nicht. Sie vermuten das der Reingungszyclus voll ist, und das ich den Zählerstand zurücksetzen kann! Ich habe dies ohne Erfolg probiert; ich muss den Netzstecker trennen, Menüknopf drücken, Netzstecker wieder einstecken, dann mit dem Menüknopf immer noch gedrückt, warten bis "Maintainance" angezeigt wird. Diese Meldung kommt nicht, nur "1. Kopie", wobei ich immer nur die Tinte eingeben kann. Nichts blockiert den Drucker; kein Papier, Büroklammer u.s.w. übrigens, der Druckkopf befindet sich ganz rechts wo ich nicht hinkomme. Danke XXXXX XXXXX Hilfe die ich von Ihnen bekommen kann
MFG M Bunzel . E-mail : [email protected]
Gepostet: vor 6 Jahren.
Kategorie: Elektronik
13757879507Diesen Beitrag teilen
Experte: Tronic hat geantwortet vor 6 Jahren.
Hallo,
vielen Dank, dass Sie Justanswer benutzen.
Die Fehlermeldung besagt, dass der Resttintenbehälter voll ist und getauscht werden muss. Die genannte Prozedur müsste funktionieren. Hier ist die Anleitung dazu:
http://www.brother.de/g3.cfm/s_page/122060/s_name/faqfehlerreinigendcp
Ansonsten könnten Sie noch Folgendes probieren:
1.) Den Menu und den Start/schwarz Knopf gemeinsam drücken. Danach den Pfeil nach oben 4mal drücken und die Eingabetaste betätigen um ins Hauptmenu zu gelangen.
2.) Mit dem Pfeil nach oben drücken bis "8" erscheint und wieder "Eingabe" drücken. Mit dem Pfeil nach oben drücken bis "null" erscheint und wieder "Eingabe" drücken.
3.) Nun den Knopf Start S/W 25mal drücken, bis "purge counter" erscheint.
4.) Nun die folgenden Zahlen einzeln über die Pfeiltasten auswählen und mit "Eingabe" bestätigen: 2, 7, 8 und 3. (Nach jeder Eingabe erscheint die Counter- Meldung wieder, nicht irritieren lassen). Bei erfolgreicher Operation wird der Zähler mit 0000 angezeigt.
5.) Stopp-Knopf drücken um ins Hauptmenu zurück zu gehen.
6.) Zweimal hintereinander mit den Pfeiltasten die "9" auswählen und einzeln mit "Eingabe" bestätigen um ins Standby-Menü zurück zu gehen.
Stellen Sie Ihre eigene Frage zum Thema Elektronik.
Fragen Sie diesen ExpertenFragen Sie alle Experten
13731581453Kunde: hat geantwortet vor 6 Jahren.
Hallo, danke für Ihre schnelle Antwort, leider hat es mir nicht geholfen. Der erste Teil Ihrer Antwort, aus dem "Brother Handbuch", hatte ich bereits ausprobiert, ohne Erfolg. Ihr zweiter Vorschlag, in dem ich "Menü + Start S/W" zusammen drücken sollte, dann mit dem Pfeil 4 mal oben drücken, bringt mir wieder die Meldung " 1. Kopie", und nach "Eingaben" komme ich auf "1. Papiersorte", aber kein Hauptmenü. Nach drücken von "Menü + Start S/W" zusammen habe ich nur die folgende Auswahl: 1. Kopie, 0. Inbetriebnahme, 3. Ausdrücke, 2. Speicherkarte. Die einzige Möglichkeit nach drücken der Pfeiltaste nach oben auf einen "8" zu kommen, ist wenn ich der Option "2. Speicherkarte" wähle, aber in den folgenden Optionen ist "0" nie gezeigt. Habe ich eine andere Möglichkeit, oder ist es so dass der Tintebehälter ausgetauscht sein muß,und brauche ich dann einen Brother Servicepartner ?
MFG M Bunzel
13757879507Experte: Tronic hat geantwortet vor 6 Jahren.
Solange der Zähler nicht zurückgesetzt ist geht das Gerät nicht mehr, unabhängig davon ob der Resttintentank nun getauscht wurde oder nicht.
Eine andere Tastenkombination als diese beiden kenne ich für Brother DCP-Geräte nicht und Sie sind auch der erste Fall dieser Art für mich. Tut mir Leid, aber dann fürchte ich werden Sie um den Brother Servicepartner leider nicht herum kommen. Ihr Anzahlung erhalten Sie dann natürlich wieder zurück."
Fax: sending test fax: brpcfax -o fax-number=XXXX-XXXX-XXXX testprint.ps
Scanner: If xsane does not work anymore (memory access violation), reinstall the scanner drivers (DCP-115C: 64bit). If the RPMsof the driver can not be installed correctly, enpack them with file-roller and copy the directories into the belonging locations and reconfigure by calling MCC/Scanner.
Printer driver for Brother DCP-115C/MFC210C (Umfang: ca. 10KB pro rpm bzw. deb): lpd-driver MFC210Clpr-1.0.2-1.i386.rpm (bzw. deb) and cupswrapperMFC210C-1.0.0-1.i386.rpm (this one can also has to be used for x86_64 (64bit), rpm and deb), scanner-driver for DCP115C/MFC210C: brscan-skey-0.2.4-1.x86_64.rpm and brscan2-0.2.5-1.x86_64.rpm, Fax-driver for DCP-115C/MFC210C: brmfcfaxcups-1.0.0-1 and brpmfcfaxlpd-1.0.0-1
 Packages needed for CUPS: kernel-5.4.110 (pclos) or kernel-4.20.13 (pclos) with hald (pclos), mkinitrd (pclos), nash (pclos), dracut (el6) and glibc (pclos), cups (pclos: 1.4.6, mdv2010.1: 1.4.5), cups-windows (pclos, MS Windows printer driver (dll)), cups-libs (el6) resp. lib64cups2 (pclos, mdv2010.1), glibc (i686), nss-softokn-freebl (i686), libfreebl, busb (el6) or lib64usb (fc, rosa2014.1 mdv2010), pygobject2 (el6) and python-cups (el6, if python(el6) is installed, otherwise use python-cups (mdv2010.1) and python-gobject2 (mdv2010.1)), a2ps (el6, mdv), paps (el6, mdv), paps-libs (el6), printer-filters (el6, mdv), printer-tools (mdv), printer-utils (mdv), tcsh (el6, csh-compatible), pstoedit (rosa2014.1, el6, mdv), pslib (el6), lib64pslib (mdv), lib64pst4 (mdv), ghostscript (rosa2014.1, el6, mdv), gutenprint (el6, mdv) and html2ps (el6, mdv), system-config-printer (mdv2010.2, el6), system-config-printer-libs (mdv2010.2, el6), system-config-printer-kde (mdv2010.2, el6) and system-config-printer-udev (el6, mdv2010), task-printing (mdv2010.2), task-printing-hp (mdv2010.2), task-printing-epson (mdv2010.2), task-printing-..., task-printing-misc (mdv2010.2), task-printing-scanner (mdv2010.2) and task-printing-server (mdv2010.2), foomatic-db, foomatic-db-engine, foomatic-db-hpijs, foomatic-filters, hpijs (el6), libgnomeprint2 (mdv), min12xxw (KonicaMinolta PagePro 1xxW), openprinting-ppds (el6, mdv2010.1), postscript-ppds (mdv2010.1), hplip-hpijs-ppds (mdv2010.1), pnm2ppa (mdv2010.1), pxljr (HP ColorLaserJet 35xx/36xx), splix (Samsung SPL2 b/w and SPLc color laser), - are they installed and do they work? Enter a2ps, gs, html2ps and pstoedit into terminal to check it out. Does ps2pdf work? Check this out by a pdf-file as an input, otherwiese libraries libgs.so.8, libgs.so.9 or a similar one still has to be installed. Packages needed for CUPS: kernel-5.4.110 (pclos) or kernel-4.20.13 (pclos) with hald (pclos), mkinitrd (pclos), nash (pclos), dracut (el6) and glibc (pclos), cups (pclos: 1.4.6, mdv2010.1: 1.4.5), cups-windows (pclos, MS Windows printer driver (dll)), cups-libs (el6) resp. lib64cups2 (pclos, mdv2010.1), glibc (i686), nss-softokn-freebl (i686), libfreebl, busb (el6) or lib64usb (fc, rosa2014.1 mdv2010), pygobject2 (el6) and python-cups (el6, if python(el6) is installed, otherwise use python-cups (mdv2010.1) and python-gobject2 (mdv2010.1)), a2ps (el6, mdv), paps (el6, mdv), paps-libs (el6), printer-filters (el6, mdv), printer-tools (mdv), printer-utils (mdv), tcsh (el6, csh-compatible), pstoedit (rosa2014.1, el6, mdv), pslib (el6), lib64pslib (mdv), lib64pst4 (mdv), ghostscript (rosa2014.1, el6, mdv), gutenprint (el6, mdv) and html2ps (el6, mdv), system-config-printer (mdv2010.2, el6), system-config-printer-libs (mdv2010.2, el6), system-config-printer-kde (mdv2010.2, el6) and system-config-printer-udev (el6, mdv2010), task-printing (mdv2010.2), task-printing-hp (mdv2010.2), task-printing-epson (mdv2010.2), task-printing-..., task-printing-misc (mdv2010.2), task-printing-scanner (mdv2010.2) and task-printing-server (mdv2010.2), foomatic-db, foomatic-db-engine, foomatic-db-hpijs, foomatic-filters, hpijs (el6), libgnomeprint2 (mdv), min12xxw (KonicaMinolta PagePro 1xxW), openprinting-ppds (el6, mdv2010.1), postscript-ppds (mdv2010.1), hplip-hpijs-ppds (mdv2010.1), pnm2ppa (mdv2010.1), pxljr (HP ColorLaserJet 35xx/36xx), splix (Samsung SPL2 b/w and SPLc color laser), - are they installed and do they work? Enter a2ps, gs, html2ps and pstoedit into terminal to check it out. Does ps2pdf work? Check this out by a pdf-file as an input, otherwiese libraries libgs.so.8, libgs.so.9 or a similar one still has to be installed.
Packages for system-config-printer and task-printing:... (?): -> install python-cups (el6), desktop-file-utils (el6), gnome-python2-gnomekeyring (el6), hplip-libs (el6), libnotify (el6), libxml2 (el6), libxml2-python (el6), nmap (el69, notification-daemon (el6), pygtk2 (el6), pygtk2-libglade (el6), rhpl (el6)
Always use hal (pclos) and not hal like hal (el6): DCP-115C does not work anymore because of errrors from /usr/lib/cups/filters/pdftops! Look out for a good working rpm of grep too to get installed!
For python (mdv2010.1) instead of python (el6) you need instead: python-cups (mdv2010.2), python-gobject2 (mdv2010.2), gnome-python (mdv2010.1), hplip-model-data (mdv2010.2), notification-daemon (mdv2010.1), pygtk2.0 (mdv2010.2), pygtk2-libglade (mdv2010.2), python-notify (mdv2010.1), python-rhpl (mdv2010.1) and python-smbc (mdv2010.1)
Printer-configuration: 1) MCC section hardware under printer, 2) browser by localhost:631, 3) systemsettings or gnome-control-center, section printer or by the 4) printer-applet appearing in the sytem-tray (mga3)
Check out ps2pdf with any pdf-file as an input. If an error-message appears, install libgs.so.8 (resp. libgs.so.9 or any file like this).
Installation of a printer-driver by PPD-file: MCC( method 1) ) , then choose "add a printer", choose the PPD-file (for DCP-115C from directory /usr/share/cups/model): ready. You can start printing now, but also set the default printer, the colors like grayscale or truecolor and the letter size (should be A4) up from there too. All this is possible with method 2) up to 4).
Ink: price for one cartdrige: see above. Alternatively you can refill it. Notice: It is well-known, that not all kind of ink can be used: glands and advections can constipate.
DCP-115C is printing fine all the years through. Install and start cups and configure the printers by PPD-files from Linux-installation-DVD, manufacturer-CD or out of the internet or openprinting.org. If not, try to get driver-material in order to generate it or to program it manually (cupsddk (mdv2010.2)).
Three methods can be used to integrate the PPD-file and to configure the printer: localhost:631, system-config-printer or lpadmin. Generally, if a printer strikes, just try to activate him already by terminal (konsole): "cupsenable printer_name", here "cupsenable DCP-115C" . If this does not work, add users like user, root and lp to the group lpadmin, possible by MCC. It is also possible, that another kernel is in use, that is not belonging to the distribution anymore. In our case choose a kernel for mdv2010 up to mdv2012. Check out ownership (chown root) and access-rights (chmod 755) of the driver, for DCP-115C those one in /lib and /usr/local/Brother. Printout a testside by MCC. Going on with general cases for printer-troubleshooting, remind, that all ghostprint-packages should not be upgraded and therefore always belong to the distribution and version (mdv2010). Configure the printer in MCC section hardware, confirm the printer in the menu named server as a network-printer. Debugging in error-cases is possible by clicking into the printer-applet. This provides significant tipps to solve the problem.
DCP-115C should work fine with: cups-1.4.1 (el6) or cups-1.4.5 (mdv2010.1) or cups-1.4.8 (mdv2011), kernel-2.6.39.4-5.1 actualized (patched e.g. from address see under "updating") or not (mdv2011), ghostscript (mdv2010.1, el6, fc14), gutenprint (mdv2010.1, el6), printer-xxx (mdv2010.2, el6), glibc (mga7, mga5, rosa2014.1, el6 and mdv2010, mdv2011, mdv2012).
Terminal-commands: usb-devices (see listed driver=... ), lsusb (printer-entry by name and model), lpstat -t (lists the printer-state and -jobs), lprm (for the remove of printer-jobs), lpadmin (for the manual configuration of a printer. PPD-files can be entered too), lpotions, lpinfo -v (lists the printer-connection resp. the device-URI, and helps to answer the question, if the printer is connected or not)
important: lpinfo -v, lpstat -t and lpadmin
Example:
lpadmin -p Brother-DCP-115C -i /dev/usblp0 -P /usr/share/cups/model/bmfc210cups.ppd -v usb://Brother-DCP-115C?serial=BROE7F... -u allow:lp,user,root,lpadmin,sys,surfuser
resp. (directly using kernel module usblp):
lpadmin -p Brother-DCP-115C -v file:/dev/usb/lp0 -m /etc/cups/ppd/Brother-DCP-115C.ppd -P /usr/share/cups/model/brmfc210c_cups.ppd -u allow:user,lp,lpadmin,sys,root
In UNIX/Linux the print-command is:
lpr -P Brother-DCP-115C
The name of the printer past option -P is the one, you manually set in system-config-priinter and also the name for the belonging printer-queue.
But does lpr really exist in /usr/bin? Some programs might not print out. If not, just link it to the printer command:
ln -sf /usr/bin/lpr-cups /usr/bin/lipr
Does Ghostscript (mdv or el6) function? Type in: "gs -help"
Does tcsh work? start tcsh and look for any error-messages.
Renew the printer-drivers. Remove old printers. Enpack the archive and copy the directories into belonging location. Call system-config printer to reconfigure the printer.
Browser-configuration of CUPS: type "localhost:631" into the address-line.
Sometimes, the device-usb-file does not provide enough access. This file can be found out by lsusb: Bus-ID and Device-ID beneath the product-ID:vendor-ID, for example 001 002 04f9:018c, this corresponds to /dev/usb/1/2 with vendor-ID 04f9 (Brother) and product-ID 018c (DCP-115C). Those two ID are always shown during system-boot, before init is starting.
A udev-rule can solve the problem:
enter in /etc/udev/rules.d/10-local.rules (if not existant, type touch -t 10-local.rules, in order to type):
ACTION=="add", SUBSYSTEM=="usb", ENV{DEVTYPE}=="usb_device", ATTRS{idVendor}=="04f9", ATTRS{idProduct}=="018c", KERNEL=="lp*", GROUP=="lp", MODE:="666"
We strongly recommend to use this rule!
Notice, that a self-compiled kernel can lead into a complete unusable printing-system, same past installation of (plenty of) updates! Cups, gutenprint and ghostscript should have the same version as the kernel. If nothing helps, beware the uncompiled kernel (vmlinuz) in /boot beneath the self-compiled, use a print-server with mdv2010.2 and tested CUPS-1.4.5 (mdv2010.1) or one or more USB-sticks with Linux Operating System and Office-Software like OpenOffice to install CUPS and the printer-drivers resp. ppd-file. Debian Linux can also be installed from a Knoppix-DVD onto an own partition. From Debian.org updating is possible as much as installing CUPS.
Printing-Systems: CUPS (mdv2010.1) and/or lpd alias lprng (mdv2010) with lprng-client (mdv2010.1). Like CUPS, the filter and the ppd-file have to be entered into /etc/printcap.
Have a look into the log-files on error: /var/log/cups/... , especially error_log!
CUPS-Troubleshooting: https://wiki.archlinux.org/index.php/CUPS/Troubleshooting
Following packages must be installed: .
Pakete: cups, cups-libs (el6) resp. lib64cups2 (pclos, mdv2010.1) glibc, libusb (el6) or lib64usb (rosa2014.1 mdv2010), libminiupnpc ( Library and tool to control NAT in UPnP-enabled routers), pygobject2 (el6) and python-cups (el6, if python(el6) is installed, otherwise python-cups (pclos, mdv2010.1) and python-gobject2 (mdv2010.1)), a2ps (el6, mdv), paps (el6, mdv), paps-libs (el6), printer-filters (el6, mdv), printer-tools (mdv), printer-utils (mdv), pstoedit (el6, mdv), ghostscript (el6, mdv), gutenprint (el6, mdv) and html2ps (el6, mdv), system-config-printer (mdv2010.2, el6), system-config-printer-libs (mdv2010.2, el6), system-config-printer-kde (mdv2010.2, el6) and system-config-printer-udev (el6, mdv2010), task-printing (mdv2010.2), task-printing-hp (mdv2010.2), task-printing-epson (mdv2010.2), task-printing-..., task-printing-misc (mdv2010.2), task-printing-scanner (mdv2010.2) and task-printing-server (mdv2010.2) are installiert and do work? a2ps, gs, html2ps and pstoedit can be checked directly in the terminal by entering their name. Does ps2pdf work? This can be checked out by a pdf-file for an input. Otherwise reinstall libgs.so.8, libgs.so.9 for ghostscript or a similar library.
In some cases, one or a few access-rights have to be set again for driver-files or files of cups listed in belonging CUPS-packages owned by root to chmod 755. One file interesting here is named together with its path within (/usr/lib/) during a testprint of one of the added printers in MCC, in our case it is the driver-file named libbrplwrapper.so. The scanner of this all-in-one-printer-model only does its work too, if the directory /usr/local owned by root (chown root:root /usr/local) is set to chmod 755.
Access-Rights for the CUPS belonging directories incl. those with the ppd-files:
chmod 775
/usr/local
/usr/local/*.ppd
/var/spool
/usr/lib/cups
/usr/share/cups
/usr/share/ppd
/etc/cups/ppd
/usr/local/share/ppd
/usr/bin/cupstestppd
/usr/share/ppd
/usr/share/ppd/gs-esp/model/
/usr/share/gs-esp/8.15/lib/cbjc600.ppd
/usr/share/gs-esp/8.15/lib/ghostpdf.ppd
/usr/share/gs-esp/8.15/lib/cbjc800.ppd
/usr/share/cups/model/stcolor2.ppd
/usr/share/cups/model/stcolor.ppd
The ppd-file must be contained in /usr/share/cups/model.
Device-URI of the printer DCP-115C (MFC210C): file:/dev/usb/lp0, usb://dev/usb/lp0 or usb://Brother/DCP-115C?serial=BROE7F871829
Starting the CUPS-daemon: sh /etc/init.d/cups restart; starting the lpd daemon (lprd (mdv2010): sh /etc/init.d/lpd restart
/etc/printcap: records the printers out of /etc/cups/printers.conf (hierin sind jeweils vermerkt und können manuell verarbeitet werden: Drucker, DeviceURI, filter (!), state (idle, ...), owner, access-rights and more), /usr/lib/cups/filter/pdftops failed: In this case, set up cups-pdf.ppd in MCC/Printer.
/usr/lib/cups/filter/brldwrapperMFC failed.: set the access-rights!
lpstat -t
 Error-messages cat /var/log/cups/error_log and solution (permissons (OpenSuSE) messed up our printer system completely):
Error-messages cat /var/log/cups/error_log and solution (permissons (OpenSuSE) messed up our printer system completely):
E Unable to set ACLs on root certificate "/var/run/cups/certs/0" - Operation not supported -> set access-rights for this and use option acl in /etc/fstab for the root-partition (reiserfs, ext4).
E :18:37:03 +0100] cupsdAuthorize: pam_authenticate() returned 7 (Authentication failure)! -> localhost:631 or modify or exchange /etc/cups/cupsd.conf.
E Pointer error (Treiber), libc.so.6, free()-pointer-error or munmap-chunk()-error ->: exchange glibc (libc.so.6) (maybe by downgrading, for the 32-bit-printer-driver for DCP-115C install glibc(mdv2011, i686)) or renew the printer driver or cups-version, in our example from cups-1.4.5 (mdv2010.2): cups1.4.4 (fc14) with lib64cups2 (mdv2010.2) or cups-libs-1.4.4 (fc14), version without localhost:631.
E "Unable to bind socket for address 127.0.0.1:631 - Address already in use. unn "Unable to bind broadcast socket - Address already in use." -> in /etc/cups/cupsd.conf set "Port 631" instead of "localhost:631".
D [CGI] error: Failed to create /tmp/.hplip -> ... this debug will be solved by the next:
N Group and SystemGroup cannot use the same groups! -> /etc/cups/cupsd.conf: set "SystemGroup wheel root lp"
E child error exited on signal ...-> exchange libcups2.so out of rpm lib64cups2.
E no printout: cups-error_log (/var/log/cups/error_log) is error-free, but there still is no (paper) printout out -> depending on KDE also install system-config-printer (mdv2010.2), system-config-printer-libs (mdv2010.2) und system-config-printer-udev (el6) together with all task-printing (mdv2010.2)! This error is mentioned in detail further below.
http://www.linuxquestions.org/questions/linux-newbie-8/cant-print-to-second-cups-printer-516051-print/
2-2.Open /usr/local/Brother/cupswrapper/cupswrapperXXXXX to edit.
2-3.Look for the line with "lpadmin -p XXXXXX -E -v .......".
2-4.Change "-m" to "-P" in the line
2-5.Add the file-path of the PPD file written in the line.
the file path = "/usr/share/cups/model/"
Example
BEFORE(no wrap):
lpadmin -p MFC9420CN -E -v usb://dev/usb/lp0 -m brmfc9420cn.ppd
AFTER(no wrap):
lpadmin -p MFC9420CN -E -v usb://dev/usb/lp0 -P
/usr/share/cups/model/brmfc9420cn.ppd
The cupswrapper from printer contains a script in csh "#! /bin/csh", which not runs per default with most Linux distros. Try to change in deb/rpm to "#! /bin/sh" or to run in csh terminal. Better solution is to use option --nodeps "rpm -ihv --nodeps MFC5440CNlpr-1.0.2-1.i386.rpm". I recommend to use this option for scanner driver too.-
...
This excerpt is the key in our problem:
Code:
[Job 99] Error: error occurred at print phase !!
[Job 99] GPL Ghostscript 8.54: Unrecoverable error, exit code 1
[Job 99] cat: write error: Broken pipe
[Job 99] *** glibc detected *** free(): invalid pointer: 0xb7e39020 *** # the whole Brother-Support was not able to solve this problem; to avoid this, install a glibc (i586) with belonging libstdc++ and libsigc++; dmesg: did usblp really start? -&get; exchange libusb and usb; kernel-module usblp (for the device /dev/usb/lp0) does not function: blacklist, exchange this module (kernel-4.9) ) or install a new kernel-version (in our case kernel-4.9.137 (pclos, alternative: el6) -> kernel-4.9.x or kernel-4.20.13 with functioning module usblp, mkinitrd (mga2), nash (mga2), dracut (el6) and glibc (pclos, i586: mga6); check out the links to /lib/ld.so.* and /lib/libc.so.6; eventually install brother-lpd-drivers-extra (ubuntu, amd64 (64 bit driver) or i586 (32 bit driver) and in addition brother-cups-wrapper-extra (ubuntu) and brother-lpr-drivers-common (ubuntu); if nothing helps, install the printer for a rescue-system on usb-memory stick! The /lib and /usr/lib/ for glibc (i586) from USB-stick can be copied to hdd/sdd (x86_64). Access-rights: chmod 755 /lib, chmod 755 /usr/lib, chmod 755 /etc/cups/* (chown root:sys, cupsd.conf and printers.conf: chown root:nogroup ), chmod 755 -R /var/spool/cups (chown root:nogroup), chmod 755 /usr/lib/cups/filter/* (chown root:sys), chmod 755 /usr/local/Brother (chown root:root ); notice: we removed group named nogroup as much as user and group named anonymous right before. In order to avoid errrors depending on access-rights (especially upon /dev/usblp0 resp. /dev/usb/lp0), the two user lp and lpadmin and in serious hard cases also the normal user named "t;user", should always be groups of root.
In fact, installation of kernel-5.4.110 (pclos) or kernel-4.20.13 (pclos) with mkinitrd (pclos), nash (pclos) and dracut (el6) solves the whole problem!
The printer works (making printouts) with kernel 2.6.39.5 (mdv), 4.12.12 (pclos), 4.20.6 (pclos), but not all kernel-versions (resp. those with buggish or locking kernel-module usblp).
Notice: mdv2010.2 from USB-memory-stick with kernel 2.6.33 lets DCP-115C print with original 32-bit-printer-driver even without usblp.
In any case, scanner and fax work fine with original 64-bit Brother-DCP-115C-drivers as much as making copies.
[Job 99] /usr/local/Brother/lpd/filterMFC5840CN: line 44: 4427 Done(1) eval cat DOLLARINPUT_TEMP
[Job 99] 4429 | DOLLARPSCONV DOLLARPSCONV_OP
[Job 99] 4430 Aborted | DOLLARBRCONV DOLLARBRCONV_OP
PID 3536 (/usr/lib/cups/filter/brlpdwrapperMFC5840CN) exited with no errors.
Here are some kernel, usblp won´t work for the 32-bit driver for DCP-115C (MFC-210C) because of error invalid pointer":
- 4.9.137 (pclos)
- 4.9.56 (kernel-server, mga6)
- > 4.14.12 (pclos)
Some glibc cause the error "invalid pointer" for this driver too:
- glibc-2.29 (pclos)
- ...
Whereas functioning:
- glibc-2.26 (pclos)
- glibc-2.22 (mga6)
- ...
- glibc-2.11 (mdv2010.1, mdv2011)
You see GPL Ghostscript; the same was happening with ESP Ghostscript. I just changed the /usr/bin/gs-symlink to see if it would change anything.
Cups goes on to process the job to the printer. You can see it lighting up "receiving" and settling down as the printjob has finished and no data is comming while there is none because of the above error.
I´m not able to pinpoint the origin of this problem. That is why I"m not able to give you a solution.
I hope I have a ubuntu 6.06 install on my pc and retry to have some comparison in installed versions.
Hoping to hear soon from Brother support in order to get this worked out.
If I know you will know;)
Some little comments:
I found this hint in some printer howto.
try to use nmap:
Code:
nmap -v -A <ip-address-of-printer>
Code:
Interesting ports on 192.168.123.109:
Not shown: 1693 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Brother printer ftpd 1.11
23/tcp open telnet Brother printer telnetd
515/tcp open printer
9100/tcp open jetdirect?
Service Info: Device: printer
The telnet password seems to be access
my printer-url is: lpd://<ipaddress>
Printer Brother DCP-115C for print - scan - copies - fax did function on " Universal Linux" with / Multifunktionsdrucker Brother DCP-115C für Drucken - Scannen - Kopieren und Faxen funktionierte auf "Universal-Linux" mit:
cups (pclose2017, mdv2010.2, 1.4.5), lib64cups2 (mdv2010.2), glibc (mga7, mga5, rosa2014.1, x86_64 (64bit)), glibc (mga6, mdv2010.2, 2.11.1-8.3mnb2, i686 (32 Bit) for the DCP-115C 32-bit-printer-driver only, for 64 bit use glibc (mga6, mga5 or rosa2014.1)), rest: glibc-common (el6, x86_64) or (mga7, mga5), glibc-.... (el6, x86_64), bluez-cups (pclos2017, mdv2010.2), cups-bjnp (pclos2017, el6), cups-browsed (rosa2014.1, mdv2010.1), cups-common (pclos2017, mdv2010.2, 1.4.5), cups-drivers (pclos2017.1, mdv2010.1), cups-drivers-bjnp (pclos2017, mdv2010.1), cups-drivers-capt (pclos2017, mdv2010.1), cups-dirvers-foo2kyo (pclos2017, mdv2010.1), cups-drivers-foo2zjs (pclos2017, mdv2010.1), cups-drivers-lbp660 (pclos2017, mdv2010.1), cups-drivers-lxx74 (pclos2017, mdv2010.1), cups-crivers-m2300w (pclos2017, mdv2010.1), cups-drivers-magicolor2430dl (pclos2017, mdv2010.1), cups-drivers-magicolor2530dl (pclos2017, mdv2010.1), cups-drivers-magicolor-5430dl (pclos2017, mdv2010.1), cups-drivrs-magicolor5440dl (pclos2017, mdv2010.1), cups-drivers-pegg (pclos2017, mdv2010.1), cups-drivers-ptouch (pclos2017, mdv2010.1), cups-drivers-splix (pclos2017, mdv2010.1), cups-filesystem (el7), cups-libs (el6), cups-lpd (el6), cups-php (el6), cups-pk-helper (el6), cups-serial (mdv2010.2, 1.4.3), cups-windows ( pclos2017, mdv2010.0), cups-x2go (el6), ghostscript-cups (fc18, mdv2010.1), gnome-cups-manager (mdv2010.1), gutenprint-cups (mdv2010.1), glib64gnomecups-1.0_1 (mdv2010.1), lib64gnomecupsui-1.0_1 (mdv2010.1), lib64cups (plcos2017, mdv2010.1), libcups (mdv2010.1, 1.4.5, 32 bit), libgnomecups (mdv2010.1), perl-Net-Cups (el6), php-cups (mdv2010.1), python-cups (el6), ghostscript (el6, rosa2014.1), ghostscript (fc18, mdv2010.1, rosa2014.1), ghostscript-common (mdv2010.1, rosa2014.1), ghostscript-cups (fc18, mdv2010.1), ghostscript-doc (mdv2010.1), ghostscript-dvipdf (mdv2010.1), ghostscript-fonts (el6, rosa2014.1), ghostscript-fonts-std (OpenSuSE, Version 9.00 Release 4.8.1, mdv2010.1), ghostscript-gtk (el6, rosa2014.), ghostscript-module-X (mdv2010.1), ghostscript-X (mdv2010.1), lib64gs8 (mdv2010.1) resp. lib64gs9 (rosa2014.1), OpenPrintingPPDs-ghostscript (OpenSuSE, Version 4.0.0 Release 15.1.1, mdv2010.1), a2ps (el6), emacs-a2ps (el6), sed (el6), libusb (el6, x86_64 and i686), libusb-compat0.1_4 (mdv2010.1), libusb1 (el6), libusb1.0_0 (mdv2010.1), libusbg (fc24), libusbg-utils (fc24), libusbmuxd (fc25), libusbmuxd-utils (fc25), libusbmuxd1 (mdv2010.1), libusbx (fc26), usbmuxd (el6)libgnomeprint (mdv2010.1), libgnomeprint22 (el6), libgnomeprintui mdv2010.1), libgnomeprintui22 (el6), pnm2ppa (el6), postscript-ppds (mdv2010.1), nss-softokn-freebl (el6), nss-softokn (el6), foomatic (el6), foomatic-db (mdv2010.1), foomatic-db-engine (mdv2010.1), foomatic-db-filesystem (el6), foomatic-db-ppds (el6), foomatic-filters (mdv2010.2), gutenprint-foomatic (el6), lib64usb-compat0.1_4 (mdv2010.1, rosa2014.1), lib64usb1.0_0 (rosa2014.1, mdv2010.1), lib64usbip0 (mdv2010.1), lib64usbmuxd1 (mdv2010.1), lib64usbmuxd4 (rosa2014.1, mdv2010.1), lib64usbredirparser1 (rosa2014.1, mdv2010.1), lib64usbx1.0_0 (rosa2014.1, mdv2010.1) , grep (el6), jasper (fc26, el6), jasper-utils (fc26, el6), jasper-libs (fc26, el6), pstoedit (mdv2010.1), lib64pstoedit0 (mdv2010.1), pslib (el6), lib64pslib0 (rosa2014.1), lib64pst4 (mdv2010.1), paps (mdv2008.1, mdv2010.1), html2ps (el6, mdv2010.1, Openmandriva2015), xhtml2ps (mdv2010.1, OpenMandriva2015), gutenprint (el6), gutenprint-common (mdv2010.1), gutenprint-cups (mdv2010.1), gutenprint-secputil (mdv2010.1), gutenprint-extras (el6), guenprint-foomatic (el6), gutenprint-gimp2 (mdv2010.1), gutenprint-ijs (mdv2010.1), gutenprint-plugin (el6), lib64gutenprint2 (mdv2010.1), lib64gutenprintui2_1 (mdv2010.1), system-config-printer (mdv2010.1), system-config-printer-libs (mdv2010.1), system-config-printer-kde (mdv2010.2), system-config-printer-udev (el6), task-printing (mdv2010.1, mga1), task-printing-canon (mdv2010.1, mga1), task-printing-epson (mdv2010.1, mga1), task-printing-hp (mdv2010.1, mga1), task-printing-lexmark (mdv2010.1, mga1), task-printing-misc (mdv2010.1, mga1), task-printing-okidata (mdv2010.1, mga1), task-printing-scanning (mdv2010.1, mga1), task-printing-server (mdv2010.1, mga1), sed (el6), hplip (el6), qpdf-libs (el6), tcsh (el6, csh), min12xxw (mdv2010.1, KonicaMinolta PagePro 1xxW), splix (el6, Samsung SPL2 b/w and SPLC color laser), pxljr (HP ColorLaserJet 35xx/36xx), hplip-hpijs-ppds (mdv2010.1), postscript-ppds (mdv2010.1), drv_z42 (mdv2010.1), hplip-hpijs (mdv2010.1), stylewriter (mdv2010.1), ml85p (mdv2010.1), pbm2lwxl (mdv2010.1), pentaxpj (mdv2010.1), ppmtomd (mdv2010.1), groff (el6, mdv2010.1), gutenprint-gimp2 (mdv2010.1 or uninstalled), lesstif (mdv2010.1), mpage (mdv2010.1, el6), netcat-traditional (mdv2010.1), net-tools (mdv2010.1, el6), nmap (mdv2010.1, el6), printer-testpages (mdv2010.1), printer-utils (mdv2010.1), scli (mdv2010.1), ImageMagick (el6)
https://forums.gentoo.org/viewtopic-t-422995-start-50.html
1. unmask cups-1.2* (~x86)
2. emerge cups tcsh a2ps
3. rpm2targz the 2 packages
4. tar xzf the 2 packages
5. cp the files over from usr/* to the corresponding folders
6. mv usr/local/Brother /usr/local/.
7. change in /usr/local/Brother/cupswrapper/cupswrapper... /etc/init.d/cups to /etc/init.d/cupsd
8. run /usr/local/Brother/cupswrapper/cupswrapper...
9. create a symbolic link from /usr/local/Brother/inf/brMFC...rc to /usr/local/Brother/inf/brPrintList (ln -sf brHL2040rc brPrintList )
10.a. copy /usr/lib/cups/filter/br... to /usr/libexec/cups/filter/br..
10.b. for amd64 copy /usr/lib/cups/filter/br... to /usr/lib64/cups/filter/br
..
11. restart cupsd
12. type in 127.0.0.1:631
13. set "change printer" and select the uri (usually /dev/usb/lp0)
14. restart cupsd
15. print test page
16. if it doesn´t work
17. cat test.txt | /usr/local/Brother/lpd/filterMFC5840CN
18. look, what it shows; correct errors (creating symbolic links)
especially step 17 is important, then you´ll see if it prints or is missing a symbolic link of libraries
good luck !
That´s part of the problem, they don´t say anything abnormal. There´s nothing in syslog regarding the USB port or CUPS. /var/log/cups/error_log merely shows the processes were started and then nothing else.
Running dmesg shows the USB device connected. It appears as one of the processes is stalling but it´s unknown which.
ok, then let´s check some more:
usbfs in /etc/fstab, check ?
permissions of /dev/usb/lp*, check ? (crw-rw---- 1 root lp 180, 0 2008-01-27 10:29 /dev/usb/lp0)
Problem solved for https://www.unixboard.de/threads/zugriff-auf-dev-usb-lp0-regeln.36194/:
Add into /etc/cups/cupsd.conf the follwoing code:
FileDevice YES # for Device-URI file:/dev/usb/lp0
dann ein
Code:
# /etc/init.d/cupsd restart
# lpadmin -p DCP-110C -E -v file:/dev/usb/lp0 -P /usr/share/cups/model/brdcp110c_cups.ppd
and the printer and scanner works!
Create /etc/udev/rules.d/100-local.rules with the entry
SUBSYSTEM=="usb",ATTRS{idVendor}=="04f9",ATTRS{idProduct}=="018c",GROUP="lp",MODE="0666"
/lib/udev/rules.d/50-udev-default.rules
# libusb device nodes
SUBSYSTEM=="usb", ENV{DEVTYPE}=="usb_device", MODE="0666"
# printer
KERNEL=="parport[0-9]*", GROUP="lp"
SUBSYSTEM=="printer", KERNEL=="lp*", GROUP="lp"
SUBSYSTEM=="ppdev", GROUP="lp"
SUBSYSTEM=="usb", KERNEL=="lp*", SYMLINK+="usb%k", GROUP="lp"
KERNEL=="lp[0-9]*", GROUP="lp", MODE="0777"
KERNEL=="irlpt[0-9]*", GROUP="lp"
# hplip and cups 1.4+ use raw USB devices, so permissions should be similar to
# the ones from the old usblp kernel module
SUBSYSTEM=="usb", ENV{DEVTYPE}=="usb_device", ENV{ID_USB_INTERFACES}=="", IMPORT{program}="usb_id --export %p"
SUBSYSTEM=="usb", ENV{DEVTYPE}=="usb_device", ENV{ID_USB_INTERFACES}==":0701*:", GROUP="lp", MODE="0666"
and eventually create a desktop-file in /usr/share/autostart with the include
EXEC=chmod 666 /dev/usb/lp0
In /etc/fstab/ add
usbfs usbfs /proc/bus/usb usbfs auto,devmode=0666 0 0 (tipps by us, Gooken)
/etc/cups/printers.conf:
# Printer configuration file for CUPS v1.4.8 (pclos2017) / v1.4.5 (mdv2010.1) / v1.4.6 (pclos, mdv2011)
# Written by cupsd on 2017-10-02 21:50
# DO NOT EDIT THIS FILE WHEN CUPSD IS RUNNING
<DefaultPrinter B-DCP-115C> # grayscale and default
Info B-DCP-115C
Location localhost.localdomain
MakeModel Brother MFC-210C CUPS v1.1
DeviceURI file:/dev/usb/lp0 # This solution is recommended for 4-kernel. The proprietary printer-driver has to be already installed through lpadmin or system-config-printer. Now this default printer can be turned off and on at any time for any printout.
State Idle
StateTime 1506965498
Type 12587084
Filter application/vnd.cups-raw 0 -
Filter application/vnd.cups-command 0 commandtops # Testpage out of system-config-printer (el6, mdv)
Filter application/vnd.cups-postscript 0 brlpdwrapperMFC210C # ppd: /usr/share/cups/model/brlpdwrapperMFC210C
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy stop-printer
</Printer>
<Printer BRFAX>
Info BRFAX
MakeModel Brother BRMFCFAX for CUPS
DeviceURI usb://dev/usb/lp0
State Idle
StateTime 1481736691
Type 12587012
Filter application/vnd.cups-raw 0 -
Filter application/vnd.cups-command 0 commandtops
Filter application/vnd.cups-postscript 0 brfaxfilter
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy stop-printer
</Printer>
<Printer Brother-DCP-115C> # colored printout
Info Brother DCP-115C
Location localhost.localdomain
MakeModel Brother MFC-210C CUPS v1.1
DeviceURI usb://Brother/DCP-115C?serial=BROE7F871829
State Idle
StateTime 1506963970
Type 12587084
Filter application/vnd.cups-raw 0 -
Filter application/vnd.cups-command 0 commandtops
Filter application/vnd.cups-postscript 0 brlpdwrapperMFC210C
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy abort-job
</Printer>
<Printer MFC210C>
Info MFC210C
DeviceURI usb://dev/usb/lp0
State Idle
StateTime 1480819042
Type 4194308
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy abort-job
</Printer>
Following man cupsd.conf for
/etc/cups/cupsd.conf :
# Show troubleshooting information in error_log.
LogLevel debug # set back to error, after problems cat /var/log/cups/error_log got solved
FileDevice YES # for Device-URI file:/dev/usb/lp0
SystemGroup root sys lpadmin
Group sys
User lp
# Allow remote access
# Listen *:631
Listen localhost:631 # most secure
# Port 631
Listen /var/run/cups/cups.sock
# Share local printers on the local network.
Browsing On
BrowseOrder allow,deny
BrowseRemoteProtocols
BrowseAddress @LOCAL
BrowseLocalProtocols CUPS dnssd
DefaultAuthType Basic
DefaultEncryption Never # also try: DefaultEncryption IfRequested
<Location />
# Allow shared printing...
Order allow,deny
Allow @LOCAL
</Location>
<Location /admin>
# Restrict access to the admin pages...
Order allow,deny
</Location>
<Location /admin/conf>
AuthType Default
Require user @OWNER @SYSTEM
# Restrict access to the configuration files...
Order allow,deny
</Location>
<Policy default>
<Limit Create-Job Print-Job Print-URI Validate-Job>
Require user @OWNER @SYSTEM
AuthType Basic
order deny,allow
Allow 192.186.178.*
</Limit>
<Limit Send-Document Send-URI Hold-Job Release-Job Restart-Job Purge-Jobs Set-Job-Attributes Create-Job-Subscription Renew-Subscription Cancel-Subscription Get-Notifications Reprocess-Job Cancel-Current-Job Suspend-Current-Job Resume-Job CUPS-Move-Job CUPS-Get-Document>
AuthType Basic
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit CUPS-Add-Modify-Printer CUPS-Delete-Printer CUPS-Add-Modify-Class CUPS-Delete-Class CUPS-Set-Default CUPS-Get-Devices>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit Pause-Printer Resume-Printer Enable-Printer Disable-Printer Pause-Printer-After-Current-Job Hold-New-Jobs Release-Held-New-Jobs Deactivate-Printer Activate-Printer Restart-Printer Shutdown-Printer Startup-Printer Promote-Job Schedule-Job-After CUPS-Accept-Jobs CUPS-Reject-Jobs>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit CUPS-Authenticate-Job>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit All>
AuthType Basic
Order deny,allow
Allow 192.168.178.*
</Limit>
</Policy>
<Policy authenticated>
<Limit Create-Job Print-Job Print-URI Validate-Job>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit Send-Document Send-URI Hold-Job Release-Job Restart-Job Purge-Jobs Set-Job-Attributes Create-Job-Subscription Renew-Subscription Cancel-Subscription Get-Notifications Reprocess-Job Cancel-Current-Job Suspend-Current-Job Resume-Job CUPS-Move-Job CUPS-Get-Document>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit CUPS-Add-Modify-Printer CUPS-Delete-Printer CUPS-Add-Modify-Class CUPS-Delete-Class CUPS-Set-Default>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.186.178.*
</Limit>
<Limit Pause-Printer Resume-Printer Enable-Printer Disable-Printer Pause-Printer-After-Current-Job Hold-New-Jobs Release-Held-New-Jobs Deactivate-Printer Activate-Printer Restart-Printer Shutdown-Printer Startup-Printer Promote-Job Schedule-Job-After CUPS-Accept-Jobs CUPS-Reject-Jobs>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit Cancel-Job CUPS-Authenticate-Job>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
Allow 192.168.178.*
</Limit>
<Limit All>
Order deny,allow
Allow 192.186.178.*
</Limit>
</Policy>
Printcap
/etc/cups/subscriptions.conf
# Subscription configuration file for CUPS v1.4.8 (pclos2017) / v1.4.5 (mdv2010.1) / v1.4.6 (mdv2011)
# Written by cupsd on 2017-10-02 18:52
NextSubscriptionId 139
<Subscription 129>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507036519
NextEventId 158
</Subscription>
<Subscription 130>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507039634
NextEventId 128
</Subscription>
<Subscription 131>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507040411
NextEventId 119
</Subscription>
<Subscription 132>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507041607
NextEventId 100
</Subscription>
<Subscription 133>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507040411
NextEventId 119
</Subscription>
<Subscription 132>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507041607
NextEventId 100
</Subscription>
<Subscription 133>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507050366
NextEventId 81
</Subscription>
<Subscription 135>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507051672
NextEventId 48
</Subscription>
<Subscription 137>
Events printer-state-changed printer-restarted printer-shutdown printer-stopped printer-added printer-deleted job-state-changed job-created job-completed job-stopped job-progress
Owner username
LeaseDuration 86400
Interval 0
ExpirationTime 1507060321
NextEventId 26
</Subscription>
/etc/printcap
BRFAX:
:mx=0:
:sd=/var/spool/lpd/BRFAX:
:sh:
:lp=/dev/usb/lp0:
:if=/usr/local/Brother/lpd/filterBRFAX:
Well, have a look at the gentoo-wiki.com, if there´s more tips to this "problem", check ?
search for brother printer cups ubuntu @ google, check ?
usbfs is applied in /etc/fstab to give devices mode 0666, lp0 comes up this way as well... no other tips or suggestions work. I tried the Ubuntu forums for them prior, everyone is basically saying the same methods on how to get it up and running, yet even following them shows no progress on my end.
Cupsd starts with an error message can not find or something like it: This depends on the cups version: Look out for /usr/bin/lp. If this file is missing and lp-cups is present instead, link lp-cups to lp (same for alle lp-xyz-cups): ln -sf /usr/bin/lp-cups /usr/bin/lp.
Set access rights upon /usr/lib64/cups/*, /usr/lib/cups/*, /usr/share/cups/*, /etc/cups., /var/spool/cups, /lib/libc*, /lib64/libc*, /usr/lib/libc* und /usr/lib64/libc/* through "chmod 775 -R", for guaranteed access eventually set belonging setfacl for user lp, user, root and group lp, root and wheel (see section for ACL)
/etc/passwd -> wie oben aufgelistet
http://foo2zjs.rkkda.com/forum/read.php?12,2342
Try changing DeviceURI in /etc/cups/printers.conf to:
DeviceURI file:///dev/usb/lp0
and /etc/cups/cupsd.conf to:
FileDevice Yes # for Device-URI file:/dev/usb/lp0
Then, restart CUPS (e.g. cd foo2zjs; sudo make cups).
This is NOT my problem... it is a CUPS problem.
https://www.experts-exchange.com/questions/28176266/Printing-problem-on-Linux.html
In order to prevent paper jam for DCP-115C (MFC-210C), always put the paper into the paper-shaft as far as possible!
Still /var/log/cups/error_log: Following messages like these should occur in sequence:
I [19:57:24 +0100] Loaded MIME database from /usr/share/cups/mime and /etc/cups: 36 types, 47 filters...
D 19:57:24 +0100] Loading printer BRFAX...
D [19:57:24 +0100] load_ppd: Loading /var/cache/cups/BRFAX.ipp4...
D [19:57:24 +0100] cupsdRegisterPrinter(p=0x7f603a9b9380(BRFAX))
D :19:57:24 +0100] Loading printer Brother-DCP-115C...
D :19:57:24 +0100] load_ppd: Loading /var/cache/cups/Brother-DCP-115C.ipp4...
D :19:57:24 +0100] cupsdRegisterPrinter(p=0x7f603a9af870(Brother-DCP-115C))
D :19:57:24 +0100] Loading printer MFC210C...
D :19:57:24 +0100] cupsdMarkDirty(P-----)
D :19:57:24 +0100] cupsdSetBusyState: Dirty files
D :19:57:24 +0100] load_ppd: Loading /etc/cups/ppd/MFC210C.ppd...
D :19:57:24 +0100] cupsdRegisterPrinter(p=0x7f603a9acb90(MFC210C))
Configuration: /etc/cups/cupsd.conf
For /etc/cups/cupsd.conf (cups 1.4.2-74 (el6) resp. cups 1.4.5 (mdv2010.2) we prefered cups-1.4.6 with lib64cups (pclos2016, mdv2010.2) or libcups.so.2 out of lib64cups (pclos2016 or mdv2010.2) copied into /usr/lib64 against the child-error on exit not started cupsd after starting cupsd, DCP-115C / MFC210C, up-to-date (patched) kernel-2.6.39.4-5, udev rule for vendor-id:product-id for usb-port in /etc/udev/rules.d, ghostscript (el6): >gs: OK (!), gutenprint (el6), either with blacklisted usblp within /etc/modprobe.d/blacklist-mdv or not blacklisted usblp, we prefer: not blacklisted (!), result cat /var/log/cups/error_log: error free, "wrote 1 page/s" ):
FileDevice YES # for device-URI file:/dev/usb/lp0 (created by module usblp)
LogLevel debug # set it back to warn, if all problems are solved
SystemGroup root sys lpadmin
Group sys
User lp
# Allow remote access
# Listen *:631
Listen localhost:631 # most secure
# Port 631
Listen /var/run/cups/cups.sock
# Enable printer sharing and shared printers.
Browsing On
BrowseOrder allow,deny
BrowseAllow all
# BrowseRemoteProtocols CUPS
BrowseAddress @LOCAL
BrowseLocalProtocols CUPS dnssd
DefaultAuthType Basic
DefaultEncryption Never
<Location />
# Allow shared printing and remote administration...
AuthType Basic
# Require user @OWNER @SYSTEM
Order allow,deny
Allow all
</Location>
<Location /admin>
# Allow remote administration...
AuthType Default
Require user @OWNER @SYSTEM
Order allow,deny
Allow @LOCAL
</Location>
<Location /admin/conf
AuthType Default
Require user @OWNER @SYSTEM
# Allow remote access to the configuration files...
Order allow,deny
Allow @LOCAL
</Location>
<Policy default>
<Limit Create-Job Print-Job Print-URI Validate-Job>
Require user @OWNER @SYSTEM
AuthType Basic
order deny,allow
# Allow 127.0.0.1:631 # depending on cups-version 1.4.2 (el6) or 1.4.5 (mdv2010)
Allow 192.186.178.*
</Limit>
<Limit Send-Document Send-URI Hold-Job Release-Job Restart-Job Purge-Jobs Set-Job-Attributes Create-Job-Subscription Renew-Subscription Cancel-Subscription Get-Notifications Reprocess-Job Cancel-Current-Job Suspend-Current-Job Resume-Job CUPS-Move-Job CUPS-Get-Document>
Require user @OWNER @SYSTEM
AuthType Basic
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit CUPS-Add-Modify-Printer CUPS-Delete-Printer CUPS-Add-Modify-Class CUPS-Delete-Class CUPS-Set-Default CUPS-Get-Devices>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit Pause-Printer Resume-Printer Enable-Printer Disable-Printer Pause-Printer-After-Current-Job Hold-New-Jobs Release-Held-New-Jobs Deactivate-Printer Activate-Printer Restart-Printer Shutdown-Printer Startup-Printer Promote-Job Schedule-Job-After CUPS-Accept-Jobs CUPS-Reject-Jobs>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit CUPS-Authenticate-Job>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit All>
AuthType Basic
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
</Policy>
<Policy authenticated>
<Limit Create-Job Print-Job Print-URI Validate-Job>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit Send-Document Send-URI Hold-Job Release-Job Restart-Job Purge-Jobs Set-Job-Attributes Create-Job-Subscription Renew-Subscription Cancel-Subscription Get-Notifications Reprocess-Job Cancel-Current-Job Suspend-Current-Job Resume-Job CUPS-Move-Job CUPS-Get-Document>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit CUPS-Add-Modify-Printer CUPS-Delete-Printer CUPS-Add-Modify-Class CUPS-Delete-Class CUPS-Set-Default>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.186.178.*
</Limit>
<Limit Pause-Printer Resume-Printer Enable-Printer Disable-Printer Pause-Printer-After-Current-Job Hold-New-Jobs Release-Held-New-Jobs Deactivate-Printer Activate-Printer Restart-Printer Shutdown-Printer Startup-Printer Promote-Job Schedule-Job-After CUPS-Accept-Jobs CUPS-Reject-Jobs>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit Cancel-Job CUPS-Authenticate-Job>
AuthType Basic
Require user @OWNER @SYSTEM
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.168.178.*
</Limit>
<Limit All>
Order deny,allow
# Allow 127.0.0.1:631
Allow 192.186.178.*
</Limit>
</Policy>
Printcap
/etc/cups/printers.conf (result of lpadmin...):
# Printer configuration file for CUPS v1.4.5
# Written by cupsd on 2016-12-09 00:36
# DO NOT EDIT THIS FILE WHEN CUPSD IS RUNNING
<DefaultPrinter Brother-DCP-115C>
Info Brother DCP-115C
Location localhost.localdomain
MakeModel Brother MFC-210C CUPS v1.1
DeviceURI usb://Brother/DCP-115C?serial=BROE7F871829
State Idle
StateTime 1481240189
Type 12587084
Filter application/vnd.cups-raw 0 -
Filter application/vnd.cups-postscript 0 brlpdwrapperMFC210C
Filter application/vnd.cups-command 0 commandtops
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy abort-job
</Printer>
<Printer Brother-DCP-115C-2>
Info Brother DCP-115C
Location localhost.localdomain
MakeModel Brother MFC-210C CUPS v1.1
DeviceURI usb://Brother/DCP-115C
State Idle
StateTime 1481240172
Type 12587084
Filter application/vnd.cups-raw 0 -
Filter application/vnd.cups-postscript 0 brlpdwrapperMFC210C
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy abort-job
</Printer>
<Printer MFC210C>
Info MFC210C
DeviceURI usb://dev/usb/lp0
State Idle
StateTime 1480819042
Type 4194308
Accepting Yes
Shared Yes
JobSheets none none
QuotaPeriod 0
PageLimit 0
KLimit 0
OpPolicy default
ErrorPolicy abort-job
</Printer>
Check out, if cupsd has started. Do so, if not, or install another version.
Printing a page (opened with kwrite), /var/log/cups/error_log (last 50), D means debug-message, I: info, W: warn and E: error:
...
D [10/Dec/2016:22:26:19 +0100] Adding default job-sheets values "none,none"...
I [10/Dec/2016:22:26:19 +0100] [Job 468] Adding start banner page "none".
D [10/Dec/2016:22:26:19 +0100] Discarding unused job-created event...
I [10/Dec/2016:22:26:19 +0100] [Job 468] Queued on "Brother-DCP-115C" by "anonymous".
D [10/Dec/2016:22:26:19 +0100] Returning IPP successful-ok for Create-Job (ipp://localhost:631/printers/Brother-DCP-115C) from localhost
D [10/Dec/2016:22:26:19 +0100] cupsdSetBusyState: Dirty files
D [10/Dec/2016:22:26:19 +0100] cupsdReadClient: 12 POST /printers/Brother-DCP-115C HTTP/1.1
D [10/Dec/2016:22:26:19 +0100] cupsdSetBusyState: Active clients and dirty files
D [10/Dec/2016:22:26:19 +0100] cupsdAuthorize: Authorized as anonymous using PeerCred
D [10/Dec/2016:22:26:19 +0100] cupsdReadClient: 12 1.1 Send-Document 1
D [10/Dec/2016:22:26:19 +0100] Send-Document ipp://localhost:631/printers/Brother-DCP-115C
D [10/Dec/2016:22:26:19 +0100] cupsdIsAuthorized: username="anonymous"
D [10/Dec/2016:22:26:19 +0100] [Job 468] Auto-typing file...
D [10/Dec/2016:22:26:19 +0100] [Job 468] Request file type is application/pdf.
D [10/Dec/2016:22:26:19 +0100] cupsdMarkDirty(----J-)
I [10/Dec/2016:22:26:19 +0100] [Job 468] File of type application/pdf queued by "anonymous".
I [10/Dec/2016:22:26:19 +0100] [Job 468] Adding end banner page "none".
D [10/Dec/2016:22:26:19 +0100] cupsdMarkDirty(----J-)
D [10/Dec/2016:22:26:19 +0100] cupsdMarkDirty(----J-)
D [10/Dec/2016:22:26:19 +0100] cupsdSetBusyState: Active clients, printing jobs, and dirty files
D [10/Dec/2016:22:26:19 +0100] Discarding unused printer-state-changed event...
D [10/Dec/2016:22:26:19 +0100] [Job 468] job-sheets=none,none
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[0]="Brother-DCP-115C"
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[1]="468"
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[2]="anonymous"
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[3]="Unbenannt"
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[4]="1"
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[5]="media=BrA4 job-uuid=urn:uuid:xxxxx originating-host-name=localhost time-at-creation=1481405179 time-at-processing=1481405179 AP_D_InputSlot="
D [10/Dec/2016:22:26:19 +0100] [Job 468] argv[6]="/var/spool/cups/d00468-001"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[0]="CUPS_CACHEDIR=/var/cache/cups"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[1]="CUPS_DATADIR=/usr/share/cups"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[2]="CUPS_DOCROOT=/usr/share/cups/doc"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[3]="CUPS_FONTPATH=/usr/share/cups/fonts"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[4]="CUPS_REQUESTROOT=/var/spool/cups"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[5]="CUPS_SERVERBIN=/usr/lib/cups"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[6]="CUPS_SERVERROOT=/etc/cups"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[7]="CUPS_STATEDIR=/var/run/cups"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[8]="HOME=/tmp"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[9]="PATH=/usr/lib/cups/filter:/usr/bin:/usr/sbin:/bin:/usr/bin"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[10]="SERVER_ADMIN=root@localhost.localdomain"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[11]="SOFTWARE=CUPS"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[12]="TMPDIR=/tmp"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[13]="USER=root"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[14]="CUPS_SERVER=/var/run/cups/cups.sock"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[15]="CUPS_ENCRYPTION=IfRequested"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[16]="IPP_PORT=631"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[17]="CHARSET=utf-8"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[18]="LANG=de_DE.UTF-8"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[19]="PPD=/etc/cups/ppd/Brother-DCP-115C.ppd"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[20]="RIP_MAX_CACHE=8m"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[21]="CONTENT_TYPE=application/pdf"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[22]="DEVICE_URI=usb://Brother/DCP-115C?serial=BROE7F871829"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[23]="PRINTER_INFO=Brother DCP-115C"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[24]="PRINTER_LOCATION=localhost.localdomain"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[25]="PRINTER=Brother-DCP-115C"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[26]="CUPS_FILETYPE=document"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[27]="FINAL_CONTENT_TYPE=printer/Brother-DCP-115C"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[28]="AUTH_U****"
D [10/Dec/2016:22:26:19 +0100] [Job 468] envp[29]="AUTH_P****"
I [10/Dec/2016:22:26:19 +0100] [Job 468] Started filter /usr/lib/cups/filter/pdftops (PID 13127)
I [10/Dec/2016:22:26:19 +0100] [Job 468] Started filter /usr/lib/cups/filter/brlpdwrapperMFC210C (PID 13128)
I [10/Dec/2016:22:26:19 +0100] [Job 468] Started backend /usr/lib/cups/backend/usb (PID 13129)
D [10/Dec/2016:22:26:19 +0100] Discarding unused job-state-changed event...
D [10/Dec/2016:22:26:19 +0100] Returning IPP successful-ok for Send-Document (ipp://localhost:631/printers/Brother-DCP-115C) from localhost
D [10/Dec/2016:22:26:19 +0100] cupsdSetBusyState: Printing jobs and dirty files
D [10/Dec/2016:22:26:19 +0100] [Job 468] STATE: +connecting-to-device
D [10/Dec/2016:22:26:19 +0100] Discarding unused printer-state-changed event...
D [10/Dec/2016:22:26:19 +0100] [Job 468] Started filter pdftops (PID 13133)
D [10/Dec/2016:22:26:19 +0100] [Job 468] Started filter pstops (PID 13134)
D [10/Dec/2016:22:26:20 +0100] [Job 468] Page = 595x842; 9,9 to 586,833
D [10/Dec/2016:22:26:20 +0100] [Job 468] slow_collate=0, slow_duplex=0, slow_order=1
D [10/Dec/2016:22:26:20 +0100] [Job 468] Before copy_comments - %!PS-Adobe-3.0
D [10/Dec/2016:22:26:20 +0100] [Job 468] %!PS-Adobe-3.0
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%Creator:
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%LanguageLevel: 3
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%DocumentSuppliedResources: (atend)
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%DocumentMedia: plain 595 842 0 () ()
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%BoundingBox: 0 0 595 842
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%Pages: 1
D [10/Dec/2016:22:26:20 +0100] [Job 468] %%EndComments
D [10/Dec/2016:22:26:20 +0100] [Job 468] Before copy_prolog - %%BeginDefaults
D [10/Dec/2016:22:26:20 +0100] [Job 468] Before copy_setup - %%BeginSetup
D [10/Dec/2016:22:26:20 +0100] [Job 468] Before page loop - %%Page: 1 1
D [10/Dec/2016:22:26:20 +0100] [Job 468] Copying page 1...
D [10/Dec/2016:22:26:20 +0100] [Job 468] pagew = 577.0, pagel = 824.0
D [10/Dec/2016:22:26:20 +0100] [Job 468] bboxx = 0, bboxy = 0, bboxw = 595, bboxl = 842
D [10/Dec/2016:22:26:20 +0100] [Job 468] PageLeft = 9.0, PageRight = 586.0
D [10/Dec/2016:22:26:20 +0100] [Job 468] PageTop = 833.0, PageBottom = 9.0
D [10/Dec/2016:22:26:20 +0100] [Job 468] PageWidth = 595.0, PageLength = 842.0
=======================================================!!!
D [10/Dec/2016:22:26:20 +0100] [Job 468] Wrote 1 pages...
=======================================================!!!
D [10/Dec/2016:22:26:20 +0100] [Job 468] PID 13134 (pstops) exited with no errors.
D [10/Dec/2016:22:26:20 +0100] [Job 468] PID 13133 (pdftops) exited with no errors.
D [10/Dec/2016:22:26:20 +0100] PID 13127 (/usr/lib/cups/filter/pdftops) exited with no errors.
D [10/Dec/2016:22:26:24 +0100] PID 13128 (/usr/lib/cups/filter/brlpdwrapperMFC210C) exited with no errors.
D [10/Dec/2016:22:26:38 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:26:38 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:26:38 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:26:38 +0100] cupsdNetIFUpdate: ""eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:26:38 +0100] Report: clients=1
D [10/Dec/2016:22:26:38 +0100] Report: jobs=66
D [10/Dec/2016:22:26:38 +0100] Report: jobs-active=1
D [10/Dec/2016:22:26:38 +0100] Report: printers=3
D [10/Dec/2016:22:26:38 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:26:38 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:26:38 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:26:38 +0100] Report: stringpool-total-bytes=23872
I [10/Dec/2016:22:26:41 +0100] Saving job cache file "/var/cache/cups/job.cache"...
D [10/Dec/2016:22:26:41 +0100] cupsdSetBusyState: Printing jobs
D [10/Dec/2016:22:27:40 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:27:40 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:27:40 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:27:40 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:27:40 +0100] Report: clients=1
D [10/Dec/2016:22:27:40 +0100] Report: jobs=66
D [10/Dec/2016:22:27:40 +0100] Report: jobs-active=1
D [10/Dec/2016:22:27:40 +0100] Report: printers=3
D [10/Dec/2016:22:27:40 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:27:40 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:27:40 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:27:40 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:28:42 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:28:42 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:28:42 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:28:42 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:28:42 +0100] Report: clients=1
D [10/Dec/2016:22:28:42 +0100] Report: jobs=66
D [10/Dec/2016:22:28:42 +0100] Report: jobs-active=1
D [10/Dec/2016:22:28:42 +0100] Report: printers=3
D [10/Dec/2016:22:28:42 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:28:42 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:28:42 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:28:42 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:29:44 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:29:44 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:29:44 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:29:44 +0100] cupsdNetIFUpdate: "eth0" = "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:29:44 +0100] Report: clients=1
D [10/Dec/2016:22:29:44 +0100] Report: jobs=66
D [10/Dec/2016:22:29:44 +0100] Report: jobs-active=1
D [10/Dec/2016:22:29:44 +0100] Report: printers=3
D [10/Dec/2016:22:29:44 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:29:44 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:29:44 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:29:44 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:30:46 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:30:46 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:30:46 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:30:46 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:30:46 +0100] Report: clients=1
D [10/Dec/2016:22:30:46 +0100] Report: jobs=66
D [10/Dec/2016:22:30:46 +0100] Report: jobs-active=1
D [10/Dec/2016:22:30:46 +0100] Report: printers=3
D [10/Dec/2016:22:30:46 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:30:46 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:30:46 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:30:46 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:31:20 +0100] Closing client 12 after 300 seconds of inactivity...
D [10/Dec/2016:22:31:20 +0100] cupsdCloseClient: 12
D [10/Dec/2016:22:31:48 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:31:48 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:31:48 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:31:48 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:31:48 +0100] Report: clients=0
D [10/Dec/2016:22:31:48 +0100] Report: jobs=66
D [10/Dec/2016:22:31:48 +0100] Report: jobs-active=1
D [10/Dec/2016:22:31:48 +0100] Report: printers=3
D [10/Dec/2016:22:31:48 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:31:48 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:31:48 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:31:48 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:32:50 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:32:50 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:32:50 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:32:50 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:32:50 +0100] Report: clients=0
D [10/Dec/2016:22:32:50 +0100] Report: jobs=66
D [10/Dec/2016:22:32:50 +0100] Report: jobs-active=1
D [10/Dec/2016:22:32:50 +0100] Report: printers=3
D [10/Dec/2016:22:32:50 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:32:50 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:32:50 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:32:50 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:33:52 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:33:52 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:33:52 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:33:52 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:33:52 +0100] Report: clients=0
D [10/Dec/2016:22:33:52 +0100] Report: jobs=66
D [10/Dec/2016:22:33:52 +0100] Report: jobs-active=1
D [10/Dec/2016:22:33:52 +0100] Report: printers=3
D [10/Dec/2016:22:33:52 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:33:52 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:33:52 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:33:52 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:34:54 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:34:54 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:34:54 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:34:54 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:34:54 +0100] Report: clients=0
D [10/Dec/2016:22:34:54 +0100] Report: jobs=66
D [10/Dec/2016:22:34:54 +0100] Report: jobs-active=1
D [10/Dec/2016:22:34:54 +0100] Report: printers=3
D [10/Dec/2016:22:34:54 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:34:54 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:34:54 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:34:54 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:35:56 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:35:56 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:35:56 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:35:56 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:35:56 +0100] Report: clients=0
D [10/Dec/2016:22:35:56 +0100] Report: jobs=66
D [10/Dec/2016:22:35:56 +0100] Report: jobs-active=1
D [10/Dec/2016:22:35:56 +0100] Report: printers=3
D [10/Dec/2016:22:35:56 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:35:56 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:35:56 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:35:56 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:36:58 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:36:58 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:36:58 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:36:58 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:36:58 +0100] Report: clients=0
D [10/Dec/2016:22:36:58 +0100] Report: jobs=66
D [10/Dec/2016:22:36:58 +0100] Report: jobs-active=1
D [10/Dec/2016:22:36:58 +0100] Report: printers=3
D [10/Dec/2016:22:36:58 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:36:58 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:36:58 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:36:58 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:38:00 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:38:00 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:38:00 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:38:00 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:38:00 +0100] Report: clients=0
D [10/Dec/2016:22:38:00 +0100] Report: jobs=66
D [10/Dec/2016:22:38:00 +0100] Report: jobs-active=1
D [10/Dec/2016:22:38:00 +0100] Report: printers=3
D [10/Dec/2016:22:38:00 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:38:00 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:38:00 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:38:00 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:39:02 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:39:02 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:39:02 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:39:02 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:39:02 +0100] Report: clients=0
D [10/Dec/2016:22:39:02 +0100] Report: jobs=66
D [10/Dec/2016:22:39:02 +0100] Report: jobs-active=1
D [10/Dec/2016:22:39:02 +0100] Report: printers=3
D [10/Dec/2016:22:39:02 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:39:02 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:39:02 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:39:02 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:40:04 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:40:04 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:40:04 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:40:04 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:40:04 +0100] Report: clients=0
D [10/Dec/2016:22:40:04 +0100] Report: jobs=66
D [10/Dec/2016:22:40:04 +0100] Report: jobs-active=1
D [10/Dec/2016:22:40:04 +0100] Report: printers=3
D [10/Dec/2016:22:40:04 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:40:04 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:40:04 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:40:04 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:41:06 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:41:06 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:41:06 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:41:06 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:41:06 +0100] Report: clients=0
D [10/Dec/2016:22:41:06 +0100] Report: jobs=66
D [10/Dec/2016:22:41:06 +0100] Report: jobs-active=1
D [10/Dec/2016:22:41:06 +0100] Report: printers=3
D [10/Dec/2016:22:41:06 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:41:06 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:41:06 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:41:06 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:42:08 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:42:08 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:42:08 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:42:08 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:42:08 +0100] Report: clients=0
D [10/Dec/2016:22:42:08 +0100] Report: jobs=66
D [10/Dec/2016:22:42:08 +0100] Report: jobs-active=1
D [10/Dec/2016:22:42:08 +0100] Report: printers=3
D [10/Dec/2016:22:42:08 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:42:08 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:42:08 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:42:08 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:43:10 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:43:10 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:43:10 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:43:10 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:43:10 +0100] Report: clients=0
D [10/Dec/2016:22:43:10 +0100] Report: jobs=66
D [10/Dec/2016:22:43:10 +0100] Report: jobs-active=1
D [10/Dec/2016:22:43:10 +0100] Report: printers=3
D [10/Dec/2016:22:43:10 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:43:10 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:43:10 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:43:10 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:44:12 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:44:12 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:44:12 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:44:12 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:44:12 +0100] Report: clients=0
D [10/Dec/2016:22:44:12 +0100] Report: jobs=66
D [10/Dec/2016:22:44:12 +0100] Report: jobs-active=1
D [10/Dec/2016:22:44:12 +0100] Report: printers=3
D [10/Dec/2016:22:44:12 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:44:12 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:44:12 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:44:12 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:45:14 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:45:14 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:45:14 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:45:14 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:45:14 +0100] Report: clients=0
D [10/Dec/2016:22:45:14 +0100] Report: jobs=66
D [10/Dec/2016:22:45:14 +0100] Report: jobs-active=1
D [10/Dec/2016:22:45:14 +0100] Report: printers=3
D [10/Dec/2016:22:45:14 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:45:14 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:45:14 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:45:14 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:46:16 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:46:16 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:46:16 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:46:16 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:46:16 +0100] Report: clients=0
D [10/Dec/2016:22:46:16 +0100] Report: jobs=66
D [10/Dec/2016:22:46:16 +0100] Report: jobs-active=1
D [10/Dec/2016:22:46:16 +0100] Report: printers=3
D [10/Dec/2016:22:46:16 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:46:16 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:46:16 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:46:16 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:47:18 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:47:18 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:47:18 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:47:18 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:47:18 +0100] Report: clients=0
D [10/Dec/2016:22:47:18 +0100] Report: jobs=66
D [10/Dec/2016:22:47:18 +0100] Report: jobs-active=1
D [10/Dec/2016:22:47:18 +0100] Report: printers=3
D [10/Dec/2016:22:47:18 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:47:18 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:47:18 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:47:18 +0100] Report: stringpool-total-bytes=23872
D [10/Dec/2016:22:48:20 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:48:20 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.12:631
D [10/Dec/2016:22:48:20 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [10/Dec/2016:22:48:20 +0100] cupsdNetIFUpdate: "eth0" = xxx::xxxx:xxxx:xxxx...%eth0:631
D [10/Dec/2016:22:48:20 +0100] Report: clients=0
D [10/Dec/2016:22:48:20 +0100] Report: jobs=66
D [10/Dec/2016:22:48:20 +0100] Report: jobs-active=1
D [10/Dec/2016:22:48:20 +0100] Report: printers=3
D [10/Dec/2016:22:48:20 +0100] Report: printers-implicit=0
D [10/Dec/2016:22:48:20 +0100] Report: stringpool-string-count=1121
D [10/Dec/2016:22:48:20 +0100] Report: stringpool-alloc-bytes=9040
D [10/Dec/2016:22:48:20 +0100] Report: stringpool-total-bytes=23872
end of error_log (eth2 ipv6 was changed here for my protection; notice: we could not copy the whole file, so times have changed some protocoling timestamps within the listing)
But since patched kernel still no printer output, no printout... (so I might still have to use my usb-stick (mdvr2010.2) or printer-server for printing, cups 1.4.5 (mdv2010.2))
Nevertheless, DCP-115C (MFC210C) prints again now, after following changes were made: Change system-config-printer (el6) and system-config-printer-libs (el6) to system-config-printer (mdv2010.2), system-config-printer-libs (mdv2010.2) and additionally use system-config-printer-kde (mdv2010.2) without printer-applet (mga2), but with task-printing (mdv2010.2) and task-printing-xxx (mdv2010.2), adjust lxml2-python (el6), python-cups (el6), add the acl-option to the root-partition in /etc/fstab, load kernel-printer-module usblp following the entry modprobe usblp by rc.modules, add the udev-rule with the vendor-id:product-id and change cups-1.4.2 (el6) to cups-1.4.5 (mdv2010.2). Finally restart cupsd:
...
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Not busy
D [12/Dec/2016:12:33:10 +0100] cupsdReadClient: 11 POST /printers/Brother-DCP-115C HTTP/1.1
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Active clients
D [12/Dec/2016:12:33:10 +0100] cupsdAuthorize: Authorized as secret using PeerCred
D [12/Dec/2016:12:33:10 +0100] cupsdReadClient: 11 1.1 Create-Job 1
D [12/Dec/2016:12:33:10 +0100] Create-Job ipp://localhost:631/printers/Brother-DCP-115C
D [12/Dec/2016:12:33:10 +0100] cupsdIsAuthorized: username="kept_anonymously_here"
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(----J-)
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Active clients and dirty files
D [12/Dec/2016:12:33:10 +0100] Adding default job-sheets values "none,none"...
I [12/Dec/2016:12:33:10 +0100] [Job 477] Adding start banner page "none".
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
I [12/Dec/2016:12:33:10 +0100] [Job 477] Queued on "Brother-DCP-115C" by "kept-anonymously-here".
D [12/Dec/2016:12:33:10 +0100] Returning IPP successful-ok for Create-Job (ipp://localhost:631/printers/Brother-DCP-115C) from localhost
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Dirty files
D [12/Dec/2016:12:33:10 +0100] cupsdReadClient: 11 POST /printers/Brother-DCP-115C HTTP/1.1
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Active clients and dirty files
D [12/Dec/2016:12:33:10 +0100] cupsdAuthorize: Authorized as secret using PeerCred
D [12/Dec/2016:12:33:10 +0100] cupsdReadClient: 11 1.1 Send-Document 1
D [12/Dec/2016:12:33:10 +0100] Send-Document ipp://localhost:631/printers/Brother-DCP-115C
D [12/Dec/2016:12:33:10 +0100] cupsdIsAuthorized: username="kept-anonymously-here"
D [12/Dec/2016:12:33:10 +0100] [Job 477] Auto-typing file...
D [12/Dec/2016:12:33:10 +0100] [Job 477] Request file type is application/pdf.
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(----J-)
I [12/Dec/2016:12:33:10 +0100] [Job 477] File of type application/pdf queued by "kept_anonymously_here".
I [12/Dec/2016:12:33:10 +0100] [Job 477] Adding end banner page "none".
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(----J-)
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(----J-)
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Active clients, printing jobs, and dirty files
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:10 +0100] [Job 477] job-sheets=none,none
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[0]="Brother-DCP-115C"
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[1]="477"
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[2]="kept-anonymously-here"
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[3]="Unbenannt"
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[4]="1"
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[5]="media=BrA4 job-uuid=urn:uuid:a514adcd-4dc3-3c85-4618-38c28b28f13a job-originating-host-name=localhost time-at-creation=1481542390 time-at-processing=1481542390 AP_D_InputSlot= PageSize=BrA4"
D [12/Dec/2016:12:33:10 +0100] [Job 477] argv[6]="/var/spool/cups/d00477-001"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[0]="CUPS_CACHEDIR=/var/cache/cups"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[1]="CUPS_DATADIR=/usr/share/cups"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[2]="CUPS_DOCROOT=/usr/share/cups/doc"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[3]="CUPS_FONTPATH=/usr/share/cups/fonts"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[4]="CUPS_REQUESTROOT=/var/spool/cups"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[5]="CUPS_SERVERBIN=/usr/lib/cups"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[6]="CUPS_SERVERROOT=/etc/cups"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[7]="CUPS_STATEDIR=/var/run/cups"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[8]="HOME=/var/spool/cups/tmp"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[9]="PATH=/usr/lib/cups/filter:/usr/bin:/usr/sbin:/bin:/usr/bin"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[10]="SERVER_ADMIN=root@localhost.localdomain"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[11]="SOFTWARE=CUPS/1.4.5"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[12]="TMPDIR=/var/spool/cups/tmp"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[13]="USER=root"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[14]="CUPS_SERVER=/var/run/cups/cups.sock"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[15]="CUPS_ENCRYPTION=IfRequested"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[16]="IPP_PORT=631"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[17]="CHARSET=utf-8"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[18]="LANG=de_DE.UTF-8"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[19]="PPD=/etc/cups/ppd/Brother-DCP-115C.ppd"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[20]="RIP_MAX_CACHE=8m"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[21]="CONTENT_TYPE=application/pdf"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[22]="DEVICE_URI=usb://Brother/DCP-115C?serial=BROE7F871829"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[23]="PRINTER_INFO=Brother DCP-115C"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[24]="PRINTER_LOCATION=localhost.localdomain"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[25]="PRINTER=Brother-DCP-115C"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[26]="CUPS_FILETYPE=document"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[27]="FINAL_CONTENT_TYPE=printer/Brother-DCP-115C"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[28]="AUTH_U****"
D [12/Dec/2016:12:33:10 +0100] [Job 477] envp[29]="AUTH_P****"
I [12/Dec/2016:12:33:10 +0100] [Job 477] Started filter /usr/lib/cups/filter/pdftops (PID 4084)
I [12/Dec/2016:12:33:10 +0100] [Job 477] Started filter /usr/lib/cups/filter/brlpdwrapperMFC210C (PID 4085)
I [12/Dec/2016:12:33:10 +0100] [Job 477] Started backend /usr/lib/cups/backend/usb (PID 4086)
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:10 +0100] Returning IPP successful-ok for Send-Document (ipp://localhost:631/printers/Brother-DCP-115C) from localhost
D [12/Dec/2016:12:33:10 +0100] cupsdSetBusyState: Printing jobs and dirty files
D [12/Dec/2016:12:33:10 +0100] [Job 477] STATE: +connecting-to-device
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
W [12/Dec/2016:12:33:10 +0100] [Job 477] If you have more than one Brother DCP-115C printer connected to this machine, please unload (and blacklist) the "usblp" kernel module as otherwise CUPS will not be able to distinguish your printers.
D [12/Dec/2016:12:33:10 +0100] [Job 477] Set job-printer-state-message to "If you have more than one Brother DCP-115C printer connected to this machine, please unload (and blacklist) the "usblp" kernel module as otherwise CUPS will not be able to distinguish your printers.", current level=WARN
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:10 +0100] [Job 477] Printer using device file "/dev/usblp0"...
D [12/Dec/2016:12:33:10 +0100] [Job 477] STATE: -connecting-to-device
D [12/Dec/2016:12:33:10 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:10 +0100] [Job 477] backendRunLoop(print_fd=0, device_fd=5, snmp_fd=-1, addr=(nil), use_bc=0, side_cb=0x7fe4a3d7c6ff)
D [12/Dec/2016:12:33:10 +0100] [Job 477] Started filter pdftops (PID 4091)
D [12/Dec/2016:12:33:10 +0100] [Job 477] Started filter pstops (PID 4092)
D [12/Dec/2016:12:33:10 +0100] [Job 477] PID 4091 (pdftops) exited with no errors.
D [12/Dec/2016:12:33:10 +0100] [Job 477] Page = 595x842; 9,9 to 586,833
D [12/Dec/2016:12:33:10 +0100] [Job 477] slow_collate=0, slow_duplex=0, slow_order=1
D [12/Dec/2016:12:33:10 +0100] [Job 477] Before copy_comments - %!PS-Adobe-3.0
D [12/Dec/2016:12:33:10 +0100] [Job 477] %!PS-Adobe-3.0
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%Creator:
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%LanguageLevel: 3
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%DocumentSuppliedResources: (atend)
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%DocumentMedia: plain 595 842 0 () ()
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%BoundingBox: 0 0 595 842
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%Pages: 1
D [12/Dec/2016:12:33:10 +0100] [Job 477] %%EndComments
D [12/Dec/2016:12:33:10 +0100] [Job 477] Before copy_prolog - %%BeginDefaults
D [12/Dec/2016:12:33:10 +0100] [Job 477] Before copy_setup - %%BeginSetup
D [12/Dec/2016:12:33:10 +0100] [Job 477] Before page loop - %%Page: 1 1
D [12/Dec/2016:12:33:10 +0100] [Job 477] Copying page 1...
D [12/Dec/2016:12:33:10 +0100] [Job 477] pagew = 577.0, pagel = 824.0
D [12/Dec/2016:12:33:10 +0100] [Job 477] bboxx = 0, bboxy = 0, bboxw = 595, bboxl = 842
D [12/Dec/2016:12:33:10 +0100] [Job 477] PageLeft = 9.0, PageRight = 586.0
D [12/Dec/2016:12:33:10 +0100] [Job 477] PageTop = 833.0, PageBottom = 9.0
D [12/Dec/2016:12:33:10 +0100] [Job 477] PageWidth = 595.0, PageLength = 842.0
D [12/Dec/2016:12:33:10 +0100] [Job 477] Wrote 1 pages...
D [12/Dec/2016:12:33:10 +0100] [Job 477] PID 4092 (pstops) exited with no errors.
D [12/Dec/2016:12:33:10 +0100] PID 4084 (/usr/lib/cups/filter/pdftops) exited with no errors.
D [12/Dec/2016:12:33:14 +0100] [Job 477] Read 2567 bytes of print data...
D [12/Dec/2016:12:33:14 +0100] [Job 477] STATE: -media-empty-warning
D [12/Dec/2016:12:33:14 +0100] [Job 477] STATE: -offline-report
I [12/Dec/2016:12:33:14 +0100] [Job 477] Drucker ist jetzt online.
D [12/Dec/2016:12:33:14 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:14 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:14 +0100] [Job 477] Wrote 2567 bytes of print data...
D [12/Dec/2016:12:33:15 +0100] [Job 477] Read 43 bytes of print data...
D [12/Dec/2016:12:33:15 +0100] [Job 477] Wrote 43 bytes of print data...
D [12/Dec/2016:12:33:15 +0100] [Job 477] Read 4096 bytes of print data... # system-config-printer (mdv2010.2, pclos) with system-config-printer-udev (el6) has been missed right before; previous: system-config-printer (el6).
D [12/Dec/2016:12:33:15 +0100] [Job 477] Wrote 4096 bytes of print data...
D [12/Dec/2016:12:33:17 +0100] [Job 477] Read 1167 bytes of print data...
D [12/Dec/2016:12:33:17 +0100] [Job 477] Wrote 1167 bytes of print data...
D [12/Dec/2016:12:33:17 +0100] [Job 477] Read 2 bytes of print data...
D [12/Dec/2016:12:33:17 +0100] [Job 477] Wrote 2 bytes of print data...
D [12/Dec/2016:12:33:17 +0100] PID 4085 (/usr/lib/cups/filter/brlpdwrapperMFC210C) exited with no errors.
D [12/Dec/2016:12:33:17 +0100] PID 4086 (/usr/lib/cups/backend/usb) exited with no errors.
D [12/Dec/2016:12:33:17 +0100] cupsdMarkDirty(-----S)
I [12/Dec/2016:12:33:17 +0100] [Job 477] Job completed.
D [12/Dec/2016:12:33:17 +0100] cupsdMarkDirty(----J-)
D [12/Dec/2016:12:33:17 +0100] cupsdMarkDirty(-----S)
D [12/Dec/2016:12:33:18 +0100] [Job 477] Unloading...
I [12/Dec/2016:12:33:41 +0100] Saving job cache file "/var/cache/cups/job.cache"...
I [12/Dec/2016:12:33:41 +0100] Saving subscriptions.conf...
D [12/Dec/2016:12:33:41 +0100] cupsdSetBusyState: Not busy
D [12/Dec/2016:12:33:45 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:33:45 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:33:45 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:33:45 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxx%eth0:631
D [12/Dec/2016:12:33:45 +0100] Report: clients=1
D [12/Dec/2016:12:33:45 +0100] Report: jobs=71
D [12/Dec/2016:12:33:45 +0100] Report: jobs-active=0
D [12/Dec/2016:12:33:45 +0100] Report: printers=2
D [12/Dec/2016:12:33:45 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:33:45 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:33:45 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:33:45 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:34:47 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:34:47 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:34:47 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:34:47 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxxx%eth0:631
D [12/Dec/2016:12:34:47 +0100] Report: clients=1
D [12/Dec/2016:12:34:47 +0100] Report: jobs=71
D [12/Dec/2016:12:34:47 +0100] Report: jobs-active=0
D [12/Dec/2016:12:34:47 +0100] Report: printers=2
D [12/Dec/2016:12:34:47 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:34:47 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:34:47 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:34:47 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:35:49 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:35:49 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:35:49 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:35:49 +0100] cupsdNetIFUpdate: "eth0" = fxxxxxxxxx%eth0:631
D [12/Dec/2016:12:35:49 +0100] Report: clients=1
D [12/Dec/2016:12:35:49 +0100] Report: jobs=71
D [12/Dec/2016:12:35:49 +0100] Report: jobs-active=0
D [12/Dec/2016:12:35:49 +0100] Report: printers=2
D [12/Dec/2016:12:35:49 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:35:49 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:35:49 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:35:49 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:36:51 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:36:51 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:36:51 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:36:51 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxxxxxxxxxxx%eth0:631
D [12/Dec/2016:12:36:51 +0100] Report: clients=1
D [12/Dec/2016:12:36:51 +0100] Report: jobs=71
D [12/Dec/2016:12:36:51 +0100] Report: jobs-active=0
D [12/Dec/2016:12:36:51 +0100] Report: printers=2
D [12/Dec/2016:12:36:51 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:36:51 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:36:51 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:36:51 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:37:54 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:37:54 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:37:54 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:37:54 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxxxxxx%eth0:631
D [12/Dec/2016:12:37:54 +0100] Report: clients=1
D [12/Dec/2016:12:37:54 +0100] Report: jobs=71
D [12/Dec/2016:12:37:54 +0100] Report: jobs-active=0
D [12/Dec/2016:12:37:54 +0100] Report: printers=2
D [12/Dec/2016:12:37:54 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:37:54 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:37:54 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:37:54 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:38:11 +0100] Closing client 11 after 300 seconds of inactivity...
D [12/Dec/2016:12:38:11 +0100] cupsdCloseClient: 11
D [12/Dec/2016:12:38:56 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:38:56 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:38:56 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:38:56 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxxxxxx%eth0:631
D [12/Dec/2016:12:38:56 +0100] Report: clients=0
D [12/Dec/2016:12:38:56 +0100] Report: jobs=71
D [12/Dec/2016:12:38:56 +0100] Report: jobs-active=0
D [12/Dec/2016:12:38:56 +0100] Report: printers=2
D [12/Dec/2016:12:38:56 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:38:56 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:38:56 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:38:56 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:39:58 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:39:58 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:39:58 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:39:58 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxxxxxx%eth0:631
D [12/Dec/2016:12:39:58 +0100] Report: clients=0
D [12/Dec/2016:12:39:58 +0100] Report: jobs=71
D [12/Dec/2016:12:39:58 +0100] Report: jobs-active=0
D [12/Dec/2016:12:39:58 +0100] Report: printers=2
D [12/Dec/2016:12:39:58 +0100] Report: printers-implicit=0
D [12/Dec/2016:12:39:58 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:12:39:58 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:12:39:58 +0100] Report: stringpool-total-bytes=20616
D [12/Dec/2016:12:41:00 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:41:00 +0100] cupsdNetIFUpdate: "eth0" = 192.168.178.10:631
D [12/Dec/2016:12:41:00 +0100] cupsdNetIFUpdate: "lo" = localhost:631
D [12/Dec/2016:12:41:00 +0100] cupsdNetIFUpdate: "eth0" = xxxxxxxxxxxxxx%eth0:631
D [12/Dec/2016:12:41:00 +0100] Report: clients=0
D [12/Dec/2016:12:41:00 +0100] Report: jobs=71
D [12/Dec/2016:12:41:00 +0100] Report: jobs-active=0
D [12/Dec/2016:12:41:00 +0100] Report: printers=2
...
D [12/Dec/2016:13:20:17 +0100] Report: stringpool-string-count=952
D [12/Dec/2016:13:20:17 +0100] Report: stringpool-alloc-bytes=9304
D [12/Dec/2016:13:20:17 +0100] Report: stringpool-total-bytes=20616
DCP-115C is printing again now, must be forever and together with paper outputs, testpage in detail: cups-1.4.6 (pclos) or cups-1.4.5 (mdv2010.2).
LogLevel: reset to "warn"
Problem: A python app does not start. Manual start by typing into terminal presents the following error: "Module a_python_module Import error"
Solution: Follow the directories and files listed by starting the underlying program resp. process with strace and copy missed modules (almost out of /usr/lib64/python2.6/site-packages/ into those directories (modules) and file-locations (modules in detail) listed empty. Check out the python-version by "python -V" (should be python-2.6(.6-66) (el6) in our case) . Also set the access rights: chmod 755 -R /usr/lib64/python2.6, chmod 755 -R /usr/share/system-config-printer, ....
Nevertheless a complete change from python2.5 (mdv2010.2) to python2.6 is possible, same for perl, and other python-versions (libraries) like python-libs (python2.7, el7) can be installed beneath python-2.6 too creating /usr/lib64/python2.7 beneath /usr/lib64/python2.6. We also linked /usr/lib64/python3.2, 3.3. and 3.4 to /usr/lib64/python2.6. For system-config-printer we installed the following mix out of mdv2010 and el6: system-config-printer (mdv2010.1, pclos), system-config-printer-libs (mdv2010.1, pclos), system-config-printer-kde4 (mdv2010.1, depending on KDE: el6, pclos) and system-config-printer-udev (el6, depending on udev), all task-printing (mdv2010.1, pclos). Even the printer-applet appears in the tray (task line) during the successful printout (printer modell: Brother DCP-115C (MFC210C)), so printer-applet (mga2) isn´t needed. If you get a unicode-error, old python2.5 (mdv with unicode ucf-4) are still in use. Replace them with python2.6 (el6, unicode ucf-2)
Printer-configuration: see /etc/cups/printers.conf or start system-config-printer, even graphically by MCC -> system-config-printer, eventually start systemsettings (kde) or start the gnome-control-center instead of system-config-printer. Manually, a printer can be configured by the command lpadmin (details for this command see above). The printer can also be configured using the browser and typing into the address line: localhost:631.
If the printout does not contain the printout (any words and letter) itself, reinstall the editor (in our case exchange kwrite (OpenSuSE 4.4.4) with kwrite (mdv2010.2 oder el6))..
How it should be (and how it is now): The client starts the printer job. The local driver transforms the document into a RAW-file and sents this file to CUPSD. CUPSD transforms the RAW into a postscript-file by ghostscript and sents it to the printer by settings and parameters within the ppd-file. But at last, KDE (mdv2010.2, patched konqueror) does contribute to the job.
Run the cups wrapper file in /usr/local/Brother/cupswrapper. This should automatically install and configure your brother printer.
lpstat -t provides on overview about the print-jobs and the state (like printing, inactive and so on) of each printer.
There you can also look out for the user, who is printing. Not all might be allowed. Configure permissions for different user through localhost:631 (CUPS > =1.4.5) or system-config-printer (el6, mdv)-
Cups-configuration: /etc/cups/cupsd.conf
cups exited with an error-message by returning an exit code like -1", child-exit-error (cups-1.4.2 (el6): reconfigure cupsd.conf and especially exchange /usr/lib64/libcups.so.2 (install lib64cups2 (pclos2016), while lib64cups2 (pclos2018) has got the same error as cups-libs (el6)).
cups does not start by searching a long time for /usr/bin/cups: Take the init-script for cups out of cups (el6 or pclos) and exchange /etc/init.d/cups !
Printer Paused - "/usr/lib/cups/backend/hp failed" [SOLVED]: chmod 666 /dev/usb/lp0 and set line
usbfs /proc/bus/usb usbfs auto,devmode=0666 0 0 in /etc/fstab,
add into /etc/udev/rules.d/70-local.rules
SUBSYSTEM=="usb", ACTION=="add", ENV{DEVTYPE}=="usb_device", ATTRS{idVendor}=="04f9", ATTRS{idProduct}=="018c", KERNEL=="lp*", GROUP=="lp", MODE:="0666"
Notice: User lp should be a member of the group of root, care for it by MCC -> user administration or manually !
another solution: https://bbs.archlinux.org/viewtopic.php?id=85454
Kernel-modules: usbcore, usblp, usb_storage, if such modules are not loaded (lsmod), load them through /etc/rc.modules by entering at the end of all lines "modprobe usblp" usw.
There is a "libusb" related bugs on certain version of cups.
If nothing helps, reinstall CUPS and/or lpr!
https://wiki.archlinux.org/index.php/CUPS/Troubleshooting: Conflict with usblp
USB printers can be accessed using two methods: The usblp kernel module and libusb. The former is the classic way. It is simple: data is sent to the printer by writing it to a device file as a simple serial data stream. Reading the same device file allows bi-di access, at least for things like reading out ink levels, status, or printer capability information (PJL). It works very well for simple printers, but for multi-function devices (printer/scanner) it is not suitable and manufacturers like HP supply their own backends. Source: here.
Warning: As of cups version 1.6.0, it should no longer be necessary to blacklist the usblp kernel module. If you find out this is the only way to fix a remaining issue please report this upstream to the CUPS bug tracker and maybe also get in contact with Till Kamppeter (Debian CUPS maintainer). See upstream bug for more info.
If you have problems getting your USB printer to work, you can try blacklisting the usblp kernel module:
/etc/modprobe.d/blacklistusblp.conf
blacklist usblp
Custom kernel users may need to manually load the usbcore kernel module before proceeding.
Once the modules are installed, plug in the printer and check if the kernel detected it by running the following:
# journalctl -e
or
# dmesg
If you are using usblp, the output should indicate that the printer has been detected like so:
Feb 19 20:17:11 kernel: printer.c: usblp0: USB Bidirectional
printer dev 2 if 0 alt 0 proto 2 vid 0x04E8 pid 0x300E
Feb 19 20:17:11 kernel: usb.c: usblp driver claimed interface cfef3920
Feb 19 20:17:11 kernel: printer.c: v0.13: USB Printer Device Class driver
If you blacklisted usblp, you will see something like:
usb 3-2: new full speed USB device using uhci_hcd and address 3
usb 3-2: configuration #1 chosen from 1 choice
michaelrsweet commented Apr 20, 2006
Version: 1.4-feature
CUPS.org User: till.kamppeter
As discussed in this thread on linuxprinting.org
and also due to problems reported with Epson multi-function devices and recent kernels it can make sense to let the "usb" backend of CUPS not use the "usblp" kernel module any more, but libusb (SANE also switched from a kernel module for USB scanners to libusb, also HPLIP from HP did so).
Our Mandriva contributor Couriousous (couriousous at mandriva dot org, couriousous at sceen dot net) has sent to me a libusb-based USB CUPS backend once (attached), which could be the start for the development of a new USB backend for CUPS.
Build instructions:
Install libusb-devel (or libusb-dev)
Uncompress CUPS source code
Copy the attached file into the backend/ directory
Edit backend/usb.c modifying the include of usb-unix.c to usb-libusb.c
Let compilation being done with "-lusb" (by LDFLAGS environment variable)
Install CUPS as usual (or simply replace your "usb" backend by the new one).
My suggestion would be either to switch the current backend to libusb-only or better to make it runtime-configurable, so that the user can choose between using the kernel module or libusb, simply by a switch in /etc/cups/cupsd.conf or /etc/cups/usb.conf.
This comment has been minimized.
Sign in to view
Collaborator
michaelrsweet commented Apr 20, 2006
CUPS.org User: till.kamppeter
Note that the usb-libusb.c was developed with CUPS 1.1.23, a slight change has to be done for CUPS 1.2 to compile it. See attached patch. You need to add "-lusb" to the "LDFLAGS" line in Makedefs after running "./configure" and before running "make". Then you get the libusb-based backend as backend/usb. Replace the original backend in /usr/lib/cups/backend by it.
Now it auto-detects the HP PhotoSmart 2600 on USB as follows:
[root@majax c]# /usr/lib/cups/backend/usb
direct usb://HP/Photosmart%202600%20series?serial=MY53OK70V10400 "HP Photosmart 2600 series" "USB Printer #1002"
https://github.com/apple/cups/issues/1575
[root@majax c]#
There is no 1284 device ID, but the web interface still assigns the correct PPD file from HPLIP.
The problem is that this backend does not actually print. When printing the test page via the web interface button I get
Unable to find USB device "usb://HP/Photosmart%202600%20series?serial=MY53OK70V10400"
and the queue gets stopped due to backend failure.
So the backend seems to need some further adaptation to CUPS 1.2.
https://github.com/apple/cups/issues/1575
Mandriva clears last printer-problems:
http://mandrivausers.org/index.php?/topic/40639-printer-driverconfig-beside-cups/
Many Linux experts gave up on cups problems and bugs:
It should work fine with cups and the hplip backend.
If it says "unable to install cups" then either you haven´t configured your urpmi repos, or the system is seriously borked
.
What happens if you run any browser and type in
http://localhost:631
Oh, by the way: How do you manage to "click" in text mode?
There is a "libusb" related bugs on certain version of cups.
... use ordinary mouse with "gpm" daemon.
I can access cups using the following command:
http://localhost:631
Unfortunately after clicking on "printing test page" / press enter, nothing happen.
I try with X-Windows, but after "sending test page" to printer nothing happen, only question: "Is the test page OK?" (Yes/No).
Is there any step by step debugging of various program / process inside/called by cups?
I want to see all the process /error in sending testpage.ps to printer port?
...
I had cleaned all foomatic, cups, ghostscript, hplip, hpijs and other printer related RPM. I had installed from the latest source code: cups, foomatic, ghostscript.
Cups with --enable-debug, but there is no cups.log or cups_log.
There are 3 files on /var/log/cups: access_log, error_log and page_log.
Page_log containing information about 1 test page.
The last 5 lines from access_log:
"POST / HTTP/1.1" 200 413 CUPS-Get-Classes successful-ok
"POST / HTTP/1.1" 200 77 CUPS-Get-Default successful-ok
"POST / HTTP/1.1" 200 411 CUPS-Get-Printers successful-ok
"POST / HTTP/1.1" 200 154 Get-Jobs successful-ok
"POST / HTTP/1.1" 200 179 CUPS-Get-Printers successful-ok
From error_log:...
After 2 weeks battle, the cups works:
1. Use Cups, Ghostscript, foomatic, hplip (for HP printers) source code from Mandriva 2007.1 in SRPMS sub-directory. Re-compile using "rpmbuild --rebuild --nodeps".
If the rpmbuild failed, change directory to "/usr/src/RPM/BUILD/cups*", run make and make install.
Run "gsc -h" command and make sure the printer driver for your printer is included in the output.
2. Make sure the required ghostscript fonts are available for foomatic, before rebuilding it.
Search for all type1 and ttf font, copy to "/usr/X11R6......fonts/Type1" and "/usr/X11R6/........fonts/TTF".
Run type1inst and ttfontmap.
Copy the fontmap to "/usr/share/ghostscript/........./Fontmap.GS".
http://pegasus.rutge...HOWTO/x338.html
Make sure GS_LIB environment variable point to the directory. Set the environment variable on /root/.bashrc or ".bashrc" file your root directory.
GS_LIB=/usr/X11R6/lib/X11/fonts/TTF
GS_LIB=/usr/X11R6/lib/X11/fonts/Type1:$GS_LIB
export GS_LIB
Exit/log out from root account and login again.
To test environment variable:
set | grep -i "gs_lib"
3. Modify "/etc/cups/cupsd.conf" to get the error. New values:
LogLevel debug
Listen 127.0.0.1:631 # or try "Port 631" and "Listen /var/run/cups/cups.sock".
Below each "order <deny, allow>" lines and
below each "order <allow, deny>" lines, you must insert the following line:
Allow 127.0.0.1
Allow 192.168.178.*
On my "/etc/cups/cupsd.conf" there are 7 "order..........." lines
You can check the debug / error messages at "/var/log/cups/error_log".
You can reset the log by using the following command:
rm -rfv /var/log/cups/*".
After this command restart cups daemon:
"service cups stop"
"service cups start"
4. I face the following printing problem: "unsupported format "text/plain" and "application/postscript". The solution:
Modify /etc/cups/mime.convs: remove the comment sign (the character ´#´)
application/vnd.cups-postscript application/vnd.cups-raster 100 pstoraster
application/octet-stream application/vnd.cups-raw 0 -
https://bugs.launchp...psys/+bug/36532
5. Create user and group: lp, lpadmin (using adduser command).
6. Change access mode of "/dev/lp0" (resp. /dev/usb/lp0 )
chmod a+w /dev/lp0
7. If you got "cannot set ACLs command not supported" problem on "/var/log/cups/error_log", you must install ACL packages.
http://acl.bestbits.at/download.html
Make sure you had compiled kernel with ACL option on "file system" kernel options (from "/usr/src/linux-...../.config")
CONFIG_EXT2_FS_POSIX_ACL=y
CONFIG_FS_POSIX_ACL=y
CONFIG_GENERIC_ACL=y
CONFIG_TMPFS_POSIX_ACL=y
CONFIG_NFS_V3_ACL=y
CONFIG_NFSD_V2_ACL=y
CONFIG_NFSD_V3_ACL=y
CONFIG_NFS_ACL_SUPPORT=y
If you use "module" option, perhaps you can use "=m" instead of "=y".
Modify "/etc/fstab". Add ",acl" after "defaults" on "/etc/fstab" entry. Example for root partition (/) on "/dev/hda1":
/dev/hda1 / ext2 defaults,acl 1 1
Reboot after modifying and saving "/etc/fstab".
How to test acl:
touch /test
setfacl -m u:root:rwx /test
8. If you face "quota limit" problem, delete the printer on CUPS menu, reboot and re-install new printer driver from scratch.
This post has been edited by anonxyz: 26 April 2007 - 02:19 PM
The paper shaft is devided into a lower one for the inlay of the papers and an upper one for the output of the printed paper. The separator for both has got a V-form. Use bright adhensive tapes to close the opening of the-"V". Then printed papers always get out of the shaft correctly without getting furled and without remaining in the shaft.
The printer does its work, but the printer-applet sometimes shows the message "Can not find the printer-driver"? We chosed dmsetup with lib64devicemapper and lib64devicemapper-event from mdv2011 and udev from 2010.2 or mdv2011 from fr2.rpmfind.net. Notice, that mdv provides separate printer-manager for HP, Epson, Canon and Lexmark and so on.
more printer-troubieshooting
If your printer does not print in black anymore, PCWelt.de, 14.08.2015
If your printer does not print in black anymore, although a new cartridge is inserted, our tipps might help you.
http://www.pcwelt.de/tipps/Wenn-Ihr-Geraet-kein-Schwarz-mehr-druckt-9587974.html
Notice: This modell still has got its awful paper-jams, especially if more than one hundred papers are put into the shaft. Jammed papers have to be pulled out in a quit difficult way and manner, in order to make this printer understand and sign, that something had already been done ...
Hardware, Printer / Drucker
Linux Printer Driver Listing
Hewlett Packard (HP)
hpijs-pcl3 IJS 10 , HP´s , HPIJS driver - PPDs for , HP´s Apollo- and Sony-branded inkjet printers
hpijs-pcl5c IJS 83 , HP´s , HPIJS driver - PPDs for compatible PCL-5c-based non-, HP color laser printers
hpijs-pcl5e IJS 354 , HP´s , HPIJS driver - PPDs for compatible PCL-5e-based non-, HP laser printers
hplip 479 , HP´s driver suite for printers and multi-function devices
hplib ( deb and rpm hplib (fc, el7, el6, rosa, debian) )
HP 2000C
, HP 2500C
, HP 2500CM
, HP 910
HP 915
HP Business Inkjet 1000
HP Business Inkjet 1100
HP Business Inkjet 1200
HP Business Inkjet 2200
HP Business Inkjet 2230
HP Business Inkjet 2250
HP Business Inkjet 2250TN
HP Business Inkjet 2280
HP Business Inkjet 2300
HP Business Inkjet 2600
HP Business Inkjet 2800
HP Business Inkjet 3000
HP CM8050 Color MFP
HP CM8050 MFP with Edgeline
HP CM8060 Color MFP
HP CM8060 MFP with Edgeline
HP Color Inkjet Printer CP1160
HP Color Inkjet Printer CP1700
HP Color LaserJet
HP Color LaserJet 2500
HP Color LaserJet 2550
HP Color LaserJet 2605
HP Color LaserJet 2605dn
HP Color LaserJet 2700
HP Color LaserJet 2800
HP Color LaserJet 3000
HP Color LaserJet 3500
HP Color LaserJet 3550
HP Color LaserJet 3600
HP Color LaserJet 3700
HP Color LaserJet 3800
HP Color LaserJet 4500
HP Color LaserJet 4550
HP Color LaserJet 4600
HP Color LaserJet 4610
HP Color LaserJet 4650
HP Color LaserJet 4700
HP Color LaserJet 4730 MFP
HP Color LaserJet 5
HP Color LaserJet 5000
HP Color LaserJet 5500
HP Color LaserJet 5550
HP Color LaserJet 5M
HP Color LaserJet 8500
HP Color LaserJet 8550
HP Color LaserJet 8550GN
HP Color LaserJet 9500
HP Color LaserJet 9500 MFP
HP Color LaserJet CM1015
HP Color LaserJet CM1017
HP Color LaserJet CM4730 MFP
HP Color LaserJet CP3505
HP Color LaserJet CP4005
HP DesignJet ColorPro CAD
HP DeskJet 1100C
HP DeskJet 1120C
HP DeskJet 1125C
HP DeskJet 1200C
HP DeskJet 1220C
HP DeskJet 1280
HP DeskJet 1600C
HP DeskJet 3320
HP DeskJet 3325
HP DeskJet 3420
HP DeskJet 3425
HP DeskJet 350C
HP DeskJet 3520
HP DeskJet 3528
HP DeskJet 3535
HP DeskJet 3550
HP DeskJet 3558
HP DeskJet 3650
HP DeskJet 3658
HP DeskJet 3668
HP DeskJet 3740
HP DeskJet 3810
HP DeskJet 3816
HP DeskJet 3820
HP DeskJet 3822
HP DeskJet 3840
HP DeskJet 3845
HP DeskJet 3920
HP DeskJet 3940
HP DeskJet 400
HP DeskJet 420C
HP DeskJet 450
HP DeskJet 460
HP DeskJet 500
HP DeskJet 500C
HP DeskJet 505J Plus
HP DeskJet 510
HP DeskJet 5150
HP DeskJet 5158
HP DeskJet 5160
HP DeskJet 520
HP DeskJet 540
HP DeskJet 540C
HP DeskJet 5440
HP DeskJet 550C
HP DeskJet 5550
HP DeskJet 5551
HP DeskJet 560C
HP DeskJet 5650
HP DeskJet 5652
HP DeskJet 5670
HP DeskJet 5740
HP DeskJet 5850
HP DeskJet 5940
HP DeskJet 600
HP DeskJet 610C
HP DeskJet 610CL
HP DeskJet 6122
HP DeskJet 6127
HP DeskJet 612C
HP DeskJet 630C
HP DeskJet 632C
HP DeskJet 640C
HP DeskJet 648C
HP DeskJet 6520
HP DeskJet 6540
HP DeskJet 656C
HP DeskJet 6600
HP DeskJet 660C
HP DeskJet 670C
HP DeskJet 670TV
HP DeskJet 672C
HP DeskJet 6800
HP DeskJet 680C
HP DeskJet 682C
HP DeskJet 6840
HP DeskJet 690C
HP DeskJet 692C
HP DeskJet 693C
HP DeskJet 6940
HP DeskJet 694C
HP DeskJet 695C
HP DeskJet 697C
HP DeskJet 6980
HP DeskJet 810C
HP DeskJet 812C
HP DeskJet 815C
HP DeskJet 816C
HP DeskJet 825C
HP DeskJet 830C
HP DeskJet 832C
HP DeskJet 840C
HP DeskJet 841C
HP DeskJet 842C
HP DeskJet 843C
HP DeskJet 845C
HP DeskJet 850C
HP DeskJet 855C
HP DeskJet 870C
HP DeskJet 880C
HP DeskJet 882C
HP DeskJet 890C
HP DeskJet 895C
HP DeskJet 916C
HP DeskJet 920C
HP DeskJet 9300
HP DeskJet 930C
HP DeskJet 932C
HP DeskJet 933C
HP DeskJet 934C
HP DeskJet 935C
HP DeskJet 940C
HP DeskJet 948C
HP DeskJet 950C
HP DeskJet 952C
HP DeskJet 955C
HP DeskJet 957C
HP DeskJet 959C
HP DeskJet 9600
HP DeskJet 960C
HP DeskJet 970C
HP DeskJet 975C
HP DeskJet 9800
HP DeskJet 980C
HP DeskJet 990C
HP DeskJet 995C
HP DeskJet D1300
HP DeskJet D1400
HP DeskJet d1660
HP DeskJet D2300
HP DeskJet D2400
HP DeskJet D4100
HP DeskJet D4200
HP DeskJet F2100
HP DeskJet F300
HP DeskJet F4100
HP e-printer e20
HP
HP LaserJet Professional M1132 MFP
HP LaserJet 1010
HP LaserJet 1012
HP LaserJet 1015
HP LaserJet 1022
HP LaserJet 1022n
HP LaserJet 1022nw
HP LaserJet 1100
HP LaserJet 1100A
HP LaserJet 1150
HP LaserJet 1160
HP LaserJet 1200
HP LaserJet 1220
HP LaserJet 1300
HP LaserJet 1320
HP LaserJet 2100
HP LaserJet 2100M
HP LaserJet 2200
HP LaserJet 2300
HP LaserJet 2300L
HP LaserJet 2410
HP LaserJet 2420
HP LaserJet 2430
HP LaserJet 3015
HP LaserJet 3020
HP LaserJet 3030
HP LaserJet 3050
HP LaserJet 3052
HP LaserJet 3055
HP LaserJet 3200
HP LaserJet 3200m
HP LaserJet 3200se
HP LaserJet 3300 MFP
HP LaserJet 3310 MFP
HP LaserJet 3320N MFP
HP LaserJet 3320 MFP
HP LaserJet 3330 MFP
HP LaserJet 3380
HP LaserJet 3390
HP LaserJet 3392
HP LaserJet 4
HP LaserJet 4000
HP LaserJet 4050
HP LaserJet 4100
HP LaserJet 4100 MFP
HP LaserJet 4200
HP LaserJet 4240
HP LaserJet 4250
HP LaserJet 4300
HP LaserJet 4345 MFP
HP LaserJet 4350
HP LaserJet 4L
HP LaserJet 4M
HP LaserJet 4ML
HP LaserJet 4MP
HP LaserJet 4P
HP LaserJet 4Si
HP LaserJet 4V
HP LaserJet 4V/4LJ Pro
HP LaserJet 4 Plus
HP LaserJet 5
HP LaserJet 5000
HP LaserJet 5100
HP LaserJet 5200
HP LaserJet 5200L
HP LaserJet 5L
HP LaserJet 5M
HP LaserJet 5MP
HP LaserJet 5P
HP LaserJet 5Si
HP LaserJet 5Si Mopier
HP LaserJet 6
HP LaserJet 6L
HP LaserJet 6MP
HP LaserJet 6P
HP LaserJet 8000
HP LaserJet 8100
HP LaserJet 8150
HP LaserJet 9000
HP LaserJet 9000 MFP
HP LaserJet 9040
HP LaserJet 9040 MFP
HP LaserJet 9050
HP LaserJet 9050 MFP
HP LaserJet 9055 MFP
HP LaserJet 9065 MFP
HP LaserJet M2727
HP LaserJet M3027 MFP
HP LaserJet M3035 MFP
HP LaserJet M4345 MFP
HP LaserJet M5025 MFP
HP LaserJet M5035 MFP
HP LaserJet P2010
HP LaserJet P2015
HP LaserJet P2055d
HP LaserJet P2055dn
HP LaserJet P3004
HP LaserJet P3005
HP LaserJet P4014
HP LaserJet P4015
HP Mopier 240
HP Mopier 320
HP OfficeJet
HP Officejet-4500-G510n-z
HP OfficeJet 300
HP OfficeJet 330
HP OfficeJet 350
HP OfficeJet 4100
HP OfficeJet 4105
HP OfficeJet 4110
HP OfficeJet 4115
HP OfficeJet 4200
HP OfficeJet 4300
HP OfficeJet 500
HP OfficeJet 5105
HP OfficeJet 5110
HP OfficeJet 5110xi
HP OfficeJet 520
HP OfficeJet 5500
HP OfficeJet 5600
HP OfficeJet 570
HP OfficeJet 580
HP OfficeJet 590
HP OfficeJet 600
HP OfficeJet 610
HP OfficeJet 6100
HP OfficeJet 6105
HP OfficeJet 6110
HP OfficeJet 6150
HP OfficeJet 6200
HP OfficeJet 625
HP OfficeJet 630
HP OfficeJet 6300
HP OfficeJet 635
HP OfficeJet 6500 Wireless
HP OfficeJet 700
HP OfficeJet 710
HP OfficeJet 7100
HP OfficeJet 7110
HP OfficeJet 7130
HP OfficeJet 7140
HP OfficeJet 720
HP OfficeJet 7200
HP OfficeJet 725
HP OfficeJet 7300
HP OfficeJet 7400
HP OfficeJet D125
HP OfficeJet D135
HP OfficeJet D145
HP OfficeJet D155
HP OfficeJet G55
HP OfficeJet G85
HP OfficeJet G95
HP OfficeJet J3600
HP OfficeJet J5500
HP OfficeJet J5700
HP OfficeJet K60
HP OfficeJet K60xi
HP OfficeJet K7100
HP OfficeJet K80
HP OfficeJet K80xi
HP OfficeJet LX
HP OfficeJet Pro 1150C
HP OfficeJet Pro 1170C
HP OfficeJet Pro 1175C
HP Officejet Pro 8500 A910
HP Officejet Pro 8500 Premier
HP OfficeJet Pro 8710
HP OfficeJet Pro K5300
HP OfficeJet Pro K5400
HP OfficeJet Pro K550
HP OfficeJet Pro K850
HP OfficeJet Pro K8600
HP OfficeJet Pro L7300
HP OfficeJet Pro L7500
HP OfficeJet Pro L7600
HP OfficeJet Pro L7700
HP OfficeJet R40
HP OfficeJet R45
HP OfficeJet R60
HP OfficeJet R65
HP OfficeJet R80
HP OfficeJet T45
HP OfficeJet T65
HP OfficeJet V40
HP OfficeJet V40xi
HP PhotoSmart 140
HP PhotoSmart 240
HP PhotoSmart 2570
HP PhotoSmart 2600
HP PhotoSmart 2700
HP PhotoSmart 3100
HP PhotoSmart 320
HP PhotoSmart 3200
HP PhotoSmart 330
HP PhotoSmart 3300
HP PhotoSmart 370
HP PhotoSmart 380
HP PhotoSmart 420
HP PhotoSmart 470
HP PhotoSmart 7150
HP PhotoSmart 7260
HP PhotoSmart 7268
HP PhotoSmart 7345
HP PhotoSmart 7350
HP PhotoSmart 7400
HP PhotoSmart 7550
HP PhotoSmart 7660
HP PhotoSmart 7760
HP PhotoSmart 7800
HP PhotoSmart 7960
HP PhotoSmart 8000
HP PhotoSmart 8100
HP PhotoSmart 8200
HP PhotoSmart 8400
HP PhotoSmart 8700
HP PhotoSmart A310
HP PhotoSmart A320
HP PhotoSmart A430
HP PhotoSmart A440
HP PhotoSmart A510
HP PhotoSmart A520
HP PhotoSmart A610
HP PhotoSmart A620
HP PhotoSmart A710
HP PhotoSmart A820
HP PhotoSmart C3100
HP PhotoSmart C4100
HP PhotoSmart C4200
HP PhotoSmart C4380
HP PhotoSmart C5100
HP PhotoSmart C5200
HP PhotoSmart C6100
HP PhotoSmart C6200
HP PhotoSmart C7100
HP PhotoSmart C7200
HP PhotoSmart C8100
HP PhotoSmart D5060
HP PhotoSmart D5100
HP PhotoSmart D5300
HP Photosmart D5460
HP PhotoSmart D6100
HP PhotoSmart D7100
HP PhotoSmart D7200
HP PhotoSmart D7300
HP PhotoSmart D7400
HP PhotoSmart P100
HP PhotoSmart P1000
HP PhotoSmart P1100
HP PhotoSmart P1115
HP PhotoSmart P1215
HP PhotoSmart P1218
HP PhotoSmart P130
HP PhotoSmart P1315
HP PhotoSmart P230
HP PhotoSmart Pro B8300
HP PSC 1100
HP PSC 1110
HP PSC 1200
HP PSC 1205
HP PSC 1210
HP PSC 1300
HP PSC 1310
HP PSC 1400
HP PSC 1500
HP PSC 1510
HP PSC 1600
HP PSC 2110
HP PSC 2150
HP PSC 2170
HP PSC 2175
HP PSC 2210
HP PSC 2300
HP PSC 2350
HP PSC 2400
HP PSC 2500
HP PSC 370
HP PSC 380
HP PSC 500
HP PSC 750
HP PSC 750xi
HP PSC 950
Epson: Drivers for Linux
epson-201101w
epson-201101w 6
epson-201102j
epson-201102j 1
epson-201102w
epson-201102w 1
epson-201103j
epson-201103j 1
epson-201104w
epson-201104w 1
epson-201105j
epson-201105j 1
epson-201105w
epson-201105w 7
epson-201106j
epson-201106j 2
epson-201106w
epson-201106w 10
epson-201107w
epson-201107w 2
epson-201108j
epson-201108j 1
epson-201108w
epson-201108w 7
epson-201109w
epson-201109w 2
epson-201110j
epson-201110j 1
epson-201110w
epson-201110w 3
epson-201111j
epson-201111j 1
epson-201111w
epson-201111w 1
epson-201112j
epson-201112j 3
epson-201112w
epson-201112w 5
epson-201113j
epson-201113j 2
epson-201113w
epson-201113w 24
epson-201114j
epson-201114j 1
epson-201114w
epson-201114w 3
epson-201115j
epson-201115j 3
epson-201115w
epson-201115w 8
epson-201201w
epson-201201w 2
epson-201202w
epson-201202w 4
epson-201203j
epson-201203j 2
epson-201203w
epson-201203w 4
epson-201204j
epson-201204j 1
epson-201204w
epson-201204w 4
epson-201205j
epson-201205j 1
epson-201206w
epson-201206w 6
epson-201207w
epson-201207w 7
epson-201208w
epson-201208w 3
epson-201209j
epson-201209j 3
epson-201209w
epson-201209w 2
epson-201210j
epson-201210j 1
epson-201211j
epson-201211j 3
epson-201211w
epson-201211w 7
epson-201212j
epson-201212j 3
epson-201212w
epson-201212w 4
epson-201213j
epson-201213j 4
epson-201213w
epson-201213w 6
epson-201214j
epson-201214j 1
epson-201214w
epson-201214w 2
epson-201215w
epson-201215w 4
epson-201301w
epson-201301w 2
epson-201302w
epson-201302w 2
epson-201303j
epson-201303j 1
epson-201303w
epson-201303w 2
epson-201304j
epson-201304j 1
epson-201304w
epson-201304w 1
epson-201305j
epson-201305j 1
epson-201305w
epson-201305w 1
epson-201306j
epson-201306j 3
epson-201307j
epson-201307j 2
epson-201308w
epson-201308w 3
epson-201309w
epson-201309w 1
epson-artisan-725-835-series
epson-artisan-725-835-series 7
epson-ep-302
epson-ep-302 1
epson-ep-702a
epson-ep-702a 1
epson-ep-703a
epson-ep-703a 1
epson-ep-803a-903f-series
epson-ep-803a-903f-series 4
epson-ep-902a-series
epson-ep-902a-series 2
epson-escpr
epson-escpr 395 Epson Inkjet Printer Driver (ESC/P-R) for Linux
epson-k100-k200-series
epson-k100-k200-series 2
epson-n10-nx127
epson-n10-nx127 17
epson-nx420
epson-nx420 5
epson-px-402a
epson-px-402a 1
epson-px-502a
epson-px-502a 1
epson-px-5v
epson-px-5v 1
epson-px-602f
epson-px-602f 1
epson-px-603f-503a-203-series
epson-px-603f-503a-203-series 3
epson-px-673f
epson-px-673f 1
epson-px-k100
epson-px-k100 1
epson-stylus-nx110-series
epson-stylus-nx110-series 11
epson-stylus-office-tx510fn-series
epson-stylus-office-tx510fn-series 5
epson-stylus-office-tx610fw-series
epson-stylus-office-tx610fw-series 4
epson-stylus-photo-px660-series
epson-stylus-photo-px660-series 1
epson-stylus-photo-px810fw-series
epson-stylus-photo-px810fw-series 6
epson-stylus-photo-r3000
epson-stylus-photo-r3000 1
epson-stylus-photo-t50-series
epson-stylus-photo-t50-series 4
epson-stylus-photo-tx650-series
epson-stylus-photo-tx650-series 2
epson-stylus-s21-series
epson-stylus-s21-series 4
epson-stylus-tx550w-series
epson-stylus-tx550w-series 3
epson-workforce-320-sx218
epson-workforce-320-sx218 9
epson-workforce-525
epson-workforce-525 3
epson-workforce-635-60-nx625-series
epson-workforce-635-60-nx625-series 17
epson-workforce-840
epson-workforce-840 2
epsonc Ghostscript built-in 13
epsonepl IJS 5
epson_l800 1
Brother - Drivers for Linux - Models available with Brother ppd file :
, DCP-7025, DCP-7045N, DCP-8020, DCP-8025D, DCP-8040, DCP-8045D, DCP-8080DN, DCP-8085DN, DCP-9040CN, DCP-9042CDN, DCP-9045CDN, HL-1450, HL-1470N, HL-1650, HL-1670N, HL-1850, HL-1870N, HL-2460, HL-2600CN, HL-2700CN, HL-3260N, HL-3450CN, HL-4050CDN, HL-4070CDW, HL-5050, HL-5070N, HL-5150D, HL-5170DN, HL-5240, HL-5250DN, HL-5270DN, HL-5280DW, HL-5340D, HL-5350DN, HL-5350DNLT, HL-5370DW, HL-5370DWT, HL-5380DN, HL-6050, HL-6050D, HL-7050, HL-7050N, HL-8050N, , MFC-7225N, , MFC-7450, , MFC-7820N, , MFC-7840N, , MFC-7840W, , MFC-8220, , MFC-8420, , MFC-8440, , MFC-8640D, , MFC-8670DN, , MFC-8820D, , MFC-8840D, , MFC-9420CN, , MFC-9440CN, , MFC-9450CDN, , MFC-9840CDW
Brother - Download (Linux Printer Driver - multifunction printer: print - scan - copy - fax - card reader von https://support.brother.com/g/s/id/linux/en/download_prn.html :
PRODUCT INDEX:
Brother DCP
, DCP-110C , DCP-115C , DCP-117C , DCP-120C , DCP-130C , DCP-135C , DCP-1400
, DCP-145C , DCP-150C , DCP-1510 , DCP-1510R , DCP-1511 , DCP-1512 , DCP-1512R
, DCP-1518 , DCP-153C , DCP-155C , DCP-163C , DCP-165C , DCP-167C , DCP-185C
, DCP-195C , DCP-197C , DCP-310CN , DCP-315CN , DCP-330C , DCP-340CW , DCP-350C
, DCP-353C , DCP-357C , DCP-365CN , DCP-373CW , DCP-375CW , DCP-377CW , DCP-383C
, DCP-385C , DCP-387C , DCP-395CN , DCP-540CN , DCP-560CN , DCP-585CW , DCP-6690CW
, DCP-7010 , DCP-7020 , DCP-7025 , DCP-7030 , DCP-7040 , DCP-7045N , DCP-7055
, DCP-7055W , DCP-7057 , DCP-7057WR , DCP-7060D , DCP-7065DN , DCP-7070DW , DCP-750CW
, DCP-770CW , DCP-8020 , DCP-8025D , DCP-8040 , DCP-8045D , DCP-8060 , DCP-8065DN
, DCP-8070D , DCP-8080DN , DCP-8085DN , DCP-8110D , DCP-8110DN , DCP-8112DN , DCP-8150DN
, DCP-8152DN , DCP-8155DN , DCP-8157DN , DCP-8250DN , DCP-9010CN , DCP-9020CDW , DCP-9040CN
, DCP-9042CDN , DCP-9045CDN , DCP-9055CDN , DCP-9270CDN , DCP-J125 , DCP-J132W , DCP-J140W
, DCP-J152W , DCP-J172W , DCP-J315W , DCP-J4110DW , DCP-J515W , DCP-J525W , DCP-J552DW
, DCP-J715W , DCP-J725DW , DCP-J752DW , DCP-J925DW
Brother FAX
, FAX-1815C , FAX-1820C , FAX-1835C , FAX-1840C , FAX-1860C , FAX-1920CN , FAX-1940CN
, FAX-1960C , FAX-2440C , FAX-2480C , FAX-2580C , FAX-2820 , FAX-2840 , FAX-2850
, FAX-2890 , FAX-2900 , FAX-2920 , FAX-2940 , FAX-2950 , FAX-2990 , FAX-3800
, FAX-4100 , FAX-4750e , FAX-5750e
Brother HL
, HL-1030 , HL-1110 , HL-1110R , HL-1111 , HL-1112 , HL-1112R , HL-1118
, HL-1230 , HL-1240 , HL-1250 , HL-1270N , HL-1430 , HL-1435 , HL-1440
, HL-1450 , HL-1470N , HL-1650 , HL-1670N , HL-1850 , HL-1870N , HL-2030
, HL-2035 , HL-2040 , HL-2070N , HL-2130 , HL-2132 , HL-2135W , HL-2140
, HL-2150N , HL-2170W , HL-2220 , HL-2230 , HL-2240 , HL-2240D , HL-2242D
, HL-2250DN , HL-2270DW , HL-2275DW , HL-2280DW , HL-2460 , HL-2460N , HL-2600CN
, HL-2700CN , HL-3040CN , HL-3045CN , HL-3070CW , HL-3075CW , HL-3140CW , HL-3150CDN
, HL-3150CDW , HL-3170CDW , HL-3260N , HL-3450CN , HL-4040CDN , HL-4040CN , HL-4050CDN
, HL-4070CDW , HL-4140CN , HL-4150CDN , HL-4570CDW / , HL-4570CDWT , HL-5030 , HL-5040 , HL-5050
, HL-5070N , HL-5130 , HL-5140 , HL-5150D , HL-5170DN , HL-5240 , HL-5250DN
, HL-5270DN , HL-5280DW , HL-5340D , HL-5350DN , HL-5350DNLT , HL-5370DW , HL-5370DWT
, HL-5380DN , HL-5440D , HL-5450DN / , HL-5450DNT , HL-5470DW / , HL-5470DWT , HL-6050 , HL-6050D , HL-6050DN
, HL-6180DW / , HL-6180DWT , HL-7050 , HL-7050N , HL-8050N , HL-S7000DN
Brother MFC
, MFC-1810 , MFC-1810R , MFC-1811 , MFC-1813 , MFC-1815 , MFC-1815R , MFC-1818
, MFC-210C (DCP-115C) , MFC-215C , MFC-230C , MFC-235C , MFC-240C , MFC-250C , MFC-255CW
, MFC-257CW , MFC-260C , MFC-290C , MFC-295CN , MFC-297C , MFC-3220C , MFC-3240C
, MFC-3320CN , MFC-3340CN , MFC-3360C , MFC-3420C , MFC-3820CN , MFC-410CN , MFC-420CN
, MFC-425CN , MFC-440CN , MFC-465CN , MFC-4800 , MFC-490CW , MFC-495CW , MFC-5440CN
, MFC-5460CN , MFC-5490CN , MFC-5840CN , MFC-5860CN , MFC-5890CN , MFC-5895CW , MFC-620CN
, MFC-640CW , MFC-6490CW , MFC-660CN , MFC-665CW , MFC-6800 , MFC-680CN , MFC-685CW
, MFC-6890CDW , MFC-7220 , MFC-7225N , MFC-7240 , MFC-7290 , MFC-7320 , MFC-7340
, MFC-7345N , MFC-7360 , MFC-7360N , MFC-7362N , MFC-7365DN , MFC-7420 , MFC-7440N
, MFC-7450 , MFC-7460DN , MFC-7470D , MFC-7820N , MFC-7840N , MFC-7840W , MFC-7860DN
, MFC-7860DW , MFC-790CW , MFC-795CW , MFC-820CW , MFC-8220 , MFC-8370DN , MFC-8380DN
, MFC-8420 , MFC-8440 , MFC-845CW , MFC-8460N , MFC-8480DN , MFC-8500 , MFC-8510DN
, MFC-8512DN , MFC-8515DN , MFC-8520DN , MFC-8640D , MFC-8660DN , MFC-8670DN , MFC-8680DN
, MFC-8690DW , MFC-8710DW , MFC-8712DW , MFC-8810DW , MFC-8820D , MFC-8840D , MFC-8840DN
, MFC-885CW , MFC-8860DN , MFC-8870DW , MFC-8880DN , MFC-8890DW , MFC-8910DW , MFC-8912DW
, MFC-8950DW / , MFC-8950DWT , MFC-8952DW / , MFC-8952DWT , MFC-9010CN , MFC-9030 , MFC-9070 , MFC-9120CN , MFC-9125CN
, MFC-9130CW , MFC-9140CDN , MFC-9160 , MFC-9180 , MFC-9320CW , MFC-9325CW , MFC-9330CDW
, MFC-9340CDW , MFC-9420CN , MFC-9440CN , MFC-9450CDN , MFC-9460CDN , MFC-9465CDN , MFC-9560CDW
, MFC-9660 , MFC-9700 , MFC-9760 , MFC-9800 , MFC-9840CDW , MFC-9860 , MFC-9880
, MFC-990CW , MFC-9970CDW , MFC-J220 , MFC-J2310 , MFC-J245 , MFC-J2510 , MFC-J265W
, MFC-J270W , MFC-J280W , MFC-J285DW , MFC-J410 , MFC-J410W , MFC-J415W , MFC-J425W
, MFC-J430W , MFC-J4310DW , MFC-J432W , MFC-J435W , MFC-J4410DW , MFC-J450DW , MFC-J4510DW
, MFC-J4610DW , MFC-J470DW , MFC-J4710DW , MFC-J475DW , MFC-J5910DW , MFC-J615W , MFC-J625DW
, MFC-J630W , MFC-J650DW , MFC-J6510DW , MFC-J6710DW , MFC-J6910DW , MFC-J825DW , MFC-J835DW
, MFC-J870DW , MFC-J875DW
More Linux Printer Drivers, Linux Foundation, https://openprinting.org:
escpage Ghostscript built-in 1
fmlbp Ghostscript built-in 1
fmpr Ghostscript built-in 1
foo2hbpl2 Filter 12
foo2hiperc Filter 19
foo2hiperc-z1 Filter 1
foo2hp Filter 5
foo2kyo Filter 1
foo2lava Filter 11
foo2oak Filter 3
foo2oak-z1 Filter 2
foo2qpdl Filter 22
foo2slx Filter 2
foo2xqx Filter 14
foo2zjs Filter 12
foo2zjs-z1 Filter 8
foo2zjs-z2 Filter 4
foo2zjs-z3 Filter 1
gdi Ghostscript built-in 30
gimp-print 560
gutenprint gutenprint 1638 Top Quality Printer Drivers for inkjets, dye sublim
fmpr Ghostscript built-in 1 ation printers, and PCL lasers
hl1250 Ghostscript built-in 45
hl7x0 Ghostscript built-in 9 Driver for Brother´s proprietary printer language (works also on the PCL/PS models)
hpdj Ghostscript built-in 49
ibmpro Ghostscript built-in 5
imagen Ghostscript built-in 1
iwhi Ghostscript built-in 3
iwlo Ghostscript built-in 3
iwlq Ghostscript built-in 1
jetp3852 Ghostscript built-in 1
jj100 Ghostscript built-in 1
la50 Ghostscript built-in 1
la70 Ghostscript built-in 1
la75 Ghostscript built-in 1
la75plus Ghostscript built-in 1
laserjet Ghostscript built-in 50
lbp310 Ghostscript built-in 1
lbp320 Ghostscript built-in 2
lbp660 Filter 2
lbp8 Ghostscript built-in 3
lbp800 Filter 1
lex5700 Ghostscript built-in 3
lex7000 Ghostscript built-in 1
lips2p Ghostscript built-in 1
lips3 Ghostscript built-in 1
lips4 Ghostscript built-in 3
lips4v Ghostscript built-in 2
lj250 Ghostscript built-in 1
lj4dith Ghostscript built-in 384
lj4dithp Ghostscript built-in 1
lj5gray Ghostscript built-in 204
ljet2p Ghostscript built-in 24
ljet3 Ghostscript built-in 31
ljet3d Ghostscript built-in 16
ljet4 Ghostscript built-in 419 Built-in Ghostscript driver for PCL 5e laser printers
ljet4d Ghostscript built-in 265
ljetplus Ghostscript built-in 23
lm1100 lm1100 Filter 3
ln03 Ghostscript built-in 1
lp2000 Ghostscript built-in 4
lp2563 Ghostscript built-in 1
lp8000 Ghostscript built-in 1
lpstyl Filter 7
lq850 Ghostscript built-in 4
lx5000 Ghostscript built-in 3
lxm3200 Ghostscript built-in 6
lxm3200-tweaked Ghostscript built-in 6
lxm3200X Ghostscript built-in 3
lxm5700m Ghostscript built-in 4
lxx74 2
lz11-V2 Filter 2
m2300w Filter 2
m2400w Filter 2
m8510 Ghostscript built-in 1
md1xMono Ghostscript built-in 2
md2k Ghostscript built-in 5
md50Eco Ghostscript built-in 2
md50Mono Ghostscript built-in 2
md5k Ghostscript built-in 2
min12xxw min12xxw Filter 8
mj500c Ghostscript built-in 3
mj6000c Ghostscript built-in 3
mj700v2c Ghostscript built-in 2
mj8000c Ghostscript built-in 1
ml600 Ghostscript built-in 2
ml85p Filter 2
necp2xX.upp Ghostscript Uniprint 1
necp6 Ghostscript built-in 8
npdl Ghostscript built-in 3
oce9050 Ghostscript built-in 1
oki182 Ghostscript built-in 2
oki4drv Filter 7
oki4w Ghostscript built-in 7
okiibm Ghostscript built-in 3
omni Ghostscript built-in 467
paintjet Ghostscript built-in 1
pbm2l2030 Filter 1
pbm2l7k Filter 7
pbm2lwxl Filter 12
pbm2ppa Filter 1
pbmtozjs Filter 2
pcl3 Ghostscript built-in 91
pcl5-Ricoh pcl5-Ricoh 20 PPD files for Ricoh´s PCL5 printers, supplied by Ricoh
PDF-Gestetner PDF-Gestetner 210 PPD files for Gestetner´s PDF printers, supplied by Ricoh
PDF-Infotec PDF-Infotec 178 PPD files for Infotec´s PDF printers, supplied by Ricoh
PDF-Lanier PDF-Lanier 240 PPD files for Lanier´s PDF printers, supplied by Ricoh
PDF-NRG PDF-NRG 230 PPD files for NRG´s PDF printers, supplied by Ricoh
PDF-Ricoh PDF-Ricoh 248 PPD files for Ricoh´s PDF printers, supplied by Ricoh
PDF-Savin PDF-Savin 228 PPD files for Savin´s PDF printers, supplied by Ricoh
pegg Filter 3
pentaxpj Filter 2
picty180 Ghostscript built-in 1
pj Ghostscript built-in 1
pjetxl Ghostscript built-in 1
pjxl Ghostscript built-in 1
pjxl300 Ghostscript built-in 3
PM760pX.upp Ghostscript Uniprint 1
PM820pX.upp Ghostscript Uniprint 1
pnm2ppa Filter 6
, Postscript PostScript 1230
Postscript-Brother Postscript-Brother PostScript 64 Manufacturer-supplied PPD files for Brother´s PostScript printers
Postscript-Dell Postscript-Dell PostScript 1 Manufacturer-supplied PPD files for Dell´s PostScript printers
Postscript-Epson Postscript-Epson PostScript 37 Manufacturer-supplied PPD files for Epson´s PostScript printers
Postscript-Genicom Postscript-Genicom PostScript 1 Manufacturer-supplied PPD files for Genicom´s PostScript printers
Postscript-Gestetner Postscript-Gestetner PostScript 266 PPD files for Gestetner´s PostScript printers, supplied by Ricoh
Postscript-, HP Postscript-, HP PostScript 8 PPD files for
HP´s PostScript printers which are not supported by
HPLIP, supplied by
HP
Postscript-InfoPrint Postscript-InfoPrint PostScript 3 PPD files for InfoPrint´s PostScript printers, supplied by Ricoh
Postscript-Infotec Postscript-Infotec PostScript 218 PPD files for Infotec´s PostScript printers, supplied by Ricoh
Postscript-KONICA_MINOLTA Postscript-KONICA_MINOLTA PostScript 22 Manufacturer-supplied PPD files for KONICA MINOLTA´s PostScript printers
Postscript-Kyocera Postscript-Kyocera PostScript 118 Manufacturer-supplied PPD files for Kyocera´s PostScript printers
Postscript-Lanier Postscript-Lanier PostScript 297 PPD files for Lanier´s PostScript printers, supplied by Ricoh
Postscript-Lexmark Postscript-Lexmark PostScript 378 Manufacturer-supplied PPD files for Lexmark´s PostScript printers
Postscript-Lexmark-black-only Postscript-Lexmark-black-only PostScript 2 Manufacturer-supplied PPD files for Lexmark´s black-only PostScript printers
Postscript-NRG Postscript-NRG PostScript 291 PPD files for NRG´s PostScript printers, supplied by Ricoh
Postscript-Oce Postscript-Oce PostScript 25 Manufacturer-supplied PPD files for Oce´s PostScript level 3 printers
Postscript-Oce-KM Postscript-Oce-KM PostScript 1 Manufacturer-supplied PPD files for Oce´s PostScript printers
Postscript-Oki Postscript-Oki PostScript 22 Manufacturer-supplied PPD files for Oki´s PostScript printers
Postscript-Ricoh Postscript-Ricoh PostScript 321 PPD files for Ricoh´s PostScript printers, supplied by Ricoh
Postscript-Samsung Postscript-Samsung PostScript 87 PPD files for Samsung´s PostScript printers, supplied by Samsung
Postscript-Savin Postscript-Savin PostScript 290 PPD files for Savin´s PostScript printers, supplied by Ricoh
Postscript-Sharp Postscript-Sharp PostScript 221 Manufacturer-supplied PPD files for Sharp´s PostScript printers
Postscript-Toshiba Postscript-Toshiba PostScript 26 Manufacturer-supplied PPD files for Toshiba´s PostScript printers
Postscript-Xerox Postscript-Xerox PostScript 113 Manufacturer-supplied PPD files for Xerox´s PostScript printers
Postscript1 PostScript 4
Postscript2-Oce Postscript2-Oce PostScript 8 Manufacturer-supplied PPD files for Oce´s PostScript level 2 printers
PostscriptColor-Ricoh PostscriptColor-Ricoh PostScript 96 PPD files for Ricoh´s Postscript color printers, supplied by Ricoh
PostscriptMono-Ricoh PostscriptMono-Ricoh PostScript 103 PPD files for Ricoh´s Postscript monochrome printers, supplied by Ricoh
ppmtocpva Filter 6
ppmtomd Filter 14
pr150 Ghostscript built-in 1
pr201 Ghostscript built-in 1
ptouch Filter 22
pxl1010 Ghostscript built-in 2
pxlcolor Ghostscript built-in 113
pxlcolor-Gestetner pxlcolor-Gestetner Ghostscript built-in 71 PPD files for Gestetner´s PCL XL color printers, supplied by Ricoh
pxlcolor-InfoPrint pxlcolor-InfoPrint Ghostscript built-in 0 PPD files for InfoPrint´s PCL XL color printers, supplied by Ricoh
pxlcolor-Infotec pxlcolor-Infotec Ghostscript built-in 74 PPD files for Infotec´s PCL XL color printers, supplied by Ricoh
pxlcolor-Lanier pxlcolor-Lanier Ghostscript built-in 77 PPD files for Lanier´s PCL XL color printers, supplied by Ricoh
pxlcolor-NRG pxlcolor-NRG Ghostscript built-in 77 PPD files for NRG´s PCL XL color printers, supplied by Ricoh
pxlcolor-Ricoh pxlcolor-Ricoh Ghostscript built-in 87 PPD files for Ricoh´s PCL XL color printers, supplied by Ricoh
pxlcolor-Samsung pxlcolor-Samsung Ghostscript built-in 2 PPD files for Samsung´s PCL-XL color printers, supplied by Samsung
pxlcolor-Savin pxlcolor-Savin Ghostscript built-in 73 PPD files for Savin´s PCL XL color printers, supplied by Ricoh
pxldpl Ghostscript built-in 1
pxljr IJS 3
pxlmono Ghostscript built-in 335
pxlmono-Gestetner pxlmono-Gestetner Ghostscript built-in 100 PPD files for Gestetner´s PCL XL monochrome printers, supplied by Ricoh
pxlmono-InfoPrint pxlmono-InfoPrint Ghostscript built-in 3 PPD files for InfoPrint´s PCL XL monochrome printers, supplied by Ricoh
pxlmono-Infotec pxlmono-Infotec Ghostscript built-in 103 PPD files for Infotec´s PCL XL monochrome printers, supplied by Ricoh
pxlmono-Lanier pxlmono-Lanier Ghostscript built-in 103 PPD files for Lanier´s PCL XL monochrome printers, supplied by Ricoh
pxlmono-NRG pxlmono-NRG Ghostscript built-in 103 PPD files for NRG´s PCL XL monochrome printers, supplied by Ricoh
pxlmono-Ricoh pxlmono-Ricoh Ghostscript built-in 108 PPD files for Ricoh´s PCL XL monochrome printers, supplied by Ricoh
pxlmono-Samsung pxlmono-Samsung Ghostscript built-in 14 PPD files for Samsung´s PCL-XL monochrome printers, supplied by Samsung
pxlmono-Savin pxlmono-Savin Ghostscript built-in 101 PPD files for Savin´s PCL XL monochrome printers, supplied by Ricoh
r4081 Ghostscript built-in 3
rastertokmXXXXdl 4 Free software printer drivers for the magicolor DL series from KONICA MINOLTA
rastertosag-gdi 2 Free software printer driver for the SAG-GDI protocol on Ricoh lasers
rpdl Ghostscript built-in 4
s400X1.upp Ghostscript Uniprint 2
sharp.upp Ghostscript Uniprint 6
sipixa6.upp Ghostscript Uniprint 1
sj48 Ghostscript built-in 1
slap Filter 9
splix splix 51 Driver for Samsung SPL2 (ML-1710, ...) and SPLc (CLP-500, ...) laser printers
st640X.upp Ghostscript Uniprint 2
st800 Ghostscript built-in 2
stc1520h.upp Ghostscript Uniprint 2
stc200_h.upp Ghostscript Uniprint 1
stc2X.upp Ghostscript Uniprint 3
stc300X.upp Ghostscript Uniprint 2
stc500pX.upp Ghostscript Uniprint 2
stc600X.upp Ghostscript Uniprint 4
Stc670pX.upp Ghostscript Uniprint 1
Stc680pX.upp Ghostscript Uniprint 1
stc740X.upp Ghostscript Uniprint 4
Stc760pX.upp Ghostscript Uniprint 1
Stc777pX.upp Ghostscript Uniprint 1
stc800X.upp Ghostscript Uniprint 2
stcanyX.upp Ghostscript Uniprint 4
stcolor Ghostscript built-in 22
stcX.upp Ghostscript Uniprint 5
Stp720pX.upp Ghostscript Uniprint 1
Stp870pX.upp Ghostscript Uniprint 1
t4693dX Ghostscript built-in 1
tek4696 Ghostscript built-in 3
xes Ghostscript built-in 3
More Linux printer drivers (rpm, deb)
Samsung Laser Printer SPL2 and SPLc: splix (el6) - cups-drivers-splix (pclos, el6), openprinting-splix
More Linux printer drivers (rpm, deb)
Samsung Laser Printer SPL2 and SPLc: splix (el6) - cups-drivers-splix (pclos, el6), openprinting-splix
openprinting-ppds (deb, rpm openprinting-ppds (fc, el7, el6, rosa, debian), gutenprint Linux printer drivers (dev, rpm gutenprint (fc, el7, el6, rosa, debian), foomatic Linux printer drivers ( deb, rpm foomatic (fc, el7, el6, rosa, debian) )
Linux Foundation openprinting.org, https://support.brother.com/g/s/id/linux/en/download_prn.html
Brother-printer does not printout - that´s, what you can do, CHIP, 25.06.2020
Mit Ihrem Brother Drucker können Sie Dokumente, Fotos und mehr ausdrucken. Wenn der Drucker nicht mehr druckt, liegt in der Regel ein Problem vor, das Sie selbst beheben können. Die wichtigsten Tipps finden Sie in diesem Artikel.
https://praxistipps.chip.de/brother-drucker-druckt-nicht-das-koennen-sie-
tun_42235
https://tipps.computerbild.de/hardware/drucker/brother-drucker-druckt-nicht-
daran-kann-es-liegen-336105.html
https://www.heise.de/tipps-tricks/Drucker-druckt-nicht-was-tun-3845599.html
https://praxistipps.chip.de/drucker-druckt-nicht-die-haeufigsten-fehler-
loesungen_37545
But several years later after printing always fine (with CUPS 1.4.6 (pclos2016)), our Brother DCP-115C failed again!
We can´t explain. This might be caused by installations and updates.
Good to remember running cups in log-level "debug" to set in /etc/cups/cupsd.conf .
The most annoying error-message one can imagine for cups appeared in /var/log/error_log, we mean the one with the invalid pointer out of rasterobeij2.
To remember: This had to do with the glibc-version. For DCP-115C you should keep a second, fitting good old glibc like libc-2.19 or libc-2.17.so (glibc(el6, mdv2010, mdv2011) not in /lib64, but /usr/lib64 .
Then we relinked belonging libanl, libnsl, libdl, libm in /usr/lib64 from the actual glibc version down to 2.19 resp. 2.17 too. This is what we had already done before
But nothing with it here!
Looking into /var/log/cups/error_log (of log-level debug) again:
CUPS also missed executables like the well-known command rm (remove) and mktemp. This (like this one with the glibc-invalid-pointer) got marked as a D (debug-message), not an E (error).
They are stored in /bin, but not /usr/bin.
So just link them with /usr/bin:
ln -sf /bin/rm /usr/bin/rm
ln -sf /bin/mktemp /usr/bin/mktemp.
And CUPS doesn´t work with /usr/lib/cups/filter/pdftops anymore. This got marked as E (an error).
So we replaced it with another, 70 up to 80 percent smaller sized one (from another version, don´t know, which one, as it got saved stored beneath the damaged one in the same directory with the name pdftops-save before).
Printing a testpage (with kwrite or system-config-printer):
You see (as we hope): DCP-115C works again by printing the printout as usual, Gooken, 11.28.2024.
But other programs like kwrite like office (LibreOffice or OpenOffice) do not make a printout?
You might got installed cups-filters (rpm).
Uninstall it!
rpm -e --nodeps cups-filters
Checkout A4 (borderless) and color equal set to grayscale (we think) for your printer in system-config-printer and the Office again.
Now, all other programs make the printout too!
Don´t you know? There are 64-bit-driver for Brother MFC and DCP printers from another distribution in:
brother-lpr-drivers-extra_1.2.0-2-0ubuntu5_amd64.deb, but still not within cups-filters.
Or try 64-bit-third-party-driver for Brother DCP- and MFC-printers: vuex64-9.8.40.rpm (for free), recommended by grand brands like Shell and so on. But this does not work with some libraries (libcairo2....) of our system.
Like our DCP-115C: Canon introduces printer with refillable tanks, PC-WELT.de, 08.04.2019
Mit dem Pixma G6050, G5050 und GM2050 bringt Canon weitere Drucker auf den Markt, deren Tintentanks sich ...
https://www.pcwelt.de/news/Canon-stellt-Drucker-mit-wiederbefuellbaren-Tintentanks-vor-10571123.html
HP Tango X
Scandi-Look statt Büro-Tristesse: Dieser Drucker ist so schick, dass er auch ins Wohnzimmer darf, STERN.de, 26.06.2020
https://www.stern.de/digital/tests/hp-tango-x-im-test--dieser-drucker-ist-so-schick--dass-er-auch-ins-wohnzimmer-darf-8702216.html
Printer ink cartrdiges in comparison: Cheap ink must not be bader, SPIEGEL ONLINE, 25.07.2018
Druckertinte von Drittanbietern ist oft erheblich günstiger als die Originaltinte der Gerätehersteller. Die Ausdrucke sind laut einem Vergleich der Stiftung Warentest manchmal trotzdem gleichwertig.
Den denkbar unsouveränsten Umgang mit billigen Ersatzpatronen für seine Drucker hatte das Unternehmen HP im Jahr 2016 demonstriert: Der Hersteller hatte an einige seiner Druckermodelle ein Firmware-Update verteilt, das Monate später heimlich eine neue Funktion aktivierte. Die sorgte dafür, dass nur noch Tintenpatronen mit einem HP-Sicherheitschip von den Geräten erkannt wurden. Alle anderen Patronen lösten eine Fehlermeldung aus, auch wenn sie vorher funktioniert hatten. HP bat später für sein Vorgehen
Gegen Corona: 3D-Drucker drucken Schutzmasken und Ventile, PC-WELT.de, 30.03.2020
Gesichtsschutz, Schutzmasken und Ventile für Beatmungsgeräte lassen sich mit dem 3D-Drucker ausdrucken. Sowohl von privaten Nutzern als auch vom Deutschen Zentrum für Luft- und Raumfahrt DLR.
https://www.pcwelt.de/news/Gegen-Corona-3D-Drucker-drucken-Schutzmasken-und-Ventile-10782123.html
http://www.spiegel.de/netzwelt/gadgets/druckerpatronen-stiftung-warentest-vergleicht-druckertinte-von-drittanbietern-a-1219949.html
Smarte future with green printers, ANZEIGE auf PC-Magazin.de, 01.06.2018
"[...] Langlebige Komponenten und Betriebszyklen minimieren auch das Abfallaufkommen der neuen Single-Funktions- und Multifunktions-Serien (MFPs) - Stichwort "Null-Abfall-Strategie". Das senkt zudem den Bedarf an Service und Support.
Doppelt so hohe Rückführungs- Quote zum Branchendurchschnitt
Für Lexmark ist grüne Nachhaltigkeit schon seit der Unternehmensgründung Anfang der 1990er Jahre ein zentraler Unternehmenswert - von der Produktentwicklung bis hin zur ganzheitlichen Kreislaufwirtschaft.
Umweltbelastend ist vor allem die Verbrennung von Druckkassetten.
Lexmark erhöht daher die Rückführungsquote seiner Druckkassetten kontinuierlich: 2017 lag die Rückführungsquote in Europa noch bei 38 Prozent - der derzeitige Branchendurchschnitt liegt bei der Hälfte. 2018 will das Unternehmen diesen Wert auf 50 Prozent steigern. Lexmark führt das Prinzip der Kreislaufwirtschaft weiter: Rohstoffe sollen über den Lebenszyklus der Geräte hinaus möglichst vollständig in den Produktionsprozess zurückgelangen.
Schon heute verwendet Lexmark zurückgeführte Druckkassetten zu 100% wieder oder recycelt sie. Dies macht auch die Lexmark DRUCKERN"Corporate"-Druckkassette möglich: aus recycelten Komponenten bestehend, bietet sie die gleiche Leistung wie herkömmliche Druckkassetten - und das inklusive der gleichen Garantie. Grüne Prinzipien und maximale Effizienz sind keine Gegensätze: Mit den Tonersensoren der Lexmark Drucker lassen sich die Original-Druckkassetten punktgenau ohne Verschwendung auswechseln.
über 98% der zurückgegebenen Druckkassetten sind mittlerweile komplett leer. Der Resttoner aus den verbleibenden 2% wird durch eine Art Staubsaugverfahren entfernt und dient zur alternativen Energiegewinnung. Ein weiteres innovatives Toner-Recycling realisiert Lexmark gemeinsam mit der Nachhaltigkeits-Initiative "Close the Loop" : Hier wird gebrauchter Toner zum Bestandteil von TonerPave, einem umweltfreundlichen Asphaltzusatz.
Umweltschutz und Nachhaltigkeit in der Unternehmens-DNA
Umweltschutz und Nachhaltigkeit sind bei Lexmark schon in die Unternehmens-DNA übergegangen. Dafür forciert der Druckerhersteller viele weitere positive Entwicklungen über die Druckkassette hinaus: die kontinuierliche Senkung des Stromverbrauchs durch intelligente Stromspar- und Ruhe-Modi sowie den energiesparenden Unison-Toner, der bei einer deutlich niedrigeren Temperatur fixiert wird als herkömmlicher Toner. Managed Print Services verringern Druckvolumina, es kommen verstärkt (PCR-) Kunststoffe durch wiederaufbereitete Komponenten aus Altgeräten zum Einsatz und man forciert technische Entwicklungen mit dem Ziel einer immer höheren Lebensdauer für Lexmark-Drucker."
https://www.pc-magazin.de/ratgeber/lexmark-sw-enterprise-drucker-nachhaltigkeit-sicherheit-3199464.html
Drucker with self-refilling ink cartridge, PC-WELT.de, 14.11.2017
Mit dem Ecotank ET-7700 präsentiert Epson die überarbeitete Fassung der Multifunktionsgeräteserie mit selbst nachfüllbaren Tintentanks. Eine echt innovative Weiterentwicklung, wie der Test zeigt.
https://www.pcwelt.de/a/epson-ecotank-et-7700-im-test,3448750
3D-printer: towns, houses, cars, protective masks, ventils, food/meat, ...: printout many and more things by pregiven templates out of increasing amount of files, archives and out of the internet, construction drawings, 3D-scanners or by making specific measurements!
3dprinter-udev-rules-0.2.1-1-rosa2016.1.noarch.rpm
/etc/udev/rules.d/66-3dprinter.rules
# udev rules for 3D printers, CNCs, laser cutters, 3D scanners, etc.
# Minitronic, Megatronic, Sanguinololu, Melzi (Prusa i2/i3, RebeliX, Velleman K8200)
SUBSYSTEMS=="usb", ATTRS{idVendor}=="0403", ATTRS{idProduct}=="6001", ENV{ID_MAKER_TOOL}="1"
# MakerBot Replicator Z18
SUBSYSTEMS=="usb", ATTRS{idVendor}=="23c1", ATTRS{idProduct}=="0006", ENV{ID_MAKER_TOOL}="1"
# MakerBot Replicator 2X
SUBSYSTEMS=="usb", ATTRS{idVendor}=="23c1", ATTRS{idProduct}=="b017", ENV{ID_MAKER_TOOL}="1"
# Arduino Mega with RAMPS, Arduino UNO* (Ultimaker Original, Ciclop scanner, ...)
SUBSYSTEMS=="usb", ATTRS{idVendor}=="2341", ATTRS{idProduct}=="0042", ENV{ID_MAKER_TOOL}="1"
# RAMBO (Lulzbot Mini, Lulzbot TAZ 4, ...)
SUBSYSTEMS=="usb", ATTRS{idVendor}=="27b1", ATTRS{idProduct}=="0001", ENV{ID_MAKER_TOOL}="1"
# Teensyduino (Imprimante 3D Microdelta Originale, ...)
SUBSYSTEMS=="usb", ATTRS{idVendor}=="16c0", ATTRS{idProduct}=="0483", ENV{ID_MAKER_TOOL}="1"
# The following rule can be removed once the systemd upstream support will get
# widely adopted (IMHO it should be safe to remove in 2017+)
# https://github.com/systemd/systemd/pull/2844
ENV{ID_MAKER_TOOL}=="?*", TAG+="uaccess"
Gegen Corona: 3D-Drucker drucken Schutzmasken und Ventile, PC-WELT.de, 30.03.2020
Gesichtsschutz, Schutzmasken und Ventile für Beatmungsgeräte lassen sich mit dem 3D-Drucker ausdrucken. Sowohl von privaten Nutzern als auch vom Deutschen Zentrum für Luft- und Raumfahrt DLR.
https://www.pcwelt.de/news/Gegen-Corona-3D-Drucker-drucken-Schutzmasken-und-Ventile-10782123.html
Alterantive for meat: Sie sehen aus wie Leinenstoff, sollen aber schmecken wie echte Steaks - Bratlinge aus dem 3D-Drucker, STERN.de, 03.03.2019
Auf dem Mobile World Congress in Barcelona stellte ein Unternehmen ein Gerät zum Drucken von veganen Koteletts vor. Bestehend aus Reisprotein, Erbsenprotein und Algen sollen sie eine ähnliche Faserstruktur aufweisen wie echtes Fleisch.
https://www.stern.de/genuss/trends/sie-sollen-schmecken-wie-echte-steaks---koteletts-aus-dem-3d-drucker-8603110.html
3D-printer in test: These are the best 3D-printer
Komplexe Kreationen aus Kunststoff, CHIP, 25.03.2020
3D-Drucker haben sich etabliert und ihre Einsatzmöglichkeiten sind noch lange nicht ausgeschöpft. Dienstleister bieten professionellen 3D-Druck auf Bestellung, doch die Geräte sind inzwischen auch für heimischen Anwender erschwinglich geworden. Wer die beste Qualität für zuhause will, zahlt aber immer noch einen heftigen Preis: Unser Testsieger ist der Ultimaker S5 und der 3D-Drucker auf FDM-Basis kostet über 6.000 Euro. Unseren Preistipp bekommen Sie für einen Bruchteil: Der immer noch gute Anycubic I3 Mega ist für rund 300 Euro zu haben. Spitzengeräte sind auch im 1.000-Euro-Bereich erhältlich. Es gibt aber Unterschiede in der Drucktechnik - alle Wichtige erfahren Sie hier.
Wir haben über 20 3D-Drucker in unserem Testcenter getestet, und die Ergebnisse zuletzt im Januar 2020 aktualisiert.
Obwohl der 3D-Druck erst vor wenigen Jahren massentauglich wurde, gibt es die Geräte bereits seit Ende der Achtzigerjahre. Seither wurde die Technik stetig verfeinert und die Fabrikationskosten wurden gesenkt, so dass 3D-Drucker nun auch im semiprofessionellen und im Hobbybereich anzutreffen sind. Es gibt verschiedene Drucktechniken, in den Heimanwender-Geräten kommen im Wesentlichen aber zwei Methoden zum Einsatz: [...]
https://www.chip.de/artikel/3D-Drucker-Test-Das-sind-die-besten-3D-Drucker_182566194.html
World record: 641-qm-house out of the 3D-printer, PC-WELT.de, 07.02.2020
Das größte Gebäude der Welt aus dem 3D-Drucker ist fertig. Es ist 641 Quadratmeter groß und besitzt zwei Stockwerke.
https://www.pcwelt.de/news/Weltrekord-641-Quadratmeter-Haus-aus-dem-3D-Drucker-10751031.html
New kind of building : 4000 Dollar cost per house: Company aims to build a complete village out of the 3D-printer, STERN.de, 18.05.2019
Gedruckt statt Stein auf Stein: Mit einem 3D-Drucker planen das Bautechnologie-Startup Icon und die Nonprofit-Organisation New Story derzeit 50 Häuser für bedürftige Familien zu bauen. Glatte Wände darf dabei jedoch keiner. erwarten.
https://www.stern.de/digital/tests/dorf-aus-dem-3d-drucker-8709798.html
Online Faxe senden und empfangen, PC-WELT.de, 12.08.2019
Um Faxnachrichten zu senden und zu empfangen, brauchen Sie kein Faxgerät. Das können Sie auch online erledigen.
https://www.pcwelt.de/a/online-faxe-senden-und-empfangen,3463870
Bestückte Leiterplatten produzieren: Prüfadapter aus dem 3D-Drucker
Die gedruckten Adapter sind auf den Prüfling zugeschnitten und dadurch kleiner als herkömmliche Prüfadapter. Geschäftsführer Georg…
http://www.finanznachrichten.de/nachrichten-2018-03/43357233-bestueckte-leiterplatten-produzieren-pruefadapter-aus-dem-3d-drucker-610.htm
Hart: 3D Drucker Formen Widerstandsfähige Metalle
3D-Drucker verbinden viele Menschen mit Plastik. Zurecht, denn die meisten 3D-Drucker formen Kunstoffpulver zu neuen Gegenständen. Aber es…
https://www.newsdeutschland.com/video/20160227/15409/Hart-3D-Drucker-Formen-Widerstandsfähige-Metalle.htm
Autos aus dem 3D-Drucker
Zuschauen, wie das neue Wunschauto per 3D-Drucker entsteht? Noch ist das Zukunftsmusik, aber eine US-Firma bastelt bereits an einem Prototypen, bei dem das Chassis zu 100 Prozent gedruckt und mit dem Elektromotor dann zusammengebaut wird. Markus Schmidt hat sich das angeschaut. | video, https://www.tagesschau.de/ausland/auto-3d-drucker-101.html
3D-Drucker sollen leichte und preiswerte Autos ermöglichen , PC-WELT
Designer Jim Kor präsentiert mit dem Urbee 2 ein kleines Großstadt-Auto, dessen Teile mit Hilfe von 3D-Druckern produziert werden. Das ermöglicht nicht nur eine leichtere Bauweise, sondern auch geringere Anschaffungskosten.
http://www.pcwelt.de/news/3D-Drucker_sollen_leichte_und_preiswerte_Autos_ermoeglichen_-Forschung-7557087.html
Quality Life Forum 2016
Neue Formen von Mobilität: Fahren wir bald ein Auto aus dem 3D-Drucker?, FOCUS Online, 10.09.2016
Quality Life Forum 2016: Neue Formen von Mobilität: Das Quality Life Forum in Kitzbühel steht dieses Jahr im Zeichen der Mobilität. Lange hat sich in diesem Bereich wenig verändert, doch die Digitalisierung macht auch hier nicht halt. In Kürze soll die große Wende kommen und dabei ..., http://www.focus.de/gesundheit/qualitylifeforum/quality-life-forum-2016-neue-mobilitaet-elektroautos-car-sharing-und-autos-aus-dem-3d-drucker_id_5613038.html .
3D-Drucker füs Haus: Hier wird Beton gedruckt!, CHIP, 23.06.2016
Ein großer Schritt zum günstigen Hausbau. Wenn Sie Lust auf das Thema 3D-Druck bekommen haben, sollten Sie sich anschauen, was der Markt an 3D-Druckern gerade bietet. Unsere Bestenliste gibt einen guten Überblick und Sie sehen, was Sie sich für Ihr Zuhause zulegen können. Ein Hausdruck ist damit zwar nicht möglich, aber Schachfiguren, Kleiderhaken, kleine Dosen, Halterungen und vieles mehr, http://www.chip.de/news/3D-Drucker-fuers-Haus-Hier-wird-Beton-gedruckt_95760815.html .
3D-Drucker druckt ganze Villa - Und sie ist sogar erdbebensicher, CHIP, 05.07.2016
http://www.chip.de/news/3D-Drucker-druckt-ganze-Villa-Und-sie-ist-sogar-erdbebensicher_96220059.html
Light Rider: E-Motorrad aus dem 3D-Drucker, PC-WELT.de, 23.05.2016
Mit dem Light Rider hat das Airbus-Tochterunternehmen APWorks ein Elektro-Motorrad aus dem 3D-Drucker entwickelt.
Angelehnt an den legendären Cafe Racer hat die Airbus-Tochter APWorks ein E-Motorrad aus dem 3D-Drucker entwickelt. Die Umsetzung des speziellen Rahmen-Designs sei nur mit dieser Technik möglich gewesen. Der an natürliche Strukturen erinnernde Rahmen wiegt nur sechs Kilogramm. Zusammen mit Batterie und E-Motor bringt der Light Rider lediglich 35 Kilogramm auf die Waage. Damit ist das E-Motorrad rund ein Drittel leichter als die Konkurrenz, http://www.pcwelt.de/news/Light-Rider-E-Motorrad-aus-dem-3D-Drucker-9984690.html
Schuhe aus dem Drucker Euromaxx
Die neue Generation von 3D-Druckern verspricht alle Bereiche des Designs zu revolutionieren. Der Schwede Naim Josefi nutzt die Technik, um…
https://www.newsdeutschland.com/video/20160402/17134/Schuhe-aus-dem-Drucker-Euromaxx.htm
Eine fleischfreie Zukunft?: Fleischfreier Beyond Burger bei Lidl: Seit heute auf dem Markt und schon ausverkauft, STERN.de, 30.05.2019
Das Potential einer fleischfreien Ära ist gigantisch. Zielgruppe sind nicht nur Veganer, sondern alle, die gern Fleisch essen, aber trotzdem um die Problematik des Fleischkonsums wissen. Eine Lösung bringt Beyond Meat mit den fleischfreien Burger, der jedoch wie ein herkömmlicher schmecken soll.
https://www.stern.de/genuss/lidls-beyond-burger--seit-heute-auf-dem-markt-und-schon-ausverkauft-8732278.html
Skurriles aus dem 3D-Drucker: Pizza, Fleisch & Hunde-Rollstühle - CHIP, 01.03.2016
Der Mensch aus der Maschine
In Australien wurde der erste Knochen aus dem 3D-Drucker erfolgreich transplantiert. Doch nicht nur die Medizin nutzt die neue Technik. Wir zeigen Ihnen die skurrilsten Produktionen aus 3D-Druckern.
Fertige 3D-Druckvorlagen im Web finden, PC-WELT.de, 29.06.2016
Viele druckbare 3D-Vorlagen gibt es schon. Sie zu finden, ist die Kunst. Auf diesen Plattformen im Internet werden Sie fündig, http://www.pcwelt.de/tipps/Fertige-3D-Druckvorlagen-im-Web-finden-10000359.html .
Nie wieder Glatze: Künstliche Haare aus dem 3D-Drucker, CHIP, 07.08.2016
http://www.chip.de/news/Nie-wieder-Glatze-Kuenstliche-Haare-aus-dem-3D-Drucker_97893820.html
Rapid Prototyping: US-Armee entwickelt günstigen 3D-Drucker - Golem.de
Das Space and Missile Defense Command der US-Armee hat einen eigenen 3D-Drucker hergestellt, der knapp 700 US-Dollar kosten soll. Das Gerät ist mit dem Ziel entwickelt worden, dass sich künftig...
http://rss.feedsportal.com/c/33374/f/578068/p/1/s/437cc74a/l/0L0Sgolem0Bde0Cnews0Crapid0
Eprototyping0Eus0Earmee0Eentwickelt0Eguenstigen0E3d0Edrucker0E12110E956330Erss0Bhtml/story01.htm
Gedruckte Organe aus dem 3D-Drucker: Hautstücke und Herzklappen, Ohren, Nasen oder eine Niere: Viele Menschen benötigen Ersatz für kranke Organe. Bislang stammen sie von Spendern und sind sehr rar. Können 3-D-Drucker diesen Engpass überbrücken?
Längst ist es keine Fiktion mehr: In vielen Labors forschen Wissenschaftler, um aus Stammzellen von Patienten eine "Tinte" zu entwickeln, die Schicht um Schicht neue Organe ausdruckt und damit Organspenden überflüssig machen könnte.
Was heute noch Vision ist, kann schon in wenigen Jahren Wirklichkeit sein und vielen Patienten wieder Hoffnung geben. Im Labor gelingt es sogar schon, funktionstüchtige, menschliche Organe "nachzubauen". Das lässt die allein in Deutschland aktuell etwa 11.000 Patienten hoffen, die auf ein Ersatzorgan warten, weil ihr Herz oder ihre Niere erkrankt oder verletzt sind. Dem gegenüber stehen aber nur etwa 1.200 Spender, denen Organe entnommen werden können. Helfen könnte diesen Patienten künstliche Organe aus lebenden Zellen, die im 3-D-Drucker entstehen und die ihnen Ärzte einpflanzen. Weltweit arbeiten Forscher an Universitäten daran. Schon "in drei bis fünf Jahren", will Stuart Williams von der University of Louisville (Kentucky) ein Herz aus Einzelteilen aus einem 3-D-Drucker zusammensetzen und implantieren. Aber können Sie sich vorstellen, mit einem gedruckten Organ zu leben?
3D-Drucker baut Haus in nur 24 Stunden: Und der Preis ist unschlagbar, CHIP, 02.04.2018
Ein einstöckiges Haus innerhalb von einem Tag bauen? Genau das macht das amerikanische Startup ICON möglich. Mithilfe eines speziellen 3D-Druckers will das Unternehmen die weltweite Wohnraumknappheit bekämpfen.
Jeder soll ein Dach über den Kopf bekommen
Das amerikanische Startup ICON schafft etwas, was viele für unmöglich hielten. Innerhalb von 24 Stunden kann ein 3D-Drucker ein Haus bauen.
Dabei dauert der Bau nur ein Bruchteil der Zeit, die sonst für Neubauten benötigt wird.
Das Haus sieht modern und schick aus, hat ein Wohnzimmer, Schlafzimmer, Badezimmer und eine gewölbte Veranda.
Auch der Preis kann sich sehen lassen:
Es kostet nur 4.000 Dollar, da die Material- und Arbeitskosten vergleichsweise gering sind.
Mit der Methode will ICON gemeinsam mit der Nonprofit-Organisation"New Story" die weltweite Wohnraumknappheit bekämpfen.
Wenn alles nach Plan läuft, entsteht im nächsten Jahr eine Gemeinschaft aus rund 100 Häusern für die Bewohner von El Salvador.
Und vielleicht gibt es sie ja auch bald bei uns.
http://www.chip.de/news/3D-Drucker-baut-Haus-in-nur-24-Stunden-Und-der-Preis-ist-unschlagbar_135927528.html
Download: Spannende 3D-Druckvorlagen,
http://www.chip.de/downloads/3D-Vorlage-Full-Size-Chess-Set_63228355.html
http://www.chip.de/downloads/SD-MicroSD-und-USB-Staender-3D-Vorlage_63006172.html
http://www.chip.de/downloads/NASA-3D-Druckvorlagen_71278045.html
Italiener druckt 100-qm-Haus in 48 Stunden: Doch das Genialste ist sein Material, CHIP, 20.04.2018
Mit einem 3D-Drucker lassen sich allerhand Dinge fertigen. Seien es Ersatzteile, Handprothesen oder Bauteile für Raketen. Neuerdings können sogar ganze Gebäude gedruckt werden.
Ein großes Haus mit einem 3D-Drucker innerhalb von 48 Stunden herstellen? Das erscheint wie eine Traumvorstellung. Dass dies durchaus möglich ist, bewies nun der bekannte italienische Architekt Massimiliano Locatelli auf der Mailänder Designwoche. Er präsentierte dort, wie die Gebäude der Zukunft aussehen könnten. Wie genau das Verfahren funktioniert, sehen Sie im Video.
3D-Drucker im Test
Wenn Sie Lust auf das Thema 3D-Druck bekommen haben, sollten Sie sich anschauen, was der Markt an 3D-Druckern gerade bietet. Unsere Bestenliste gibt einen guten überblick und Sie sehen, was Sie sich für Ihr Zuhause zulegen können. Ein Hausdruck ist damit zwar nicht möglich, aber Schachfiguren, Kleiderhaken, kleine Dosen, Halterungen und vieles mehr.
Bestenliste: Alle 3D-Drucker im Test, http://www.chip.de/bestenlisten/Bestenliste-3D-Drucker--index/index/id/1111
Dieses Haus hat ein 3D-Drucker ausgedruckt, PC-WELT.de, 07.03.2017
Das Start-Up Apis Cor hat das erste Haus gebaut, welches nahezu komplett aus einem 3D-Drucker stammt.
http://www.pcwelt.de/a/dieses-haus-hat-ein-3d-drucker-ausgedruckt,3422723
Mercedes: Wir produzieren mehr Bauteile selbst
Auch interessant: Weltpremiere der Fertigungstechnik Titan-Teil: Bugatti bringt Bremssattel aus dem 3D-Drucker Zusammen mit dem Hamburger…
http://www.finanznachrichten.de/nachrichten-2018-03/43344721-mercedes-wir-produzieren-mehr-bauteile-selbst-548.htm
Britische Tochter Material Solutions: Siemens investiert in 3D-Druck-Anlage
Die Anzahl der 3D-Drucker soll auf insgesamt 50 steigen, außerdem sollen 50 Arbeitsplätze entstehen. Die Investition ist Teil der…
http://www.finanznachrichten.de/nachrichten-2018-03/43332503-britische-tochter-material-solutions-siemens-investiert-in-3d-druck-anlage-129.htm
Forscher entwickeln künstliche Muskeln mit 3D-Drucker, PC-WELT
Synthetisch im 3D-Drucker erzeugte Muskeln könnten schon bald humanoide Roboter mit Superkräften ermöglichen.
https://www.pcwelt.de/a/forscher-entwickeln-kuenstliche-muskeln-mit-3d-drucker,3448174
Neues Verfahren erkennt gehackte 3D-Drucker, PC-WELT
Ein neues Sicherheitsverfahren soll erkennen, ob ein 3D-Drucker manipuliert wurde.
https://www.pcwelt.de/a/neues-verfahren-erkennt-gehackte-3d-drucker,3447801
Kommt nach dem 3D-Drucker nun der 3D-Stricker?, PC-WELT.de, 25.04.2017
Die Strickmaschine Kniterate nimmt Designs vom PC entgegen und strickt im Anschluss eigenständig.
http://www.pcwelt.de/a/kniterate-revival-der-strickmaschine-im-heimbereich,3446561
Nachdem er selbst wieder greifen kann: 5-Jähriger baut Handprothesen im 3D-Drucker - und jeder kann sie bezahlen
Einen Brief schreiben, essen, Zähne putzen: Für Menschen mit deformierten Händen keine leichte Aufgabe. Passgenaue Prothesen, die den…
http://www.chip.de/news/Nachdem-er-selbst-wieder-greifen-kann-Fuenfjaehriger-baut-Prothesen-im-3D-Drucker-und-jeder-kann-die-bezahlen_136229045.html
Galerie
3D Modelle: Kostenlose Download-Tipps, PC-Magazin.de, 23.3.2017
Sie haben einen 3D-Drucker und suchen kostenlose 3D-Modelle? Unsere Galerie zeigt Ihnen verschiedene Download-Tipps.
http://www.pc-magazin.de/bildergalerie/3d-modelle-kostenlos-download-free-tipps-galerie-3197594-118533199.html
Motorrad aus dem 3D-Drucker Euromaxx
Der "Light Rider&quto; ist nicht das schnellste Motorrad - aber er hat eine besondere Geschichte! Das Motorrad wiegt gerade einmal 35 Kilogramm…
https://www.newsdeutschland.com/video/20160820/22076/Motorrad-aus-dem-3D-Drucker-Euromaxx.htm
Knochenersatz: Frau erhält neuen Unterkiefer aus 3D-Drucker, SPIEGEL ONLINE
Belgische Chirurgen haben einer 83-jährigen Patientin einen neuen Unterkiefer aus Titan und Keramik eingesetzt. Die Prothese wurde mit einem...
http://www.spiegel.de/wissenschaft/medizin/knochenersatz-frau-erhaelt-neuen-unterkiefer-aus-3d-drucker-a-813885.html
Herzsensor aus dem 3D-Drucker, heise online
Wissenschaftler wollen die menschliche Blutpumpe künftig extrem genau vermessen, um Schrittmacher und andere Hilfsmittel besser anzupassen.
http://www.heise.de/newsticker/meldung/Herzsensor-aus-dem-3D-Drucker-2133385.html
Haut und Ohren zum Ausdrucken: 3D-Drucker schaffen die Welt der Zukunft, FOCUS Online
Ersatzhaut für verletzte Kinder aus körpereigener DNA, Lungengewebe oder künstliche Ohren - Forscher entwickeln 3D-Drucker, die die Produktion der ...
http://www.focus.de/wissen/zukunft-entwicklung/technologie/tid-29759/haut-und-ohren-zum-ausdrucken-3d-drucker-schaffen-die-welt-der-zukunft_aid_928417.html
Das Wunder aus dem 3D-Drucker: Chirurgen flicken entstelltes Gesicht - n-tv.de
Die 3D-Druck-Revolution ist in vollem Gange. Ob Lebensmittel, Geschenke oder Autos - zukünftig kommt einfach alles aus dem Drucker. Auch vor der ...
http://www.n-tv.de/panorama/Chirurgen-flicken-entstelltes-Gesicht-article12449136.html
Essen aus dem 3D-Drucker Wirtschaft
Mehr unter http://www.dw.com/de/themen/wirtschaft/s-1503 3D-Druck wird In Barcelona ganz groß geschrieben. Bei Natural Machines etwa kommt…
https://www.newsdeutschland.com/video/20160531/19658/Essen-aus-dem-3D-Drucker-Wirtschaft.htm
Nudelhersteller Barilla: Spaghetti aus dem 3D-Drucker - Unternehmen, FAZ
Kommt die Pasta bald aus dem Drucker? Der italienische Nudel-Hersteller Barilla arbeitet daran. Kunden könnten ihren eigenen Wunsch auf...
http://www.faz.net/aktuell/wirtschaft/unternehmen/nudelhersteller-barilla-spaghetti-aus-dem-3d-drucker-12744277.html
3DVarius, die Geige aus dem 3D-Drucker
Sie klingt gut und sieht aus wie ein Designobjekt. Das Besondere an dieser E-Geige: Sie stammt aus dem 3D-Drucker, in einem Druck-Durchgang…
https://www.newsdeutschland.com/video/20170111/32896/3DVarius-die-Geige-aus-dem-3D-Drucker.htm
Zukunft der Raumfahrt: Pizza aus dem 3D-Drucker
Astronauten der Nasa können sich freuen. Die US-Weltraumbehörde plant nämlich eine Pizza aus dem 3D-Drucker. So soll die Ernährung im…
https://www.newsdeutschland.com/video/20170316/44388/Zukunft-der-Raumfahrt-Pizza-aus-dem-3D-Drucker.htm
"Der Cheeseburger aus dem 3D-Drucker" und zwei weitere Vorträge beim 7. SchülerCampus - Wissenschaft, JuraForum.de
Nachrichten zum Thema "Der Cheeseburger aus dem 3D-Drucker" und zwei weitere Vorträge beim 7. SchülerCampus lesen Sie kostenlos auf JuraForum.de!
http://www.juraforum.de/wissenschaft/der-cheeseburger-aus-dem-3d-drucker-und-zwei-weitere-vortraege-beim-7-schuelercampus-465973
Für Menschen mit Kaustörungen: Mittagessen kommt aus dem 3D-Drucker, n-tv.de
Über das tägliche Essen wird heute so viel gesprochen, geplant und geschrieben wie nie zuvor. Die Vorstellung, seine Mahlzeiten aus einem 3D-Drucker zu bekommen, ist für die meisten äußerst abwegig, für andere jedoch ein echter Knüller.
https://www.n-tv.de/wissen/Mittagessen-kommt-aus-dem-3D-Drucker-article20377209.html
Essen drucken: Sushi aus dem 3D-Drucker: Ist Pixelessen die Zukunft?
Das japanische Unternehmen Open Meals hat auf der Technikkonferenz SKSW den sogenannten "Pixel Food Printer" vorgestellt. Ihr ausgedrucktes…
https://www.stern.de/digital/technik/neuer-3d-drucker--sushi-aus-dem-pixel-food-printer-7899420.html?utm_campaign=alle&utm_medium=rss-feed&utm_source=standard
Tiere: Greifvogel Söckchen tritt mit Bein aus dem Drucker auf
Was wurde aus "Söckchen"? Die Greifvogeldame aus dem Vogelpark Walsrode hatte nach einem Beinbruch eine Prothese bekommen. Mit dem…
https://www.abendblatt.de/region/niedersachsen/article214005341/Greifvogel-Soeckchen-tritt-mit-Bein-aus-dem-Drucker-auf.html
Das Wunder aus dem 3D-Drucker: Chirurgen flicken entstelltes Gesicht, n-tv.de
Die 3D-Druck-Revolution ist in vollem Gange. Ob Lebensmittel, Geschenke oder Autos - zukünftig kommt einfach alles aus dem Drucker. Auch vor der Medizin macht der Trend längst keinen Halt mehr.
http://www.n-tv.de/panorama/Chirurgen-flicken-entstelltes-Gesicht-article12449136.html
Bei uns können Sie erschwinglich und ohne Zeitverlust modernste 3D-Drucker-Modelle herstellen lassen: Musterteile, Architekturmodelle und vieles mehr.
https://3d-drucker.org/
3D-Drucker: Das Handwerk der Zukunft?, meinbezirk.at
Der 3-D-Druck ist in aller Munde. Auch im Bezirk Braunau hat der Trend schon Einzug gehalten. [...] Adidas-Sportschuhe, Brillen von...
https://www.meinbezirk.at/braunau/lokales/3-d-drucker-das-handwerk-der-zukunft-d2508825.html
3-D-Drucker: Das Handwerk der Zukunft?
[...] Adidas-Sportschuhe, Brillen von namhaften Unternehmen - in vielen Bereichen kommt der 3-D-Druck bereits heute schon zum…
https://www.meinbezirk.at/braunau/lokales/3-d-drucker-das-handwerk-der-zukunft-d2508825.html
Italiener druckt 100-qm-Haus in 48 Stunden: Doch das Genialste ist sein Material
Mit einem 3D-Drucker lassen sich allerhand Dinge fertigen. Seien es Ersatzteile, Handprothesen oder Bauteile für Raketen. Neuerdings können…
http://www.chip.de/news/Italiener-druckt-100-qm-Haus-in-48-Stunden-Doch-das-Genialste-ist-sein-Material_138156920.html
Innovationen - Raketenteile aus dem 3D-Drucker: Europas Antwort auf SpaceX
Trägerrakete Ariane 6 soll in rund zwei Jahren abheben...
https://derstandard.at/2000077655190/Raketenteile-aus-dem-3D-Drucker-Europas-Antwort-auf-SpaceX?ref=rss
3D-Wasser-Drucker zaubert Tropfen-Turner in den Raum
3D-Druck mit Hightech-Plastik, mit Beton oder auch mit Metall können uns nicht mehr wirklich erstaunen, aber 3D-Druck mit Wasser? …
http://de.engadget.com/2018/03/27/3d-wasser-drucker-zaubert-tropfen-turner-in-den-raum/
Futuristisch: Hund Mit 3D-Drucker-Prothesen
Der Hund Derby hatte mit seinen missgebildeten Vorderläufen ein schweres Handicap zu ertragen. Dank eines 3D-Druckers konnte man ihm…
https://www.newsdeutschland.com/video/20160215/14487/Futuristisch-Hund-Mit-3D-Drucker-Prothesen.htm
Wie aus einem Alien-Film: So sieht die weltweit erste Stahlbrücke aus dem 3D-Drucker aus
Nach mehreren Jahren Planung ist sie fast fertig: Die weltweit erste 3D-gedruckte Stahlbrücke. Sie soll über einen Kanal im Amsterdamer…
http://www.chip.de/news/So-sieht-die-weltweit-erste-Stahlbruecke-aus-dem-3D-Drucker-aus_137054657.html
Im FabLab kommen die Geschenke aus dem 3D-Drucker
LEOBEN. Das charmante Chaos in der "Werkstatt" in der Leobener Langgasse 11 erstaunt zunächst viele Besucher, aber die "Lab-Manager"…
https://www.meinbezirk.at/leoben/lokales/im-fablab-kommen-die-geschenke-aus-dem-3d-drucker-d2472840.html
Fötus-Modell aus dem 3D-Drucker: So können werdende Mütter ihr Baby schon vor der Geburt in den Händen halten
Die russische Firma "Embryo 3D" erstellt auf Basis von Ultraschalldaten ein dreidimensionales Computermodell eines ungeborenen Kindes im…
https://www.stern.de/nido/familienleben/embryo-3d--werdende-muetter-bekommen-foetus-modell-aus-dem-3d-drucker-7900476.html?utm_campaign=alle&utm_medium=rss-feed&utm_source=standard
Experte: Waffe im 3D-Drucker ausdrucken ist eine Straftat, PC-WELT.de, 31.07.2018
Wer in Deutschland eine Waffe am 3D-Drucker ausdruckt, der begeht eine Straftat. Davor warnen Experten.
https://www.pcwelt.de/a/experte-waffe-im-3d-drucker-ausdrucken-ist-eine-straftat,3451787
Verhaftet: Schusswaffen mit 3D-Drucker hergestellt, PC-WELT.de, 01.03.2017
Ein Mann druckte mehrere Schusswaffen mit einem 3D-Drucker aus, darunter eine Glock-Pistole. Die Polizei nahm den Mann fest.
http://www.pcwelt.de/a/verhaftet-schusswaffen-mit-3d-drucker-hergestellt,3409928
3D-Druck: Semi-automatische Waffen für alle, netzpolitik.org, 25.07.2018
Der Download von 3D-Drucker-Bauplänen für einsatzbereite Schusswaffen wird ein großes Stück einfacher. Ab dem 1. August stellt die Plattform defcad.com fertige Vorlagen ins Internet, darunter auch das des semi-automatischen Gewehres AR-15, das sich bei Massenmördern in den USA großer Beliebtheit erfreut.
https://netzpolitik.org/2018/3d-druck-semi-automatische-waffen-fuer-alle/
Innovationen - OpenCat: Die Roboter-Katze aus dem 3D-Drucker
Maschinenhaustier sollte ursprünglich eine Kamera werden und kann mit Alexa kommunizieren
https://derstandard.at/2000075569904/OpenCat-Die-Roboter-Katze-aus-dem-3D-Drucker?ref=rss
Bossard Gruppe steigt in den Markt des 3D-Drucks ein
Zug (awp/sda) - Das Zuger Verbindungstechnik- und Logistikunternehmen Bossard steigt in den Markt mit 3D-Drucker ein. Es ist dazu eine…
http://www.finanznachrichten.de/nachrichten-2018-03/43171541-bossard-gruppe-steigt-in-den-markt-des-3d-drucks-ein-485.htm
Ikea: Individuelles Gaming-Zubehör aus dem 3D-Drucker, PC-WELT.de, 04.06.2019
Ikea verkauft bald Gaming-Zubehör. Darunter auch individuell an jeden Gamer angepasste Teile aus dem 3D-Drucker!
https://www.pcwelt.de/news/Ikea-bringt-Moebel-fuer-Gamer-und-Fernbedienung-fuer-Sonos-Symfonisk-Speaker-10604388.html
All-IP: Fax by Fritzbox: send and receive, PC-WELT.de, 11.11.2019
If you do not have a phone with integrated fax device or a multifuntion printer with functions for copying, but even though likes to send or receive fax, you can do it with the Fritzbox.
https://www.pcwelt.de/tipps/All-IP-Faxe-mit-der-Fritzbox-verschicken-und-empfangen-10675106.html
8 GB Mini-USB-memory stick PConkey
ready for the keyring, 24 carat Gold SMI for 3,95 € Pearl.de (Stand 2014; in spite of the opinion, you can use five meter cable for usb, always put USB-sticks directly into the slot of the PC-tower. Never use hubs.)
Mouse: trackball
still recommended because of see the newsgroup-article from Dario from links left menu (!)
Keyboard: German Keyboard, german keys, 2,95 € Pollin, 2015
To go sure for many mainboards, most PCI-ethernet-cards for about 5 € do guarant access to the internet.
Time for the boot of mdv2007.0 under SSD: kdm: 15 up to 30 sec., including KDE: around 1 minute
Time for handling programs and DSL Internet: per mouseclick except large files over USB 2.0
Notice: The tolerance for the temperature of the environment is not listed, almost between 0 and 70 °C. One also should avoid moisture.
Cybercriminals use access points in the Domain Name Systems (DNS), trojaner-info.de, 17.11.2018
The DNS is a popular malware-transport-media for hacker.
Das eigentlich bewährte Domain Name System (DNS) wird heutzutage zunehmend von Angriffen bedroht. Da das DNS oft weitgehend unkontrolliert Firewalls passiert, wird es bei Hackern zunehmend beliebter. Cyberkriminelle missbrauchen das altgediente System heute immer öfter als Transportmittel für Malware oder als Zugang ins Unternehmensnetzwerk, wie Frank Ruge, Director Sales Central Europe bei Infoblox erläutert.
https://www.trojaner-info.de/business-security/aktuell/cyberkriminelle-nutzen-sicherheitsluecken-des-domain-name-systems-dns.html
CIAO DNS! Anonymized (and encrypted) name resolution with pdnsd and dnscrypt-proxy and /etc/hosts all in one (pdnsd, or special combined)
Put on the protecting mask, "Let´s surf!"
DNS: changing the DNS...
instruction for debian and mdv Linux
DNS-Server in different ways
| DNS | short description | disadvantage |
| current remote hosted DNS | direct entry "nameserver ip" like from ChaosComputerClub in /etc/resolv.conf. | Nachteil: without caching, no encryption, no anonymization, Man-In-The-Middle-Attackse |
| dhcp | | |
| dnsproxy | Token, DNSSEC | verifcation, but still without any encryption |
| dnsmasq | local DNS-Cache | temporary cache instead of durable storage within a file on harddisc after cacheing, without encryption (Man-In-The-Middle-Attacks), no anonymization |
| dnsmasq mit dnscrypt | | no encryption, Man-In-The-Middle-Angriffe |
| unbound | | see dnsmasq |
| unbound mit dnscrypt | | |
| pdnsd | lokaler DNS-Cache | remote-DNS requests for unsolved domain-ip-pairs |
| local (/etc/hosts) only | | the classic, most secure solution, but very unhandy |
| dnscrypt | | with connection-certification, but without encryption |
| pdnsd with dnscrypt | | |
| lokal per /etc/hosts | | without any remote host DNS requests, orphaned entries |
| DoH: encrypting DNS | | encrypted HTTPS-DNS-queries, Firefox >64 | no storage resolved domain-ip on harddisc, actual DNS-Server: Nextcloud and Cloudfare only |
| DoT: like DoH, TLS-encryption | complex protocol | |
| Handshake: alternative DNS upon the base of blockchains | | |
| ... | | |
| TorDNS | anonymizing DNS of Tor, see Tor | |
| TorDNS with dnsmasq | | |
| TorDNS with ... | | |
 TorDNS past pdsnd ( including preceeding "mini-mask" local /etc/hosts ) TorDNS past pdsnd ( including preceeding "mini-mask" local /etc/hosts ) | see Tor | disadvantages: none (but the entry node runs in the background). This method is the one we´d like to recommend! |
| bind u.a | the own DNS-Server | |
| Adguard home (DoH, DoT, DNSCrypt, DoQ, ...) | | |
DNS von CCC: 192.76.134.3 world.ccc.de
Changing the DNS to an anonymizing:
 tor-resolve (this command is part of the TOR-Project (TOR, The Onion Router resp. Tor-Browser); we even replaced on our computer all commands for DNS-queries like nslookup, host and dig by linking with ln with it - as it is more than possible, that already any programs do make their DNS-queries, by using such commands! tor-resolve (this command is part of the TOR-Project (TOR, The Onion Router resp. Tor-Browser); we even replaced on our computer all commands for DNS-queries like nslookup, host and dig by linking with ln with it - as it is more than possible, that already any programs do make their DNS-queries, by using such commands!
213.73.91.35 (dnscache.berlin.ccc.de)
85.214.20.141 (FoeBud)
2001:4f8:0:2::14 (f.6to4-servers.net, IPv6, ISC)
194.150.168.168 (dns.as250.net; Berlin/Frankfurt)
0) mdv2010: MCC, simple by configuring established connections and by setting your own DNS instead of DNS from the router
or other methods like:
a) DNS by your computer (host), recommended: Set the both DNS in the system-configuration (mdv: drakconf). Change or add both DNS in LINFW3 (also after b) and c)).
b) DNS by router (resp. gateway): Call the GUI for the router-configuration like fritz.box. If the option for DNS is missing: 1. export the router-configuration by securing into a file, 2. change both DNS in this filei, 3. backup: Import the file, 4. restart the connection by the GUI
b) methode from CCC: Change the DNS in /etc/resolv.conf:
If nscd is installed, type
> /etc/init.d/nscd restart
A fast, (local) cacheing DNS-server can be configured with dnsmasq too: http://www.pcwelt.de/ratgeber/Schneller-DNS-Server-unter-Linux-mit-Dnsmasq-9931341.html . Notice, that in /etc/resolv.conf both, nameserver DNS-ip and "nameserver 127.0.0.1", are entered. Adavatage: The IP is only asked one time the requested domain.
 At first the file dnsmasq.conf within direcotry /etc should be configured:
At first the file dnsmasq.conf within direcotry /etc should be configured:
nano /etc/dnsmasq.conf or (creating a new configuration file):
touch /etc/dnsmasq.conf
Then this file should be opened:
sudo nano /etc/dnsmasq.conf
Comment out the following five rows or type them in:
listen-address=127.0.0.1
port=53
domain-needed
bogus-priv
resolv-file=/etc/resolv.dnsmasq
expand-hosts # Set this, if you want to have a domain # automatically added to simple names in a hosts-file.
addn-hosts=/home/surfuser/addn-hosts-list # if you want it to read another file, as well as /etc/hosts, use this.
cache-size=500
interface=eth0
no-negcache
The entry "listen-address" administrates Dnsmasq to make local requests by the address localhost (127.0.0.1) on port 53 only. Host names out of the LAN are not forwarded to other DNS-server by the option "domain-needed", and "bogus-priv" avoids the resolution of IP-addresses from private subnets (192.168.x.x, 10.x.x.x).
Compact DNS-Server: Dnsmasq as a DNS-Cache requires these eight lines only, last three lines are optional, but cache-size has to be set for cacheing - no caching possible without.
The link "resolv-file" is refering to another configuraiton file "/etc/resolv.dnsmasq", that still has to be created. In this file you enter the IP-address of the (real) DNS-Server like of the provider or the router. The network-interface should also be set and no-negcache cares for cacheing even on errors, what should be kep optional. With
sudo touch /etc/resolv.dnsmasq
this second configuration file is created. Open it with a text editor like nano and enter the addresses of the DNS-Server, dnsmasq needs to resolve the domains. For stationary PCs within local networks the DNS-Server-addresses of the provider resp. of the router (192.168.178.1) should be set.
To be more concrete, what DNS-addresses to take, use the following command:
cat /etc/resolv.conf
Behind "nameserver" the IP to take are shown.
For example, if "192.178.168.1" for the address of a Fritzbox is shown, all to enter into the file "/etc/resolv.dnsmasq" is
nameserver 134.100.9.61
For computers using changing DNS-Server within other LAN/WLANs, the address of a fast public DNS-Server has to be entered as a last ending line too.
For Local Caching using NetworkManager set this in /etc/NetworkManager/NetworkManager.conf:
[main]
dns=none
plugins=keyfile
dhcp=dhclient
rc-manager=unmanaged
[ifupdown]
managed=false
[logging]
level=error
domains=none
NetworkManager.conf: https://developer.gnome.org/NetworkManager/1.11/NetworkManager.conf.html
[main]
dns=dnsmasq
and restart network-manager service.
Howto start dnsmasq:
dnsmasq is started depending from the usage of systemd or not in different ways by one of the the commands:
sh /etc/init.d/dnsmasq start resp. MCC->system services or, if systemd is not used by
sudo systemctl enable dnsmasq.service
sudo systemctl restart dnsmasq.service
Now /etc/resolv.conf has to be configured by text editors like nano, so that dnsmasq can can forward dns-name-resolution to external DNS-server. Either the network connection has to be reconfigured by system control resp. MCC or directly within /etc/resolv.conf. Go sure, that the local DNS-server (dnsmasq) is entered within the first line at first (127.0.0.1), followed by the lines for the other DNS-server, consisting of at last one .An example for the forwarding to the DNS-cache of the Fritz-Box is:
# resolv.conf generated by NetworkManager
nameserver 127.0.0.1
nameserver 134.100.9.61
Be careful for WICD. resolv.conf is admininstrated automatically resp. overwritten. Therefore the static DNS must be set in this certain order only.
If NetworkManager is used, resolv.conf does not have to be overworked manually. The network connection within the Networkmanager can be set to "automatic (DHCP), addresses only" or to "manuell".Now IP-addresses of up to three DNS-server can be set - separated by colon - into the belonging field. After this is stored, all is written into resolv.conf.
Check out, if local cacheing is possible:
>dig mandriva.com
Respond:
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
# Normally responses which come form /etc/hosts and the DHCP lease
# file have Time-To-Live set as zero, which conventionally means do not cache further. If you are happy to trade lower load on the
# server for potentially stale date, you can set a time-to-live (in seconds) here.
# /etc/dnsmasq.conf
local-ttl=99999999
Nothing more has to be configured anymore, if dnsmasq is just working as a DNS-Server. Computers within the LAN that shall use this DNS-Server have to be configured in such way, that they really use this server.
 DNSCrypt DNSCrypt
"DNSCrypt is a DNS resolver that encrypts the content of your request between you and the first level resolver. It prevents an attacker from hijacking or viewing your DNS resolution and the program itself is hardened quite a lot.
For a guide to install, http://www.insanitybit.com/2012/07/23/setting-up-dnscrypt-by-opendns-on-an-ubuntu-12-04-system-8/
For a guide to harden further, http://www.insanitybit.com/2013/06/26/hardening-dnscrypt/
https://itsecblog.de/dnscrypt-mehr-sicherheit-und-privatsphaere/
http://www.insanitybit.com/2012/12/17/hardening-ubuntu-linux/
 /etc/hosts /etc/hosts
Our tip and strong advice: Line by line make a manual entry "IP host" in /etc/hosts using a text-editor. If done, the DNS-server is not queried anymore in all cases, an entry was made! In order to find out the IP to a belonging domain, programs like nslookup, hosts, dig, connection-tracking (Linfw3), iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) and "netstat -n" resp. netstat can be used (in our case, firefox ESR 52.5.1 still seems to send out some information to telefonica and vodafone right at the beginning past its process starting. Update FF 52.5.2.5 against can be installed next days. ). Blacklisting these IP in Linfw3 helps to block.
This (first mentioned host-) method can prevent phishing too.
Check the browser right up from the time he got started, look out for unpredicted, unwanted data transfer indicated by programs like iptraf (iptraf-ng(rosa2016.1, rosae2014.1)), netstat and their invertation nslookup, dig or host in order to block such IP by /etc/hosts resp. Linfw3.
Also think of installing advert-block (pclos). It contains a script named block-advert.sh to add more advert-blocks from choosable adblock-server into /etc/hosts: sh advert-block.sh.during linfw3-lineblock-root. Change to default after performing the steps of this script. Reset /etc/hosts to chmod 644 /etc/hosts.
If you think, enough entries including FTP-, POP3- and SMTP-server and so on, each pairwise with their IP, were added, add the last line: "*.*.*.* localhost" or "ALL:ALL:DENY" ( as this might not really work, to go sure, enter 127.0.0.1 in /etc/resolv.conf and /etc/resolv.dnsmasq for the DNS-Server. There are some cases, more domain like those with images and films of same IP have to be entered into /etc/hosts too, additionally those from software like marble and viking for example, both use katie.openstreetmap.org with IP 81.7.11.83 ). For the rest use tor or reset /etc/resolv.dnsmasq.conf back to the (DNS-) nameserver right before to enter more server and IP.
In /etc/nsswitch modify the line with hosts to
"hosts: files [success=return] dns [success=return]"
and
/etc/host.conf to the include:
order hosts,bind
multi off
reorder on
nospoof on
spoofalert on
First check: add into /etc/hosts
0.0.0.0 test.com
ping gives the follwing output:
>ping test.com
... 0.0.0.0...
But still check this out using iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) or contrack of Linfw3 and then you might also read:
man /etc/host.conf
ENVIRONMENT VARIABLES
The following environment variables can be used to enable users
in /etc/host.conf to make the configured behavior irrelevant:
RESOLV_HOST_CONF
For example, by now, we set in /etc/rc.local
export RESOLV_HOST_CONF="/etc/hosts"
...
 http://bencane.com/2013/10/29/managing-dns-locally-with-etchosts/
http://bencane.com/2013/10/29/managing-dns-locally-with-etchosts/
http://blmte.com/life-arts/3763317_force-system-to-use-local-hosts-file-before-dns-os-x-el-capitan
http://wwija.com/life-arts/3763317_force-system-to-use-local-hosts-file-before-dns-os-x-el-capitan.html
https://www.tecmint.com/setup-local-dns-using-etc-hosts-file-in-linux/
https://fedoraproject.org/wiki/Changes/Default_Local_DNS_Resolver
This means, if the order above is not given inspite of its agreement in /etc/nsswitch.conf, use Linfw3 and remove the ip of the dns-server from item dnslist, but nevertheless one remote-host-dns should still be entered into the field named DNS of Linfw3, otherwise all DNS get allowed to get queried.
Now all DNS-queries are answered locally within file resp. /etc/hosts, until the DNS is set again..
But this might already help:
setfacl -m u:surfuser:- /usr/bin/nslookup
setfacl -m u:surfuser:- /usr/bin/host
setfacl -m u:surfuser:- /usr/bin/dig
No, this does not really help.
Unbound will help (... in main). We show how in the following.
This helps, local /etc/hosts is really functioning like a preused mask using firefox always right before the remote-host-DNS, but the DNS-server itself still gets contacted each Firefox startup. So the DNS gets all the startup-times...
This can be prevented by pdnsd (el6, rosa2016.1, we recommend (el6)) with "addon" dnscrypt-proxy (mga2) tested on the base of firefox-52.7-ESR (el6, OpenSuSE42.3/42.2).
Gratulations! So you "own DNS-Server" is made ready (but you still should check it out once). This methods contributes once more to an increasing speed surfing online.
Overworking the hosts-file in Windows, CHIP
Overworking the hosts-file of Windows can be problematic. Although the file can be find in the windows-system-directory, changes can ...
praxistipps.chip.de/hosts-datei-bearbeiten-in-windows_1307
dnscrypt-proxy can be used upon dnsmasq.
## Configure /etc/resolv.conf to use dnsmasq
nameserver 127.0.0.1
## Configure /etc/dnsmasq.conf
# ignore resolv.conf
no-resolv
# Listen only on localhost
listen-address=127.0.0.1
# dnscrypt is on port 53
server=127.0.0.2#53
## Configure /etc/systemd/system/sockets.target.wants/dnscrypt-proxy.socket with the following 5 lines, if you are using systemd
[Socket]
ListenStream=
ListenDatagram=
ListenStream=127.0.0.2:53
ListenDatagram=127.0.0.2:53
## restart both daemons
https://wiki.debian.org/HowTo/dnsmasq
nano /etc/dnsmasq.conf
Enter right at the beginning resp. search within this file like an insane for the following:
server=127.0.0.2#53
listen-adress=127.0.0.1
cache-size=1000
no-hosts
no-resolv # /etc/hosts won´t be noticed, so try to comment this line in!
keep-in-foreground
no-dhcp-interface=lo
bind-interfaces
bogus-priv
stop-dns-rebind
rebind-localhost-ok
proxy-dnssec
Source: https://debianforum.de/forum/viewtopic.php?f=30&t=157758
Start of dnscrypt-proxy (mga2, mga5) per termial or with each system-boot in /etc/rc.local for example by:
dnscrypt-proxy --daemonize --user=root --local-address 127.0.0.2:53 -r 192.168.178.1 --tcp-port 443 -l /dev/null # -r with OpenDNS´s DNSSEC-support: -r 208.67.222.222 or -r 208.67.222.220
Use dnscrypt-proxy together with local (/etc/hosts) also both in order to do something against the risk of Man-In-The-Middle-Attacks and or use (packages) unbound and dnssec-trigger:
"Summary
Plain DNS protocol is insecure and therefore vulnerable from various attacks (e.g. cache poisoning). A client can never be sure that there is no man-in-the-middle, if it does not do the DNSSEC validation locally.
We want to have Unbound server installed and running on localhost by default on Fedora systems. Where necessary, have also dnssec-trigger installed and running by default. Unbound and dnssec-trigger will be properly integrated with the default network configuration manager (e.g. NetworkManager for Fedora Server and Workstation) and with the graphical user interface (especially GNOME). The localhost address will be the only record in /etc/resolv.conf and no other software except dnssec-trigger will be allowed to change its content.
Detailed Description
Plain DNS protocol is insecure and therefore vulnerable from various attacks (e.g. cache poisoning). DNSSEC is a DNS extension which enabled the client to verify the DNS query response and make sure there is no attacker to spoof some records. A user connected to network usually receives a set of resolvers from DHCP, which should be used for name resolution. These resolvers may also do the DNSSEC validation. However a client can never be sure that there is no man-in-the-middle, if it does not do the DNSSEC validation locally. Purpose of this Fedora change is to have a validating DNS resolver installed on Fedora systems by default. This includes necessary discussions, coordination and integration with other components installed on Fedora by default.
There are growing instances of discussions and debates about the need for a trusted local validating DNS resolver. There are multiple reasons for having such a resolver, most importantly security and usability. Security and protection of user´s privacy becomes paramount with the backdrop of the increasingly snooping governments and service providers world wide.
People use Fedora on portable/mobile devices which are connected to diverse networks as and when required. The automatic DNS configurations provided by these networks are never trustworthy for DNSSEC validation, as currently there is no way to establish such trust.
Apart from trust, these name servers are often known to be flaky and unreliable which only adds to the overall bad and at times even frustrating user experience. In such a situation, having a trusted local validating DNS resolver not only makes sense but is, in fact, badly needed. It has become a need of the hour.
All DNS literature strongly recommends it and amongst all discussions and debates about the issues involved in establishing such trust, it is unanimously agreed upon and accepted that having a trusted local DNS resolver is the best solution possible. It will simplify and facilitate a lot of other design decisions and application development in the future."
How to get Unbound and dnssec-trigger running?
Install dnssec-trigger daemon.
If you use NetworkManager, configure it to use unbound. Add the following line into /etc/NetworkManager/NetworkManager.conf
dns=unbound
/etc/unbound/unbound.conf
server:
interface: 127.0.0.1
# interface: 0.0.0.0
directory: "/etc/unbound"
username: surfuser
# make sure unbound can access entropy from inside the chroot.
# e.g. on linux the use these commands (on BSD, devfs(8) is used):
# mount --bind -n /dev/random /etc/unbound/dev/random
# and mount --bind -n /dev/log /etc/unbound/dev/log
# chroot: "/etc/unbound"
logfile: "/tmp/unbound.log" #uncomment to use logfile.
pidfile: "/etc/unbound/unbound.pid"
# verbosity: 1 # uncomment and increase to get more logging.
# listen on all interfaces, answer queries from the local subnet.
# interface: 0.0.0.0
# interface: ::0
# access-control: 10.0.0.0/8 allow
# access-control: 2001:DB8::/64 allow
access-control: 127.0.0.0/8 allow access-control: 192.168.172.12 allow
access-control: ::1 deny
access-control: 0.0.0.0/0 deny
# whitespace is not necessary, but looks cleaner.
# verbosity number, 0 is least verbose. 1 is default.
verbosity: 1
statistics-interval: 0
statistics-cumulative: 0
num-threads: 2
interface-automatic: yes
port: 53 # 443
outgoing-range: 256
num-queries-per-thread: 256
cache-min-ttl: 9
cache-max-ttl: 9999999
infro-host-ttl: 999999
do-ipv4: yes
do-ipv6: no
do-udp: yes
do-tcp: yes
do-daemonize: yes
chroot: ""
use-syslog: yes
hide-identity: yes
hide-version:yes
version: ""
harden-short-bufsize: yes
harden-large-queries: yes
harden-glue: yes
harden-dnssec-stripped: yes
harden-below-nxdomain: yes
harden-referral-path: yes
use-caps-for-id: no
unwanted-reply-threshold: 1000000
do-not-query-address: ::1
prefetch: yes
prefetch-keys: yes
trusted-key-file: /etc/unbound/root.key # run unbound-control-setup before
aut-trust-anchor-file: "/var/lib/unbound/root.key"
val-bogus-ttl: 99999
val-sig-skew-min: 99999
val-sig-skeq-max: 9999999
val-clean-additional: yes
val-permissive-mode: no
val-log-level: 1
add-holddown: 2592000000
del-holddown: 2592000000
keep-missing: 0
key-cache-size: 10m
ssl-service-key: "/etc/unbound/unbound_server.key"
ssl-service-pem: "/etc/unbound/unbound_server.pem"
ssl-port: 443
remote-control:
control-enable: no
control-interface: 127.0.0.1
control-port: 953
Add the following line into /etc/NetworkManager/NetworkManager.conf
dns=unbound.
/etc/resolv.conf
nameserver 127.0.0.1
nameserver: 192.168.172.1 # any IP of a remote or local DNS
Starting unbound (CentOS 6):
sh /etc/init.d/unbound restart
Use chkconfig to start unbound each boot.
Unbound with DNSSEC-support:
unbound-control-setup of unboung (rosa2014.1) presents the message:
setup in directory /etc/unbound
unbound_server.key exists
unbound_control.key exists
create unbound_server.pem (self signed certificate)
create unbound_control.pem (signed client certificate)
Signature ok
subject=CN = unbound-control
Getting CA Private Key
Setup success. Certificates created. Enable in unbound.conf file to use
Enabled in /etc/unbound/unbound.conf:
ssl-service-key: "/etc/unbound/unbound_server.key"
ssl-service-pem: "/etc/unbound/unbound_server.pem"
ssl-port: 443
# unbound server key file
.
server-key-file: "/etc/unbound/unbound_server.key"
# unbound server certificate file
.
server-cert-file: "/etc/unbound/unbound_server.pem"
# unbound-control key file
control-key-file: "/etc/unbound/unbound_control.key"
# unbound-control certificate file
.
control-cert-file: "/etc/unbound/unbound_control.pem"
Configuration-Check of unbound:
unbound-checkconf
Configure /etc/dnssec-trigger/dnssec-trigger.conf this way too.
Enable and start dnssec-trigger (by systemd). If dnssec blocks all traffic, killall dnssec-trigger again.
systemctl enable dnssec-triggerd.service
disable and stop any existing DNS service, e.g., dnsmasq (systemd)
systemctl start dnssec-triggerd.service resp. start within terminal or add command "dnssec-triggerd" into /etc/rc.local to boot each time.
If an anchor in the tray (system task line) is missing indicating that all get installed and is working fine, start dnssec-trigger by dnssec-trigger and not the daemon dnssec-triggerd.
Now it should just work. Please file a bug against dnssec-trigger component in Fedora, if it doesn´t. If not, disable dnssec-triggerd again.
Note that this is only true for programs using the system standard resolver functions. Programs can use their own resolving mechanism that is not guaranteed to honor anything you write in the hosts file. However, those programs should be rare and far between."
https://fedoraproject.org/wiki/Changes/Default_Local_DNS_Resolver
As promised, we show now, how /etc/hosts is alwas queried first using firefox:
Add to resp. uncomment in /etc/unbound/unbound.conf (configured right above) the following lines:
forward-zone:
name: "."
forward-addr: 192.2.1.20 # remote-host-DNS-Server-IP
forward-first: no
Now unbound supports /etc/hosts always getting queried right before the remote-host-DNS. What we get is the promised previous consulted mask.
Disadavantage: The DNS sill gets queried each firefox-startup. So the DNS-Server gets the starting times of Firefox.
To prevent this too ( and going sure), the DNS-remote-host-IP still has to get removed from the field DNS of Linfw3. Firefox should have get started, before entering the DNS-remote-host-IP again.
This all was tested out with Firefox-52.9.0-ESR (el6) and MozillaFirefox-52.5.3-72.1 (OpenSuSE 42.3) and iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) (el6). Results might differ from the browser-name and version. As mentioned, Linfw3 should beware at least one remote DNS-IP in the field DNS regardless from getting queried or not.
Notice, that iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) is also able to resolv the other way IP to host name (and not the used one by nslookup etc. "host name to IP") by clicking upon configuraiton and enabling resolv..
As described, unbound supports the storage of the pair domain-IP in an own cache for we hope a long period of time (TTL) too.
Our DNS-protection-mask /etc/hosts has reached a large size of several MB of pairs "IP domain" by now and in our opinion it can not include enough pairs. A backup of this file is a must as there might exist some few root-processes initialising this file back into its original, quit empty include... Use commands like "chattr +i /etc/hosts" to fix this.
 pdnsd pdnsd
pdnsd is a so-called DNS-proxy for name resolution against remote DNS-Server.
The responses to DNS-requests are stored within the local cache /var/cache/pdnsd/pdnsd.cache for a free determinable time. Other DNS-proxies and - server are cacheing only within the RAM. So pdnsd is high recommended.
Details and howto configure pdnsd for the example of CCC-DNS (Chaos Computer Club Hamburg): https://wiki.kairaven.de/open/zensurfilter/azensur_dns
For automatical made dns-entries instead of /etc/hosts try the following instead:
 Name resolution without censorship and surveys by DNS-Proxy pdnsd, tor, tor using dnsmasq, tor using pdnsd and ttdnsd Name resolution without censorship and surveys by DNS-Proxy pdnsd, tor, tor using dnsmasq, tor using pdnsd and ttdnsd
/etc/pdnsd.conf, test by commenting in and out and using iptraf (iptraf-ng(rosa2016.1, rosae2014.1))
global {
perm_cache=99999999;
cache_dir="/var/cache/pdnsd"; # chown pdns:pdnsd /var/cache/pdnsd
server_port=53;
server_ip=127.0.0.1;
linkdown_kluge=off;
# pid_file = /var/run/pdnsd.pid;
max_ttl=999999d;
min_ttl=3d;
neg_ttl=99999d;
run_as=pdnsd;
strict_setuid=on;
paranoid=on;
status_ctl=on;
daemon=on;
verbosity=2;
query_method=udp_tcp;
run_ipv4=on;
debug=off;
proc_limit=15;
procq_limit=30;
tcp_qtimeout=30;
par_queries=1;
timeout=60;
randomize_recs=on;
query_port_start=1025;
query_port_end=65535;
use_nss=on;
udpbufsize=1024; # Upper limit on the size of UDP messages.
}
#server {
# label= "dnscrypt-proxy";
# ip = 127.0.0.2; # bzw. nach unserer Einstellung für dnscrypt-proxy 127.0.0.2, enable in linfw3 too
# port = 53;
# proxy_only=on; # Do not query any name servers beside your ISP´s.
# # This may be necessary if you are behind some
# # kind of firewall and cannot receive replies
# # from outside name servers.
# timeout=10; # Server timeout; this may be much shorter
# # that the global timeout option.
# uptest=query; # Test if the network interface is active.
# interface=eth0; # The name of the interface to check.
# interval=15m; # Check every 10 minutes.
# purge_cache=off; # Keep stale cache entries in case the ISP´s
# # DNS servers go offline.
# caching=on;
# edns_query=yes; # Use EDNS for outgoing queries to allow UDP messages
# # larger than 512 bytes. May cause trouble with some
# # legacy systems.
# lean_query=off;
# exclude=.thepiratebay.org, # If your ISP censors certain names, you may
# .thepiratebay.se, # want to exclude them here, and provide an
# .piratebay.org, # alternative server section below that will
# .piratebay.se; # successfully resolve the names.
#}
#
#
#
# and/or the anonymous remote-DNS from Chaos Computer Club ccc
#
server {
label= "cccdc";
ip=213.73.91.35; #enable in linfw3 too
interface=eth0;
#randomize_servers=off;
port=53;
#uptest=query|ping|if;
uptest=none;
#interval=ontimeout;
interval=900;
timeout=1;
purge_cache=off;
caching=on;
# edns_query=off;
# lean_query=off;
# preset=on;
# proxy_only=on;
# reject=10.0.0.0/8,172.16.0.0/8;
# reject_policy=fail;
# reject_recursively=on;
# exclude=.meinebank.de;
# policy=included;
# interval=10m; # Check every 10 minutes.
}
# same is possible for opendns 208.67.222.222 and 208.67.220.220 too
#
# ... and many more remote-DNS
#
and:
server {
label = "root-servers";
root_server=on;
interface=eth0;
ip=213.73.91.35; # ccc anonymizing remote host DNS, enable resp. disable in linfw3 too
timeout = 1;
uptest = none;
# edns_query=on;
# lean_query=off;
caching=on;
purge_cache=off;
interval = 30m; # Test every half hour.
# ping_timeout = 300; # 30 seconds.
purge_cache = off;
# exclude = .localdomain;
# policy = included;
# preset = off;
}
and/or
#server {
# label = tor;
# ip = 127.0.0.1;
# port = 1053;
# interface=eth0;
# uptest = none;
# timeout = 30s;
# purge_cache = off;
# caching = on;
# # edns_query=no;
# # lean_query = on;
# # preset = on;
# # proxy_only = on;
# # exclude = .meine-bank.de,googleapis.com;
# # policy = included;
# }
source {
ttl=86400;
owner=localhost;
serve_aliases=on;
file="/etc/hosts";
}
#rr {
# name=localhost;
# reverse=on;
# a=127.0.0.1;
# owner=localhost;
# soa=localhost,root.localhost,42,86400,900,86400,86400;
#
#}
#
#neg {
# name=doubleclick.net;
# types=domain; # This will also block xxx.doubleclick.net, etc.
#}
#
#neg {
# name=bad.server.com; # Badly behaved server you don´t want to connect to.
# types=A,AAAA;
#}
https://wiki.kairaven.de/open/zensurfilter/azensur_dns (in german language)
Set within /etc/NetworkManager/NetworkManager.conf
"dns=pdnsd"
Check out everything by pdnsd and iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) well, if domain and ip get really cached in /var/cache/pdnsd/pdnsd.cache. Increase perm_cache to 99999 for example or higher.
pdnsd works fine, we gonna prefer it. In /etc/rc.local set chown -R pdnsd:pdnsd /var/cache/pdnsd, chmod 755 /var/cache/pdnsd/pdnsd.cache, chmod 644 /etc/pdnsd.conf, chown root:root /etc/hosts with chmod 644 /etc/hosts. Now even the strange building-up of the connection to the remote-DNS each firefox-startup is prevented! So there is no contact to the remote DNS except for requests for the IP of the very first time elected domain, but one should still check this out for the first time with iptraf (iptraf-ng(rosa2016.1, rosae2014.1)).
If noscript is used and a star (*) is entered in the first field of register for http-addresses, do not forget to add all the exclusions resp. http-server connected with the main server (http-address) resp. by the belonging webside to exclude in the second field right below the first one for the exclusions. Such addresses are listed in the status bar of firefox or by ABP resp. ABL. So pdnsd did not block objects like images right before, but noscript. This last case of more than one server to add as an exclusion remains quit seldomly.
/etc/resolv.conf resp. MCC#Internet#network-connection:
Only addressing Ebay for the process of payment pdnsd and /etc/hosts with pdnsd-"addition" dnscrypt-proxy (mga2, mga5) still made some trouble. Short deactivation helped to enter a ip with belonging domain offer.ebay.de into /etc/hosts ( www.ebay.com, signin.ebay.com, pay.ebay.com, offer.ebay.com, my.ebay.com, ... generally, please tell us the insane amount of Ebay-server...).
Mozilla starts test of DNS-queries over HTTPS, Pro-Linux, 23.03.2018
In order to improve the privacy for DNS-name-resolution over HTTPS, Mozilla plans to test the development-version of Firefox in future. However the choice of the DNS-provider led into cutups.
https://www.pro-linux.de/news/1/25729/mozilla-startet-test-von-dns-abfragen-%C3%BCber-https.html
... and Tor!
In the constellation above out of pdnsd regarding /etc/hosts at first and the optional addition dnscrypt-proxy, internet traffic still does not go over anything, but nodes and the Internet Service Provider (ISP).
 For tor (TorDNS, Tor with firefox-ESR >= 52.9.0) /etc/tor/torrc should include: For tor (TorDNS, Tor with firefox-ESR >= 52.9.0) /etc/tor/torrc should include:
# This file was generated by Tor; if you edit it, comments will not be preserved
#
 #Anonymizing UserAgents: #Anonymizing UserAgents:
#"Privoxy/1.0"
#"Twitterbot/1.0"
#"Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)"
#"Mozilla/5.0 (compatible; bingbot/2.0; +http://www.bing.com/bingbot.htm)"
#"Mozilla/5.0 (compatible; Yahoo! Slurp; http://help.yahoo.com/help/us/ysearch/slurp)"
#"Mozilla/5.0 (compatible; Gooken; +http://www.gooken.de)"
 Tor- configuration file torrc (hardened) /etc/tor/torrc (not for TorBrowser, but TorDNS) and /home/toruser1/tor-browser_en-US/Browser/TorBrowser/Data/Tor/torrc ( for Tor with TorBrowser) : Tor- configuration file torrc (hardened) /etc/tor/torrc (not for TorBrowser, but TorDNS) and /home/toruser1/tor-browser_en-US/Browser/TorBrowser/Data/Tor/torrc ( for Tor with TorBrowser) :
# This file was generated by Tor; if you edit it, comments will not be preserved
# The old torrc file was renamed to torrc.orig.1 or similar, and Tor will ignore it
## Default SocksPort
SocksPort auto IsolateDestAddr IsolateDestPort
## SocksPort for Tails-specific applications
# SocksPort 127.0.0.1:9062 IsolateDestAddr IsolateDestPort
## SocksPort for the default web browser
SocksPort auto IsolateSOCKSAuth KeepAliveIsolateSOCKSAuth
## Entry policies to allow/deny SOCKS requests based on IP address.
## First entry that matches wins. If no SocksPolicy is set, we accept
## all (and only) requests from SocksListenAddress.
# SocksPolicy accept 192.168.0.0/16
# SocksPolicy reject *
## Logs go to stdout at level "notice" unless redirected by something
## else, like one of the below lines. You can have as many Log lines as
## you want.
##
## We advise using "notice" in most cases, since anything more verbose
## may provide sensitive information to an attacker who obtains the logs.
##
## Send all messages of level ´notice´ or higher to /var/log/tor/notices.log
#Log notice file /var/log/tor/notices.log
## Send every possible message to /var/log/tor/debug.log
#Log debug file /var/log/tor/debug.log
## Use the system log instead of Tor´s logfiles
#Log notice syslog
## To send all messages to stderr:
#Log debug stderr
#
## Uncomment this to start the process in the background... or use
## --runasdaemon 1 on the command line. This is ignored on Windows;
## see the FAQ entry if you want Tor to run as an NT service.
#RunAsDaemon 1
#
## The directory for keeping all the keys/etc. By default, we store
## things in $HOME/.tor on Unix, and in Application Datator on Windows.
DataDirectory /var/lib/tor
#
## The port on which Tor will listen for local connections from Tor
## controller applications, as documented in control-spec.txt.
# ControlPort 9051
# ControlListenAddress 127.0.0.1
#
############### This section is just for location-hidden services ###
#
## Once you have configured a hidden service, you can look at the
## contents of the file ".../hidden_service/hostname" for the address
## to tell people.
##
## HiddenServicePort x y:z says to redirect requests on port x to the
## address y:z.
#
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#
#HiddenServiceDir /var/lib/tor/other_hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#HiddenServicePort 22 127.0.0.1:22
#
################ This section is just for relays #####################
#
## See https://www.torproject.org/docs/tor-doc-relay for details.
#
## A unique handle for your server.
#Nickname ididnteditheconfig
#
## The IP or FQDN for your server. Leave commented out and Tor will guess.
#Address noname.example.com
#
## Define these to limit the bandwidth usage of relayed (server)
## traffic. Your own traffic is still unthrottled.
## Note that RelayBandwidthRate must be at least 20 KB.
#RelayBandwidthRate 100 KBytes # Throttle traffic to 100KB/s (800Kbps)
#RelayBandwidthBurst 200 KBytes # But allow bursts up to 200KB/s (1600Kbps)
#
## Contact info to be published in the directory, so we can contact you
## if your server is misconfigured or something else goes wrong.
#ContactInfo Random Person nobody AT example dot com
## You might also include your PGP or GPG fingerprint if you have one:
#ContactInfo 1234D/FFFFFFFF Random Person nobody AT example dot com
#
## Required: what port to advertise for Tor connections.
#ORPort 9001
## If you need to listen on a port other than the one advertised
## in ORPort (e.g. to advertise 443 but bind to 9090), uncomment the
## line below too. You´ll need to do ipchains or other port forwarding
## yourself to make this work.
#ORListenAddress 0.0.0.0:9090
#
## Uncomment this to mirror directory information for others. Please do
## if you have enough bandwidth.
#DirPort 9030 # what port to advertise for directory connections
## If you need to listen on a port other than the one advertised
## in DirPort (e.g. to advertise 80 but bind to 9091), uncomment the line
## below too. You´ll need to do ipchains or other port forwarding yourself
## to make this work.
#DirListenAddress 0.0.0.0:9091
#
## Uncomment this if you run more than one Tor server, and add the
## nickname of each Tor server you control, even if they´re on different
## networks. You declare it here so Tor clients can avoid using more than
## one of your servers in a single circuit. See
## http://wiki.noreply.org/noreply/TheOnionRouter/TorFAQ#MultipleServers
#MyFamily nickname1,nickname2,...
#
## A comma-separated list of exit policies. They´re considered first
## to last, and the first match wins. If you want to _replace_
## the default exit policy, end this with either a reject *:* or an
## accept *:*. Otherwise, you´re _augmenting_ (prepending to) the
## default exit policy. Leave commented to just use the default, which is
## available in the man page or at https://www.torproject.org/documentation.html
##
## Look at https://www.torproject.org/faq-abuse.html#TypicalAbuses
## for issues you might encounter if you use the default exit policy.
##
## If certain IPs and ports are blocked externally, e.g. by your firewall,
## you should update your exit policy to reflect this -- otherwise Tor
## users will be told that those destinations are down.
##
#ExitPolicy accept *:6660-6667,reject *:* # allow irc ports but no more
#ExitPolicy accept *:119 # accept nntp as well as default exit policy
#ExitPolicy reject *:* # no exits allowed
#
################ This section is just for bridge relays ##############
#
## Bridge relays (or "bridges" ) are Tor relays that aren´t listed in the
## main directory. Since there is no complete public list of them, even if an
## ISP is filtering connections to all the known Tor relays, they probably
## won´t be able to block all the bridges. Unlike running an exit relay,
## running a bridge relay just passes data to and from the Tor network --
## so it shouldn´t expose the operator to abuse complaints.
#
#ORPort 443
#BridgeRelay 1
#RelayBandwidthRate 50KBytes
#ExitPolicy reject *:*
#
################ Local settings ########################################
## Torified DNS
DNSPort 5353
AutomapHostsOnResolve 1
AutomapHostsSuffixes .exit,.onion
#
## Transparent proxy
TransPort 9040
TransListenAddress 127.0.0.1
#
## Misc
## We don´t care if applications do their own DNS lookups since our Tor
## enforcement will handle it safely.
WarnUnsafeSocks 0
#
## Disable default warnings on StartTLS for email. Let´s not train our
## users to click through security warnings.
WarnPlaintextPorts 23,109
#
# The old torrc file was renamed to torrc.orig.1 or similar, and Tor will ignore it
# SocksPort auto IsolateDestAddr IsolateDestPort
# SocksPort auto IsolateSOCKSAuth KeepAliveIsolateSOCKSAuth
# ControlPort 9051
#ControlSocket /var/run/tor/control
CookieAuthentication 1
#CookieAuthFile /var/run/tor/control.authcookie
Sandbox 1
DNSPort 9053
AutomapHostsOnResolve 1
AutomapHostsSuffixes .exit,.onion
AllowSingleHopCircuits 0
EnforceDistinctSubnets 1
#DataDirectory /var/lib/tor
#WarnUnsafeSocks 0
#WarnPlaintextPorts 23,109
ClientUseIPv4 1
ClientUseIPv6 0
# Transparent proxy
# TransPort 9040
# TransListenAddress 127.0.0.1
ClientOnly 1
FascistFirewall 1
AvoidDiskWrites 1
DirReqStatistics 0
GeoIPExcludeUnknown 1
Log notice stdout
UseEntryGuards 1
NumEntryGuards 72 # Number of guards: What are the tradeoffs in performance and anonymity from picking three guards vs two or one? By default Tor picks three guards, since if we picked only one, then some clients would pick a slow one and be sad forever. On the other hand, picking only one makes users safer (but we, Gooken, do not think so).
TrackHostExits forum.ubuntuusers.de,wiki.ubuntuusers.de # Eine bestimmte Domain immer über die gleichen Exitnodes aufrufen
TrackHostExits forum.ubuntuusers.de,wiki.ubuntuusers.de # Eine bestimmte Domain immer über die gleichen Exitnodes aufrufen
TrackHostExitsExpire 1800
EntryNodes $9BA84E8C90083676F86C7427C8D105925F13716C,$578E007E5E4535FBFEF7758D8587B07B4C8C5D06,$F47B13BFCE4EF48CDEF6C4D7C7A99208EBB972B5,$EFAE44728264982224445E96214C15F9075DEE1D,$C656B41AEFB40A141967EBF49D6E69603C9B4A11,$8E6EDA78D8E3ABA88D877C3E37D6D4F0938C7B9F,$C793AB88565DDD3C9E4C6F15CCB9D8C7EF964CE9,$AD86CD1A49573D52A7B6F4A35750F161AAD89C88,$B5CED6834BEE8E38D2C62F00CCB6715F0440DA21,$BCF55F865EE6EF17E25EFEAF851BC429F190B85D,$BF1B662D1DA4E55F700C130AC58574B47FB7EB8E,$DD8BD7307017407FCC36F8D04A688F74A0774C02,$A10C4F666D27364036B562823E5830BC448E046A,$EC84E23249F74BFFBC82B4E63CDA295CCC0292A0,$A478E421F83194C114F41E94F95999672AED51FE,$185663B7C12777F052B2C2D23D7A239D8DA88A0F,$134B49D0212C89064F9778E5E8FD9E7BC346F3C9,$311A4533F7A2415F42346A6C8FA77E6FD279594C,$8C25BA134D579B8AAF420E01215EB2CF06AAE907,$9EAD5B2D3DBD96DBC80DCE423B0C345E920A758D,$C2AAB088555850FC434E68943F551072042B85F1,$9AA3FF35E7A549D2337E962333D366E102FE4D50,$9C61FC0A01401EDF71C4048665E53968E81351FC,$7B28971D4A29995784E3066B9D87E42E9C685F3A,$90FD830C357A5109AB3C505287713F1AC811174C,$F47B13BFCE4EF48CDEF6C4D7C7A99208EBB972B5,$C656B41AEFB40A141967EBF49D6E69603C9B4A11,$C793AB88565DDD3C9E4C6F15CCB9D8C7EF964CE9,$AD86CD1A49573D52A7B6F4A35750F161AAD89C88,$DD8BD7307017407FCC36F8D04A688F74A0774C02,$A10C4F666D27364036B562823E5830BC448E046A,$EC84E23249F74BFFBC82B4E63CDA295CCC0292A0,$A478E421F83194C114F41E94F95999672AED51FE,$185663B7C12777F052B2C2D23D7A239D8DA88A0F,$134B49D0212C89064F9778E5E8FD9E7BC346F3C9,$9EAD5B2D3DBD96DBC80DCE423B0C345E920A758D,$C2AAB088555850FC434E68943F551072042B85F1,$CEACA34874EAD103D27CA6A7650B16112F12B209,$FAF3236D37B0B18D8438C46317940F642E296924,$9AA3FF35E7A549D2337E962333D366E102FE4D50,$9C61FC0A01401EDF71C4048665E53968E81351FC,$AD86CD1A49573D52A7B6F4A35750F161AAD89C88,$BCF55F865EE6EF17E25EFEAF851BC429F190B85D,$0111BA9B604669E636FFD5B503F382A4B7AD6E80,$1BDBE9C0F7034E6789A9BF7BED82BE2045F0F5B7,$311A4533F7A2415F42346A6C8FA77E6FD279594C,$42EB556E25A3C33A238AB68AFD043273D0FC6B41,$3CEA56B817455E13C4B063E7D3E7726C286F7C9B,$6B9D965C6149D09DF970C1D086AC8F575643F587,$7B28971D4A29995784E3066B9D87E42E9C685F3A,$90FD830C357A5109AB3C505287713F1AC811174C,$F47B13BFCE4EF48CDEF6C4D7C7A99208EBB972B5,$C656B41AEFB40A141967EBF49D6E69603C9B4A11,$C793AB88565DDD3C9E4C6F15CCB9D8C7EF964CE9,$AD86CD1A49573D52A7B6F4A35750F161AAD89C88,$DD8BD7307017407FCC36F8D04A688F74A0774C02,$A10C4F666D27364036B562823E5830BC448E046A,$EC84E23249F74BFFBC82B4E63CDA295CCC0292A0,$A478E421F83194C114F41E94F95999672AED51FE,$185663B7C12777F052B2C2D23D7A239D8DA88A0F,$134B49D0212C89064F9778E5E8FD9E7BC346F3C9,$9EAD5B2D3DBD96DBC80DCE423B0C345E920A758D,$C2AAB088555850FC434E68943F551072042B85F1,$CEACA34874EAD103D27CA6A7650B16112F12B209,$FAF3236D37B0B18D8438C46317940F642E296924,$9AA3FF35E7A549D2337E962333D366E102FE4D50,$9C61FC0A01401EDF71C4048665E53968E81351FC,$AD86CD1A49573D52A7B6F4A35750F161AAD89C88,$BCF55F865EE6EF17E25EFEAF851BC429F190B85D,$0111BA9B604669E636FFD5B503F382A4B7AD6E80,$1BDBE9C0F7034E6789A9BF7BED82BE2045F0F5B7,$311A4533F7A2415F42346A6C8FA77E6FD279594C,$42EB556E25A3C33A238AB68AFD043273D0FC6B41,$3CEA56B817455E13C4B063E7D3E7726C286F7C9B,$6B9D965C6149D09DF970C1D086AC8F575643F587,$1BDBE9C0F7034E6789A9BF7BED82BE2045F0F5B7,$0111BA9B604669E636FFD5B503F382A4B7AD6E80,$DCAA176F75B04287131C6D78B7CFDDAC6F2691D9,$19083549B3F2BFD96FAACA934D7872CD578A8B99,$0A2366980A2842D770EF8E136A7DA14876360447,$13FB26F9361F803AD190FE88B35E241DC084B026,$1C7700A94DBBFECFA234C1ADD0D23FB87D1D7599,$1E9B32A00C594B032597D8B6A1DF79B734531530,$22296CB6AE56609A96F02FB843AB7B4B0A31CAF4,$35B503FB546815CC9EDE91022555B5D0ED04E389,$35B503FB546815CC9EDE91022555B5D0ED04E389,$4381E471E9358AE4D815021302C7F2E16502BEE1,$52CD98902F6376E84DF2415B906F1426D585564D,$58BC2CFFA7894FC8F4CC5D8A77E38FDCFDB1DC0E,$68EC657DC8A587B38D5D7763D5C72E93C2CD456C,$6B61EFE3AEDEB3351FD3C910443D95556316E01C,$DCAA176F75B04287131C6D78B7CFDDAC6F2691D9,$19083549B3F2BFD96FAACA934D7872CD578A8B99,$3CEA56B817455E13C4B063E7D3E7726C286F7C9B,$6B9D965C6149D09DF970C1D086AC8F575643F587,$DCAA176F75B04287131C6D78B7CFDDAC6F2691D9
# Only use fingerprints! To achieve effective anonymity, all EntryNodes should be member of EU-countries (European Union), be organized as NGOs and have to be typed in here in one line only! AlGrothendiek, ekumen, marylou1, marylou2, Elangb, marcuse1 and marcuse2 (nos-oignons e.V., fr), ori and freki (lux) plus at least 10 × Digitalcourage e.V. (nonprofit) in mix with around 14 × DigiGes Digitale Gesellschaft e.V. (nonprofit, ch) and DFRI0, ..., DFRI09 (DFRI e.V., se), followed by pairoj, krigernes and some Raspberry-Pi, find out the fingerprints from torstatus.blutmagie.de or https://onionoo.torproject.org/details?search=flag:Guard%20running:true etc.! Start tor by terminal first times, in order to get error-messages and warnings!
ExcludeNodes unnamed,default,togma2,behrmann,mccowan,maatuska,kasperskytor04,dannenberg,dizum,gabelmoo,RedOctober1917,kebab,tylerlockedotorg,{us},{ca},{gb},{ro},{hk},{in},{il},{jm},{ke},{ki},{kr},{kw},{mh},{mt},{mc},{nz},{nf},{om},{pa},{ph},{pr},{rw},{ws},{lk},{kn},{sd},{sr},{th},{af},{ax},{al},{dz},{ad},{ao},{ai},{aq},{ag},{ar},{am},{aw},{at},{az},{bs},{bh},{bd},{bb},{by},{bz},{bj},{bm},{bt},{bo},{ba},{bw},{bv},{br},{io},{vg},{bn},{bg},{bf},{bi},{kh},{cm},{cv},{cf},{ky},{td},{cl},{cx},{cc},{co},{km},{cg},{cd},{ck},{cr},{ci},{hr},{cu},{cy},{dj},{dm},{do},{ec},{eg},{sv},{gq},{et},{fk},{fo},{fj},{gf},{pf},{tf},{ga},{gm},{ge},{gh},{gi},{gl},{gd},{gp},{gu},{gt},{gn},{gw},{gy},{ht},{hm},{hn},{is},{id},{iq},{im},{il},{jm},{jp},{jo},{kz},{kg},{la},{lb},{ls},{lr},{ly},{lt},{mo},{mk},{mg},{mw},{my},{mv},{ml},{mq},{mr},{mu},{yt},{mx},{fm},{md},{mc},{me},{ms},{ma},{mz},{mm},{na},{nr},{np},{nc},{nz},{ni},{ne},{ng},{nu},{nf},{mp},{om},{pw},{ps},{pa},{pg},{py},{pe},{pn},{pt},{qa},{re},{rw},{ws},{sm},{st},{sa},{sn},{rs},{sl},{sg},{sk},{si},{sb},{so},{as},{za},{gs},{lk},{lc},{pm},{vc},{sd},{sr},{sj},{sz},{sy},{tw},{tj},{tz},{th},{tg},{tk},{to},{tt},{tn},{tm},{tc},{tv},{ug},{ua},{ae},{um},{uy},{uz},{vu},{va},{ve},{vi},{wf},{eh},{ye},{zm},{no}
ExitNodes $18cfb7ba07f13aeabf50a7148786da68773b2498,$d5f2c65f4131a1468d5b67a8838a9b7ed8c049e2,$74c0c2705db1192c03f19f7cd1bb234843b1a81f,$9ead5b2d3dbd96dbc80dce423b0c345e920a758d,$adb2c26629643dbb9f8fe0096e7d16f9414b4f8d,$c2aab088555850fc434e68943f551072042b85f1,$c2c2b839f4cffa5f7b7a40cb0be84f7d948cb510,$d529e870e7ccfcda2cfee9d317a8dc6e85497fda,$93c6be420fbd2327db591a372c58807bb788d79c,$35919e197c6c7f372a26c747d66aca6a39642b3e,$4ef28f0acba7db83f532cf649db13a00c2f9fdf2,$9171101e709ade5881f5e2ca1100d4044b44263e,$3d615def97f387631f50201fafa6e7b67fdf3fef,$0111ba9b604669e636ffd5b503f382a4b7ad6e80,$ad86cd1a49573d52a7b6f4a35750f161aad89c88,$0111ba9b604669e636ffd5b503f382a4b7ad6e80,$ad86cd1a49573d52a7b6f4a35750f161aad89c88,$9aa3ff35e7a549d2337e962333d366e102fe4d50,$311a4533f7a2415f42346a6c8fa77e6fd279594c,$1bdbe9c0f7034e6789a9bf7bed82be2045f0f5b7,$b5ced6834bee8e38d2c62f00ccb6715f0440da21,$bf1b662d1da4e55f700c130ac58574b47fb7eb8e,$0d2de242ada0ed77325e3aee3a9d8c5cd07c2cf3,$08ce3dbfdaa27db6c044a677af68d7235c2afc85,$bcf55f865ee6ef17e25efeaf851bc429f190b85d,$9c61fc0a01401edf71c4048665e53968e81351fc,$e006ea04c696bbd6e35407538131305ff3cb8c16,$8c25ba134d579b8aaf420e01215eb2cf06aae907,$81b75d534f91bfb7c57ab67da10bcef622582ae8,$e9289af85e5edec87fd741ab5e4a62d2af796f01,$e2baafece5c3d3b4ffe6173b3097948e0f730623,$9e0058300401f6687eae59f9fe82db89230344c1,$63f0043819468fd86c761eae45b4b72db9a795b9,$b27cf1dceecd50f7992b07d720d7f6bf0edf9d40,$c282248597d1c8522a2a7525e61c8b77bbc37614,$97aee1eefbcbb6ff8fa482029830e8e10a961883,$113143469021882c3a4b82f084f8125b08ee471e,$530277866466a1425f43a73dbfcb5fc7410c9852,$de847d94e78b2e560ab87d272dc90192d3144f17,$b1045e12fa4ea0d457a74013866cb41dc0d290bf,$97aee1eefbcbb6ff8fa482029830e8e10a961883,$0d12d8e72ded99ee31bb0c57789352bed0ceeeff,$96e095d5cdbfc3988deb708ec155346472402c32,$763b7d67a6b2d19b3e9ea57d1fbdc48f3b85b559,$9661ac95717798884f3e3727d360dd98d66727cc,$8cf987ff43fb7f3d9aa4c4f3d96ffdf247a9a6c2,$5ba19b5d5ab0cb9ef8ea33da77585b75449400b0,$4bfc9c631a93ff4ba3aa84bc6931b4310c38a263,$d24d0c28ab48768cf8b79dd762d61db4fd015677,$B15A74048934557FCDEA583A71E53EBD2414CAD9,$6D3EE5088279027AD8F64FF61A079DC44E29E3DF,$9E9FAD3187C9911B71849E0E63F35C7CD41FAAA3,$FDBA46E69D2DFA3FE165EEB84325E90B0B29BF07,$FDFD125372A694F0477F0C4322E613516A44DF04,$294cab9ac06a4484e48e61fe1fb7ef4d7839e402,$6088c9ae1f712a9478fde64cadeff8e74ed4ae7c,$4a0c3e177af684581ef780981aeaf51a98a6b5cf,$88c3708a9d71ecec1910b63c3faa5bf60cd7e199,$42e0fb190d20522c6c8c71e42b71da33ac7a780e,$65c86182fdaacb59c9db6d9ddb83148933415a3c,$12ad30e5d25aa67f519780e2111e611a455fdc89,$80aaf8d5956a43c197104cef2550cd42d165c6fb,$b83dc1558f0d34353bb992ef93afeafdb226a73e,$b42c9ef0892ade0f83d00a6488a3391bd8da75c0,$9634ff450315c691e1e2185636318eaf457e4227,$7d05a38e39fc5d29afe6be487b9b4dc9e635d09e,$0e8c0c8315b66db5f703804b3889a1dd66c67ce0,$03dc081e4409631006efcd3af13afaaf2b553ffc,$9ba84e8c90083676f86c7427c8d105925f13716c,$c793ab88565ddd3c9e4c6f15ccb9d8c7ef964ce9,$cd406a3cbcf313b0b068690cc706c142484ce29c,$8f02fe5e233730a6ab4c982e18a2136e662a0b59,$847b916d90fa1db85d57addfa1e50510f68538a1,$9BDF3EEA1D33AA58A2EEA9E6CA58FB8A667288FC,$1A1DA6B9F262699A87F9A4F24EF48B50148EB018,$31A993F413D01E68117F76247E4F242095190B87,$A07FF746D9BA56C3F916BBD404307396BFA862E0,$A3279B1AC705C9F3478947598CF0557B81E12DE1,$AB176BD65735A99DCCB7889184E62EF0B2E35751,$B7BE1D35762155FEB2BC9DAE0A157C706D738FE5,$85D4088148B1A6954C9BFFFCA010E85E0AA88FF0,$39659458160887CC8A46FAE627EE01EEDAAED07F,$0111BA9B604669E636FFD5B503F382A4B7AD6E80,$AD86CD1A49573D52A7B6F4A35750F161AAD89C88,$DC41244B158D1420C98C66F7B5E569C09DCE98FE,$B060482C784788B8A564DECD904E14CB305C8B38,$88487BDD980BF6E72092EE690E8C51C0AA4A538C,$9EAD5B2D3DBD96DBC80DCE423B0C345E920A758D,$95DA61AEF23A6C851028C1AA88AD8593F659E60F,$487092BA36F4675F2312AA09AC0393D85DAD6145,$B15A74048934557FCDEA583A71E53EBD2414CAD9,$2DDAC53D4E7A556483ACE6859A57A63849F2C4F6,$B15A74048934557FCDEA583A71E53EBD2414CAD9,$6D3EE5088279027AD8F64FF61A079DC44E29E3DF,$9E9FAD3187C9911B71849E0E63F35C7CD41FAAA3,$FDBA46E69D2DFA3FE165EEB84325E90B0B29BF07,$FDFD125372A694F0477F0C4322E613516A44DF04,$294cab9ac06a4484e48e61fe1fb7ef4d7839e402,$6088c9ae1f712a9478fde64cadeff8e74ed4ae7c,$4a0c3e177af684581ef780981aeaf51a98a6b5cf,$88c3708a9d71ecec1910b63c3faa5bf60cd7e199,$42e0fb190d20522c6c8c71e42b71da33ac7a780e,$65c86182fdaacb59c9db6d9ddb83148933415a3c,$ed2338cac2711b3e331392e1ed2831219b794024,tor4thepeople1,hviv118,hviv119,AccessNow000,AccessNow001,$93fab6f91c2ef33d0aceef7448177fca2ceb99a0,$c8ab1b2af0cbaae3611a814b4c7d38dce0cbfeb4,$b84f248233fea90cad439f292556a3139f6e1b82,$7bfb908a3aa5b491da4ca72ccbee0e1f2a939b55,$204dfd2a2c6a0dc1fa0eacb495218e0b661704fd,$f47b13bfce4ef48cdef6c4d7c7a99208ebb972b5,$efae44728264982224445e96214c15f9075dee1d,$c656b41aefb40a141967ebf49d6e69603c9b4a11,$6df493c83d0f5c337f7166a108adb891bce3fa1c,$6290a2d08e5eb89c809223c5c7bf52597690751d,$dd8bd7307017407fcc36f8d04a688f74a0774c02,$2dfdea5dd415b95594bfb12d59fe841167f94b5f,$a10c4f666d27364036b562823e5830bc448e046a,$d255268bacbb4562554cf20147731bda0d8c452b,$b0dd527be01842d46030265fbd9928217a709f28,DFRI2,$65e6eb676633328ade3bd3168a59134cddd21e19,$0516085d6cac40ed4cdcefdfc5ccf6b00de61ded,$ec84e23249f74bffbc82b4e63cda295ccc0292a0,$7e006a46a222ce42f84b4a175698b3b593a7b3b7,$6c20cb9a0e95edc143f29194a0a4cc2a593aa15c,$05ffa39d71da116f7669ea4ee53a0baea315ba7f,$bcc94cdf386887fc10365152104978aded8dddea,$0d874d3bbcbe88a61efc8379a68ac3f1314d4b7a,$6df493c83d0f5c337f7166a108adb891bce3fa1c,$3febfb6a491d30cacc2c2995edb41717a6f94e95,$00cce6a84e6d63a1a42e105839bc8ed5d4b16669,$a478e421f83194c114f41e94f95999672aed51fe,$578e007e5e4535fbfef7758d8587b07b4c8c5d06,$874d84382c892f3f61cc9e106bf08843de0b865a,$185663b7c12777f052b2c2d23d7a239d8da88a0f,$90fd830c357a5109ab3c505287713f1ac811174c,$4a3b874f0187f2cf0da3c8f76063b070f9f7a14f,$8d093c9c2b42bc224a5319a660a6cf5edefe839f,$46f90ef3a3628c134dbb4654d0e4ff7eb914b690,$b1d56058c14ded9a32a131cf48877de5e48c440e,$56781ccc9f6d29fea148799ab588429c893a473c,$c862daf2165cf089e6be08c7e1a4939e71b0f42a,$69620419a3d0077272b2ea3952a1f46880fdfae5,$2053a4764080bebbec590be4418a782028d05e0f,$fb646d915dd7e1531764a42ab149416e7e0ef429,$de8eabe166c09f7f8b61907fd8a6cbd6d551f901,$30ee4433780753120eca788d0f95d19ab2722819,$0ac4c4d8bca8da7bae6be3fea87442e724353cbf,$46791d156c9b6c255c2665d4d8393ec7dbaa7798,$dc161f3b2ff30446a14b69a1e6493fd6300a45d2,$0bc8ba32cc3cb0f598e0c92778f7c0946dfbce91,$750c4332414558ab8c973b64dcabb5ca42fa642c,$babc1cf1b3b6fc580a1102cb5214bbd55e57ab60,$968cb7da0c56e66f22b78cba0562fe132939d8bf,$90152ba61de052f96956a72db5928650e14914c2,$56621b6880b20012b11af7d1f44ef7d2779428f5,$37535409102dffe92f3dac809e470e62bc27f1df,$3bd1376cd339edac6aefcf355a703a16af913496,$a2a6616723b511d8e068bb71705191763191f6b2,$4b084ad6a0ba70761a333829f52042bb6ea009af,$d39f2cd90a236f94a61b76616b4873329da77888,$56781ccc9f6d29fea148799ab588429c893a473c,$e27b11e7caaeaf7b2bd09dd440dd5ade2be45461,$044d00bc0ab1e3b4e3854dd522c471ede8d0cb42,$41f07731207742860d43ac426fbae2f3947bd1ca,$4a3b874f0187f2cf0da3c8f76063b070f9f7a14f,$1747f77cc71a7d073e9f960b9b77d33734f6216d,$ffa72bd683bc2fcf988356e6bec1e490f313fb07,$56621b6880b20012b11af7d1f44ef7d2779428f5,$f7b024db02c601185c202e26dffd2ad525c16a36,$46791d156c9b6c255c2665d4d8393ec7dbaa7798,$0bc314281c83167f24c7cfcd68de069b02a92345,$995afa869526ba8e3b714e8bd1f455dc084832cd,$28a3a7d742b7cabdc006c055496dad9814d4e930,$22e8493d6ae611c8e243492bd4935160a5ec8f2f,$f294910258be8299d876de18864577d849e69d6c,$a23e7874e05a3cf5b42ab12dc7b779d994dcf023,$45ec3912c624d0c1a3873ba30214f06ccd946de6,$c5c6947ffa435e8ae12285e36e555a42d13f4332,$b7c6fe4a8cfbc97563e14a01b1e9897123d82cbd,$b7476cd563a6aaa31f851815c751ab03ddf16ed1,$12efbb9560f5bf7d09625c99e488f982fa3483e7,$4ff868be8b403085f4c351094d392a7230766435,$995afa869526ba8e3b714e8bd1f455dc084832cd,$3b4fa23831cc69c136418b0305381a5103a3b470,$b143d439b72d239a419f8dce07b8a8eb1b486fa7,$1c0d0af3ff05ccbba4b6ed262196a4c5a76102e6,$55580d71b317a072f4a4dcf6ea4edb015734aee7,$8154154c636ec317c7165fd839f34f79963376c1,$93fab6f91c2ef33d0aceef7448177fca2ceb99a0,$5e5040ea472aeb11c3dd4beac37ebe50ef40c93b,$61b8bdc91aa7bc9a05eb5a3d652fff88c98e6911,$9684c4d6c71131eeef2e5c23c3ea234a684cd501,$db5a100152fb7937f02f00b5ddfffd012789c242,$40b206539ecdf83aceaa34245cc82508077bba14,$92bbadcb0697f5eb1792c607ee2dc1c291a98adc,$a25128a6162e6f721ae34d521a2c2bf4da1496da,$f84900a93b969e441ff1a1e33fddedc3ddcce549,$e4d6d57a2a572e572e98f86bb5686fd6ce17d385,$1747f77cc71a7d073e9f960b9b77d33734f6216d,$87ea8620a1368f19c43a037115f15461c9487b31,$1901e98a08077fbba4c9e0368dd4dc6dbbd4cf77,$5f1c955a83ffec2548d2a4637d2ccd09124a1957,$6270d21d6cef0a4b1abea0730983aae08126701a,$d9d6c35e932fef7100a00c99c199356e82dab7e6,$fcb454eab56713c641c7a8f2e45b85e7921b9760,$0cdc8fdd8a487271decb791c0d46585f16bc8f19,$6a7479eb4378b946dc2a65a7f2c706b42bae2ebd,$c862daf2165cf089e6be08c7e1a4939e71b0f42a,$cd406a3cbcf313b0b068690cc706c142484ce29c,$777e9e3bb371cfb436cb993cf8c7f631137beeb2,$bfd831d1e7e1e438c3f0fdd21929e91aad279b52,$683a668ebd5e275889b510caea45752016e3de30,$15f2b269295017bbaace4d15a312d4c89682d036,$68854e6f0c8c7b48c1a28934881ad10736da7f8d,$ac98cfa627d79ea10177cd449b24682efc95c325,$b1d56058c14ded9a32a131cf48877de5e48c440e,$750c4332414558ab8c973b64dcabb5ca42fa642c,$babc1cf1b3b6fc580a1102cb5214bbd55e57ab60,$0c039f35c2e40dcb71cd8a07e97c7fd7787d42d6,$8164d74a15a2c10afbd2429a913ffa9b83332580,$ac66ffa4ab35a59ebbf5bf4c70008bf24d8a7a5c,$70b5746578dfe2b373599703b8dfb2af37743405,$2e045a15872b52d7c9955225bb791f91a3ed2f2c,$12efbb9560f5bf7d09625c99e488f982fa3483e7,$569bc61051c78801d96a682ba15d992f347316ed,$edb9c65b939940ec5e9da800ee1574f1d68042b4,$9635968bb4e2d1b8395b0a1f4a7dda5ec4b5c435,$61875bb87f7c6bb9b656be7b95ebbfb3d5500c97,$78bc2254d3b31cd865f7682633aa438212132532,$995afa869526ba8e3b714e8bd1f455dc084832cd,$f47b13bfce4ef48cdef6c4d7c7a99208ebb972b5,$69620419a3d0077272b2ea3952a1f46880fdfae5,$c862daf2165cf089e6be08c7e1a4939e71b0f42a,$2596d998149eaed2c6fb28c1ca39923bc9cc1103,$3bd1376cd339edac6aefcf355a703a16af913496,$70b5746578dfe2b373599703b8dfb2af37743405,$8164d74a15a2c10afbd2429a913ffa9b83332580,$f4c486af57c605837d7ce2a2564dc2082bf66e87,$f7b024db02c601185c202e26dffd2ad525c16a36,$0bc314281c83167f24c7cfcd68de069b02a92345,$46791d156c9b6c255c2665d4d8393ec7dbaa7798,$55a92be2a76c64a5a0db0d4f61d5dca37b55ee52,$ae3893e8f6941e7701963ee1c4fd90491e3fdb8f,$995afa869526ba8e3b714e8bd1f455dc084832cd,$4fb8c28667f785c9cc98bf7317c76daec8072e6f,$13bc57be4a6287d5c9ab970e94823bcaf7b5ffb2,$0bc314281c83167f24c7cfcd68de069b02a92345,$46791d156c9b6c255c2665d4d8393ec7dbaa7798,$96dafdce92ba94e4cc95f8314ae48e272a702fdc,$465d17c6fc297e3857b5c6f152006a1e212944ea,$bcc9fa5994200032e9cd04866b823b6d929f22a8,$86cbf65f98e84681156444d048374aae1c809b17,$87ea8620a1368f19c43a037115f15461c9487b31,$ec3ec2e26c9c57b46686e9efe7eeabd4b570d6d3,$3b0efde689693cfdec2305f7b99d5b2fa4a77d91,$73e8a55b158fe750aaf711b402d3702e3fc395ee,$07c536d732850e3abbb51176fbcf9e79fc2c6e7a,$5b0e2e519fc6e61775895be7cde504c4aa8d6820,$ec45e1e4987affa65941000b71d242bdfcf3a072,$51c0096f3d7ee2a082bc367a29f81c9fcd9bf273,$cafea06e2e4c77a862dd015ef5f490260b09c0ee,$8bbe7a90dc03a954673a99ffb6d79308ad4f643c,$27f890a58693ebb080184c8d8477f0281b2585f7,$27f890a58693ebb080184c8d8477f0281b2585f7,$27f890a58693ebb080184c8d8477f0281b2585f7,$d729c688382cc2a576089716be10490d2d66fce4,$166f00ea1bf27f20e8b2d7ef7fff200e52b47d00,$98138dfd3e2c8c89d8f5ab11ef9b6bff272d83b4,$db4ed7047f787e42ab1f5a1834d66777a3b05c80,$a983a0fa2228f38eaeca10c674a60e836af11239,$98f94858106715983d6ff0123334f94b62ff00b7,$6b29a78eeb42d318290db60c6a2edc714f1bad42,$58d214a5147a7488897d3f187df84ef859d68184,$48042bf1da7d7515dcf5ab468943cac47724ec26,$c290725d86d40ac22fc0e83e7179e4d3a4a0fa16,$58a9921dd0a1389356634625c5b14acc1194a95c,$9ac272d5c5bf479b56f062b91b89d6fe3740185d,$995afa869526ba8e3b714e8bd1f455dc084832cd,$46791d156c9b6c255c2665d4d8393ec7dbaa7798,$55a92be2a76c64a5a0db0d4f61d5dca37b55ee52,$5af95dff3a7b45a01d83c68b9408a280f7a3cdf8,$ffe96e5b8f052c26d73d82af41ec5f91b6801bc7,$912056eae8410c1768ad2efc007ce5d22625bc23,$ce92bc47adb94fce6b975781e5804ed5b63429b2,$b840c7de596e77a22187e638c5116dc5b3bbddd1,$b143d439b72d239a419f8dce07b8a8eb1b486fa7,$a9b5f04f073de48ca5216c3343775dae38cbd150,$876c7ce43774366250d3e768e690dab9d4b5d5a3,$8154154c636ec317c7165fd839f34f79963376c1,$d1f2c5c820b3f96be6144cbfb84fddf9d0ec0810,$5918b0913a59d18262e74f9b1f0c034ccc31fbcc,$8eb722fa1ae9dde1914bc21fea22819d4de99db4,$feff975a45cbb350d7a59a8be61a1071a37c52a3,$ffe96e5b8f052c26d73d82af41ec5f91b6801bc7,$07dd4f0e6d2c7a58937f5c2760da19ee9be8ca80,$2af1f03ca502a23d554eb61c6649c531674c9627,$4df67280a6aa88c8e2807b58deac67e6e599cbba,$2b434018efb233acbdb220a6a14e5657cc6a63c8,$40fae4540cf4c126b1b15c0f5e048fdbd66e2d88,$27f890a58693ebb080184c8d8477f0281b2585f7,$9ae53d17ea4695e94e5cb60e54df57d011b989a0,$1e5618c079d74cf9ae0c5370de4c6e1afd5c0b39,$847b1f850344d7876491a54892f904934e4eb85d,$38b6b15f14bcf4d5b342ba1d67004287d1bcb9dc,$760dd1184f576fbbe4d3f834be16ab3d192bbcda,$abb90a42f0e604daf0716df11c16a7f19c3a6ca7,$cfec7575c7c7eded28fc612eed037ab6dd1abfcd,$b444107f1fbddb0211b7e7645bbe6d14f9904711,$67549c743eb7a9d06a75e37beb82417ebb22e97f,$23439cf3eced46bb327a32373cd1d17e835777ee,$2f1a6481756d34bbf2cd3bebabbfec2e863a6f55,$4f3056e9d4bac38ec2100063745221553630eccb,$ed9649ad9ac439f70560efe3349b4ac4aaf8b6ac,$89abc96e57c44085c6d520f6b27a23f3823e119b,$d5f2c65f4131a1468d5b67a8838a9b7ed8c049e2,$0fedebe83c1f2de3d6673876bba1433ccf0ade51,$922c780d6a32944890a9c2bdb288037eb2f06392,$d734e137dd5362d5068ae3e0211eb297b76c1615,$ab95c99a80ca2ef9b4b2df411ebf3865cf5d40d4,$460f2eb956c09933a7e495c800786f11fd6d6336,$4f9bb4555bcfa49260e382c6d156eb49de07c63b,$adc9038ea5888ca3a9f83ddd85b96febac487b4d,$dc0616b5948379c08865c498063938f76df01fab,$01181b31be5860c7d66da88f88ad522c06470fd9,$a65e1523f313405bb60e4aa136a69efa504c4f60,$53ae17b558dfa2eaf551b650f6260b3e31fbead0,$2c752c180089ddc89bc3ffccb17facfeeafd79aa,$44ef5f90f4e15b2a7937b33908b79675086b0e4b,$c76113d5ab3fc731d678a408eb75bc06f4465f4e,$58a9921dd0a1389356634625c5b14acc1194a95c,$48b4f7ee8e1f87ea544c9498ff463a6ddc3a4795,$587e0a9552e4274b251f29b5b2673d38442ee4bf,$4cdcc833fb70b9f3915522fdc90e52c531feec49,$73a5a81688bd536bfbabe18630f5bd6306c9ac8e,$0b555940d37dc849728841c0b290074e1a1bdca8,$980afb485d04c566c74d5704c96cf80d29de3793,$d15aff44be641368b958a32fb6b071ac2136b8b1,$30c67a09630503e911ba3b9f9e48bd99ba01c5dc,$c0f508ada14ae7ea9f8f6650af149b8dfc35b598,$a9f5135ae18c7e25c7c79117cd8c7619bfeb85ed,$395cec4f978857b1169da78cf1208fd13b715fd0,$519d9147bfc7d8b84dcd7ac0b816080777d0e4c6,$3ea2217a01c61b1c17b6d8571b26fa6a44144d6f,$912056eae8410c1768ad2efc007ce5d22625bc23,$f38fb55a8cca6a00cdd024a5ea2cfecb38a48e15,$890530c5b510a506f5cf206efec1595f96e727a5,$18fd0903330cd865023cf8737aae5d9bfbe4c025,$e7b036d933d6e0a68983e8e3f664eaa54acdea37,$92d8008026aa72131a5357005054048f879f2808,$0c039f35c2e40dcb71cd8a07e97c7fd7787d42d6,$2e72eeabe4ee19183befaa10d88b3c16829c9f99,$b86137ae9681701901c6720e55c16805b46bd8e3,$8a8dba05b9fa31a5511b79768cf191c84c9035de,$7e8bc43ae75eae16d7ec4676f4a5c355f454b809,$8456dfa94161cdd99e480c2a2992c366c6564410,$2880a4d6a33f9becf2ae106d2951965a97527e96,$1e5618c079d74cf9ae0c5370de4c6e1afd5c0b39,$995afa869526ba8e3b714e8bd1f455dc084832cd,$a65e1523f313405bb60e4aa136a69efa504c4f60,$ec9a4651641e21ad335ddcfe68a96c845f5758ec,$9638d8a46d8cba79f8122d77e038ed99ebfdaead,$38b6b15f14bcf4d5b342ba1d67004287d1bcb9dc,$9a725c9660640fd82782f89e755553b29a14e791,$8b029434401afdc8b9793a49005e2bc3af76c02c,$d729c688382cc2a576089716be10490d2d66fce4,$8a2d71cbca33f13a3ea9614de28ae3f669d84987,$519d9147bfc7d8b84dcd7ac0b816080777d0e4c6,$b5edd091d81655c2ebadb38065a868aa20259ac3,{mn},{cz},{se} # all exit nodes in one line only!
ExcludeExitNodes {us},{ca},{gb},{ro},{hk},{in},{il},{jm},{ke},{ki},{kr},{kw},{mh},{mt},{mc},{nz},{nf},{om},{pa},{ph},{pr},{rw},{ws},{lk},{kn},{sd},{sr},{th},{af},{ax},{al},{dz},{ad},{ao},{ai},{aq},{ag},{ar},{am},{aw},{at},{az},{bs},{bh},{bd},{bb},{by},{bz},{bj},{bm},{bt},{bo},{ba},{bw},{bv},{br},{io},{vg},{bn},{bg},{bf},{bi},{kh},{cm},{cv},{cf},{ky},{td},{cl},{cx},{cc},{co},{km},{cg},{cd},{ck},{cr},{ci},{hr},{cu},{cy},{dj},{dm},{do},{ec},{eg},{sv},{gq},{et},{fk},{fo},{fj},{gf},{pf},{tf},{ga},{gm},{ge},{gh},{gi},{gl},{gd},{gp},{gu},{gt},{gn},{gw},{gy},{ht},{hm},{hn},{is},{id},{iq},{im},{il},{jm},{jp},{jo},{kz},{kg},{la},{lb},{ls},{lr},{ly},{lt},{mo},{mk},{mg},{mw},{my},{mv},{ml},{mq},{mr},{mu},{yt},{mx},{fm},{md},{mc},{me},{ms},{ma},{mz},{mm},{na},{nr},{np},{nc},{nz},{ni},{ne},{ng},{nu},{nf},{mp},{om},{pw},{ps},{pa},{pg},{py},{pe},{pn},{pt},{qa},{re},{rw},{ws},{sm},{st},{sa},{sn},{rs},{sl},{sg},{sk},{si},{sb},{so},{as},{za},{gs},{lk},{lc},{pm},{vc},{sd},{sr},{sj},{sz},{sy},{tw},{tj},{tz},{th},{tg},{tk},{to},{tt},{tn},{tm},{tc},{tv},{ug},{ua},{ae},{um},{uy},{uz},{vu},{va},{ve},{vi},{wf},{eh},{ye},{zm},{no}
StrictExitNodes 1
StrictEntryNodes 1
NodeFamily {ch},{ch}
NodeFamily {de},{de}
NodeFamily {nl},{nl}
NodeFamily {fr},{fr}
NodeFamily {se},{se}
NodeFamily {fi},{fi}
NodeFamily {au},{au}
NodeFamily {ch},{au}
NodeFamily {dk},{dk}
NodeFamily {pl},{pl}
# SocksListenAddress 127.0.0.1
ReachableAddresses *:80,*:443,reject *:*
ReachableDirAddresses *:443,reject *:*
ReachableORAddresses *:443,reject *:*
ExitPolicy accept *:443
ExitPolicy accept *:80
ExitPolicy reject *:*
# GeoIPFile /use/share/tor/geoip
# GeoIPv6File /usr/share/tor/geoip6
GeoIPFile /home/surfuser/geoip
GeoIPv6File /home/surfuser/geoip6
 You are looking for good (secure anyonymizing) tor nodes, good entry and good exit relais, of NGOs from secure countries? Then you are in the right place here and within our section News&Links! You are looking for good (secure anyonymizing) tor nodes, good entry and good exit relais, of NGOs from secure countries? Then you are in the right place here and within our section News&Links!
Relais listing including fingerprints: https://torstatus.blutmagie.de or...
"for example, to get all the running Exit nodes, we have
Exit-nodes: https://onionoo.torproject.org/details?search=flag:Exit%20running:true
to get all the running Guard nodes, we have
Guard-nodes (Entry Nodes): https://onionoo.torproject.org/details?search=flag:Guard%20running:true
to get all the running Guard nodes, we have
https://onionoo.torproject.org/details?search=flag:Guard%20running:true
https://tor.stackexchange.com/questions/14697/list-of-all-the-entry-nodes
torrc with bridges instead of guard nodes (entry nodes), comment all linesrefering to EntryNodes and comment out all those dealing with bridges:
UseBridges 1
Bridge obfs3 YOUR_BRIDGE
ClientTransportPlugin obfs3 exec /usr/bin/obfsproxy --managed
Prefer newest protocol obfs4.
bridges.torproject.org
Get a list of bridges, in our example for obfs3, mailto: bridges@bridges.torproject.org, Subject and body: get transport obfs3 (but we did not receive any reply....)
example for YOUR_BRIDGE using obfs3:
obfs3 IP fingerprint
obfs3 60.16.182.53:9001 cc8ca10a63aae8176a52ca5129ce816d011523f5
obfs3 87.237.118.139:444 0ed110497858f784dfd32d448dc8c0b93fee20ca
obfs3 60.63.97.221:443 daa5e435819275f88d695cb7fce73ed986878cf3
... or configure the bridge graphically through the Tor-Browser-Extension.
"Bridge nodes are the nodes, which are not listed on the public directory of TOR nodes."
Nevertheless we would prefer bridges. Tor access is guranteed and ISP won´t notice any of it
Here are your bridges (recommended are more than just one bridge):
obfs4 60.16.182.53:9001 cc8ca10a63aae8176a52ca5129ce816d011523f5
obfs4 87.237.118.139:444 0ed110497858f784dfd32d448dc8c0b93fee20ca
obfs4 60.63.97.221:443 daa5e435819275f88d695cb7fce73ed986878cf3
...
Once you´ve received the email with bridge information, you can continue the configuration steps outlined above.
https://torpat.ch/tpo/docs/bridges.html.en
https://bridges.torproject.org/
https://bridges.torproject.org/howto
obfs4 198.96.90.247:14829 009AE9841C5C7EE104F89F7903246E42689554DA cert=4v04LELp0/hnMpzcWxLM0UYEFEp6O0GtHVZYUB/vcflzRI1fDvpOxrqZyuDEqgk+qnVACQ iat-mode=0
obfs4 194.132.209.17:55068 018A09A41B1B5134FFFF908F69CD65CA91625ECC cert=XuBpMmQdIlRiX71utnbVExuHnicns1dH23ev4r/vzlNUhN4tZ0WkNTAzxd2jir35yfpXAQ iat-mode=0
obfs4 194.132.209.214:37610 A974AAC430D8D65DCCAE9B48152DEC31B92F8FAC cert=o1RKMEIS8SzSoMZoBwxZs/Qxvx4bg+Nr5Kk4vsA15BeDgv2uuy5t9Aaah6R6mZdIQaOvaw iat-mode=0
obfs4 37.218.246.152:34991 22B355C5AAC5F69E46070DBE7544ACCE7957A1B4 cert=hIg+9gYazPkivd50ejP4iNyvEOw/a7dIF08tBknmAm45ClbU5+vYHtYo3COTDJ3RMNQeEw iat-mode=0
obfs4 192.36.31.13:51477 8FDA1F3601535FEFE3BE0457BE5DA7E69CF1B82C cert=YRf/RzlKNzxKm4DTTgdTw0nXn+7r2HZaVROfdqDN/7WdEM9xd+D/jjXoLUhMJhQvCThXKg iat-mode=0
obfs4 174.138.219.97:51987 CCEA79197A59ABCD2BDCAEF796D68654B3C84895 cert=bbMKfqgR3KUHImGQEInuhWOm1hly8jEgDkaDTU9AAVtnp1oC0iw+Jwv/mTXKnTvxn2jFGA iat-mode=0
https://www.ibtimes.co.uk/tor-blocked-turkey-heres-how-circumvent-tor-ban-using-bridges-1597217
Notice the tor-version. Options might have to be commented in for lower ones, see the pregoing example for configuring torrc for TorDNS for tor (el6).
DNSPort 127.0.0.1:9053
Above torrc refers to tor (el6), comment more options out for higher tor versions. The sandbox does not really work in this version too. Now copy tor´s configuration file torrc and the two geodata-files geoip and geoip6 from /etc/tor/ into /home/surfuser and start tor by "tor -f /home/surfuser/torrc". All pathes to these configuration files should be accessable. Tor runs on 127.0.0.1 port 9050 or 9150 by default (you might want (or should) enter the network connection into the browser configuration: socks: localhost:9050). Therefore we recommend extensions like RequestPolicyBlockContinued integrating browser Pale Moon 28.4.1 upon engine Firefox. Also set a hook there for "use TorDNS proxy for DNS-queries" If tor should be used directly for name resolution without installed DNS-Proxy for the anonymized one (pdnsd) instead, simple enter:
DNSPort 127.0.0.1:53
instead.
Reference: pdnsd (rosa2016.1), dnscrypt-proxy (mga5), Firefox-52.9.0-ESR (el6, OpenSuSE 42.3), iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) (el6) and https://wiki.kairaven.de/open/zensurfilter/azensur_dns
If a domain-resolution into an IP malfunctions, add one nameserver with remote-host-ip into /etc/resolv.conf. Set it back, after the resolution got solved.
Alternative to our DNS-concept out of pdnsd, local (/etc/hosts) and TorDNS (tor-resolve):
 AdGuard Home for Linux and Android AdGuard Home for Linux and Android
Privacy protection center for you and your devices
Free and open source, powerful network-wide ads & trackers blocking DNS server.
AdGuard Home is a network-wide software for blocking ads &tracking. After you set it up, it´ll cover ALL your home devices, and you don´t need any client-side software for that.
It operates as a DNS server that re-routes tracking domains to a "black hole", thus preventing your devices from connecting to those servers. It´s based on software we use for our public AdGuard DNS servers -- both share a lot of common code.
https://github.com/AdguardTeam/AdguardHome/
DNS-Filter als Adblocker einrichten: AdGuard Home macht Pi-hole Konkurrenz, heise.de, 17.03.2021
Adblocker helfen gegen unerwünschte Werbung und können auch Malware blockieren. AdGuard Home kommt hierfür als übersichtlicher und kompaker Wettbewerber daher.
Unter den Adblockern nimmt Pi-hole auf der Beliebtheitsskala seit Längerem einen der vorderen Plätze ein. Aber einen wichtigen Entwicklungszweig berücksichtigen die Pi-hole-Entwickler bisher nicht: Der DNS-Dienst pihole-FTL beziehungsweise der zugrunde liegende Server Dnsmasq kommuniziert nur unverschlüsselt mit der Außenwelt - genauer: mit DNS-Resolvern, die angefragte Domainnamen zu IP-Adressen auflösen und damit den Weg zu gesuchten Zielen im Internet weisen. Daher können Dritte die Pi-hole-Anfragen manipulieren und belauschen, beispielsweise am weltgrößten Internet-Drehkreuz DE-CIX in Frankfurt.
Dagegen helfen Protokolle zur verschlüsselten Kommunikation mit dem Domain Name System (DNS). Bisher üblich sind DNS-over-TLS (DoT), DNS-over-HTTPS (DoH) und DNSCrypt. DNS-over-QUIC (DoQ) gewinnt langsam an Fahrt und mehrere Arbeitsgruppen weltweit entwickeln weitere Protokolle. Pi-hole-Nutzer behelfen sich, indem sie verschlüsselnde Proxies wie Stubby oder DNSCrypt-Proxy davorschalten.
Im AdBlocker AdGuard Home stecken DoT, DoH, DNSCrypt und DoQ schon drin. Den Quellcode finden Sie auf GitHub. Die Firma AdGuard wurde 2009 in Moskau gegründet und hat ihren Sitz 2018 nach Zypern und damit in die EU verlegt. Sie verdient ihr Geld mit kommerziellen DNS-Filtern und AdBlockern.
https://www.heise.de/ratgeber/DNS-Filter-als-Adblocker-einrichten-AdGuard-Home-macht-Pi-hole-Konkurrenz-5077869.html
Router-Update: AVM keeps his promise, to extend the Fritzbox-firmware with new functions by updates form time to time ( so that itself is protected and firewalls like Linfw3 get supplemented ). What all is provided by the new version, is described here: http://www.pcwelt.de/ratgeber/Fritzbox-Das-neue-Fritz-OS-9730440.html
Any good router has got its own router-firewall. The new version is also able to block pings. "Internet -> Filter -> Listen" enpossibles the stealth-Modus. Attacker use the ping-command, in order to scan ports and ip address ranges, if a device reacts by a confirmation (ACK-)package, PCWelt.de, 05.11.2015, http://www.pcwelt.de/ratgeber/Fritzbox-Das-neue-Fritz-OS-9730440.html
 Censorship! Censorship!
Orbot analyzes traffic, it makes a traffic control, that can lead into domains and websites not loading anymore! In order to prevent this, allow full Circuit Padding in the setting of Orbot!
Well done.
Orbot should work now fine!
 Digital self defence: Beware broadcast (funk) discipline, netzpolitik.org, 09.04.2024 Digital self defence: Beware broadcast (funk) discipline, netzpolitik.org, 09.04.2024
Wer das Internet nutzt, verrät ständig Details aus seinem Leben. Den Standort oder mit wem man kommuniziert oder wofür man sich interessiert zum Beispiel. Viele dieser Dauerdatenlecks lassen sich versiegeln. Wie man sich datensparsam durchs Netz bewegt, steht hier.
Wenn man es lässt, kräht das Mobiltelefon ziemlich viel in der Gegend herum. - Public Domain Midjourney
Das Wichtigste zuerst: Daten, die nicht anfallen, können auch nicht missbraucht werden. Datensparsamkeit ist die höchste Form von Datenschutz und umfasst zahlreiche Maßnahmen. Eine wäre: Nur das Nötigste übers Netz kommunizieren. Eine andere: Die Apps auf seinem Telefon radikal aussortieren. Denn Apps können Datenschleudern und mögliche Einfallstore für Angriffe sein.
Aaron Wey, Veranstalter von CryptoPartys, sagt: "Die einzigen Daten, die sicher sind, sind Daten, die gar nicht erhoben werden. Sobald Daten irgendwo rumliegen, hat sich in Vergangenheit leider sehr häufig gezeigt, dass die dann doch irgendwann für irgendwen interessant werden."
Ein weiterer zentraler Aspekt der digitalen Funkdisziplin betrifft den persönlichen Standort. Denn es gibt zahlreiche Wege, auf denen ein Mobiltelefon den in die Welt hinauskräht. Einer davon ist die Mobile Advertising ID (MAID). Zahlreiche Apps verkaufen diese mit den dazugehörigen Standortdaten an allerlei Werbetreibende. Doch auch Sicherheitsbehörden und andere können die Daten in die Hände bekommen.
Wer wann wo war
Eine MAID ist noch kein Klarname, aber oft lässt sich der rekonstruieren, etwa wenn die zugehörigen Standortdaten Bewegungsprofile offenbaren. Wohnort und Arbeitsstelle werden so zum Beispiel relativ schnell offensichtlich. Die MAID lässt sich aber löschen (Android) oder ID-basiertes Tracking verbieten (iOS).
Zusätzlich sollte man allen Apps, die ihn nicht benötigen, den Zugriff auf den Standort entziehen. Dem Berechtigungssystem der modernen mobilen Betriebssysteme lasse sich dabei durchaus trauen, sagt Alexander Paul von resist.berlin, einer IT-Sicherheitsberatung vor allem für Aktivist*innen. "Wer den Standort eh nicht braucht, kann ihn auch einfach für das gesamte Profil deaktivieren, dann hat keine App Zugriff darauf", sagt er.
Nicht nur Handy-Apps übermitteln Standorte, sondern auch die SIM-Karte. Über eine Funkzellenabfrage lässt sich für staatliche Stellen einsehen, welche Geräte zu einem bestimmten Zeitpunkt in einer bestimmten Funkzelle angemeldet waren. Alexander Paul von der Digitalberatung resist.berlin sagt: "Wenn man mit einer SIM-Karte ein Handy benutzt, weiß der Mobilfunkanbieter, wo man ist, und diese Information ist über ein vereinheitlichtes Portal relativ leicht von Behörden abfragbar."
Die Information, welche Geräte sich an einem gegebenen Ort befinden, liefert auch ein IMSI-Catcher - eine Art Fake-Funkmast. Manche dieser IMSI-Catcher können auch Gespräche und Datenverkehr über das Mobilfunknetz mitschneiden. Bei modernen Übertragungsstandards wie 4G sind solche Angriffe aufwändiger. Moderne Telefone haben deshalb eine Option, 2G komplett zu deaktivieren.
 So sicher ist der Flugmodus So sicher ist der Flugmodus
Alexander Paul sagt: "Die Mobilfunkkomponente des Handys kann leicht getrackt werden, der Flugzeugmodus ist aber eine gute Waffe dagegen. Dann kann man im Alltag sein Handy als Handy benutzen. Man kann aber dann, wenn man im Flugzeug-Modus ist, auch an Orte gehen, an denen man nicht so gerne gesehen werden möchte."
Das Telefon verrät seinen Standort auch, wenn es mit einem W-LAN oder einem Bluetooth-Gerät kommuniziert. Die MAC-Adresse, die in diesem Fall weitergegeben wird, ändert sich bei modernen Geräten jedoch häufig regelmäßig. Das erschwert das Tracking. Mit einem Google-Pixel-Telefon sei es auf jeden Fall möglich, über öffentliche W-LAN-Netze anonymisiert und ohne Angabe des Standorts zu kommunizieren, sagt Alexander Paul. Allerdings müsse man dabei ein Virtual Private Network (VPN) oder das Tor-Netzwerk nutzen.
 Datenschutz per VPN Datenschutz per VPN
Ein VPN-Service schaltet zwischen Anfragendem und Angefragtem einen Rechner zwischen. Die gesamte Kommunikation vom persönlichen Gerät zum VPN-Server wird verschlüsselt. Wer eine Seite der Kommunikation beobachtet, bekommt nur mit, dass ein Gerät diesen VPN-Server anfragt oder von ihm angefragt wird.
Bei der Nutzung von VPN über mobile Daten fallen allerdings über die Funkmasten weiter Standortdaten an. Dazu kommt der kleine Nachteil, "dass man, je nachdem wo das VPN ins Internet geht, Webseiten vielleicht in einer anderen Sprache sieht", sagt Alexander Paul von resist.berlin.
Wichtig bei der Nutzung von VPN ist, einen seriösen Anbieter zu wählen. Denn der hat ja letztlich Zugriff auf den gesamten Datenverkehr. Alexander Paul und resist.berlin empfehlen ProtonVPN. Das sei in einer eingeschränkten Version kostenlos, wodurch über die Zahlungsmethode keine Rückschlüsse auf die Nutzer*innen getroffen werden könnten. Außerdem sei es ohne Account nutzbar, ausreichend schnell und logge keine IP-Adressen. Das Unternehmen dahinter habe Sicherheitsprüfungen erfolgreich bestanden und wandele sich gerade zu einer Non-Profit-Organisation.
Eine Auswahlhilfe, welche Faktoren man bei der VPN-Anbieterwahl beachten sollte, bietet die EFF.
Das VPN-Prinzip schützt den Datenverkehr nicht nur im öffentlichen W-LAN sondern auch vor dem persönlichen Mobilfunk- oder Festnetzanbieter. Janik Besendorf vom Digital Security Lab der Reporter ohne Grenzen sagt: "Es gibt ja Gesetze, die sagen, dass die Provider auf gerichtliche Anordnung Daten herausgegeben müssen. Und das machen die auch alle. Sonst müssten sie so hohe Strafzahlungen zahlen, dass sie irgendwann bankrott gehen würden."
 Tor zur Anonymität Tor zur Anonymität
Das Tor-Netzwerk macht im Prinzip das Gleiche wie ein VPN, nur dass es standardmäßig drei Rechner zwischenschaltet. Allerdings gibt es laut Alexander Paul von resist.berlin aktuell keinen zuverlässigen Tor-Client für Android. Der Client Orbot schicke, wenn er abstürze, die Daten unter Umständen offen durchs Internet. "Und solche Vorfälle kann man sich zum Beispiel im aktivistischen Bereich halt einfach nicht erlauben. Dann lieber ein etabliertes, qualitatives VPN benutzen. Dann kann man ja immer noch den Tor-Browser in einem Profil mit VPN benutzen. Aber der Basisschutz sollte durch den VPN erfolgen", sagt er.
Es ist allerdings ein offizieller Tor-Client für Android in Arbeit. "Der wird vermutlich besser als Orbot", sagt Alexander Paul.
Der Tor-Browser für Laptop- oder Desktopcomputer kann die Datensicherheit auf jeden Fall deutlich verbessern. Um einen Account, der über Tor bedient wird, mit dem oder der Nutzer*in zu verknüpfen braucht es aufwändige Überwachung, die dann per zeitlicher Korrelation zu belegen versucht, dass sich beispielsweise ein bestimmter Account immer dann einloggte, wenn sich eine Person an ihren Rechner setzte.
Aaron Wey von der CryptoParty-Bewegung sagt: "Das ist ein Szenario, das den Tor-Leuten bekannt ist und das die für die große Schwäche von Tor halten. Wenn jemand die Ressourcen dafür motivieren kann, dann kann auch Tor nichts machen."
 Daten sicher löschen Daten sicher löschen
Wer sich datensparsam durchs Netz bewegen möchte, sollte außerdem keine Fotos von sich im Netz veröffentlichen, dann kann mensch auch nicht mit PimEyes und ähnlichen Suchmaschinen gefunden werden - so lange auch niemand anderes ein Foto hochlädt.
Wie man Google möglichst datensparsam verwendet, kann man hier lernen. Ein nützliches Werkzeug der Datensparsamkeit sind auch verschwindende Nachrichten. Denn wenn irgendwer irgendwann Zugriff auf das Gerät erhalten sollte, fällt so zumindest nicht gleich auch die komplette über Jahre gesammelte Kommunikation in fremde Hände.
Andere Daten, die nicht mehr benötigt werden, sollte man als datensparsame Person ebenfalls löschen. Und zwar am besten so, dass sie sich nicht wiederherstellen lassen. Das bedeutet, sie etwa auf Festplatten und USB-Sticks zu überschreiben, was einige Zeit in Anspruch nehmen kann. Falls das nicht möglich ist, bleibt noch die physische Zerstörung des Datenträgers. Auch deshalb empfiehlt es sich, die Daten zu verschlüsseln, so dass auch mutmaßlich gelöschte Daten unzugänglich bleiben.
https://netzpolitik.org/2024/digitale-selbstverteidigung-funkdisziplin-wahren/
Lesermeinung Gooken
Lassen Sie auf Orbot nichts kommen! Rückmeldungen nach Abstürzen lassen sich mit Herausnahme des Häkchens verhindern.
 Clamd and Clamav: Virenscan for the control and scan of directories and files Clamd and Clamav: Virenscan for the control and scan of directories and files
Files from MS Windows and E-Mail can contain virusses, but as we know, can not threaten introduces system very much. For the check of mailviruses, Kmail uses clamav by a filter configured automatically during the installation of clamav, while clamd might control and scan directories and files on-the-fly:
/etc/clamd.conf
User root # eventually another user later on
... # eventually more settings
Start clamd:
sh /etc/init.d/clamd start
or by ntsysv, MCC->"Services" or systemd ( which is not a mandatory part of mdv2010 and el6, although installable ).
Now start clamdscan too: :
clamdscan -m -z --fdpass
or start
clamdscan -m -z --stream file|directory.
Source: https://wiki.kairaven.de/open/os/linux/maldetect
Die Virendefintionsdatei und andere Dateien von Clamav aus /var/lib/clamav lassen sich mit freshclam und per Installation einer aktuellen Version von Clamav aktualisieren. Einmal im Jahr ( falls überhaupt ) sollte unserer Meinung nach genügen.
You see: With the excurs, mdv2010.0-final with the software also recommended by prism-break.org including "NSA-"Tomoyo-Linux (.jp) and SELinux, Gooken, Mycompanies and the data-sheed we can´t say that fast good bye to the computer technology catastrophe after its expencive, terrifying decades- maybe except mdv and Debian 2014 or so! Not much to consume for power, to exchange or to repair with mdv2010.0, although a view upon the links from our linkside like upon http://prism-break.org/ is strongly recommended! Notice, that not all software from there earns our trust, even not Ubuntu from Canotical inc.! Resigned from some services we even do not know after all our efforts, where all the insecurity remains, using internet by SSL, TLS and other secure protocols, excluding risks in conjunction with DNS (Provider?) and the recipients themselves, maybe security-browser-plugins. Partitions and therefore USB-sticks too, if ever infected, can be repaired within few seconds. We still have to wait for the first system-breakdown. All kind of Tarballs (Tar-Archives) from a more than hugh and day-by-day increasing software-repertoire can be installed just by typing "./configure [--prefix=/usr] && make && make install" resp. cmake and ohter make. The makefile for make producing "./configure --prefix=/usr" always tests out the system-environment, in order to lead into successful installations. Back to the future, we resume: Not much to improve for the sniffing-box computer by mdv2007.0 resp. mdv2010.0 - so together with LINFW3 we are confident enough to resign from only again insecure operating systems past mdv2007.0 and mdv2010-final probably with an 3.X.X-Kernel (<3.4) with actually again more than 4.000 intern bugs, all at lowest cost on the ground of power-consumption like that of energy saving lamps. All software is present on CD/DVD except such for special purposes. Together with the following step and according PDF we have realized our demand for a calm, secure work with computers typically signalized by a green LED as we mentioned from the beginning of the excursion! From programming up to configuring and surfing - now we really can work with computers!
"I am so happy, that my (SuSE 7.3 from year 2003) Linux run for more than 12 hours" (alt.linux.suse, 2003)?
Awful times, one broken distro after the other one. We had to wait a long time, maybe about one decade.
And ´m afraid that, see our linksite part Wikipedia, quit insolvent Mandrake resp. Mandriva with mdk10.1 form year 2004, mdv2007.0 and mdv2010.0 runs forever now!
To achieve, what can be called security, I just had to wait for my own excursion!
 
Do you know, that mdv2010 is able to convert image formats by filetype, seize and color-depth and so on by a single command? Use convert, for example:
convert -resize 1366×768 -colors 24 image1.png image2.jpg
You can do this also for several image-files like at once, or for converting images into splashimages through something like "convert -resize 640x480 -colors 14 Bild.png Bild.xpm", Then "splashimage (hd0,0)/grub/splashimages/Bild.xpm.gz" should be entered into the configuration file of grub in graphical mode named grub.conf resp. menu.lst. Converting is also possible for videos by transcode or ffmpeg, textfiles and program-source-code from one programming language into another one. This can save storage and large programs sometimes and a programm with a GUI doing this too not need to be processed.
mdv 2007 and 2010 even in compiz-cube- and metisse-3d run in our eyes secure as computer can! We are going to report about the cases, if not! I remember an elder ad for Linux with a tongue out: "problems missing - problems creating!"
(Tarif: Freenet DSL1000 (19,95 Euro/month) with internet-telephony)
Ciao, hacker!
CIAO, partitionwise mount and chroot, CIAO, remote-root-logins and root-logins!
All user- and system-user-accounts are password-encrypted and locked (except account for user named surfuser), while all shells got locked accountwise by login /sbin/nologin too (including method sandbox Firefjail and setfacl upon su and bash even for surfuser)! FSE by LUKS (dm-crypt/cryptsetup) encrypts all partitions by option --key-file (instead manually by password-login) except the root-partition: quit no password-cracks senseful as much as possible!
Ciao, trojans!
Ciao, malware!
Ciao, spyware!
Ciao, spammer!
Ciao, scammer!
Ciao, trolls!
...
Ciao, tracker!
Ciao, ad- and spyware!
Ciao, remote DNS (except IP of first time read-in domain)!
Ciao, man-in-the-middle!
Ciao, all unencrypted and unsigned email (thanks Kmail)!
Ciao, all horrifying expensive electric bills!
Ciao, registrations in any databases ( listed Firefox-browser-extensions, especially ABP (Adblockplus), Noscript and Policy Blocked Continued)!
Ciao, weak point human (owner- and access-rights, protocolling the users and an user audit is also possible)
Ciao, all you graphic and hardware-problems ... and pains in the necks!
Ciao, backup-problems (most reliable solution: 1:1-partitionwise through command dd from rescue-DVD/-CD/-USB-memory-stick, best: rescue-partition with Rescue-OS like Knoppix, Mindi or Mondo etc.)
Ciao, all you shaby, shaby computer-problems!
Ciao, IPv6 or make it perfect with Tor: Ciao, IP, ciao Provider (except dial-in)!
Ciao, Suneater!
Ciao, INTEL inc. & Co.(* News&Links#Computer ...)!
Where are all the problems with the computer gone? See the image of circus with Clever and Smart from year 1983:
Nevertheless it managed us to move an elephant over the tiny row!
One problem-box less!
We repeat the often used stamp from trojan-board-expert and Süch-Tiger Cosinus:
"Why Linux is better than Windows..."
and resume: The craziest of all elephants computer, here alias Linux, after several breaddowns, did finally manage the circus-row to achieve the goal (through a mix over several distributions and versions, updates over updates and actions over actions after more than 25 years full of trouble): No hacker, no trojan, no viruses (except maybe one day appearing, but harmless remaining mail-viruses and from emulated progs), no worms, no malware, no adware, no spyware etc., not much or not any remote-DNS-host queried, a stable kernel (4.20) with mkinitrd (mga2), nash (mga2), dracut (mga2) and glibc (pclos) upon except by violence everlasting hardware, cheap ASUS-19W-motherboard Mini-ITX-220 mouseclick-fast out of Intel-CPU, RAM, BIOS and other chips like graphic, sound, LAN and the sensor-based Coretemp for temperature-measurements and control, netadapter SLA-500(W) and 13W-ultraslim quit large displayed WLED-TFT from AOC, all FSE (full system encyption with LUKS, openssl resp. gnutls, openpgp or smime) while as much rpm-packages have been installed surface-covering as installable at once on our SSD and all of them got updated well - not much problems do remain for the intoduced stable computermodel.
 Do you want the everlasting peace with your computer? Contribute to Gooken for the manufacturing of the (consistent) IT-security-standard! For correspondent please click here! Contact us: You can buy the complete rights of Gooken (over all websides and products) to become its owner for 100.000 €!
Do you want the everlasting peace with your computer? Contribute to Gooken for the manufacturing of the (consistent) IT-security-standard! For correspondent please click here! Contact us: You can buy the complete rights of Gooken (over all websides and products) to become its owner for 100.000 €!
to step 2 "additional filter concepts for enhanced security levels"
© 2006-2018 by Gooken - everlasting since computer might run secure
Win, if you want! ... but nothing to win there: You see: Once descripted how and howto, you know everything too!"
Download a funny wallpaper as one important motive for step 1 of this excursion (for free)! Its message seems to be from another system... It always needs our help and special care... noone does know the next step, do you?
Once described how and howto, you know everything too!

News&Links#Computer
Our rubriques for computer:
Computer |
Monitor |
Printer / Drucker |
SSD |
Network / Netzwerk |
Smartphone |
MS Windows
As promiced, here´s the example for /etc/hosts delivering a remote-DNS-protection-"mask" to enhance by yourself. Domain are .de (german) in many cases.
Secure Surfing: At the end of this webside we are introducing and configuring Tor (the Onion Router)..
.
But now, as promised, here is the file /etc/hosts
Wie versprochen, hier die exemplarische remote-DNS-Schutzmaske alias hosts-Datei /etc/hosts, allerdings noch ohne die Sektion zum Adblocken. Für ihren Inhalt ü,bernehmen wir aber keinerlei Garantie und Haftung. Nicht aufgelistete und künfit DNS-Einträge bzw. aufgelistete Paare "IP Domain" befinden sich entweder im Cache des vorgestellten pdnsd, und zwar in /var/cache/pdnsd.cache, oder werden dort mit dem Abfrage von selbst aufgenommen. Für die remote-DNS besteht somit immer weniger Bedarf.
 Make a backup of /etc/hosts : Make a backup of /etc/hosts :
#The risk of pharming is not given as in MS Windows, but nevertheless /etc/hosts is hunted the hell regardless from protecting access-rights, for example through updates (or is it from anywhere?). Make a copy of /etc/hosts: "cp -f /etc/hosts
#/etc/hosts.save" and restore /etc/hosts each bootup by adding "cp -fp /etc/hosts.save /etc/hosts" in /etc/rc.local !
ONLY add often visited domain (domain-ip-pairs) in /etc/hosts (and its backup /etc/hosts-save)!
Following method is only suitable for UNIX/Linux and not suitable for MS-Windows: risc of pharming !!!
# generated by drakconnect
# 127.0.0.1 localhost.localdomain localhost
# This MVPS HOSTS file is a free download from: #
# http://winhelp2002.mvps.org
/hosts.htm #
# #
# Notes: The Operating System does not read the "#" symbol #
# or anything after the # symbol on the same line #
# #
# This *must* be the first line: 0.0.0.0 #
# #
# -------------- Updated: April-24-2017 --------------- #
# #
# Disclaimer: this file is free to use for personal use #
# only. Furthermore it is NOT permitted to copy any of the #
# contents or host on any other site without permission or #
# meeting the full criteria of the below license terms. #
# #
# This work is licensed under the Creative Commons #
# Attribution-NonCommercial-ShareAlike License. #
# https://creativecommons.org
/licenses/by-nc-sa/4.0/ #
#
# Alle Angaben ohne Gewähr! Technische Änderungen vorbehalten!
# NICHT GEEIGNET FÜR MS WINDOWS (pharming)!
# Mache eine SICHERUNGSKOPIE von dieser Datei (etc/hosts/) und sichere Sie den Zugriff auf beide Dateien!
 Sicherung der /etc/hosts : Sicherung der /etc/hosts :
# Die Gefahr des Pharmings ist zwar nicht wie bei MS Windows gegeben, dennoch wird z.B. über Updates (oder sogar von überall her) höllisch Jagd auf /etc/hosts gemacht. Die /etc/hosts sollte daher noch einmal gesichert werden:. "cp -f # /etc/hosts /etc/hosts.save" . Diese /etc/hosts.save wiederum sollte vorsichtshalber, trotz Zugriffsrechte, bei jedem Start die /etc/hosts überschreiben
# Dazu bedarf es in /etc/rc.local des Eintrags "cp -fp /etc/hosts.save /etc/hosts" !
# VERIFIZIERE im Fehlerfall einige im Kommenden aufgelistete IP, insbesonders für ebay etc. mit nslookup oder dig noch einmal! Ergibt sich hier tatsächlich ein Fehler oder erscheint NXDOMAIN, setze die mit nslookup gefundende IP über "nameserver remote-host-ip" vorü,bergehend gleich zu Beginn von /etc/resolv.conf ! TESTE, ob ein REFERER gesendet werden muss und erlaube ihn, falls erforderlich. Überprüfe ggfls. die Zugriffsrechte von /etc/hosts und /var/cache/pdns/pdnsd.cache.
# Einige Webseiten verlangen (ff-extension RefControl: normal, NOT BLOCKED)! Javascript und Cookies ab. Setze sie im Fehlerfall! Wann auch immer ssl/tls (https) möglich ist, aber das Zertifikat Fehler aufweiset, füge eine Ausnahme in die http-exception-Liste von noscript ein unter -> https-exclusion-list. Hilft alles nichts, benutze den eine eigene (anonymisierende) DNS verwendenden Tor-Browser!
# Zertifikatsfehler: Installiere eine browser-verträgliche Version von nss und OpenSSL und füge dem Browser eine Ausnahme hinzu, z.B. für Firefox über Edit->Preferences->Advanced->Certificates->View Certificates->Servers->Add an exception
NOTICE: ADD ONLY THE PAIRS IP-DOMAIN USED VERY OFTEN in /etc/hosts and its backup /etc/hosts-save !
#
# 0.0.0.0
# ::1 #[IPv6]
# ALL:ALL:DENY
127.0.0.1 localhost
# [Start of entries generated by MVPS HOSTS]
# [Misc A - Z]
0.0.0.0 example.com
0.0.0.0 example.com
0.0.0.0 www.example.com
0.0.0.0 google.de
0.0.0.0 google.com
0.0.0.0 r.search.yahoo.com
0.0.0.0 api.smartredirect.com
0.0.0.0 api.smartredirect.de
0.0.0.0 www.redhat.com
0.0.0.0 redhat.com
0.0.0.0 nodpi.org
0.0.0.0 www.nodpi.org
0.0.0.0 www.dephormation.org.uk
0.0.0.0 www.badphorm.co.uk
0.0.0.0 www.inphormationdesk.org
0.0.0.0 www.phonecallsuk.co.uk
0.0.0.0 www.telefonica.de
0.0.0.0 telefonica.de
0.0.0.0 phonecallsuk.co.uk
0.0.0.0 inphormaitondesk.org
0.0.0.0 badphorm.co.uk
0.0.0.0 all-systems.mcast.net
0.0.0.0 1.0.0.224.in-addr.arpa
0.0.0.0 fritz.box # Setze die lokale IP wieder zurück auf die Router-IP (fritz.box), wenn der Router konfiguiert werden soll !
# from https://www.instructables.com/id/Improve-ADSL-Broadband-Performance/
0.0.0.0 googleads.g.doubleclick.net
0.0.0.0 googleadsense.ya.com
0.0.0.0 refer.ccbill.com
0.0.0.0 domains.googlesyndication.com
0.0.0.0 video-stats.video.google.com
0.0.0.0 www.google-analytics.com
0.0.0.0 googleadservices.com
0.0.0.0 ad.doubleclick.net
0.0.0.0 .adserve.com
0.0.0.0 bit.ly
0.0.0.0 goo.gl
0.0.0.0 Mitt.ly
0.0.0.0 owl.ly
0.0.0.0 ytimg.com
0.0.0.0 ytimg.l.google.com
0.0.0.0 googleadservices.com
0.0.0.0 googlevideo.com
0.0.0.0 adblockplus.org
0.0.0.0 addons.mozilla.org
0.0.0.0 noscript.net
0.0.0.0 mybrowseraddon.com
0.0.0.0 stardrifter.org
0.0.0.0 www.stardrifter.org
0.0.0.0 Dephormation.org
0.0.0.0 dephormation.org
0.0.0.0 www.dephormation.org
0.0.0.0 www.Dephormation.org
0.0.0.0 customer4.orypt.info
0.0.0.0 secure.informaction.com
0.0.0.0 t.bollingh.eu
0.0.0.0 a23-206-24-64.deploy.static.akamaitechnologi
0.0.0.0 api.smartredirect.com
0.0.0.0 api.smartredirect.de
0.0.0.0 www.hetzner-online.de
0.0.0.0 hetzner-online.de
0.0.0.0 example.com
0.0.0.0 www.example.com
0.0.0.0 r.search.yahoo.com
0.0.0.0 www.redhat.com
0.0.0.0 redhat.com
0.0.0.0 nodpi.org
0.0.0.0 www.nodpi.org
0.0.0.0 www.dephormation.org.uk
0.0.0.0 www.badphorm.co.uk
0.0.0.0 www.inphormationdesk.org
0.0.0.0 www.phonecallsuk.co.uk
0.0.0.0 www.telefonica.de
0.0.0.0 telefonica.de
0.0.0.0 phonecallsuk.co.uk
0.0.0.0 inphormaitondesk.org
0.0.0.0 badphorm.co.uk
0.0.0.0 dephormation.org.uk
0.0.0.0 all-systems.mcast.net
0.0.0.0 1.0.0.224.in-addr.arpa
0.0.0.0 84-173-172-163.rev.cloud.scaleway.com
0.0.0.0 natsu-no-yuki.de
0.0.0.0 mail.nrwision.de
0.0.0.0 s14.sam-schwedler.de
0.0.0.0 www.nrwision.fb15.tu-dortmund.de
0.0.0.0 www2.nrwision.fb15.tu-dortmund.de
0.0.0.0 www.fastbot.de
0.0.0.0 fastbot.de
0.0.0.0 addons.palemoon.org
0.0.0.0 fritz.box # Setze die lokale IP wieder zurück auf die Router-IP (fritz.box), wenn der Router konfiguiert werden soll !
# online-bank1
# online-bank2
144.76.70.77 katie.openstreetmap.org # for marble and merkaartor
81.7.11.83 konqi.openstreetmap.org
78.46.186.102 www.openstreetmap.de
78.46.186.102 openstreetmap.de
78.47.224.226 w9.geonames.org
193.63.75.109 nominatim.openstreetmap.org
188.40.62.8 www.geonames.org
188.40.62.8 geonames.org
# ip your_pop3_server
212.227.17.* pop3.web.de
212.227.17.177 pop3.web.de
213.165.67.124 smtp.web.de
# ip imap_server
# ip smtp_server
# ip your_ftp-server_1: ...
# ip your_ftp-server_2: ...
# ...
# ip cloud_server: ...
# ...
217.160.0.241 www.gooken.de
217.160.0.241 gooken.de
5.1.72.34 gooken.safe-ws.de
5.1.72.34 safe-ws.de
78.47.224.226 w9.geonames.org
193.63.75.109 nominatim.openstreetmap.org
188.40.62.8 www.geonames.org
188.40.62.8 geonames.org
78.46.186.102 www.openstreetmap.de
78.46.186.102 openstreetmap.de
89.16.162.21 openstreetmap.org
89.16.162.21 www.openstreetmap.org
192.168.178.1 fritz.box
144.76.70.77 katie.openstreetmap.org
81.7.11.83 konqi.openstreetmap.org
130.117.76.9 nominatim.openstreetmap.org
212.227.17.* pop3.web.de
212.227.17.177 pop3.web.de
213.165.67.124 smtp.web.de
82.165.230.36 freemail.web.de
104.103.91.15 www.tagesschau.de
104.103.91.15 tagesschau.de
104.75.68.62 faktenfinder.tagesschau.de
# ... # but do not add too much, as IP of IPv4 change sometimes.
# ALL:ALL:DENY
0.0.0.0 www.google.de
0.0.0.0 google.de
0.0.0.0 www.google.com
0.0.0.0 google.com
0.0.0.0 www.yahoo.com
0.0.0.0 www.yahoo.de
0.0.0.0 de.yahoo.com
0.0.0.0 us.yahoo.com
0.0.0.0 yahoo.de
0.0.0.0 yahoo.com
0.0.0.0 yahoo.us
0.0.0.0 fastbot.de
0.0.0.0 www.fastbot.de
0.0.0.0 www.telefonica.de
0.0.0.0 telefonica.de
0.0.0.0 www.telefonica.com
0.0.0.0 telefonica.com
0.0.0.0 www.vodafone.de
0.0.0.0 vodafone.de
0.0.0.0 vodafone.com
0.0.0.0 www.vodafone.com
# advert-block*.rpm (pclos) and other adblocker tarballs/packages
# ...
Mozilla testet DNS-Abfragen über HTTPS in Firefox Beta, PRO LINUX, 14.09.2018
Nachdem eine DNS-Namensauflösung über HTTPS zur Verbesserung der Privatsphäre in der Entwicklerversion von Firefox erfolgreich getestet wurde, zieht die neue Lösung in die Betaversion von Firefox ein.
[...] Wie bisher werden alle DNS-über-HTTPS-Abfragen an einen Server von Cloudflare gestellt. Damit werden aber Informationen über die besuchten Webseiten an Cloudflare preisgegeben - auch im privaten Modus, was von einigen Benutzern kritisiert wird. Mozilla versucht die Kritik mit dem Verweis auf Datenschutzrichtlinien zu entkräften. Cloudflare hat jetzt eine explizite Datenschutzerklärung für diesen Test abgegeben.
Mozilla arbeitet laut der Mitteilung auf einen breiteren Einsatz von DoH hin, wofür eine größere Zahl von vertrauenswürdigen DoH-Anbietern benötigt wird, die den Datenschutz beachten.
https://www.pro-linux.de/news/1/26303/mozilla-testet-dns-abfragen-%C3%BCber-https-in-firefox-beta.html
Lesermeinung
Mozilla,
Von Jonn Jonsen am Fr, 14. September 2018 um 17:30 #
Mozilla driftet immer mehr ab.Zitat: Damit werden aber Informationen über die besuchten Webseiten an Cloudflare preisgegeben - auch im privaten Modus
Das ist ein Nogo und damit macht sich der Firefox unbrauchbar!
mehr Re: Mozilla
Von Josef Hahn am Fr, 14. September 2018 um 17:44 #
... die Preisfrage ist: Wie kommt man in Zukunft (sagen wir mal in fünf Jahren) an einen brauchbaren Open Source Browser, wenn beide Browser eigentlich regelmäßig mit Verschlimmbesserungen auffallen? Oder anders gefragt: Wann ist der Zeitpunkt erreicht, an dem man beide eigentlich nicht mehr brauchen kann? Und was macht man dann stattdessen?
https://www.pro-linux.de/news/1/26303/comm/627484/mozilla.html
Vorteile von DNS-Abfragen über HTTPS, PRO LINUX, 30.05.2018
Patrick McManus von Mozilla erläutert, warum DNS-Abfragen über HTTPS eine bessere Alternative sind als DNS über einfache TLS-verschlüsselte Verbindungen.
DNS over HTTPS (DoH) steht kurz vor der Standardisierung durch die Internet Engineering Task Force (IETF). Patrick McManus von Mozilla und P. Hoffman von ICANN sind die beiden treibenden Kräfte hinter diesem Protokoll. Schon im März hatte Mozilla bekannt gegeben, diesen Standard in der Entwicklerversion von Firefox testen zu wollen. Die verschlüsselte übertragung soll nicht nur zur Verbesserung der Privatsphäre beitragen, sondern auch DNS-basierte Angriffe erschweren.
DNS über HTTPS ist ein neues Protokoll, das die Sicherheit der DNS-Abfragen verbessern soll, indem es sie über eine verschlüsselte HTTP-Verbindung sendet. Es ist nicht der erste Versuch, DNS sicher zu machen. Schon lange gibt es DNSSEC, das jedoch nur eine Verifizierung der Daten ermöglicht, keine Verschlüsselung einsetzt und auf Clients kaum verwendet wird. Eine Alternative zu DoH ist DNS over TLS (DoT), das bereits vor DoH von der DPRIVE-Arbeitsgruppe spezifiziert wurde und theoretisch einfacher ist. Denn HTTPS setzt auch TLS zur Verschlüsselung ein, ist aber darüber hinaus ein weiteres komplexes Protokoll.
Patrick McManus schreibt nun, dass DoH auf der großartigen Vorarbeit von DoT aufbaue. Die Gemeinsamkeiten zwischen beiden Protokollen seien wichtiger als die Unterschiede und in vielen Fällen seien beide gleichermaßen geeignet. Beide verschlüsseln und authentifizieren die Kommunikation zwischen Clients und DNS-Resolvern. Einer der Vorteile von DoH ist jedoch, dass es auf die gesamte HTTP-Infrastruktur zurückgreifen kann. Beispiele sind die Content-Verteilnetzwerke, hunderte von Programmbibliotheken, Autorisierungsbibliotheken, Proxys, ausgefeilte Lastverteiler, Server für sehr hohe Datenmengen und die allgegenwärtigen Javascript-Engines, die bereits HTTP-Funktionen mitbringen und ein vernünftiges Sicherheitsmodell (CORS) enthalten. DoH ermöglicht wie HTTP außerdem das Aushandeln der Content-Typen, so dass DNS-Daten auch in Formaten wie JSON oder XML übertragen werden könnten.
DoH hat laut McManus auch Vorteile auf der Protokollebene, da es die ganze HTTP/2-Funktionalität nutzen kann, darunter Multiplexing, Priorisierung, Flusskontrolle und einiges mehr. Wenn HTTP/2 zu QUIC weiterentwickelt wird, wird DoH auch dessen Vorteile ohne neue Standardisierung nutzen können. Unter anderem soll dann die Geschwindigkeit deutlich steigen, besonders wenn mit Paketverlusten gerechnet werden muss.
Ein weiterer Vorteil von DoH ist, dass es in anderen HTTP-Traffic integriert werden kann, was die Anzahl der nötigen Verbindungen senkt und die Geschwindigkeit erhöht. Ein weiterer, allerdings spekulativer Vorteil ist, das DoH künftig die Möglichkeit von HTTP nutzen könnte, Push-Nachrichten zu senden. McManus sieht hier allerdings noch Fragen bezüglich der Sicherheit und der Privatsphäre zu klären, die seiner Ansicht nach schwierig sind, bevor konkrete Schritte in diese Richtung unternommen werden.
https://www.pro-linux.de/news/1/25943/vorteile-von-dns-abfragen-%C3%BCber-https.html
Handshake: Alternative DNS based upon Blockchain, PRO-LINUX, handshake.org, 05.08.2018
https://www.pro-linux.de/news/1/26158/handshake-alternatives-dns-auf-blockchain-basis.html
 Multicast: Sometimes traffic monitors like iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) monitor in the (we hope elsewhere empty field) the connection "IGMP: Router-IP -> 224.0.0.1". How can this connection get blocked? Multicast: Sometimes traffic monitors like iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) monitor in the (we hope elsewhere empty field) the connection "IGMP: Router-IP -> 224.0.0.1". How can this connection get blocked?
Ich habe es bereits geschafft eine andere verwandte Multicast Verbindung, IP 224.0.0.251, mit dem folgendem Befehl zu unterbinden:
sudo ifconfig eth0 -multicast
Der all-systems.mcast.net traffic ist aber weiterhin aktiv.
https://forum.ubuntuusers.de/topic/wieso-laesst-sich-das-ding-nicht-abschalten/
Theoretisch sollte das für alle interfaces reichen:
ip link set interface multicast off
Der all-systems.mcast.net traffic ist aber weiterhin aktiv.
Welcher Dienst auf deinem System nutzt denn Multicast? Im Zweifelsfall kannst du einfach Avahi oder Konsorten deinstallieren.
Ich habe auch schon Avahi und Cups verdächtigt weswegen ich die Config Files /etc/init/cups /etc/init/cups-browsed und /etc/init/avahi-daemon.conf abgeändert habe um den Start dieser services zu unterbinden.
Zusätzlich habe ich auch noch jeglichen Traffic über die offenen Ports welche sie verwenden, 631 tcp und 5353 tcp mit iptables und ufw geblockt.
Trotzdem scheint all-systems.mcast.net immer wieder in diversen Packet Sniffer Tools auf. Im screenshot habe ich zB iftop verwendet.
Ich habe auch schon versucht mit tcdump und wireshark herauszufinden was genau hinter dieser IP steckt, jedoch ohne Erfolgt.
Hättest du vielleicht noch einen anderen Vorschlag?
Jun 8 18:11:53 kernel: IGMP Drop: IN=eth1 OUT= SRC=192.168.100.1 DST=224.0.0.1 LEN=28 TOS=0x00 PREC=0xC0 TTL=1 ID=0 PROTO=2
Jun 8 18:14:53 kernel: IGMP Drop: IN=eth1 OUT= SRC=192.168.100.1 DST=224.0.0.1 LEN=28 TOS=0x00 PREC=0xC0 TTL=1 ID=0 PROTO=2
Jun 8 18:17:53 kernel: IGMP Drop: IN=eth1 OUT= SRC=192.168.100.1 DST=224.0.0.1 LEN=28 TOS=0x00 PREC=0xC0 TTL=1 ID=0 PROTO=2
filter violation livelog
18:11:53 192.168.100.1 -> 224.0.0.1
18:14:53 192.168.100.1 -> 224.0.0.1
18:17:53 192.168.100.1 -> 224.0.0.1
How to enable or disable multicast for a NIC
Enable Multicast for eth0:
# ifconfig eth0 multicast
# ifconfig eth0
eth0 Link encap:Ethernet HWaddr 00:0C:29:F1:FF:EA
inet addr:78.46.74.27 Bcast:78.46.74.31 Mask:255.255.255.224
inet6 addr: fe80::20c:29ff:fef1:ffea/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:5339836 errors:0 dropped:0 overruns:0 frame:0
TX packets:5486444 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:820300389 (782.2 MiB) TX bytes:1929979381 (1.7 GiB)
Base address:0x1400 Memory:e8820000-e8840000
Disable Multicast for eth0:
# ifconfig eth0 -multicast
# ifconfig eth0
eth0 Link encap:Ethernet HWaddr 00:0C:34:FE:AB:6A
inet addr:10.0.0.100 Bcast:10.0.0.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fef1:ffea/64 Scope:Link
UP BROADCAST MTU:1500 Metric:1
RX packets:5339836 errors:0 dropped:0 overruns:0 frame:0
TX packets:5486444 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:820300389 (782.2 MiB) TX bytes:1929979381 (1.7 GiB)
Base address:0x1400 Memory:e8820000-e8840000
Other useful command to test Multicast Configuration:
Command Description
cat /proc/net/igmp List multicast group to which the host is subscribed. Use Internet Group Management Protocol.
cat /proc/net/dev_mcast List multicast interfaces.
ping -L 239.192.104.2 To check connectivity with another multicast address
ping -L 224.0.0.1 All hosts configured for multicast will respond with their IP addresses
ping 224.0.0.2 All routers configured for multicast will respond
ping 224.0.0.3 All PIM routers configured for multicast will respond
ping 224.0.0.4 All DVMRP routers configured for multicast will respond
ping 224.0.0.5 All OSPF routers configured for multicast will respond
Check If Multicast enabled in the kernel or not:
#grep -i multi /boot/config-<Kernel version>
* CONFIG_IP_MULTICAST=y
* CONFIG_IP_ROUTER=y
* CONFIG_IP_MROUTE=y
* CONFIG_NET_IPIP=y
Configuring Map Network Interface to Send Multicast Traffic
To Configure a NIC to send multicast network, we need to add a default route for muticast traffic , to the specific NIC. For example, Below command will allow eth0 to send multicast traffic:
# route add -net 224.0.0.0 netmask 240.0.0.0 dev eth0
And check the route settings with
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.0.1 0.0.0.0 255.255.255.0 U 0 0 0 eth0
224.0.0.0 0.0.0.0 240.0.0.0 U 0 0 0 eth0
0.0.0.0 192.168.0.254 0.0.0.0 UG 0 0 0 eth0
How to Verify the Mutlicast groups in our current system
# netstat -g
IPv6/IPv4 Group Memberships
Interface RefCnt Group
lo 1 all-systems.mcast.net
bond0 1 239.192.153.137
bond0 2 all-systems.mcast.net
$ cat proc/net/igmp
Idx Device : Count Querier Group Users Timer Reporter
1 lo : 0 V2
010000E0 1 0:00000000 0
2 eth0 : 2 V2
9B9B9BEA 1 0:00000000 1
010000E0 1 0:00000000 0
4 eth2 : 1 V2
010000E0 1 0:00000000 0
5 eth3 : 1 V2
010000E0 1 0:00000000 0
Above output shows that eth0 interface configures with Multicast address 9B9B9BEA = 234.155.155.155 ( that means - EA = 234; 9B = 155; 9B = 155; 9B = 155 ). Same information will be reflected from the file /proc/net/igmp
Other Popular Posts
inetd Vs xinetd in linux
Linux Admin Reference - Configuring Auditd in RedHat Enterprise Linux
Network Physical Connectivity Check for Solaris and Linux
Linux Admin Reference - Network Bonding - Redhat Enterprise Linux ( RHEL5 / RHEL6)
RHEL 6 - ISCSI Administration Series - ISCSI Lun resize
RHEL 6 - ISCSI Administration Series - Configuring ISCSI Server and Client
RHEL 6.3 - LDAP Series - Part 1 : Implementation of LDAP Authentication
Linux Admin Reference - SUDO Configuration in RedHat Enterprise Linux
Understanding Linux Hugepages
RHEL 6 - Controlling Cache Memory / Page Cache Size
Configuring Map Network Interface to Send Multicast Traffic
To Configure a NIC to send multicast network, we need to add a default route for muticast traffic , to the specific NIC. For example, Below command will allow eth0 to send multicast traffic:
# route add -net 224.0.0.0 netmask 240.0.0.0 dev eth0
And check the route settings with
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.0.1 0.0.0.0 255.255.255.0 U 0 0 0 eth0
224.0.0.0 0.0.0.0 240.0.0.0 U 0 0 0 eth0
0.0.0.0 192.168.0.254 0.0.0.0 UG 0 0 0 eth0
http://unixadminschool.com/blog/2014/03/rhel-what-is-multicast-and-how-to-configure-network-interface-with-multicast-address/
route del -net 224.0.0.0 netmask 240.0.0.0 dev eth2
How to Verify the Mutlicast groups in our current system
# netstat -g
IPv6/IPv4 Group Memberships
Interface RefCnt Group
————— —— ———————
lo 1 all-systems.mcast.net
bond0 1 239.192.153.137
bond0 2 all-systems.mcast.net
$ cat proc/net/igmp
Idx Device : Count Querier Group Users Timer Reporter
1 lo : 0 V2
010000E0 1 0:00000000 0
2 eth0 : 2 V2
9B9B9BEA 1 0:00000000 1
010000E0 1 0:00000000 0
4 eth2 : 1 V2
010000E0 1 0:00000000 0
5 eth3 : 1 V2
010000E0 1 0:00000000 0
Above output shows that eth0 interface configures with Multicast address 9B9B9BEA = 234.155.155.155 ( that means - EA = 234; 9B = 155; 9B = 155; 9B = 155 ). Same information will be reflected from the file /proc/net/igmp
So add into /etc/rc.local:
ifconfig eth0 -multicast
ifconfig lo -multicast
ifconfig lo -broadcast
ip link set eth0 multicast off
ip link set lo multicast off
Telecommunication service provider (ISP)
Stored data through the backdoor, netzpolitik.org, 11.12.2019
Partially, telecommunication servcie provider do store customer data for months and transfer them to authorities like investigation authorities, what is uncovered by a request to the german government net agency.
https://netzpolitik.org/2019/vorratsdaten-durch-die-hintertuer/
Summary: Security with DNS can be achieved 1000%. As already mentioned, the risks found in the man-in-the-middle-attacks and the queried remote-host-DNS itself:
* /etc/hosts: local DNS, filled up with the example for /etc/hosts from above and
* pdnsd: Start and (permanent) fill up of the harddisc-cache of pdnsd with pairs IP and Domain. If the remote-host-dns (IP) is entered into the section for root-server in /etc/pdnsd.conf while all other remote-DNS (section server) are commented in, next two steps with Linfw3 and TOR-Browser are not essential anymore.
* Linfw3: Blocking of all DNS of Linfw3 (except one unrequested DNS only, otherwise Linfw3 will release all DNS). The removal of DNS( by IP) might not be essential to reach maximal security, but we removed them to go really sure.
* Tor-Browser: Now for Domains with belonging IP not stored local in /etc/hosts and not stored in pdnsd-cache (var/cache/pdnsd/pdnsd.cache), the tor-browser (with its own anonymizing remoted hosted DNS) is used (Firefox ESR 52.9, RedHat) instead of the IP not anonymizing current browser (Firefox-ESR-52.9 (slackware14.2/slack14.2, el6, OpenSuSE, ...) - and for IP with belonging domain already local stored the current browser is used again.
Or always use the Tor-Browser, then your IP gets in any possible case ( always ) anonymized !
Goal (Tor) or own self-goal (goal into the really wrong direction, Eigentor) ?
Past our local DNS-concept (out of pdnsd and accompanying "protective mask" /etc/hosts), the preference of the ip-addressroom IPv4 (instead of IPv6 or both), firewall Linfw3, user.js with all the user_prefs out of about:config from Firefox, its switching into the private mode, firefox-extensions, and the hopeful expectations for the propagation of the DPI- (Deep Packet Inspection - ) clean, secure TLS 1.3 (by server- and clientsided OpenSSL > 1.1.1a)
it´s all up to you!
All the reports from diffent sources and following ones tell us, that TOR does not always keep transfered data really anonymously, which is only partially caused by websides not called by https (ssl), so that they do not get encrypted past the ExitNode.
Have a look onto the listed Entry- and ExitNodes from https://torstatus.blutmagie.de. In our eyes there might be plenty of NSA-relais resp. those captured by NSA & Co..
So be careful during their selection -either their inclusion as exclusion, what might begin countrywise. An explicit example of howto configure the Tor-configuration-file torrc is given on here on Gooken soon, still one, we can not guarantee for each relais.
So get more to know about all the countries of the world in Gooken´s NewsäLinks ( from left menu ), if relais should origin from one or better not!
Do censorship and provider (ISP) bypassing bridges the better than common Entry-Nodes (which to go sure only can be from switzerland) resp. those well-known by you for being the really secure ones?
After torrc is configured, also (additionally) think about magic-hood-hardware (Rasbperry Pi etc), the local proxy Privoxy and finally quit recommended VPN, all (additionally) beneath Tor. VPN is a great impovement, but has got its own weak points, especially at the other end of the "connections", the provider itself.
So think well about everything concerning Tor (right up beginning in its configuration-file torrc)...
 Identity theft: 5 tips, howto protect yourself, PC-WELT.de, 11.08.2020 Identity theft: 5 tips, howto protect yourself, PC-WELT.de, 11.08.2020
https://www.pcwelt.de/ratgeber/Identitaetsdiebstahl-5-Tipps-wie-Sie-sich-schuetzen-koennen-10859914.html
 Uncovered: The 7 most horrible online-traps, PC-WELT.de, 11.08.2020 Uncovered: The 7 most horrible online-traps, PC-WELT.de, 11.08.2020
Cyberkriminelle do always invent methods becoming more clever, in order to get the money of clueless internet user. Simple basic rules can prevent from online theft.
https://www.pcwelt.de/ratgeber/Aufgedeckt-Die-7-fiesesten-Online-Fallen-8028039.html
 Highend-anonymization within the net with Tor & Co, trojaner-info.de, 28.11.2018 Highend-anonymization within the net with Tor & Co, trojaner-info.de, 28.11.2018
Wer maximale Anonymisierung im Internet wünscht, muss mehr tun, als seine Daten über Proxies und VPN-Gateways ins Netz zu leiten.
Es gibt laut Artikel 10 des Grundgesetzes ein verfassungsrechtliches Grundrecht auf anonyme und geschützte Kommunikation, auch im Internet. Wer maximale Anonymisierung im Internet und Schutz vor Tracking wünscht, muss aber schon mehr tun, als seine Daten über Proxies ins Netz zu leiten und Anti-Tracking-Tools zu nutzen. Wer echte Tarnkappen im Internet haben möchte, setzt auf professionelle Netzwerk-Anonymisierungsdienste wie Tor, JonDon, Freenet oder I2P.
https://www.trojaner-info.de/sicher-anonym-im-internet/anonymisierungs-dienste/articles/Tor-und-Co-die-Champions-League-der-Anonymisierungs-Dienste.html
The Tor Project, Inc - Wikipedia
History. The Tor Project was founded by computer scientists Roger Dingledine, Nick Mathewson and five others in December 2006. The Electronic Frontier Foundation (EFF) acted as The Tor Project´s fiscal sponsor in its early years, and early financial supporters of The Tor Project included the U.S. International Broadcasting Bureau, Internews, Human Rights Watch, the University of Cambridge ...
Tor is free software for enabling anonymous communication.The name is derived from an acronym for the original software project name "The Onion Router". Tor directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user´s location and usage from anyone conducting network surveillance or traffic analysis.
The Tor Project is a US 501(c)(3) non-profit organization advancing human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.
No one´s personal information should be up for grabs. Advertising is a billion-dollar industry in the US, and it´s easier than ever for your information to be collected and exploited by ad companies and other corporations. Almost half of all websites -- and a whopping 99% of popular news sites ...
en.m.wikipedia.org/wiki/The_Tor_Project,_Inc
https://www.crowdrise.com/o/en/campaign/tor-project
Tor is a network for the anonymization of connection data. It can be used for TCP-connecitons and in the web for browsing, Instant Messaging, IRC, SSH, E-Mail or P2P.
Tor protects its user from traffci data analyzings. It is based upon the idea of Onion-Routing.
Die ersten Ideen für Tor stammen aus dem Jahr 2000. Zwei Jahre später wurde die Arbeit an Tor durch Matej Pfajfar an der Universität Cambridge begonnen. Darauf folgte am 20. September 2002 die Veröffentlichung der ersten Alpha-Version.
In der Anfangszeit von 2001 bis 2006 wurde Tor durch das United States Naval Research Laboratory mit Unterstützung des Office of Naval Research (ONR) und der Defense Advanced Research Projects Agency (DARPA),[6] vertreten durch Paul Syverson, unterstützt. Die weitere Entwicklung wurde vom Freehaven-Projekt unterstützt. Die Electronic Frontier Foundation (EFF) unterstützte die Entwicklung von Tor zwischen dem letzten Quartal 2004 bis ins späte Jahr 2005 hinein.
Im Dezember 2006 gründeten Dingledine, Mathewson und andere das Tor-Projekt, die The Tor Project, Inc, eine Non-Profit-Organisation für Forschung und Bildung, verantwortlich für die Aufrechterhaltung von Tor.
Im März 2011 wurde das Tor-Projekt von der Free Software Foundation mit dem Preis für gesellschaftlichen Nutzen (engl. "social benefit") ausgezeichnet. Als Grund wurde angegeben, dass Tor weltweit ca. 36 Millionen Menschen unzensierten Zugang zum Internet mit der Kontrolle über Privatsphäre und Anonymität ermögliche. Tor habe sich als sehr wichtig für die Oppositionsbewegungen im Iran und in Ägypten erwiesen.
Im Jahr 2011 finanzierte sich das Projekt zu etwa 60 % aus Zuwendungen der US-Regierung und zu 40 % aus privaten Spenden.
Im Juni 2014 machte der Fall des Erlanger Studenten Sebastian Hahn eine größere Öffentlichkeit und insbesondere den gerade tagenden NSA-Untersuchungsausschuss darauf aufmerksam, dass die NSA neben der Bundeskanzlerin auch den Betreiber eines Tor-Knotens überwacht.
Seit Ende Oktober 2014 ist Facebook über eine eigene Adresse im Tor-Netzwerk erreichbar (https://facebookcorewwwi.onion/), um damit den Zugang für Menschen zu erleichtern, in deren Ländern der Zugang zu Facebook durch Zensur erschwert wird.[12][13] DigiCert hat für Facebook eines der ersten TLS-Zertifikate für eine .onion-Adresse ausgestellt.
Die bisherige Tor-Führungsspitze, der Verwaltungsrat, hat im Juli 2016 sechs neue Mitglieder gewählt und ist gleichzeitig selbst zurückgetreten. Zu den zurückgetretenen zählen auch die Projekt-Mitgründer Roger Dingledine und Nick Matthewson, die jedoch weiterhin die technische Entwicklung des Dienstes leiten. Zum neuen Aufsichtsgremium gehören unter anderem der prominente Kryptologe Bruce Schneier und die Leiterin der Electronic Frontier Foundation, Cindy Cohn.
https://de.wikipedia.org/wiki/Tor_%28Netzwerk%29
What is Tor? A beginner´s guide to the privacy tool ...
Use of Tor has increased since the revelations about NSA surveillance. Photograph: Alex Milan Tracy/NurPhoto/Corbis Who uses Tor? The Tor project team say its users fall into four main groups ...
https://www.theguardian.com/technology/2013/nov/05/tor-beginners-guide-nsa-browser
Review: Tor Browser Bundle lets you browse in anonymity
If you want to beef up and anonymize your Internet browsing experience as well, Tor Browser Bundle (free) is the way to go. The Tor network provides a way to browse anonymously. Tor´s Vidalia ...
pcworld.com/article/2026362/review-tor-browser-bundle
Erneuerbare Freiheit - Projekt Tor
Tor: Für Anonymität, gegen Zensur
In der Allgemeinen Erklärung der Menschenrechte heißt es in Artikel 19: "Jeder hat das Recht auf Meinungsfreiheit und freie Meinungsäußerung; dieses Recht schließt die Freiheit ein, Meinungen ungehindert anzuhängen sowie über Medien jeder Art und ohne Rücksicht auf Grenzen Informationen und Gedankengut zu suchen, zu empfangen und zu verbreiten."
Dieses Recht gilt universell. Es ist ganz explizit nicht beschränkt auf bestimmte Bevölkerungsgruppen, auf eine bestimmte Art der Kommunikation, oder physischen oder anderen Grenzen unterworfen.
[...] Im Juni 2016 hat der Menschenrechtsrat der Vereinten Nationen in einer Resolution über The promotion, protection and enjoyment of human rights on the Internet erneut auf diese Universalität hingewiesen. Er zeigt sich in dieser Resolution tief besorgt darüber, dass dieses Recht weiterhin mit großer Regelmäßigkeit verletzt wird Personen, die sich dafür einsetzen, oft mit aller Macht eingeschüchtert und verfolgt werden. Der Menschenrechtsrat bekräftig daher in seiner Resolution, dass die Rechte, die für Menschen "offline" gelten, auch "online" geschützt und durchgesetzt werden müssen.
In diesem Sinne fördern wir Technologien, die Menschenrechte respektieren und fördern - immer und überall. Tor gehört für uns dabei zu den wichtigsten Technologien in diesem Bereich, und wir würdigen dies in unserer Unterstützung entsprechend.
Tor bietet einen zensurresistenten und sicheren Zugang zum Internet, und ermöglicht es so Hunderttausenden von Menschen in autoritären Regimen, auf freie Medien und Informationen zuzugreifen. Ebenso hilft es Journalisten, Bloggern, Whistleblowern und insbesondere Menschenrechtsaktivisten dabei, sich ohne Furcht vor Repressionen, vor Freiheitsentzug oder Schlimmerem, miteinander zu vernetzen und auszutauschen. Aus diesem Grund wird Tor auch von Organisationen wie Reporter ohne Grenzen, Amnesty International oder Human Rights Watch empfohlen.
Tor ist freie und offene Software, und ermöglicht so jedem die kostenlose und sichere Nutzung. Zugleich garantiert der offene Quellcode, dass die Funktionen von Tor auch unabhängig überprüft werden können. Viele andere Tools bieten dies gerade nicht.
https://erneuerbare-freiheit.de/projekte/tor/
Turn Your Raspberry Pi into a Tor Relay Node
[...] The Tor project attempts to provide a solution to this problem by making it impossible (or, at least, unreasonably difficult) to trace the endpoints of your IP session. Tor achieves this by bouncing your connection through a chain of anonymizing relays, consisting of an entry node, relay node, and exit node:
The entry node only knows your IP address, and the IP address of the relay node, but not the final destination of the request;
The relay node only knows the IP address of the entry node and the IP address of the exit node, and neither the origin nor the final destination
The exit node only knows the IP address of the relay node and the final destination of the request; it is also the only node that can decrypt the traffic before sending it over to its final destination
Relay nodes play a crucial role in this exchange because they create a cryptographic barrier between the source of the request and the destination. Even if exit nodes are controlled by adversaries intent on stealing your data, they will not be able to know the source of the request without controlling the entire Tor relay chain.
As long as there are plenty of relay nodes, your privacy when using the Tor network remains protected -- which is why I heartily recommend that you set up and run a relay node if you have some home bandwidth to spare.
https://www.linux.com/blog/intro-to-linux/2018/6/turn-your-raspberry-pi-tor-relay-node
Raspberry Pi als Tor Node betreiben - Gefahren von Tor Sniffing
Wir editieren nun die Tor Konfiguration um unseren Exit Node zu erstellen. Fügt die untern aufgeführten Zeilen ans Ende der Datei an, eventuell müsst ihr die IP ...
https://raspberry.tips/raspberrypi-tutorials/raspberry-pi-als-tor-node-betreiben-gefahren-von-tor-sniffing
Raspberry PI als TOR Relay Knoten, Tobias Hardes
Raspberry PI als TOR Relay Knoten Das TOR-Netzwerk (TOR kurz für The Onion Routing) ist ein Netzwerk für die Anonymisierung von Verbindungsdaten des Internetnutzers. Damit das Netzwerk funktioniert, erfordert dies viele Teilnehmer, die eigenen...
thardes.de/raspberry-pi-als-tor-relay-knoten
Raspberry Pi as TOR Middle Relay, Blogger
Raspberry Pi as TOR Middle Relay The onion Router - Tor is a service that helps you to protect your anonymity while using the Internet. The goal of the Tor project is to provide a censorship-resistant & safer access to the Internet.
cavebeat.blogspot.com/2012/11/raspberry-pi-tor-middle-relay.html
How to: Use Tor | Surveillance Self-Defense
Tor is a volunteer-run service that provides both privacy and anonymity online by masking, who you are and where you are connecting. The service also protects you from the Tor network itself—you can have good assurance, that you´ll remain anonymous to other Tor users. For people who might need ...
ssd.eff.org/en/module/how-use-tor-windows
TOR Project - Anonymity Online - cccure.training
Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: It prevents somebody watching your Internet connection from learning, what sites you visit, and it prevents the sites you visit from learning your physical location. Tor was ...
cccure.training/m/articles/view/TOR-Project-Anonymity-Online
Support the Tor Project Today!
Donate to the Tor Project today! Take a stand against surveillance and censorship. Protect activists worldwide.
donate.torproject.org
.onion - Dark Web and Deep Web
.onion is a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network. Such addresses are not actual DNS names, and the.onion TLD is not in the Internet DNS root, but with the appropriate proxy software installed, Internet programs such as web browsers can access sites with.onion addresses by sending the request through the network of Tor servers. More at "Wikipedia"
https://en.wikipedia.org/wiki/.onion
Tor Project | Privacy Online
The Tor Project´s free software protects your privacy online. Site blocked? Email [mailto:gettor@torproject.org] for help downloading Tor Browser.
torproject.org
Tor-Relays Info-Page
This mailing list is for support and questions about running Tor relays (entry, middle, non-exit, exit, bridge). To see the collection of prior postings to the list, visit the tor-relays Archives.
lists.torproject.org/cgi-bin/mailman/listinfo/tor-relays/
How can we help? | Tor Project | Support
Tor Browser can certainly help people access your website in places where it is blocked. Most of the time, simply downloading the Tor Browser and then using it to navigate to the blocked site will allow access.
support.torproject.org
Troubleshooting - Tor Browser User Manual
If Tor Browser doesn´t connect, there may be a simple solution. Try each of the following:
tb-manual.torproject.org/en-US/troubleshooting.html
Tor Project download | SourceForge.net
Download Tor Project for free. Tor Bundle Brower and Tails are projects from TorProject.org. Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.
sourceforge.net/projects/torproject/
Packets to download and to install from fr2.rpmfind.net and torproject.org:
- tor (el6)
- torsocks (el6)
- torbrowser (torproject.org)
eventually also install:
- vidalia (el6) - Vidalia is a cross-platform controller GUI for Tor, built using the Qt framework. Vidalia runs on any platform supported by Qt 4.1, including Windows, Mac OS X, and Linux or other Unix variants using the X11 window system. Vidalia allows you to start and stop Tor, view the status of Tor at a glance, and monitor Tor´s bandwidth usage. Vidalia also makes it easy to contribute to the Tor network by helping you setup a Tor server, if you wish.
- polipo (mdv2012) - Polipo is a lightweight caching web proxy that was designed as a personal cache. It is able to cache incomplete objects and will complete them using range requests. It will use HTTP/1.1 pipelining if supported by the remote server.
Install the packages (rpm -i --force paket_name) and enpack torbrowser (Tarball) with file-roller or manual by terminal into /home/toruser1/
Start Tor (and the tor-Browser)
su toruser1 &&sg torgroup "sh /home/toruser1/tor-browser_en-US/Browser/start-tor-browser"
I consider the TOR project quite important. But, since typical internet users are urged to use the TOR network in order to browse the internet, the involved risks have to be explained in detail, g-loaded.eu, 04.02.2011
https://www.g-loaded.eu/2011/04/02/how-secure-is-the-tor-network-for-everyday-internet-browsing/
How can I stay anonymous with TOR?, lifehacker.com
1. Don´t use Windows. Just don´t. This also means don´t use the Tor Browser Bundle on Windows. Vulnerabilities in the software in TBB figure prominently in both the NSA slides and FBI´s recent takedown of Freedom Hosting.
2. If you can´t construct your own workstation capable of running Linux and carefully configured to run the latest available versions of Tor, a proxy such as Privoxy, and a web browser (with all outgoing clearnet access firewalled), consider using Tails or Whonix instead, where most of this work is done for you. It´s absolutely critical that outgoing access be firewalled so that third party applications cannot accidentally leak data about your location.
3. If you are using persistent storage of any kind, ensure that it is encrypted. Current versions of LUKS are reasonably safe, and major Linux distributions will offer to set it up for you during their installation. TrueCrypt might be safe, though it´s not nearly as well integrated into the OS. BitLocker might be safe as well, though you still shouldn´t be running Windows. Even if you are in a country where rubber hosing is legal, such as the UK, encrypting your data protects you from a variety of other threats.
4. Remember that your computer must be kept up to date. Whether you use Tails or build your own workstation from scratch or with Whonix, update frequently to ensure you are protected from the latest security vulnerabilities. Ideally you should update each time you begin a session, or at least daily. Tails will notify you at startup if an update is available.
5. Be very reluctant to compromise on JavaScript, Flash and Java. Disable them all by default. If a site requires any of these, visit somewhere else. Enable scripting only as a last resort, only temporarily, and only to the minimum extent necessary to gain functionality of a web site that you have no alternative for.
6. Viciously drop cookies and local data that sites send you. Neither TBB nor Tails do this well enough for my tastes; consider using an addon such as Self-Destructing Cookies to keep your cookies to a minimum. Of zero.
7. Your workstation must be a laptop; it must be portable enough to be carried with you and quickly disposed of or destroyed.
8 Don´t use Google to search the internet. A good alternative is Startpage; this is the default search engine for TBB, Tails, and Whonix. Plus it won´t call you malicious or ask you to fill out CAPTCHAs.
Your Environment
Tor contains weaknesses which can only be mitigated through actions in the physical world. An attacker who can view both your local Internet connection, and the connection of the site you are visiting, can use statistical analysis to correlate them.
1. Never use Tor from home, or near home. Never work on anything sensitive enough to require Tor from home, even if you remain offline. Computers have a funny habit of liking to be connected. This also applies to anywhere you are staying temporarily, such as a hotel. Never performing these activities at home helps to ensure that they cannot be tied to those locations. (Note that this applies to people facing advanced persistent threats. Running Tor from home is reasonable and useful for others, especially people who aren´t doing anything themselves but wish to help by running an exit node, relay, or bridge.
2. Limit the amount of time you spend using Tor at any single location. While these correlation attacks do take some time, they can in theory be completed in as little as a day. And while the jackboots are very unlikely to show up the same day you fire up Tor at Starbucks, they might show up the next day. I recommend for the truly concerned to never use Tor more than 24 hours at any single physical location; after that, consider it burned and go elsewhere. This will help you even if the jackboots show up six months later; it´s much easier to remember a regular customer than someone who showed up one day and never came back. This does mean you will have to travel farther afield, especially if you don´t live in a large city, but it will help to preserve your ability to travel freely.
3. When you go out to perform these activities, leave your cell phone turned on and at home.
https://lifehacker.com/how-can-i-stay-anonymous-with-tor-1498876762
Links about TOR (TOR-Project with TOR-Browser) in german language only
Letztlich lebt das Tor-Netz vor allem davon, dass jeder als Freiwilliger durch den Betrieb verschiedener Arten von Nodes das offene Netz stärken kann—und dass es einige Unermüdliche gibt, die das Netz mit ihrem Einsatz sicherer machen. Sie erinnern uns daran, dass der Schutz der Privatsphäre auch im Internet ein Grundrecht ist, dass der Kampf gegen die NSA technisch noch nicht verloren ist, und dass die Utopie eines dezentralen Internets trotz Kommerzialisierung und Datensammelwut großer Firmen noch nicht ganz ausgeträumt ist.
[...] Die durch Tor unterstützte Anonymität darf dabei nicht missverstanden werden. Es geht nicht darum, dass man "anonym" bleibt—die Anonymität bezieht sich auf den Kommunikationsweg: Wenn ich z.B. Facebook mit meinem Realnamen nutze, macht Tor dennoch Sinn, da so mein Provider und alle, die massenweise überwachen, nicht mitbekommen, dass ich überhaupt Facebook nutze. Und Facebook bekommt nicht mit, wo ich mich gerade befinde—etwas, das ich ihnen höchstens freiwillig mitteilen will. Das heute so populäre Tracking läuft so ins Leere.
https://motherboard.vice.com/de/article/8q8ym4/das-sind-die-menschen-die-in-deutschland-tor-server-betreiben-123
So funktioniert Tor, ein Beispiel: Ein Anwender möchte die Seite tecchannel.de anonym aufrufen. Benutzt er das TOR-Netzwerk, bekommt der Nutzer zunächst eine Liste mit allen verfügbaren TOR-Servern. Danach nimmt der installierte Client Kontakt zu einem zufälligen TOR-Server auf. Dieser Server kontaktiert nun einen zufälligen zweiten Server, welcher einen dritten in den Verbund mit aufnimmt. Über Server Nummer drei verlässt der Anwender das TOR-Netzwerk und wird auf die entsprechende Seite weitergeleitet. Somit würde in der Log-Datei von tecchannel.de die IP-Adresse des dritten Servers auftauchen.
The Onion Router: So funktioniert der dezentrale Anonymisier-Dienst. (Quelle: EFF.org)
Die einzelnen TOR-Server selbst kennen nur die Vorgänger und die Nachfolger. Server Nummer drei hat also keine Ahnung, wo sich Server Nummer eins befindet oder was dessen IP-Adresse ist. Wer der Anwender ist, weiß nur TOR-Server Nummer eins. TOR verwendet immer drei Server. Somit will man die Antwortzeiten so gering wie möglich halten und trotzdem eine möglichst hohe Anonymität schaffen. Die TOR-Server wiederum können überall auf der Welt stehen. Die Software ist so ausgelegt, dass jeder mit wenigen Schritten auch als TOR-Server auftreten kann. Somit sind alle in der Lage, der Schnüffelei entgegenzuwirken.
https://www.tecchannel.de/a/gegen-zensur-und-ausspaehung-anonym-im-internet-mit-tor-und-privoxy,1732021
Entry Guards (Entry Relays, Entry Nodes, Guards, Guard Nodes oder auch Tor-Eingangsknoten)
Tor kann, wie alle Echtzeitanonymisierungsdienste, keinen ausreichenden Schutz gegen Angreifer bieten, die den ersten und den letzten Knoten einer Verbindung kontrollieren. Dies ist unabhängig davon, wie viele Knoten dazwischen liegen. Der Angreifer kann hier allein über Paketanzahl und zeitliche Abfolge von Paketen einen Zusammenhang - auch über die Zwischenknoten hinweg - herstellen und hätte somit die Verbindung zwischen Sender und Empfänger aufgedeckt. Da Tor-Routen kurzlebig sind und regelmäßig neu ausgewählt werden, geht die Wahrscheinlichkeit, dass so zumindest eine der vom Tor-Client aufgebauten Routen durch einen Angreifer aufdeckbar wäre, für jeden Tor-Nutzer auf Dauer gegen 100 %. Insbesondere Nutzer, die Tor regelmäßig zum Schutz einer immer gleichen Kommunikationsbeziehung nutzen, würden bezüglich dieser früher oder später nahezu sicher deanonymisiert. Verschärfend kommt hinzu, dass der Angreifer eine Route boykottieren kann, wenn er mindestens einen beliebigen Knoten in ihr kontrolliert. Auf diese Weise kann er auf allen Routen eine Neuauswahl der Knoten erzwingen, bei denen er beteiligt ist, aber nicht die zur Deanonymisierung nötige Kontrolle über den Start- und Endknoten hat. Somit müssen zusätzliche Routen aufgebaut werden, und damit steigt die Wahrscheinlichkeit einer für den Angreifer günstigen Route an.
Deshalb werden bei Tor, dem Standardmodell des Onion-Routings widersprechend, die ersten Knoten der Routen vom Client nicht dynamisch gewählt, sondern es werden für alle aufgebauten Routen dieselben Einstiegsknoten verwendet, sogenannte Entry Guards. Der Client wählt dazu aus einer Liste mit Entry Guards zufällig eine kleine Menge (standardmäßig drei) aus und verwendet diese anschließend über mehrere Wochen und Sitzungen hinweg als erste Knoten auf allen aufgebauten Routen. Lediglich bei Ausfall dieser Knoten wird eine ggf. vorübergehende Ersatzauswahl getroffen. Entry Guards können dabei nur Knoten werden, die bereits längere Zeit laufen, über diese Zeit eine hohe Verfügbarkeit aufwiesen und eine überdurchschnittliche Übertragungskapazität haben.
Auf diese Weise kann weitgehend ausgeschlossen werden, dass auf Dauer jeder Nutzer nahezu zwangsläufig eine für einen Angreifer deanonymisierbare Route aufbaut. Sollte der Nutzer nämlich keine der durch einen Angreifer kontrollierten Entry Guards gewählt haben, kann er auf obigem Weg überhaupt nicht deanonymisiert werden, da der erste Knoten der Routen dann stets außerhalb der Kontrolle des Angreifers ist. Liegen die gewählten Entry Guards des Nutzers dagegen unter der Kontrolle des Angreifers, so ist die Wahrscheinlichkeit einer Deanonymisierung erhöht, bzw. diese geschieht entsprechend häufiger, weil der Eingangsknoten dann sicher vom Angreifer kontrolliert wird und die Sicherheit der Route nur noch von der Wahl des Ausgangsknotens abhängt. Außerdem wird auf diese Weise das Risiko gesenkt, dass ein Angreifer eine Liste sämtlicher Tor-Nutzer erstellen kann. Da die Nutzer sich stets mit denselben Eingangsknoten verbinden, werden die vom Angreifer kontrollierten Entry Guards immer nur von derselben Gruppe Nutzer kontaktiert, während alle anderen Tor-Nutzer stets bei ihren Eingangsknoten außerhalb des Einflussbereiches des Angreifers bleiben.
https://de.wikipedia.org/wiki/Tor_(Netzwerk)
Middle Nodes (Middle Relays, Tor-Mittelknoten)
Exit Nodes (Exit Relays, Tor-Ausgangsknoten)
Ein neuralgischer Punkt des Tor-Netzwerks sind die sogenannten Exit Nodes: Je mehr es davon gibt, um so schwerer ist es auch, das Deepweb zu überwachen: Exit Nodes sind der Endpunkt einer langen Verschlüsselungskette, die dafür sorgt, dass das Tor-Netzwerk noch immer ein relativ anonymes Surfen erlaubt, das von Geheimdiensten und vor allem von kommerziellen Big-Data-Firmen nur schwer überwacht werden kann.
Zwar ist das Betreiben eines Exit Nodes mit besonderen Risiken verbunden, weil die IP eines solchen Servers stets sichtbar ist. Trotzdem wurde in Deutschland noch nie ein solcher Betreiber rechtskräftig verurteilt. Je mehr Menschen Tor-Server betreiben, desto schneller und vor allem sicherer wird das Netz. Und je mehr Nutzer es gibt, desto geringer die Wahrscheinlichkeit, identifiziert zu werden.
Deutschland spielt dabei im Tor-Netzwerk eine wichtige Rolle. So liefen noch vor einigen Jahren rund 80% des Tor-Ausgangstraffics nur über die Server des Augsburgers Moritz Bartl. Die Arbeit deutscher Tor-Aktivisten wird dabei auch durch die relativ überwachungskritische deutsche Gesetzgebung erleichtert.
[...] Dabei sind wir auf Exit Relays spezialisiert, weil die selbst mit dem nötigen technischen Know-How nicht von jedem selbst betrieben werden wollen. Im Jahr 2011 wurde daraus der erste gemeinnützige Tor-Verein Zwiebelfreunde e.V., inzwischen sind 13 Organisationen in 10 Ländern dabei. Wir sammeln Spenden und teilen sie dann unter den teilnehmenden Organisationen auf.
https://motherboard.vice.com/de/article/8q8ym4/das-sind-die-menschen-die-in-deutschland-tor-server-betreiben-123
Impressum
Eine Telefonnummer anzugeben ist nach deutschem Recht erforderlich. Dies ist jedoch keine Support-Hotline!
Zwiebelfreunde e.V.
c/o DID Dresdner Institut für Datenschutz
Palaisplatz 3
D-01097 Dresden
Fax. +49-(0)-911-30 844 667 48
Tel. +49-(0)-351-212 960 18
Amtsgericht Dresden, VR 5388. Vertretungsberechtiger Vorstand: Moritz Bartl, Juris Vetra, Jens Kubieziel. Satzung.
https://www.zwiebelfreunde.de/contact.html
heise.de:
"Nicht alle Verbindungen, über die die Datenpakete transportiert werden, sind verschlüsselt, sondern nur die zwischen den Routern
Und hier ist auch schon der Haken an der Sache: Vom Client bis zum Ausgangsknoten ist der Tor-Verkehr zwar verschlüsselt, ab dann hängt es aber vom Browser ab, ob eine SSL/TLS-Verbindung aufgebaut wird.
Der Datenverkehr wird also nicht mehr auf der kürzesten Internet-Route transportiert, sondern über das Tor-Netz. Wenn sich nun ein Tor-Ausgangsknoten unter der Kontrolle einer staatlichen Stelle befindet, kann diese den kompletten Verkehr mitschneiden.
Knoten unter staatlicher Überwachung?
Gerüchten aus dem Umfeld der Telekommunikationsüberwachung ("Lawful Interception") zufolge sollen 50 Prozent der Tor-Ausgangsknoten unter der Kontrolle staatlicher Organe sein, die den darübergeleiteten Verkehr mitschneiden. Datenschutzkonforme Maßnahmen sind in diesem Zusammenhang wohl nicht zu erwarten. Auch können Kriminelle solche Tor-Ausgangsknoten betreiben und dort versuchen, Kreditkarteninformationen oder Bitcoins abzufischen. Da es viele Tor-Ausgangsknoten gibt, muss jemand, der ein Interesse an den Informationen hat, auch eine Vielzahl von ihnen überwachen - oder noch einfacher die Knoten selbst betreiben. Private oder vertrauliche Informationen sollte man via Tor keinesfalls übertragen.
Neben der Liste der Knoten, die der Client über den Directory Server herunterladen kann, bietet Tor noch die Funktion einer dynamischen Bridge (Middle Node). Manche Staaten, die den Internetgebrauch zensieren, können über den Directory Server sehr schnell eine Filterliste erstellen und somit das Benutzen des Anonymisierungsnetzwerks verhindern. Die Bridge-Funktion soll es ermöglichen, den Tor-Client so zu konfigurieren, dass er als Bindeglied zwischen dem blockierten Nutzer und dem Tor-Netzwerk fungieren und Ersterem den Zugang zum Anonymisierungsnetzwerk verschaffen kann. Mittels Deep Packet Inspection (DPI) sind jedoch staatliche Stellen in der Lage, selbst diese dynamischen Bridges in wenigen Minuten zu finden. Ein Bot prüft dann, ob der Internetrechner das Tor-Protokoll spricht, und blockiert auch diesen Server.
Ein weiterer sicherheitsrelevanter Aspekt ist, dass Tor den Browser nicht vor Angriffen schützt. Mit speziellen Remote-Forensic-Tools kann man gezielt den Tor-Browser infizieren und das Verhalten des Nutzers inklusive seiner echten IP-Adresse mitlesen. In der Praxis ist genau das passiert und die mitgeschnittenen Daten wurden anonym an staatliche Stellen übermittelt. Diese können mit solchen Werkzeugen zwar Kriminelle aushorchen, die das Tor-Netzwerk missbrauchen, allerdings ist die Anonymität der nicht kriminellen Nutzer ebenfalls bedroht.
Rückschlüsse auf den Nutzer
Eine Studie [1] von Forschern der Georgetown University (Washington, D. C.) zeigt: Wenn ein Angreifer Zugriff auf entsprechende autonome Systeme und Internet-Austauschknoten hat, kann er mit einer Wahrscheinlichkeit von 95 Prozent die Tor-Benutzer deanonymisieren. Auch kann Tor die Signatur eines Browsers nicht verbergen. Wenn ein Benutzer ein paar Toolbars und Erweiterungen installiert, kann man ihn selbst ohne IP-Adresse anhand seiner Browser-Signatur erkennen.
Wenn sich beispielsweise ein Benutzer via Tor Inhalte beschafft, die in der Amazon-Cloud gehostet sind, und anschließend mit demselben Browser nicht über das Anonymisierungsnetzwerk auf Amazon zugreift, kann man anhand seiner Signatur auf ihn schließen. Selbst der empfohlene Tor-Browser mit Sicherheitserweiterungen liefert beim Test "Panopticlick" der Electronic Frontier Foundation (EFF), der über die Rückverfolgbarkeit von Browser-Signaturen Aufschluss gibt, ein schlechtes Ergebnis (Abb. 3). Er hinterlässt noch immer 12,84 Bit, die zur Identifizierung des Benutzers führen können.
Fazit
Wer annimmt, dass man nach dem Installieren eines Tor-Clients im Internet anonym unterwegs sein kann, irrt sich. Tor verbirgt nur bedingt die IP-Absenderadresse auf IP-Ebene. Weder die Applikation noch die Browser-Signatur werden geschützt. Verschlüsselt wird nur innerhalb des Tor-Netzes, nicht zwingend an den Ausgangsknoten. Wer dort die Daten mitliest und wer die Exit Nodes betreibt, ist unbekannt. Tor-Nutzer sollten sich darüber keine Illusionen machen. (ur)
Literatur
Studie "Users Get Routed: Traffic Correlation on Tor by Realistic Adversaries"; www.ohmygodel.com/publications/usersrouted-ccs13.pdf
https://www.heise.de/ix/heft/Hinter-Schichten-2268444.html?artikelseite=&view=
Die Ultraschall-Töne sind sogar unbemerkt in Fernseh- und Radioprogramme, Audio- und Videodateien sowie Streamingangebote integrierbar. Auf diese Weise ist es zum Beispiel möglich festzustellen, dass ein Computer, Tablet oder Fernseher, auf dem gerade eine Serie gestreamt oder eine Audionachricht abgehört wird, der gleichen Person gehört wie das Smartphone, das das versteckte Signal empfängt.
Der Internet-Sicherheitspezialist Vasilios Mavroudis bewies sogar, dass auch Webseiten so manipuliert werden, dass sie beim Aufrufen uXTD-Signale aussenden. Selbst Verschlüsselungen oder die Nutzung von Proxy- oder TOR-Servern garantieren dann keine Anonymisierung mehr.
https://www.tagesschau.de/wirtschaft/handy-uxtd-technik-101.html
Sicherheitslücke: Tor-Browser enttarnt Nutzer-IP, PC-WELT.de, 06.11.2017
Eine Lücke im Tor-Browser für Mac und Linux gibt unter bestimmten Umständen die Nutzer-IP preis. Ein vorläufiger Hotfix löst das Problem teilweise.
Ende Oktober entdeckte Filippo Cavallarin vom Sicherheitsunternehmen We Are Segment eine Sicherheitslücke im Tor-Browser für Linux und Mac OS. Die TorMoil getaufte Schwachstelle öffnet Links, die mit "file://" beginnen, am Tor-Browser vorbei. Bei diesem Versuch kann die IP-Adresse des Tor-Nutzers mit übertragen werden - die vom Tor-Browser versprochene Anonymität wird somit ausgehebelt. Wie die Sicherheitsexperten von We Are Segment erklären, liegt die Schwachstelle im Umgang des Browsers Firefox mit Links begründet. Windows-, sowie Tail- und Sandbox-Nutzer sind von der Sicherheitslücke nicht betroffen.
Die Tor-Entwickler haben noch vor dem Wochenende einen Hotfix für den Tor-Browser erarbeitet. Der Tor-Browser für Mac und Linux steht auf torproject.org in Version 7.0.9 zum Download bereit. Wer den Tor-Browser für Linux oder Mac OS sowie Tor-Software aus dem Alpha-Zweig nutzt, sollte die neue Version umgehend installieren. Noch heute soll eine überarbeitete Alpha-Version für Linux und Mac OS folgen. Der Hotfix in der neuen Browser-Version schließt zwar die Sicherheitslücke, bringt jedoch eine Einschränkung mit. Das Klicken auf "file://"-Links funktioniert hier nicht mehr. Nutzer können Links stattdessen einfach in die Adressleiste ziehen, um dieses Problem zu umgehen.
https://www.pcwelt.de/a/sicherheitsluecke-tor-browser-enttarnt-nutzer-ip,3448687
Software::Security
Tor-Projekt stellt nächste Protokollgeneration vor, PRO-LINUX, 03.11.2017
Das Tor-Projekt arbeitet seit vier Jahren daran, das in die Jahre gekommene Protokoll zu erneuern. Jetzt stehen die Spezifikation sowie eine erste Alphaversion der neuen Protokollgeneration bereit.
Tor ist ein Anonymisierungs-Netzwerk, das das sogenannte Onion-Routing verwendet, um den Anwendern den größtmöglichen Schutz vor überwachung und Traffic-Analyse zu bieten. In diesem Netz können verschiedene Dienste betrieben werden, es kann aber auch genutzt werden, um normale Webseiten anonym zu erreichen. Speziell für das Web hat das Projekt den Tor-Browser entwickelt, eine modifizierte Version von Firefox.
Schon vor viereinhalb Jahren wurde klar, dass das Tor-Protokoll aktualisiert werden muss. Einige der damals nach mehrjährigem Betrieb erkannten Mängel waren die mangelnde Skalierbarkeit der verborgenen Dienste, die auch in einer Anfälligkeit gegen Denial-of-Service-Angriffe resultierte, generell langsame Geschwindigkeit, Angriffe durch verborgene feindselige Verzeichnis-Server, wie sie von den Geheimdiensten zweifellos in großer Menge betrieben werden, und das inzwischen als zu schwach geltende RSA-Verschlüsselungsverfahren mit 1024 Bit.
Das Tor-Projekt begann bereits kurz darauf, eine neue Generation des Protokolls auszuarbeiten. Diese Arbeit resultierte in der Freigabe einer Alphaversion vor kurzer Zeit. Jetzt steht auch eine Spezifikation des neuen Protokolls zur Verfügung. Die neue Version enthält zumindest bereits den Kern der Spezifikation und verbessert unter anderem die Verschlüsselung. Das neue Protokoll, dessen Versionsnummer 3 ist, ist auch zukunftssicherer, da es erweiterbar ist.
Statt SHA1, Diffie-Hellman und RSA mit 1024 Bit kommen in der neuen Version SHA3, ed25519 und curve25519 zum Einsatz. Die Onion-Adressen sind dadurch notwendigerweise länger geworden und bestehen nun aus 56 zufällig erzeugten Zeichen. Das neue Protokoll kann in der aktuellen Alphaversion des Tor-Browsers verwendet werden. Laut der Ankündigung ist die Alphaversion erst der Anfang. Es sind noch Funktionen wie Offline-Schlüssel für Dienste, verbesserte Client-Autorisierung, eine Steuerungs-Schnittstelle, verbesserte Wächter-Algorithmen, sichere Namensdienste, Statistiken, Routing mit gemischter Latenz, Unterstützung von Blockchains, Künstliche Intelligenz und eine Schnittstelle für Virtuelle Realität geplant. Die Entwickler wollen jedoch nichts überstürzen.
Das alte Protokoll wird noch längere Zeit erhalten bleiben und wird zunächst auch noch die Standardversion bleiben, bis die neue Version besser ausgereift ist. Details zur Nutzung der neuen Generation des Protokolls können im Projekt-Wiki nachgelesen werden.
https://www.pro-linux.de/news/1/25298/tor-projekt-stellt-nächste-protokollgeneration-vor.html
Darknet-Browser Tor is ready for Android: You can surf complete anonymously with your handy, CHIP, 27.05.2019
The Tor-Browser is rated as a symbol for anonymes surfing in the internet and the easiest way into the Darknet. Now a ready version of the browser was provided in the Google Play Store. We show you, howto surf with this browser by upon your Android smartphone over the Tor-network.
https://www.chip.de/news/Darknet-Browser-Tor-fuer-Android-fertig-Am-Handy-komplett-anonym-surfen_148414180.html
Tor-Browser mit neuem Update: Anonym surfen mit Windows, macOS, Android und iOS, CHIP, 27.09.2017
Wer im Internet surft, ist Freiwild. Von allen Seiten wird Ihr Browser angezapft: sei es von der Werbeindustrie, von Dienstanbietern, Geheimdiensten und Hackern. Das Tor-Netzwerk ist zwar in den letzten Jahren etwas in Verruf geraten, bietet aber immer noch mehr Anonymität als alle anderen Maßnahmen. Außerdem kommen Sie über den Tor-Browser in das sonst geheime Darknet.
Want Tor really work?, torproject.org, noticed by Gooken on 02.01.2017
You need to change some of your habits, as some things won´t work exactly as you are used to.
Use Tor Browser
Tor does not protect all of your computer´s Internet traffic when you run it. Tor only protects your applications that are properly configured to send their Internet traffic through Tor. To avoid problems with Tor configuration, we strongly recommend you use the Tor Browser. It is pre-configured to protect your privacy and anonymity on the web as long as you´re browsing with Tor Browser itself. Almost any other web browser configuration is likely to be unsafe to use with Tor.
Don´t torrent over Tor
Torrent file-sharing applications have been observed to ignore proxy settings and make direct connections even when they are told to use Tor. Even if your torrent application connects only through Tor, you will often send out your real IP address in the tracker GET request, because that´s how torrents work. Not only do you deanonymize your torrent traffic and your other simultaneous Tor web traffic this way, you also slow down the entire Tor network for everyone else.
Don´t enable or install browser plugins
Tor Browser will block browser plugins such as Flash, RealPlayer, Quicktime, and others: they can be manipulated into revealing your IP address. Similarly, we do not recommend installing additional addons or plugins into Tor Browser, as these may bypass Tor or otherwise harm your anonymity and privacy.
Use HTTPS versions of websites
Tor will encrypt your traffic to and within the Tor network, but the encryption of your traffic to the final destination website depends upon on that website. To help ensure private encryption to websites, Tor Browser includes HTTPS Everywhere to force the use of HTTPS encryption with major websites that support it. However, you should still watch the browser URL bar to ensure that websites you provide sensitive information to display a blue or green URL bar button, include https:// in the URL, and display the proper expected name for the website. Also see EFF´s interactive page explaining how Tor and HTTPS relate.
Don´t open documents downloaded through Tor while online
Tor Browser will warn you before automatically opening documents that are handled by external applications. DO NOT IGNORE THIS WARNING. You should be very careful when downloading documents via Tor (especially DOC and PDF files, unless you use the PDF viewer that´s built into Tor Browser) as these documents can contain Internet resources that will be downloaded outside of Tor by the application that opens them. This will reveal your non-Tor IP address. If you must work with DOC and/or PDF files, we strongly recommend either using a disconnected computer, downloading the free VirtualBox and using it with a virtual machine image with networking disabled, or using Tails. Under no circumstances is it safe to use BitTorrent and Tor together, however.
Use bridges and/or find company
Tor tries to prevent attackers from learning, what destination websites you connect to. However, by default, it does not prevent somebody watching your Internet traffic from learning that you´re using Tor. If this matters to you, you can reduce this risk by configuring Tor to use a Tor bridge relay rather than connecting directly to the public Tor network. Ultimately the best protection is a social approach: the more Tor users there are near you and the more diverse their interests, the less dangerous it will be that you are one of them. Convince other people to use Tor, too!
Be smart and learn more. Understand what Tor does and does not offer. This list of pitfalls isn´t complete, and we need your help identifying and documenting all the issues.
https://www.torproject.org/download/download.html.en#warning
Tor-network: KAX17 made massive attacks for deanonymization, trojaner-info.de, 12.09.2021
Seit mindestens 2017 hat ein unbekannter, mit umfangreichen Ressourcen ausgestatteter und offenbar staatlich unterstützter Angreifer tausende potenziell schädliche Server in Eingangs-, Mittel- und Ausgangspositionen des Tor-Netzwerks betrieben. Ein IT-Sicherheitsforscher mit dem Pseudonym Nusenu, der selbst Mitglied der Community ist, sieht darin einen Versuch, im großen Stil Nutzer des Dienstes zu deanonymisieren.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/tor-netzwerk-kax17-fuehrt-massive-deanonymisierungsangriffe-durch.html
Tor-Nutzer über Mausbewegungen identifizieren, netzpolitik.org, 03.10.2016
Jose Carlos Norte hat Methoden gefunden, wie man Nutzerinnen und Nutzer des Anonymisierungsdienstes Tor anhand von Mausradbewegungen identifizieren kann.
Er schreibt auf seinem Blog:
It is easy to fingerprint users using tor browser to track their activity online and correlate their visits to different pages. getClientrects provides a very interesting vector for fingerprinting TOR Browser users. The CPU benchmark and the Mouse wheel and mouse speed methods provide even more information to distinguish between similar users.
Wie diese Form des Fingerprintings genau funktioniert, hat Golem.de auch auf deutsch zusammengefasst, https://netzpolitik.org/2016/tor-nutzer-ueber-mausbewegungen-identifizieren/
EU-US-Datenschutzschild: Was passiert mit unseren Daten?, Tagesschau.de, 07.12.2016
Wenn europäische und US-Vorstellungen zum Datenschutz aufeinander stoßen, prallen Welten aufeinander. Das hat auch der Europäische Gerichtshof so gesehen, und das Datenschutzabkommen Safe Harbour gestoppt. Nun tritt der Nachfolger in Kraft.
Was machen Google, Facebook oder anderen Internetgiganten mit meinen Daten? Das fragen sich viele. Denn im Internet wird das Innerste nach außen gekehrt. Es geht um Namen, Freunde, Adressen, um Profile und Positionen, ob man gerne viel kauft oder bescheiden lebt, in einem guten oder schlechten Viertel wohnt. Wer darf das alles wissen? Möglichst wenige, sagt die EU. Denn das alles ist Privatsache, solange die Daten nicht anonymisiert sind - oder die Weitergabe von den Nutzern ausdrücklich gestattet wird. Die EU wollte auch die USA für die Sorgen der Nutzer sensibilisieren - sie sollen dort ernst genommen werden. Denn jenseits des Atlantiks laufen die meisten Daten zusammen, an einem Ort, der eigentlich unerreichbar ist für europäische Datenschutzregeln.
Das soll sich mit dem neuen Abkommen ändern. Ob das tatsächlich so sein wird, hängt nicht nur vom guten Willen in den USA ab. Ob es so funktioniert, wie man es sich in Brüssel vorstellt, soll jährlich überprüft werden. Ein Druckmittel der Europäer. Denn vor allem im EU-Parlament, bei den europäischen Datenschutzbehörden und nicht zuletzt bei den Internetnutzern ist das Misstrauen gegenüber der Datensicherheit in den USA deutlich gewachsen - nicht zuletzt nach den Enthüllungen des Whistleblowers Edward Snowden. Er hatte behauptet, die US-Geheimdienste bedienten sich uneingeschränkt und ungeniert aus dem Datenreservoir, das aus Europa auf US-Servern landet.
Recht auf Vergessen?
Das "Recht auf Vergessen" soll also auch dann Wirklichkeit werden, wenn unerwünschte Daten längst nicht mehr in der EU sind. Die Zugriffsmöglichkeiten werden erweitert: "Der Datenschutzschild wird die transatlantische Wirtschaft stärken und unsere gemeinsamen Werte bekräftigen", hofft EU-Kommissarin Jourova. Für ihre US-Verhandlunspartnerin geht es aber nicht nur um Werte, vor allem aber um von Bürokratie möglichst wenig behindertes Wirtschaftswachstum im boomenden Internetsektor: " Für Verbraucher bedeutet der freie Fluss von Informationen, dass sie von den neuesten digitalen Produkten und Dienstleistungen profitieren, unabhängig davon, wo sie entstehen".
Das zeigt: Die Vorstellungen, was guter Datenschutz ist, liegen trotz des neuen Abkommens noch weit auseinander. Für die Europäer geht es um den Schutz der Privatsphäre. Für die Amerikaner vor allem um Sicherheit. Ein heikler Punkt bleibt der umstrittene Zugriff durch US-Geheimdienste auf Daten von EU-Bürgern, die in den USA gespeichert sind. Aber auch hier können sich die US-Behörden nicht mehr einfach wegducken.
Bei Fehlern müssen Geheimdienste löschen
Eine spezielle Schiedsstelle soll dafür sorgen, dass Nachfragen von EU-Bürgern auch bei den Geheimdiensten nicht in den Papierkorb wandern. Es soll also etwas mehr Transparenz geben. Es gibt sogar Korrekturpflichten, falls die Geheimdienste etwas "falsch" gespeichert haben. Zum Löschen können sie aber nicht gezwungen werden. Sie lesen auch weiterhin mit. Allerdings wird in Washington versichert, dass eine "Massenspeicherung" europäischer Daten nicht existiert und auch nicht geplant sei. Nachzuprüfen ist das nicht.
Der österreicher Maximilian Schrems ist damit weniger zufrieden: "Da gehts eben darum, dass man sich irgendwo beschweren kann. Aber wenn das alles sowieso legal ist, bringt mir auch eine Beschwerdestelle nicht viel." Der 29-jährige Jurist aus Salzburg hatte den Stein ins Rollen gebracht. Mit einer Klage gegen ein älteres Datenschutzabkommen zwischen Europa und den USA mit dem Namen "Safe harbour" (Sicherer Hafen).
Alter Datenhafen galt als unsicher
Der Europäische Gerichtshof hatte diesen Datenhafen im vergangenen Jahr für äußerst unsicher erklärt und Neuverhandlungen mit den USA erzwungen. Daraus ist jetzt der EU-US-Datenschutzschild geworden. "Jetzt ist die gesamte Massenüberwachung anscheinend doch nicht mehr da, weil die EU ein paar Briefe aus den USA bekommen hat, dass das alles nicht so ist", beklagt Schrems. Er glaubt: Die Geheimdienste lesen weiterhin mit.
Allerdings: Mit dem neuen Abkommen könnte es für Nutzer einfacher werden, zu erfahren, was die Geheimdienste am Ende tatsächlich gespeichert haben. Dazu soll eine schriftliche Eingabe über die besagte Schiedsstelle genügen. Die US-Behörden sind zu einer Antwort angehalten - wenn keine Sicherheitsbedenken dagegen stehen. Das bedeutet: Die Antworten aus übersee dürften oft recht kurz ausfallen. Und nicht immer zufriedenstellend für europäische Internetnutzer.
https://www.tagesschau.de/wirtschaft/privacy-shield-103.html
Deutsche im Visier des US-Geheimdienstes: Von der NSA als Extremist gebrandmarkt, tagesschau.de, 07.03.2014
Die NSA späht gezielt Deutsche aus, die sich mit Software zum Schutz vor Überwachung im Internet beschäftigen. Das geht aus einem geheimen Quellcode hervor, der NDR und WDR vorliegt. NSA-Opfer lassen sich damit namentlich identifizieren. Einer von ihnen ist ein Student aus Erlangen.
Von Lena Kampf, Jacob Appelbaum und John Goetz, NDR
Es ist eines der empfindlichsten Geheimnisse der NSA, der Motor der weltweiten Überwachungsmaschine: der Quelltext des Programms XKeyscore, dem umfassendsten Ausspähprogramm des US-Auslandsgeheimdiensts.
NDR und WDR liegen Auszüge des Quellcodes vor. Teile der Sammlungs-Infrastruktur also, sogenannte Software-Regeln, in denen die Geheimdienstler festlegen, was oder wen sie ausforschen wollen.
Es sind nur wenige Zahlen und Zeichen, die die Programmierer aneinanderreihen müssen. Doch wenn das Programm XKeyscore diese Regeln ausführt, geraten Menschen und ihre Daten in ihr Visier. Die Verbindungen von Computern mit dem Internet werden gekennzeichnet und in einer Art Datenbank abgelegt. Die Nutzer sind quasi markiert. Es ist die Rasterfahndung des 21. Jahrhunderts.
Nutzer des Tor-Netzwerks Ziel der Spähattacken
In dem vorliegenden Quellcode geht es um die Ausspähung der Infrastruktur und der Nutzer des Tor-Netzwerks. Tor steht für "the onion router" - ein Programm, bei dem Internetverkehr, beispielsweise eine Anfrage an eine Suchmaschine, durch verschiedene Server geleitet wird und sich Anonymisierungsschichten ähnlich wie bei einer Zwiebel um die Anfrage legen. So wird die Herkunft der Anfrage, also die IP-Adresse verschleiert. Die IP-Adresse ist ähnlich wie eine Postadresse und verrät unter anderem den Standort des Rechners.
Es gibt zirka 5000 Tor-Server weltweit, die von Freiwilligen betrieben werden. Es ist eine Anonymisierungsinfrastruktur, die vielfach gerade in Ländern gebraucht wird, in denen es gefährlich ist, dem Regime preiszugeben, welche Webseiten man besucht oder von wo man sie abruft. Im Iran und in Syrien zum Beispiel. Tor wird von Journalisten, Menschenrechtsaktivisten und Anwälten weltweit verwendet.
Deutsche IP-Adressen in Fort Meade begehrt
Die Berichterstattung des "Guardian" über Powerpoint-Präsentationen aus dem Snowden-Archiv hat im vergangenen Jahr gezeigt, dass das Tor-Netzwerk der NSA ein besonderer Dorn im Auge ist. Die Top-Secret-Dokumente und der hier erstmals veröffentlichte Quellcode zeigen, dass die NSA erhebliche Versuche unternimmt, Nutzer des Tor-Netzwerks zu deanonymisieren. Recherchen von NDR und WDR zeigen: Deutsche IP-Adressen sind im Quellcode der NSA als eindeutiges Ziel definiert.
Die IP 212.112.245.170 führt zu einem grauen, fabrikartigen Gebäude, dessen hohe Mauern mit Stacheldraht umzäunt sind. "Am Tower" heißt die Straße in einem Industriegebiet in der Nähe von Nürnberg. Es ist ein Rechenzentrum mit Mietservern in langen Regalen. Sie sehen alle gleich aus. Aber einer wird von der NSA ausgespäht. Sebastian Hahn, ein Student und Mitarbeiter am Informatiklehrstuhl in Erlangen hat diesen Server gemietet.
Zweites namentlich bekanntes NSA-Opfer
Obwohl er nur Mittel zum Zweck für die NSA ist - schließlich wollen die Geheimdienstler über seinen Server herausfiltern, wer das Tor-Netzwerk nutzt - fühlt sich Hahn in seiner Privatsphäre verletzt. Weil er etwas Gutes tun wolle, gerate er "in den Fokus der Geheimdienste", sagt er sichtlich entsetzt. Er ist nun wohl nach Bundeskanzlerin Angela Merkel das zweite namentlich bekannte deutsche Überwachungsopfer des amerikanischen Geheimdienstes.
Der Fachanwalt für IT-Recht, Thomas Stadler, sieht einen "Anfangsverdacht der geheimdienstlichen Agententätigkeit". Die Bundesanwaltschaft äußerte sich nur allgemein: Sie prüfe alle Hinweise. Auf Anfrage teilt die NSA lediglich allgemein mit, man halte sich strikt an das Gesetz: "Privatsphäre und Bürgerrechte werden in der Computerüberwachung immer bedacht."
Es geht nicht nur um Metadaten
Außerdem lässt sich durch den Quellcode zum ersten Mal zweifelsfrei belegen, dass die NSA nicht nur sogenannte Metadaten, also Verbindungsdaten, ausliest. Werden E-Mails zur Verbindung mit dem Tor-Netzwerk genutzt, dann werden laut Programmierbefehl auch die Inhalte, der sogenannte E-Mail-Body, ausgewertet und gespeichert. Das entsprechende Zitat aus dem Quellcode lautet: "email_body(´https://bridges.torproject.org/´´ : c++ extractors".
William Binney, 70, war technischer Direktor bei der NSA, bis er 2001 ausstieg, weil die Maschinen, die er erfand, gegen die eigene Bevölkerung gerichtet wurden. Heute wird er vor dem NSA-Untersuchungssauschuss aussagen. Im Interview mit NDR und WDR erklärt er, warum die Geheimdienstler es ausgerechnet auf Nutzer des Tor-Netzwerks abgesehen haben: "Es darf keine freien, anonymen Räume geben", sagt er. "Die wollen alles über jeden wissen."
Nur einige wenige sind davon ausgenommen: Eingeschrieben in den Quelltext, der NDR und WDR vorliegt, ist die Differenzierung zwischen den Partnerländern der USA, den sogenannten "Five Eyes", Neuseeland, Australien, Großbritannien sowie Kanada, und den anderen Ländern. Verbindungen, die aus den "Five-Eyes"-Ländern auf die Tor-Webseite vorgenommen werden, sollen laut der vorliegenden Regel nicht markiert werden. Aus allen anderen Ländern allerdings schon. Ohne Ausnahme, https://www.tagesschau.de/inland/nsa-xkeyscore-100.html .
IT-Sicherheit: Koalition will Deep Packet Inspection und Netzsperren, heise.de, 04.13.2017
In einer Nacht- und Nebelaktion haben die Regierungsfraktionen ohne öffentliche Debatte den Weg freigemacht für eine umfangreiche änderung des Telekommunikationsgesetzes (TKG), mit dem Provider künftig bei auftretenden Netzstörungen eine abgespeckte Variante der umstrittenen "Internet-Nacktscanner" in Stellung bringen und damit eine "Deep Packet Inspection light" (DPI) durchführen dürften. Die Regierungsfraktionen betonen zwar nun gleich zweimal, dass "Kommunikationsinhalte" nicht erfasst werden dürften. Zur Analyse freigeben wollen sie aber die "Steuerdaten", mit denen im OSI-Modell für Netzwerkprotokolle auf der vergleichbar hohen "Sitzungsschicht" die Prozesskommunikation zwischen zwei Systemen aufrechterhalten werden soll. Zugleich will die große Koalition den Anbietern von Telekommunikationsdiensten gestatten, "Datenverkehr bei Vorliegen einer Störung einzuschränken", auf Warnseiten umzuleiten "oder zu unterbinden". Ferner soll es den Diensteanbietern zur Abwehr von Cyberangriffen erlaubt werden, den Datenverkehr zu filtern und dabei "legitime von maliziöser Kommunikation" zu trennen. Den federführenden Innenausschuss des Bundestags hat die Initiative bereits Ende März still und leise passiert, sie soll in der nächsten Sitzungswoche am 27. April kurz vor 23 Uhr vom Plenum ohne weitere Korrekturen verabschiedet werden.
Spurlos und Anonym im Netz mit Tor & Co.
Spurlos im Netz mit Tor & Co.: Die wichtigsten Anonymisierungsdienste und Tools für anonymes Surfen im Internet
Rechner benötigen Gatekeeper zum Schutz vor Tracking, 06.02.2018
Mehr als zwei Drittel der Deutschen vertrauen einer Bitkom-Umfrage nach weder dem Staat noch der Wirtschaft gerne ihre Daten an. Nutzer möchten sich anonym im Internet bewegen und so Ihre Daten und Privatsphäre vor der NSA, dem Staat oder auch kommerziellen Anbietern schützen und dem Online-Betrug vorbeugen. Anonymisierungsdienste, Proxies, VPN-Gateways, Anti-Tracking-Tools, Tor & Co. sind die als wichtigen Gatekeeper zum Schutz vor Datenschnüfflern.
https://www.trojaner-info.de/sicher-anonym-im-internet/anonymisierungs-dienste/articles/Anonymisierungsdienste-und-tools-fuer-sicheres-und-anonymes-Surfen-im-Internet.html
Neues Anonymisierungsverfahren stoppt NSA, PC-WELT.de,
Sicherer als Tor und nicht zu langsam: Die neue Anonymisierungstechnik Riffle soll eine absolut sichere Internetnutzung ermöglichen. Wissenschaftler des renommierten Massachusetts Institute of Technology MIT haben zusammen mit der Schweizer École Polytechnique Fédérale de Lausanne ein neues Verfahren zum anonymen Datenaustausch im Internet entwickelt. Es soll sicherer als das bekannte Tor sein und selbst der NSA widerstehen, http://www.pcwelt.de/news/Riffle-Neues-Anonymisierungsverfahren-soll-NSA-Co.-aussperren-10009874.html
Überwachung
Geheime Dokumente: Der BND hat das Anonymisierungs-Netzwerk Tor angegriffen und warnt vor dessen Nutzung, netzpolitik.org. 09.14.2017
Der BND hat ein System zur Überwachung des Tor-Netzwerks entwickelt und Bundesbehörden gewarnt, dass dessen Anonymisierung "unwirksam" ist. Das geht aus einer Reihe geheimer Dokumente hervor, die wir veröffentlichen. Der Geheimdienst gab einen Prototyp dieser Technik an die NSA, in Erwartung einer Gegenleistung.
[...] Weltweiter, passiver Angreifer
Wie alle in der Praxis eingesetzten Anonymisierungs-Systeme dieser Art kann auch Tor nicht gegen "einen weltweiten passiven Angreifer" schützen. Das steht so explizit im Design-Dokument. Auch die Dokumentation warnt: "Wenn ein Angreifer den Internet-Verkehr beobachten kann, der aus ihrem Rechner kommt und den Verkehr, der an dem von ihnen gewählten Ziel ankommt, kann er mit statistischen Analysen herausfinden, dass beide zusammen gehören." Die Internet-Überwachung von NSA und GCHQ tut genau das.
Eine ganze Reihe an Forschern hat diesen Angriff praktisch demonstriert, durch simples Zählen der übertragenen Pakete, über die Analyse von Zeitfenstern bis zur De-Anonymisierung durch einen Bruchteil des Verkehrs. All diese Forschung ist öffentlich einsehbar. Auch die Geheimdienste beobachten diese Forschung, nutzen sie für eigene Zwecke und nutzen theoretische Schwachstellen in ihrer praktischen Überwachung aus.
Die Hacker vom BND stützen sich bei ihrem Angriff auf "eine Studie einer amerikanischen Universität", die sie auch an die NSA weitergeben.
[...] Der BND-Spitze kommt das gelegen. Man erhofft sich zwar, dass auch die BND-eigene Auswertung wieder "angestoßen" werden kann, an Tor zu arbeiten. Aber das eigentliche Ziel ist größer. Der BND will etwas von der NSA: Eine Technologie aus dem "Bereich Kryptoanalyse" zur Entzifferung verschlüsselter Inhalte. Pullach weiß, dass Fort Meade das Objekt der Begierde "erfahrungsgemäß nicht so leicht herausrücken", wird. Deshalb sammeln die Deutschen Gegenleistungen, der Angriff auf Tor ist "ein weiterer Baustein" dafür.
[...] Wie genau der BND Tor "zerhäckseln" will, ist in der uns vorliegenden Version leider weitgehend geschwä,;rzt. Doch wie zuvor beruft sich der Geheimdienst auf öffentliche Forschung. Zur Umsetzung dürfte der BND eigene Server im Tor-Netzwerk betreiben. M.S. verweist auf passiv schnüffelnde Server, die mutmaßlich von der NSA betrieben werden und betont den "Schutz der eigenen Anonymität" der Geheimdienste.
[...] Sehr hohe Überwachungsdichte
Anderthalb Jahre später warnt der BND deutsche Bundesbehörden davor, Tor zu verwenden. Der "Anonymisierungsdienst Tor garantiert keine Anonymität im Internet", betitelt die Hacker-Abteilung "IT-Operationen" eine Meldung. Das sechsseitige Papier geht am 2. September 2010 an Kanzleramt, Ministerien, Geheimdienste, Bundeswehr und Polizeibehörden.
Laut Kurzfassung ist Tor "ungeeignet" für drei Szenarien: "für die Verschleierung von Aktivitäten im Internet", "zur Umgehung von Zensurmaßnahmen" und für "Computernetzwerkoperationen für Nachrichtendienste" - also geheimdienstliches Hacking. Der BND geht "von einer sehr hohen Überwachungsdichte innerhalb des Netzes" aus, unter anderem durch ",die Möglichkeit, selbst sogenannte Exit-Knoten zur Überwachung einzurichten".
https://netzpolitik.org/2017/geheime-dokumente-der-bnd-hat-das-anonymisierungs-netzwerk-tor-angegriffen-und-warnt-vor-dessen-nutzung/
Tor-Browser
Tor-Browser Der Tor-Browser macht es Spionen beinahe unmöglich, Ihre Spur im Netz zu verfolgen. Seine hohe Sicherheit gegen PRISM bezahlt der User mit langsamen Surfgeschwindigkeiten. Wem Tor zu lahm ist, kann den Browser nur für sensible Surf-Sessions nutzen.
Die hier genannten Programme sind nur ein Teilaspekt des Schutzes vor neugierigen PRISM-Blicken. Wer sich möglichst komplett schützen will, muss konsequenterweise auch auf die Google-Suche oder Yahoo-Mails verzichten (um nur zwei Beispiele zu nennen). Lesen Sie also unbedingt auch unseren Ratgeber zum Schutz vor PRISM . Achtung: Eine hundertprozentig blickdichte Anti-PRISM-Mauer werden Sie kaum errichten können. Dafür kreuzen die Wege Ihres Datenverkehrs im Internet zu oft den Einflussbereich der NSA. Und selbst die beste Verschlüsselung kann theoretisch geknackt werden. Außerdem gibt es für manche Dienste keine vernünftige Alternative. Zwar können Sie beispielsweise Facebook entsagen und zu Diaspora wechseln. Doch dürften Sie dort ziemlich alleine sein und höchstens Monologe führen, während Sie auf Ihre Freunde aus Facebook warten.
Das ist jedoch kein Grund, zu verzagen. Mit unseren Tipps und Tools setzen Sie die Hürden teilweise so hoch, dass die NSA-Agenten gehörig ins Schwitzen kommen werden. Nur ein Beispiel: Selbst superschnelle Hardware braucht für gut verschlüsselte Daten Jahrzehnte, wenn nicht Jahrhunderte, um sie knacken.
http://www.pcwelt.de/galerien/Kostenlose_Anti-PRISM-Tools-8007699.html
Kooperation von BND und NSA: Heimliche Amtshilfe unter Freunden, tagesschau.de, 25.06.2014
Der BND hat jahrelang Daten eines Frankfurter Internetknotenpunkts an die NSA weitergegeben. Nach Recherchen von NDR, WDR und "SZ" leitete er mindestens von 2004 bis 2007 abgefangene Rohdaten direkt an den US-Dienst, von Georg Mascolo, NDR
In Frankfurt laufen die Fäden zusammen. Hier verbindet die weltweit größte Internet-Schnittstelle die Netze von mehr als 50 Ländern. Daten aus Russland fließen über Frankfurt beispielsweise in den Nahen Osten. Schon immer hatten die Amerikaner ein Auge auf Frankfurt geworfen und drängten auf einen direkten Zugriff auf die Glasfasernetze. Bereinigt um die Daten deutscher Bürger soll der BND drei Jahre lang der NSA Datenmaterial zur Verfügung gestellt haben. Vor allem Telefonate sollen so direkt in die Computer der NSA geleitet worden sein. Über den Umfang der Datenweitergabe gibt es widersprüchliche Angaben. Während einige Quellen sie als "sehr umfassend" beschreiben, heißt es in BND-Kreisen, es habe sich zwar um große Mengen gehandelt, aber nur eine von mehreren Leitungen sei betroffen gewesen. Erst 2007 soll die Operation vom damaligen BND-Chef Uhrlau gestoppt worden sein. Auch im Kanzleramt war man zu dem Schluss gekommen, dass die Aktion "viel zu heikel ist", so ein damals Beteiligter. Gegen den Protest der NSA wurde das Projekt eingestellt. Die gemeinsame Operation soll den Recherchen zufolge 2004 begonnen haben und war auch im Kanzleramt bekannt. Offenbar sind aber weder das Parlamentarische Kontrollgremium noch die Bundestagskommission, die für die Abhörmaßnahmen der Geheimdienste zuständig ist, jemals über die damalige Operation informiert worden.
"Ich bin noch nie so belogen worden"
#34c3: Die Lauschprogramme der Geheimdienste, netzpolitik.org, 29.01.2018
"Ich bin noch nie so belogen worden", sagte Hans-Christian Ströbele über seine Arbeit im NSA-BND-Untersuchungsausschuss. In einem Gespräch mit Constanze Kurz resümiert der grüne Politiker die Ergebnisse der parlamentarischen Untersuchung.
https://netzpolitik.org/2018/34c3-die-lauschprogramme-der-geheimdienste/
Deep Packet Inspection (DPI)
Pro & Contras, wiki.kairaven.de
Pro
- Bandbreiten-Management
- Spambekämpfung
- Virenbekämpfung
- Einbruchserkennung
Contra
- Inhaltliche ITK-Überwachung parallel zur oder nach der Vorratsdatenspeicherung
- Analyse und Überwachung des Inhalts von E-Mails, Instant Messaging, Webchats, SMS im Rahmen personen- und gruppenbezogener Überwachungsmaßnahmen oder allgemeiner Überwachungsprogramme der Geheimdienste
- Filterung / Zensur, Blockierung von E-Mails, Instant Messages, Webchats, SMS, Webseiten
- Drosselung, Blockierung, Erkennung von P2P-Anwendungen, Filesharing, Anonymisierungsdiensten, Web-Proxys
- Generierung von Benutzer- und Kundenprofilen, personenbezogener Werbung
- Aufweichung bzw. Abschaffung der Netzneutralität (siehe auch Wissenschaftliche Dienste Deutscher Bundestag - Aktueller Begriff: Netzneutralität)
Verschlüsselung
Die DPI Analyse des Inhalts der Nutzdaten der Datenpakete wird durch ihre Verschlüsselung unterbunden, sofern sichere Verschlüsselungsalgorithmen, Verschlüsselungsimplementierungen und Schlüssellängen verwendet werden.
Die DPI Analyse kann aber zumindest die Anwendung und Existenz von Verschlüsselung aufdecken und auswerten, um z. B. anschließend den Transport verschlüsselter Datenpakete zu blockieren oder sie für Versuche zur
Entschlüsselung zu spiegeln.
Anonymisierung
Sofern Anwendungen oder Netzwerke (z. B. VPN, Tor, I2P), die für die Anonymisierung genutzt werden, sichere Verschlüsselungsmethoden integrieren, treffen die Aussagen wie unter Verschlüsselung zu.
Hersteller
DPI Kontext
In order to prevent the cut off TOR like an onion, listed firefox-extensions from above should get installed and the configuration from kairaven.de from above should be made like for the current used firefox-browser too!
 Use a Raspberry Pi as a Tor/VPN Router for Anonymous Browsing, 1/28/15 Use a Raspberry Pi as a Tor/VPN Router for Anonymous Browsing, 1/28/15
Roll Your Own Anonymizing Tor Proxy with a Raspberry Pi
We´ve shown you how to use a Raspberry Pi as both a Tor proxy and a personal VPN, but Make shows off how to do both in one unit for truly anonymous browsing everywhere.
There are many interesting things you can do with a Raspberry Pi, but this one isn´t just fun, …
The build here uses two Wi-Fi adapters to get the job done. Once it´s complete, you´ll have a passive VPN connection that you´ll hardly even notice is there. You´ll also have Tor installed, so you can flip over to that connection with just a couple of clicks. It´s a pretty simple setup all things considered, and it´ll act as a nice bridge between your standard router for those times when you want to browse anonymously or get around any location-specific blocks.
Browse Anonymously with a DIY Raspberry Pi VPN/Tor Router
https://lifehacker.com/use-a-raspberry-pi-as-a-tor-vpn-router-for-anonymous-br-1682296948
Preis: ca. 40 Euro
or
Tarnkappen-Hardware
Tarnkappe im Internet mit der richtigen Anonymisierungs-Hardware
Im Internet mit der richtigen Anonymisierungs-Hardware, trojaner-info.de, 2015
[...] Anonymität und digitale Integrität kann über Anonymisierungsprogramme wie Tor, aber auch über spezielle Hardware-Lösungen erreicht werden.
Nachfolgend einige Router für das Heimnetzwerk im Porträt im Kampf gegen Tracking, Fingerprinting und digitale Bespitzelung im Kurzporträt.
Anonymebox: Anonym in einer Zigarettenschachtel
Die Anonymebox ist wie die meisten anderen Lösungen eine Ready-to-use-Möglichkeit, anonym zu surfen. Alle Komponenten sind in einer schicken roten Box verbaut, die nicht größer als eine Zigarettenschachtel ist. Anonymebox wird mit einer Software auf SD-Karte, einem LAN- und WLAN-Adapter sowie einem Netzteil und Ethernet-Kabel geliefert. Die Hardware-Tarnkappe ist schnell eingerichtet. Per TOR gehts dann - wenn alle anderen Vorkehrungen für das anonyme Surfen getroffen wurden - unerkannt durchs World Wide Web. Das gilt für Desktop-Rechner, Smartphones, Tablets und Laptops gleichermaßen. Per Web-Interface lässt sich die vorgetäuschte IP-Adresse bzw. deren Standort einsehen. Alternativ kann über Geoiptool ein Geolocation-Tool aufgerufen werden, das ebenfalls den Fake-Standort anzeigt.
Die Anonymebox kostet aktuell 199 Euro inklusive MwSt.
eBlocker: Anoymisierungs-Know-how von der "anderen Seite"
[...] Das noch recht junge Produkt eBlocker bietet einen interessante Plug-and-Play-Ansatz. Die Mini-Box wird schlüsselfertig geliefert und kann ohne Software-Installation an den Router angeschlossen werden. Der eBlocker soll auf allen Endgeräten, die über das Heimnetzwerk mit dem Internet verbunden sind, Werbung und Tracking eliminieren. Optional kann ein Nutzer auch seine IP-Adresse anonymisieren. Technologisch basiert die Anonymisierungs-Hardware auf dem Einplatinenrechner Banana Pi: Ein kleiner Mini-Rechner, der sich großer Beliebtheit in der Open-Source-Community erfreut.
Öffentliche Filterlisten in Kombination mit algorithmischen Filtern sollen dabei helfen, die zunehmende Zahl von Tracking-TAGs zu blockieren, die von Werbenetzwerken in Umlauf gebracht wird. Mit einfachem Klick kann zusätzlich auch das Tor-Netzwerk integriert werden.
eBlocker soll Ende 2015 auf den Markt kommen und nach Herstellerangaben unter 200 Euro kosten. Im Paket ist Hard- und Software erhalten und ein Update-Service für ein Jahr.
...
https://www.trojaner-info.de/anonymisierungs-hardware/articles/anonymisierungs-hardware-als-tarnkappe-im-internet.html
Proxys oder "Rewebber" gelten dagegen als hinreichend, seine eigene IP-Adresse gegenüber der jeweils besuchten Seite zu verschleiern.
Auch diese Sicherheit ist jedoch trügerisch: Zumindest der Betreiber des Proxy-Servers weiß stets, wer da nach was sucht im Web, wer da was besucht. Ob es also klappt mit der Anonymisierung, ist nicht nur eine Frage der Technik, sondern vor allem eine der Vertrauenswürdigkeit des Anbieters. Es ist nicht unwahrscheinlich, dass etliche offene Proxy-Dienste in Wahrheit genau das Gegenteil von dem tun, was sie behaupten: So mancher mag beobachten und protokollieren, wer sich da weswegen anonymisieren will.
[...] Der vielleicht interessanteste Web-basierte Proxy ist derzeit das deutsch-schweizerische Projekt picidae. Der Dienst holt sich die vom Nutzer angefragte Web-Seite und wandelt diese komplett in ein Bild um. Der Nutzer braucht nur die gewünschte Web-Adresse in ein einfaches Suchfeld eingeben, der Rest ergibt sich.
Damit ist nicht nur der Seitenaufruf verschleiert, sondern auch jeder Filter ausgehebelt. Das Beste daran: Die Bilder lassen sich völlig normal als Web-Seiten nutzen. Ein Klick auf einen Link, und picidae generiert ein Bild der dahinterliegenden Web-Seite. Die von picidae erzeugten PNG-Screenshots sind also voll funktionale, mit Link-Infos versehene Bitmaps.
http://www.spiegel.de/netzwelt/tech/internet-tricks-gegen-zensur-und-ueberwachung-a-570421.html
JAP (Jondo) - Zertifizierte Betreiber, golem.de, 03.03.2015
Mixkaskaden sorgen für Anonymität
Der Jondonym-Anonymous-Proxy-Server oder kurz JAP wird von seinen Machern als Forschungsprojekt bezeichnet, das den Namen AN.ON - Anonymität Online trägt. Entwickelt wurde es von der Universität Regensburg zusammen mit der Technischen Universität Dresden.
Die Daten werden über sogenannte Mixkaskaden versendet. Dabei werden mehrere Proxys hintereinandergeschaltet und zusätzlich die Daten unterschiedlicher Herkunft miteinander vermischt. Sie werden auch als Mixnetzwerk mit kaskadierenden Proxy-Servern bezeichnet. Jede Proxy-Station kennt nur den vorherigen Server, von dem die Daten kommen, und denjenigen Proxy-Server, an den die Daten weitergereicht werden. Zwischen jeder Station werden die Daten gesondert verschlüsselt.
Anders als bei Tor kann aber nicht jeder eine Zwischenstation - oder Mixe, wie sie genannt werden - betreiben. Lediglich vom Projekt zugelassene Server dürfen an dem Netz teilnehmen. Der Vorteil ist, dass jeder Mix im JAP-Netzwerk vertrauensvoll ist. Die Mixe werden von dem Projekt zertifiziert und müssen eine Selbstverpflichtung unterschreiben, die unter anderem besagt, dass keine Logfiles angelegt werden dürfen. Damit entfällt die bei Tor mögliche Angriffsmethode, dass ein Unbekannter eine Zwischenstation betreibt und so Einsicht in den Datenverkehr bekommt.
[...] Da es aber nur eine begrenzte und bekannte Anzahl an Mixen gibt, ist die theoretische Wahrscheinlichkeit größer, dass ein Angreifer den Eingang und den Ausgang kennt und überwachen kann. Dann kann der Datenverkehr eines Nutzers komplett deanonymisiert werden. Deshalb liegt auf den JAP-Betreibern die Last sicherzustellen, dass kein Angreifer einen Mix betreiben kann. Die begrenzte Anzahl der Mixe ist gewollt, denn je mehr Nutzer ihre Daten über einen einzigen Server leiten, desto schwieriger ist es, einzelne Datenströme daraus zu identifizieren.
[...] Schnelleres anonymes Surfen kostet
Die meisten Mixe werden in Deutschland betrieben, etwa von der Technischen Universität Dresden, dem Unabhängigen Landeszentrum für Datenschutz in Schleswig-Holstein oder der bayerischen Piratenpartei. Da der Betrieb eines Mixes Geld und Aufwand kostet, haben die TU Dresden und die Universität Regensburg das Unternehmen Jondos gegründet, das ebenfalls Mixe betreibt. Jondos bietet auch eine kostenpflichtige Version des Dienstes an, der deutlich höhere Datenraten ermöglicht als die kostenfreie Version. Und hier liegt der entscheidende Nachteil gegenüber Tor: Aktuell liegt dort die Surfgeschwindigkeit durchschnittlich bei über 2 GBits pro Sekunde. In der kostenfreien Variante lässt sich in JAP lediglich mit bis zu 50 KBits pro Sekunde surfen. Erst mit kostenpflichtigen Tarifen lässt sich mit bis zu 1,5 GBit pro Sekunde surfen.
[...] Die kostenfreie Variante hat auch noch weitere Einschränkungen. Dort lassen sich Dateien mit höchstens 2 MByte hoch- und herunterladen und außerdem steht nur HTTP beziehungsweise HTTPS zur Verfügung. In der kostenfreien Variante laufen die Daten durch zwei Mixe, in der kostenpflichtigen können es bis zu drei sein. Die kostenpflichtigen Tarife sind nach Volumen gestaffelt bei Preisen zwischen 5 und 140 Euro für ein halbes Jahr.
Da die Betreiber in Deutschland sind, sind sie dem hiesigen Recht unterworfen. Im Zuge der inzwischen wieder fallengelassenen Vorratsdatenspeicherung von 2009 hatten sich einige Mix-Betreiber verpflichtet, die IP-Adressen sowie Datum und Uhrzeit des Verbindungsaufbaus in das JAP-Netzwerk sowie die Weiterleitungen zu speichern. Mit diesen Daten hätte ein Benutzer deanonymisiert werden können.
[...] Die Geschwindigkeit des JAP-Netzwerks bei kostenfreier Nutzung ist einfach zu gering und die Beschränkung auf 2 MByte große Dateien ist kaum noch zeitgemäß, auch wenn dank Addons kaum mehr als Texte und ein paar Bilder von den angesurften Webseiten übrigbleiben. Nach dem Start des Proxy-Servers dauert es eine ganze Weile, bis eine Verbindung hergestellt werden kann. Manchmal klappt die Verbindung gar nicht. Zwischendurch nervt die Software immer wieder mit Hinweisen auf das kostenpflichtige Angebot.
Schade, denn ansonsten ist die JAP-Software gut, der vorkonfigurierte Jondofox-Browser erspart dem Anwender so manche Fummelei. Er ist vergleichbar mit dem Tor-Browser-Bundle. Allerdings wird dort Tor gleich mitinstalliert, für den Zugriff auf das JAP-Netzwerk muss Jondo zusätzlich installiert werden.
https://www.golem.de/news/jap-netzwerk-anonymes-surfen-fuer-geduldige-1503-112712.html
JAP (Jondo) unterliegt sicherheitstechnisch in vielen Punkten im Vergleich zu Tor.
Zugrundeliegende Studie aus dem Internet ist möglicherweise aber nicht mehr aktuell.
Programme wie das Java-basierte JAP fungieren für den Internet-Nutzer als Proxy, der allen Teilnehmern am Netzwerkwerk die gleiche IP-Adresse zuweist: Eine Aufschlüsselung, wer für welchen Teil des Datenverkehrs verantwortlich ist, soll nicht möglich sein. Das wird unter anderem dadurch ausgeschlossen, dass JAP den Datenverkehr des Nutzers mit dem anderer Nutzer mischt und zudem verschlüsselt.
JAP ist eine deutsche Entwicklung, die in den Anfangsjahren unter anderem durch staatliche Fördergelder finanziert wurde. Inzwischen ist diese Förderung ausgelaufen, die Betreiber bieten nun einen kostenfreien, aber merklich langsameren Service neben einem kostenpflichtigen, aber schnelleren Dienst an. Gesetzesänderungen in Deutschland haben dazu geführt, dass die JAP-Betreiber Daten offenlegen müssen, wenn Verdacht auf Straftaten via Web besteht: Die Anonymität im JAP-Netz findet ihre Grenzen also vor den Schranken der hiesigen Gesetze.
http://www.spiegel.de/netzwelt/tech/internet-tricks-gegen-zensur-und-ueberwachung-a-570421-2.html
Anonymität im Internet wird auch von Kriminelle genutzt, was in der Folge die Strafverfolgungsbehörden auf den Plan ruft. Diese können eine Überwachung eines Nutzers von Jondo bewirken. Dieser Punkt lässt sich bei Jondofox/Jondo als Vorteil verbuchen, da die Vorgehensweise einer möglichen Überwachung eindeutig und transparent ist. Nur bei einem konkreten Verdacht und nach rechtsstaatlichen Vorgaben kann eine Überwachung beantragt werden. Der Gegensatz dazu ist das System Tor. Wer diesen Anonymisierer nutzt, kann so unbescholten sein wie nur möglich, die Überwachungsapparate mehrerer Länder werden versuchen, seine Wege im Tor-Netzwerk zu verfolgen.
http://www.heise.de/download/product/jondofox-58547/download
Anonymität im Internet wird auch von Kriminellen genutzt, was in der Folge die Strafverfolgungsbehörden auf den Plan ruft. Diese können eine Überwachung eines Nutzers von Jondo bewirken. Dieser Punkt lässt sich bei Jondofox/Jondo als Vorteil verbuchen, da die Vorgehensweise einer möglichen Überwachung eindeutig und transparent ist. Nur bei einem konkreten Verdacht und nach rechtsstaatlichen Vorgaben kann eine Überwachung beantragt werden. Der Gegensatz dazu ist das System Tor. Wer diesen Anonymisierer nutzt, kann so unbescholten sein wie nur möglich, die Überwachungsapparate mehrerer Länder werden versuchen, seine Wege im Tor-Netzwerk zu verfolgen.
http://www.heise.de/download/product/jondofox-58547/download
Den (für Tor einzig erforderlichen) Tor-Browser samt mitgelieferten Erweiterungen gibt es für alle gängigen Plattformen.
Ein machtvolles Werkzeug zum Schutz der eigenen Privatsphäre ist der Tor Browser. Die Software leitet den eigenen Internetverkehr verschlüsselt durch ein zwiebelartiges Netzwerk an Servern und verhindert damit, dass irgendwer die eigenen Schritte nachverfolgen kann. Die Webseite Lifehacker schreibt dazu:
"Tor ist nützlich für jeden, der seine Aktivität im Internet vor der Werbeindustrie, Internetprovidern und Webseitenbetreibern schützen möchte. Gleiches gilt für jene, die Zensurbestimmungen in ihrem Land umgehen möchten, […] und jeden, der nicht möchte, dass sein Surf-Verhalten mit ihm in Verbindung gebracht wird."
Der Nachteil des Tor-Browsers: Mit ihm surft man etwas langsamer, da jedes Stück Information nur über Umwege verschickt werden kann. Dafür ist man damit relativ anonym im Internet unterwegs, selbst wenn auch dieser keine absolute Sicherheit gewährleisten kann und noch einige Angriffs-Vektoren übrig bleiben. Anders als noch vor einigen Jahren ist aber die Verlangsamung nicht mehr so auffällig, sofern man nicht seine gesamte Zeit auf Videoportalen verbringt.
Mit Orbot und Orfox gibt es inzwischen auch eine Möglichkeit, Tor auf Android-Geräten mobil zu nutzen.
https://netzpolitik.org/2018/kleines-einmaleins-der-digitalen-selbstverteidigung/
Software::Browser
Firefox erbt weitere Funtionen von Tor-Browser, PRO-LINUX, 05.12.2017
Im zu Ende gehenden Jahr hat Firefox einige Funktionen vom Tor-Browser geerbt, der seinerseits auf Firefox ESR basiert.
Mozilla Foundation
Bereits seit 2014 arbeiten Mozilla und das Tor-Projekt zusammen, um die Sicherheit von Firefox zu erhöhen. Seit den Nightly Builds von Firefox 50 fließen unregelmäßig Patches vom Tor-Browser zu Mozilla zurück. Einer der ersten Patches im Jahr 2016 betraf die Eindämmung von Browser-Fingerprinting. Weitere Patches folgten im Rahmen des "Tor Patch Uplifting"-Projekts. Alle diese Patches sind und bleiben laut Aussage von Mozilla deaktiviert und müssen vom Anwender per about:config aktiviert werden. Der Grund hierfür ist, dass manche der Patches restriktiv wirken und beispielsweise die Darstellung von Webseiten verändern oder blockieren.
Der Code von Tor-Browser entspricht zu 95 Prozent dem von Firefox ESR. Die restlichen 5 Prozent sind größtenteils Patches für Sicherheit und Schutz der Privatsphäre. Diese Patches für Firefox verfügbar zu machen verbessert nicht nur Firefox, sondern erspart dem Tor-Browser-Team die Arbeit, bei jeder neuen Version die Patches erneut zu aktualisieren, wie das Tor-Browser-Team berichtet.
Der erste Patch, der im Rahmen von "Tor Patch Uplifting" in Firefox 50 im August integriert wurde, war "First-Party Isolation". Diese Funktion beschränkt den Zugriff auf Cookies, Cache und andere Daten auf die Domain-Ebene, so dass nur die Domain, die das Cookie oder die Datei auf dem Benutzersystem abgelegt hat, darauf zugreifen kann. Damit soll das Tracking von Anwendern erschwert werden. Bei Tor heißt die Funktion "Cross-Origin Identifier Unlinkable". Ein weiter Patch aus dem Tor-Projekt, der erst in Firefox 58 integriert sein wird, wenn dieser im Januar 2018 veröffentlicht wird, soll den Schutz vor HTML-Canvas-Fingerprinting erhöhen.
http://www.pro-linux.de/news/1/25406/firefox-erbt-weitere-funktionen-von-tor-browser.html
about:config?filter=privacy.firstparty.isolate true
https://browserengine.net/how-to-enable-first-party-isolation-in-firefox/
Tor-Entwickler bemängeln "Tor Browser"-App, heise.de
Eine App zur Nutzung des Anonymisierungsdienstes auf dem iPhone sei "voll von Adware und Spyware", beklagen Tor-Entwickler - und wundern sich, warum.
http://www.heise.de/mac-and-i/meldung/Tor-Entwickler-bemaengeln-Tor-Browser-App-2151505.html?wt_mc=rss.apple.beitrag.atom
Anonymes Surfen
Tor-Browser statt Tor-Button, golem.de, 04.05.2011
Der Entwickler des Tor-Buttons Mike Perry will sich künftig auf die Programmierung des Tor-Browsers konzentrieren. Der Tor-Button für Firefox wird nicht mehr weiterentwickelt - er ist laut Perry ein "sicherheitstechnischer Albtraum".
www.golem.de/1105/83233.html
Wie muss man den Tor Browser einstellen oder konfigurieren, so dass man "wirklich" anonym surft?, gutefrage.net, 02.08.2014
Hintergrund ist die Annahme oder Vermutung, dass ein Großteil der Tor-Knoten nicht mehr sauber sind. Indem die Zahl der Proxy erhöht, kann man anonymer surfen. Richtig?
Wird dazu das Programm "Vidalia" (el6) benötigt?
3 Antworten
Sortiert nach:
Vom Fragesteller als hilfreich ausgezeichnet
Antwort
von Diedda, 01.08.2014, 22:57
Nur den Tor Browser (https://www.torproject.org/download/download-easy.html.en) oder das Betriebssystem (Live-CD) "TAILS" verwenden
Immer updaten wenn es neue Updates gibt
Im Tor Browser links oben über den "S" Button Skripte global ausschalten
Keine privaten Informationen wie dein Name oder Facebook-Account preisgeben
Wird dazu das Programm "Vidalia" benötigt?
Nein (siehe den 1. Punkt).
jeffrey94 02.08.2014, 10:21
Und wenn ich mich irgendwo einloggen möchte, keine Ahnung, ins Online-Banking oder irgendwo wo meine Daten sind. Wie mache ich denn das dann anonym?
Mit "Vidalia", was früher immer dazu installiert wurde, jetzt nicht mehr. Kann man aber hinzuinstallieren, habe ich gelesen. Mit "Vidalia" also, kann man alle Nodes auflisten lassen und den Standort sehen. Außerdem kann man den Datenverkehr steuern, und über weitere Nodes und Ländern leiten lassen, so wie ich das jetzt verstanden habe.
TeeTier 02.08.2014, 12:38
Und wenn ich mich irgendwo einloggen möchte, keine Ahnung, ins Online-Banking oder irgendwo, wo meine Daten sind.
Wer benutzt denn Online-Banking über TOR? Ich schätze mal, dass ein guter Teil der Exit-Nodes kompromittiert ist.
Ich habe selbst mal Wireshark an einem lokalen Exit-Node laufen lassen, und war geschockt wie naiv viele User sind. Zumal viele Websites kein SSL anbieten.
Du solltest NIEMALS irgendwelche Accounts über TOR benutzen, die man mit deiner wahren Identität in Verbindung bringen kann!
jeffrey94 02.08.2014, 16:52
Vielen Dank für die Antwort.
OK, kein Online-Banking, kein sonstigen Logins über Tor..
Dann also überhaupt keine Logins über Tor?
Was haben denn die vielen naiven User denn gemacht?
Ich dachte Tor wäre nicht zurück verfolgbar und zu deanonymisieren?
TeeTier 02.08.2014, 19:47
Also ich habe damals den TOR-Quellcode runtergeladen und alles selbst konfiguriert. Ich habe weder Vidalia und auch kein TOR-Browserbundle benutzt.
Wenn man die torrc Konfigurationsdatei per Hand editiert, hat man VIEL mehr Kontrolle und Möglichkeiten bzgl. des Verhaltens von TOR.
Ich hatte TOR als Relay mit Exit-Node eingerichtet und nur Verbindungen zu Europäischen Domain-Namen zugelassen. (wollte mich keiner unnötigen Gefahr wegen Kinderpornos usw. aussetzen., sprich: es waren nur DE, AT, CH, FR, IT, UK und US Domains erlaubt)
Desweiteren habe ich ausschließlich Verbindungen über Port 80 erlaubt ... sprich unverschlüsselte HT TP Verbindungen.
Dann habe ich mit Wireshark einfach alle Pakete mitgesnifft und als Filter "ht tp.request.method == "POST"" eingetragen.
Da normalerweise POST Anfragen fast nur für Logins oder irgendwelche Aktivitäten, die ein Session-Cookie beinhalten, verwendet werden, konnte ich somit im Klartext alle Möglichen Passwörter und Session-Cookies mitlesen. Von Foren-Beiträgen, privaten Nachrichten und Mails mal ganz abgesehen.
Ja, und mit dieser einfachen Kombination bin ich innerhalb von Minuten an Login-Daten gekommen.
Zum Beispiel GF bietet ebenfalls kein SSL und das Login erfolgt hier im Klartext über HT TP Port 80 per POST Methode ... würdest du dich hier über TOR einloggen, hätte ich (oder jemand anderes, der einen Exit-Node betreibt) dein Passwort ergaunert.
Dazu muss man sagen, dass dieses Mitsniffen von unverschlüsselten Verbindungen technisch weder detektier, noch blockierbar ist. Da kann das TOR Projekt auch nichts für ... ist einfach prinzipbedingt so. :)
Die einzige Möglichkeit, wie du dich davor schützen kannst ist, immer nur über SSL verbinden (also deine Webadressen beginnen mit "ht tps" anstatt "ht tp")
Ich würde behaupten, sich über TOR bei GuteFrage einzuloggen ist unsicherer, als am Berliner Hauptbahnhof ein offenes unverschlüsseltes WLAN zu benutzen. Die Wahrscheinlichkeit einer Man-In-The-Middle-Attacke halte ich dort für geringer.
Wenn du dich schon jemals über TOR irgendwo eingeloggt hast, würde ich schleunigst meine Passwörter ändern ... bei TOR solltest du wirklich alles als kompromittiert ansehen.
Es ist wirklich trivial einfach als TOR ExitNode mitzusniffen. Und - wie gesagt - da gibt es auch kein Mittel gegen.
Dennoch bietet TOR natürlich sehr schöne Anonymittät ... und genau dafür ist TOR ja auch gemacht! :)
Edit: Ich habe im obigen Text immer "ht tp" geschrieben ... das muss natürlich ohne Lücke geschrieben werden, aber der GF Parser ist zu dämlich und denkt es handele sich um Spam. Also bitte einfach das Leerzeichen wegdenken! :)
Diedda 04.08.2014, 20:21
ins Online-Banking oder irgendwo wo meine Daten sind
Wie willst du denn anonym sein wenn du dich wo einloggst wo dein Klarname oder gar deine Bankdaten gespeichert sind ?!
Wenn du einen Falschnamen bei Facebook hast und sonst auch keine anderen persönlichen Daten und dich dort bloß über Tor einloggst dann wäre das anonym insofern man deine echten persönlichen Daten nicht mit dem Account in Verbindung bringen könnte.
Mit "Vidalia"
Wie gesagt nur den Tor Browser (oder "TAILS"). Vidalia ist bloß eine grafische Benutzeroberfläche die du nicht brauchst.
jeffrey94 05.08.2014, 18:44
Wie kann ich denn, den "Weg" über den mein Internet-Traffic gehen soll steuern? Ich dachte das wäre mit "Vidalia" möglich?
Wenn ich also z.B. über mehrere Länder gehen will und z.B. in der Schweiz herauskommen möchte (Exit-Node)?
Diedda 05.08.2014, 19:07
Das wird alles durch Tor automatisch geregelt, wenn du selbst was drann änderst (wie das Land deines Exit-Nodes), hat das bloß negative Auswirkungen auf den Grad deiner Anonymität.
Ansonsten suchst du vielleicht nach einem VPN oder einem normalen Proxy ? Beides ist für 100%ige Anonymität nicht empfehlenswert, reicht im Normalfall aber, und da kannst du auch "vorgetäuschtes" Land angeben (bei bestimmten VPNs oder indem du eben einen Proxy eines bestimmten Landes benutzt)
jeffrey94 05.08.2014, 20:46
Der "automatisch" konfigurierte Tor Browser ist der "unsicherste".
Man kann es - so wie ich höre - auch manuell festlegen und z.B. über 7 oder 8 Server gehen, so dass es dann noch schwieriger wird für eine Deanonymisierung, weil die Wahrscheinlichkeit dann einen "sauberen" Node zu erwischen höher ist. Und man einen "sauberen" Node erwischt, ist eine Deanonymisierung unmöglich, der Aufwand dazu immens groß.
Deshalb verstehe ich nicht was für negative Auswirkungen es haben soll?
Dann ist man doch noch sicherer.
Soweit ich Bescheid weiß, bringen Proxy überhaupt nichts. Da gab es Tests.
Ein VPN ist OK, und kann sogar mit Tor kombiniert werden. IP am Eintritts-Server wird anonymisiert. Und nur der VPN-Dienst kennt die echte IP, und hält dicht, außer vor richterlicher Anordnung und Nachrichtendiensten.
Und jeder VPN-Dienst speichert die echte IP-Adresse und Log-Daten, ja jeder, es gibt keine Ausnahmen. Wer etwas anderes glaubt, ist naiv.
Es ist klar, dass es keine 100%-Anonymität gibt. Aber es geht ja auch kein Mensch auf die Straße, und trägt ein Schild um den Kopf, mit Namen, Adresse, Surfgewohnheiten, Hobbys, letzten Einkäufen, usw.
jeffrey94 06.08.2014
Vielen Dank für die ausführliche Antwort und die Tipps! ;-)
Kurze Nachfragen:
Angenommen man loggt sich über das Tor-Netzwerk irgendwo ein, aber diese Login-Seite verfügt über SSL-Absicherung (https mit grünen Balken oder Schloss). Besteht dann ebenfalls die Gefahr sein Passwort zu offenbaren?
TeeTier 10.08.2014, 15:16
Der TOR-Browser hat immer dieses HTTPS-Anywhere-Addon installiert. D.h. wenn du eine Seite nur mit "http" ohne SSL aufrufst, wird automatisch erst mal versucht, die sichere "https" Variante zu laden. Schlägt dies fehl, wird unverschlüsselt verbunden.
Das ist zwar sehr gut, aber dass kann man umgehen, indem man an einem manipulierten Exit-Node als MITM die SSL-Verschlüsselung entfernt. Unter Umständen muss man dann noch dynamisch ein paar JavaScripte umschreiben, da die oftmals zusätzlich überprüfen, ob die Verbindung sicher ist. Aber für beide Fälle gibt es fertige Skripte, die das ganze voll automatisch erledigen!
Also wenn dein TOR Browser mit deiner Bank tatsächlich über SSL verbunden ist, sehe ich keine Möglichkeit, den Traffic mitzuschneiden. Aber a) halte ich SSL bzw. TLS nicht für das Maß aller Dinge, d.h. ob dort Sicherheitslücken bekannt sind oder werden, weiß ich nicht, und b) ist es - wie oben erwähnt - trivial einfach das "S" aus "HTTPS" zu entfernen! :)
Normalerweise ist das TOR-Netzwerk darauf ausgelegt, solche Manipulationen zu erkennen und den entsprechenden Exit-Node dann auf die "Bad-Exit-Node-List" zu setzen. In der Realität sieht das dann aber so aus, dass ich fast eine Woche auf Teufel komm raus den Traffic manipuliert habe, und es wurde nicht entdeckt. Zudem ist die Bad-Exit-Node-Liste so kurz (Momentan nur knapp 5 Einträge!), dass ich mir nicht vorstellen kann, dass TOR hier über ein effektives Erkennungssystem verfügt.
Also ich würde mich bei TOR auf nichts verlassen, und wenn ich unbedingt SSL benutzen muss, auch wirklich darauf achten, dass ich per SSL verbunden bin!
Zu VPN: Die billigen VPN-Dienste kann man getrost alle als kompromitierte TOR-Exit-Nodes betrachten, die zumindest mitsniffen. Vor allem wenn man sich mal das Impressum von solchen Anbietern anguckt und feststellt, was die Betreiber für zwielichtige Typen sind. Vertrauen kann man solchen Diensten nicht! Das heißt zwar nicht, dass die alles mitsniffen, aber ich würde es tun, wenn ich ein chinesischer VPN-Anbieter wäre ... und sei es nur zum Spaß! :)
Anders sieht es mit eigenen VPN-Servern aus, die man bei seriösen Providern gemietet hat. Dort ist die Wahrscheinlichkeit, dass jemand mitliest vermutlich nur minimal höher, als wenn du dich in Deutschland mit einem T-Online Anschluss verbindest ... mit anderen Worten: Kann man vernachlässigen! :)
Also wirklich "vertrauen" würde ich weder TOR noch VPN ... wobei die Betonung hier auf TOR liegt. :)
FloTheBrain
01.08.2014, 15:09
Selbst wenn alle Knoten im Besitz eines Angreifers sind, auch dann ist es erst nach langer Analyse und statistischer Auswertung möglich eine Person gezielt zu identifizieren.
Was du tun kannst ist den Exit-Node manuell zu bestimmen. Dann kommst du immer an dieser Stelle raus. Da kannst du einen wählen, wo man sich sicher sein kann, dass dieser vertrauenswürdig ist. Zum Beispiel den vom CCC.
Dann sollte man auch nie seinen gesamten Traffic durch Tor leiten, da man sich so angreifbarer für statistische Analysen macht. Daher nur Tor benutzen wenn du bei was bestimmten unsichtbar bleiben willst.
Tor-Browser 100%-anonym, gutefrage.net, 01.03.2015
Antwort
von TeeTier
01.03.2015, 08:00
Es gibt die Möglichkeit durch Timing-Unterschiede den Nutzer fast eindeutig zu enttarnen, wobei man den Traffic aber über mehrere Monate beobachten muss, was insgesamt sehr unwahrscheinlich ist, und auch nicht garantiert zu 100% funktioniert.
Allerdings hat das FBI vor einer Weile ne Menge Kriminelle hochgenommen (Pedos oder Drogenverkäufer oder so), die über TOR kommuniziert haben. Das FBI hat nicht eindeutig verraten, wie sie das genau gemacht haben, und sogar die TOR-Entwickler selbst waren ratlos. Später kam raus, dass es offensichtlich über fehlkonfigurierte Hidden-Services gelang.
Wie gesagt, das war vor ein paar Wochen ... und ich habe mich danach nicht mehr sonderlich um das Thema gekümmert, also kenne ich den aktuellen Stand leider nicht.
Ich würde dringend davon abraten, sich einzig und allein auf TOR zu verlassen.
JavaScript im TOR-Browser sollte man sowieso abschalten und die Anzahl der Hops in der torrc Konfigurationsdatei mindestens auf 5 erhöhen und darüber hinaus die möglichen Exit-Nodes auf eine Hand voll vertrauenswürdiger Betreiber (CCC z. B.) beschränken. Das geht alles nicht mit den grafischen Tools des TOR-Browser Bundles, aber im Internet gibt es Anleitungen für die Konfigurationsdatei ... ist alles eigentlich sehr einfach, und du brauchst nur einen Texteditor.
Aber als "sicher" würde ich TOR nicht mal dann ansehen! :)
Zum Schluss zitiere ich nochmal einen Golem-Artikel:
Denn inzwischen haben mehrere Studien belegt, dass Nutzer im Tor-Netzwerk sehr wohl identifiziert werden können. Aber das Tor-Team behauptet auch gar nichts anderes. Es warnt immer wieder davor, sich nur auf Tor zu verlassen. Tor sei lediglich eines von vielen Werkzeugen, die erst in der Kombination effektiv vor der Enttarnung schützen könnten. Außerdem könnten Fehlkonfigurationen oder andere Unvorsichtigkeiten dazu führen, dass Dritte die anonymen Surfer identifizieren könnten.
Schönen Tag noch! :)
Antwort
von unLieb
Community-Experte
Computer
01.03.2015, 07:43
100 %ige Anonymität im Internet gibt es nicht! Man sieht ja dass ab und an sogar die versiertesten "Hacker" gebustet werden.
Antwort
von Ifm001, 01.03.2015, 08:28
https://de.m.wikipedia.org/wiki/Tor_(Netzwerk)
... hättest Du aber auch selbst finden können.
https://www.gutefrage.net/frage/tor-browser-100-prozentig-anonym
...
...
https://www.gutefrage.net/frage/wie-muss-man-den-tor-browser-einstellen-oder-konfigurieren-so-dass-man-wirklich-anonym-surft
Tor und Proxys
Tails: Das Anonyme Surf-Linux in der VM nutzen, PC-WELT.de, 26.10.2015
Beim Surfen im Internet hinterlassen Sie Spuren in Form Ihrer IP. Mit Tails lässt sich die für andere aber nur schwer ermitteln.
Tails steht für "The Amnesic Incognito Live System", und dieser Name beschreibt die wesentlichen Eigenschaften dieser Linux-Distribution. Tails geht nicht auf dem direkten Weg zur Website, die Sie anfordern, sondern über drei zufällige Zwischenstationen. Die Site erfährt daher nicht Ihre IP, sondern nur jene des letzten Vermittlungsknotens.. Tails nutzt dafür das Tor-Netzwerk und dessen Server. Vor dem Verbindungsaufbau erhält Ihr Rechner von einem Tor-Verzeichnis-Server eine Liste der derzeit verfügbaren Knoten. Der Tor-Client baut anschließend über den ersten Server eine verschlüsselte Verbindung auf. Die Daten fließen verschlüsselt über zwei weitere Tor-Server bis zur Zieladresse. Das Netzwerk Tor steht natürlich auch ohne das System Tails zur Verfügung. Tails nimmt Ihnen aber die Konfiguration ab, geht standardmäßig über Tor online und bietet weitere Sicherheit: Für die Verschlüsselung des eingesetzten Datenträgers kommt Luks zum Einsatz, beim Browser wird eine verschlüsselte Kommunikation priorisiert, und Mails werden mit Open PGP verschlüsselt. Ferner ist die Messenger-Kommunikation über OTR (Off-the-Record) abgesichert, und zusätzlich gibt es zum sicheren Löschen von Daten noch Nautilus Wipe ... , http://www.pcwelt.de/ratgeber/Tails-als-virtueller-PC-9827433.html.
Tor Hidden Services: Über 100 spionierende Tor-Nodes, golem.de, 26.07.2016
Mit Hilfe sogenannter Honions haben US-Forscher mindestens 110 Tor-Nodes identifizieren können, die offenbar aktiv versuchten, Tor Hidden Services auszuspähen. Wer sind die Urheber?
https://www.golem.de/news/tor-hidden-services-ueber-100-spionierende-tor-nodes-1607-122344.html
Can you trust Tor´s exit nodes?, nakedsecurity.sophos.com, 06.25.2015
Tor is the encrypted, anonymous way to browse the web that keeps you safe from prying eyes, right?
Well, no, not always.
Blogger and security researcher Chloe spent a month tempting unscrupulous Tor exit node operators with a vulnerable honeypot website to see if anyone was looking for passwords to steal.
In all, the trap sprung for twelve exit nodes, raising a finger of suspicion for them and reminding us, that you can´t get complacent about security even if you´re using Tor.
Tor is a bit of heavy duty open source security software that´s famously used to access anonymous, hidden services (the so-called Dark Web) but, more commonly, used as a way to access the regular internet anonymously and in a way, that´s resistant to surveillance.
Tor (short for The Onion Router) works by sending your encrypted network traffic on an eccentric journey between Tor ‘nodes´. At each step along the way each Tor node helps keep you safe by never knowing what´s in your message and never knowing more about your data´s journey than the node it came from and the next one it´s going to.
Eventually your network traffic leaves Tor"s safe embrace via an exit node - a gateway computer that decrypts your traffic, so it can rejoin the regular internet, before it arrives at its final destination.
Anyone can set up an exit node and because it´s the place, where traffic is decrypted, anyone who runs an exit node can read the traffic passing through it.
Bad exit nodes are entirely possible then, and bad news if they exist, but how do we find them?
Chloe set up a fake website with a Bitcoin theme, downloaded a complete list of exit nodes and then logged in to the honeypot site multiple times via Tor, using a different exit node and a unique password each time.
Crucially the usernames and passwords were sent over regular HTTP rather than encrypted HTTPS so that when Tor´s layers of encryption were peeled back they were visible in the stream of traffic.
If the login attempts had gone unobserved and unabused then the total number of website visits and log in attempts recorded by the honeypot should have matched the number performed by Chloe exactly.
They didn´t.
https://nakedsecurity.sophos.com/2015/06/25/can-you-trust-tors-exit-nodes/
Neue Dokumente belegen Überwachung: CCC erweitert Strafanzeige gegen Geheimdienste und Bundesregierung, 2014-07-16 00:09:00, henning
Nachdem durch neue Veröffentlichungen bekannt wurde, dass Daten von und zu mindestens einem der Tor-Server, der vom Chaos Computer Club (CCC) in Deutschland betrieben wird, offenbar direkt in den Überwachungssystemen der NSA landen, sind Ermittlungen des Generalbundesanwalts Harald Range nun dringend geboten. Der CCC erweitert daher seine Strafanzeige vom Februar gegen die Verantwortlichen bei den Geheimdiensten und in der Bundesregierung um die neuen Fakten und fordert, die verbotene geheimdienstliche Agententätigkeit gegen den CCC und alle betroffenen Nutzer des Anonymisierungsnetzwerks Tor zu ahnden. mehr …
Chaos Computer Club klagt gegen GCHQ, 2014-07-02 09:00:00, erdgeist
Zusammen mit sieben internationalen Organisationen legt der Chaos Computer Club (CCC) Beschwerde gegen die Programme des britischen Geheimdienstes GCHQ ein, die zum Angreifen und Ausspähen von Netzwerkinfrastruktur und persönlichen Daten von Millionen von Menschen genutzt werden. mehr …
Tor-Weaknesses, en.wikipedia
Like all current low-latency anonymity networks, Tor cannot and does not attempt to protect against monitoring of traffic at the boundaries of the Tor network (i.e., the traffic entering and exiting the network). While Tor does provide protection against traffic analysis, it cannot prevent traffic confirmation (also called end-to-end correlation).[90][91]
In spite of known weaknesses and attacks listed here, a 2009 study revealed Tor and the alternative network system JonDonym (Java Anon Proxy, JAP) are considered more resilient to website fingerprinting techniques than other tunneling protocols.
The reason for this is conventional single-hop VPN protocols do not need to reconstruct packet data nearly as much as a multi-hop service like Tor or JonDonym. Website fingerprinting yielded greater than 90% accuracy for identifying HTTP packets on conventional VPN protocols versus Tor which yielded only 2.96% accuracy. However some protocols like OpenSSH and OpenVPN required a large amount of data before HTTP packets were identified.
Researchers from the University of Michigan developed a network scanner allowing identification of 86% of live Tor "bridges" with a single scan.
Eavesdropping
Autonomous system (AS) eavesdropping
If an autonomous system (AS) exists on both path segments from a client to entry relay and from exit relay to destination, such an AS can statistically correlate traffic on the entry and exit segments of the path and potentially infer the destination with which the client communicated. In 2012, LASTor proposed a method to predict a set of potential ASes on these two segments and then avoid choosing this path during path selection algorithm on client side. In this paper, they also improve latency by choosing shorter geographical paths between client and destination.
Exit node eavesdropping
In September 2007, Dan Egerstad, a Swedish security consultant, revealed he had intercepted usernames and passwords for e-mail accounts by operating and monitoring Tor exit nodes. As Tor cannot encrypt the traffic between an exit node and the target server, any exit node is in a position to capture traffic passing through it that does not use end-to-end encryption such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS). While this may not inherently breach the anonymity of the source, traffic intercepted in this way by self-selected third parties can expose information about the source in either or both of payload and protocol data.[96] Furthermore, Egerstad is circumspect about the possible subversion of Tor by intelligence agencies:
"If you actually look in to where these Tor nodes are hosted and how big they are, some of these nodes cost thousands of dollars each month just to host because they´re using lots of bandwidth, they´re heavy-duty servers and so on. Who would pay for this and be anonymous?"
In October 2011, a research team from ESIEA claimed to have discovered a way to compromise the Tor network by decrypting communication passing over it. The technique they describe requires creating a map of Tor network nodes, controlling one third of them, and then acquiring their encryption keys and algorithm seeds. Then, using these known keys and seeds, they claim the ability to decrypt two encryption layers out of three. They claim to break the third key by a statistical-based attack. In order to redirect Tor traffic to the nodes they controlled, they used a denial-of-service attack. A response to this claim has been published on the official Tor Blog stating these rumours of Tor´s compromise are greatly exaggerated.
Traffic-analysis attack
There are two methods of traffic-analysis attack, passive and active. In passive traffic-analysis method, the attacker extracts features from the traffic of a specific flow on one side of the network and looks for those features on the other side of the network. In active traffic-analysis method, the attacker alters the timings of the packets of a flow according to a specific pattern and looks for that pattern on the other side of the network; therefore, the attacker can link the flows in one side to the other side of the network and break the anonymity of it. It is shown, although timing noise is added to the packets, there are active traffic analysis methods robust against such a noise.
Steven J. Murdoch and George Danezis from University of Cambridge presented an article at the 2005 IEEE Symposium on security and privacy on traffic-analysis techniques that allow adversaries with only a partial view of the network to infer, which nodes are being used to relay the anonymous streams. These techniques greatly reduce the anonymity provided by Tor. Murdoch and Danezis have also shown that otherwise unrelated streams can be linked back to the same initiator. This attack, however, fails to reveal the identity of the original user. Murdoch has been working with and has been funded by Tor since 2006.
Tor exit node block
Operators of Internet sites have the ability to prevent traffic from Tor exit nodes or to offer reduced functionality to Tor users. For example, it is not generally possible to edit Wikipedia when using Tor or when using an IP address also used by a Tor exit node, due to the use of the TorBlock MediaWiki extension, unless an exemption is obtained. The BBC blocks the IP addresses of all known Tor guards and exit nodes from its iPlayer service - however relays and bridges are not blocked.
Bad apple attack
In March 2011, researchers with the Rocquencourt French Institute for Research in Computer Science and Automation (Institut national de recherche en informatique et en automatique, INRIA), documented an attack that is capable of revealing the IP addresses of BitTorrent users on the Tor network. The "bad apple attack" exploits Tor´s design and takes advantage of insecure application use to associate the simultaneous use of a secure application with the IP address of the Tor user in question. One method of attack depends on control of an exit node or hijacking tracker responses, while a secondary attack method is based in part on the statistical exploitation of distributed hash table tracking. According to the study:
The results presented in the bad apple attack research paper are based on an attack in the wild launched against the Tor network by the authors of the study. The attack targeted six exit nodes, lasted for twenty-three days, and revealed a total of 10,000 IP addresses of active Tor users. This study is significant because it is the first documented attack designed to target P2P file-sharing applications on Tor.[104] BitTorrent may generate as much as 40% of all traffic on Tor. Furthermore, the bad apple attack is effective against insecure use of any application over Tor, not just BitTorrent.
Some protocols expose IP addresses
Researchers from the French Institute for Research in Computer Science and Automation (INRIA) showed that the Tor dissimulation technique in BitTorrent can be bypassed by attackers controlling a Tor exit node. The study was conducted by monitoring six exit nodes for a period of twenty-three days. Researches used three attack vectors.
Inspection of BitTorrent control messages
Tracker announces and extension protocol handshakes may optionally contain client IP address. Analysis of collected data revealed that 35% and 33% of messages, respectively, contained addresses of clients.
Hijacking tracker´s responses
Due to lack of encryption or authentication in communication between tracker and peer, typical man-in-the-middle attacks allow attackers to determine peer IP addresses and even verify the distribution of content. Such attacks work when Tor is used only for tracker communication.
Exploiting distributed hash tables (DHT)
This attack exploits the fact that distributed hash table (DHT) connections through Tor are impossible, so an attacker is able to reveal a target´s IP address by looking it up in the DHT even if the target uses Tor to connect to other peers.
With this technique, researchers were able to identify other streams initiated by users, whose IP addresses were revealed.
Sniper attack
Jansen et al., describe a DDoS attack targeted at the Tor node software, as well as defenses against that attack and its variants. The attack works using a colluding client and server, and filling the queues of the exit node until the node runs out of memory, and hence can serve no other (genuine) clients. By attacking a significant proportion of the exit nodes this way, an attacker can degrade the network and increase the chance of targets using nodes controlled by the attacker.
Heartbleed bug
The Heartbleed OpenSSL bug disrupted the Tor network for several days in April 2014 while private keys were renewed. The Tor Project recommended Tor relay operators and hidden service operators revoke and generate fresh keys after patching OpenSSL, but noted Tor relays use two sets of keys and Tor´s multi-hop design minimizes the impact of exploiting a single relay.[108] 586 relays later found to be susceptible to the Heartbleed bug were taken off-line as a precautionary measure.
Relay early traffic confirmation attack
On 30 July 2014 the Tor Project issued a security advisory "´relay early´ traffic confirmation attack" in which the project discovered a group of relays that tried to deanonymize hidden service users and operators.[113] In summary, the attacking hidden service directory node changed the headers of cells being relayed tagging them as "relay" or "relay early" cells differently to encode additional information and sent them back to the requesting user/operator. If the user´s/operator´s guard/entry node was also part of the attacking relays, the attacking relays might be able to capture the IP address of the user/operator along with the hidden service information that the user/operator was requesting. The attacking relays were stable enough to achieve being designated as "suitable as hidden service directory" and "suitable as entry guard"; therefore, both the hidden service users and the hidden services might have used those relays as guards and hidden service directory nodes.
The project discovered that the attacking nodes joined the network early in the year on 30 January and the project removed them on 4 July.[ Although when the attack began was unclear, the project implied that between February and July, hidden service users´ and operators´ IP addresses might be exposed.
In the same advisory, the project mentioned the following mitigations for the attack besides removing the attacking relays from the network
patched relay software to prevent relays from relaying cells with "relay early" headers that were not intended
planned update for users´ proxy software so that they could inspect if they received "relay early" cells from the relays (as they are not supposed to), along with the settings to connect to just one guard node instead of selecting randomly from 3 to reduce the probability of connecting to an attacking relay
recommended that hidden services might want to change their locations
reminded users and hidden service operators that Tor could not prevent deanonymization if the attacker controlled or could listen to both ends of the Tor circuit, the class of attack that this attack belonged to
In November 2014 there was speculation in the aftermath of Operation Onymous, resulting in 17 arrests internationally, that a Tor weakness had been exploited. A representative of Europol was secretive about the method used, saying: "This is something we want to keep for ourselves. The way we do this, we can´t share with the whole world, because we want to do it again and again and again."A BBC source cited a "technical breakthrough"[33] that allowed the tracking of the physical locations of servers, and the number of sites that police initially claimed to have infiltrated led to speculation that a weakness in the Tor network had been exploited. This possibility was downplayed by Andrew Lewman, a representative of the Tor project, suggesting that execution of more traditional police work was more likely.
However, in November 2015 court documents on the matter[34] generated serious [34] aconcerns about security research ethics and the right of not being unreasonably searched guaranteed by the US Fourth Amendment. Moreover, the documents along with expert opinions may also show the connection between the network attack and the law enforcement operation including:
the search warrant for an administrator of Silkroad 2.0 indicated that from January 2014 until July, the FBI received information from "university-based research institute" with the information being "reliable IP addresses for TOR and hidden services such as SR2" that led to the identification of "at least another seventeen black markets on TOR" and "approximately 78 IP addresses that accessed a vendor .onion address." One of these IP addresses led to the arrest of the administrator
the chronology and nature of the attack fitted well with the operation
a senior researcher of International Computer Science Institute, part of University of California, Berkeley, said in an interview that the institute which worked with the FBI was "almost certainly" Carnegie Mellon University (CMU), and this concurred with the Tor Project´s assessment and with an earlier analysis of Edward Felten, a computer security professor at Princeton University, about researchers from CMU´s CERT/CC being involved
In his analysis published on 31 July, besides raising ethical issues, Felten also questioned the fulfilment of CERT/CC´s purposes which were to prevent attacks, inform the implementers of vulnerabilities, and eventually inform the public. Because in this case, CERT/CC´s staff did the opposite which was to carry out large-scale long-lasting attack, withhold vulnerability information from the implementers, and withhold the same information from the public.
CERT/CC is a non-profit, computer security research organization publicly funded through the US federal government.
Further information: CERT Coordination Center § Operation Onymous, and Operation Onymous § Tor 0-day exploit
Mouse fingerprinting
In March 2016 a security researcher based in Barcelona, demonstrated laboratory techniques using time measurement via JavaScript at the 1-millisecond level could potentially identify and correlate a user´s unique mouse movements provided the user has visited the same "fingerprinting" website with both the Tor browser and a regular browser.This proof of concept exploits the "time measurement via JavaScript" issue which has been an open ticket on the Tor Project for ten months.
Circuit fingerprinting attack
In 2015, the administrators of Agora, a darknet market, announced they were taking the site offline in response to a recently discovered security vulnerability in Tor. They did not say what the vulnerability was, but Wired speculated it was the "Circuit Fingerprinting Attack" presented at the Usenix security conference.
https://en.wikipedia.org/wiki/Tor_%28anonymity_network%29
TOR Good Exit Nodes, privacy-handbuch.de
IT-Sicherheitsforscher haben mehrfach nachgewiesen, dass es recht einfach möglich ist, mit schnüffelnden Exits Informationen über die Nutzer zu sammeln (D. Egerstad 2007, C. Castelluccia 2010). Man kann davon ausgehen, dass verschiedene Organisationen mit unterschiedlichen Interessen im Tor Netz nach Informationen phishen. Auch SSL-verschlüsselte Verbindungen sind nicht 100% geschützt. C. Soghoian und S. Stamm haben in einer wiss. Arbeit gezeigt, dass Geheimdienste wahrscheinlich in der Lage sind, gültige SSL-Zertifikate zu faken.
Als Verteidigung könnte man in der Tor-Konfiguration Exit Nodes angeben, denen man vertraut und ausschließlich diese Nodes als Exit-Nodes nutzen. Welche Nodes vertrauenswürdig sind, muss jeder Nutzer selbst entscheiden. Die folgende kurze Liste soll Anregungen zum Nachdenken liefern. Man sollte möglichst viele Tor Exit Nodes verwenden.
From the map it is clear to see the high concentration of Tor exit nodes within Europe, once you start to zoom in and see the European nodes it is clear there is quite a spread of locations where the Tor nodes are operating.
https://hackertarget.com/tor-exit-node-visualization/
Some Tor exit nodes attempt to spy on encrypted traffic
Computer scientists found almost 20 exit relays in the Tor anonymity network that attempted to spy on users encrypted traffic using man-in-the-middle techniques.
https://www.pcworld.com/article/2090400/some-tor-exit-nodes-attempt-to-spy-on-encrypted-traffic-researchers-find.html
Researchers find over 100 spying Tor nodes that attempt to compromise darknet sites
The lack of exit nodes means that if you run an exit node and want to spy on people, you can see an appreciable fraction of all the Tor traffic that goes to and from the public internet.
https://boingboing.net/2016/07/01/researchers-find-over-100-spyi.html
Rund 1.000 Exit Nodes gibt es derzeit weltweit, betrieben werden sie von Freiwilligen, ZEIT.de, 24.01.2014
.
22 dieser Exit Nodes aber tun genau das, wovor sich Tor-Nutzer schützen wollen - sie spionieren den Verkehr, der über sie läuft, aus. Laut Lindskog und Winter versuchen sie zu erkennen, welche Daten zwischen Nutzer und seinem Ziel hin- und hergeschickt werden. Das tun sie selbst dann, wenn die Verbindung zum Ziel per HTTPS verschlüsselt ist. In dem Fall versuchen die 22 Server, die Verschlüsselung mit speziellen Attacken aufzubrechen und aus einer gesicherten Verbindung eine ungesicherte zu machen. Unter bestimmten Umständen funktioniert so etwas.
Wer hinter den 22 Servern steckt, die größtenteils in Russland stehen, ist unklar. In den Zeiten des NSA-Skandals liegt es nahe, einen Geheimdienst zu verdächtigen, und tatsächlich gibt es diese Theorie schon seit Jahren. Philipp Winter glaubt nicht daran. "Organisationen wie die NSA haben Zugriff auf weite Teile der Internetinfrastruktur", sagte er Ars Technica, "sie haben es deshalb schlicht nicht nötig, Tor Exit Nodes zu betreiben." Ihr Zugriff auf die globale Infrastruktur erlaube es theoretisch, Tor-Nutzer mit statistischen Verfahren zu identifizieren. Winter glaubt vielmehr, "dass die Attacken überwiegend von Individuen kommen, die damit herumexperimentieren".
Was bedeutet die Untersuchung der beiden Schweden nun für Tor-Nutzer? Das versucht Winter in einem Blogpost beim Tor-Projekt zu erklären. Zunächst beruhigt er: Die Chance, einen der korrupten Ausgangsknoten zugeteilt zu bekommen, sei gering. Es gebe schließlich nur wenige von ihnen und zudem sucht die Tor-Software bevorzugt solche Austrittspunkte, die viel Bandbreite bereitstellen. Das treffe auf die gefährlichen Server aber nicht zu.
https://www.zeit.de/digital/datenschutz/2014-01/spionierende-exit-nodes-im-tor-netz-entdeckt/seite-2etrieben werden sie von Freiwilligen, ZEIT.de, 24.01.2014
.
22 dieser Exit Nodes aber tun genau das, wovor sich Tor-Nutzer schützen wollen - sie spionieren den Verkehr, der über sie läuft, aus. Laut Lindskog und Winter versuchen sie zu erkennen, welche Daten zwischen Nutzer und seinem Ziel hin- und hergeschickt werden. Das tun sie selbst dann, wenn die Verbindung zum Ziel per HTTPS verschlüsselt ist. In dem Fall versuchen die 22 Server, die Verschlüsselung mit speziellen Attacken aufzubrechen und aus einer gesicherten Verbindung eine ungesicherte zu machen. Unter bestimmten Umständen funktioniert so etwas.
Wer hinter den 22 Servern steckt, die größtenteils in Russland stehen, ist unklar. In den Zeiten des NSA-Skandals liegt es nahe, einen Geheimdienst zu verdächtigen, und tatsächlich gibt es diese Theorie schon seit Jahren. Philipp Winter glaubt nicht daran. "Organisationen wie die NSA haben Zugriff auf weite Teile der Internetinfrastruktur", sagte er Ars Technica, "sie haben es deshalb schlicht nicht nötig, Tor Exit Nodes zu betreiben." Ihr Zugriff auf die globale Infrastruktur erlaube es theoretisch, Tor-Nutzer mit statistischen Verfahren zu identifizieren. Winter glaubt vielmehr, "dass die Attacken überwiegend von Individuen kommen, die damit herumexperimentieren".
Was bedeutet die Untersuchung der beiden Schweden nun für Tor-Nutzer? Das versucht Winter in einem Blogpost beim Tor-Projekt zu erklären. Zunächst beruhigt er: Die Chance, einen der korrupten Ausgangsknoten zugeteilt zu bekommen, sei gering. Es gebe schließlich nur wenige von ihnen und zudem sucht die Tor-Software bevorzugt solche Austrittspunkte, die viel Bandbreite bereitstellen. Das treffe auf die gefährlichen Server aber nicht zu.
https://www.zeit.de/digital/datenschutz/2014-01/spionierende-exit-nodes-im-tor-netz-entdeckt/seite-2
Liste bekannter Tor Bad Exit Nodes (unvollständig), privacy-handbuch.de, Jahr 2016
1. Die folgenden Nodes wurde dabei erwischt, den Exit Traffic zu modifizieren, z.B Javascript in abgerufene Websites einzuschmuggeln. Dabei handelte es sich zumeist um Werbung oder Redirects auf andere Seiten.
2. Die folgenden Nodes wurden bei dem Versuch erwischt, SSL-Zertifikate zu fälschen, um den verschlüsselten Traffic mitlesen zu können:
3. Im Februar/März 2012 haben mehrere Exit-Nodes in einer konzertierten Aktion die HTTPS-Links in Webseiten durch HTTP-Links ersetzt. Wie man damit erfolgreich die SSL-Verschlüsselung ausgehebeln kann, wurde auf der Black Hack 2009 demonstriert. Die Software für diesen Angriff heisst "ssl-stripe" und ist als Open Source verfügbar.
4. Im Juli 2014 wurden 115 Tor-Nodes auf die schwarze Liste gesetzt, die mit einer Kombination von Traffic Confirmation Attack und Sybill Attack versuchten, Tor Hidden Services zu lokalisieren und Nutzer von Tor Hidden Services zu deanonymisieren. TorProject.org hat eine Warnung publiziert:
While we don´t know when they started doing the attack, users who operated or accessed hidden services from early February through July 4 should assume they were affected .... Hidden service operators should consider changing the location of their hidden service.
5. Möglicherweise wurden die von diesen Bad Nodes gesammelten Daten für die Operation Ononymous des FBI genutzt, um 410 illegale Tor Hidden Services abzuschalten, u.a. die Drogenmarktplätze Silk Road 2.0, Cloud 9, Hydra, Pandora, Blue Sky, Topix, Flugsvamp, Cannabis Road, und Black Market.
6. Im Oktober 2014 wurde ein Tor Exit Node aufgespürt, der Windows Binaries (z.B. DLLs oder EXE-Dateien) beim Download on-the-fly mit dem Trojaner OnionDuke infizierte, einer Variation der russischen Cyberwaffe MiniDuke. Der Trojaner sammelte Login Daten und spionierte die Netzwerkstruktur der Opfer aus. F-Secure konnten die ersten Infektionen mit OnionDuke auf Oktober 2013 datieren. Der Bad Exit Node wurde nur gefunden, weil ein Sicherheitsforscher gezielt nach diesem Angriff suchte.
Im April 2015 wurden 70 Bad Tor Nodes identifiziert, die den Hidden E-Mail Service SIGAINT angegriffen hatten. Die Betreiber von SIGAINT warnen, dass es den Angreifern gelungen ist, den Tor Hidden Service mit einem man-in-the-middle Angriff zu kompromittieren und Daten inklusive Login Credentials mitzulesen.
"I think we are being targeted by some agency here. That´s a lot of exit nodes."
Diese 70 Tor Nodes meldeten sich innerhalb eines Monats kurz vor dem Angriff als neue Tor Nodes im Netzwerk an. 31 weitere Nodes stehen noch in dem Verdacht, ebenfalls zu dieser Gruppe zu gehören, aber noch nicht aktiv angegriffen zu haben.
7. Um passiv schnüffelnde Tor Exit Nodes in eine Falle tappen zu lassen, hat Chloe im Juni 2015 einen Honigtopf aufgestellt und 11 passiv schnüffelnde Exit Nodes aufgespürt. Zwei der elf Nodes hatten Guard Status.
Im März 2016 haben 14 Bad Exit Nodes in einer konzertierten Aktion versucht, sich als man-in-the-middle in STARTTLS Verschlüsselung einiger Jabber/XMPP Server einzuschleichen. Folgende Jabber Server waren von dem Angriff betroffen:
8. Tor Exit Nodes aus dem Iran sind generell als Bad Exits markiert. Diese Nodes unterliegen der iranischen Zensur. Au&zslig;erdem wird beim Aufruf von Webseiten über diese Nodes von der staatlichen Firewall ein unsichtbarer IFrame aus dem Hidden Internet of Iran eingefügt.
9. Die Unterlagen des Whistleblowers E. Snowden haben bestätigt, dass NSA und GCHQ passiv schnüffelnde Exit-Nodes betreiben. Die NSA soll damals 10-12 leistungsfähige Tor-Server genutzt haben (aktuelle Angriffe zeigen, dass es inzwischen deutlich mehr sein müssen). Zum Engagement des GSHQ wurden keine Zahlen bekannt.
Europol betreibt seit Jahren ein Projekt mit dem Ziel "to provide operational intelligence related to TOR". Die Formulierung lässt vermuten, dass ebenfalls passiv schnüffelnde Exit-Nodes genutzt werden.
https://www.privacy-handbuch.de/handbuch_24j.htm
Man kann davon auszugehen, dass die Geheimdienste verschiedener Länder ebenfalls im Tor-Netz aktiv sind und sollte die Hinweise zur Sicherheit beachten: sensible Daten nur über SSL-verschlüsselte Verbindungen übertragen, SSL-Warnungen nicht einfach wegklicken, Cookies und Javascript deaktivieren… Dann ist Tor für anonyme Kommunikation geeignet.
https://almnet.de/privacy-handbuch/privacy-handbuch-html/handbuch_22a.htm
Four tips for anonymous surfing in the internet, PC-WELT.de, 01.11.2019
Sich Gedanken über die eigenen persönlichen Datenspuren im Internet zu machen, lohnt sich nicht erst, seitdem die NSA für Schlagzeilen sorgt. Wir stellen Strategien für mehr Webanonymität vor und zeigen deren Grenzen.
Bleiben Sie Herr über Ihre Daten und surfen Sie anonym im Internet.
Um unmittelbare Erfahrungen mit den Auswirkungen der Spurensammler im Internet zu machen, genügt eine einfache Shoppingtour. Jeder kennt die Werbebanner, die plötzlich Produkte anpreisen, über die man sich auf einer anderen Site informiert hat. Re-Targeting nennen das Marketing-Profis. Auch Dynamic Pricing ist ein gängiges Verfahren: Dabei wechselt der angezeigte Produktpreis nicht nur in Abhängigkeit der Nachfrage. Wenn Sie die Seite häufiger besuchen und als Besucher identifiziert werden, kommt Ihnen der Händler (vielleicht) entgegen. Wenn die Browser-Kennung den Nutzer als Besitzer eines Apple-Geräts verrät, wird hingegen gerne ein höherer Preis angezeigt, als wenn Sie mit dem Linux-Notebook surfen.
Die Auswertung der IP-Adresse ist nur ein Kennzeichen, über das Sie nachverfolgbar sind. E-Mails werden über Kaskaden von Servern versendet, bis sie den Empfänger erreichen. Jeder, der unterwegs eine E-Mail abfängt, kann deren Inhalt lesen, sofern sie nicht verschlüsselt wurde. Das gilt für Instant Messenger streng genommen genauso. Ohne Gegenmaßnahmen ist es mit der Privatsphäre im Internet nicht gut bestellt.
PC-WELT Anonym Surfen VPN
Das einfach zu bedienende VPN-Tool hindert Spione am Mitlesen Ihrer Mails & Surfspuren. Und es hebelt lästige Ländersperren aus.
1. Undurchschaubarer Datenverkehr mittels VPN-Tunnel
Cafés, Bäckereien, Warenhäuser locken die Kunden inzwischen mit kostenfreien WLAN-Zugängen. Gedanken an die Sicherheit dürften sich nur die wenigsten Nutzer machen. Dabei kann dieser Zugang kompromittiert sein und der Datenverkehr von einem Dritten mitgeschnitten werden. Wer nicht möchte, dass seine Datenpakete abgefangen und durchsucht werden können, setzt am besten einen VPN-Tunnel (Virtual Private Network) ein. Einen solchen Tunnel können Sie auch selbst, zum Beispiel mit Ihrem Raspberry, aufbauen.
Die Funktionsweise ist simpel, erfordert aber einige grundlegende Arbeiten. Auf dem kleinen Computer installieren Sie die Open-VPN-Software und richten diese ein. Über einen Anbieter für dynamische DNS-Einträge eröffnen Sie einen Zugang, der Anfragen an Ihren privaten Internetanschluss durchlässt. Schließlich muss der Router so eingestellt werden, dass externe Anfragen über den Port des VPN an den Raspberry weitergeleitet werden. Auf dem Computer, den Sie verwenden, müssen Sie dagegen nur einen VPN-Client installieren. Diese Programme gibt es für nahezu jedes Betriebssystem in kostenlosen Versionen. Unter Ubuntu kann der Network Manager entsprechend konfiguriert werden. Eine zusätzliche Software ist dort nicht notwendig.
Die Vorteile der Selbstbaulösung: Sie können sich auf Ihren eigenen Tunnel absolut verlassen, und der Datenverkehr kann nicht eingesehen werden. Der Nachteil: Die IP-Adresse wird nicht verschleiert und auch nicht permanent verändert. Sie hinterlassen also in den Angeboten, die Sie aufrufen, entsprechende Einträge. Kommerzielle Anbieter im Internet, die VPN-Zugänge anbieten, arbeiten prinzipiell nach dem gleichen Prinzip und bieten in aller Regel auch eine Verschleierung der IP-Adresse. Größter Nachteil: Sie müssen sich darauf verlassen, dass der Service Ihr Vertrauen nicht missbraucht und eventuell doch Daten weitergibt. Selbst Anbieter mit einem guten Ruf wie Ipredator müssen ja etwa die Zahlungsinformationen der Kunden über einen längeren Zeitraum aufbewahren.
Lesetipp: Mit diesen 3 Tipps schützen Sie Ihre Online-Privatsphäre
2. Mit Tor die IP-Adresse verschleiern und anonym bleiben
[...] Das Prinzip hat auch Nachteile: Je nach Auslastung wird die Surfgeschwindigkeit deutlich langsamer. Schon eine überlastete Zwischenstation kann bremsen. Und wie bei allen Netzwerken gilt auch hier, dass es nur so sicher sein kann, solange es nicht kompromittiert wird. Gelingt es Überwachungsstellen, einen Tor-Knoten zu überwachen, ist es nicht nur theoretisch möglich, einen Nutzer wieder zu de-anonymisieren.
Download-Tipp: Tor-Browser auch für Linux erhältlich
Im Zweifel sorgen die Nutzer selbst dafür, weil etwa Toolbars und Erweiterungen im Browser eingerichtet sind, die ihn identifizierbar machen. Beachten Sie ferner, dass die meisten Zwischenknoten im Tor-Netz durch Freiwillige bereitgestellt werden. Eine Kontrolle dieser Personen findet nicht statt. Auch Sie selbst können einen PC jederzeit als Vermittlungsknoten anbieten - etwa über Tails.
[...] Privoxy auf Raspberry: Ein alternativer Einstieg in die Nutzung von Tor, der recht einfach zu konfigurieren ist, besteht in der Nutzung eines Proxy-Servers, den Sie mit wenigen Kommandozeilen etwa auf einem Raspberry Pi installieren.
3. Mit Jondo die IP-Adresse verschleiern und anonym surfen
[...] Jondo können Sie zwar kostenfrei nutzen, müssen dann aber mit einer eingeschränkten Geschwindigkeit leben. Wer Speed braucht, muss kostenpflichtige Premiumpakete erwerben. Das günstigste Flat-Angebot für 8,33 Euro pro Monat ist auf zwei GB Datenvolumen limitiert.
[...] 4. E-Mail und Chats absichern
Die Verschleierung der IP-Adresse mit der Nutzung eines Services wie Tor oder Jondo verringert das Risiko, als Person identifiziert zu werden. Bei der Kommunikation per E-Mail oder Instant Messengern besteht nach wie vor das Risiko, dass die Botschaften abgefangen werden. Wer sichergehen möchte, dass die per Tastatur eingegebenen Passwörter oder TANs nicht von einem Keylogger ausgelesen werden, nutzt am besten eine Bildschirmtastatur. Tails bietet eine solche Tastatur direkt in seiner Menüleiste an. Außerdem ist in Tails ein Messenger enthalten, der das OTR-Protokoll (Off the record) unterstützt.
Das Verfahren ist so konzipiert, das zu einem späteren Zeitpunkt nicht mehr nachgewiesen werden kann, welche Person welchen Schlüssel verwendet hat.
https://www.pcwelt.de/ratgeber/Anonym-im-Netz-dank-VPN-und-Co-9903684.html
Wie viele TOR-Knoten daher inzwischen von Geheimdiensten und Polizei betrieben werden, bleibt im Dunkeln. Sind es genügend, lassen sich Teilnehmer durch die Daten von Entry- und Exit-Nodes auch wieder deanonymisieren (die US-Regierung ist einer der Hauptsponsoren des TOR-Netzwerks). Und nicht zuletzt garantieren Zwischenknoten keine absolute Anonymität: Die Rückverfolgung einer Ausgangs-IP über mehrere Knoten hinweg ist sehr aufwendig, aber nicht unmöglich.
https://www.pcwelt.de/ratgeber/Tails__Mit_Linux_unsichtbar_im_Internet_surfen-Unter_dem_Radar-8862001.html
Torservers.net ist eine (angeblich) vertrauenswürdige Organisation, die mehrere Exit-Nodes betreibt.
Die von der Swiss Privacy Foundation betriebenen Tor Nodes sind vertrauenswürdig.
Der CCC betreibt zur Zeit acht Tor Nodes (siehe Liste im Tor Atlas).
Der Tor Node Digitalcourage3ip1 wird vom Verein Digitalcourage e.V. betrieben.
Die Heinlein Support GmbH betreibt den Tor Node mailboxorg und empfiehlt die Konfiguration von MapAdresses in der torrc, so dass dieser Node als Exit Node für alle Mailbox.org Dienste genutzt wird.
bitte selbst erweitern
Bei der Auswahl der Server sollte man nicht einfach nach dem Namen im TorStatus gehen. Jeder Admin kann seinem Server einen beliebigen Namen geben und den Anschein einer vertrauenswürdigen Organisation erwecken. Die Identität des Betreibers sollte verifiziert werden, beispielsweise durch Veröffentlichung auf einer Website.
In der Tor Konfigurationsdatei "/etc/tor/torrc" bzw. für das TorBrowserBundle in der Datei "<TorBrowserBundleVerzeichnis>/Browser/TorBrowser/Data/Tor/torrc" kann man die gewünschten Exit Nodes mit folgenden Optionen konfigurieren:
Start tor together with Firefox:
su - surfuser
sg surfgroup "unshare firejail --nice=19 --profile=/etc/firejail/firefox.profile /usr/lib64/firefox/firefox --no-remote &" && sg surfgroup "unshare firejail --nice=19 --profile=/etc/firejail/tor.profile tor -f /home/surfuser/torrc" && export RESOLV_HOST_CONF="/etc/hosts"
Again, you can put this quit long command into the exec-line of a created quick launching symbol to get started by one mouseclick only.
Discretion: Read reports about any conjunctions of countries and relays to NSA & Co.!
Example from torstatus.blutmagie.de from 01.02.2019:
US thanksgoogle 0 0 53 d 78.176.198.35.bc.googleusercontent.com [35.198.176.78] Directory Server Stable Server Tor 0.3.4.9 on Linux 9001 None 2018-04-23 GOOGLE - Google LLC, US
Russia counts 230.000 Tor users every day and only 46 exit nodes. Tor is very popular there.
Check out all listed ExitNodes, before they get added in torrc: https://www.dan.me.uk/tornodes, https://torstatus.blutmagie.de/ and torservers.net, Freya,Vor,Tyr,Mani,Hlin,Forseti,Mimir,Eir,Fulla,Sif from torworld.org, a list of their name, their ip, their fingerprint, their nationality, their provider, their capacities and if they are good- or bad-nodes. Allow ExitNode {ch} for using ExitNodes DigiGesTor. This is already prevented by NodeFamily {ch},{ch}.
Alle ExitNodes nach Links von Zwiebelfreunde e.V., https://www.privacy-handbuch.de/handbuch_24n.htm und https://www.s-f-n.org/sicherheitshinweise/datenschutz/weltnetz/anonymitaet-im-weltnetz/tor-netzwerk/7.html außer ThankYouMrSnowden,EdSnowdenIsAHero, MyHeroEdSnowden,ForEdSnowden,AnonymousCluster1,F3Netze,PiratenparteiNRW,Piratenpartei,theOnionKnight01 (UNI Berlin), VS (UNI Duisburg-Essen),fluxe4 und gabelmoo (UNI Erlangen),torais (UNI Kassel),cn (UNI Düsseldorf), csUniHB (UNI Bremen), birnenpfeffimitzimt, onion, PrivacyRepublic0001 und PrivacyRepublick0002 von https://torstatus.blutmagie.de, DigiGesTor (Swiss Privacy Foundation) und Fingerprint-Adressen von https://www.privacy-handbuch.de/handbuch_24n.htm
Tor-Browser of Linux Tails (3.12, 3.13): kramse2, exit3, MYLEX, niftypika, dorrisdeebrown, ATZv5, SPECTRE, che, niftyeuropeanrabbit, MS3cTor528, Quintex35, cosimaniahouse, flowjob11,frantz, Hydra6,Jpsi2, MrTerence,weizenbaum2,weizenbaum3,cryptocrax0r,Thadassaexit4,cry,amartysen,onyx,argon,TheEpTicScal4s,giovanna,hers,RainerWinkler,MYLEX,che,SPECTRE,sofia
Weitere eingetragene ExitNodes: cherryjam: IN-BERLIN-AS Individual Network Berlin e.V., DE, F3Netze: Freifunknetz Berlin, weitere: DFN: fluxe4, tortoise, csUniHB, SevenLayers, thedoctor, torais, MarkTwain, gabelmoo, theOnionKnight01, theOnionKnight02, E10, onion: Verein zur Foerderung eines Deutschen Forschungsnetzes e.V., DE. Das DFN ist der deutsche Partner des internationalen Netzwerks Eduroam. Education Roaming (eduroam) ist eine Initiative, die Mitarbeitern und Studenten von partizipierenden Universitäten und Organisationen einen Internetzugang an den Standorten aller teilnehmenden Organisationen unter Verwendung ihres eigenen Benutzernamens und Passwortes oder eines persönlichen X.509-Nutzer-Zertifikates einer gültigen PKI über Wireless Local Area Network (WLAN) oder Local Area Network (LAN) ermöglichen will. Mitarbeitende und Studierende müssen bei Gastvorträgen, Auslandssemestern, Dienstreisen und ähnlichem an der Fremduniversität nicht erst einen Gastzugang beantragen, sondern können sich direkt mit ihren bekannten Daten einloggen. Mittlerweile sind fast alle europäischen Länder bei eduroam vertreten und immer mehr Universitäten der jeweiligen Länder schließen sich ihren Forschungsnetzen an. Inzwischen hat die Initiative weltweit viele Unterstützer, so im asiatisch-pazifischen Raum (z. B. Indien, Singapur), in Nord- und Südamerika (z. B. USA, Kanada, Brasilien), sowie im afrikanisch-arabischen Raum (z. B. Saudi-Arabien, Südafrika), DFN, Alexanderplatz 1 D - 10178 Berlin Germany
"We collect a wide range of Internet data and provide statistics and tools that our members and the wider Internet community can use for their own operations and analyses."
https://www.ripe.net/membership/indices/data/de.dfn.html
Beachte mit dem Editor die Wahrung der bereits hier möglicherweise verrutschten Zeilen (nur eine Zeile für ExitNodes mit den einzelnen ExitNodes)!
Die Option StrictExitNodes.gibt an, dass nur die im folgenden gelisteten Nodes als Exit verwendet werden dürfen. Für die Liste der Exits nutzt man die Fingerprints der Nodes, beginnend mit einem Dollar-Zeichen (ihre IP oder Server-Name). Die Fingerprints erhält man beim Tor Atlas.
https://www.privacy-handbuch.de/handbuch_24n.htm, replacement with "good" ExitNodes by Zwiebelfreunde e.V.. (http://torproject.org, https://www.torservers.net/partners.html und https://check.torproject.org/exit-addresses ) und https://www.privacy-handbuch.de/handbuch_24n.htm
To go sure, make up your own tor node, Golem.de
Tor selbst ist recht genügsam. Selbst die Leistung eines Kleinstrechners wie des Raspberry Pi reicht vollkommen aus, um einen Tor-Server als Entry-Node und -Relay zu betreiben.
https://www.golem.de/news/anonymisierung-zur-sicherheit-den-eigenen-tor-knoten-betreiben-1506-114438.html
In dependency from the provider (ISP) the usage of dynamic IPv4-addresses (IPv4-IP) only might be sufficient, red., Gooken.
The traffic is encrypted from your client to the exit node, so your ISP cannot see, what web sites you are accessing. On the exit node, the traffic is ... Tor (The Onion Router) is a free software project used to surf anonymously. It can be compared...
https://en.cship.org/wiki/Tor
 Even if Tor is used, do not forget to anonymize the useragent-UA-specification (browser´s user-agent-string)! Even if Tor is used, do not forget to anonymize the useragent-UA-specification (browser´s user-agent-string)!
Otherwise agencies like NSA are able to advise and collect them to the right place, as those specifications are very informative - similar to an IPv6-address.
We suggest those agents pregiven by Firefox-extensions for useragents. Most popular useragent-specifications without nums as ciphers like the default one from squid (out of squid.conf) or privoxy (out of default.action) provide high anonymisation with "Privoxy/1.0" as much as the popular "googlebot/1.0 resp. ".bzw. "Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)" out of many useragent-extensions for Firefox (our is named : "gookenbot/0.1" bzw.Gooken Bot: "Mozilla/5.0 (compatible; Gookenbot/0.1; +http://www.gooken.de)" ). There is a satisfying amount of such useragents provided by those extensions, one of them provides a downloadable lists to for extension. All these useragents up to right now are most anonymizing.
Top anonymizing: Privoxy/1.0
More (more or less) anonymizing useragents:
blanked: the empty string (no useragent set)
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:60.0) Gecko/20100101 Firefox/60.0
Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0)
Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)
Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)
Mozilla/4.0 (compatible; MSIE 9.0; Windows NT 6.1)
Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2)
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0)
Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0)
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; Trident/5.0)
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; Trident/5.0; Trident/5.0)
Mozilla/5.0 (Windows; U; Windows NT 6.1; rv:2.2) Gecko/20110201
Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.75.14 (KHTML, like Gecko) Version/7.0.3 Safari/7046A194A
More useragents can be find from http://useragentstring.com/pages/useragentstring.php/
https://developers.whatismybrowser.com/useragents/explore/
...
 Mini-IP-domain-mask /etc/hosts Mini-IP-domain-mask /etc/hosts
And past pdnsd, Tor-DNS, the anonymization by Tor and the anonymization of the browser-useragent-specification with useragents like "Privoxy/1.0" think of mentioned small DNS-IP-mask within /etc/hosts. This mask protects from remote-DNS-host-requests of IP to domain favorized (often addressed) websites, as so called anonymized DNS-requests can open up a lot of information to anywhere. This mask should be sized small, as some single IP-domain-pairs might change from time to time within addressroom IPv4, see our description (content listing) of /etc/hosts from above.
To use a bridge, you have two options. Tor Browser now provides some bridges by default. You can enable these easily. Unfortunately, because these bridges are publically distributed, it is easy for censors to block some of them, so some of them may not work. In this case, you´ll need to locate different bridges. Furthermore, you´ll need to configure Tor Browser with whichever bridge address you intend to use. If your Internet connection requires the use of a proxy, you´ll probably need to configure Tor Browser to use it first. If you don´t think you need to configure a proxy for your Internet connection, you probably don´t. Give it a try and if you have issues, ask us for help.
Pluggable Transports
Over the last few years, censors have found ways to block Tor even when clients are using bridges. They usually do this by installing special boxes at ISPs that peek into network traffic and detect Tor; when Tor is detected they block the traffic flow.
To circumvent such sophisticated censorship Tor introduced pluggable transports. These transports manipulate all Tor traffic between the client and its first hop such that it is not identifiable as a Tor connection. If the censor can´t decide if the connection is a Tor connection, then they are less likely to block it.
Sadly, pluggable transports are not immune to detection, if a censor is given enough time. In the past, we promoted obfs and obfs2 as safe transports. These are now deprecated and were replaced by obfs3, scramblesuit, fte, and obfs4.
Bridges which support pluggable transports can be used with Tor Browser easily. Tor Browser includes some pre-configured bridges and you can get more from BridgeDB, if those don´t work.
Here are your bridges for TOR:
obfs4 60.16.182.53:9001 cc8ca10a63aae8176a52ca5129ce816d011523f5
obfs4 87.237.118.139:444 0ed110497858f784dfd32d448dc8c0b93fee20ca
obfs4 60.63.97.221:443 daa5e435819275f88d695cb7fce73ed986878cf3
obfs4 141.201.27.48:420 4352e58420e68f5e40bf7c74faddccd9d1349413
Once you´ve received the email with bridge information, you can continue the configuration steps outlined above.
Running a Tor Bridge
If you want to help out, you should decide whether you want to run a normal Tor relay or a bridge relay. You can configure your bridge either manually or graphically:
manually edit your torrc file to be just these four lines:
SocksPort 0
ORPort auto
BridgeRelay 1
Exitpolicy reject *:*
When configured as a bridge, your server will not appear in the public Tor network.
Your bridge relay will automatically publish its address to the bridge authority, which will give it out via https or email as above. You can construct the bridge address using the format above (you can find the fingerprint in your Tor log files or in /var/lib/tor/fingerprint depending on your platform).
https://bridges.torproject.org
 Install Firefox-extensions listed above for the Tor-Browser (Firefox-ESR-52.9.0) too, although this was reported above as not recommended: SecretAgent (rotating user agent with many more security options, an extension from palemoon.org), AdblockPlus, Noscript, RequestPolicy(Block)Continued, RefControl, CookieController, SkipRedirect and FireGloves. Deactivate their check for updates, by setting this option to "no"! Install Firefox-extensions listed above for the Tor-Browser (Firefox-ESR-52.9.0) too, although this was reported above as not recommended: SecretAgent (rotating user agent with many more security options, an extension from palemoon.org), AdblockPlus, Noscript, RequestPolicy(Block)Continued, RefControl, CookieController, SkipRedirect and FireGloves. Deactivate their check for updates, by setting this option to "no"!
 IAt last, within Tor´s security settings, push the control from "standard" to "safest"! Because of the configuration of AdblockPlus from above, JavaScript can still be enabled, type "about:config" into the address-line and set "javascript.enabled" to true. IAt last, within Tor´s security settings, push the control from "standard" to "safest"! Because of the configuration of AdblockPlus from above, JavaScript can still be enabled, type "about:config" into the address-line and set "javascript.enabled" to true.
Tor Project - more links:
https://digitalcourage.de/support/tor
https://www.torproject.org/docs/tor-manual.html.en
https://wiki.ubuntuusers.de/Tor/Konfiguration/
https://kubieziel.de/blog/archives/627-torrc-Kontrolle-der-Verbindungen-zu-anderen-Torknoten.html
https://thesprawl.org/research/tor-control-protocol/#creating-really-fast-one-hop-circuits
https://wiki.ubuntuusers.de/Tor/Server/
https://motherboard.vice.com/de/article/8q8ym4/das-sind-die-menschen-die-in-deutschland-tor-server-betreiben-123
https://rstforums.com/forum/topic/102608-hardening-torrc/
https://www.torservers.net/partners.html
https://www.privacy-handbuch.de/handbuch_24n.htm: Good and Bad Exit Nodes
https://www.dan.me.uk/tornodes - über 7.000 Tor-Exit-Nodes nach ip|name|router-port|directory-port|flags|uptime|version|contactinfo
https://torstatus.blutmagie.de/ - All Tor-Exits! Liste mit über 2.000 Exit-Nodes aus verschiedenen Ländern sortiert nach Bandbreite. Seien Sie obigen Angaben nach vorsichtig mit dieser Liste!
https://appliedprivacy.net/don - weitere Exit Nodes von der Foundation for Applied Privacy
https://udger.com/resources/ip-list/tor_exit_node # daily List mit weiteren Exit-Nodes
https://tor.stackexchange.com/questions/103/is-it-possible-to-make-the-tor-onion-routing-path-longer - Erhöhung der Anzahl der Hops von (empfohlen) 3 auf 4, 5 oder über 5
https://hackertarget.com/tor-exit-node-visualization/
https://saveyourprivacy.net/tor
https://nos-oignons.net/Services/index.fr.html
 Anonymizing TorDNS-Server
Tor-Browser, TorMail, TorChat, ..., TorDNS: Anonymizing TorDNS-Server
Tor-Browser, TorMail, TorChat, ..., TorDNS:
Tor uses an own anonymising DNS-server.
We recommend to choose this TorDNS for the DNS for the complete computer-system beneath the local /etc/hosts. To use such TorDNS generelly, configure as follows:
 1) /etc/tor/torrc ( this is not Tor-Browser configuration file /home/toranonym/tor*/Browser*/Tor*/Data*/Tor*/torrc; tor is installed by rpm tor (el6) and rpm tor-socks (el6) ) 1) /etc/tor/torrc ( this is not Tor-Browser configuration file /home/toranonym/tor*/Browser*/Tor*/Data*/Tor*/torrc; tor is installed by rpm tor (el6) and rpm tor-socks (el6) )
# This file was generated by Tor; if you edit it, comments will not be preserved
# The old torrc file was renamed to torrc.orig.1 or similar, and Tor will ignore it
Sandbox 1
DNSPort 9053
ClientUseIPv4 1
ClientUseIPv6 0
AutomapHostsOnResolve 1
AutomapHostsSuffixes .exit,.onion
AvoidDiskWrites 1
DirReqStatistics 0
Log notice stdout
EnforceDistinctSubnets 0
UseEntryGuards 1
NumEntryGuards 7
TrackHostExitsExpire 1800
...
[...] Will man hingegen nur Tor direkt per DNSPort ohne installierte DNS-Proxys zur anonymisierten Namensauflösung nutzen (wovon wir an dieser Stelle abraten), verwendet man als DNSPort einfach:
DNSPort 127.0.0.1:53
... und 2) /etc/pdnsd.conf:
global {
perm_cache=99999999;
cache_dir="/var/cache/pdnsd";
server_port=53;
server_ip=127.0.0.1;
linkdown_kluge=off;
pid_file = /var/run/pdnsd.pid;
max_ttl=999999d;
min_ttl=99999d;
neg_ttl=99999d;
run_as=pdnsd;
strict_setuid=on;
paranoid=on;
status_ctl=on;
daemon=on;
verbosity=2;
query_method=udp_tcp;
run_ipv4=on;
debug=off;
proc_limit=15;
procq_limit=30;
tcp_qtimeout=30;
par_queries=1;
timeout=60;
randomize_recs=on;
query_port_start=1025;
query_port_end=65535;
use_nss=on;
udpbufsize=1024; # Upper limit on the size of UDP messages.
neg_rrs_pol=on;
par_queries=1;
}
server {
label = tor;
ip = 127.0.0.1;
port = 9053;
interface=eth0;
uptest = none;
timeout = 2s;
purge_cache = off;
caching = on;
edns_query=no;
lean_query = on;
preset = on;
proxy_only = on;
exclude = .meine-bank.de,googleapis.com;
policy = included;
}
source {
ttl=86400;
owner=localhost;
serve_aliases=on;
file="/etc/hosts";
}
/etc/resolv.conf
nameserver 127.0.0.1
In Linfw3 all DNS-Server can be removed from dialog -> nonyesno ->DNS-Server. But to prevent from allowing all DNS-Server, one DNS should still be entered like the pseudo-DNS 1.1.1.2.
Finally restart pdnsd by "sh /etc/init.d/pdnsd restart" (as a process started by the user psad) and start tor for user surfuser and group surfgroup ( su - surfuser && sg surfgroup tor -f /etc/tor/torrc ) - so have a good surf-time !
Source: Tor - ArchWiki - Arch Linux
TorDNS. The Tor 0.2.x series provides a built-in DNS forwarder. To enable it add the following lines to the Tor configuration file and restart the daemon:
/etc/tor/torrc DNSPort 9053 AutomapHostsOnResolve 1 AutomapHostsSuffixes .exit,.onion
wiki.archlinux.org/index.php/
 Start TorDNS with the start of any browser, for example palemoon and firefox (both additionally started by firejail and some options; notice that tor depending on the tor-version might already start its own sandbox too): Start TorDNS with the start of any browser, for example palemoon and firefox (both additionally started by firejail and some options; notice that tor depending on the tor-version might already start its own sandbox too):
su - surfuser
knemo && sg goonline "firejail --nice=19 --profile=/etc/firejail/palemoon.profile /usr/lib64/palemoon/palemoon --no-remote &" && sg goonline "firejail --nice=19 --profile=/etc/firejail/palemoon.profile tor -f /home/surfuser/torrc" && export RESOLV_HOST_CONF="/etc/hosts"
|
su - surfuser
sg surfgroup "unshare firejail --nice=19 --profile=/etc/firejail/firefox.profile /usr/lib64/firefox/firefox --no-remote &" && sg surfgroup "unshare firejail --nice=19 --profile=/etc/firejail/tor.profile tor -f /home/surfuser/torrc" && export RESOLV_HOST_CONF="/etc/hosts"
|
Eine anonymisierte DNS-Domain-IP-Abfrage mit TorDNS lässt sich übrigends auch manuall durchführen:
tor-resolve www.gooken.de
liefert
die IP von Gooken.
Die IP von Gooken kann man nun in /etc/hosts eintragen.
Eine solche anonymisierte remote DNS-Abfrage mit TorDNS bzw. manuell mit tor-resolve gelingt beim ersten Mal nicht immer sofort. Dann sollte man noch ein bi&szig;chen surfen, und es geht auf mal... ("kleiner Wackelkontakt" am Anfang?)
Alte TLS-Versionen werden ab 2026 von den großen Browsern nicht mehr unterstützt, PC-WELT.de, 16.10.2018
Microsoft, Mozilla, Google und Apple sind sich einig. Ab 2026 werden die alten TLS-Versionen nicht mehr unterstützt.
Mit der geplanten Einstellung der Unterstützung für die TLS-Versionen 1.0 und 1.1 im Jahr 2026 haben Webseiten-Betreiber also noch ausreichend Zeit, auf die neueren Versionen umzustellen. Die alten Versionen enthielten Sicherheitslücken, die bestimmte Angriffe erlaubten, dazu zählen der "Beast"- und "Sloth"-Angriff. Der "Sloth"-Angriff wurde beispielsweise durch die schwachen Hash-Funktionen wie MD5 und SHA1 möglich. Bei beiden Angriffen handelt es sich aber um theoretische Angriffe, in der Praxis werden diese kaum ausgeführt. Bereits heute laufen rund 94 Prozent aller Webseiten auf dem Protokoll der Version 1.2, Grund zur Sorge besteht also nicht. Die neue Version TLS 1.3 wird teilweise schon eingesetzt.
https://www.pcwelt.de/a/alte-tls-versionen-werden-ab-2026-von-den-grossen-browsern-nicht-mehr-unterstuetzt,3462573
Hintertüren vs. Trojaner
Europol prüft Möglichkeiten gegen Ende-zu-Ende-Verschlüsselung, netzpolitik.org, 13.02.2020
Das Bundeskriminalamt nutzt eine "Entschlüsselungsplattform" bei Europol, um auf verschlüsselte Datenträger zuzugreifen. Die Anlage gehört zu einem "Innovationslabor" und wird derzeit mit neuer Technik ausgestattet. Demnächst entscheidet die EU-Kommission, ob Europol auch die Entschlüsselung sicherer Verbindungen erledigen soll.
https://netzpolitik.org/2020/europol-prueft-moeglichkeiten-gegen-ende-zu-ende-verschluesselung/
 Wie alles anfing Wie alles anfing
Fünf Jahre Kampf gegen Ende-zu-Ende-Verschlüsselung, netzpolitik.org, 02.12.2020
Die Regierungen der EU-Mitgliedstaaten wollen ihre Polizeien und Geheimdienste befähigen, Ende-zu-Ende-verschlüsselte Kommunikation zu umgehen oder mit technischen Werkzeugen auszuhebeln. Ein Rückblick.
https://netzpolitik.org/2020/wie-alles-anfing-fuenf-jahre-kampf-gegen-ende-zu-ende-verschluesselung/
ePrivacy-Verordnung
EU-Staaten verspielen Chance auf Kompromiss, netzpolitik.org, 27.11.2020
Ein EU-Gesetz soll die Vertraulichkeit der Online-Kommunikation stärken. Doch die deutsche Ratspräsidentschaft blitzt mit einem Kompromissvorschlag ab. Die Reform könnte endgültig gescheitert sein.
https://netzpolitik.org/2020/eprivacy-verordnung-eu-staaten-verspielen-chance-auf-kompromiss/
ZITiS:
Hacker-government authority gets 66 millionen Euro, trojaner-info.de, 12.12.2020
ZITiS grows again and gets the double amount of money next year as 2019. That was decided by the coalition CDU/CSU/SPD together with the budgeting of the ministry of interior. This authority provides &eavesdropping and surveillance- technology like state trojans and supercomputer for the police and secret agencies.
https://netzpolitik.org/2020/zitis-hacker-behoerde-bekommt-66-millionen-euro/
Quantencomputer - Was kann er schon?:
Computertechnologie Ein Quantensprung für Deutschland?, tagesschau.de, 15.06.2021
In Ehningen bei Stuttgart wurde Europas erster Quantencomputer eingeweiht. Der ultraschnelle Rechner der Firma IBM soll der Wirtschaft helfen, im Wettstreit mit China und den USA zu bestehen.
Das "Wunderwerk der Technologie", wie Angela Merkel es nannte, ist wuchtig: Immerhin eine Grundfläche von drei mal drei Metern bei einer Höhe von drei Metern soll der Quantencomputer haben, den IBM zusammen mit der Fraunhofer-Gesellschaft am Dienstag in der Deutschland-Zentrale des IT-Konzerns in Ehningen bei Stuttgart der Öffentlichkeit präsentiert hat. Der laut IBM "leistungsstärkste Quantencomputer im industriellen Umfeld Europas" ist damit auch offiziell in Schwaben angekommen. Aufgestellt wurde er bereits letztes Jahr im November. Wegen der Pandemie konnte der Rechner erst heute eingeweiht werden.
Noch größer als der Computer sind die Erwartungen, die viele in die Anlage setzen: Einige Experten prognostizieren, dass von der Quantentechnik die nächste industrielle Revolution ausgeht. Dass Deutschland an vorderster Front dabei ist, wenn sie ausbricht, auch dafür soll der Quantencomputer sorgen.
Lieblingsprojekt der Kanzlerin
Der neue Rechner in Ehningen trägt den Namen "Quantum System One" - und gilt als eine Art Lieblingsprojekt Merkels. Bei der Eröffnung ließ sie sich immerhin live zuschalten. Sie hat das Projekt höchstselbst eingefädelt - am Rande des Weltwirtschaftsforums in Davos 2019, bei einem Gespräch mit IBM-Chefin Ginni Rometty. Im Herbst desselben Jahres kam die Zusage: Der Computer kommt nach Deutschland.
Bis Ende 2023 werden nun zunächst die Forscherinnen und Forscher von Fraunhofer die Anlage exklusiv nutzen. Fraunhofer-Präsident Reimund Neugebauer sagte, dass man Rechnerleistungen an Forschungseinrichtungen sowie Firmen in allen Größen vermieten wolle. Auch Unternehmen sollen sich deren Forschungsergebnisse zunutze machen.
Erst kürzlich hat sich in Deutschland eine Quantenallianz führender Konzerne auf dem Gebiet gegründet. An Bord sind unter anderem BASF, SAP und VW. Insgesamt sechs Projekte wurden inzwischen mit Partnern aus Wissenschaft und Industrie zur Erforschung der Quanten-Technologie, möglichen Anwendungsszenarien und Algorithmen gestartet. Der Rechner ist der erste, den der US-Konzern IBM außerhalb der USA zur Verfügung stellt.
Revolution der Computertechnik
Nachdem das Potenzial von Supercomputern weitgehend ausgereizt ist, gelten Quantencomputer als neuer Hoffnungsträger für Industrie und Forschung. Überall dort, wo größere Datenmengen anfallen, etwa bei der Simulation von Molekülen oder in der Medikamentenforschung mit ihren unzähligen Variablen, haben Quantencomputer die Nase vorn. Der Grund dafür liegt in ihrer besonderen Art der Informationsverarbeitung.
Ein normaler Computer rechnet in Bits. Diese können allerdings nur zwei Zustände annehmen, 1 oder 0. Die Rechenleistung, die damit erbracht werden kann, ist daher begrenzt. Quantencomputer rechnen dagegen mit Qubits, winzigen Quantenteilchen, beispielsweise Photonen oder Elektronen. Diese können - vereinfacht gesprochen - nicht nur abwechselnd die Zustände 1 oder 0 annehmen, sondern beide gleichzeitig. Das ermöglicht ihnen, viele Rechnungen parallel durchzuführen.
Deutschland Entwicklungsland beim Quantencomputing
Bislang tauchten Deutschland und Europa auf der Weltkarte des Quantencomputing praktisch nicht auf. Das zeigt nicht zuletzt die Tatsache, dass es erst einen US-Konzern brauchte, um den ersten kommerziellen Quantencomputer nach Europa zu holen. Die großen Player im Geschäft sitzen in den USA; insgesamt 13 etablierte Unternehmen arbeiten dort derzeit an Rechnern oder dazugehörige Software, darunter klingende Namen wie Google oder Microsoft. Auch China hat riesige Summen in die Technologie investiert.
Um den Rückstand der deutschen Wirtschaft aufzuholen, hat der Staat kräftig in die Tasche gegriffen: Für das System in Ehingen werden 40 Millionen Euro bereitgestellt, finanziert vom Bund und vom Land Baden-Württemberg. Es handele sich um eine Zukunftstechnologie, mit der etwa medizintechnische Durchbrüche erreicht und die Materialforschung revolutioniert werden könne, weil sehr komplexe Berechnungen durch die Schnelligkeit der Computer möglich würden, sagte die Kanzlerin. Die Bundesregierung wolle mit ihrer Förderung von zwei Milliarden Euro bis 2025 vor allem die marktnahe Entwicklung unterstützen. Zudem will Deutschland mit einem Firmen-Konsortium in den kommenden zwei Jahren einen eigenen Quantencomputer-Demonstrator entwickeln.
In Deutschland müsse man sich die Ergebnisse der Quantentechnologieforschung jetzt "möglichst schnell" auch wirtschaftlich zunutze machen, sagte Merkel. Heißt: Neue industrielle Anwendungsfälle für die Technik müssen her. Viele Einsatzmöglichkeiten der Quantenmechanik stecken nämlich bislang allenfalls im Forschungsstadium.
Quantentechnologie verbessert Krebsdiagnostik
Welches Potenzial die Technik hat, sieht man schon heute beim Start-up "NVision" in Ulm. 30 Mitarbeiterinnen und Mitarbeiter aus neun Nationen arbeiten hier. Sie eint das Wissen und die Neugier für Quantenphysik. Deren Prinzipien machen sie sich für neue Diagnoseverfahren zu nutzen, mit denen Krebserkrankungen besser und früher erkannt werden können. Dazu nutzen sie einen zuckerähnlichen Wirkstoff, der im Magnetresonanztomographen Krebszellen erkennbar macht.
"Wir machen Zucker sichtbar, indem wir Signale, die er aussendet, mit der Quantentechnologie zehntausendfach vergrößern." erklärt Ilia Schwartz, einer der Gründer von "NVision" und einer der renommiertesten Quantenwissenschaftlern überhaupt. Mit der neuen Technik könnten Tumordiagnosen bald ohne den Einsatz radioaktiver Kontrastmittel erfolgen. Und Ärztinnen und Ärzte bekämen tiefe Einblicke in erkranktes Gewebe wie nie zuvor: Tumore könnten früher erkannt werden, Erfolg oder Misserfolg von Therapien festgestellt werden.
Dass solche Erfolgsgeschichten der Quantentechnologie in Deutschland noch häufiger werden, auch dafür soll der neue Rechner sorgen. Allerdings ist auf dem Weg dorthin ein weiteres Problem zu beseitigen: Bislang mangelt es hierzulande an einer ausreichenden Zahl von Programmiererinnen und Programmierern, die das Potenzial der neuen Maschine ausnutzen können.
https://www.tagesschau.de/wirtschaft/technologie/quantencomputer-technologiestandort-deutschland-101.html
Erfolgreicher Test eines Medikaments, das den Krebs zerstört, uncut-news.ch, 01.06.2021
Gesundheit/Heilmethoden/Alternative Medizin/Ernährung
Forscher haben erfolgreich ein "Trojanisches Pferd"-Medikament getestet, das Krebs- und Bakterienzellen abtöten kann, ohne nahe gelegenes gesundes Gewebe zu schädigen.
Wissenschaftler der Universität Edinburgh kombinierten das winzige krebsabtötende Molekül SeNBD mit einer chemischen Nahrungsmittelverbindung, um bösartige Zellen dazu zu bringen, es zu sich zu nehmen.
[...] Krebszellen sind "gierig" und müssen hohe Mengen an Nahrung für Energie verbrauchen, und sie nehmen typischerweise mehr als gesunde Zellen auf, sagte die Universität von Edinburgh.
Durch die Kopplung von SeNBD mit einer chemischen Nahrungsmittelverbindung wird es zur "idealen Beute für schädliche Zellen", die es aufnehmen, "ohne auf seine toxische Natur aufmerksam gemacht zu werden".
Die Forscher der University of Edinburgh verglichen das Medikament mit einem Trojanischen Pferd und seine Wirkung mit einem "metabolischen Sprengkopf".
Die Ergebnisse sind in der Zeitschrift Nature Communications veröffentlicht.
Der leitende Forscher Professor Marc Vendrell, Lehrstuhl für translationale Chemie und Biomedizinische Bildgebung an der Universität Edinburgh, sagte:
"Diese Forschung stellt einen wichtigen Fortschritt bei der Entwicklung neuer Therapien dar, die einfach durch Lichtbestrahlung aktiviert werden können, was im Allgemeinen sehr sicher ist."
Er fuhr fort: "SeNBD ist einer der kleinsten Photosensibilisatoren, die je hergestellt wurden, und seine Verwendung als ‚trojanisches Pferd‘ eröffnet viele neue Möglichkeiten in der interventionellen Medizin, um schädliche Zellen abzutöten, ohne das umliegende gesunde Gewebe zu beeinträchtigen."
Quelle: Successful test of cancer-killing drug
https://uncutnews.ch/erfolgreicher-test-eines-medikaments-den-krebs-zerstoert/
Darmkrebs: Erste klinische Studie startet: Methadon wird als Krebsmittel untersucht, STERN.de, 28.10.2019
Kann Methadon Krebspatienten neue Hoffnung bieten? Nach kontroversen Debatten um das Mittel soll nun eine Therapiestudie zeigen, ob sich damit Tumore wirksam bekämpfen lassen - oder nicht.
https://www.stern.de/gesundheit/methadon-wird-als-krebsmittel-untersucht---klinische-studie-startet-8973910.html
...
Krebsforschung: Weltsensation wird zur Luftblase: Krebstest der Uniklinik Heidelberg existiert nicht, STERN.de, 30.05.2019
Von wegen marktreif. Der im Februar präsentierte Brustkrebstest des Uniklinikums Heidelberg existiert so gar nicht. Das ergab eine interne Untersuchung, deren Ergebnisse der "Süddeutschen Zeitung" vorliegen. Die Umstände der missglückten PR-Kampagne sind dubios.
https://www.stern.de/gesundheit/uniklinik-heidelberg-blamiert-sich--brustkrebstest-existiert-nicht-8730684.html
Supercomputer
Google feiert Durchbruch beim Quantencomputing, PC-WELT.de, 23.10.2019
In 200 Sekunden hat ein Quantencomputer eine Aufgabe gelöst, für die der schnellste Supercomputer über 10.000 Jahre bräuchte.
https://www.pcwelt.de/news/Google-feiert-Durchbruch-beim-Quantencomputing-10689669.html
 Weitere Studie belegt Lüge "anonymer" Daten, netzpolitik.org, 26.07.2019 Weitere Studie belegt Lüge "anonymer" Daten, netzpolitik.org, 26.07.2019
Anonyme Daten sind oft gar nicht wirklich anonym, in vielen Datensätzen können Einzelne auch ohne Namen eindeutig identifiziert werden. Mit welcher erstaunlicher Präzision das geht, verdeutlicht eine neue Studie. Viele Firmen und Datenbanken unterlaufen die Datenschutzgrundverordnung.
https://netzpolitik.org/2019/weitere-studie-belegt-luege-anonymer-daten/
 Pale Moon extension: Certificate Patrol Pale Moon extension: Certificate Patrol
"Welcome to Certificate Patrol 2.0. We introduced some improvements, that we should first explain to you.
Before we even list the details of a certificate, we first show you the certification hierarchy. That is the most important clue for oyou to find out, if you´re being tricked. An intermediate authority can put any text in the certificate, that you would like to see, but it cannot falsify the certificate checksums and its position in the hierarchy. Dangerous certificates are likely to be generated by a long list of authorities belonging to different companies or governments. Genuine ones are likely to be signed directly by a root certificate in your browser or by an intermediate creaated by the same company. All the inbetween cases are likely to be legitimate, but you can´t be sure. We are still taking guesses hsere because we steill don´t know, which root certificates in our browsers are worthy of trust. By keeping your eyes open and observing the patterns, you are a lot likelier to notice, when you are being attacked. In case of doubt, compare (by telephone) the checksums with somebody, that could not possibly be affected.
Another important change is, that we now inspect certificates for all parts of webpage, so you may see server names and domains comping up, that you never thourght youwere visiting, just because they host some Javascript or media files.
It´s also new, that you can reject all new certificate, when you see them.
That doesn´t mean, that you will be protected from using them, because we don´t have that much control over your browser.
If you don´t trust a site, you still have to close the window yourself. But it maens, that, if you bump into the same certificate again, you will be asked again. You could use this to see, if a certain website always has the same certificate, when you change internet connection. (like open it from work, then from home). Then again, if you store the certificate, you´re even safer, that the certificate is the same.
Several websites hat the bad habit of using multiple certificates for the same hostname. We consider it a configuration error on their side, but since they insist, you now have a little option of the certificate change pop-up to accept any certificate for the host as long as the issuer, that is the next higher level authority, stays the same. This should help in most cases, although I bet there are some, which are more misconfigured than that."
Überwachung
36 Millionen Euro: ZITiS baut Supercomputer zur Entschlüsselung, netzpolitik.org, 16.10.2018
Die Hacker-Behörde ZITiS will einen Hochleistungsrechner bauen, um verschlüsselte Daten zu entziffern. Das geht aus dem 36 Millionen Euro teuren Haushaltsentwurf der Behörde hervor, den wir veröffentlichen. Nach wie vor sucht ZITiS Staats-Hacker, aktuell ist nur die Hälfte der Stellen belegt.
Die IT-Behörde ZITiS soll nächstes Jahr 36,7 Millionen Euro bekommen, 20 Prozent mehr als dieses Jahr. Die vor anderthalb Jahren gegründete "Zentrale Stelle für IT im Sicherheitsbereich" hilft Polizei und Geheimdiensten bei der technischen Überwachung. Wir veröffentlichen an dieser Stelle das bisher unveröffentlichte ZITiS-Kapitel aus dem Bundeshaushalt sowie eingestufte Informationen aus dem Bundesinnenministerium.
Von diesem Geld wollen die staatlichen Hacker "hochmoderne technische Ausstattung" kaufen. Ganz oben auf der Wunschliste steht ein Hochleistungsrechner, "der vorrangig im Bereich der Kryptoanalyse genutzt wird" - also zur Entschlüsselung. Dieser Supercomputer hat "höchste Priorität" für die ZITiS-Abnehmer Verfassungsschutz, Bundeskriminalamt und Bundespolizei.
Vor zwei Wochen wurde bekannt, dass ZITiS auch einen Quantencomputer einsetzen will. Ob Supercomputer und Quantencomputer verschiedene Projekte sind, will ZITiS auf Anfrage nicht verraten: "Zu unseren Projekten und verwendeten Technologien können wir keine Auskunft geben." Da die Entwicklung nutzbarer Quantencomputer jedoch noch in den Kinderschuhen steckt, dürfte der Hochleistungsrechner ein eigenes Projekt sein, der zeitnah in Betrieb gehen soll.
Staatstrojaner für mobile Endgeräte
In den anderen Arbeitsfeldern rüstet ZITiS ebenfalls auf, wobei zwei besonderes Gewicht erhalten. Im Bereich der Digitalen Forensik forscht und entwickelt ZITiS unter anderem an "Passwortsuche" und der "Auswertung von Smartphones". Bisher haben Polizeibehörden sieben verschiedene Software-Tools gekauft, um beschlagnahmte Mobilgeräte auszulesen. Dieser Wildwuchs soll bei ZITiS vereinheitlicht werden.
Im Bereich Telekommunikationsüberwachung (TKÜ) arbeitet ZITiS an zwei Projekten, die bisher beim BKA angesiedelt waren. ZITiS setzt das "Projekt INTLI" (Internationale Zusammenarbeit in der TKÜ) fort, "das sich mit der Standardisierung des Austauschs von TKÜ-Daten auf Grundlage der Rahmenrichtlinie Europäische Ermittlungsanordnung beschäftigt". Die EU-Richtlinie ermöglicht grenzüberschreitende Überwachung von Telekommunikation.
ZITiS will auch die Entwicklung von Staatstrojanern vorantreiben. Mit dem "Projekt SMART" soll ZITiS das BKA unterstützen "bei der Entwicklung einer Quellen-TKÜ-Lösung für mobile Endgeräte", also einem Trojaner zum Abhören von Kommunikation. Das BKA hatte für sechs Millionen Euro den Staatstrojaner "RCIS" programmiert, der seit diesem Jahr auch Smartphones infizieren und abhören kann. Jetzt wollen ZITiS und BKA die Software gemeinsam weiterentwickeln.
Hacker gegen IT-Unsicherheitsbehörde
Insgesamt will ZITiS nächstes Jahr mehr als zehn Millionen Euro für Investitionen ausgeben, über elf Millionen sind für Personal geplant. Das Innenministerium bezeichnet die Personalgewinnung als "anspruchsvoll" und "eine zentrale Herausforderung". Vom Behördensprech übersetzt: Nur wenige IT-Experten wollen für den Staat hacken. Der BND nannte das mal "knappe Ressource brillantes Personal".
Derzeit hat ZITiS erst "74 der im Kalenderjahr 2018 zur Verfügung stehenden 150 Planstellen belegt". Fast die Hälfte der bisher eingestellten Mitarbeiter*innen ist in Verwaltung und Leitung tätig. Das existierende "MINT-Fachpersonal" arbeitet nicht nur in der Umsetzung der Aufgaben, sondern auch bei internen IT-Diensten und Beratung. Zwei Drittel der Angestellten kommen aus anderen Behörden, nur ein Drittel sind "Externe".
Falk Garbsch, Sprecher des Chaos Computer Clubs, kommentiert gegenüber netzpolitik.org:
Es ist gut zu sehen, dass Hacker offenbar keinerlei Interesse haben, für eine IT-Unsicherheitsbehörde zu arbeiten. Die Community hat schon vor vielen Jahren verstanden, was verbohrte Politiker nicht akzeptieren wollen: Das Ausnutzen und Offenhalten von Sicherheitslücken ist ein nachhaltiges Risiko für Unternehmen, kritische Infrastrukturen und Zivilgesellschaft. Statt Steuergelder in absurde Angriffsphantasien zu verschwenden, wird es Zeit für Investitionen in das konsequente Schließen von Sicherheitslücken.
Der Regierungsentwurf zum Bundeshaushalt 2019 wird derzeit im Bundestag verhandelt. Bisher hat die Große Koalition keine Änderungen bezüglich ZITiS beantragt oder beschlossen. Anträge der Opposition werden üblicherweise abgelehnt. Ende November soll der Haushalt im Bundestag verabschiedet werden.
Hier die Dokumente in Volltext:
Ministerium: Bundesministerium des Innern, für Bau und Heimat
Stand: 17. August 2018
...
https://netzpolitik.org/2018/36-millionen-euro-zitis-baut-supercomputer-zur-entschluesselung/
Supercomputer
Google feiert Durchbruch beim Quantencomputing, PC-WELT.de, 23.10.2019
In 200 Sekunden hat ein Quantencomputer eine Aufgabe gelöst, für die der schnellste Supercomputer über 10.000 Jahre bräuchte.
https://www.pcwelt.de/news/Google-feiert-Durchbruch-beim-Quantencomputing-10689669.html
 Weitere Studie belegt Lüge "anonymer" Daten, netzpolitik.org, 26.07.2019 Weitere Studie belegt Lüge "anonymer" Daten, netzpolitik.org, 26.07.2019
Anonyme Daten sind oft gar nicht wirklich anonym, in vielen Datensätzen können Einzelne auch ohne Namen eindeutig identifiziert werden. Mit welcher erstaunlicher Präzision das geht, verdeutlicht eine neue Studie. Viele Firmen und Datenbanken unterlaufen die Datenschutzgrundverordnung.
https://netzpolitik.org/2019/weitere-studie-belegt-luege-anonymer-daten/
Konsultation des BfDI
"Anonym" ist höchstens eine Momentaufnahme, netzpolitik.org, 16.02.2020
Ulrich Kelber sucht den Dialog. Erstmalig bitte der Bundesdatenschutzbeauftragte die Öffentlichkeit mit einer Konsultation um Stellungnahmen zum Thema Anonymisierung. Wir haben ihn gefragt, worum es bei dieser Dauerbaustelle des Datenschutzes geht und was er mit den Einsendungen anfängt.
https://netzpolitik.org/2020/anonym-ist-hoechstens-eine-momentaufnahme-kelber-bfdi-datenschutz-anonymisierung/
Anti-Terror-Koordinator
EU-Beamter fordert Gesetz gegen Verschlüsselung, netzpolitik.org, 15.05.2020
Die Europäische Union soll endlich ein Gesetz auf den Weg bringen, um den Trend unregulierter Verschlüsselung zu brechen. Das fordert der Anti-Terror-Koordinator in einem Brief, den wir veröffentlichen. Unterdessen gründen NGOs eine Globale Koalition für Verschlüsselung.
Seit 2007 ist der Belgier Gilles de Kerchove Anti-Terror-Koordinator der EU. In dieser Position fordert er immer wieder mehr Befugnisse für Polizei und Geheimdienste. Dass Internet-Anbieter auf die von Edward Snowden enthüllte staatliche Überwachung mit mehr Verschlüsselung reagierten, sieht er kritisch, spätestens seit 2015 fordert er verpflichtende Hintertüren.
Am Freitag erneuerte er seine Forderungen in einem Brief an die EU-Mitgliedsstaaten, den wir an dieser Stelle veröffentlichen: Strafverfolgung und rechtliche Aspekte der Verschlüsselung.
Trend unregulierter Verschlüsselung brechen
Kerchove will "den Trend der unregulierten Verschlüsselungspraxis brechen". Er bezeichnet "ungehinderte Verschlüsselung" in Anwendungen und Standards als "massive Herausforderung" für Polizei und Geheimdienste und fordert eine "robuste Antwort" der Politik: "Es ist Zeit, dass die EU in dieser Hinsicht tätig wird."
https://netzpolitik.org/2020/eu-beamter-fordert-gesetz-gegen-verschluesselung/
Coronavirus
Die Krise als Hebel für Überwachung und Kontrolle, netzpolitik.org, 26.03.2020
Weltweit bauen demokratische Staaten Grundrechte ab, um gegen das Coronavirus vorzugehen. Manchen Regierungen scheint das aber nur ein vordergründiges Anliegen zu sein. Leichtfertig abgesegnet könnten temporäre Maßnahmen zur Dauereinrichtung werden ...
https://netzpolitik.org/2020/die-krise-als-hebel-fuer-ueberwachung-und-kontrolle/
Tomas Rudl - 26.03.2020
Safer Internet Day
Auch hinter SSL-Verschlüsselung lauern Gefahren im Internet, 05.02.2019
https://www.it-daily.net/it-sicherheit/datenschutz/20512-auch-hinter-ssl-verschluesselung-lauern-gefahren-im-internet
Zeitungsbericht über CIA-Quellen: Noch mehr US-Spione in Ministerien?, Tagesschau, 13.07.2014
Der US-Geheimdienst CIA führt laut einem Zeitungsbericht mehr als ein Dutzend Mitarbeiter der Bundesregierung in Deutschland als Quellen. Im Visier seien dabei die vier Bundesministerien Verteidigung, Wirtschaft, Inneres und Entwicklung, berichtet die "Bild am Sonntag" unter Berufung auf US-Geheimdienstkreise. Viele der Spione würden schon jahrelang für den amerikanischen Auslandsgeheimdienst arbeiten. Aufgrund der jüngsten Enthüllungen über US-Spionage auf deutschem Boden gäbe es derzeit hierzulande aber keine Treffen zwischen den Spionen und der CIA. Darüber hinaus prüften die USA dem Bericht zufolge, ihre Agentenführer in die US-Botschaften nach Warschau und Prag zu verlegen. Am Donnerstag hatte die Bundesregierung den obersten CIA-Vertreter in Berlin aufgefordert, Deutschland zu verlassen. Begründet wurde der drastische Schritt mit den Ermittlungen gegen zwei mutmaßliche Spione der USA beim Bundesnachrichtendienst und im Verteidigungsministerium. Beide Fälle hängen nach Informationen von NDR, WDR und SZ zusammen.
Lobby-Drehtür: Google stellt in zehn Jahren 65 Regierungsvertreter aus EU-Staaten ein, netzpolitik.org, 06.06.2016
Das Google Transparency Project hat herausgefunden, dass in den letzten zehn Jahren 80 Personen sowohl bei EU-Regierungen wie auch bei Google angestellt waren. Google stellte im untersuchten Zeitraum 65 Regierungsvertreter ein, während 15 Google-Mitarbeiter in Regierungsdienste wechselten. Fünf Personen wechselten gar von der Regierung zu Google und dann zurück in Regierungsdienste,
https://netzpolitik.org/2016/lobby-drehtuer-google-stellt-in-zehn-jahren-65-eu-regierungsvertreter-ein/
Wochenrückblick KW 19
Überwachungswahnsinn abseits von Corona, netzpolitik.org, 08.05.2020
Die Polizei im Saarland will mehr überwachen dürfen - der norwegische Geheimdienst auch. Geflüchtete wollen gerichtlich durchsetzen, dass sie sich weniger überwachen lassen müssen, Gewerkschaften sollten das auch tun und wie Facebook und Twitter die Meinungsfreiheit ihrer Nutzer:innen überwachen, ist nicht so ganz demokratisch. Die Nachrichten der Woche im Überblick.
https://netzpolitik.org/2020/ueberwachungswahnsinn-abseits-von-corona/
Verräterische Cookies
Über Cookies bleiben Sie trotz anonymer IP identifizierbar. Deshalb deaktiviert Torbutton zum Surfen über Tor die bisher gesammelten Cookies.
Firefox fängt jedoch wieder an, alle ab diesem Moment in der von der IP-Adresse her anonymen Surfsession angefallenen Cookies zu sammeln.
Bitte beachten Sie deshalb trotz Nutzung des Torbuttons, dass Sie vor jedem Ansteuern einer Seite, auf der Sie sich einloggen sowie sofort nach jedem Ausloggen aus solchen Seiten im Firefox "Extras / Private Daten löschen" ausführen, bevor Sie weitersurfen!
Andernfalls könnte die vorherige und weitere über Tor durchgeführte Surfsession inkl. evtl. weiterer Logins, wenn auch nicht Ihrer IP-Adresse so doch dem oft personenbezogenen Login zugeordnet werden!
Ansonsten birgt auch der Flash-Player entsprechende Gefahren (Flash-Cookies), falls mensch nicht beim Surfen über Tor auf diesen verzichten will und deswegen beim Torbutton die temporäre Abschaltung von Erweiterungen und Plugins deaktiviert hat.
https://www.selbstdatenschutz.info/anonym/
And GOAL (TOOO...R) !
VPN via Tor
 If you want to surf free from eavesdropping, (beneath Tor) a VPN (Virtual Private Network, virtuelles privates Netzwerk) is a must. Such technique is used for example by companies, in order to provide staff members an access free from eavesdropping into the company net from home. A Virtual Private Network is seldom offered for free - except Opera´s built-in one. If you want to surf free from eavesdropping, (beneath Tor) a VPN (Virtual Private Network, virtuelles privates Netzwerk) is a must. Such technique is used for example by companies, in order to provide staff members an access free from eavesdropping into the company net from home. A Virtual Private Network is seldom offered for free - except Opera´s built-in one.
https://www.pcwelt.de/a/inkognito-modus-privatsphaere-beim-surfen-schuetzen,3450334
 https://saveyourprivacy.net/vpn-service: https://saveyourprivacy.net/vpn-service:
"Wir wollen so vielen Menschen wie möglich Zugang zu freiem unzensiertem Internet ermöglichen. Besonders wichtig ist uns, dass sich die Nutzer keine Sorgen machen müssen, ob jemand im Hintergrund alles protokolliert und aufzeichnet.
.
Deshalb bieten wir einen OpenVPN-Server an, der keine Protokolle über ihre Aktivitäten im Internet anlegt. Zudem wird eine vollständige Anonymität auch durch unseren Tor Exit-Node (saveyourprivacyexit) auf dem Server garantiert. Eine Unterscheidung zwischen Tor -und VPN-Traffic ist nicht möglich was eine Traffic-Analyse erheblich erschwert.
Da uns natürlich nicht nur die Anonymität unserer Nutzer wichtig ist, sondern auch die Sicherheit, verwenden wir sichere Verschlüsselung mit Perfect Forward Secrecy nach dem neuesten Stand der Technik. Wir fordern unsere Nutzer auf den Dienst nicht mit sinnlosem Unsinn (z.B. Spam-Versand) in Verruf zu bringen.
We are offering a free &anonymous VPN server to all who need to protect themselves against surveillance. There are no logs or blocked websites, nobody watches what you are doing. We couldn´t even do this because a large Tor exit node is running on the same server. But still, please don´t abuse it and ruin it for everybody!
Scroll down, download your config files and you are ready to go!
Technische Details:
OpenVPN-Server
Standort: Finnland
Port: 1194 (UDP), 8080 (TCP)
AES 256-bit Verschlüsselung
SHA512 Message Authentication mit einem 4096-bit (RSA) Key für eine sichere Authentifizierung.
Perfect Forward Secrecy mit stündlichem Re-keying.
Konfigurationdaten:
Download: Konfigurationsdateien für alle Betriebssysteme
Download: Konfigurationsdateien für alle Betriebssysteme (alles in einer Datei)
Download: Tor-Konfigurationsdateien für Windows
Download: Tor-Konfigurationsdateien für Windows (alles in einer Datei)
Download: Tor-Konfigurationsdateien für Android oder Linux
Download: Tor-Konfigurationsdateien für Android oder Linux (alles in einer Datei)
Bitte nutzt nicht die Tor-Konfigurationsdateien, wenn ihr euch nicht über das Tor-Netzwerk verbinden möchtet, da sonst eine Verbindung nicht möglich ist.
Risiken:
Bevor ihr die VPN nutzt, solltet ihr die Artikel DNS-Leaks gefährden VPN-Nutzer, Schutz vor IPv6-Leaks und WebRTC gefährdet VPN-Nutzer lesen und die Empfehlungen umsetzen, um einen wirklich anonym Internetzugang zu nutzen.
OpenVPN einrichten
VPN via Tor
Wenn Sie sich über Tor mit der VPN verbinden, ist es sehr schwer Sie als Nutzer der VPN zu identifizieren. Selbst Geheimdienste wie die NSA oder GCHQ sind nicht in der Lage, spezielle Tor-Nutzer zuverlässig zu deanonymisieren. So bietet Ihnen die Nutzung der VPN über das Tor-Netzwerk mehr Sicherheit und Privatsphäre. Wenn Sie sich über das Tor-Netzwerk zum VPN-Server verbinden möchten und Windows nutzen, müssen Sie sich lediglich die Tor-Konfigurationsdateien herunterladen und in den richtigen Ordner extrahieren. Anschließend laden Sie sich das Tor Browser Bundle hier herunter und installieren es. Sobald der Tor Browser startet, können Sie die VPN-Verbindung wie gewohnt starten.
Falls ihr Linux nutzt, müsst ihr folgende Einstellungen anpassen: Falls ihr Tor noch nicht installiert haben solltet, könnt ihr das schnell nachholen: "sudo apt-get install tor" (bzw. rpm -i --force tor_browser*.rpm). Vergessen Sie nicht nach den Änderungen den Tor-Service neuzustarten: "sudo service tor restart". In der Datei /etc/tor/torrc (bzw. /home/toruser1/tor_browser-en/Browser/Tor*/Data/Tor/torrc) fügt ihr die folgenden Zeilen hinzu:
SocksPort 9050
StrictNodes 1
EntryNodes splitDNA
DNSPort 53
In der Datei /etc/resolv.conf ändert ihr den Eintrag zu:
nameserver 127.0.0.1
In der Konfigurationsdatei saveyourprivacy.ovpn fügt ihr folgenden Eintrag hinzu:
route 62.210.82.44 255.255.255.255 net_gateway
In der Datei /etc/dhcpcd.conf fügt ihr folgenden Eintrag hinzu:
nohook resolv.conf
Wenn ihr jetzt die VPN-Verbindung aufbaut (siehe Linux), werden alle DNS-Anfragen und die VPN-Verbindung über das Tor-Netzwerk geleitet. Wir könnten somit nicht einmal sagen, wer unseren VPN-Service nutzt, da wir nur die IP-Adresse des Exit-Nodes sehen würden.
Auch auf Ihrem Smartphone könnt ihr mithilfe der App "Orbot" eine VPN-Verbindung über das Tor-Netzwerk aufbauen. Leider benötigt ihr eine aktuelle Version des Betriebssystems Android (>= 5). Installiert und startet die App "Orbot" und ladet die Tor-Konfigurationsdateien für Android herunter. Anschließend importiert die heruntergeladenen Konfigurationsdateien in der "OpenVPN für Android"-App. Danach bearbeitet ihr das importierte VPN-Profil (siehe Android) in der "OpenVPN für Android"-App indem ihr mit einem Klick auf den "Stift" neben dem VPN-Profilnamen (saveyourprivacy) das Konfigurationsmenü öffnet. Nun setzt bei der App "Orbot" ein Häkchen unter "Erlaubte Anwendungen" um der App den Internetzugriff an der VPN vorbei zu erlauben. Dies ist notwendig, da sonst eine VPN-Verbindung nicht möglich ist. Danach könnt ihr wie gewohnt eine VPN-Verbindung mit einem Klick auf den Profilnamen starten. Eure VPN-Verbindung wird jetzt durch das Tor-Netzwerk getunnelt und anonymisiert euch zusätzlich als VPN-Nutzer.
Eure OpenVPN-Verbindung läuft dann über einen sogennanten Tor-Circuit, der aus Entry, Middle -und Exit-Node besteht. Jeder Circuit hat eine "Lebensdauer" von zwei Stunden und akzeptiert nach dieser Zeit keine neuen Verbindungen mehr. Eure alte Verbindung läuft aber weiterhin über den eigentlich "toten" Circuit und benutzt so die gleiche Server-Kombination über den kompletten Zeitraum eurer Sitzung. Mit dem Einsatz erheblicher Ressourcen und einer Menge Zeit ist es möglich euch theoretisch zu deanonymisieren, deshalb solltet ihr bei einer längeren Nutzung die OpenVPN-Verbindung ab und zu (alle 1-2 Stunden) trennen und wieder neuaufbauen.
Linux
Installieren Sie OpenVPN: sudo apt-get install openvpn
Laden Sie die Konfigurationsdateien herunter: wget http://saveyourprivacy.net/SaveYourPrivacy-VPN.zip
Extrahieren Sie die Konfigurationsdateien: unzip SaveYourPrivacy-VPN.zip
Starten Sie OpenVPN: sudo openvpn --config saveyourprivacy.ovpn "
https://saveyourprivacy.net/vpn-service
OpenVPN ist kostenlos, gilt als hochgradig sicher, ist aber auch reichlich kompliziert: Während die Installation des Programms noch problemlos läuft (Windows-Nutzer werden hier die sogenannte GUI-Version vorziehen), ist der Erstaufbau eines VPN-Tunnels, die Konfiguration des eigenen virtuellen privaten Netzwerkes ein ziemlicher Akt. Man muss das regelrecht lernen: Während man die offiziellen Dokumentationen aus der Open-Source-Szene als Normal-User getrost vergessen kann, gibt es zum Glück aus der deutschsprachigen OpenVPN-Szene ein hinreichend verständliches Wiki: http://vpnforum.de/wiki/index.php/Hauptseite
Trotzdem gilt bei OpenVPN: Aller Anfang ist mühsam - allerdings muss man den Prozess der Netzwerkkonfiguration auch nur einmal durchlaufen. Markus Feilner und Norbert Graf bieten beim "Linux Magazin" http://www.linux-magazin.de/online_artikel/openvpn_fuer_windows_rechner eine Schritt-für-Schritt-Anleitung aller notwendigen Schritte, die zumindest fortgeschrittenen Nutzern weiterhelfen dürfte.
http://www.spiegel.de/netzwelt/tech/internet-tricks-gegen-zensur-und-ueberwachung-a-570421-4.html
tinc (rpm, deb) is a Virtual Private Network (VPN) daemon that uses tunnelling and encryption to create a secure private network between hosts on the Internet. Because the tunnel appears to the IP level network code as a normal network device, there is no need to adapt any existing software. This tunnelling allows VPN sites to share information with each other over the Internet without exposing any information to others.
How to Use a VPN and Tor together, bestvpn.com
It also provides protection against malicious Tor exit nodes, and allows you to evade censorship via blocks on Tor exit nodes. You should be aware, however, that if an adversary can compromise your VPN provider, then it controls one end of the Tor
https://www.bestvpn.com/guides/using-vpn-tor-together/
Welchen VPN-Dienst brauche ich? Anbieter im Vergleich, PC-WELT.de, 04.11.2019
VPN-Dienste bieten Schutz der Privatsphäre und mehr. Der Markt ist unübersichtlich, doch wir sorgen für Durchblick.
https://www.pcwelt.de/a/die-besten-vpn-dienste-2019-im-vergleich,3451061
VPN für mehr Schutz in offenen Netzen, netzpolitik.org, 30.04.2018
"VPN steht für Virtual Private Network. Mit einem VPN-Client lässt sich nicht nur weitgehend anonym surfen, sondern auch bei anderen Online-Aktivitäten die eigene Identität verschleiern. Das ist vor allem wichtig, wenn man in offenen WLANs unterwegs ist, wo der Betreiber den Datenverkehr mitüberwachen kann. VPN-Software leitet sämtlichen Verkehr zunächst vom eigenen Gerät verschlüsselt zum Server des Anbieters und von dort ins Netz. Auch kann man durch VPN-Server vorgeben, aus einem bestimmten Land zu sein, und dadurch Geoblocking umgehen.
Manche VPN-Anbieter versprechen ihren Nutzern, ihre Zugriffsdaten nicht zu speichern und dadurch ihre Anonymität zu wahren. Aber Obacht: Wenn der gesamte Internetverkehr durch einen VPN-Anbieter getunnelt wird, versetzt das diesen in eine besonders wichtige Lage und macht ihn zu einem attraktiven Ziel. Dass Anbieter von VPN-Diensten selbst nicht mitlesen, gilt bei weitem nicht für alle VPN-Anbieter, etwa den entsprechenden Dienst von Facebook. Auf keinen Fall sollte man daher Gratis-Lösungen nutzen. Im Umfeld von netzpolitik.org werden beispielsweise IPredator oder F-Secure verwendet. Am sichersten ist aber immer noch, den VPN über einen eigenen Server zu betreiben.
Staaten wie China, Russland und der Iran schränken die Nutzung von VPN-Diensten stark ein. Das sollte man vor einem Reiseantritt bedenken. Auch gilt es bei der Verwendung von VPN-Diensten und Tor-Browsern zu bedenken: Sobald man sich im Browser irgendwo einloggt, ist es - zumindest gegenüber dem verwendeten Dienst - vorbei mit der Anonymität."
https://netzpolitik.org/2018/kleines-einmaleins-der-digitalen-selbstverteidigung/
Zenmate: Ihr sicherer und kostenloser Tunnel ins Internet, PC-WELT.de, 09.12.2018
Die Browser-Erweiterung Zenmate für Chrome, Firefox und Opera ist ein genial einfaches Tool für eine sichere Verbindung ins Internet. Es baut nach einer einfachen Installation und Anmeldung eine verschlüsselte Verbindung zum VPN-Server von Zenmate im Internet auf. So kann niemand auf dem Weg dorthin mitlesen, was Sie im Internet anstellen. Da sich Browser-Erweiterungen ohne Administratorrechte installieren lassen, lässt sich das Zenmate-Plug-in auch auf einem Arbeitsplatz-PC installieren, auf dem Sie sonst keine Tools aufspielen können. Dank VPN-Verbindung kann dann selbst die IT-Abteilung Ihrer Firma Ihre Websiten-Zugriffe nicht mehr mitloggen.
Die Browser-Erweiterung Zenmate lässt sich dauerhaft kostenlos nutzen, wenn auch nur mit eingeschränkter Leistung. Alternativ gibt es Zenmate auch als VPN-Client für Windows , der nicht nur den Browser unterstützt.
https://www.pcwelt.de/a/22-effektive-sicherheitstools-fuer-jeden-bereich,3386884
Achtung!
Der Betreiber einer Exit-Node als solcher ist nicht anonym. Dadurch kann es vorkommen, dass, wenn jemand anderes Unsinn über Tor macht, die Polizei dann bei einem nachfragt bzw. man beschuldigt wird, dass man selbst die Straftat begangen hat. Auch Beschlagnahmung von Tor-Servern gab es bereits in Deutschland.
[...] Es wurde in Deutschland auch noch nie ein Betreiber einer Exit-Node verurteilt (aber mittlerweile in Österreich - wegen Beihilfe zur Verbreitung von Kinderpornographie). Daher sollte man im Zweifelsfall unbedingt einen Anwalt hinzuziehen; auf den dadurch entstehenden Kosten wird man vermutlich sitzen bleiben, wenn man keine Rechtsschutzversicherung hat.
https://forum.chip.de/discussion/1872336/tor-exit-node-betrieb-in-deutschland
Zwiebelfreunde: Polizei durchsucht Räume von Tor-Aktivisten, golem.de, 04.07.2018
Aufgrund einer vagen Verbindung durch eine E-Mail-Adresse hat die Polizei Wohnungen und Vereinsräume von Mitgliedern des Vereins Zwiebelfreunde durchsucht. Doch den Betroffenen wird nichts vorgeworfen, sie gelten lediglich als Zeugen.
Die Zwiebel ist das Symbol des Tor-Netzwerks.
Polizeibeamte haben Vereinsräume des Zwiebelfreunde e. V. und die Wohnungen von dessen Vorstandsmitgliedern in Berlin, Dresden, Augsburg und Jena sowie einen Augsburger Hackerspace durchsucht. Laut einem Bericht des Spiegel ordnete die Generalstaatsanwaltschaft München die Durchsuchungen am 20. Juni an, um die Urheber eines Blogs zu finden. Diese hatten dazu aufgerufen, den AfD-Parteitag in Augsburg zu stören, der am vergangenen Wochenende stattfand.
Eine direkte Verbindung zwischen dem Verein Zwiebelfreunde und der Website existiert nicht. Die Zwiebelfreunde haben sich der Förderung des Anonymisierungsnetzwerks Tor verschrieben, betreiben selbst Tor-Server und sind Ansprechpartner für Projekte, Presse und Behörden. Die Generalstaatsanwaltschaft sah jedoch einen indirekten Zusammenhang: Auf dem Anti-AfD-Blog war eine E-Mail-Adresse des Tech-Kollektivs Riseup als Kontakt angegeben. Die Zwiebelfreunde verwalten Spendengelder für die Gruppe, die unter anderem E-Mail-Accounts für linke Aktivisten und Gruppen anbietet.
Den Betroffenen wird nichts vorgeworfen
Der Mitgründer von Zwiebelfreunde, Moritz Bartl, sagte dem Spiegel, die von der Durchsuchung betroffenen Personen gelten nicht als Beschuldigte, sondern als Zeugen. Die Ermittlungsbeamten hätten gegenüber Bartl angegeben, dass sie die Blogbetreiber ermitteln wollten. Dafür hätten sie sowohl Vereinsgeräte und -dokumente als auch persönliche Gegenstände Familienangehöriger und Eigentum von Bartls Firma beschlagnahmt. Es sei ihm unmöglich, weiter seiner Arbeit nachzugehen.
Im Interview mit Netzpolitik.org berichtete Jens Kubieziel, laut dem Durchsuchungsbeschluss seien die Behörden davon ausgegangen, Nutzerdaten in den Wohnungen zu finden. Er ist einer der Vorstände der Zwiebelfreunde und war selbst von den Polizeimaßnahmen betroffen. Dabei sei klar gewesen, dass diese nicht bei ihm lagerten: "Schon ein einfacher Anruf oder Besuch eines Polizisten hätte die Lage schnell aufklären können", sagte Kubieziel. Seine Frau erwähnte, die Polizisten hätten ihr nahegelegt, dass Kubieziel als Vorstand zurücktreten solle - sonst könne eine weitere Hausdurchsuchung drohen.
Polizei interpretiert typisches Hackerspace-Inventar als Sprengstoffzutaten
Bei der Durchsuchung des Augsburger Hackerspaces Openlab hatten die Polizeibeamten Gegenstände gefunden, die ihnen verdächtig vorkamen: Chemikalien, chemische Formeln an einer Tafel und ein bombenförmiges Plastikspielzeug. Derartige Gegenstände lassen sich wohl in zahlreichen Hacker- und Makerspaces finden, doch für die Ermittler genügte das, um Bartl und andere Anwesende festzunehmen und eines geplanten Sprengstoffanschlags zu beschuldigen. Es stellte sich heraus, dass die Gegenstände für das Ätzen von Platinen und 3D-Druck gedacht waren. Das hatten die Betroffenen nach eigenen Angaben bereits währenddessen versucht zu erklären.
Im Openlab ist auch der Augsburger Ableger des Chaos Computer Club beheimatet. In einer Mitteilung verurteilte der CCC die Maßnahmen der Polizei: "Sowohl die initiale Verdachtsgewinnung gegen die Vorstände der Zwiebelfreunde als auch die nachfolgende Verdächtigung in Richtung Sprengstoff sind entweder inkompetent oder böswillig." Wenn das als Verdachtsmoment ausreiche, müsse "bald jeder Schüler sein Chemiebuch gut vor den Augen neugieriger Polizisten verstecken".
Der CCC kündigte außerdem an, dass in der kommenden Folge des Podcasts Logbuch:Netzpolitik einer der Betroffenen über den Vorfall berichten wird. Die Folge erscheint am 6. Juli
https://www.golem.de/news/zwiebelfreunde-polizei-durchsucht-raeume-von-tor-aktivisten-1807-135310.html
Invisible Internet Project (I2P): Die Alternative zu TOR, PC-WELT.de, 31.01.2018
Das "Invisible Internet Project" arbeitet, anders als TOR, nach dem Peer-to-Peer-Prinzip, um ein alternatives Internet aufzubauen.
https://www.pcwelt.de/a/invisible-internet-project-i2p-die-alternative-zu-tor,3449599
Details about Tor and I2P, wiki.kairaven.de, 2018
Block Cloudflare MiTM Attack, https://wiki.kairaven.de/open/anon/netzwerk/anet
Seite 1
Nicht anonym im Internet • Anonym und abgesichert im Internet • Anon-Netiquette
Seite 2
Tor und das Tor Netzwerk • Aufbau von Tor Tunnels • Transport über Tor Tunnel
Seite 3
Nicht anonyme Namensauflösung • Anonymisierte Namensauflösung über Tor • Das SOCKS Protokoll • Internetanwendungen mit SOCKS • SOCKS Wrapper und Proxy • DNS-Proxys • manuelle Namensauflösung • Kontrolle mit Paket-Sniffer
Seite 4
Tor installieren und starten • Mailinglisten • Projekte rund um Tor • Tor Browser • Tor Kontrolle • Arm • Vidalia
Seite 5
Tor mit der torrc konfigurieren • Tor als Onion Proxy • Tor als Onion Router • Bridges • Transport-Module
Seite 6
Tor Onion Dienste • Einrichtung von Tor Onion Diensten • Aufbau der Verbindungen mit und der Nutzung von Tor Onion Diensten
Seite 7
Privoxy Proxy • Installation und Start • Konfiguration • Weiterleitungen • Aktionen • Filter
Seite 8
I2P - das Invisible Internet Project • Installation • Konfiguration • Adressbücher und SusiDNS
Seite 9
I2P Einsatz - Standard-Anwendungen • E-Mails per Postman • Mailkonto einrichten und konfigurieren • E-Mails mit SusiMail • E-Mails mit Thunderbird
Seite 10
I2P Einsatz - Standard-Anwendungen • Datenaustausch mit I2Psnark • I2Psnark konfigurieren • Torrent erstellen und veröffentlichen • Torrent herunterladen
Seite 11
I2P Einsatz - Standard-Anwendungen • Eepsite Homepage • I2P-Webserver Servertunnel konfigurieren • Erweiterte Eepsite Netzwerkoptionen • I2P Einsatz - Plugins • Plugins &externe Anwendungen • Plugins installieren &nutzen
https://wiki.kairaven.de/open/anon/netzwerk/anet
 Damit UNIX/Linux alles in allem gut und stabil läuft, kann man noch versuchen, wer weiß wieviele Libraries z.B. von PCLinuxOS (pclos) einzuspielen, auch mehrfach vorhandene unterschiedlicher Versionen, indem zugehörige Pakete unter rpm einfach mit der Option -i statt -u installiert werden. Damit wappnet sich Linux und läuft umso zukunftsicherer. Damit UNIX/Linux alles in allem gut und stabil läuft, kann man noch versuchen, wer weiß wieviele Libraries z.B. von PCLinuxOS (pclos) einzuspielen, auch mehrfach vorhandene unterschiedlicher Versionen, indem zugehörige Pakete unter rpm einfach mit der Option -i statt -u installiert werden. Damit wappnet sich Linux und läuft umso zukunftsicherer.
 Now it´s the time to think about installing more libraries than required like those from PCLinuxOS (pclos). There are some of the same name, but different version. You can install many of them by rpm with option -i instead of option -u. This makes UNIX/Linux even more a good, stable platform. Now it´s the time to think about installing more libraries than required like those from PCLinuxOS (pclos). There are some of the same name, but different version. You can install many of them by rpm with option -i instead of option -u. This makes UNIX/Linux even more a good, stable platform.
 Finally please check all your browser with iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) for unwanted connections, best in mode for reverse IP lookup, so that all domain are shown within the first field. Block them with Linfw3 by adding belonging IP into the TCP-IP-blacklist, eventually together with their subnetmask (for example subnetmask 255.255.255.0 stands for 24, so add blacklist-ip/24 ! Following our exurs, anonymizing TorDNS (Entry node of /etc/tor/torrc, if set) is used for the remote-host-DNS, so do not cut belonging IP out. The second field below the first one for TCP-connections should be always empty. Finally please check all your browser with iptraf (iptraf-ng(rosa2016.1, rosae2014.1)) for unwanted connections, best in mode for reverse IP lookup, so that all domain are shown within the first field. Block them with Linfw3 by adding belonging IP into the TCP-IP-blacklist, eventually together with their subnetmask (for example subnetmask 255.255.255.0 stands for 24, so add blacklist-ip/24 ! Following our exurs, anonymizing TorDNS (Entry node of /etc/tor/torrc, if set) is used for the remote-host-DNS, so do not cut belonging IP out. The second field below the first one for TCP-connections should be always empty.
Applying this, the IP-blacklist for TCP-INPUT (in Linfw3 also for TCP-OUTPUT) for browser Firefox-52.9 (ESR, slack, el6) and Pale Moon (28.2.x) anyway consists of the following IP:
/usr/local/LINFW3/LINFW3.sh
blacklistINPUT="94.130.73.100/24 91.219.237.244/24 222.228.15.51/24 51.15.228.222/24 94.16.116.137/24 128.31.0.34/24 78.46.103.30/24 52.24.88.25/24 95.101.81.120/24 95.216.143.200/24 192.34.67.51/24 141.255.166.142/16 91.221.119.33/24 81.17.30.48/24 217.147.214.107/24 179.43.169.21/24 188.116.11.162/24 86.59.21.38 185.77.129.35 88.70.204.23/24 163.172.43.101/24 217.182.196.65/16 192.168.1.1 5.9.43.211/24 188.102.2.34/24 109.70.100.6/24 195.154.237.170/24 163.172.21.117 79.137.112.5/24 74.208.236.142 52.52.181.175 92.222.39.183 163.172.21.117 178.10.0.0/16 103.224.182.244 217.160.0.57 31.3.242.58 217.70.184.38 188.40.0.0/16 88.77.94.143/24 54.69.55.68/24 151.101.0.133/24 151.101.128.133/24 151.101.112.133/24 151.101.0.133/16 94.221.75.168/24 185.93.238.11/24 93.184.220.29/24 146.60.190.246/24 185.93.238.72/24 192.168.178.0 169.254.0.0/16 224.0.0.1 255.255.255.255 0.0.0.0 146.60.93.115/16 224.0.0.1"
In the list there are IP for firefox-extensions trying to build-up connections (ABP, first IP of the list).
What´s up now?
Did you decide to use the secure "telescoped" tor-proxy (Tor, Tor-Browser or also named the Onion Router) free from secret agencies eavesdropping by building up connections through a once more anonymizing and protecting VPN (for example see https://www.saveyourprivacy.net with an own AGB, also providing Tor two exits (exit nodes) saveyourpivacyex1 and saveyourprivacyexit )? Laymen might still not trust it, where some experts like from above already swear for it...
Trojaner-info namely reinforces VPN once again...:
 Anonym und getarnt im Tunnel: VPN Gateways, trojaner-info.de, 18.11.2018 Anonym und getarnt im Tunnel: VPN Gateways, trojaner-info.de, 18.11.2018
Einen höheren Schutz der Privatsphäre als Proxies versprechen VPN Lösungen.
Sie gibt es als Freeware, aber auch zumeist als Premium-Version.
Anonym und getarnt im Tunnel: VPN Gateways
https://www.trojaner-info.de/sicher-anonym-im-internet/anonymisierungs-dienste/articles/Anonyme-VPN-Gateways.html
Tor-Proxy - Your Fritz!Box as a magic hat router, 26.05.2015
With Fritz!Box-extension Freetz Fritz!Box is brought into the stealth-mode. Die Tor-Erweiterung erlaubt es bei Bedarf den gesamten ausgehenden Weltnetzverkehr über das anonyme Tor-Netzwerk zu leiten. Das Tor-Netzwerk leitet alle Anfragen - von Weltnetzseiten-Aufrufen und Suchanfragen bis hin zu Downloads - über drei verschiedene Server weltweit und versteckt damit deine IP-Adresse.
Der Clou: Das Tor-Plugin leistet das alles direkt im Router: Jeder Computer und jedes Smartphone können somit mit wenigen Handgriffen anonym im Weltnetz surfen.
Wer eine modifizierte Firmware mit seiner Fritz!Box verwendet, verliert die Gewährleistung des Herstellers. Im Test mit Freetz traten bei uns zwar keine Probleme auf, es kann aber vorkommen, dass etwa nach dem Flashen der Firmware die Fritz!Box nicht mehr erreichbar ist.
https://www.s-f-n.org/sicherheitshinweise/datenschutz/weltnetz/anonymitaet-im-weltnetz/tor-netzwerk/tarnkappen-router/
OnionMail (Tor network, E-mail)
Website: https://onionmail.info/
OnionMail is a mail service which uses the Tor network, it provides 100% encryption to all E-mails by "not" using the traditional SMTP servers to send/receive mails and instead by routing the mails via the Tor network.
It also makes use of "Asymmetric keys" for dual protection, in addition to advanced level spam detection and filtration in the mailboxes.
What´s best is it also lets you select your server entry and exit nodes if you understand them.
Considering it uses the onion network, there´s no doubt of it being off-the-grid, and secure, especially from the govt. censorship and regulations.
Here´s a Detailed list of Anonymous and private E-mail service providers!
https://www.deepwebsiteslinks.com/best-privacy-tools/
OnionShare (Tor network, File-sharing)
Website: https://onionshare.org/
Onionshare is a file-sharing platform, available for Windows, Linux, MacOS, Ubuntu, Fedora and every other Linux distro.
The working infrastructure is what makes it unique, anonymous and highly trust worthy.
When a file is shared, it creates a temporary web server, on the Tor network, and gives you a random, long URL which is like a "download link" for your file.
Note that your computer acts as the "host" for the download link so you don´t have to trust any third-party service to host your files and the files are never actually "uploaded" online.
Also, you don´t have to share your name, email or anything else with the receiver hence keeping your identity a secret.
It even has a "stealth mode" which protects the URL against hidden Tor nodes which may try to gain access to the file. Not to mention that the files are encrypted end to end so yes they can´t be intercepted no matter what.
https://www.deepwebsiteslinks.com/best-privacy-tools/
Tor Messenger
trac.torproject.org/projects/tor/wiki/doc/TorMessenger
On 29 October 2015, the Tor Project released Tor Messenger Beta, an instant messaging program based on Instantbird with Tor and OTR built in and used by default. Like Pidgin and Adium, Tor Messenger supports multiple different instant messaging protocols; however, it accomplishes this without relying on libpurple, implementing all chat protocols in the memory-safe language JavaScript instead.
In April 2018, the Tor Project shut down the messenger project because the developers of Instantbird discontinued support for their own software.
Third-party applications for Tor
Vuze (formerly Azureus) BitTorrent client, Bitmessage anonymous messaging system and TorChat instant messenger include Tor support.
The Guardian Project is actively developing a free and open-source suite of applications and firmware for the Android operating system to improve the security of mobile communications. The applications include ChatSecure instant messaging client, Orbot Tor implementation, Orweb (discontinued) privacy-enhanced mobile browser, Orfox, the mobile counterpart of the Tor Browser, ProxyMob Firefox add-on and ObscuraCam.
https://en.m.wikipedia.org/wiki/Tor_(anonymity_network)
Back in text to presented "Universal Linux" having performed suggested operations marked by hooks we notice by the following article, that -as we wrote in the introduction from this side high above - there is also no need for any maintenance (and hardware/-disk scan) anymore, same for updates, where there is almost probably no need for updating el6 etc. past year 2026:
Small ABC of Linux-System maintenance, PC-WELT.de, 03.12.2018
Komprimierter Ratgeber: Die wichtigsten Pflichten auf dem Linux-Desktop und Homeserver.
https://www.pcwelt.de/ratgeber/Server-Administration_-_Tipps_fuer_mehr_Sicherheit-Loechrige_Server-8716223.html
KDE 4
Smartphones: Access through MTP with KDE
Wer ein Smartphone oder Tablet mit Android an einen Linux-PC per USB anschließt, bekommt erst mal keinen Zugriff auf die dort gespeicherten Dateien. Denn Android nutzt schon seit Version 3.x für den Dateiaustausch das Protokoll MTP (Media Transfer Protocol), das sich nicht als gewöhnliches USB-Speichermedium am System anmeldet. Linux kann daher nicht ohne Hilfsmittel auf diese Datenträger zugreifen.
https://www.pcwelt.de/ratgeber/Tipps_und_Tricks_zum_Linux-Desktop_-Linux-7979095.html
Installation kio-mtp (mga5)
Linux-Smartphones
Software::Mobilgeräte
Neues Smartphone mit Plasma Mobile angekündigt, PRO LINUX, 01.12.2018
Das KDE-Projekt kündigt zusammen mit dem finnischen Hersteller Necuno Solutions ein neues Smartphone mit Plasma Mobile an.
Necuno mit Plasma Mobile
Necuno Solutions ist ein in der Open-Source-Szene verwurzelter Hersteller von Smartphones für Unternehmen. Deren in der Entwicklung befindliches Smartphone hat laut Firmenphilosophie einen hohen Anspruch an Sicherheit und Schutz der Privatsphäre. So sollen etwa notwendige Firmware-Blobs keinerlei Zugriff auf den Speicher haben.
Um auch die Gemeinschaft zu involvieren, hat das Unternehmen nun zusammen mit KDE bekannt gegeben, eine Version des Smartphones Necuno Mobile mit Plasma Mobile auszustatten. Bisher sind noch nicht allzu viele Informationen verfügbar. Das Gerät im Formfaktor 5,5 Zoll soll einen Aluminiumkorpus bekommen und neben den üblichen Tasten zum An- und Ausschalten und für die Lautstärkerregelung auch eine individuell belegbare Taste haben.
Als SoC kommt der NXP i.MX6 Quad, ein ARM Cortex-A9-Chip zum Einsatz, die Vivante-GPU soll den freien OpenGL-Treiber Etnaviv verwenden. Leider setzt Necuno hier auf den älteren MX6-SoC und nicht wie Purism beim Librem 5 auf den neuen MX8.
Als Kernel ist Linux 4.20 LTS vorgesehen. WLAN soll per SDIO-Karte realisiert werden und neben Ethernet wird auch LTE verfügbar sein. Darüber hinaus erwähnt das Datenblatt lediglich eine Audiobuchse, Micro-USB sowie Mikrofon und Lautsprecher. Eine Kamera wird ebensowenig erwähnt wie die Menge an Hauptspeicher.
Damit wird neben dem Librem 5 von Purism derzeit ein zweites möglichst freies Smartphone entwickelt. Liegt beim Purism der Fokus auf dem hauseigenen PureOS mit Plasma Mobile als Alternative, so spielt KDE beim Necuno Mobile die erste Geige. Beide Geräte sind wichtig für die weitere Entwicklung von Plasma Mobile. So sagte denn auch Bushan Sha, einer der Plasma-Mobile-Entwickler, in der Ankündigung: "Es ist wichtig, dass Entwickler innerhalb des mobilen Ökosystems mit offenen Geräten arbeiten können, die leicht zu modifizieren und zu optimieren sind und nicht von Anbietern an ein bestimmtes Betriebssystem gebunden sind. Necuno Solutions arbeitet an einem solchen Gerät und wird letztendlich dazu beitragen, Plasma Mobile aufgrund seiner offenen Natur zu verbessern.
https://www.pro-linux.de/news/1/26552/neues-smartphone-mit-plasma-mobile-angek%C3%BCndigt.html
Linux auf Samsung Galaxy-Smartphones, Pro-Linux, 19.10.2017
Samsung hat angekündigt, dass es bald möglich sein wird, Linux auf den Smartphones Galaxy Note 8, S8 und S8+ zu betreiben.
https://www.pro-linux.de/news/1/25254/linux-auf-samsung-galaxy-smartphones.html
"Geräte, die Sicherheit und Privatsphäre zur Priorität machen, widersprechen dem Interesse der meisten Hersteller"
Software::Mobilgeräte
KDE verkündet Zusammenarbeit mit Purism für offenes Smartphone, Pro-Linux, 14.09.2017
Purism und KDE haben angekündigt, beim geplanten offenen und sicheren Smartphone Librem 5 zusammenzuarbeiten. Plasma Mobile von KDE soll als alternatives Betriebssystem für das Gerät entwickelt werden.
Plasma Mobile auf dem Purism Librem 5
KDE entwickelt seit einiger Zeit Plasma Mobile als vollständig freies Betriebssystem für Mobilgeräte. Dabei bildet das Android Open Source Project (AOSP) die Basis, während ein an die mobilen Verhältnisse angepasstes KDE Plasma die grafische Oberfläche stellt und viele bekannte KDE- und andere Anwendungen lauffähig sind. Plasma Mobile auf Geräte zu bringen, ist allerdings kein leichtes Unterfangen. Bei einigen heute erhältlichen Geräten ist es möglich, jedoch fehlen dann meist einige Treiber, die proprietär sind, und es ist nicht möglich, den vollen Funktionsumfang zu nutzen.
Geräte, die Sicherheit und Privatsphäre zur Priorität machen, widersprechen dem Interesse der meisten Hersteller, wären für die Benutzer allerdings dringend angebracht. Deshalb hatte die Firma Purism vor drei Wochen einen Plan verkündet, das offene Linux-Smartphone Librem 5 zu entwickeln. Purism ist ein in San Francisco, USA, ansässiges Unternehmen, das sich den Prinzipien der freien Software verschrieben hat und als Unternehmen registriert ist, das soziale Ziele höher bewertet als Gewinne. Das erste Produkt von Purism war das Notebook Notebook Librem 13, das durch eine Crowdfunding-Kampagne finanziert wurde, die über eine Million US-Dollar erbrachte. Seit einem halben Jahr ist dieses Notebook, das versucht, moderne Technik mit möglichst viel Freiheit zu verbinden, mit Coreboot statt BIOS ausgestattet.
Das Smartphone Librem 5 soll in einer Kampagne, die zwei Monate andauert, mit 1,5 Mio. US-Dollar finanziert werden. Die Kampagne läuft auf dem eigenen Online-Shop von Purism statt bei Crowdfunding-Anbietern. Während verschieden hohe Beträge zur Unterstützung des Vorhabens möglich sind, ist der niedrigste Preis, um in den Besitz eines Librem 5 zu kommen, 599 US-Dollar. Bisher hat die Kampagne allerdings erst ein Fünftel des erstrebten Betrags eingebracht.
Das Librem 5 soll Sicherheit und Privatsphäre maximieren. Es ist dafür ausgelegt, dass viele Linux-Distributionen darauf laufen können, primär soll jedoch das eigene PureOS zum Einsatz kommen, das auf Debian beruht, komplett auf proprietäre Software, Treiber und Firmware verzichtet und auch die Anwendungen mit Bedacht wählt. Durch die jetzt verkündete Zusammenarbeit mit KDE wird das KDE-Projekt vollen Zugang zu den Spezifikationen erhalten. Daraus kann eine vollwertige oder bessere freie Alternative zu PureOS entstehen.
Das Librem 5 wird mit einem 5-Zoll-Display nicht gerade klein und es soll sich mit einem externen Monitor, Tastatur und Maus in ein Arbeitsplatzsystem verwandeln lassen. Die geplante Hardware, die sich noch ändern kann, umfasst eine i.MX6/i.MX8 CPU, eine Vivante GPU mit Etnaviv-Treiber, 3 GB RAM, 32 GB eMCC, einen MicroSD-Slot, zwei Kameras, 3,5-mm-Anschlüsse für Mikrofon und Kopfhörer, WLAN, Bluetooth 4, interne Debugging-Schnittstellen, USB Host, USB Type-C, GPS, Sensoren wie Beschleunigungsmesser, Gyroskop, Kompass, Helligkeits- und Näherungssensoren und Hardware-Schalter für Kamera, Mikrofon, Baseband, WLAN und Bluetooth.
Details können erst im Verlauf der Entwicklung genannt werden. Die Auslieferung von Entwicklerboards soll Mitte 2018 beginnen, die der kompletten Geräte im Januar 2019.
https://www.pro-linux.de/news/1/25152/kde-verkündet-zusammenarbeit-mit-purism-für-offenes-smartphone.html
Software::Security, Linux-Smartphone
Librem 5 erreicht über 2 Millionen US-Dollar, Pro Linux, 24.10.2017
Die Schwarmfinanzierung für das Linux-Smartphone der Firma Purism ging mit Zusagen für über 2 Millionen US-Dollar zu Ende.
KDE
Auch wenn es zu Beginn der Kampagne nicht so aussah und viele Stimmen dem Projekt den Erfolg bereits damals absprachen: Das Librem 5 wird gebaut. Das Geld dazu kommt von rund 3.000 Unterstützern, die zusammen über zwei Millionen US-Dollar oder rund 140 Prozent der anvisierten 1,5 Millionen US-Dollar zusagten. Diese Summe, die zum Erfolg der Kampagne mindestens nötig war, wurde bereits am 10. Oktober, zwei Wochen vor dem Ende der Kampagne erreicht.
Interessierte können sich auch weiterhin für ein Developer Kit für 299 US-Dollar, ein komplettes Librem 5 für 599 US-Dollar oder für eine der anderen Optionen in Kombination mit externen Displays entscheiden. Der Stand am heutigen Morgen weist über 2.131.000 US-Dollar aus und wächst weiter.
[...] Nun geht es zunächst darum, die Hardware weiter einzugrenzen, mit der das Librem 5 ausgeliefert werden wird. Die bisherigen Tests mit Prototypen-Mainboards wurden hauptsächlich mit der i.MX-6-CPU der Firma NXP durchgeführt. Das Ziel ist es, im fertigen Produkt den Nachfolger i.MX-8 einzusetzen, da der i.MX-6 bereits jetzt veraltet ist. Das Problem ist hier jedoch, dass der freie Etnaviv-Treiber für den Vivante-Grafikchip im i.MX-8 noch nicht fertig ist.
In rund einem Monat will Purism zudem bekanntgeben, welche Bedienoberfläche auf dem hauseigenen Betriebssystem PureOS für das Librem 5 entwickelt wird. Sowohl KDE als auch Gnome haben ihre Mitarbeit zugesagt.
https://www.pro-linux.de/news/1/25267/librem-5-erreicht-über-2-millionen-us-dollar.html
Purism startet Finanzierungskampagne für Linux-Smartphone, Pro-Linux, 25.08.2017
Die Firma Purism plant ein Smartphone zu entwickeln, das Sicherheit und Privatsphäre zur Priorität erhebt. FÜr das "Librem 5" wurde jetzt eine Crowdfunding-Kampagne gestartet, bei der man bereits...
https://www.pro-linux.de/news/1/25084/purism-startet-finanzierungskampagne-für-linux-smartphone.html
Software::Mobilgeräte
LineageOS 16 in Arbeit, PRO LINUX, 01.12.2018
LineageOS, eine Android-Modifikation mit Fokus auf Software-Freiheit und Datenschutz, hat die Arbeit an Version 16.0 begonnen, die Android 9 "Pie" entspricht.
LineageOS war Ende 2016 aus der Asche von Cyanogenmod hervorgegangen, das bis zu diesem Zeitpunkt eine der populärsten Android-Abwandlungen war. Cyanogenmod musste eingestellt werden, nachdem sich die Firma hinter dem Projekt finanziell übernommen hatte und einige erhoffte Geschäfte nicht zustande kamen. LineageOS dürfte inzwischen eine große Beliebtheit als Android-Alternative erlangt haben, insbesondere bei Benutzern, die aus Datenschutzgründen auf alle Google-Apps verzichten wollen.
https://www.pro-linux.de/news/1/26554/lineageos-16-in-arbeit.html
Malware: Jedes dritte Handy infiziert, trojaner-info.de, 12.11.2018
SIM-Karten-Sperre und Lokalisierungsfunktion sind häufigste Schutzmaßnahmen.
Gelöschte Daten, exzessive Werbung oder verschlüsselte Geräte: Schadprogramme auf Smartphones sind für viele Nutzer ein Problem. Mehr als jeder dritte Smartphone-Nutzer (35 Prozent) wurde in den vergangenen 12 Monaten Opfer von bösartiger Software. Das ist das Ergebnis einer repräsentativen Umfrage im Auftrag des Digitalverbands Bitkom unter 1.021 Smartphone-Nutzern in Deutschland.
Infektionsquelle Apps
[...] Dazu erklärt Susanne Dehmel, Mitglied der Bitkom-Geschäftsleitung:
"Bösartige Software versteckt sich häufig in scheinbar harmlosen Apps"
"Bei der Installation dieser Apps infiziert sie dann automatisch das Smartphone."
Sicherheitsmaßnahmen der Nutzer
Um das eigene Smartphone zu schützen, setzen Verbraucher auf unterschiedliche Sicherheitsmaßnahmen:
Drei Viertel (76 Prozent) haben einen SIM-Karten-Schutz aktiviert, der das Smartphone sperrt, sobald die SIM-Karte entfernt wird.
Über die Hälfte (53 Prozent) hat eine Lokalisierungsfunktion aktiviert, mit der ein verlorenes Gerät wieder aufgespürt werden kann.
Vier von zehn Nutzern (40 Prozent) haben ein Virenschutzprogramm installiert
gut ein Drittel (34 Prozent) erstellt regelmäßig Backups der Smartphone-Daten in der Cloud oder auf dem privaten Computer.
Nur 3 Prozent nutzen überhaupt keine Sicherheitsdienste.
Um den Smartphone-Bildschirm zu sperren, setzen viele mittlerweile auf biometrische Daten: Per Fingerabdruck sichert gut ein Drittel (35 Prozent) den Handy-Bildschirm,
4 Prozent sperren über die Gesichtserkennung des Geräts.
Erst 2 Prozent der Smartphone-Nutzer tun dies über einen Iris-Scanner.
Klassisch per Code oder PIN sperren fast zwei Drittel (64 Prozent) den Bildschirm,
vier von zehn (41 Prozent) nutzen dafür ein Muster.
Bitkom Tipps für sichere Smartphone-Nutzung
Vorsicht beim Kauf alter Handys
Die regelmäßige Aktualisierung von Smartphone-Betriebssystemen wie Android oder iOS dient dazu, neue Funktionen der Software einzuführen und mögliche Sicherheitslücken zu schließen. Viele ältere Geräte werden jedoch wegen technischer Einschränkungen nicht mehr mit neuen Updates versorgt. Sicherheitslücken der Vorgängerversionen bleiben somit bestehen.
Regelmäßig Updates installieren
Was für das Betriebssystem gilt, gilt auch für die installierten Apps. Software-Entwickler arbeiten permanent daran, Fehler in den Anwendungen aufzuspüren und Schwachstellen zu beheben. Hierfür werden regelmäßig neue Software-Versionen veröffentlicht. Betriebssystem und Apps sollten daher stets auf die neueste Version aktualisiert werden.
Achtung bei der App-Auswahl
Nutzer sollten Apps nur aus verifizierten Shops und offiziellen App-Stores herunterladen. Die Betreiber der großen App-Plattformen scannen das App-Angebot nach schädlichen Programmen und legen bestimmte Sicherheitsstandards an die Veröffentlichung von Apps in ihrem Store an.
Bildschirmsperre nutzen
Eine Bildschirmsperre schützt das eigene Smartphone vor einem ungewollten Zugriff durch Dritte. Sperr-Muster gelten dabei nicht als sicher, da die Wischbewegungen auf dem Display erkennbar sein können. Ein möglichst sechsstelliger Zahlen-PIN ist hingegen schwerer nachzuvollziehen. Die PIN für die SIM-Karte sollte ohnehin immer aktiviert sein.
Fremden Geräten nicht automatisch vertrauen
Möchte man sein Smartphone mit einem fremden Gerät verbinden, sei es für den Austausch von Daten oder nur zum Laden, sollte man beachten, dass das fremde Gerät auch zum Angreifer werden kann. Insbesondere bei Funk-Verbindungen ist Vorsicht geboten.
Verschlüsselungs-Funktionen nutzen
Die Verschlüsselung des Dateisystems eines Smartphones sichert darauf gespeicherte Daten wie Fotos, Passwörter, Kurznachrichten, Kontakte, Anruflisten oder den Browserverlauf. Im Falle eines Diebstahls sind die Daten für den Dieb wertlos.
Virenscanner und Firewall installieren und aktivieren
Durch immer neue Angriffsmuster von kriminellen Hackern kann Schadsoftware - so genannte Malware - über App Stores, Webseiten, E-Mails oder per SMS auf das Smartphone gelangen. Virenscanner-Apps können Bedrohungen durch Malware frühzeitig erkennen und blockieren. Eine Firewall-App überwacht die Netzwerkaktivitäten aller aktiven Apps und sorgt dafür, dass nur vertrauenswürdige Apps auf das Internet zugreifen können.
Keine fremden USB-Ladegeräte nutzen
Vor allem öffentliche USB-Ladestationen sind oftmals nicht vertrauenswürdig. Hackern ist es bereits gelungen, über manipulierte USB-Stecker und -Netzteile Daten aus Mobilgeräten zu ziehen. Wer auf Nummer sicher gehen will, verwendet ein so genanntes "USB-Kondom", eine Platine, die zwar Ladestrom, aber keine Daten passieren lässt.
Backups für Handydaten einrichten
Durch regelmäßige Sicherungskopien, auch Backups genannt, bleiben persönliche Daten auch dann erhalten, wenn das Gerät defekt ist oder verloren geht. Die gesicherten Daten lassen sich anschließend auf einem neuen Gerät problemlos wiederherstellen. Das Backup der Daten kann als Synchronisation mit dem Heim-PC, mit Hilfe eines Massenspeichers wie einer Micro-SD-Karte oder in einem Cloud-Speicher erfolgen....
https://www.trojaner-info.de/mobile-security/aktuell/malware-jedes-dritte-handy-infiziert.html
REMAINING RISC
Firefox ESR 60 (Firefox ESR >52.9): Webextensions verhindern die Installation zahlreicher Extensions wie gegen Tracker und Server-Datenaustausch abzielendes RequestPolicyBlockContinued (hilft nur teilweise: JavaScript abschalten und/oder ABP allein in empfohlener Konfiguration oder Browser PaleMoon verwenden). Erst Firefox >=64 ermöglicht wieder das Blocken.
So groß ist die Bedrohung, PC WELT, 01.10.2017
Laut der aktuellen Studie "Industriespionage 2012" ist bereits über die Hälfte aller Unternehmen in Deutschland Opfer von Industriespionage geworden. Schätzungen gehen dahin, dass der finanzielle Schaden für deutsche Unternehmen durch Industriespionage bei etwa 4,2 Miliarden Euro pro Jahr liegt. Das ist ein Anstieg um 50 Prozent seit der letzten Studie 2007.
"Die Hackerangriffe auf Sony, Google, die Nato oder den IWF zeigen, dass die Cyber-Kriminellen Ziele und Taktiken radikalisiert haben. Diese veränderte Bedrohungslage macht ein grundlegendes Umdenken in Bezug auf Informationsschutz, speziell die IT-Sicherheit, Mitarbeiterbindung und die Grundregeln für den Wissensaustausch erforderlich", sagt Christian Schaaf, Studienleiter und Geschäftsführer von Corporate Trust.
"Wenn es um den Schutz des eigenen Know-how geht, ist es zwar wichtig, ein vernünftiges Bewusstsein für die Risiken zu haben, es ist jedoch ebenso wichtig, ein gesundes Vertrauen in die eigenen Sicherheitsvorkehrungen und die Zuverlässigkeit seiner Mitarbeiter (wie insbesonders Netz- und Systemadministratoren) zu setzen", so Schaaf.
https://www.pcwelt.de/ratgeber/Das_grosse_Kompendium_zur_Netzwerksicherheit-Netzwerke-7811930.html
Überwachungskapitalismus, STERN.de, 03.02.2019
[...] Wie es soweit kommen konnte, wie die Politik das auch lange zulassen konnte, ist nicht so einfach zu fassen, nicht so einfach zu erklären.
Derzeit ist es die US-Autorin Shosana Zuboff, eine ehemalige Harvard-Professorin, die in ihrem Buch "Das Zeitalter des Überwachungskapitalismus" Phänomene wie Facebook - und damit auch die Ursachen der Zuckerbergschen Hybris - sehr hellsichtig analysiert. "Überwachungskapitalisten", argumentiert sie unter anderem, verdienen ihr Geld, indem sie das privaten Verhalten ihrer Nutzer ausbeuten. Und dabei ist es diesen Kapitalisten völlig egal, was für Daten das sind. Die "Überwachungskapitalisten", so die These, bewerten nichts moralisch. Sie bewerten es nicht einmal politisch. Hauptsache, sie kriegen Daten.
https://www.stern.de/digital/online/facebook-wird-15-jahre-alt--der-teenie-braucht-endlich-grenzen-8563384.html
From News&Links#computer :
Überwachung
36 Millionen Euro: ZITiS baut Supercomputer zur Entschlüsselung, netzpolitik.org, 16.10.2018
Die Hacker-Behörde ZITiS will einen Hochleistungsrechner bauen, um verschlüsselte Daten zu entziffern. Das geht aus dem 36 Millionen Euro teuren Haushaltsentwurf der Behörde hervor, den wir veröffentlichen. Nach wie vor sucht ZITiS Staats-Hacker, aktuell ist nur die Hälfte der Stellen belegt.
Die IT-Behörde ZITiS soll nächstes Jahr 36,7 Millionen Euro bekommen, 20 Prozent mehr als dieses Jahr. Die vor anderthalb Jahren gegründete "Zentrale Stelle für IT im Sicherheitsbereich" hilft Polizei und Geheimdiensten bei der technischen Überwachung. Wir veröffentlichen an dieser Stelle das bisher unveröffentlichte ZITiS-Kapitel aus dem Bundeshaushalt sowie eingestufte Informationen aus dem Bundesinnenministerium.
Von diesem Geld wollen die staatlichen Hacker "hochmoderne technische Ausstattung" kaufen. Ganz oben auf der Wunschliste steht ein Hochleistungsrechner, "der vorrangig im Bereich der Kryptoanalyse genutzt wird" - also zur Entschlüsselung. Dieser Supercomputer hat "höchste Priorität" für die ZITiS-Abnehmer Verfassungsschutz, Bundeskriminalamt und Bundespolizei.
Vor zwei Wochen wurde bekannt, dass ZITiS auch einen Quantencomputer einsetzen will. Ob Supercomputer und Quantencomputer verschiedene Projekte sind, will ZITiS auf Anfrage nicht verraten: "Zu unseren Projekten und verwendeten Technologien können wir keine Auskunft geben." Da die Entwicklung nutzbarer Quantencomputer jedoch noch in den Kinderschuhen steckt, dürfte der Hochleistungsrechner ein eigenes Projekt sein, der zeitnah in Betrieb gehen soll.
Staatstrojaner für mobile Endgeräte
In den anderen Arbeitsfeldern rüstet ZITiS ebenfalls auf, wobei zwei besonderes Gewicht erhalten. Im Bereich der Digitalen Forensik forscht und entwickelt ZITiS unter anderem an "Passwortsuche" und der "Auswertung von Smartphones". Bisher haben Polizeibehörden sieben verschiedene Software-Tools gekauft, um beschlagnahmte Mobilgeräte auszulesen. Dieser Wildwuchs soll bei ZITiS vereinheitlicht werden.
Im Bereich Telekommunikationsüberwachung (TKÜ) arbeitet ZITiS an zwei Projekten, die bisher beim BKA angesiedelt waren. ZITiS setzt das "Projekt INTLI" (Internationale Zusammenarbeit in der TKÜ) fort, "das sich mit der Standardisierung des Austauschs von TKÜ-Daten auf Grundlage der Rahmenrichtlinie Europäische Ermittlungsanordnung beschäftigt". Die EU-Richtlinie ermöglicht grenzüberschreitende Überwachung von Telekommunikation.
ZITiS will auch die Entwicklung von Staatstrojanern vorantreiben. Mit dem "Projekt SMART" soll ZITiS das BKA unterstützen "bei der Entwicklung einer Quellen-TKÜ-Lösung für mobile Endgeräte", also einem Trojaner zum Abhören von Kommunikation. Das BKA hatte für sechs Millionen Euro den Staatstrojaner "RCIS" programmiert, der seit diesem Jahr auch Smartphones infizieren und abhören kann. Jetzt wollen ZITiS und BKA die Software gemeinsam weiterentwickeln.
Hacker gegen IT-Unsicherheitsbehörde
Insgesamt will ZITiS nächstes Jahr mehr als zehn Millionen Euro für Investitionen ausgeben, über elf Millionen sind für Personal geplant. Das Innenministerium bezeichnet die Personalgewinnung als "anspruchsvoll" und "eine zentrale Herausforderung". Vom Behördensprech übersetzt: Nur wenige IT-Experten wollen für den Staat hacken. Der BND nannte das mal "knappe Ressource brillantes Personal".
Derzeit hat ZITiS erst "74 der im Kalenderjahr 2018 zur Verfügung stehenden 150 Planstellen belegt". Fast die Hälfte der bisher eingestellten Mitarbeiter*innen ist in Verwaltung und Leitung tätig. Das existierende "MINT-Fachpersonal" arbeitet nicht nur in der Umsetzung der Aufgaben, sondern auch bei internen IT-Diensten und Beratung. Zwei Drittel der Angestellten kommen aus anderen Behörden, nur ein Drittel sind "Externe".
Falk Garbsch, Sprecher des Chaos Computer Clubs, kommentiert gegenüber netzpolitik.org:
Es ist gut zu sehen, dass Hacker offenbar keinerlei Interesse haben, für eine IT-Unsicherheitsbehörde zu arbeiten. Die Community hat schon vor vielen Jahren verstanden, was verbohrte Politiker nicht akzeptieren wollen: Das Ausnutzen und Offenhalten von Sicherheitslücken ist ein nachhaltiges Risiko für Unternehmen, kritische Infrastrukturen und Zivilgesellschaft. Statt Steuergelder in absurde Angriffsphantasien zu verschwenden, wird es Zeit für Investitionen in das konsequente Schließen von Sicherheitslücken.
Der Regierungsentwurf zum Bundeshaushalt 2019 wird derzeit im Bundestag verhandelt. Bisher hat die Große Koalition keine Änderungen bezüglich ZITiS beantragt oder beschlossen. Anträge der Opposition werden üblicherweise abgelehnt. Ende November soll der Haushalt im Bundestag verabschiedet werden.
Hier die Dokumente in Volltext:
Ministerium: Bundesministerium des Innern, für Bau und Heimat
Stand: 17. August 2018
...
https://netzpolitik.org/2018/36-millionen-euro-zitis-baut-supercomputer-zur-entschluesselung/
From News&Links#NSA&Co. :
Internetknotenpunkt De-Cix Gericht billigt BND-Abhörpraxis, 31.05.2018
Der Internetknotenpunkt De-Cix in Frankfurt ist der größte der Welt. Das macht sich auch der BND zunutze und greift Daten ab. Dagegen hatte der Betreiber geklagt. Nun hat das Bundesverwaltungsgericht geurteilt.
Der Bundesnachrichtendienst (BND) darf weiterhin in großem Umfang Daten beim Internet-Knoten De-Cix aus Frankfurt am Main abzapfen. Das entschied nach dpa-Informationen das Bundesverwaltungsgericht.
De-Cix (Deutsche Commercial Internet Exchange) hatte gegen den Eingriff des BND geklagt. Dieser überwache ohne konkreten Verdacht. Dabei würde auch rein inländische Telekommunikation beobachtet. Dies lasse das Gesetz zur Beschränkung des Brief-, Post- und Fernmeldegeheimnisses jedoch nicht zu. Es ermächtige lediglich zur überwachung von internationaler Telekommunikation.
Richter: BND darf überwachen
Dieser Argumentation folgten die Richter nicht und stärkten dem BND mit ihrem Urteil den Rücken. Der Geheimdienst sei berechtigt, auf Anordnung des Bundesinnenministeriums internationale Telekommunikation zu überwachen und aufzuzeichnen.
Für den Schutz der Bürger sorgt laut Bundesregierung die G-10-Kommission des Bundestages. Sie muss die Eingriffe in das Fernmeldegeheimnis erlauben.
Wie wichtig die Datenüberwachung für den Geheimdienst ist, zeigt eine Äußerung von Ex-Chef Gerhard Schindler: In vertraulicher Runde hatte er gesagt, ohne Fernmeldeaufklärung "kann ich den Laden dichtmachen".
Inländische Kommunikation ausgeschlossen
Um inländische Kommunikation aus der Überwachung auszuschließen, verwendet der BND laut eigener Auskunft ein mehrdimensionales Filtersystem. Man nehme auch Browser- und Programmeinstellungen mit in den Blick, Geodaten und mehr, um ein Gesamtbild zu bekommen und deutsche Nutzer auszusortieren.
Die Filter sollen zu mehr als 99 Prozent wirksam sein. Wenn am Ende immer noch irrtümlich eine E-Mail eines Deutschen durch den Filter rutsche, dann werde sie per Hand entfernt, das komme aber nur selten vor. Anders als von De-Cix behauptet, gebe es deshalb keinen Rechtsbruch.
Mehr als sechs Terabyte pro Sekunde
Der Frankfurter Knotenpunkt besteht seit 1995. Mit zeitweise mehr als sechs Terabyte pro Sekunde weist er den höchsten Datendurchsatz weltweit auf. Auch ein Großteil des deutschen Internetverkehrs läuft dort hindurch.
Aktenzeichen: BVerwG 6 A 3.16
https://www.tagesschau.de/inland/de-cix-bnd-klage-101.html
Kooperation von BND und NSA: Heimliche Amtshilfe unter Freunden, Tagesschau, 25.06.2014
Der BND hat jahrelang Daten eines Frankfurter Internetknotenpunkts an die NSA weitergegeben. Nach Recherchen von NDR, WDR und "SZ" leitete er mindestens von 2004 bis 2007 abgefangene Rohdaten direkt an den US-Dienst. von Georg Mascolo, NDR
In Frankfurt laufen die Fäden zusammen. Hier verbindet die weltweit größte Internet-Schnittstelle die Netze von mehr als 50 Ländern. Daten aus Russland fließen über Frankfurt beispielsweise in den Nahen Osten. Schon immer hatten die Amerikaner ein Auge auf Frankfurt geworfen und drängten auf einen direkten Zugriff auf die Glasfasernetze. Bereinigt um die Daten deutscher Bürger soll der BND drei Jahre lang der NSA Datenmaterial zur Verfügung gestellt haben. Vor allem Telefonate sollen so direkt in die Computer der NSA geleitet worden sein. Über den Umfang der Datenweitergabe gibt es widersprüchliche Angaben. Während einige Quellen sie als "sehr umfassend" beschreiben, heißt es in BND-Kreisen, es habe sich zwar um große Mengen gehandelt, aber nur eine von mehreren Leitungen sei betroffen gewesen. Erst 2007 soll die Operation vom damaligen BND-Chef Uhrlau gestoppt worden sein. Auch im Kanzleramt war man zu dem Schluss gekommen, dass die Aktion "viel zu heikel ist", so ein damals Beteiligter. Gegen den Protest der NSA wurde das Projekt eingestellt. Die gemeinsame Operation soll den Recherchen zufolge 2004 begonnen haben und war auch im Kanzleramt bekannt. Offenbar sind aber weder das Parlamentarische Kontrollgremium noch die Bundestagskommission, die für die Abhörmaßnahmen der Geheimdienste zuständig ist, jemals über die damalige Operation informiert worden.
"Ich bin noch nie so belogen worden"
#34c3: Die Lauschprogramme der Geheimdienste, netzpolitik.org, 29.01.2018
"Ich bin noch nie so belogen worden", sagte Hans-Christian Ströbele über seine Arbeit im NSA-BND-Untersuchungsausschuss. In einem Gespräch mit Constanze Kurz resümiert der grüne Politiker die Ergebnisse der parlamentarischen Untersuchung.
https://netzpolitik.org/2018/34c3-die-lauschprogramme-der-geheimdienste/
Staatstrojaner stoppen!
Verfassungsbeschwerde gegen den Staatstrojaner - für sichere und vertrauenswürdige IT, digitalcourage.de, gesehen am 09.09.2018
"Der Staatstrojaner ist ein Schlag ins Gesicht all derer, die an unsere parlamentarische Demokratie glauben", sagte Digitalcourage-Vorstand padeluun im ZDF-Morgenmagazin.
Die Große Koalition schlägt mit den Staatstrojanern gefährliche Sicherheitslücken in all unsere Smartphones und Computer. Der Plan: Jedes Gerät bekommt eine Hintertür, durch die staatliche Hacker und Kriminelle nach Lust und Laune einsteigen können. Kommunikation wird mitgehört, Verschlüsselung wird gebrochen, Daten werden gesammelt und Geräte, Netzwerke und ganze Clouds werden manipuliert. Das ist katastrophal für Zivilgesellschaft, Behörden und Unternehmen. Der Staat missachtet seine Pflicht, Bürgerinnen und Bürger zu schützen, wenn er Sicherheitslücken gezielt offen hält, anstatt sie zu schließen.
Mit einer Verfahrenslist wurde das Gesetz ohne große öffentliche Diskussion durch den Bundestag gedrückt, doch es kollidiert klar mit Urteilen des Bundesverfassungsgerichts. Darum gibt es gute Chancen, das Gesetz zu kippen - wir müssen es nur tun!
Helfen Sie uns, die Staatstrojaner mit einer Verfassungsbeschwerde vor dem Bundesverfassungsgericht zu stoppen!
Wichtig: Geben Sie diese Info auch an Freunde, Nachbarinnen und Kollegen weiter! Denn der Staatstrojaner schlägt eine Sicherheitslücke in jedes Kommunikationsgerät!
https://aktion.digitalcourage.de/kein-staatstrojaner
From News&Links#Alternatives :
 ( maybe in future) Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018 ( maybe in future) Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018
Wer im Internet miteinander kommuniziert, hinterlässt unweigerlich Spuren. Wiener Forscher wollen jetzt ein Verfahren entwickelt haben, das die Kommunikation auch in einem größeren Netzwerk abhörsicher macht.
Die Quantenkryptografie will in Zukunft eine abhörsichere Kommunikation im Internet ermöglichen. Österreichische Forscher haben nun - nach eigenen Angaben - eine wichtige Hürde auf diesem Weg genommen. Ihnen gelang, dass vier Teilnehmer eines Netzwerkes abhörsicher kommuniziert haben. Die Wissenschaftler um Rupert Ursin vom Wiener Institut für Quantenoptik und Quanteninformation der Österreichischen Akademie der Wissenschaften haben ihre Forschung im britischen Fachblatt "Nature" vorgestellt. Nach Angaben der Wissenschaftler lässt sich das Netzwerk einfach erweitern - und könnte so für eine breite Anwendung infrage kommen.
Herkömmliche Verschlüsselungstechnologien bieten nur relativen Schutz, sagt Rupert Ursin von der Akademie der Wissenschaften im Gespräch mit dem ORF. "Wenn ich meine E-Mails lese, könnte ein Dritter im Prinzip beliebig viele Kopien davon anfertigen - und es würde niemand bemerken. Bei der Quantenkryptografie ist das unmöglich. Wenn Hacker versuchen, eine Quantenbotschaft zu belauschen, hinterlassen sie unweigerlich eine Spur. Das ist ein Naturgesetz."
Die Quantenkryptographie nutzt dabei ein Phänomen der Quantenphysik. Nach deren Regeln können zwei Teilchen einen gemeinsamen Zustand bilden, auch wenn sie anschließend über weite Entfernungen getrennt werden. In diesem Zustand der Verschränkung sind die Eigenschaften der beiden individuellen Teilchen unbestimmt. Wird dann bei einem der beiden Teilchen eine Eigenschaft wie beispielsweise die Schwingungsrichtung gemessen, nimmt das andere Teilchen augenblicklich eine korrespondierende Eigenschaft an. Die Verschränkung endet. Auf diese Weise ist es möglich, abhörsicherer Schlüssel bei Sender und Empfänger zu erzeugen.
Lauscher können Anwesenheit nicht verschleiern
Entscheidend ist: Der Schlüssel kann von Hackern nicht abgefangen werden. Denn es werden nur einzelne Lichtteilchen (Photonen) ausgetauscht. Und nach den Gesetzen der Quantenphysik ist es unmöglich, den Quantenzustand eines einzelnen Lichtteilchens ohne Fehler zu kopieren. Ein Lauscher kann seine Anwesenheit daher nicht verschleiern und würde sich sofort verraten. Die verschlüsselte Nachricht wird dann auf klassischem Weg ausgetauscht.
Bisher nur bei zwei Teilnehmern nachgewiesen
Bisher ließen sich auf diese Weise meist jedoch nur zwei Teilnehmer mit einer garantiert abhörsicheren Leitung verbinden. Weitere Verbindungen seien kompliziert, fehleranfällig und mit Kommunikationseinschränkungen behaftet.
Das Team versorgte nun vier Teilnehmer aus einer zentralen Quelle mit verschränkten Photonen, sodass alle vier miteinander kryptographische Schlüssel erzeugen und für eine abhörsichere Kommunikation verwenden konnten. "Ein entscheidender Vorteil dieser Architektur ist ihre Flexibilität", betont Ursin in einer Mitteilung der Akademie. "Wir sind damit in der Lage, neue Kommunikationspartner in das Quantennetzwerk zu integrieren - und zwar mit lediglich minimalen Eingriffen. Damit ist gezeigt, dass Quantennetzwerke Realität werden können - für Jedermann."
https://www.tagesschau.de/ausland/quanten-101.html
DLD-conference in Munic
"Stop doing all this right now!": Google-manager warns against gigantic security exploit, FOCUS ONLINE, 19.01.2020
[...] Vor allem die deutlich überragende Rechenleistung von Quanten-Technologie machen es möglich, solche heute noch komplexe Codes zu entschlüsseln.
Anders als bisherige Systeme, die nach wie vor nur mit Nullen und Einsen rechnen, haben Quanten-Maschinen unendliche Möglichkeiten ihre Rechnungen aufzubauen - und damit einen deutlichen Vorteil gegenüber ihren Vorfahren.
Die Zukunft ist uns also näher, als wir denken. Und das birgt Risiken. "Hören Sie noch heute auf, RSA-Verschlüsselung zu benutzen", rät Google-Forscher Jack Hidary auf dem DLD.
Veraltete Verschlüsselungstechnik
Der Grund: die Technik ist schon jetzt veraltet. Beim RSA-Verfahren wird eine Information mit einem privaten Schlüssel verschlüsselt und so gegen das Auslesen gesichert
In einer Zukunft mit Quantenkommunikation gebe es aber nur eine sichere Verschlüsselungstechnik: PQC - Post-Quantum Kryptographie. Diese sei schon in wenigen Jahren fähig, die herkömmlichen Verfahren wie RSA oder ECC zu brechen.
"Es gibt einen neuen Trend", scherzt Hidary: "SNDL: Store now, decrypt later, manche meiner Freunde sagen auch: Stehl es heute, dechiffrier es später."
Vor allem die deutlich überragende Rechenleistung von Quanten-Technologie machen es möglich, solche heute noch komplexe Codes zu entschlüsseln.
Anders als bisherige Systeme, die nach wie vor nur mit Nullen und Einsen rechnen, haben Quanten-Maschinen unendliche Möglichkeiten ihre Rechnungen aufzubauen - und damit einen deutlichen Vorteil gegenüber ihren Vorfahren.
https://www.focus.de/digital/dldaily/dld-konferenz-in-muenchen-googlex-dld202_id_11567641.html
 Transportverschlüsselung Teil 3, HTTPS mit TLS 1.3 in der Praxis, 11.06.18 | Autor / Redakteur: Filipe Pereira Martins und Anna Kobylinska / Peter Schmitz Transportverschlüsselung Teil 3, HTTPS mit TLS 1.3 in der Praxis, 11.06.18 | Autor / Redakteur: Filipe Pereira Martins und Anna Kobylinska / Peter Schmitz
TLS 1.3 verspricht mehr Sicherheit von verschlüsselten HTTPS-Verbiundungen. Leider ist die Implementierung voller Tücken und Überraschungen.
Wem die Sicherheit von HTTPS-Verbindungen am Herzen liegt, der ist gut beraten, die TLS-Konfiguration zu überdenken, denn ohne eine moderne Transportverschlüsselung sind gute Vorsätze beim Datenschutz nur ein Papiertiger. Zwar ist TLS 1.3 nun offiziell aus den Startlöchern, aber die Implementierung ist leider voller Tücken und Überraschungen.
Da die Verwundbarkeiten des TLS-Protokolls bis einschließlich Version 1.2 allgemein bekannt sind (siehe dazu den Bericht "TLS 1.3 - Viel heiße Luft oder ein großer Wurf?") ist davon auszugehen, dass das Herumschnüffeln an vermeintlich "verschlüsselten" HTTPS-Verbindungen öfter vorkommen dürfte als einem lieb sein mag. TLS 1.3 verspricht Abhilfe.
Leider ist die Implementierung voller Tücken und Überraschungen.
Es beginnt schon damit, dass ein völliger Verzicht auf TLS 1.2 als einen Fallback für Clients mit fehlender Unterstützung für TLS 1.3 vorerst nicht in Frage kommt.
Server-Unterstützung für TLS 1.3 mit einem TLS 1.2-Fallback einrichten
Die Umsetzung von TLS 1.3 setzt so Einiges an Handarbeit voraus.
Schritt 1: Ein Kernel-Upgrade installieren:
Der Einsatz von TLS 1.3 steht und fällt mit einem Linux-Kernel ab der Version 4.13 ("1600 LoC-Patch"). Linux-Kernel bis einschließlich Version 4.12 unterstützten nur maximal AES-128-GCM (gemäß RFC 5288) und scheiden damit aus. Die AEAD-Verschlüsselung, die TLS 1.3 automatisch erwartet, ist erst mit dem sogenannten 1600 LoC-Patch möglich. Mit diesem Patch kann Linux erstmals die Verschlüsselung für eine bereits bestehende Verbindung intern im Kernel (ab Version 4.13) handhaben. Der User-Space übergibt dem Kernel die Kryptoschlüssel für eine bereits aufgebaute Verbindung, sodass die Verschlüsselung transparent innerhalb des Kernels stattfindet. CentOS/RHEL in der Version 6 bleiben mit ihrem 2.6.x-er Kernel außen vor.
Schritt 2. Ein OpenSSL-Upgrade einspielen:
Linux-Distributionen richten standardmäßig "stabile" (sprich: veraltete) Versionen der OpenSSL-Bibliothek ein, die mit TLS 1.3 bisher nicht zu Recht kommen. OpenSSL muss in der Version 1.1.1 Beta 4 oder neuer vorliegen.
Schritt 3. Zertifikate von einer Zertifizierungsstelle (CA) beschaffen und einrichten:
Zertifizierungsstellen (CAs) gibt es wie Sand am Meer. Doch in der Vergangenheit waren SSL-Zertifikate ein schmerzhafter Kostenpunkt. Dank der kostenfreien SSL-Zertifikate von Let´s Encrypt hat sich endlich dieses Problem größtenteils erledigt. Die leistungsstarke API sorgt für eine schmerzlose Automatisierbarkeit auf allen Unix/Linux-Derivaten.
Schritt 4. Den Webserver konfigurieren:
Wer die benötigten SSL-Zertifikate installiert hat, kann sich im nächsten Schritt der Server-Konfiguration widmen. Die Details der Implementierung hängen von der Art und Versionsnummer des Webservers ab. Grundlegende Parameter zum Aktivieren der SSL-Verschlüsselung in Apache, Nginx, Lighttpd, HAProxy und AWS ELB lassen sich einem Online-Assistenten wie dem SSL Configuration Generator von Mozilla entnehmen. Leider halten sich die Fähigkeiten dieses Werkzeugs in argen Grenzen. Es fehlt hier u.a. die Unterstützung für TLS 1.3 und auch TLS 1.2 leidet unter mangelnder Beachtung (Diffie-Hellman gefälligst? Fehlanzeige). Die Übernahme von Konfigurationsparametern für die TLS-Verschlüsselung nach dem Fertiggericht-Prinzip gehen nach hinten los.
Sicherheitsbewussten Administratoren bleibt nichts anderes übrig als die fehlenden Parameter für den eigenen Webserver samt der passenden Syntax selbst zu eruieren. Zu den wichtigsten Ergänzungen bzw. Korrekturen zählen:
Aktivieren der Unterstützung für HTTP/2
Umlenkung von HTTP-Anfragen auf HTTPS
Unterbinden von Protokoll-Downgrades auf HTTP unter Verwendung von HSTS
Einrichtung von Browser-Anweisungen mit Hilfe von Sicherheits-Headern (HTTP Security Headers, verfügbar nur mit HTTPS): HTTPS-Sicherheitsheader sorgen für die Übergabe von Anweisungen durch den Webserver an einen (kompatiblen) Webbrowser, um sein Verhalten zu beeinflussen. Zum Schutz gegen Downgrade-Attacken und Cookie-Hijacking lässt sich unverschlüsselte Kommunikation mit dem so genannten HSTS-Header deaktivieren (HSTS steht für HTTP Strict Transport Security). Gegen Clickjacking-Attacken hilft ein X-Frame-Options-Header. Um das Aushebeln von deklarierten Mime-Typen zu verhindern, kommen X-Content-Type-Optionen zum Einsatz. Für den Schutz gegen Cross-Site-Request Forgeries (kurz: X-XSS) zeichnet der X-XSS-Protection-Header verantwortlich. Diese Einstellungen können die verfügbare Angriffsfläche stark reduzieren.
Deaktivieren verwundbarer Protokollversionen: Als sicher gelten derzeit nur TLS 1.2 und TLS 1.3
Optimieren der TLS 1.2-Konfiguration zur Härtung durch den Verzicht auf verwundbare Cipher-Suites: Als verwundbar gelten alle Cipher-Suites außer ECDHE- und DHE-basierter Varianten
Eine nicht zu unterschätzende Verwundbarkeit, die sich durch die Umstellung auf HTTPS nicht von selbst erledigt, stellt JavaScript-Code von externen Domains dar. Ein klassisches Beispiel sind Werbeeinblendungen. Mit einer aktivierten CSP-Richtlinie (kurz für Content Security Policy) können Website-Betreiber für eine erhöhte Sicherheit sorgen. Bei CSPs handelt es sich um Sicherheitsrichtlinien, welche unsichere Web-Inhalte aus externen Quellen und Verbindungen über HTTP unterdrücken können. So lassen sich nicht zuletzt auch Clickjacking- und andere Code-Injection-Attacken unterbinden.
Schritt 5. Konfiguration testen:
Zu guter Letzt gilt es, die Konfiguration mit einem Dienst wie der SSL Server Test von Qualys SSL Labs auf ihre Vollständigkeit hin zu überprüfen.
Encrypted Traffic Analytics
Eine robuste Transportverschlüsselung hat jedoch auch ihre Schattenseiten: Malware kann jetzt einfach unbemerkt durchsegeln.
Beim Einsatz von TLS bis einschließlich der Version 1.2 (insbesondere mit RSA-Ciphern) konnten IT-Fachkräfte den Datentransfer z.B. vor dem Eingang ins firmeneigene Datencenter auf bösartige Payloads hin überprüfen. Die Kommunikation wurde in diesem Fall durch sogenannte Middleboxes eingelesen, dechiffriert, analysiert und weitergeleitet. Mit TLS 1.3 gehört diese Art von Monitoring der Vergangenheit an. Denn beim Verbindungsaufbau über TLS 1.3 mit ephemeralen Diffie-Hellman-Schlüsseln schlägt die sogenannte "Deep-Packet Inspection" fehl, weil sich die Kommunikation in Echtzeit nicht ohne Weiteres dechiffrieren lässt — und schon erst recht nicht in Echtzeit. Das Bedürfnis an adäquaten Sicherheitsmaßnahmen für die Unternehmens-IT besteht jedoch weiter.
So mussten sich die Anbieter von Sicherheitslösungen für Traffic-Analytics bei TLS 1.3 nach alternativen Wegen zur Gewährleistung der Integrität der internen Systeme umschauen. Die ersten konkreten Produkte sind bereits auf dem Markt. Alleine Cisco hat vier interessante Lösungen im Köcher:...
https://www.security-insider.de/https-mit-tls-13-in-der-praxis-a-714096/
Mausklick-schnell: Sicherheit beim Surfen mit TLS 3.0
Firefox-ESR >= 52.9 : Inhalte von lib64nss3 (mga7, pclos, fc, ...) oder nss (fc, ...) und >= libssl3.so.1.1.1a (openssl-1.1.1a, fc27) nach /usr/lib64/firefox/libssl3.so ( Installationsverzeichnis )
Tor-Browser (Firefox-ESR >= 52.9: Inhalte von lib64nss3 (mga7, pclos oder nss (fc, ...) und >= nss-3.41.0 (fc30) mit libssl.so.3 nach /home/toruser/tor*/Browser*/
Pale Moon >=: Inhalte von lib64nss3 (mga7, pclos oder nss (fc, ...) und libssl3.so.1.1.1a (von openssl-1.1.1a, fc27) nach /usr/lib64/palemoon/libssl3.so
Dabei zeigt /usr/lib64/libcrypto.so.1.1 auf /usr/lib64/libcrypto.so.1.1.1a und /usr/lib64/libssl.so.1.1 auf libssl.so.1.1.1a.
VPN für mehr Schutz in offenen Netzen, netzpolitik.org, 30.04.2018
"VPN steht für Virtual Private Network. Mit einem VPN-Client lässt sich nicht nur weitgehend anonym surfen, sondern auch bei anderen Online-Aktivitäten die eigene Identität verschleiern. Das ist vor allem wichtig, wenn man in offenen WLANs unterwegs ist, wo der Betreiber den Datenverkehr mitüberwachen kann. VPN-Software leitet sämtlichen Verkehr zunächst vom eigenen Gerät verschlüsselt zum Server des Anbieters und von dort ins Netz. Auch kann man durch VPN-Server vorgeben, aus einem bestimmten Land zu sein, und dadurch Geoblocking umgehen.
Manche VPN-Anbieter versprechen ihren Nutzern, ihre Zugriffsdaten nicht zu speichern und dadurch ihre Anonymität zu wahren. Aber Obacht: Wenn der gesamte Internetverkehr durch einen VPN-Anbieter getunnelt wird, versetzt das diesen in eine besonders wichtige Lage und macht ihn zu einem attraktiven Ziel. Dass Anbieter von VPN-Diensten selbst nicht mitlesen, gilt bei weitem nicht für alle VPN-Anbieter, etwa den entsprechenden Dienst von Facebook. Auf keinen Fall sollte man daher Gratis-Lösungen nutzen. Im Umfeld von netzpolitik.org werden beispielsweise IPredator oder F-Secure verwendet. Am sichersten ist aber immer noch, den VPN über einen eigenen Server zu betreiben.
Staaten wie China, Russland und der Iran schränken die Nutzung von VPN-Diensten stark ein. Das sollte man vor einem Reiseantritt bedenken. Auch gilt es bei der Verwendung von VPN-Diensten und Tor-Browsern zu bedenken: Sobald man sich im Browser irgendwo einloggt, ist es - zumindest gegenüber dem verwendeten Dienst - vorbei mit der Anonymität."
https://netzpolitik.org/2018/kleines-einmaleins-der-digitalen-selbstverteidigung/
VPN: Sicherer Zugriff von unterwegs auf Ihre Daten, PC-WELT.de, 03.02.2019
Verschlüsselte VPN-Verbindungen oder -Tunnel schützen beim Surfen an öffentlichen Hotspots, umgehen lästiges Geoblocking und sorgen für mehr Privatsphäre. Ein Überblick über Anwendungsszenarien und Anbieter dieser sicheren virtuellen privaten Netzwerke.
Ein Netzwerk wie das Internet verbindet alle angeschlossenen Geräte miteinander. So kann jeder mit jedem kommunizieren, selbst wenn der Kommunikationspartner auf der anderen Seite der Erdkugel sitzt. Der Nachteil: Alle Daten, die im Internet über das TCP/IP-Protokoll übertragen werden, passieren sehr viele Zwischenstationen und können dort mitgelesen oder sogar manipuliert werden. Auf diese Weise werden die Daten zwar effizient rund um den Globus geschickt, einen effektiven Schutz vor unerwünschten Zugriffen bietet TCP/IP jedoch nicht.
[...] Allerdings genügt eine VPN-Verbindung allein nicht, um die eigene Anonymität vollständig zu wahren. Wer beim Surfen und aktiviertem VPN unerkannt bleiben möchte, sollte seinen Browser im privaten oder Inkognito-Modus nutzen und sich nicht parallel bei Facebook, Google oder einem anderen "Datenkrakendienst" anmelden.
[...] Der kostenlose Browser Opera bietet die Möglichkeit, alle Browser-Verbindungen über einen VPN-Server von Opera zu leiten. Im Gegensatz zu einer klassischen VPN-Verbindung, die alle Datenpakete im Netzwerk zwischen VPN-Client und -Server verschlüsselt, kümmert sich das Opera-VPN nur um die vom Browser übertragenen Daten. Da bei der Auswahl des Opera-VPN-Servers nicht nach Ländern, sondern nur nach Kontinenten gewählt werden kann, eignet sich der Opera-VPN auch nur bedingt zur Umgehung von Geoblocking. Dennoch sorgt Opera-VPN für zusätzliche Sicherheit beim Surfen am Hotspot, und auch der Werbeblocker arbeitet effektiv. Der Dienst lässt sich in Opera über Einstellungen -> Datenschutz & Sicherheit aktivieren und dann komfortabel in der Adressleiste ein-und ausschalten.
Hinweis: Bei aktiviertem VPN-Filter bekommt der Browserhersteller durch die Umleitung auf die eigenen Server ein vollständiges Abbild Ihrer Surfgewohnheiten und kann diese beispielsweise für personalisierte Werbung nutzen.
https://www.pcwelt.de/ratgeber/Virtual-Private-Networks-VPN-Sicherer-Zugriff-von-unterwegs-4731380.html
VPN Perfect Privacy
Keine Speicherung von Log-Dateien (Nutzeraktivitäten)
Für alle Ihre Geräte
Kaskadierung über bis zu 4 VPN-Server
Konfigurierbare Port-Weiterleitungen
Keine Traffic-Begrenzung
Bis zu 1000 Mbit/s Bandbreite
Einfach benutzbare Client-Software
Support via E-Mail, Forum und TeamViewer
Wahlweise über OpenVPN, IPsec/IKEv2, SSH2-Tunnel oder PPTP
TrackStop™ (blockiert Werbe, Tracking- und Phishing-Domains)
Stealth VPN Technologie (VPN wahlweise: über mehrere VPN-Server, Eintrittspunkt (eigenes Land etc), VPN-Netzwerk (Ausland etc.)
NeuroRouting™ (sicheres Routing auf BAsis von KI und gesteuert durch Algorithmen)
Automatische Einrichtung Ihrer Windows Firewall
DNS-Leak-Schutz
8 Port-Weiterleitungen inklusive (z.B. für BitTorrent)
Serverwechsel so oft Sie mögen
Ping-Zeiten zu den Servern in Echtzeit überprüfen
Geld-zurück-Garantie
https://www.perfect-privacy.com/de/?p=609
 Use a Raspberry Pi as a Tor/VPN Router for Anonymous Browsing, 1/28/15 Use a Raspberry Pi as a Tor/VPN Router for Anonymous Browsing, 1/28/15
Roll Your Own Anonymizing Tor Proxy with a Raspberry Pi
We´ve shown you how to use a Raspberry Pi as both a Tor proxy and a personal VPN, but Make shows off how to do both in one unit for truly anonymous browsing everywhere.
There are many interesting things you can do with a Raspberry Pi, but this one isn´t just fun, …
The build here uses two Wi-Fi adapters to get the job done. Once it´s complete, you´ll have a passive VPN connection that you´ll hardly even notice is there. You´ll also have Tor installed, so you can flip over to that connection with just a couple of clicks. It´s a pretty simple setup all things considered, and it´ll act as a nice bridge between your standard router for those times when you want to browse anonymously or get around any location-specific blocks.
Browse Anonymously with a DIY Raspberry Pi VPN/Tor Router
https://lifehacker.com/use-a-raspberry-pi-as-a-tor-vpn-router-for-anonymous-br-1682296948
Preis: ca. 40 Euro
oder
Hardware-Tarnkappen für das anonyme Surfen im Internet, trojaner-info.de, 28.04.2019
Im Internet mit der richtigen Anonymisierungs-Hardware
Geschützt ins Internet mit der richtigen Anonymisierungs-Hardware
Internetnutzer stellen mit der Anonymisierung von Daten und Informationen sicher, dass persönliche Inhalte nicht von Unbefugten gelesen und betrügerisch oder missbräuchlich genutzt werden können. Anonymität und digitale Integrität kann über Anonymisierungsprogramme wie Tor und Hardware-Lösungen wie eBlocker oder dem Onion Pi erreicht werden.
https://www.trojaner-info.de/anonymisierungs-hardware/articles/anonymisierungs-hardware-als-tarnkappe-im-internet.html
Anonymebox, Leipzig
Preis: 189 Euro (Stand: 28.04.2019)
https://pi3g.com/neu-anonymebox-anonym-frei-einfach/
Mouseclick-fast computer, ... especially the evening (around 20:30 o´clock)...
Publications
"Humble Bundle Hacking 2.0" announced, PRO LINUX, 29.05.2019
Das Humble Bundle-Team hat ein weiteres Book-Bundle veröffentlicht. Die bis zu vierzehn Bücher kommen vom "No Starch Press" und behandeln dieses Mal das Thema "Hacking". Wie gewohnt können Käufer dabei selbst entscheiden, wie viel ihnen ein Buchpaket wert ist und wie ihr Geld verteilt wird.
humblebundle.com
Humble Bundle Hacking 2.0
Im "Humble Bundle Hacking 2.0" finden sich dieses Mal zahlreiche Bücher des "No Starch Press"-Verlags zu Themen rund um "Hacking". Alle Bücher können nach demselben Muster gekauft werden wie schon die letzten Pakete. So können die Interessenten beim Kauf entscheiden, wie viel sie zahlen und wie ihr Geld zwischen dem Verlag, Humbe Bundle und den gemeinnützigen Organisationen aufgeteilt wird. Unterstützt werden können auch dieses Mal Electronic Frontier Foundation, das Rote Kreuz oder zahlreiche weitere Organisationen, darunter Wikimedia Foundation, Child´s Play und Charity Water. Bezahlt wird via Amazon, Kreditkarte oder Paypal.
Wer weniger als einen Euro investiert, erhält "The IDA Pro Book, 2nd Edition: The Unofficial Guide to the World´s Most Popular Disassembler", "Designing BSD Rootkits: An Introduction to Kernel Hacking", "The Practice of Network Security Monitoring: Understanding Incident Detection and Response", "A Bug Hunter´s Diary: A Guided Tour Through the Wilds of Software Security" und "Hacking the Xbox: An Introduction to Reverse Engineering".
Wer bereit ist, um die 7 Euro für den Lesestoff auszugeben, kann sich über die Bonustitel "Serious Cryptography: A Practical Introduction to Modern Encryption", "Attacking Network Protocols: A Hacker´s Guide to Capture, Analysis, and Exploitation", "Pentesting Azure Applications: The Definitive Guide to Testing and Securing Deployments", "Practical Packet Analysis, 3rd Edition: Using Wireshark to Solve Real-World Network Problems" und "PoC||GTFO" freuen.
Käufer, die den Maximalbetrag bezahlen und rund 13 Euro investieren, gelangen zudem in den Besitz von "Linux Basics for Hackers: Getting Started with Networking, Scripting, and Security in Kali", "Malware Data Science: Attack Detection and Attribution", "PoC||GTFO, Volume 2" und "Practical Binary Analysis: Build Your Own Linux Tools for Binary Instrumentation, Analysis, and Disassembly". Zudem erhalten Käufer des dritten Pakets auch einen Preisnachlass auf die Bücher "PoC||GTFO" und "PoC||GTFO, Volume 2".
Die E-Books des "Humble Bundle Hacking 2.0" sind in verschiedenen Formaten und in der englischen Sprache erhältlich. Wie üblich können Käufer, die die Bücher verschenken möchten, einen Geschenklink erhalten. Das Bundle ist noch dreizehn Tage erhältlich.
https://www.pro-linux.de/news/1/27103/humble-bundle-hacking-20-angek%C3%BCndigt.html
Software::Kernel
Lacks in security within kernel TCP-Code, PRO LINUX, 21.06.2019
Ein Team bei Netflix hat drei Sicherheitslücken im TCP-Code im Kernel entdeckt. Durch speziell präparierte SACK-Pakete lässt sich im schlimmsten Fall ein Kernel-Stillstand erzielen. Alle Linux- und FreeBSD-Anwender sollten ihren Kernel aktualisieren oder temporäre Gegenmaßnahmen ergreifen.
https://www.pro-linux.de/news/1/27174/sicherheitsl%C3%BCcken-im-tcp-code-im-kernel.html
Software::Distributionen::Tails
Security updates: Tails 3.14.1 closes security lacks in Firefox and tor browser, PRO LINUX, 21.06.2019
Tails 3.14.1 schließt eine kritische Sicherheitslücke, die Mozilla mit Firefox 67.0.3 behoben hatte. Eine zweite Lücke im Sandboxing-Code der Browser bleibt derzeit offen.
https://www.pro-linux.de/news/1/27176/sicherheitsupdate-tails-3141-schlie%C3%9Ft-kritische-l%C3%BCcke-in-firefox-und-tor-br.html
The best tools for more data control for Apps, trojaner-info.de, 17.07.2019
Apps bieten tolle Funktionen und machen Spaß. Damit eine App aber wegen späterem Datenmissbrauch oder Schadsoftware nicht zum Alptraum wird, sollten Nutzer einige Tipps beherzigen.
Es klingt zwar wie eine Binsenweisheit, wird aber von Nutzern von Smartphones und Tablets kaum beherzigt: "Laden Sie nicht gedankenlos Apps herunter". Wer es dennoch macht, öffnet den Datenkraken freiwillig das Tor zu den eigenen Daten. Mit den richtigen Tools können App-Nutzer wieder die Kontrolle über das Verhalten und den Berechtigungs-Dschungel von Apps zurückgewinnen.
[...] Falls Zweifel an der Vertrauenswürdigkeit der App aufkommen, zunächst im Internet weiterrecherchieren. Auf der offiziellen Webseite des App-Entwicklers sollte ein Impressum vorhanden sein. Die Seriosität der inhaltlichen Bewertungen im Play Store ist wegen des Verdachts von Fake-Postings umstritten. Eine geringe Zahl von Bewertungen und App Downloads könnte jedoch ein deutliches Warnsignal sein.
Ein verlässlicher Indikator für Integrität des Angebots ist dagegen das von Google vergebene Prädikat "Top-Entwickler". Darüber hinaus finden sich im Web Hinweise auf unsichere oder gefährliche Apps, die aktuell im Umlauf sind. Ein regelmäßiger Blick in unsere Rubrik "Aktuelle Bedrohungen" hilft hier zum Beispiel weiter.
Vorsicht bei "App Schnäppchen". Beliebte Apps und Spiele werden nicht selten imitiert und kopiert. Die Nachahmungen werden günstig oder sogar kostenlos angeboten. Gefahr droht von den Imitationen, da hier Schadsoftware bzw. Malwarefunktionen eingebaut sein könnte.
Apps erst nach kritischer Prüfung der App Einstellungen und Berechtigungen installieren. Klicken Sie nicht unbedenklich weiter, wenn die App Einstellungen Zugriff auf Funktionen Ihres Geräts und Ihre persönlichen Daten verlangen — Sie könnten sich damit schutzlos ausliefern. Vor jeder Installation sollten sich App-Anwender fragen, ob eine App tatsächlich die angeforderte Berechtigung für ihren spezifische Nutzen benötigt. Schad-Apps könnten Ihre Berechtigung dazu missbrauchen, kostenpflichtige Nummern anzurufen oder Abos via SMS abzuschließen. Wenn eine Anwendung, die eigentlich nichts mit Telefonieren verbindet, die Erlaubnis zum Telefonieren einfordert, ist Vorsicht geboten. Seriöse App-Anbieter bieten dem Nutzer nicht selten die Möglichkeit an, die App Berechtigungen und App Einstellungen diverser Funktion selbst mitzubestimmen. Fehlen AGBs oder sind diese sehr knapp verfasst, ist nicht zuletzt Skepsis geboten.
[...] Hilfreich sind"Prozessmonitor" Apps. Diese überprüfen, welche Anwendungen aktuell auf Ihrem Smartphone aktiv sind. Falls Akku- und Datenverbrauch einer App den Akkuverbrauch in die Höhe treiben, sollten Sie aufmerksam werden. Die Ursache könnte in einem andauernden Datentransfer liegen — eventuell erfolgt ein Datenaustausch, für den ursprünglich keine Berechtigung erteilt wurde. Alternativ könnte eine bösartige App im Hintergrund einen kostenintensiven Dialer installieren, der Premium-SMS selbstständig versendet und so hohe Kosten wie auch erheblichen finanziellen Schaden verursacht.
[...] Der Netzwerkausrüster Alcatel-Lucent hat in einer 2015 veröffentlichten Malware-Studie festgestellt, dass die Zahl der mobilen Schädlinge deutlich zugenommen hat. So wurden demnach 2014 weltweit 16 Mio. Geräte mit mobiler Malware infiziert, dies entspricht einem Plus von 25 Prozent gegenüber dem Vorjahr. Der Studie zufolge ist Spyware auf mobiler Hardware immer verbreiteter. Damit werden Telefonate abgehört, SMS und E-Mails abgefischt, oder der Standort eines Nutzers und von ihm aufgesuchten Websites festgestellt.
https://www.trojaner-info.de/apps-security/articles/apps-kontrolle-und-schutz-pers%C3%B6nliche-daten.html
Tester in year 2016: Around 5500 connection buildup-attempts into internet per day of MS Windows
In wenigen Stunden schnell mehrere hundert Kontakte zu Internetservern
Windows-Datenschutz auf BSI-Level - so gehts, PC-WELT.de, 17.04.2019
Seit der Einführung von Windows 10 wird das Betriebssystem für seinen mangelnden Datenschutz kritisiert: Es werden zu viele Daten ins Internet gesendet. Nun hat das BSI nachgemessen und aufgedeckt, wie Sie den Datenversand komplett abstellen können.
Kritik am Datenschutz von Windows 10 hagelt es von Sicherheitsexperten, Bloggern und Firmen. Ein PC mit Windows 10, der aktuell keine Aufgabe zu erledigen hat, nimmt dennoch laufend Verbindungen zu Servern im Internet auf. Die Kritik ist nicht neu. Schon Windows XP wurde für seine sogenannte "Call-Home"-Funktionen kritisiert. Damals im Jahr 2001 waren einige Programme, etwa der Windows Media Player, für den unangemeldeten Kontakt ins Internet verantwortlich.
Forstetzung des Berichts mit zugehörigen Sicherheits-Einstellungen: News&Links#MSWindows und
https://www.pcwelt.de/a/bundesamt-fuer-it-sicherheit-bsi-untersucht-sicherheit-von-windows-10,3463082
 Linux: Sperrung aller Konten (System- und Benutzerkonten) außer den Konten "root" und "surfuser" Linux: Sperrung aller Konten (System- und Benutzerkonten) außer den Konten "root" und "surfuser"
Noch einmal empfehlen wir die Kontensperrung ü,ber MCC (drakconf) mit Klick auf Benutzerkonten oder manuell. Zusammen mit der Sperrung für alle Benutzer einschließlich root außer surfuser mit Gruppe surfgruppe sorgenden Linfw3 (und ggfls chown, chmod und ACL (setfacl) auf möglichst viele Verzeichnisse und Dateien von surfuser (und ggfls. Einsatz der shell-Aufrufe (bash) verhindernden und Zugriffsrechte erneut einschräknenden Sandbox firejail, FSE (Systemvollverschlüsselung) und und und... ) erhalten wir damit den perfekten, paranoiden (gleich mehrfachen) Rundumschutz frei von Wartung etc. selbst dann, werden Passwörter (z.B. über Beobachtungs-Satellit mit Blick durchs Fenster) bekanntgegeben bzw. gehackt. Selbst noch so bekannt gewordene Passwörter verhelfen also niemanden weiter, halt nur noch einem selbst. Für den einmaligen KDE-Login nach dem Systemstart sorgt ja pam (el6), für die Sicherheit im Internet Firefox-ESR-52.9 (genauer, bei allen Bedenken, der Onion Router Tor), beide mit den oben empfohlenen Erweiterungen. Diese (Firefox-Erweiterungen) sollten nach ihrer jeweiligen Konfiguration im Browser keinen Kontakt (Verbindungen) mehr aufnehmen. Der lokale DNS-Server pdnsd zusammen mit der lokalen /etc/hosts sichert die DNS-Abfrage (Tor-DNS, tor-resolve). Und auch Der E-Mail-Verkehr erfolgt ja nun bei kmail (OpenPGP oder smime) und Thunderbird (enigmail) über Signierung und die Verbindungs- wie Inhalts-Verschlüsselung mit TLS/SSL und OpenPGP, ggfls. gefolgt von 2-Faktor-Authentifizierung (2FE) mit dem Handy/Smartphone. Die Bildschirmsperre funktioniert danach aber nicht mehr für den Benutzer. Hierzu ist erneut eine Ausnahmeregel in pam ähnlich wie für den KDE-Login erforderlich. Nur noch die einigen wenigen unter root laufenden Kernel-Prozesse aus dem Hause Linus Tovalds bleiben nun (neben Tor im Internet) ein gewisses, minimales Restrisiko. Natürlich kann sogar Konto root gesperrt werden. Zum Entsperren des Kontos von root bedarfs dann aber eines rettenden Systems von außen auf einer eigenen bootfähigen Partition (mit LUKS/dm-crypt (cryptsetup) zum Einbinden der verschlüsselten root-Partition). Ein Sperren der Shell von root mit /sbin/nologin sollte immer erfolgen und genügen. Allerspätestens jetzt läuft der Computer mit selbst "nur Celeron"-Prozessor total mausklick-schnell.
Weitere Studie belegt Lüge "anonymer" Daten, netzpolitik.org, 26.07.2019
Anonyme Daten sind oft gar nicht wirklich anonym, in vielen Datensätzen können Einzelne auch ohne Namen eindeutig identifiziert werden. Mit welcher erstaunlicher Präzision das geht, verdeutlicht eine neue Studie. Viele Firmen und Datenbanken unterlaufen die Datenschutzgrundverordnung.
https://netzpolitik.org/2019/weitere-studie-belegt-luege-anonymer-daten/
Networkk: Howto send hidden packages through Linux systems, PC-WELT.de, 26.01.2020
A netowrk protocol like DNS or ICMP mustn´t do certainly this like it was once made for. A tricky encapsulation allows the data transfer by unusal protocols, in order to bypasses strong firewall rules.
https://www.pcwelt.de/ratgeber/Netzwerk-Versteckte-Pakete-mit-Linux-verschicken-10539971.html
This requires the installation of some software. Linfw3 is hardened against ICMP by default configuration.
Right to encryption
"Encryption is basic right protection!", netzpolitik.org, 27.01.2020
Eine Expertenrunde hat heute im Bundestag über einen Antrag diskutiert, der ein Recht auf Verschlüsselung fordert. Demnach sollen Hintertüren verboten und Ende-zu-Ende-Verschlüsselung standardmäßig implementiert werden. Ein Sachverständiger warnte jedoch vor rechtsfreien Räumen und dem "Going Dark"-Problem.
https://netzpolitik.org/2020/verschluesselung-ist-grundrechtsschutz/
 IT-basic-protection-compendium, trojaner-info.de, 07.02.2020 IT-basic-protection-compendium, trojaner-info.de, 07.02.2020
Das IT-Grundschutz-Kompendium ist die grundlegende Veröffentlichung des IT-Grundschutzes. Zusammen mit den BSI-Standards bildet es die Basis für alle, die sich umfassend mit dem Thema Informationssicherheit befassen möchten. Im Fokus des IT-Grundschutz-Kompendiums stehen die sogenannten IT-Grundschutz-Bausteine. Diese sind in zehn unterschiedliche Schichten aufgeteilt und reichen thematisch von Anwendungen (APP) über Industrielle IT (IND) bis hin zu Sicherheitsmanagement (ISMS).
https://www.trojaner-info.de/business-security/aktuell/it-grundschutz-kompendium.html
NetzDG-Erweiterung
Wie der Staat mit Gummiparagrafen Zugriff auf die Accounts der Bürger:innen erhalten will, netzpolitik.org, 17.12.2019
Die große Koalition nutzt den Kampf gegen Rechtsextremismus, um kräftig an der Überwachungsschraube zu drehen: Soziale Netzwerke sollen bald bestimmte Straftaten automatisch ans Bundeskriminalamt melden. Darüber hinaus sollen alle Anbieter von Telemediendiensten Daten ihrer Nutzer:innen an Polizei und Geheimdienste herausgeben müssen.
https://netzpolitik.org/2019/wie-der-staat-mit-gummiparagrafen-zugriff-auf-die-accounts-der-buergerinnen-erhalten-will/
 Gesetzesentwurf: Justiz will Zugriff auf Facebook, Twitter und E-Mail, PC-WELT.de, 16.12.2019 Gesetzesentwurf: Justiz will Zugriff auf Facebook, Twitter und E-Mail, PC-WELT.de, 16.12.2019
Ein Gesetzesentwurf sieht für Strafverfolgungsbehörden den Zugriff auf soziale Netzwerke, E-Mail und andere Telemediendienste vor.
https://www.pcwelt.de/news/Gesetzesentwurf-Justiz-will-Zugriff-auf-Facebook-Twitter-und-E-Mail-10724344.html
US-Regierung drängt Unternehmen zu verstärktem Datenaustausch, Tagesschau, 14.02.2015
Obama beim Gipfeltreffen zur Datensicherheit beim Kampf gegen Cyberkriminalität: Ein "Gipfel", bei dem einige fehlten, Tagesschau, 14.02.2015
Barack Obama hatte zum "Gipfel für Cybersicherheit" geladen, doch die Chefs einiger der wichtigsten der Branche kamen nicht. Denn während die US-Regierung vor der Gefahr durch Hacker warnt, sehen Internetkonzerne noch eine ganz andere Bedrohung: die Regierung.
US-Präsident Barack Obama hat die großen Internetfirmen im Silicon Valley zur Zusammenarbeit mit dem Staat im Kampf gegen Hackerangriffe aufgerufen. "Das muss eine gemeinsame Mission sein", sagte Obama beim "Summit on Cybersecurity" und betonte, dies sei eine Frage der nationalen Sicherheit. Ein großer Teil der Computernetze und der kritischen Infrastruktur sei im Besitz von Privatfirmen. Daher könne die Regierung nicht allein für die Sicherheit im Internet sorgen, so Obama. "Aber Tatsache ist, dass der Privatsektor es auch nicht alleine tun kann, weil die Regierung oft die aktuellsten Informationen über neue Bedrohungen hat."
Heimatschutzministerium und Firmen sollen zusammenarbeiten
Er unterzeichnete ein Dekret für einen besseren Informationsaustausch zwischen Behörden und Unternehmen, um Cyberattacken von ausländischen Geheimdiensten, kriminellen Vereinigungen oder Terroristen abzuwehren. Davon hatte es im vergangenen Jahr in den USA gleich mehrere besonders spektakuläre gegeben: auf den Handelsriesen Target, die Baumarktkette Home Depot, das Filmstudio Sony und zuletzt auf Anthem, einen der größten Krankenversicherer der USA.
Das Dekret ermöglicht eine engere Kooperation zwischen dem Heimatschutzministerium und Unternehmen, die einfacher an vertrauliche Informationen über die Gefahrenlage im Cyberspace kommen sollen.
Es wird offenbar immer schwieriger, Geheimnisse zu bewahren. Selbst im heimischen Wohnzimmer ist man vor ungewollten Lauschattacken nicht mehr sicher. Wunder Punkt: die Spracherkennung im Smart-TV. Datenschützer sind alarmiert. "Big Samsung is watching you": Wem der Umstand, die TV-Lautstärke wie ein Technik-Neandertaler per Knopfdruck zu regeln ein Graus ist, der greift seit den neuen Smart-TV-Modellen oft und gerne auf die Sprachsteuerung zurück. Dumm nur, wenn diese neben den Befehlen auch jedes andere im heimischen Wohnzimmer gesprochene Wort registrieren und aufzeichnen kann, wie nun aus den Lizenzvereinbarungen des Herstellers Samsung hervorgeht. Darin heißt es: "Bitte seien Sie sich bewusst, dass wenn Sie persönliche oder sensible Informationen sagen, diese zu den Inhalten zählen, die durch die Spracherkennung aufgezeichnet und an dritte Parteien weitergeleitet werden." Datenschützer dürften über diese Entwicklung alles andere als begeistert sein. Dabei werden Erinnerungen an Microsoft wach, das mit der Markteinführung ihrer Konsole "Xbox One" die für die Bewegungssteuerung notwendige Kamera zunächst stets aktiviert lassen wollte. Erst nach einem medialen Sturm der Entrüstung ließ das Unternehmen von diesem Plan ab.
 Hintertüren vs. Trojaner Hintertüren vs. Trojaner
Europol prüft Möglichkeiten gegen Ende-zu-Ende-Verschlüsselung, netzpolitik.org, 13.02.2020
Das Bundeskriminalamt nutzt eine "Entschlüsselungsplattform" bei Europol, um auf verschlüsselte Datenträger zuzugreifen. Die Anlage gehört zu einem "Innovationslabor" und wird derzeit mit neuer Technik ausgestattet. Demnächst entscheidet die EU-Kommission, ob Europol auch die Entschlüsselung sicherer Verbindungen erledigen soll.
https://netzpolitik.org/2020/europol-prueft-moeglichkeiten-gegen-ende-zu-ende-verschluesselung/
Sind Daten das neue Öl?, trojaner-info.de, 13.11.2
 Gesetzesentwurf: Justiz will Zugriff auf Facebook, Twitter und E-Mail, PC-WELT.de, 16.12.2019 Gesetzesentwurf: Justiz will Zugriff auf Facebook, Twitter und E-Mail, PC-WELT.de, 16.12.2019
Ein Gesetzesentwurf sieht für Strafverfolgungsbehörden den Zugriff auf soziale Netzwerke, E-Mail und andere Telemediendienste vor.
https://www.pcwelt.de/news/Gesetzesentwurf-Justiz-will-Zugriff-auf-Facebook-Twitter-und-E-Mail-10724344.html019
Der steigende Wert der Daten führt dazu, dass sie als das "neue Öl" gehandelt werden. Jedes Unternehmen generiert einen Fundus an Daten, doch nur die wenigsten Unternehmen können behaupten, dass sie auf einer "großen Ölquelle" sitzen.
https://www.trojaner-info.de/business-security/aktuell/sind-daten-das-neue-oel.html
Netzwerkdurchsetzungsgesetz
Bundesregierung beschließt Pflicht zur Passwortherausgabe, netzpolitik.org, 19.02.2020
Nach dem antisemitischen Attentat von Halle und dem Mord am CDU-Politiker Walter Lübcke steht die Bundesregierung unter Druck, mehr gegen Rechtsextreme und Rechtsterroristen zu tun. Doch eine heute von der Regierung verabschiedete umstrittene Gesetzesänderung droht neue Probleme zu schaffen.
https://netzpolitik.org/2020/bundesregierung-beschliesst-pflicht-zur-passwortherausgabe/
 Facebook fragte Banken nach Nutzerdaten, PC-WELT.de, 07.08.2018 Facebook fragte Banken nach Nutzerdaten, PC-WELT.de, 07.08.2018
Facebook hat laut einem Medienbericht bei mehreren großen US-Banken angefragt, um von diesen Kundendaten zu bekommen.
https://www.pcwelt.de/a/facebook-fragte-banken-nach-nutzerdaten,3451879 ä
 Google kennt Ihre Online-Einkäufe via Gmail-Tracking, PC-WELT.de, 20.05.2019 Google kennt Ihre Online-Einkäufe via Gmail-Tracking, PC-WELT.de, 20.05.2019
Google ist in der Lage, alle Online-Einkäufe der Nutzer zu tracken, auch wenn diese nicht via Google getätigt wurden.
https://www.pcwelt.de/news/Google-kennt-Ihre-Online-Einkaeufe-via-Gmail-Tracking-10594891.html
 Google trackt Mastercard-Nutzer Google trackt Mastercard-Nutzer
Bericht: Google verfolgt Nutzer offline mit Mastercard-Daten, PC-WELT.de, 31.08.2018
Laut einem Bloomberg-Bericht kauft Google Kunden-Daten von Mastercard, um Kunden auch offline zu tracken.
Wie die News-Plattform Bloomberg berichtet, ist Google wohl einen Deal mit Mastercard eingegangen, um Offline-Einkäufe von Kreditkarten mit Nutzerkonten zu verknüpfen. Für die Daten von 70 Prozent aller Mastercard-Inhaber der USA aus dem Jahr 2017 soll Google demnach mehrere Millionen US-Dollar gezahlt haben. Darin enthalten sind Transaktionsdaten, die für Google ausreichen, um Personen eindeutig zu identifizieren.
[...] Laut den Angaben von Bloomberg sind sich aber beide Unternehmen wohl darüber bewusst, dass hier jede Menge Datenschutz-Probleme auftauchen. Der Deal wurde daher nur zögerlich eingegangen. Vier Jahre wurde zwischen den zwei Unternehmen verhandelt, bevor der Deal abgeschlossen wurde. Mastercard-Inhaber wurden darüber hinaus nicht über das Tracking informiert. Zwar gäbe es in Googles Web-Console eine Möglichkeit das Tracking zu untersagen, jedoch ist dies für den Großteil der Nutzer nicht ersichtlich.
[...] Der Bloomberg-Bericht bezieht sich nur auf die USA. Ob Google in weiteren Ländern ähnlich vorgeht, geht aus dem Artikel nicht hervor. In den Vereinigten Staaten machen Umsätze mit Mastercard rund 25 Prozent des gesamten Umsatzes aus.
https://www.pcwelt.de/a/bericht-google-verfolgt-nutzer-offline-mit-mastercard-daten,3452190
Zur Wiederholung: Immer wieder unmittelbar nach unseren Einkäufen bei eBay erhielten wir als treue E-Bay-Kunden E-Mails von Amazon mit verseuchten Binärdateien..., Anmerkung, Gooken, Jahr 2017.
Eine denkbare Erklärung liefern bald folgende Berichte über siehe PayPal.
 Google kennt Ihre Online-Einkäufe via Gmail-Tracking, PC-WELT.de, 20.05.2019 Google kennt Ihre Online-Einkäufe via Gmail-Tracking, PC-WELT.de, 20.05.2019
Google ist in der Lage, alle Online-Einkäufe der Nutzer zu tracken, auch wenn diese nicht via Google getätigt wurden.
https://www.pcwelt.de/news/Google-kennt-Ihre-Online-Einkaeufe-via-Gmail-Tracking-10594891.html
SAP schließt Sicherheitslücken, trojaner-info.de, 14.02.2020
Das Unternehmen hat nun im Februar drei Sicherheitslücken mit "hoch"-Einstufung geschlossen. Sie stecken im SAP Host Agent sowie in Landscape Management zum Managen von SAP-Betriebsabläufen und ermöglichen unter bestimmten Voraussetzungen Denial-of-Service-Angriffe sowie das Umgehen von Sicherheitsvorkehrungen durch fehlende Validierung von Eingaben.
https://www.trojaner-info.de/business-security/aktuell/sap-schliesst-sicherheitsluecken.html
 Deutsche Bank in rund 1200 Verfahren verwickelt, tagesschau.de, 22.05.2014 Deutsche Bank in rund 1200 Verfahren verwickelt, tagesschau.de, 22.05.2014
Der Bankenskandal u.a. der Deutschen Bank, hier klicken
 Ärger mit Online-Bezahldienst Ärger mit Online-Bezahldienst
Verkäufer aufgepasst! Mit diesem Trick zocken Betrüger über Paypal ab, STERN.de, 09.09.2017
Paypal gilt als eins der sichersten Online-Bezahlsysteme weltweit. Trotzdem schaffen es Betrüger, Verkäufer über den Dienst abzuzocken. Mit einem einfachen Trick, den jeder kennen sollte, der den Bezahldienst für seine Geschäfte nutzt.
http://www.stern.de/tv/verkaeufer-aufgepasst--mit-diesem-trick-zocken-betrueger-ueber-paypal-ab-7607550.html
Vorratsdatenspeicherung
Bundesregierung plädiert für Datensammlung durch Geheimdienste, netzpolitik.org, 11.02.2020
Die Bundesregierung liefert vor dem EU-Gerichtshof Argumente für die massenhafte Speicherung von Kommunikationsdaten. Als Begründung zieht sie ausgerechnet die ePrivacy-Richtlinie heran.
https://netzpolitik.org/2020/bundesregierung-plaediert-fuer-datensammlung-durch-geheimdienste/
 ESET warnt vor Identitätsdiebstahl im Internet, trojaner-info.de, 12.02.2019 ESET warnt vor Identitätsdiebstahl im Internet, trojaner-info.de, 12.02.2019
Kriminelle stehlen vollautomatisiert persönliche Daten aus sozialen Netzwerken.
Immer häufiger geben sich Cyberkriminelle nicht mit dem Diebstahl einzelner Datensätze zufrieden. Sie rauben Internetnutzern gleich ganze Identitäten und missbrauchen sie für ihre Zwecke. In den sozialen Medien finden sie alles: vom Profilbild über den Job bis hin zum Wohnort und den Hobbies ihres Opfers. Auch Privatpersonen geraten zunehmend ins Visier der Diebe, warnt der europäische IT-Security-Hersteller Eset.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/eset-warnt-vor-identitaetsdiebstahl-im-internet.html
 Identitätsdiebstahl und seine Folgen, trojaner-info.de, 14.10.2019 Identitätsdiebstahl und seine Folgen, trojaner-info.de, 14.10.2019
Mithilfe weniger persönlicher Daten können Kriminelle problemlos Onlinekäufe in Ihrem Namen tätigen, sie können Geld vom Konto abbuchen oder andere illegale Geschäfte durchführen. Deswegen: Passen Sie auf, was Sie wem preisgeben.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/identitaetsdiebstahl-und-seine-folgen.html
Privoxy, Tor and Privoxy
Risks upon HTTPS-encrypted connections, fabiankeil.de
Verschlüsselte Verbindungen kann Privoxy nur weiterleiten, Filter können auf sie nicht angewendet werden, da der Inhalt Privoxy nicht im Klartext passiert.
Um Privoxy zu umgehen könnte eine unverschlüsselte Webseite Bilder oder CSS-Dateien über eine verschlüsselte Verbindung einbinden, verschlüsselte Verbindungen sollten daher mit der Aktion +limit-connect{,} generell gesperrt und nur für vertrauenswürdige Websites freigeschaltet werden.
Solange man bei einer Website nicht absichtlich persönlichen Daten hinterlässt, etwa um einen Online-Shop zu nutzen, gibt es keinen Grund HTTPS einzusetzen. Die Verbindung wurde bereits über Tor anonymisiert und HTTPS wäre dazu auch gar nicht in der Lage, da Start- und End-Punkt der Verbindung im Klartext gesendet werden.
Wenn man einer Website weit genug vertraut persönliche Daten zu hinterlassen, gibt es wenig wovor Privoxy noch schützen könnte: im Vergleich zu Kontodaten oder Passwörtern sind Cookies und Spionage-Pixel nicht der Rede wert.
https://www.fabiankeil.de/privoxy-anleitung/
Tor, The Anonymizing Network - Äh, ... Looking out for Good Tor Nodes now (entry-, middle- and exit-nodes / relais)..., text 2019 by Gooken
Von News&Links#Der_Überwachungsskandal:_NSA_GHCQ_&CO
It´s just ridiculous
The small company got totally IT-secured - but only ingrattitude results from it ( in the background compounds like CIA, downturn of company profit ) !
NSA, CIA & Co.
Another kind of thinking
"The man with the good ol´ cash is always Mr. Right" ("Living in a material world" from song: Material Girl by Madonna, 80er Jahre)
Job and carreer for net-, system- and database-administrators
Why the comopany might already belong other ones
Beginning with system-administrator "root" (root-rights over all): Owner- and acess-rights, exploit codes: With all the authority, insights into and knowledge about the company doing the job for the most weightful company & Co.:
 Chefsache Netz- und Systemadministration? Chefsache Netz- und Systemadministration?
6 Tipps zum Schutz vor diebischen IT-Admins, PC-WELT, 10.12.2017
Hin und wieder begehen Mitarbeiter Datendiebstahl im eigenen Unternehmen. So schützen Sie sich.
https://www.pcwelt.de/ratgeber/Ratgeber-Datensicherheit-6-Tipps-zum-Schutz-vor-diebischen-IT-Admins-1340729.html
Schwachstelle Mensch: Die fiesen Tricks und Methoden des Social Engineering, trojaner-info.de, 06.03.2018
Soziale Cyber-Manipulation nutzt die Gutmütigkeit von Menschen
Der Mensch! Er ist eines der wichtigsten und meist unterschätzten IT- und Cyber-Security-Risiken für Business Security. Mitarbeiter erzeugen aus Unvorsichtigkeit oder Good-will-Mentalität Sicherheitslücken und werden so auch ohne offensichtliche Erpressung zum freiwilligen Einfallstor für die Gefahren des sogenannten Social Engineering. Erfahren Sie mehr über die wichtigsten psychologischen Instrumente, die bei der Cyber-Manipulation des Menschen Anwendung finden, und über typische Bauerntricks, mit denen Mitarbeiter von Unternehmen ausgetrickst werden …
https://www.trojaner-info.de/business-security/schutz-vor-social-engineering/articles/die-methoden-des-social-engineering.html
Cyberkriminelle auf frische Tat ertappen!, trojaner-info.de, 23.10.2019
Wenn man an Cyberkriminalität denkt, denkt man oft an Hackerangriffe, die von außen stattfinden. Doch die Gefahr durch Datenlecks aus dem Inneren einer Organisation ist mindestens genauso groß. Laut aktuellem Insider Threat Index sollen in Europa Insider-Bedrohungen zwar leicht gesunken sein, aber immer noch sind 38 Prozent der Sicherheitsvorfälle auf die direkte Bedrohung durch böswillige oder unachtsame Mitarbeiter zurückzuführen.
https://www.trojaner-info.de/business-security/aktuell/cyberkriminelle-auf-frische-tat-ertappen.html
So groß ist die Bedrohung, PC WELT, 01.10.2017
Laut der aktuellen Studie "Industriespionage 2012" ist bereits über die Hälfte aller Unternehmen in Deutschland Opfer von Industriespionage geworden. Schätzungen gehen dahin, dass der finanzielle Schaden für deutsche Unternehmen durch Industriespionage bei etwa 4,2 Miliarden Euro pro Jahr liegt. Das ist ein Anstieg um 50 Prozent seit der letzten Studie 2007.
"Die Hackerangriffe auf Sony, Google, die Nato oder den IWF zeigen, dass die Cyber-Kriminellen Ziele und Taktiken radikalisiert haben. Diese veränderte Bedrohungslage macht ein grundlegendes Umdenken in Bezug auf Informationsschutz, speziell die IT-Sicherheit, Mitarbeiterbindung und die Grundregeln für den Wissensaustausch erforderlich", sagt Christian Schaaf, Studienleiter und Geschäftsführer von Corporate Trust.
"Wenn es um den Schutz des eigenen Know-how geht, ist es zwar wichtig, ein vernünftiges Bewusstsein für die Risiken zu haben, es ist jedoch ebenso wichtig, ein gesundes Vertrauen in die eigenen Sicherheitsvorkehrungen und die Zuverlässigkeit seiner Mitarbeiter (wie insbes. Netz- und Systemadministratoren) zu setzen", so Schaaf. Er mahnt zum richtigen Augenmaß und rät zu bedarfsgerechten Maßnahmen mit dem Verweis, dass zu viel Sicherheit unwirtschaftlich und zu wenig Sicherheit fahrlässig sei. Man sollte sich als Unternehmen auf jeden Fall vor allen bekannten und neuen Bedrohungen wappnen, damit man nicht seine Stellung auf dem internationalen Markt verliert, sondern diese behält beziehungsweise stärkt. Schaaf merkt aber abschließend an: "Sicherheit sollte ermöglichen und nicht verhindern. Daher ist es wichtig, die aktuellen Risiken zu kennen, um nur dort in Sicherheit zu investieren, wo es tatsächlich nötig ist."
https://www.pcwelt.de/ratgeber/Das_grosse_Kompendium_zur_Netzwerksicherheit-Netzwerke-7811930.html
Social Engineering - Angriffe von innen und menschliche Schwächen, PC-WELT.de, 01.10.2017
Die wohl größte Gefahr kommt aber aus den eigenen Reihen. Es sind oft die eigenen Mitarbeiter, die für den Verlust von wichtigen Datenbeständen verantwortlich sind. Doch geschieht dies nicht nur, weil Mitarbeiter aus Vorsatz auf Datenklau gehen, sondern vielmehr weil sie geschickt von Angreifern manipuliert werden. Diese Methode, Social Engineering genannt, greift das System von innen an und muss keine Firewalls oder Passwörter umgehen, um Zugriff auf Daten zu erhalten. So ist es denkbar, dass sich ein Angreifer bei einem Telefonat als technischer Mitarbeiter ausgibt und für Reparaturzwecke am System vom Mitarbeiter die Herausgabe eines Passwortes verlangt. Auch das Platzieren oder Verschenken von USB-Sticks im Unternehmen ist denkbar. Sollten einige präparierte USB-Sticks von Mitarbeitern an Arbeitsrechnern angeschlossen werden, könnten so bestehende Sicherheitsvorkehrungen umgangen werden und das gesamte Netzwerk infiltriert werden. Nach all diesen Erkenntnissen ist es also extrem wichtig nicht nur auf der technischen Seite bestens vor einem bevorstehenden Angriff geschützt zu sein, sondern man sollte auch die menschliche Komponente als mögliche Schwachstelle nicht vernachlässigen und durch Sensibilisierung und Schulungen der Mitarbeiter diese Schwachstelle auf ein Minimum reduzieren.
Physische Schutzmaßnahmen
Serverräume sind das Herzstück eines Firmennetzwerks und sollten besonders geschützt sein. Schützt man das Herzstück nicht ausreichend, ist es für fachkundige Angreifer kein Problem sich Zugang zu sämtlichen Daten sowie jeglichem Datenverkehr zu verschaffen. Die Serverräume sollten stets verschlossen und der Zugang zu ihnen sollte nur für einen eingeschränkten Personenkreis möglich sein, der die administrativen Rechte besitzt.
Es sollte der Zugang zum Rechenzentrum mit einem elektronischen Zahlenschloss, Magnetkarten oder durch Sicherheitskräfte zusätzlich gesichert sein. Am besten eignet sich eine Kombination aus mehreren Authentifizierungsmethoden, zum Beispiel eine Kombination aus Passwort, Magnetkarte und einem biometrischen Abgleich, wie einem Fingerabdruck. Somit kann ziemlich sicher gewährleistet werden, dass sich nur autorisierte Personen Zugang verschaffen.
Weiterhin ist es wichtig, die Netzstruktur zu sichern. Hubs und Switches sollten sich immer in abgeschlossen Schränken oder hinter verschlossen Türen befinden, damit sich potenzielle Angreifer nicht über diese Zugriff verschaffen können. Um das Anzapfen oder den Zugriff auf Datenanschlüsse zu verhindern, sollten alle Kabel in Wänden und Decken verlegt werden. Außerdem sollten Drahtlos-Netzwerke die höchste WAP2-Verschlüsselung besitzen und die standardmäßigen SSID geändert werden.
Um den Diebstahl der Hardware zu verhindern, sollten die Gehäuse der Computer abgeschlossen werden und gegebenenfalls ein Sicherheitskabel installiert werden, um das Mitnehmen dieser zu verhindern. Auf den Rechnern sollte es keine Möglichkeit geben, die Konfiguration des BIOS zu verändern. Das Booten von externen Massenspeichern, wie USB-Sticks sollte ebenfalls nicht möglich sein. Jedes Anwenderprofil sollte außerdem durch ein individuelles Passwort geschützt sein, welches in regelmäßigen Abständen geändert werden muss. Ein weiterer aber kostspieliger Schutzmechanismus ist die Installation von Bewegungssensoren in Verbindung mit Kameras in Büro- oder Serverräumen. Sie dienen zum zusätzlichen Schutz und schrecken potentielle Angreifer ab.
https://www.pcwelt.de/ratgeber/Netzwerke-Social_Engineering_-_Angriffe_von_Innen_und_menschliche_Schwaechen-7812014.html
Weak Point Human"
Kaspersky auf der it-sa 2019
Das Kaspersky-Programm auf der it-sa 2019
Nur die Kombination aus zuverlässigen "Next Generation"-Technologien, Cybersecurity Services und einem nachhaltigen Sicherheitsbewusstsein der Mitarbeiter schützt die Infrastruktur und sorgt dafür, dass nicht der Mensch selbst zum Risikofaktor wird, wie Kaspersky auf der it-sa 2019 demonstriert.
https://www.trojaner-info.de/business-security/aktuell/kaspersky-auf-der-it-sa-2019.html
 Partial "solution to resp. help for" the matter "chief issue - administration" (at least possible for UNIX/Linux-systems): isolation of the (even in future) general-authorized company-owner and superuser Root with belonging strong restricted group rights, setting the login-shell "/sbin/nologin" for root (while an access to root is still possible by MCC resp. the system-control-center or from the outside like through rescue-systems and the installation and update of software-packets is not possible anymore), the forbid of Chrooting (chroot), full system encryption, the disclosure (super-/top-secrecy) of the root-password, PAM-noroot-login (added belonging rule), the creation of sub-administrator-accounts with department-wise owner-, access-righs and allowed views, Firewall Linfw3 with its blocking of user and groups like even root (user-ID (uid) 0 and group-ID (gid) 0 ), followed by the creation of the other single group- and user-accounts, deinstallation of sudo, performing each method introduced here in this excurs like anonymized user-agent-browser-specification, SUID-sandbox firejail for browser etc, localized DNS query through the protective mask /etc/hosts, local dns cache pdnsd and anonymizing tor-resolve (TOR-DNS, TOR), TOR with VPN, ... Partial "solution to resp. help for" the matter "chief issue - administration" (at least possible for UNIX/Linux-systems): isolation of the (even in future) general-authorized company-owner and superuser Root with belonging strong restricted group rights, setting the login-shell "/sbin/nologin" for root (while an access to root is still possible by MCC resp. the system-control-center or from the outside like through rescue-systems and the installation and update of software-packets is not possible anymore), the forbid of Chrooting (chroot), full system encryption, the disclosure (super-/top-secrecy) of the root-password, PAM-noroot-login (added belonging rule), the creation of sub-administrator-accounts with department-wise owner-, access-righs and allowed views, Firewall Linfw3 with its blocking of user and groups like even root (user-ID (uid) 0 and group-ID (gid) 0 ), followed by the creation of the other single group- and user-accounts, deinstallation of sudo, performing each method introduced here in this excurs like anonymized user-agent-browser-specification, SUID-sandbox firejail for browser etc, localized DNS query through the protective mask /etc/hosts, local dns cache pdnsd and anonymizing tor-resolve (TOR-DNS, TOR), TOR with VPN, ...
Munichs ex-OB: Ballmer jumped angrily through his buro because of the change to Linux, PC-WELT.de, 12.11.2019
https://www.pcwelt.de/news/Muenchens-Ex-OB-Ballmer-sprang-durchs-Buero-wegen-Wechsel-zu-Linux-10700234.html
Münchens Ex-OB: Ballmer sprang durchs Büro wegen Wechsel zu Linux, PC-WELT.de, 12.11.2019
Münchens Ex-OB Christian Ude plaudert aus dem Nähkästchen: Als München von Windows zu Linux wechselte, sprang Steve Ballmer durch Udes Büro. Bill Gates saß fassungslos im Auto mit Ude. Und ausgerechnet eine Grüne war dann plötzlich für die Rückkehr zum Monopolisten.
[...] Das rief den damaligen Microsoft-CEO Steve Ballmer auf den Plan. Er unterbrach seinen Ski-Urlaub in der Schweiz und flog eigens nach München, um Ude umzustimmen. Ballmer sprang Ude zufolge in dessen Amtszimmer herum, pries die Schönheit Münchens - und senkte mehrmals die Kosten für den Umstieg. Um 35 Prozent war das letzte Angebot Ballmers schließlich günstiger geworden - doch Ude blieb hart.
Daran konnte auch Bill Gates nichts ändern, der ebenfalls mit Ude während einer Autofahrt zum Flughafen sprach. Gates verstand Udes Wunsch nach Unabhängigkeit offensichtlich überhaupt nicht und war fassungslos.
[...] Zur Rückwärtsrolle, die ausgerechnet Udes Parteigenosse und Nachfolger als OB Dieter Reiter durchführte, äußert sich Ude ebenfalls. Demnach war es überraschenderweise die damalige OB-Kandidatin der Grünen, die zurück zum Monopolisten wollte. Die Grünen folgte ihrer OB-Kandidatin allerdings nicht und hielten Limux die Treue. Nicht so Reiter: Er trieb als neuer Oberbürgermeister von München zusammen mit seinem Koalitionspartner CSU (die bereits 2003 gegen Linux und für Windows war) die Rückkehr zu Windows voran. Datensicherheit und Unabhängigkeit spielten plötzlich keine Rolle mehr, so Ude. Von den Kosten ganz zu schweigen.
https://www.pcwelt.de/news/Muenchens-Ex-OB-Ballmer-sprang-durchs-Buero-wegen-Wechsel-zu-Linux-10700234.html
 Tester im Jahr 2016: Rund 5500 Verbindungsversuche pro Tag von MS Windows 10 ins Internet Tester im Jahr 2016: Rund 5500 Verbindungsversuche pro Tag von MS Windows 10 ins Internet
In wenigen Stunden schnell mehrere hundert Kontakte zu Internetservern
Windows-Datenschutz auf BSI-Level - so gehts, PC-WELT.de, 17.04.2019
Seit der Einführung von Windows 10 wird das Betriebssystem für seinen mangelnden Datenschutz kritisiert: Es werden zu viele Daten ins Internet gesendet. Nun hat das BSI nachgemessen und aufgedeckt, wie Sie den Datenversand komplett abstellen können.
Kritik am Datenschutz von Windows 10 hagelt es von Sicherheitsexperten, Bloggern und Firmen. Ein PC mit Windows 10, der aktuell keine Aufgabe zu erledigen hat, nimmt dennoch laufend Verbindungen zu Servern im Internet auf. Die Kritik ist nicht neu. Schon Windows XP wurde für seine sogenannte "Call-Home"-Funktionen kritisiert. Damals im Jahr 2001 waren einige Programme, etwa der Windows Media Player, für den unangemeldeten Kontakt ins Internet verantwortlich.
Was sich mit Windows 10 im Jahr 2015 geändert hat, war die schiere Menge an Verbindungen.
Fortsetzung des Berichts und Maßnahmen: in Kürze!
Immer mehr Unternehmen schnüffeln uns aus, digitalcourage.de, gesehen am 09.09.2018
Suchmaschinen, soziale Netzwerke und andere "Gratis"-Dienste sammeln rund um die Uhr persönliche Daten. Daraus erstellen sie Verhaltensprofile, mit denen sie Profit machen: Die Daten werden verkauft an Versicherungen oder Werbeunternehmen. Auf diese Weise verletzten Datenkraken an vielen Stellen unsere Persönlichkeitsrechte, in dem sie ohne Zustimmung Daten auswerten, weiterverkaufen oder auch an Geheimdienste weiterleiten. Sie rauben uns die Kontrolle über unsere Daten und schränken die freie Kommunikation im Internet ein. Sie gehen sogar soweit, dass sie behaupten zu wissen, was wir brauchen, fühlen und denken. Einige Datenkraken verdienen ihr Geld mit der Bewertung von Menschen. Dieses Vorgehen wird "Scoring" genannt. Wer zum Beispiel im "richtigen" Stadtteil lebt, bekommt eine Ware auf Rechnung. Eine andere Person nicht. Auch Google ist nicht neutral und zeigt personalisierte Suchergebnisse an. Datenkraken behandeln Menschen nicht gleichwertig und diskriminieren sie. Darum klärt Digitalcourage über Datenkraken auf. An besonders bissige Exemplare verleihen wir jährlich die Big-Brother-Awards, .http://bigbrotherawards.de/
Hintergrund zu kommerziellen Datenkraken
Fortsetzung in Kürze weiter unten
Unternehmen sammeln mehr Daten, als sie verarbeiten können
Jason Hart, Vice President und CTO für Data Protection bei Gemalto, trojaner-info.de, 13.07.2018
Gemalto, das weltweit führende Unternehmen im Bereich der digitalen Sicherheit, gab aktuell die Ergebnisse des jährlichen Data Security Confidence Index (DSCI) für 2018 bekannt. Unter anderem geben zwei Drittel (65 Prozent) der Unternehmen zu, dass sie nicht in der Lage sind, alle von ihnen gesammelten Daten zu analysieren. Nur die Hälfte (54 Prozent) weiß, wo alle ihre sensiblen Daten gespeichert sind. Über zwei Drittel der Organisationen (68 Prozent) müssen eingestehen, dass sie nicht alle Verfahren im Einklang mit den Datenschutzgesetzen, wie der Datenschutz-Grundverordnung (DSGVO), durchführen.
https://www.trojaner-info.de/business-security/aktuell/data-security-confidence-index-von-gemalto-zeigt-unternehmen-sammeln-mehr-daten-als-sie-verarbeiten-koennen.html
Fragwürdige Auszeichnung: Datenschutz-Negativpreise für Microsoft und Amazon, CHIP/DPA, 22.04.2018
Für Verstöße gegen den Datenschutz vergibt ein Verein aus Bielefeld jedes Jahr einen Negativpreis. Diesmal trifft es auch Microsoft und Amazon. "Big Brother Awards" gibt es 2018 auch für Software, mit deren Hilfe Angestellte und Flüchtlinge analysiert werden.
Microsoft Deutschland erhält in diesem Jahr den "Big Brother Award". Der von Datenschutz-Aktivisten verliehene Negativpreis für Datensammlung und Verletzungen der Privatsphäre geht in der Kategorie Technik an das Software-Unternehmen mit Deutschlandsitz in München. Der Bielefelder Verein Digitalcourage wirft Microsoft vor, mit dem Betriebssystem Windows 10 über das Internet Diagnose-Daten (Telemetrie) zu sammeln. Das Problem: Selbst erfahrene Nutzer könnten den Datenfluss nicht abschalten.
Microsoft hatte die Kritik im Vorfeld zurückgewiesen und kam nicht zur Preisvergabe am Freitagabend ins Bielefelder Stadttheater. Dem Unternehmen komme es nicht auf die Abschöpfung der Kundendaten an, sondern es nutze die Telemetrie zur Verbesserung des Produkts, hieß es aus München. 2002 war Microsoft bereits Preisträger. Der Preis wurde zum 18. Mal an Politiker, Unternehmen oder Organisationen verliehen, die nach Ansicht der Datenschützer besonders unverantwortlich mit Daten anderer umgehen.
http://www.chip.de/news/Fragwuerdige-Auszeichnung-Datenschutz-Negativpreise-fuer-Microsoft-und-Amazon_138155040.html
 There still might exist databases (almost SQL) within a webside´s code, so a risk during the surfing remains, that means, listed Firefox-extensions are able now to filter out all tracking scripts - but there are still databasis within the code of a webside like in it´s Perl- and PHP-sections. They still do exist and nothing can keep them to store as much as exchange data like (we hope anonymized) IP and the (we hope faked) UserAgent-specification of the browser and, in our opinion, we are sorry to say, that nothing can be done against it! There still might exist databases (almost SQL) within a webside´s code, so a risk during the surfing remains, that means, listed Firefox-extensions are able now to filter out all tracking scripts - but there are still databasis within the code of a webside like in it´s Perl- and PHP-sections. They still do exist and nothing can keep them to store as much as exchange data like (we hope anonymized) IP and the (we hope faked) UserAgent-specification of the browser and, in our opinion, we are sorry to say, that nothing can be done against it!
 Kleines Einmaleins der digitalen Selbstverteidigung Kleines Einmaleins der digitalen Selbstverteidigung
Wie man die Datensammler im Internet in den Griff bekommt: Wir tragen hier einige Basics zum eigenen Schutz zusammen und nennen Alternativen zu den Diensten der großen Konzerne. Ein Überblick,
netzpolitik.org, 30.04.2018 um 15:50 Uhr - Alexander Fanta, Ingo Dachwitz, Tomas Rudl - in Nutzerrechte - 76 Ergänzungen
Die Großen Fünf abwehren? Designer Oliver Hinzmann hat das für uns illustriert. CC-BY-SA 4.0 Oliver Hinzmann
Der Datenskandal um Facebook und Cambridge Analytica war nicht der erste und wird auch nicht der letzte sein. Immer mehr Menschen realisieren, dass die alltägliche Sorglosigkeit mit der eigenen digitalen Kommunikation Konsequenzen nach sich zieht: Staatliche Akteure wollen in ihrem Kontrollwahn auch das letzte Detail aus dem Leben der Menschen wissen, Datenkonzerne schlagen Kapital aus den persönlichen Informationen ihrer Kundinnen und Kriminelle suchen Schwachstellen für Betrug, Erpressung, Mobbing. Solange Politik und Tech-Industrie nicht umdenken, müssen Nutzerinnen ihren Schutz deshalb weitgehend selbst in die Hand nehmen. Wir haben dafür ein paar einfach Tipps zusammengestellt.
Vorab: Unterschiedliche Gefahrensituationen erfordern unterschiedliche Maßnahmen. Die hier gesammelten Anregungen können Menschen helfen, Datensammlern das Leben schwerer zu machen. Sie wären aber etwa für Aktivistinnen in autoritären Staaten nicht ausreichend, um ihre Spuren zu verwischen. Wichtig ist es deshalb, sich selbst Gedanken darüber zu machen, vor welchen Gefahren man sich eigentlich schützen möchte - und sich im Zweifelsfall professionelle Hilfe zu suchen. Eine Basissammlung wie diese hier ist immer fragmentarisch und kann nie vollkommene Sicherheit gewähren. Alltägliche Nutzerinnen sollten sich im Klaren sein, dass sie selbst ein bisschen Aufwand betreiben und mitdenken müssen, um sich selbst zu schützen. Nur weil ein Angebot von vielen Menschen genutzt wird, heißt es beispielsweise noch lange nicht, dass der Dienst sicher oder datenschutzfreundlich ist. Deshalb sollte man sich immer fragen, was eigentlich das Geschäftsmodell eines Dientes ist - gerade bei vermeintlich kostenlosen Angeboten.
https://netzpolitik.org/2018/kleines-einmaleins-der-digitalen-selbstverteidigung/
 Working secure in the Homeoffice thanks NSA-tips, trojaner-info.de, 16.07.2020 Working secure in the Homeoffice thanks NSA-tips, trojaner-info.de, 16.07.2020
Über das Internet Protocol Security (IPsec) oder einen Virtual-Private-Network-Tunnel (VPN) baut man beispielsweise aus dem Homeoffice gesicherte Verbindungen ins Büro auf. Oft sind die Verbindungen jedoch nicht optimal konfiguriert. Darunter leidet die Sicherheit! Nun hat der US-Geheimdienst NSA Empfehlungen zur Absicherung von IPsec und VPN veröffentlicht.
In dem Beitrag zum Thema "Cybersecurity Information" erklärt die NSA, wie es zu Schutzproblemen kommen kann und wo die Schwachstellen der beiden Zugänge liegen. Gleichzeitig gibt sie auch Tipps, wie man die Sicherheitslücken umgehen kann und so sicher von Zuhause aus arbeiten kann.
 Zugriff checken Zugriff checken
Insebsondere die Admins sind für die Sicherheit verantwortlich. Diese sollten sicherstellen, dass ausschließlich berechtigte Geräte die Verbindung nutzen dürfen. Das können sie beispielsweise über das Anlegen von Filtern von IP-Adressen und Port-Regeln festlegen. An dieser Position kann auch eine Monitor-Lösung in Form eines Intrusion Prevention Systems (IPS) helfen den Überblick zu wahren und gegebenenfalls einzugreifen.
 Verschlüsselung sicher stellen Verschlüsselung sicher stellen
Zudem sollten die Standardeinstellungen eines VPN-Gateways angepasst werden. Wenn Admins bekannte Standard-Passwörter nicht ändern, ist das für Angreifer ein gefundenes "Fressen". Außerdem sollten die Verantwortlichen sicherstellen, dass ausschließlich als derzeit sicher geltende Verfahren zum Schlüsselaustausch und bei der Verschlüsselung zum Einsatz kommen. Das sind für den Schlüsselaustausch beispielsweise Diffie-Hellman und die Verschlüsselung auf Basis elliptischer Kurven. Nach Heise-Online sollte sichergestellt werden, dass Gateways und Clients auf ein sicheres Verschlüsselungsverfahren abgestimmt sind. Als unsicher geltende Cipher Suites sollten beispielsweise komplett deaktivieren, da sonst Angreifer über Downgrade-Attacken den Einsatz eines als unsicher geltenden Verfahrens erzwingen.
 Regelmäßige Überprüfungen dringend erforderlich Regelmäßige Überprüfungen dringend erforderlich
Eine regelmäßige Überprüfung ist ratsam. Andernfalls könnten sich Angreifer nach erfolgreichen Downgrade-Attacken als Man-in-the-Middle in Verbindungen einklinken und mitlesen. Außerdem sollten die Admins darauf aufpassen, dass sie die neuesten Patchs nicht verpassen, um so mögliche Lücken vorzubeugen.
https://www.trojaner-info.de/business-security/aktuell/sicher-arbeiten-im-homeoffice-dank-nsa-tipps.html
 Regelmäßige Überprüfungen dringend erforderlich Regelmäßige Überprüfungen dringend erforderlich
Eine regelmäßige Überprüfung ist ratsam. Andernfalls könnten sich Angreifer nach erfolgreichen Downgrade-Attacken als Man-in-the-Middle in Verbindungen einklinken und mitlesen. Außerdem sollten die Admins darauf aufpassen, dass sie die neuesten Patchs nicht verpassen, um so mögliche Lücken vorzubeugen.
https://www.trojaner-info.de/business-security/aktuell/sicher-arbeiten-im-homeoffice-dank-nsa-tipps.html
 Risiks for the Tor-network: Sybil-attackf, digitalcourage.de Risiks for the Tor-network: Sybil-attackf, digitalcourage.de
Kritiker des Tor-Netzwerkes weisen daraufhin, dass die Verwendung von Tor auch Risiken birgt. Die Größe des Tor-Netzes erschwert nämlich auch die Überprüfung der Identität und der Motive der einzelnen Tor-Relays. Wer etwa besonders viele Server unter seine Kontrolle bringt, kann durch statistische Untersuchungen die Kommunikation deanonymisieren (Sybil-Angriff).
https://digitalcourage.de/support/tor
 ... Isn´t that good, when it comes to catching bad guys? Yes, but only till a certain extent. The digital world is full of vultures such as spammers, attackers, troll armies, digital marketing firms and many more whose only objective is to use/violate our private data for their gain. Even governments are known to spy on people to meet their political needs. Many journalists, activists and researchers work has been exploited due to such a vulnerable structure. However even in today´s world anonymity could be achieved with few private network implementations. One such private network implementation is the TOR Network. ... Isn´t that good, when it comes to catching bad guys? Yes, but only till a certain extent. The digital world is full of vultures such as spammers, attackers, troll armies, digital marketing firms and many more whose only objective is to use/violate our private data for their gain. Even governments are known to spy on people to meet their political needs. Many journalists, activists and researchers work has been exploited due to such a vulnerable structure. However even in today´s world anonymity could be achieved with few private network implementations. One such private network implementation is the TOR Network.
[...] Detecting TOR usage in your environment
Understanding how the TOR network works makes it much simpler to detect but, knowing what services are being availed by its users isn´t quite possible yet. Be it a country´s government or a corporate organization, they can always choose to monitor or block the usage of TOR. However, there are limitations when it comes to blocking TOR completely and that is due to the existence of bridge nodes as discussed in the previous section. Even the introduction of Bridge nodes did not stop certain organizations and governments from trying to detect and block the usage of TOR. Here are few ways to block the usage of TOR:
Block the publicly available list of TOR Nodes. Few websites to check the currently available nodes and their details are https://www.dan.me.uk/tornodes, https://torstatus.blutmagie.de/, https://check.torproject.org/cgi-bin/TorBulkExitList.py.
Create Application Filter Policies in Firewalls where only certain approved networks (LAN Networks) will be able to utilize proxy services. The same can be implemented as a rule in SIEM solutions and Intrusion detection systems.
Create a SSL Decryption policy on your Firewall, IDS/IPS which can be used to decrypt SSL certificates and detect traffic related to websites hosted on TOR.
TOR browsing involves usage of two types of ports i.e. ORPort and DirPort. ORPorts are usually used to make connections and transmissions where as DirPorts are used to fetch updates from the directory servers. The ORPorts usually include ports 80 and 443, but can also be changed with advanced proxy settings while DirPorts include port 9001 and port 9003. Firewall and IDS filters can be configured to monitor any traffic going towards or coming from the ports 9001 and 9003.
Implementing any or all of the above steps may block the usage of TOR but only till a certain extent. In addition to the existence of Bridge nodes, it also depends upon how the organization´s policies and applications are configured.
Now that we´ve come to the end, I hope the above article has added a cent to everyone´s pocket. Please feel free to post any questions, suggestions or topics that you´re interested. I´d be happy to write and learn different stuff with the reader-based interests!
https://medium.com/coinmonks/tor-nodes-explained-580808c29e2d
Software::Browser
Mozilla nimmt Änderungen am System der Erweiterungen von Firefox vor, die den Schutz der Privatsphäre betreffen, PRO-LINUX.de, 28.03.2019
Mozilla nimmt in den nächsten Versionen einige größere Anpassungen bei Erweiterungen vor. Die Änderungen sind bereits in Firefox 67 Beta und in den Nightlies zu Firefox 68 enthalten, sodass Entwickler von Erweiterungen sich darauf einstellen können, wie Mozilla im Blog schreibt.
Die größere der Änderungen in Version 67 ist, dass Firefox jetzt Steuerelemente anbietet, um zu bestimmen, welche Erweiterungen in privaten Browserfenstern ausgeführt werden können. Bisher liefen alle Erweiterungen in allen Fenstern, was aber nicht im Einklang mit Mozillas Engagement für die Privatsphäre der Benutzer stand. Ab Version 67 haben Entwickler und Benutzer die Möglichkeit, festzulegen, welche Erweiterungen in den privaten Inkognito-Fenstern ausgeführt werden dürfen.
Mozillas Richtlinien für Add-ons legen fest, dass Erweiterungen kein
 Risiken des Tor-Netzwerks: Sybil-Angriff, digitalcourage.de Risiken des Tor-Netzwerks: Sybil-Angriff, digitalcourage.de
Kritiker des Tor-Netzwerkes weisen daraufhin, dass die Verwendung von Tor auch Risiken birgt. Die Größe des Tor-Netzes erschwert nämlich auch die Überprüfung der Identität und der Motive der einzelnen Tor-Relays. Wer etwa besonders viele Server unter seine Kontrolle bringt, kann durch statistische Untersuchungen die Kommunikation deanonymisieren (Sybil-Angriff).
https://digitalcourage.de/support/tore Browsing-Daten speichern oder Identitätsinformationen an private Fenster weitergeben. Deshalb unterstützt Firefox künftig den Schlüssel not_allowed im Inkognito-Manifest. Beginnend mit Firefox 67 ist es jeder installierten Erweiterung zunächst standardmäßig untersagt, in privaten Fenstern zu laufen. Der Anwender kann künftig in dem Fenster, das die Installation eines Add-ons bestätigt, einen Haken setzen und die Erweiterung für Inkognito-Fenster freigeben. Erweiterungen, die bei der Aktualisierung auf Firefox 67 bereits installiert sind, sind, um den Arbeitsfluss nicht zu stören, standardmäßig in privaten Fenstern erlaubt.
https://www.pro-linux.de/news/1/26913/firefox-mozilla-nimmt-%C3%84nderungen-bei-erweiterungen-vor.html
 SSL-verschlüsselt und doch nicht sicher?, trojaner-info.de, 08.02.2019 SSL-verschlüsselt und doch nicht sicher?, trojaner-info.de, 08.02.2019
[...] Trügerische Sicherheit
Bei dieser Einstufung wird missachtet, dass Cyberkriminelle heutzutage ihre Malware hinter SSL verschlüsseltem Datenverkehr zum ahnungslosen Anwender transportieren, wie Mathias Widler, Regional Vice President und General Manager Central EMEA bei Zscaler, auf it-daily.net, erläuterte.
[...] Malware wird nicht erkannt
Die Herausforderung besteht darin, dass die Sicherheits-Software von Endgeräten in der Regel den SSL-Verkehr nicht entschlüsselt für eine Malware-Untersuchung, sondern lediglich prüft, ob es einen verschlüsselten Tunnel gibt. Malware, die über eine https-Verbindung verbreitet wird, wird in vielen Fällen somit nicht erkannt. Dies stellt eine große Bedrohung für die Benutzer dar, da die Anzahl der hinter SSL-Traffic verborgener Malware rasant anwächst, wie regelmäßige Analysen des Internet Security Spezialisten Zscaler zeigen.
[...] Um diesen mit Schadcode behafteten Datenverkehr aufzuspüren, sind Streckenposten auf der Straße erforderlich, die in der Lage sind, die Malware zu stoppen, bevor sie sich auf den Anwendergeräten einnisten kann. Auf das Geschäftsumfeld übertragen bedeutet das, dass Unternehmen auf durchgängige SSL-Inspektion setzen sollten, um das Einschleusen von Malware zu unterbinden. Vor allem dann, wenn Anwender mit ihren Privatgeräten auf zwischen privatem und beruflichem Gebrauch wechseln.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/ssl-verschluesselt-und-doch-nicht-sicher.html
 Alte TLS-Versionen werden ab 2020 von den großen Browsern nicht mehr unterstützt, PC-WELT.de, 16.10.2018 Alte TLS-Versionen werden ab 2020 von den großen Browsern nicht mehr unterstützt, PC-WELT.de, 16.10.2018
Microsoft, Mozilla, Google und Apple sind sich einig. Ab 2020 werden die alten TLS-Versionen nicht mehr unterstützt.
Mit der geplanten Einstellung der Unterstützung für die TLS-Versionen 1.0 und 1.1 im Jahr 2020 haben Webseiten-Betreiber also noch ausreichend Zeit, auf die neueren Versionen umzustellen. Die alten Versionen enthielten Sicherheitslücken, die bestimmte Angriffe erlaubten, dazu zählen der "Beast"- und "Sloth"-Angriff. Der "Sloth"-Angriff wurde beispielsweise durch die schwachen Hash-Funktionen wie MD5 und SHA1 möglich. Bei beiden Angriffen handelt es sich aber um theoretische Angriffe, in der Praxis werden diese kaum ausgeführt. Bereits heute laufen rund 94 Prozent aller Webseiten auf dem Protokoll der Version 1.2, Grund zur Sorge besteht also nicht. Die neue Version TLS 1.3 wird teilweise schon eingesetzt.
https://www.pcwelt.de/a/alte-tls-versionen-werden-ab-2020-von-den-grossen-browsern-nicht-mehr-unterstuetzt,3462573
 Venafi-Umfrage: Vorgeschriebene Verschlüsselungs-Hintertüren und die Folgen, trojaner-info.de, 06.04.2019 Venafi-Umfrage: Vorgeschriebene Verschlüsselungs-Hintertüren und die Folgen, trojaner-info.de, 06.04.2019
Kevin Bocek, Vice President of Security Strategy and Threat Intelligence bei Venafi
Venafi®, der führende Anbieter von Sicherheitslösungen für maschinelle Identitäten, gibt heute die Ergebnisse einer Umfrage zu staatlich vorgeschriebenen Verschlüsselungshintertüren bekannt. Sie wurde auf der RSA-Konferenz 2019 durchgeführt und spiegelt die Meinungen von 517 IT-Sicherheitsexperten wider. 73 Prozent der Befragten meinen, dass Länder mit staatlich vorgeschriebenen Verschlüsselungshintertüren anfälliger sind für nationalstaatliche Angriffe.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/venafi-umfrage-vorgeschriebene-verschluesselungs-hintertueren.html
Anti-Terror-Koordinator
EU-Beamter fordert Gesetz gegen Verschlüsselung, netzpolitik.org, 15.05.2020
Die Europäische Union soll endlich ein Gesetz auf den Weg bringen, um den Trend unregulierter Verschlüsselung zu brechen. Das fordert der Anti-Terror-Koordinator in einem Brief, den wir veröffentlichen. Unterdessen gründen NGOs eine Globale Koalition für Verschlüsselung.
Seit 2007 ist der Belgier Gilles de Kerchove Anti-Terror-Koordinator der EU. In dieser Position fordert er immer wieder mehr Befugnisse für Polizei und Geheimdienste. Dass Internet-Anbieter auf die von Edward Snowden enthüllte staatliche Überwachung mit mehr Verschlüsselung reagierten, sieht er kritisch, spätestens seit 2015 fordert er verpflichtende Hintertüren.
Am Freitag erneuerte er seine Forderungen in einem Brief an die EU-Mitgliedsstaaten, den wir an dieser Stelle veröffentlichen: Strafverfolgung und rechtliche Aspekte der Verschlüsselung.
Trend unregulierter Verschlüsselung brechen
Kerchove will "den Trend der unregulierten Verschlüsselungspraxis brechen". Er bezeichnet "ungehinderte Verschlüsselung" in Anwendungen und Standards als "massive Herausforderung" für Polizei und Geheimdienste und fordert eine "robuste Antwort" der Politik: "Es ist Zeit, dass die EU in dieser Hinsicht tätig wird."
https://netzpolitik.org/2020/eu-beamter-fordert-gesetz-gegen-verschluesselung/
 Mit Hashabgleich und TPM gegen Ende-zu-Ende-Verschlüsselung, trojaner-info.de, 10.09.2020 Mit Hashabgleich und TPM gegen Ende-zu-Ende-Verschlüsselung, trojaner-info.de, 10.09.2020
Angesichts der Schlüsselrolle, die Messenger-Dienste wie WhatsApp oder Telegram sowie E-Mail bei der Verbreitung von Darstellungen sexuellen Kindesmissbrauchs spielen, sucht die EU-Kommission nach Gegenmitteln. Eine Expertengruppe aus Vertretern von Microsoft, Google, Europol, Polizeibehörden, dem britischen Geheimdienst GCHQ, dem National Center for Missing and Exploited Children der USA sowie mehreren Kinderschutzorganisationen hat nun erste Ansätze zum Umgang mit Ende-zu-Ende-Verschlüsselung entwickelt.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/mit-hashabgleich-und-tpm-gegen-ende-zu-ende-verschluesselung-8005.html
 (Planned in future) Vienna, net-communiciaiton: Free from eavesdropping with the help by quantum physics?, tagesschau.de, 16.12.2018 (Planned in future) Vienna, net-communiciaiton: Free from eavesdropping with the help by quantum physics?, tagesschau.de, 16.12.2018
Whoever communicats in the internet with eachother, he leaves tracks within the internet without fail. Research scientists from Vienna invented a new method making communication free from eavesdropping even in larger networks.
In future the quantum cryptography enables a eavesdrop-free communication in the internet. Researchers from Austria have - following their own descriptions - made the important step. It managed them to keep four members of a network communicate free from eavesdropping. Scientists around Rupert Ursin from the Institution for quantum optics and quantum information of the academia of sciences in Austria introduced their research in the british expert report "Nature".
https://www.tagesschau.de/ausland/quanten-101.html
 IP2Location C library enables the user to get the country, region, city, coordinates, ZIP code, time zone, ISP, domain name, connection type, area code, weather info, mobile carrier, elevation and usage type from any IP address or hostname. This library has been optimized for speed and memory utilization. The library contains API to query all IP2Location LITE and commercial binary databases. Users can download the latest LITE database from IP2Location web site using e.g. the included downloader. IP2Location C library enables the user to get the country, region, city, coordinates, ZIP code, time zone, ISP, domain name, connection type, area code, weather info, mobile carrier, elevation and usage type from any IP address or hostname. This library has been optimized for speed and memory utilization. The library contains API to query all IP2Location LITE and commercial binary databases. Users can download the latest LITE database from IP2Location web site using e.g. the included downloader.
https://fr2.rpmfind.net
 Notice: IP2Location C library enables the user to get the country, region, city, coordinates, ZIP code, time zone, ISP, domain name, connection type, area code, weather info, mobile carrier, elevation and usage type from any IP address or hostname. This library has been optimized for speed and memory utilization. The library contains API to query all IP2Location LITE and commercial binary databases. Users can download the latest LITE database from IP2Location web site using e.g. the included downloader. Notice: IP2Location C library enables the user to get the country, region, city, coordinates, ZIP code, time zone, ISP, domain name, connection type, area code, weather info, mobile carrier, elevation and usage type from any IP address or hostname. This library has been optimized for speed and memory utilization. The library contains API to query all IP2Location LITE and commercial binary databases. Users can download the latest LITE database from IP2Location web site using e.g. the included downloader.
"They want to get to know everything - without exceptions.", tagesschau.de
Nur einige wenige sind davon ausgenommen: Eingeschrieben in den Quelltext, der NDR und WDR vorliegt, ist die Differenzierung zwischen den Partnerländern der USA, den sogenannten "Five Eyes", Neuseeland, Australien, Großbritannien sowie Kanada, und den anderen Ländern. Verbindungen, die aus den "Five-Eyes"-Ländern auf die Tor-Webseite vorgenommen werden, sollen laut der vorliegenden Regel nicht markiert werden. Aus allen anderen Ländern allerdings schon. Ohne Ausnahme, .
https://www.tagesschau.de/inland/nsa-xkeyscore-100.html .
Unvorstellbar schon die elterliche Vorstellung, ihr kleiner Spröszlig;ling plappert bereits in der Schule und anderswo ihre Ansichten, Meinungen und Gesinnungen aus...
 No matter, how they tried No matter, how they tried
Berlin LKA-building
Police as much as ZITiS did not manage to decrypt devices of suspicous ones, netzpolitik.org, 02.10.2020
Die Berliner Polizei scheitert daran, Handy und Laptop eines Neonazis zu knacken. Das geht aus dem Abschlussbericht der Ermittlungsgruppe zu Brandstiftungen und Sprühereien im Bezirk Neukölln hervor. Auch Bundesbehörden und Firmen haben sich an den Geräten die Zähne ausgebissen.
https://netzpolitik.org/2020/rechte-anschlagserie-polizei-und-zitis-koennen-geraete-von-verdaechtigen-nicht-entschluesseln/
 The object of the E-signature past the signment, PC-WELT.de, 03.10.2020 The object of the E-signature past the signment, PC-WELT.de, 03.10.2020
Nach der Unterschrift müssen Unternehmen ihre Verträge verwalten. Welches Einspar-Potenzial sich dabei bietet, zeigt ein Live-Webcast der Computerwoche.
https://www.pcwelt.de/news/Die-Rolle-der-E-Signatur-nach-der-Unterschrift-10894341.html
 Robbed and selled Robbed and selled
Risk Based Authentication: The crook for passwords and how they gets traded, trojaner-info.de, 29.11.2020
Passwords are out of order. This means: They are not good for the identification of the user on the other end of the conneciton. Is this really the user or a betrayer? The reason: Passwords can be robbed and selled, what is happening in many cases. One knowns, howto make it better. But one still has to wait for years for the Two-Factor-Authentification and FIDO2.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/risk-based-authentication-die-kruecke-fuer-passwoerter-und-wie-sie-ausgenutzt-wird.html
From News&Links ( and all the essential security actions for Linux in this excurs... )
"2020: The world is lamed", STERN.de, 21.03.2020
https://www.stern.de/reise/deutschland/tourismus-in-zeiten-der-coronakrise---die-welt-ist-lahmgelegt---sagt-ury-steinweg-von-gebeco-9190342.html
"Unacnny, mad, horrible", tagesschau.de, 12.09.2020
Die Busch- und Waldbrände in Kalifornien gehören zu den Schlimmsten, die es je gab. Mehr als 12.500 Quadratkilometer sind von den Feuern betroffen. Und nicht nur Kalifornien, die gesamte Westküste der USA brennt.
https://www.tagesschau.de/ausland/kalifornien-waldbraende-135.html
"All people confident with the 80th know, that USA is a criminal state, who takes his superiority ... / Allen mit der Geschichte der vergangenen 80er Jahre vertrauten denkenden Menschen ist doch bekannt, dass die USA ein verbrecherischer Staat ist, der seine Übermacht mit ..."
www.compact-online.de/us-strategie-weltpolizei-oder-beobachtender-raushalter

 The part of the E-signature, PC-WELT.de, 03.10.2020 The part of the E-signature, PC-WELT.de, 03.10.2020
Nach der Unterschrift müssen Unternehmen ihre Verträge verwalten. Welches Einspar-Potenzial sich dabei bietet, zeigt ein Live-Webcast der Computerwoche.
https://www.pcwelt.de/news/Die-Rolle-der-E-Signatur-nach-der-Unterschrift-10894341.html
 E-Mail- and IP-adresse are no address, netzpolitik.org, 10.12.2020 E-Mail- and IP-adresse are no address, netzpolitik.org, 10.12.2020
Rückschlag für Filmverwerter: Constantin Film hat keinen Anspruch auf die Mail- und IP-Adressen von YouTube-Nutzer:innen, die rechtswidrig urheberechtliche geschützte Filme hochgeladen haben.
https://netzpolitik.org/2020/bgh-urteil-zu-youtube-fall-e-mail-und-ip-adresse-sind-keine-anschrift/
Ergonomy at the workplace, Stern.de, 12.01.2020
Although our body ist not made for long sitting, each day we spend plenty of hours at the workplace without moving. To keep fit, the workplace should be kept ergonomically.
https://www.stern.de/gesundheit/ruecken/ergonomie-am-arbeitsplatz--beschwerden-lindern-8900818.html
 "Wir töten Leute auf der Basis von Metadaten" "Wir töten Leute auf der Basis von Metadaten"
Hacking und Spionage
Ist WhatsApp sicher genug für die Diplomatie?, netzpolitik.org, 24.02.2020
In den Korridoren der Macht ist der Messengerdienst das Mittel der Wahl. Nun empfehlen EU-Experten den Wechsel zu Signal. Hat WhatsApp in der Diplomatie ausgedient?
[...] Doch Sicherheitslücken bei WhatsApp werfen Fragen auf. Der Beliebtheit der App schaden könnten auch die Cryptoleaks-Enthüllungen. Sie zeigen, dass die USA und Deutschland über Jahrzehnte systematisch die verschlüsselte Kommunikation ihrer Verbündeten belauschten.
Der NSA-Skandal vor sechs Jahren rüttelte am Image des Mutterkonzerns Facebook. Die Affären schüren Zweifel, ob ein US-amerikanischer Gratisdienst wie WhatsApp tatsächlich die nötigen Maßnahmen trifft, um den sensiblen Austausch unter EU-Staaten vor dem Zugriff von Geheimdiensten und Spionage aus Russland und China zu schützen.
[...] WhatsApp verwendet zur Verschlüsselung das gleiche Protokoll wie Signal, das von Überwachungsgegnern wie etwa NSA-Enthüller Edward Snowden empfohlen wird. Diese Verschlüsselung ist mit heutiger Technik schwer zu knacken.
Das gilt jedoch nicht für die Metadaten. Bei den Metadaten handelt es sich um Angaben über Sender und Empfänger, Zeit und Datum sowie Nachrichtengröße.
Aus den Metadaten lässt sich ablesen, wer mit wem kommuniziert. Durch die Dateigröße lassen sich Rückschlüsse treffen, ob etwa Bilder oder Videos mitgeschickt wurden.
Der Facebook-Konzern speichert Metadaten zentral auf seinen Servern. WhatsApp greift zudem regulär auf das gesamte Telefonbuch im Handy der Nutzer:innen zu. WhatsApp teilt die Daten mit Facebook.
Signal speichert nach eigenen Angaben möglichst wenige Informationen über Nutzer:innen. Der Dienst verschlüsselt Metadaten und löscht sie von seinen Servern, sobald die Nachricht verschickt ist.
Schrems: "Metadaten gehen an US-Behörden"
Geheimdienste drängen auf den verpflichtenden Einbau von Hintertüren in Messengerdienste, um verschlüsselte Nachrichteninhalte lesen zu können. WhatsApp, Apple sowie ein breites Bündnis aus Firmen und NGOs wehren sich dagegen - bisher erfolgreich.
Metadaten verraten aber oft genausoviel wie Nachrichteninhalte. In der Diplomatie geht es um Netzwerke, um vertrauliche Absprachen. Schreibt eine französische Diplomatin ihrem deutschen Gegenüber vor der entscheidenden Abstimmung, ist das Wissen darum nicht ebenso bedeutend wie der Inhalt?
[...] Eine drastische Illustration der möglichen Konsequenzen des Datenzugriffs durch US-Geheimdienste brachte der frühere NSA-Chef Michael Hayden auf den Punkt: "Wir töten Leute auf der Basis von Metadaten".
Der deutsche Bundesdatenschutzbeauftragte Ulrich Kelber sieht die Nutzung von WhatsApp durch von ihm beaufsichtigte Behörden "kritisch", schrieb uns sein Pressesprecher. Kelber bemängelt, dass Metadaten von WhatsApp an Facebook weitergeleitet werden.
Der österreichische Datenschützer Max Schrems formuliert es gegenüber netzpolitik.org drastischer: "Die Metadaten gehen direkt an Facebook und damit auch an die amerikanischen Geheimdienste. Allein wer wann wie oft mit wem kommuniziert, kann extrem viele Rückschlüsse erlauben."
Facebook antwortete nicht auf die Frage von netzpolitik.org, wie es die Metadaten seiner Nutzer:innen wirksam vor dem Zugriff durch US-Geheimdienste schützen möchte.
[...] Diplomaten und EU-Beamte müssen generell damit rechnen, belauscht zu werden. Brüssel gilt seit Jahren als Spionagehochburg, erst im Januar geriet ein prominenter deutscher Ex-Diplomat wegen mutmaßlicher Spionage für China unter Verdacht.
Doch solche Fälle sind eher selten: Der Großteil der Spionage läuft vermutlich elektronisch ab.
Die NSA-Affäre enthüllte 2013 ein massives Abhörprogramm der USA gegen EU-Diplomaten in Brüssel und an den UN-Sitzen in Wien und Genf.
Am Schweizer Sitz der Vereinten Nationen war Whistleblower Edward Snowden stationiert, als er noch für den US-Geheimdienst spionierte. Snowden sagte später, die USA spioniere weiterhin in Genf und anderen Orten.
Engster Verbündeter der USA in Geheimdienstangelegenheiten ist Großbritannien. Gemeinsam mit Kanada, Australien und Neuseeland bilden die Staaten die Five-Eyes-Allianz.
Für die technisch hochgerüsteten Dienste sind die EU-Staaten attraktive Ziele, besonders nach dem Brexit.
[...] Diplomaten und EU-Beamte müssen generell damit rechnen, belauscht zu werden. Brüssel gilt seit Jahren als Spionagehochburg, erst im Januar geriet ein prominenter deutscher Ex-Diplomat wegen mutmaßlicher Spionage für China unter Verdacht.
Doch solche Fälle sind eher selten: Der Großteil der Spionage läuft vermutlich elektronisch ab.
Die NSA-Affäre enthüllte 2013 ein massives Abhörprogramm der USA gegen EU-Diplomaten in Brüssel und an den UN-Sitzen in Wien und Genf.
Am Schweizer Sitz der Vereinten Nationen war Whistleblower Edward Snowden stationiert, als er noch für den US-Geheimdienst spionierte. Snowden sagte später, die USA spioniere weiterhin in Genf und anderen Orten.
Engster Verbündeter der USA in Geheimdienstangelegenheiten ist Großbritannien. Gemeinsam mit Kanada, Australien und Neuseeland bilden die Staaten die Five-Eyes-Allianz.
Für die technisch hochgerüsteten Dienste sind die EU-Staaten attraktive Ziele, besonders nach dem Brexit.
[...] Wer aus beruflichen oder persönlichen Gründen die Möglichkeit eines Zugriffs auf Metadaten durch US-Geheimdienste verringern will, solle zu anderen Diensten wie Signal greifen, empfiehlt Jan Penfrat von EDRi.
Als Alternativen nennt der NGO-Experte neben Signal Dienste wie die Messengern Threema oder Wire, beide mit Sitz in der Schweiz, oder das Open-Source-Projekt Matrix, dessen Technologie von der Bundeswehr genutzt wird.
Die EU-Kommission verfolgt allerdings andere Pläne. In der Notiz, die wir veröffentlichen, ist Signal nur als Zwischenlösung gedacht. Längerfristig rät die Gruppe zu Skype for Business, einem Dienst von Microsoft.
Eine Lösung, die unabhängig von US-Konzernen und Geheimdiensten ist, liegt offenbar noch weiter in der Ferne.
[...] Diplomaten und EU-Beamte müssen generell damit rechnen, belauscht zu werden. Brüssel gilt seit Jahren als Spionagehochburg, erst im Januar geriet ein prominenter deutscher Ex-Diplomat wegen mutmaßlicher Spionage für China unter Verdacht.
Doch solche Fälle sind eher selten: Der Großteil der Spionage läuft vermutlich elektronisch ab.
Die NSA-Affäre enthüllte 2013 ein massives Abhörprogramm der USA gegen EU-Diplomaten in Brüssel und an den UN-Sitzen in Wien und Genf.
Am Schweizer Sitz der Vereinten Nationen war Whistleblower Edward Snowden stationiert, als er noch für den US-Geheimdienst spionierte. Snowden sagte später, die USA spioniere weiterhin in Genf und anderen Orten.
Engster Verbündeter der USA in Geheimdienstangelegenheiten ist Großbritannien. Gemeinsam mit Kanada, Australien und Neuseeland bilden die Staaten die Five-Eyes-Allianz.
Für die technisch hochgerüsteten Dienste sind die EU-Staaten attraktive Ziele, besonders nach dem Brexit.
[...] Wer aus beruflichen oder persönlichen Gründen die Möglichkeit eines Zugriffs auf Metadaten durch US-Geheimdienste verringern will, solle zu anderen Diensten wie Signal greifen, empfiehlt Jan Penfrat von EDRi.
Als Alternativen nennt der NGO-Experte neben Signal Dienste wie die Messengern Threema oder Wire, beide mit Sitz in der Schweiz, oder das Open-Source-Projekt Matrix, dessen Technologie von der Bundeswehr genutzt wird.
Die EU-Kommission verfolgt allerdings andere Pläne. In der Notiz, die wir veröffentlichen, ist Signal nur als Zwischenlösung gedacht. Längerfristig rät die Gruppe zu Skype for Business, einem Dienst von Microsoft.
Eine Lösung, die unabhängig von US-Konzernen und Geheimdiensten ist, liegt offenbar noch weiter in der Ferne.
https://netzpolitik.org/2020/ist-whatsapp-sicher-genug-fuer-die-diplomatie/
https://netzpolitik.org/2020/is-whatsapp-safe-for-diplomats/
 Encryption Encryption
Secure communcation provider warn against backdoors, netzpolitik.org, 01.28.2021
Four euopean Software-companies warn against the recent push of EU-countries for breaking encrypted communication. Backdoors would threaten the data security in Europe, means a common letter at the day for european data protection.
Am heutigen Europäischen Datenschutztag rufen vier Anbieter sicherer Kommunikation die EU dazu auf, ihre "verschlüsselungsfeindliche Rhetorik" zu überdenken. Hintertüren in Verschlüsselung würden die Datensicherheit von Millionen von Europäern bedrohen und das Vertrauen in die Ende-zu-Ende-Verschlüsselung untergraben, schreiben die Unternehmen ProtonMail, Threema, Tresorit und Tutanota in einer gemeinsamen Erklärung.
Zuletzt hatte der EU-Ministerrat im Dezember einen "rechtmäßigen Zugang zu Daten" von verschlüsselten Nachrichteninhalten gefordert. Zwar finden sich in der Resolution mit dem Titel "Sicherheit durch Verschlüsselung und Sicherheit trotz Verschlüsselung" keine konkreten Vorschläge, die EU-Länder wünschen sich von den Diensteanbietern jedoch "technische und operative Lösungen", um auf sichere Kommunikation zugreifen zu können.
Ohne Hintertüren können Anbieter auf Ende-zu-Ende-verschlüsselte Inhalte allerdings nicht zugreifen, da dies technisch nicht möglich ist. "Die Installation von Hintertüren in verschlüsselten Apps ist so, als würde man den Strafverfolgungsbehörden einen Schlüssel zum Haus eines jeden Bürgers geben", erklären die vier betroffenen Diensteanbieter.
[...] Betont wurde die notwendige Verbesserung der Fähigkeit sich gegen Cyber-Bedrohungen zu schützen "insbesondere durch Quantenverschlüsselung und den Zugang zu Daten für Gerichts- und Strafverfolgungszwecke sicherzustellen".
[...] Secure method
End-to-end-encryption is a method popular within application of daily communication technology. This technique has been used in messengers like Signal, WhatsApp or iMessage for years. End-to-ende means communication transfer without any breaks. Transferred contents can only be decrypted and read out at the end points of each communication partner.
Encryption technique is nothing to argue, it depends on mathematic, a science that is non-ambiguous. Wie die Kommunikationsanbieter ProtonMail, Threema, Tresorit und Tutanota in ihrem Gegenstatement auf den Punkt bringen: "Der aktuelle Entwurf der Resolution des EU-Ministerrates beruht auf einem eingeschränkten Verständnis der technischen Aspekte von Ende-zu-Ende-Verschlüsselung. Denn Ende-zu-Ende-Verschlüsselung ist absolut, Daten sind entweder verschlüsselt oder nicht.
[...] Obwohl bisher noch nichts entschieden ist, raten Datenschützer:innen und Expert:innen dazu aufmerksam zu bleiben. Es ist zwar noch kein Gesetz im Entwurf, die Annahme der Entschließung bereitet jedoch einen Weg für einen Entwurf der Kommission. Die zuständige EU-Innenkommissarin Ylva Johansson äußerte sich zuletzt ambivalent.
Zwar teilte sie in einem Schreiben EU-Abgeordneten Anfang Januar mit, dass es keine Pläne gebe, Verschlüsselung zu verbieten. Allerdings fügte die Kommissarin hinzu, "weiterhin gemeinsam mit den Mitgliedstaaten mögliche rechtliche, operative und technische Lösungen für den rechtmäßigen Zugang zu solchen Daten zu prüfen."
https://netzpolitik.org/2021/verschluesselung-sichere-kommunikationsanbieter-warnen-vor-hintertueren/
 Impressment of E-Mails Impressment of E-Mails
In all secrecy, netzpolitik.org, 05.03.2021
Erst ganz zum Schluss ist bei geplanten Änderungen der Strafprozessordnung die heimliche Beschlagnahme im Gesetzentwurf der Bundesregierung aufgetaucht. Behörden sollen leichter auf E-Mails und Cloud-Inhalte zugreifen können. Die Betroffenen würden das nicht erfahren.
https://netzpolitik.org/2021/beschlagnahme-von-e-mails-in-aller-heimlichkeit/
 Secure E-Mails for everyone!, tutanota.com/de, 12.11.2019 Secure E-Mails for everyone!, tutanota.com/de, 12.11.2019
Tutanota is the world´s most secure E-Mail-service, for free and very easy to use. Get the encrypted mailbox now protecting your privacy!
Sicher vor Angreifern
Mit Ende-zu-Ende-Verschlüsselung & 2FA waren deine E-Mails nie sicherer. Die eingebaute Verschlüsselung garantiert, dass deine Mailbox nur dir gehört: Niemand sonst kann deine Daten entschlüsseln oder lesen.
Wir lieben Open Source
Tutanota ist Open Source, so dass Sicherheitsexperten den Code jederzeit überprüfen können. Außerdem macht die komplett Google-freie Android App Tutanota zum besten Open Source E-Mail-Service.
Auf deinem Gerät
Mit Apps für iOS und Android sind deine sicheren E-Mails jederzeit griffbereit. Unser schneller Web-Client und unsere funktionsreichen Apps machen E-Mail-Verschlüsselung zum Vergnügen.
Sichere E-Mails - kostenlos & ohne Werbung
Bei Tutanota bekommst du eine sichere Mailbox ganz ohne Werbung. Wir arbeiten rund um die Uhr, um dir einen E-Mail-Service zur Verfügung zu stellen, mit dem du dich auf die wichtigen Dinge fokussieren kannst.
Wir verschlüsseln alles
Wir garantieren, dass deine Daten in Tutanota stets verschlüsselt werden - ob du unseren sicheren Webmail-Client nutzt, unsere Apps für Android und iOS oder unsere Desktop-Clients für Windows, Linux und Mac OS. Schicke ganz einfach eine verschlüsselte E-Mail mit dem Wissen, dass Tutanota Betreff, Inhalt und alle Anhänge verschlüsselt. Importiere alle deine Kontakte in das verschlüsselte Adressbuch von Tutanota und sei sicher, dass niemand sonst die persönlichen Daten deiner Kontakte einsehen kann.
Unser gesamtes Team sitzt in Hannover, Deutschland. Alle deine verschlüsselten E-Mails werden auf unseren eigenen Servern in Hochsicherheitsdatenzentren in Deutschland gespeichert. Mit seinen strengen Datenschutzgesetzen und der DSGVO hat Deutschland einige der besten Gesetze weltweit, um deine Privatsphäre zu schützen. Das Grundgesetz Deutschlands betont die Wichtigkeit von freier Meinungsäußerung und dem Menschenrecht auf Privatsphäre.
Wir glauben an Privatsphäre
Privatsphäre ist ein Menschenrecht. Wir entwickeln Tutanota, damit du sichere E-Mails an jeden schicken kannst. Dies schützt nicht nur Journalisten, Whistleblower und Aktivisten, sondern einfach jeden Mensch auf der ganzen Welt. Unsere Mission ist es die illegale Massenüberwachung zu beenden. Mach mit und baue mit uns das Internet der Zukunft: privat und sicher!
Stopp die Google-Überwachung: So holen Sie sich Ihre Privatsphäre zurück.
Für viele ist das Internet Google: Google nutzt jedoch alle Daten, die es über seine Dienste sammelt, um geziel Anzeigen zu schalten. So profitiert Google massiv von den Daten, die viele so freimütig mit dem Internetriesen teilen. Es ist an der Zeit, dieses unbegrenzte Data Mining zu beenden und unser Recht auf Privatsphäre zurückzuholen! Hier sind ein paar Tipps mit sicheren Alternative, so dass Sie Ihre Daten nicht mehr mit Google und Facebook teilen müssen.
Der sichere E-Mail-Anbieter Tutanota arbeitet an Post-Quantum-Kryptographie.
Wir freuen uns, Ihnen mitteilen zu können, dass die Leibniz Universität Hannover und der sichere E-Mail-Service Tutanota gemeinsam EU-Mittel für ein Forschungsprojekt zur Post-Quantenkryptographie akquiriert haben. Kryptographie-Experten schätzen, dass Quantencomputer in wenigen Jahren in der Lage sein werden, weit verbreitete Verschlüsselungsalgorithmen zu brechen. Mit den Fortschritten bei der Entwicklung von Quantencomputern ist es an der Zeit, die Verschlüsselungsalgorithmen von Tutanota gegen mögliche Angriffe von Quantencomputern abzusichern.
https://tutanota.com/de/
 Favicons: Possible access points for tracking, PC-WELT.de, 22.02.2021 Favicons: Possible access points for tracking, PC-WELT.de, 22.02.2021
Sicherheitsforscher der Universität von Illinois in Chicago haben eine Methode entdeckt, mit der sich Anwender eindeutig über den Browser identifizieren lassen. Damit wird es möglich, das Surfverhalten des Anwenders zu verfolgen. Möglich machen dies die Favicons. Diese kleinen Bilder werden vom Browser von einer besuchten Webseite geladen, um dann in den Tabs, im Verlauf und in der Lesezeichenliste bei der jeweiligen Webseite angezeigt zu werden. Und damit der Browser die Favicons nicht jedes Mal neu laden muss, werden sie auf dem Rechner in einem Cache-Verzeichnis (F-Cache) gesichert. Zusätzlich werden die dazugehörige URL, eine Identifikationsnummer und ein Zeitstempel gesichert.
https://www.pcwelt.de/news/Favicons-Moegliches-Einfallstor-fuer-Tracking-10981620.html
 Anonymous surf with RiseupVPN, heise.de Anonymous surf with RiseupVPN, heise.de
Riseup.net ist ein Projekt, um Menschen mit anonymen Kommunikationsmöglichkeiten zu versorgen. Genauer gesagt ist es eine aktivistische, eher linksgerichtete und spendenfinanzierte Gruppe. Ob man das nun mag oder nicht: Es erhöht die Wahrscheinlichkeit, dass hier tatsächlich, wie versprochen, nichts geloggt wird. Das versprechen zwar auch kommerzielle Anbieter immer wieder, aber sie sind auch immer wieder mal aufgeflogen, weil sie eben doch Daten von Nutzern gespeichert haben. Offiziell noch als Beta eingestuft, läuft der RiseupVPN-Dienst nun schon seit einer ganzen Weile sehr zuverlässig und performant.
Das Beste an der RiseupVPN-App: Es ist eine vorkonfigurierte Variante des VPN-Clients Bitmask. Und vorkonfiguriert heißt für Sie, dass die ganze Arbeit von der Fritzbox-Variante von oben wegfällt. Sie finden RiseupVPN bei Google Play und natürlich auch bei F-Droid.
Nach der Installation rufen Sie die App auf und tappen auf den einzigen vorhandenen Button: "Einschalten" - ein, zwei Sekunden später meldet die App, dass die VPN-Verbindung steht. Das können Sie natürlich auch oben im Android-Status sehen, wo wiederum das Schlüssel-Symbol auftaucht. Die Einfachheit hat, wie oben bereits angedeutet, einen kleinen Nachteil: Es scheint sich immer um ein und denselben Server in den Niederlanden zu handeln, sodass das Umgehen von Ländersperren mit RiseupVPN tendenziell meist nicht so einfach funktioniert.
https://www.heise.de/tipps-tricks/VPN-unter-Android-einrichten-so-klappt-s-4455738.html
 There is no WLAN-Router secure: Howto protext yourself even though in your home net, CHIP, 07.30.2020 There is no WLAN-Router secure: Howto protext yourself even though in your home net, CHIP, 07.30.2020
Der heimische WLAN-Router ist Dreh- und Angelpunkt für den Internet-Zugang all Ihrer Geräte. Leider ist es mit der Sicherheit der Geräte oft nicht allzu weit her, wie Forscher aktuell wieder einmal bestätigt haben. An allen 127 untersuchten WLAN-Routern gab es Beanstandungen. CHIP zeigt, wie Sie Ihren WLAN-Router optimal absichern.
https://www.chip.de/news/Kein-WLAN-Router-ist-sicher-Heimnetz-absichern_138443184.html
 FritzBox and Co. are affected by serious hard lacks in security: Howto protect yourself, CHIP, 05.14.2021 FritzBox and Co. are affected by serious hard lacks in security: Howto protect yourself, CHIP, 05.14.2021
Das Original dieses Beitrages ist zuerst erschienen auf inside digital*
Einem neuen Bericht zufolge sind so gut wie alle WLAN-Geräte von einer Sicherheitslücke bedroht - darunter auch beliebte Router wie die FritzBoxen von AVM. Viele Hersteller haben mit Updates bereits auf die Schwachstelle reagiert. Nutzer sollten die neuen Versionen möglichst bald installieren.
https://www.chip.de/news/FritzBox-und-Co.-von-Schwachstelle-betroffen-So-schuetzen-Sie-sich_183613412.html
 Bugs with intention: Linux Foundation presents the anaylises of the kernel-patches, trojaner-info.de, 22.05.2021 Bugs with intention: Linux Foundation presents the anaylises of the kernel-patches, trojaner-info.de, 22.05.2021
Das Technical Advisory Board der Linux Foundation, das als eine Art Beratergremium für Fragen rund um die Entwicklung des Linux-Kernels fungiert, hat seinen Bericht zum "Hypocrite Commits"-Papier der Universät von Minnesota (University of Minnesota, UMN) vorgelegt. Darin fasst es die Ergebnisse des Reviews der inkriminierten Commits zusammen und gibt der UMN Tipps, wie sie das Vertrauen der Kernel-Entwickler wie Greg Kroah-Hartmann zurückgewinnen. Kroah-Hartmann selbst war maßgeblich an der Code-Analyse beteiligt.
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/bugs-mit-vorsatz-linux-foundation-legt-analyse-der-kernel-patches-vor.html
 Your operating system could be so beautiful: Against this operating system, Windows 10 looks pretty old Your operating system could be so beautiful: Against this operating system, Windows 10 looks pretty old
Linux Deepin: A powerful operating system, CHIP, 05.18.2021
https://www.chip.de/news/Viel-schoener-als-Windows-10-Deepin-Linux_153049961.html
"Mehr Respekt vor Altenpflegern als Industrie-Bossen", Maja Schmidt; falls aus Voerde (Pornomodell): Irgendwas musste ich an ihr ja mal gefunden haben...
Neuer NSA-Abhörskandal
Außerhalb Europas herrscht Unverständnis über die Nicht-Reaktion der Europäer auf den NSA-Abhörskandal, uncut-news.ch, 07.06.2021
Der neue NSA-Abhörskandal findet in den Medien praktisch nicht statt, er wurde kurz gemeldet und ist dann schnell wieder verschwunden. Ein Nachruf aus dem russischen Fernsehen.
Die Reaktion der europäischen Staaten auf den neuen NSA-Abhörskandal hat deutlich gezeigt, dass die EU-Staaten nur Vasallen der USA sind, die sich alles gefallen lassen und im Gegenzug - auch zum eigenen Schaden - die US-Politik wunschgemäß umsetzen. Der neue NSA-Abhörskandal wurde in den westlichen Medien kurz erwähnt und dann schnell wieder vergessen. Dazu hat das russische Fernsehen am Sonntag in der Sendung "Nachrichten der Woche" einen kurzen Kommentar gebracht, den ich übersetzt habe.a
Beginn der Übersetzung:
Ein Skandal, der riesig hätte werden können, wenn die Europäer von den regelmäßigen Schikanen der USA nicht so müde wären und wenn die amerikanische Presse die Begriffe "Gewissen" und "Scham" nicht völlig vergessen hätte. Es kam heraus, dass Amerika einen Partnerstaat in Kontinentaleuropa hatte, von dessen...
https://uncutnews.ch/ausserhalb-europas-herrscht-unverstaendnis-ueber-die-nicht-reaktion-der-europaeer-auf-den-nsa-abhoerskandal/
https://www.anti-spiegel.ru/2021/ausserhalb-europas-herrscht-unverstaendnis-ueber-die-nicht-reaktion-der-europaeer-auf-den-nsa-abhoerskandal/
Neuer NSA-Abhörskandal
Außerhalb Europas herrscht Unverständnis über die Nicht-Reaktion der Europäer auf den NSA-Abhörskandal, uncut-news.ch, 07.06.2021
Der neue NSA-Abhörskandal findet in den Medien praktisch nicht statt, er wurde kurz gemeldet und ist dann schnell wieder verschwunden. Ein Nachruf aus dem russischen Fernsehen.
Die Reaktion der europäischen Staaten auf den neuen NSA-Abhörskandal hat deutlich gezeigt, dass die EU-Staaten nur Vasallen der USA sind, die sich alles gefallen lassen und im Gegenzug - auch zum eigenen Schaden - die US-Politik wunschgemäß umsetzen. Der neue NSA-Abhörskandal wurde in den westlichen Medien kurz erwähnt und dann schnell wieder vergessen. Dazu hat das russische Fernsehen am Sonntag in der Sendung "Nachrichten der Woche" einen kurzen Kommentar gebracht, den ich übersetzt habe.a
Beginn der Übersetzung:
Ein Skandal, der riesig hätte werden können, wenn die Europäer von den regelmäßigen Schikanen der USA nicht so müde wären und wenn die amerikanische Presse die Begriffe "Gewissen" und "Scham" nicht völlig vergessen hätte. Es kam heraus, dass Amerika einen Partnerstaat in Kontinentaleuropa hatte, von dessen...
https://uncutnews.ch/ausserhalb-europas-herrscht-unverstaendnis-ueber-die-nicht-reaktion-der-europaeer-auf-den-nsa-abhoerskandal/
https://www.anti-spiegel.ru/2021/ausserhalb-europas-herrscht-unverstaendnis-ueber-die-nicht-reaktion-der-europaeer-auf-den-nsa-abhoerskandal/
 Verfassungsschutz und Bundespolizei Verfassungsschutz und Bundespolizei
Bundestag beschließt Staatstrojaner für Geheimdienste und vor Straftaten, netzpolitik.org, 13.06.2021
Der Bundestag hat die beiden Staatstrojaner-Gesetze angenommen. Das neue Verfassungsschutz-Recht erlaubt allen Geheimdiensten die "Quellen-TKÜ plus". Was die Große Koalition als Sicherheitsgewinn feiert, schafft neue Sicherheitsrisiken und ist möglicherweise verfassungswidrig.
Der Bundestag hat gestern mit einer Mehrheit von 355 Stimmen aus CDU/CSU und SPD das Gesetz zur Anpassung des Verfassungsschutzrechts angenommen. Es erlaubt allen 19 Geheimdiensten Geräte wie Smartphones oder Computer mit Staatstrojanern zu hacken. Alle Oppositionsparteien haben das Gesetz zuvor heftig kritisiert und dagegen gestimmt.
[...] Bereits am Dienstagabend hatte sich die Große Koalition auf einen Änderungsantrag geeinigt. Mit dem Gesetz bekommen die Verfassungsschutzämter auf Bundes- und Länderebene, der Militärische Abschirmdienst und der Bundesnachrichtendienst die Erlaubnis, Geräte zu hacken um Kommunikation auszulesen.
Außerdem verpflichtet das Gesetz Internet-Provider, bei der Installation von Schadsoftware zu helfen. Andere Telekommunikationsanbieter wie Messenger- oder E-Maildienste sind davon ausgenommen. Die G-10-Kommission soll um sechs Richter:innen verstärkt die Fälle kontrollieren, in denen Staatstrojaner zum Einsatz kommen.
Die Quellen-Telekommunikationsüberwachung (Quellen-TKÜ), auch "kleiner Staatstrojaner" genannt, bedeutet, dass Behörden Schadsoftware auf Geräten installieren und ab diesem Zeitpunkt laufende Kommunikation überwachen. Der große Staatstrojaner, die "Online-Durchsuchung", leitet nicht nur laufende, sondern auch gespeicherte Daten aus - zum Beispiel ältere Chatnachrichten, die vor der Installation der Schadsoftware gesendet und empfangen wurden.
Quellen-TKÜ plus: mehr als der kleine Staatstrojaner
Bei der nun beschlossenen Verfassungsschutzrechts-Novelle handelt es sich um einen Kompromiss aus kleinem und großem Staatstrojaner: die "Quellen-TKÜ plus". Diese ermöglicht den Zugriff auf laufende Kommunikation plus die Kommunikation, die vor Installation der Schadsoftware, aber nach Anordnung der Überwachungsmaßnahme stattgefunden hat.
Ursprünglich wollte Innenminister Horst Seehofer mit seinem ersten Gesetzentwurf im März 2019 den großen Staatstrojaner für BND und Verfassungsschutz durchsetzen. Damals stieß das noch auf heftige Kritik beim Koalitionspartner SPD. Die Parteivorsitzende Saskia Esken sagte, sie lehne Staatstrojaner ab, die SPD werde das Vorhaben der Union nicht unterstützen.
Der zweite Gesetzentwurf des Innenministeriums im Juni 2019 sah dann den kleinen Staatstrojaner vor - aber für alle 19 Geheimdienste. Und die Kritik der SPD verstummte mehr und mehr: Im Oktober 2020 setzte sich das Innenministerium mit seinem Vorschlag durch und die Koalition einigte sich, alle Geheimdienste mit Staatstrojanern auszustatten.
Verfassungswidrig und schädlich für innere Sicherheit
Viele Sachverständige und Jurist:innen schätzen die Quellen-TKÜ als verfassungswidrig ein, da sie weit in die Grundrechte eingreift. Die Gesellschaft für Freiheitsrechte erwägt, gegen die Regelung zu klagen. Gegen andere Gesetze, die den Einsatz von Staatstrojanern erlauben, laufen bereits Verfahren vor dem Bundesverfassungsgericht.
Auch die Organisation Reporter ohne Grenzen kündigte gestern an, mit dem Berliner Rechtsanwalt Prof. Niko Härting Verfassungsbeschwerde einzulegen. Sie sieht die Pressefreiheit und den digitalen Quellenschutz durch das Gesetz bedroht. "Einen so massiven Angriff auf die Vertraulichkeit journalistischer Recherchen und die Anonymität von Quellen dürfen wir nicht hinnehmen", so Geschäftsführer Christian Mihr.
Kritik an den Staatstrojanern vereint auch internationale Tech-Konzerne wie Google und Facebook mit zivilgesellschaftlichen Organisationen wie dem Chaos Computer Club, die sich in einem offenen Brief gegen diese Form von Überwachung wehren.
Die Unionsfraktion begründet den Einsatz von Staatstrojanern damit, dass man den Verfassungsschutz so auf den Stand der Technik bringe. "Als die Leute sich noch mit Rauchzeichen oder Topfschlagen verständigt haben, da konnte jeder mithören", so der CDU Abgeordnete Mathias Middelberg in der Aussprache im Bundestag. Die Quellen-TKÜ plus sei einfach "die Anpassung an technische Verhältnisse" und wichtig, um Terrorismus abzuwehren und die innere Sicherheit zu verbessern.
Es sei "ein guter Tag für die Sicherheit in Deutschland", meinte der CSU-Abgeordnete Michael Kuffer im Bundestag. "Ein massives Sicherheitsproblem, was sie hier veranstalten", nannte es der Grünen-Abgeordnete Konstantin von Notz. Auch Stephan Thomae von der FDP warnte vor dem Sicherheitsrisiko, das Staatstrojaner mit sich bringen.
Staatstrojaner brauchen offene Sicherheitslücken
Um Staatstrojaner zu installieren, müssen Behörden IT-Sicherheitslücken auf Geräten ausnutzen. Es entsteht also ein Anreiz, bekannte Sicherheitslücken offen zu halten. Und das kann der inneren Sicherheit mehr schaden als nützen.
https://netzpolitik.org/2021/verfassungsschutz-und-bundespolizei-bundestag-beschliesst-staatstrojaner-fuer-geheimdienste-und-vor-straftaten/
Es geht gar nicht um abgehörte Spitzenpolitiker, sondern um aufgeblähte Geheimdienstapparate, die niemand kontrolliert
Ausspähen unter Freunden
Merkels Geheimdienst-Bla-Bla-Blamage, netzpolitik.org, 01.06.2021
Es gibt neue brisante Enthüllungen über geheimdienstliche Überwachung, die es eigentlich nicht geben durfte. Aber nach ein bisschen öffentlicher Verharmlosung und Beschwichtigung gehen wieder alle zur Tagesordnung über. Doch es geht gar nicht um abgehörte Spitzenpolitiker, sondern um aufgeblähte Geheimdienstapparate, die niemand kontrolliert.
https://netzpolitik.org/2021/ausspaehen-unter-freunden-merkels-geheimdienst-bla-bla-blamage/
 Bundespolizeigesetz Bundespolizeigesetz
Große Koalition einigt sich auf Staatstrojaner-Einsatz schon vor Straftaten, netzpolitik.org, 13.06.2021
Die Bundespolizei soll Staatstrojaner gegen Personen einsetzen, die noch gar keine Straftat begangen haben. Darauf haben sich SPD und Union im Bundestag geeinigt, übermorgen wollen sie das Gesetz beschließen. Die SPD-Vorsitzende Saskia Esken hatte eigentlich angekündigt, das "auf keinen Fall" mitzutragen.
https://netzpolitik.org/2021/bundespolizeigesetz-grosse-koalition-einigt-sich-auf-staatstrojaner-einsatz-schon-vor-straftaten/
 BND-Gesetz BND-Gesetz
Bundesnachrichtendienst erhält so viele Überwachungsbefugnisse wie noch nie, netzpolitik.org, 26.03.2021
Der Bundesnachrichtendienst darf jetzt Internet-Anbieter hacken und fast unbegrenzt abhören. Bundestag und Bundesrat haben das neue BND-Gesetz beschlossen. Vor ein paar Jahren waren solche Geheimdienst-Befugnisse ein Skandal. Nichtregierungsorganisation kündigen rechtliche Schritte an.
https://netzpolitik.org/2021/bnd-gesetz-bundesnachrichtendienst-erhaelt-so-viele-ueberwachungsbefugnisse-wie-noch-nie/
 Bündnisse: Five Eyes, Nine Eyes, ... Bündnisse: Five Eyes, Nine Eyes, ...
"Wir töten Leute auf der Basis von Metadaten"
Hacking und Spionage
Ist WhatsApp sicher genug für die Diplomatie?, netzpolitik.org, 24.02.2020
In den Korridoren der Macht ist der Messengerdienst das Mittel der Wahl. Nun empfehlen EU-Experten den Wechsel zu Signal. Hat WhatsApp in der Diplomatie ausgedient?
[...] Doch Sicherheitslücken bei WhatsApp werfen Fragen auf. Der Beliebtheit der App schaden könnten auch die Cryptoleaks-Enthüllungen. Sie zeigen, dass die USA und Deutschland über Jahrzehnte systematisch die verschlüsselte Kommunikation ihrer Verbündeten belauschten.
Der NSA-Skandal vor sechs Jahren rüttelte am Image des Mutterkonzerns Facebook. Die Affären schüren Zweifel, ob ein US-amerikanischer Gratisdienst wie WhatsApp tatsächlich die nötigen Maßnahmen trifft, um den sensiblen Austausch unter EU-Staaten vor dem Zugriff von Geheimdiensten und Spionage aus Russland und China zu schützen.
[...] WhatsApp verwendet zur Verschlüsselung das gleiche Protokoll wie Signal, das von Überwachungsgegnern wie etwa NSA-Enthüller Edward Snowden empfohlen wird. Diese Verschlüsselung ist mit heutiger Technik schwer zu knacken.
Das gilt jedoch nicht für die Metadaten. Bei den Metadaten handelt es sich um Angaben über Sender und Empfänger, Zeit und Datum sowie Nachrichtengröße.
Aus den Metadaten lässt sich ablesen, wer mit wem kommuniziert. Durch die Dateigröße lassen sich Rückschlüsse treffen, ob etwa Bilder oder Videos mitgeschickt wurden.
Der Facebook-Konzern speichert Metadaten zentral auf seinen Servern. WhatsApp greift zudem regulär auf das gesamte Telefonbuch im Handy der Nutzer:innen zu. WhatsApp teilt die Daten mit Facebook.
Signal speichert nach eigenen Angaben möglichst wenige Informationen über Nutzer:innen. Der Dienst verschlüsselt Metadaten und löscht sie von seinen Servern, sobald die Nachricht verschickt ist.
Schrems: "Metadaten gehen an US-Behörden"
Geheimdienste drängen auf den verpflichtenden Einbau von Hintertüren in Messengerdienste, um verschlüsselte Nachrichteninhalte lesen zu können. WhatsApp, Apple sowie ein breites Bündnis aus Firmen und NGOs wehren sich dagegen - bisher erfolgreich.
Metadaten verraten aber oft genausoviel wie Nachrichteninhalte. In der Diplomatie geht es um Netzwerke, um vertrauliche Absprachen. Schreibt eine französische Diplomatin ihrem deutschen Gegenüber vor der entscheidenden Abstimmung, ist das Wissen darum nicht ebenso bedeutend wie der Inhalt?
[...] Eine drastische Illustration der möglichen Konsequenzen des Datenzugriffs durch US-Geheimdienste brachte der frühere NSA-Chef Michael Hayden auf den Punkt: "Wir töten Leute auf der Basis von Metadaten".
Der deutsche Bundesdatenschutzbeauftragte Ulrich Kelber sieht die Nutzung von WhatsApp durch von ihm beaufsichtigte Behörden "kritisch", schrieb uns sein Pressesprecher. Kelber bemängelt, dass Metadaten von WhatsApp an Facebook weitergeleitet werden.
Der österreichische Datenschützer Max Schrems formuliert es gegenüber netzpolitik.org drastischer: "Die Metadaten gehen direkt an Facebook und damit auch an die amerikanischen Geheimdienste. Allein wer wann wie oft mit wem kommuniziert, kann extrem viele Rückschlüsse erlauben."
Facebook antwortete nicht auf die Frage von netzpolitik.org, wie es die Metadaten seiner Nutzer:innen wirksam vor dem Zugriff durch US-Geheimdienste schützen möchte.
[...] Diplomaten und EU-Beamte müssen generell damit rechnen, belauscht zu werden. Brüssel gilt seit Jahren als Spionagehochburg, erst im Januar geriet ein prominenter deutscher Ex-Diplomat wegen mutmaßlicher Spionage für China unter Verdacht.
Doch solche Fälle sind eher selten: Der Großteil der Spionage läuft vermutlich elektronisch ab.
Die NSA-Affäre enthüllte 2013 ein massives Abhörprogramm der USA gegen EU-Diplomaten in Brüssel und an den UN-Sitzen in Wien und Genf.
Am Schweizer Sitz der Vereinten Nationen war Whistleblower Edward Snowden stationiert, als er noch für den US-Geheimdienst spionierte. Snowden sagte später, die USA spioniere weiterhin in Genf und anderen Orten.
Engster Verbündeter der USA in Geheimdienstangelegenheiten ist Großbritannien. Gemeinsam mit Kanada, Australien und Neuseeland bilden die Staaten die Five-Eyes-Allianz.
Für die technisch hochgerüsteten Dienste sind die EU-Staaten attraktive Ziele, besonders nach dem Brexit.
[...] Diplomaten und EU-Beamte müssen generell damit rechnen, belauscht zu werden. Brüssel gilt seit Jahren als Spionagehochburg, erst im Januar geriet ein prominenter deutscher Ex-Diplomat wegen mutmaßlicher Spionage für China unter Verdacht.
Doch solche Fälle sind eher selten: Der Großteil der Spionage läuft vermutlich elektronisch ab.
Die NSA-Affäre enthüllte 2013 ein massives Abhörprogramm der USA gegen EU-Diplomaten in Brüssel und an den UN-Sitzen in Wien und Genf.
Am Schweizer Sitz der Vereinten Nationen war Whistleblower Edward Snowden stationiert, als er noch für den US-Geheimdienst spionierte. Snowden sagte später, die USA spioniere weiterhin in Genf und anderen Orten.
Engster Verbündeter der USA in Geheimdienstangelegenheiten ist Großbritannien. Gemeinsam mit Kanada, Australien und Neuseeland bilden die Staaten die Five-Eyes-Allianz.
Für die technisch hochgerüsteten Dienste sind die EU-Staaten attraktive Ziele, besonders nach dem Brexit.
[...] Wer aus beruflichen oder persönlichen Gründen die Möglichkeit eines Zugriffs auf Metadaten durch US-Geheimdienste verringern will, solle zu anderen Diensten wie Signal greifen, empfiehlt Jan Penfrat von EDRi.
Als Alternativen nennt der NGO-Experte neben Signal Dienste wie die Messengern Threema oder Wire, beide mit Sitz in der Schweiz, oder das Open-Source-Projekt Matrix, dessen Technologie von der Bundeswehr genutzt wird.
Die EU-Kommission verfolgt allerdings andere Pläne. In der Notiz, die wir veröffentlichen, ist Signal nur als Zwischenlösung gedacht. Längerfristig rät die Gruppe zu Skype for Business, einem Dienst von Microsoft.
Eine Lösung, die unabhängig von US-Konzernen und Geheimdiensten ist, liegt offenbar noch weiter in der Ferne.
[...] Diplomaten und EU-Beamte müssen generell damit rechnen, belauscht zu werden. Brüssel gilt seit Jahren als Spionagehochburg, erst im Januar geriet ein prominenter deutscher Ex-Diplomat wegen mutmaßlicher Spionage für China unter Verdacht.
Doch solche Fälle sind eher selten: Der Großteil der Spionage läuft vermutlich elektronisch ab.
Die NSA-Affäre enthüllte 2013 ein massives Abhörprogramm der USA gegen EU-Diplomaten in Brüssel und an den UN-Sitzen in Wien und Genf.
Am Schweizer Sitz der Vereinten Nationen war Whistleblower Edward Snowden stationiert, als er noch für den US-Geheimdienst spionierte. Snowden sagte später, die USA spioniere weiterhin in Genf und anderen Orten.
Engster Verbündeter der USA in Geheimdienstangelegenheiten ist Großbritannien. Gemeinsam mit Kanada, Australien und Neuseeland bilden die Staaten die Five-Eyes-Allianz.
Für die technisch hochgerüsteten Dienste sind die EU-Staaten attraktive Ziele, besonders nach dem Brexit.
[...] Wer aus beruflichen oder persönlichen Gründen die Möglichkeit eines Zugriffs auf Metadaten durch US-Geheimdienste verringern will, solle zu anderen Diensten wie Signal greifen, empfiehlt Jan Penfrat von EDRi.
Als Alternativen nennt der NGO-Experte neben Signal Dienste wie die Messengern Threema oder Wire, beide mit Sitz in der Schweiz, oder das Open-Source-Projekt Matrix, dessen Technologie von der Bundeswehr genutzt wird.
Die EU-Kommission verfolgt allerdings andere Pläne. In der Notiz, die wir veröffentlichen, ist Signal nur als Zwischenlösung gedacht. Längerfristig rät die Gruppe zu Skype for Business, einem Dienst von Microsoft.
Eine Lösung, die unabhängig von US-Konzernen und Geheimdiensten ist, liegt offenbar noch weiter in der Ferne.
https://netzpolitik.org/2020/ist-whatsapp-sicher-genug-fuer-die-diplomatie/
https://netzpolitik.org/2020/is-whatsapp-safe-for-diplomats/
Ex-CIA-Offizier im Interview zum US-Drohnenprogramm: Wir töten ohne jede rechtliche Grundlage, uncutnews.ch, 12.04.2021
https://ex-cia-offizier-im-interview-zum-us-drohnenprogramm-wir-toeten-ohne-jede-rechtliche-grundlage/
Immer mehr Unternehmen schnüffeln uns aus, digitalcourage.de, gesehen am 09.09.2018
Suchmaschinen, soziale Netzwerke und andere "Gratis"-Dienste sammeln rund um die Uhr persönliche Daten. Daraus erstellen sie Verhaltensprofile, mit denen sie Profit machen: Die Daten werden verkauft an Versicherungen oder Werbeunternehmen. Auf diese Weise verletzten Datenkraken an vielen Stellen unsere Persönlichkeitsrechte, in dem sie ohne Zustimmung Daten auswerten, weiterverkaufen oder auch an Geheimdienste weiterleiten. Sie rauben uns die Kontrolle über unsere Daten und schränken die freie Kommunikation im Internet ein. Sie gehen sogar soweit, dass sie behaupten zu wissen, was wir brauchen, fühlen und denken. Einige Datenkraken verdienen ihr Geld mit der Bewertung von Menschen. Dieses Vorgehen wird "Scoring" genannt. Wer zum Beispiel im "richtigen" Stadtteil lebt, bekommt eine Ware auf Rechnung. Eine andere Person nicht. Auch Google ist nicht neutral und zeigt personalisierte Suchergebnisse an. Datenkraken behandeln Menschen nicht gleichwertig und diskriminieren sie. Darum klärt Digitalcourage über Datenkraken auf. An besonders bissige Exemplare verleihen wir jährlich die Big-Brother-Awards, .http://bigbrotherawards.de/
Hintergrund zu kommerziellen Datenkraken
Wenn wir bei Google suchen, auf Facebook posten oder mit Paypal bezahlen, nutzen wir kostenlose Dienste, die sehr viel Geld mit unsere Daten verdienen. Wir erläutern wie das Geschäft mit den Daten funktioniert.
Auf dieser Seite haben wir Links gesammelt, die über kommerzielle Datenkraken wie Google, Facebook, Twitter, PayPal, Apple und Co. informieren.
Facebook - eine Grundsatzentscheidung
Jede Organisation steht vor der Entscheidung: "Wollen wir Facebook nutzen oder nicht?" Facebook bedeutet eine vermeintlich größere Reichweite, vor allem aber Auslieferung vieler Daten. Wir haben eine Grundsatzentscheidung getroffen, die auch Ihnen helfen kann.
Den BigBrotherAward 2013 in der Kategorie Globales Datensammeln erhielt Google Inc. Die Laudatio hielten Rena Tangens und padeluun.
Verfassungsbeschwerde gegen Staatstrojaner
Die Große Koalition hat Staatstrojaner in die Strafprozessordnung gebracht, wir klagen in Karlsruhe dagegen. Der Einbruch in unsere Geräte gefährdet die Privatsphäre und die IT-Sicherheit. Verleihen Sie unserer Forderung mit Ihrer Unterschrift mehr Gewicht: Staatstrojaner Stoppen!
Der BigBrotherAward 2015 in der Kategorie "Wirtschaft" ging an die Crowdworking-Plattformen Amazon Mechanical Turk und Upwork (vormals Elance-oDesk) für die Einführung des digitalen Tagelöhnertums mit Arbeitsbedingungen wie in den Anfängen der Industrialisierung plus elektronische Komplettüberwachung - alles natürlich komplett "freiwillig". Die Laudatio hielt Rena Tangens.
Der BigBrotherAward 2012 in der Kategorie "Kommunikation" ging an die Cloud als Trend, den Nutzerinnen und Nutzern die Kontrolle über ihre Daten zu entziehen. Laudatio von Rena Tangens.
PM: "Schutzranzen": Neue Version ist keine Lösung, sondern ein Problem
Der Datenschutz- und Grundrechteverein Digitalcourage warnt vor der neuen Version der "Schutzranzen"-Apps. Laut Medienberichten plant die Stadt Ludwigsburg Kinder-Tracking flächendeckend einzuführen, trotz Kritik von vielen Seiten. Digitalcourage fordert, dass nach Wolfsburg auch die Stadt Ludwigsburg den Kinder-Tracking-Test an Grundschulen abbricht.
Kommt mit uns ins Fediverse
Facebook und Twitter sind nicht (mehr) alternativlos. Jetzt liegt es v.a. an den "Influencern", diese Alternativen attraktiv zu machen.
PM Digitalcourage: Stadt Ludwigsburg hält weiter an Kinder-Tracking fest - Autoindustrie auf Überwachungskurs
Die Stadt Ludwigsburg will trotz Kritik vernetztes Fahren mit Tracking von Grundschulkindern realisieren - Ehemaliger Autolobbyist und jetziger Referent für Stadtentwicklung stellt sich taub für Kritik.
Ludwigsburg: Beenden Sie das Kinder-Tracking mit "Schutzranzen"!
Die Stadt Ludwigsburg hält an Kinder-Tracking fest - hier ist unsere Antwort auf eine Einladung zu einem runden Tisch.
Google Inc.
Mountain View, Kalifornien, USA.
Bei diesem Preisträger kritisieren wir nicht einen einzelnen Datenschutzverstoß. Wir prangern auch nicht einzelne Sätze in seinen Geschäftsbedingungen an. - Nein, der Konzern selbst, sein globales, allumfassendes Datensammeln, die Ausforschung der Nutzerinnen und Nutzer als Wesenskern seines Geschäftsmodells und sein de facto Monopol - das ist das Problem.
..
US-Regierung drängt Unternehmen zu verstärktem Datenaustausch, Tagesschau, 14.02.2015
Obama beim Gipfeltreffen zur Datensicherheit beim Kampf gegen Cyberkriminalität: Ein "Gipfel", bei dem einige fehlten, Tagesschau, 14.02.2015
Barack Obama hatte zum "Gipfel für Cybersicherheit" geladen, doch die Che
Deutschland ist für den US-Konzern der zweitgrößte Markt nach den USA. In den ersten Monaten der Infektionswelle blieben viele Geschäfte geschlossen und Kunden kauften verstärkt im Internet ein.
... einiger der wichtigsten der Branche kamen nicht. Denn während die US-Regierung vor der Gefahr durch Hacker warnt, sehen Internetkonzerne noch eine ganz andere Bedrohung: die Regierung.
US-Präsident Barack Obama hat die großen Internetfirmen im Silicon Valley zur Zusammenarbeit mit dem Staat im Kampf gegen Hackerangriffe aufgerufen. "Das muss eine gemeinsame Mission sein", sagte Obama beim "Summit on Cybersecurity" und betonte, dies sei eine Frage der nationalen Sicherheit. Ein großer Teil der Computernetze und der kritischen Infrastruktur sei im Besitz von Privatfirmen. Daher könne die Regierung nicht allein für die Sicherheit im Internet sorgen, so Obama. "Aber Tatsache ist, dass der Privatsektor es auch nicht alleine tun kann, weil die Regierung oft die aktuellsten Informationen über neue Bedrohungen hat."
Heimatschutzministerium und Firmen sollen zusammenarbeiten
https://www.tagesschau.de/wirtschaft/amazon-kartellamt-vorwuerfe-101.html
Follow up more such reports: News&Links, News&Links#NSA_GHCQ_&Co
Flood-water-damages: Which insurance does pay?
Collapsed houses, swamped cellars, damaged vehicles - which insurance can help against these harms?, tagesschau.de, 16.07.2021
https://www.tagesschau.de/wirtschaft/verbraucher/unwetter-versicherung-zahlungen-101.html
Past thunderstorms
The dimension of damages of the infrastructure isn´t clear, tagesschau.de, 19.07.2021
Destroyed rails and bridges, inaccessible highways - and a mobile net full of gaps:
https://www.tagesschau.de/inland/infrastruktur-schaeden-101.html
Germany
Emergency service: "Our warn-system has functioned", tagesschau.de, 19.07.2021
More than 160 people are dead, plenty of property damages: Could this be prevented by better warnings? Experts talk about neglects, the chief of concerning authority rejects the critics.
https://www.tagesschau.de/inland/unwetter-katastrophenschutz-kritik-103.html
 World Economic Forum / Cyber Polygon: Jedes einzelne Gerät vom Internet trennen, uncut-news.ch, 29.06.2021 World Economic Forum / Cyber Polygon: Jedes einzelne Gerät vom Internet trennen, uncut-news.ch, 29.06.2021
Ein kleines Video, dass die bei der Cyber Poligon Simulation zu entwickelnde Schutz-Lösung bei einem angeblichen "Cyber Angriff" als Ziel der Veranstaltung andeutet: Die Abschaltung des Internets.
https://uncutnews.ch/world-economic-forum-cyber-polygon-jedes-einzelne-geraet-vom-internet-trennen/
"Das Internet muss weg!"
Schlecky Silberstein surft in unserer Filterbubble
Christian Brandes aka Schlecky Silberstein würde gern das Medium abschaffen, das ihn ernährt. In "Das Internet muss weg" beschreibt der Blogger, wie wir von Algorithmen, Trollen und Tech-Firmen gebrainwasht werden. Aber ist er nicht selbst ein Teil davon? Eine Rezension.
https://netzpolitik.org/2018/schlecky-silberstein-surft-in-unserer-filterbubble/
 Experte über Privatsphäre: "Ich frage mich ständig, warum die Leute das alles noch mitmachen", STERN.de, 09.06.2019 Experte über Privatsphäre: "Ich frage mich ständig, warum die Leute das alles noch mitmachen", STERN.de, 09.06.2019
Marc Al-Hames kennt alle Tricks der Werbeindustrie. Im Gespräch mit dem Stern erklärt er, warum die plötzlichen Datenschutz-Bekenntnisse einiger Konzerne nicht ernstzunehmen sind und was der größte Unterschied zwischen Apple und Google in puncto Datenschutz ist.
[...]."Facebook zum Beispiel hat Privatsphäre nie verstanden und versteht sie auch jetzt nicht."
[...] "Umfragen zufolge liest der Großteil der Nutzer keine Geschäftsbedingungen und stimmt allen Anfragen zu."
https://www.stern.de/digital/online/datenschutz---die-werbe-industrie-kann-uns-ueber-alle-geraete-hinweg-verfolgen--denen-entgeht-nichts--8723748.html
Betrüger kaum zu belangen
Hunderte Spendenmillionen versickern, tagesschau.de, 09.07.2019
Nach Recherchen von Report Mainz werden jedes Jahr Hunderte Millionen Euro an Spendengeldern nicht ordnungsgemäß verwendet. Die Rechtslage macht es Betrügern dabei leicht.
https://www.tagesschau.de/investigativ/report-mainz/spendenbetrug-101.html
 Offenlegung der Identität, VPN-Anbieter sehen und speichern, was der Nutzer macht, Nutzerdaten-Weitergabe, Sperrlisten, Deep-Package-Inspection-Systeme der Provider Offenlegung der Identität, VPN-Anbieter sehen und speichern, was der Nutzer macht, Nutzerdaten-Weitergabe, Sperrlisten, Deep-Package-Inspection-Systeme der Provider
Netzfreiheit
Russland zieht Tor-Browser den Stecker, tagesschau.de, 11.12.2021
Russland stellt weltweit die zweitgrößte Nutzergruppe des Anonymisierungs-Browsers Tor - doch die russische Medienaufsicht blockiert schrittweise den Zugang. Nicht nur Journalisten sehen sich dadurch weiter eingeschränkt.
Russlands Medienaufsichtsbehörde Roskomnadsor hat große Teile des Tor-Netzwerks blockiert, mit dem Nutzer anonym im Netz surfen und auch das Darknet betreten können - ein Schritt, der die Informationsfreiheit im Land weiter einschränkt.
Nach Angaben der Organisation RosKomSvoboda, die sich für Anonymität und gegen Zensur im Internet einsetzt, begann die Blockierung von Tor am 1. Dezember: Nutzer in Moskau, Sankt Petersburg, Jekaterinburg und vielen weiteren russischen Städten meldeten, dass sie keine Verbindung zum Tor-Netzwerk herstellen konnten.
Nur wenige Tage später, am 7. Dezember, erhielten die Internet-Aktivisten des Tor-Projekts eine Aufforderung von Roskomnadsor, "verbotene" Inhalte auf ihrer Website zu löschen. Andernfalls drohe der Website eine Sperrung. Welche Inhalte damit gemeint waren, nannte die Behörde nicht. Die Blockade folgte noch am selben Tag.
Probleme bei der Nutzung des Anonymisierungsdienstes habe es bereits seit Herbst geben, berichtet eine Journalistin der Nowaja Gaseta: Die ohnehin langsame Verbindung sei gedrosselt. Sie nutzt den Tor-Browser, um abseits von staatlicher Beobachtung ihrer Recherche nachzugehen - denn der Browser verwische ihre digitalen Spuren im Netz, erklärt sie.
In Russland nutzen rund 300.000 Menschen täglichen den Dienst. Damit hat das Land nach den USA die zweitgrößte Nutzergruppe. Auf Twitter forderte Edward Snowden, der das Tor-Netzwerk selbst nutzte, ein Ende der Blockierung.
VPN keine Ausweichmöglichkeit
"Tor ist eine Möglichkeit, sicher und verschlüsselt zu kommunizieren und Informationen auszutauschen", erklärt Lisa Dittmar, Referentin für Internetfreheit bei Reporter ohne Grenzen (RSF). "Es gibt viele gute Gründe, Netzwerke wie Tor aufrechtzuerhalten. Besonders in Ländern wie Russland, wo Journalisten kriminalisiert werden und deren Arbeit lebensgefährlich sein kann. Im russischen Internet hat die Regierung bereits viele Möglichkeiten, zu verfolgen, zu welchen Themen jemand recherchiert und mit wem die Person spricht." Daher unterstütze RSF mit finanziellen Mitteln den Betrieb zweier Tor-Server.
Zwar seien VPN-Dienste eine Alternative zum Tor-Netzwerk, sagt Dittmar - jedoch sei bei diesen die Offenlegung der Identität gegenüber dem VPN-Betreiber ein Problem: "Der sieht und speichert, was der Nutzer macht. Es besteht die Gefahr, dass sich VPN-Betreiber staatlichen Forderungen beugt und die Nutzerdaten weitergibt. Das ist ein reales Problem in Russland." Tatsächlich sperrte Roskomnadsor parallel zur Blockade des Tor-Netzwerks eine Vielzahl an VPN-Diensten.
Roskomnadsor blockiert IP-Adressen
Tor, Abkürzung für "The Onion Router", funktioniert wie eine Zwiebel: Der Browser leitet den Internetverkehr mehrfach um, sodass nicht mehr klar ist, von wem eine Nachricht kommt und an wen sie geht. Jede Umleitung stellt eine Zwiebelschicht dar, die sich über die Identität des Senders legt.
Da das Tor-Netzwerk aber ein öffentliches Netzwerk ist und die IP-Adressen aller Tor-Portale öffentlich gelistet sind, ist es relativ einfach, direkte Tor-Verbindungen zu blockieren. Die russische Regierung versucht nun zu unterbinden, dass die Menschen in Russland überhaupt Kontakt mit einem dieser Tor-Portale aufnehmen können.
Um die aktuelle Blockade zu umgehen, sind die Internet-Aktivisten rund um das Tor-Projekt dazu übergegangen, sogenannte Bridges, Brücken, zu erstellen - das sind nicht öffentliche IP-Adressen. Sie dienen als alternative Portale zum Tor-Netzwerk und sind schwieriger zu blockieren.
Auf dem Weg ins "souveräne Runet"
Doch Roskomnadsor ist den Aktivisten bereits auf den Fersen: "Wir haben Beweise dafür gefunden, dass die russische Regierung nicht nur die öffentlichen IP-Adressen im Tor-Netzwerk blockiert, sondern auch die nicht-öffentlichen", erklärt Gustavo Gus, der beim Tor-Projekt den Community-Bereicht leitet. "Das bedeutet, die russische Regierung setzt Zensurtechnologien in Form von Deep-Package-Inspection-Systemen (DPI) ein. Provider werden dazu verpflichtet, diese Systeme einzubauen. Sie analysieren Datenpakete nach vorher festgelegten Kriterien, blockieren oder verlangsamen die Übertragung."
Stanislav Shakirov, technischer Direktor von RosKomSvoboda, sieht darin ein "typisches" Vorgehen der Behörde, wie er sagt: Sie gehe in kleinen Schritten vor, teste die Blockierung, beobachte, was passiert. Neben den technischen Erkenntnissen habe Roskomonadsor aber auch gesehen, dass viele Menschen bereit seien, ihr Recht zur Tor-Nutzung zu verteidigen.
Dennoch, ist Shakirov überzeugt, beginne die Regierung jetzt Schritt für Schritt, das russische Internet vom Rest der Welt zu isolieren - und schaffe sich stetig ein "souveränes russisches Internet".
https://www.tagesschau.de/ausland/europa/tor-russland-101.html
"Das Internet muss weg!"
Schlecky Silberstein surft in unserer Filterbubble
Christian Brandes aka Schlecky Silberstein würde gern das Medium abschaffen, das ihn ernährt. In "Das Internet muss weg" beschreibt der Blogger, wie wir von Algorithmen, Trollen und Tech-Firmen gebrainwasht werden. Aber ist er nicht selbst ein Teil davon? Eine Rezension.
https://netzpolitik.org/2018/schlecky-silberstein-surft-in-unserer-filterbubble/
Urheberrecht
Springer-Verlag verliert erneut gegen Adblock-Hersteller Eyeo, netzpolitik.org, 19.01.2022
Die Browser-Erweiterung Adblock Plus verstößt nicht gegen das Urheberrecht, urteilte das Landgericht Hamburg. Der Axel-Springer-Verlag wollte mit der vorerst gescheiterten Klage verhindern, dass das Plug-in Werbeanzeigen auf seinen Webseiten ausblendet.
https://netzpolitik.org/2022/urheberrecht-springer-verlag-verliert-erneut-gegen-adblock-hersteller-eyeo/
Urteil: Ad-Blocker verstoßen nicht gegen Wettbewerbsrecht, PC-WELT.de, 18.08.2017
Laut einem aktuellen Urteil des OLG München verstoßen Ad-Blocker nicht gegen Kartell-, Wettbewerbs- und Urheberrecht.
https://www.pcwelt.de/a/urteil-ad-blocker-verstossen-nicht-gegen-wettbewerbsrecht,3447802
Gerichtsurteil Internet-Werbeblocker sind zulässig, tagesschau.de, 17.08.2017
Programme, mit denen Internetnutzer Werbung beim Surfen blockieren können, sind zulässig. Das entschieden Richter des Münchner Oberlandesgerichts. Damit bestätigten sie auch das Geschäftsmodell, bei dem Unternehmen sich "freikaufen", damit ihre Anzeige doch zu sehen ist.
Blinkende Banner und bildschirmfüllende Einblendungen: Wer sich beim Surfen im Internet vor aufdringlicher Werbung schützen will, nutzt einen Werbeblocker - eine Browsererweiterung, die Reklame im Internet blockiert. Medienunternehmen sind nun mit einer Klage gegen Adblocker vor dem Oberlandesgericht München gescheitert. Wie die Richter entschieden, darf das Kölner Unternehmen Eyeo sein Angebot "AdBlock Plus" weiter anbieten.
Legitimes Geschäft oder "Schutzgeld"?
"AdBlock Plus" ist das beliebteste Programm in diesem Zusammenhang in Deutschland und steht kostenlos zum Download bereit. Will ein Webseiten-Betreiber Werbung trotz eingeschalteten Filters präsentieren, bieten die Blocker ihm an, sich in eine sogenannte Whitelist eintragen zu lassen. Webseiten, die auf dieser Liste vermerkt sind, sind vom Werbe-Bann ausgenommen. Wird eine Seite monatlich mehr als zehn Millionen Mal besucht, verlangen die Werbeblocker Geld für die Aufnahme in die Whitelist. Für sie eine Lizenzgebühr - Webseiten-Betreiber kritisieren es als "freikaufen".
Mehr zum Thema
Facebook will Werbeblocker aushebeln, 08.09.2016
Neue Studie: Milliardenverluste durch Werbeblocker, 11.08.2015
Niederlage für Medienhäuser
Auch diese Praxis der Whitelists haben die Richter in München für zulässig erklärt - eine herbe Niederlage für die "Süddeutsche Zeitung", ProSiebenSat.1 und die RTL-Tochter IP, die gemeinsam geklagt hatten. Sie hatten Eyeo einen Verstoß gegen das Wettbewerbsrecht vorgeworfen und Schadenersatz verlangt. Verlage und Medienhäuser finanzieren ihr Online-Angebot zu großen Teilen über die bei ihnen geschalteten Anzeigen. Blenden Nutzer die aus, brechen Einnahmen weg.
https://www.tagesschau.de/wirtschaft/werbeblocker-109.html
 Aktive Elemente blockieren in Firefox: NoScript einrichten, uncut-news.ch, 25.01.2022 Aktive Elemente blockieren in Firefox: NoScript einrichten, uncut-news.ch, 25.01.2022
Die Präsentation von Werbung und die Nachverfolgung unserer Aktivitäten im Weltnetz erfolgt häufig durch aktive Elemente auf den besuchten Seiten.
Wenn wir eine solche Seite aufrufen, werden diese Elemente auf unseren Rechner übertragen und hier gestartet. Wir gehen also nicht "ins Netz", wo sich etwas ereignet, irgendwo "da draussen", sondern "das Netz" kommt zu uns mit guten Absichten und mit schlechten.
Dabei lässt sich Werbung nicht eindeutig trennen von Überwachung.
In diesem Bereich tätig sind private Unternehmen, die ihre Milliarden nicht damit erzielen, dass sie uns eine Suchmaschine zur Verfügung stellen oder eine "Chat"-Plattform.
Wir sind nicht deren Kunden, sondern unsere Daten sind die Ware, mit der sie Geld verdienen.
Seit Regimes weltweit ohne begründeten Anfangsverdacht flächendeckend die bürgerliche Gesellschaft ausspionieren und damit zu Untertanen degradieren wollen, sollten wir uns dagegen schützen.
Manche suchen Sicherheit in TOR-Netzwerk oder in VPNs.
Das mag schützen oder nicht, wir haben keinen Einfluss darauf und können nur den Versprechungen vertrauen. Vielleicht legen "die" sich genau da auf die Lauer oder sind selbst Betreiber eines gar so sicheren Proxy-Servers. Ein befreundeter Ermittler nannte das einmal "Honigtöpfchen aufstellen".
Sicherheit, die wir beeinflussen können, findet auf unserem Rechner statt.
Ziel dieser Anleitung soll sein, diese Datensammler zu blockieren, aber die Funktionalität der Netz-Seite möglichst zu bewahren.
Ich habe diese Anleitung erstellt auf Firefox V.95 für NoScript 11.2.x.
Laut Hersteller läuft NoScript auf Firefox (Desktop sowie Mobile auf Android), Tor Browser (wo es bereits eingebaut ist), Chromium/Chrome wie auch auf weiteren "Browsern" auf Mozilla-Basis, z.b. Seamonkey.
Aktuelle Version ist NoScript 11.2.14.
https://uncutnews.ch/aktive-elemente-blockieren-in-firefox-noscript-einrichten/
https://dudeweblog.wordpress.com/2022/01/22/aktive-elemente-blockieren-in-firefox-noscript-einrichten/
 Viele von Providern gelieferte Router-Modelle sind recht alt geworden, 5, 7, 10 Jahre und älter.... und werden seit Langem nicht mehr mit akutellen Updates versorgt Viele von Providern gelieferte Router-Modelle sind recht alt geworden, 5, 7, 10 Jahre und älter.... und werden seit Langem nicht mehr mit akutellen Updates versorgt
 Profi-Hacker beantwortet Ihre WLAN-Fragen: Sicherheit bei FritzBox & Co., CHIP, 21.02.2022 Profi-Hacker beantwortet Ihre WLAN-Fragen: Sicherheit bei FritzBox & Co., CHIP, 21.02.2022
In Ihrem privaten WLAN müssen Sie selbst für Sicherheit sorgen, im Webinar wird erklärt, wie das geht
WLAN hat fast jeder zu Hause, doch ist das heimische Funknetz auch wirklich gut abgesichert? Finde Sie es in unserem Gratis-Webinar heraus, bei dem ein Profi-Hacker aus dem Nähkästchen plaudert. Er beantwortet Ihnen am morgigen Dienstag, 22.02.2022, ab 18:30 Uhr auch Ihre Fragen zum Thema Sicherheit von FritzBox und anderen WLAN-Routern.
https://www.chip.de/news/Kostenloses-Webinar-bei-CHIP-WLAN-Sicherheit_184061919.html
 Nutzt jemand heimlich Ihr WLAN? So ertappen Sie Fremde in Ihrem Internet, CHIP, 20.02.2022 Nutzt jemand heimlich Ihr WLAN? So ertappen Sie Fremde in Ihrem Internet, CHIP, 20.02.2022
Joerg Geiger, Michael Humpa, Marianne Westenthanner
Das WLAN kann zum Einfallstor für heimliche Mitleser werden. Im günstigsten Fall schnorrt jemand gratis Ihre Bandbreite, im schlimmsten Fall hackt jemand Ihre Accounts und klaut Daten. Wir zeigen, wie einfach Sie das herausfinden!
https://www.chip.de/news/Nutzt-jemand-heimlich-Ihr-WLAN-So-ertappen-Sie-Fremde-in-Ihrem-Internet_167272413.html
 BigBlueButton (BBB) und Jitsi Meet BigBlueButton (BBB) und Jitsi Meet
Besserer Datenschutz
Alternative Videokonferenz-Systeme müssen sich nicht verstecken, netzpolitik.org, 24.02.2022
Es gibt für Online-Konferenzen gute und einfach handhabbare Alternativen zu den bekannten US-Produkten. Warum es sich lohnt, diese auszuprobieren und einen Umstieg zu wagen.
Während der Pandemie haben wir uns öfter auf Bildschirmen als im physischen Leben gesehen. Online-Konferenzsysteme sind Teil des Arbeitsalltags vieler Menschen geworden, aber auch weite Teile unserer Freizeit sind ins Digitale verlagert. Wann immer das Pandemie-Ende kommen wird, eines ist sicher: Videokonferenzen werden nicht verschwinden und sollten nicht mehr als Provisorium gesehen werden. Spätestens nach der Pandemie hat niemand mehr eine Ausrede, sich nicht endlich Gedanken darüber zu machen, welches technische System er dauerhaft verwenden will.
Seit dem sogenannten Schrems-II-Urteil des Europäischen Gerichtshofs im Jahr 2020 ist eine rechtskonforme Nutzung von US-Diensten insgesamt schwierig geworden, da das schon zuvor hochumstrittene pauschale Privacy-Shield-Abkommen für transatlantische Datentransfers seither nicht mehr gilt.
[...] Häufig behilft man sich - falls vorhanden - mit Standardvertragsklauseln. Ganz Europa wartet aktuell noch auf entsprechende Neuregelungen, also ein neues Abkommen mit den Vereinigten Staaten. Bis das aber vorliegt, kann es noch dauern.
Ein weiteres Problem fällt in die Kategorie Biometrie: Es ist unvermeidlich, dass bei Online-Konferenzen auch biometrische Daten anfallen, etwa von Gesichtsbildern und von Stimmen. In ihren Allgemeinen Geschäftsbedingungen schließen die US-Anbieter die Verwertung von biometrischen Daten nicht explizit aus. Sie könnten daher Videobilder und Stimmdaten für weitere Analysen auch zu kommerziellen Zwecken nutzen. Ob und welche Datenschutzbehörden in Europa für die US-Unternehmen zuständig sind, bleibt zudem oft vage. Zoom hat beispielsweise zwar Niederlassungen in Frankreich und den Niederlanden, aber auf Datenschutzfragen verweigert es die Antwort.
Welches Potential einerseits für die Unternehmen und andererseits welche Bedrohungen durch Software-Fehler oder durch Nutzung oder Weitergabe der biometrischen Daten für die betroffenen Menschen besteht, lässt sich hier nur andeuten. So plant beispielsweise das Unternehmen Clearview aktuell, seine Gesichter-Datenbank trotz breiter Gegenwehr auf 100 Milliarden Fotos anwachsen zu lassen. Damit würde fast jeder Mensch auf der Welt durch Clearview identifizierbar werden. Die Gesichtserkennung soll sowohl dem öffentlichen als auch dem privaten Sektor angeboten werden, die Datenbasis wächst um 1,5 Milliarden Bilder pro Monat.
Neben der klassischen biometrischen Auswertung ist zudem an Emotionsanalysen anhand von Stimmprofilen oder an Gestenerkennung zu denken, auch an Analysen der (Privat-)Räume im Bildhintergrund. Die Szenarien für Geschäftsmodelle und Überwachung lassen sich ohne viel Fantasie weiterdenken: Der Fakt, dass viele Menschen Einblicke in ihre Arbeits- und Wohnräume geben und in Online-Konferenzen zusammen gedacht, gelacht und diskutiert wird, erlaubt detailliertere Personenprofile, als andere Technologien das zulassen würden.
Wem nicht egal ist, wer bei einer Online-Konferenz zuschauen könnte, der hat also eine ganze Reihe Gründe für einen Wechsel zu Alternativen. Ein weiterer Aspekt neben dem Datenschutz, der für einen Anbieterwechsel spricht, ist eine gewisse Abhängigkeit, die man vielleicht vermeiden möchte: Getreu dem Motto "Was der Bauer nicht kennt, das frisst er nicht", verwenden Menschen immer gern, was sie schon kennen und meiden anderes. Damit begeben sie sich in eine Abhängigkeit zu diesem Anbieter und gehen zumeist bei jeder AGB-Änderung mit - selbst wenn diese zu ihren Ungunsten ausfällt.
US-Anbieter: Was ist das Problem?
Warum sind die oben erwähnten typischen US-Angebote eigentlich ein Problem? Zunächst ist für die Nutzung von US-Diensten die Rechtslage bei der Datenübertragung in die Vereinigten Staaten wichtig. Anders als in Europa üblich sind US-Unternehmen datenschutzrechtlich wenig eingeschränkt: Nach amerikanischem Recht können personenbezogene Daten der Kunden auch kommerziell genutzt werden, auch zum Weiterverkauf. So ist in den letzten zwanzig Jahren ein riesiger Markt beim Handel mit Nutzerdaten und zum Weiterverkauf von aggregierten Personenprofilen entstanden.
Sämtliche Unternehmen mit einem Firmenbezug zu den Vereinigten Staaten sind nach amerikanischem Recht verpflichtet, Nutzerdaten den US-Behörden nach Aufforderung zur Verfügung zu stellen, ohne ihre Kunden darüber zu informieren - auch ohne dass die Server, auf denen diese Daten liegen, überhaupt auf US-Territorium stehen müssen.
Das gilt also auch für Server, die in Deutschland oder sonstwo auf der Welt stehen. Die Grundlage hierfür bildet der US CLOUD Act. Wenn keine echte Ende-zu-Ende-Verschlüsselung in den Dienst eingebaut ist oder sie nicht verwendet wird, weil sie beispielsweise nur in der Bezahl-Version der Software enthalten ist, dann steht der Weitergabe der Daten an US-Behörden gemäß den gesetzlichen Vorschriften auch technisch nichts im Wege.
... dürfte der Grund für die vermeintlich bessere Performance sein, dass die Videoverarbeitung nicht auf dem Endgerät der Nutzerin stattfindet, sondern zentral auf Zoom-Servern. Dabei wird - zumindest bei Gratis-Accounts - nur eine TLS-Transportverschlüsselung verwendet, also keine Ende-zu-Ende-Verschlüsselung. Das bedeutet, dass die Daten auf dem Zoom-Server unverschlüsselt vorhanden sind, aber Dritte, die versuchen, die Daten unterwegs abfangen, wegen der Transportverschlüsselung nicht an die Inhalte kommen.
Die Daten werden auf dem Zoom-Server unverschlüsselt verarbeitet und wieder an alle Teilnehmenden zurückgeschickt, wobei der Weg zurück wieder nur transportverschlüsselt verläuft - mit Ausnahme der Text-Chats, deren Inhalte tatsächlich verschlüsselt übertragen werden.
Datenfreundliche Alternativen
Was aber kann man verwenden, wenn man guten Gewissens online-konferieren möchte? Die beiden großen Alternativen sind BigBlueButton (BBB) und Jitsi Meet.
https://netzpolitik.org/2022/besserer-datenschutz-alternative-videokonferenz-systeme-muessen-sich-nicht-verstecken/
Jahresbericht zum Datenschutz: Von Corona, Cookies und Beschäftigtendatenschutz, netzpolitik.org, 05.04.2022
In seinem Tätigkeitsbericht zieht der Bundesdatenschutzbeauftragte Ulrich Kelber Bilanz über das letzte Jahr. Die fällt durchwachsen aus: Nur wenige seiner Empfehlungen aus dem Vorjahr wurden umgesetzt, dafür gibt es aber Hoffnung auf ein dringend notwendiges Beschäftigtendatenschutzgesetz.
https://netzpolitik.org/2022/jahresbericht-zum-datenschutz-von-corona-cookies-und-beschaeftigtendatenschutz/
Transatlantisches Daten-Dilemma: Das Privacy-Shield 2.0 ist zum Scheitern verurteilt, netzpolitik.org, 30.03.2022
Und täglich grüßt das Murmeltier: Die USA versprechen, die Daten von EU-Bürger:innen künftig besser zu schützen, wenn Europa nur endlich grünes Licht für unkomplizierte Datenausfuhren gibt. Doch einen Ausweg aus dem Daten-Dilemma wird es nur geben, wenn Europa seine digitale Abhängigkeit von den USA reduziert.
Transatlantisches Daten-Dilemma: Das Privacy-Shield 2.0 ist zum Scheitern verurteilt
Und täglich grüßt das Murmeltier: Die USA versprechen, die Daten von EU-Bürger:innen künftig besser zu schützen, wenn Europa nur endlich grünes Licht für unkomplizierte Datenausfuhren gibt. Doch einen Ausweg aus dem Daten-Dilemma wird es nur geben, wenn Europa seine digitale Abhängigkeit von den USA reduziert. Ein Kommentar.
https://netzpolitik.org/2022/transatlantisches-daten-dilemma-das-privacy-shield-2-0-ist-zum-scheitern-verurteilt/
Appendix
Errata in /etc/fstab
Security on the one and other hand: What does all this security our Online-Excurs "1000% Gooken 1000%" help, if you still can not open (and close) the shaft of your DVD/CD-rom-device in UNIX/Linux´s KDE like KDE 4?
We searched for a solution for hours.
Try it the following way, at first enter next line into /etc/fstab:
/dev/sr0 /media/cdrom udf,iso9660 ro,user,noauto,unhide,users,mode=1777 0 0
resp. ( if the filesystem causes still problems )
/dev/sr0 /media/cdrom auto ro,user,noauto,unhide,users,mode=1777 0 0
Kernel modules like cdrom, udf, isofs and probbably further more should be loaded, before scripts like modules-disalbled out of /etc/init.d are run, so just add them into this script, add all such modprobe line by line.
Now type into a terminal, where the usermode is already possible for it:
"eject /dev/sr0 && mount /media/cdrom"
( you can close it in the similar way, either by pressing the flap into the shaft by your hand or typing into the terminal: "eject -t /dev/sr0" ).
Configure /etc/udev/rules.d like we did for lp in the section printer troubleshooting above, set /dev/sr0 to acess rights (chmod) 777, and let the user (you) be part in the group set for /dev/sr0 to guarantee for the needed access rights.
Nevertheless, audio-CDs suddenly did and do not get play within my cd-rom-device resp. DVD-/CD-burner anymore like they did times ago, because of the mount does not function.
The entry in fstab prevents some cd-rom-devices from playing audio-CDs, as they do not have got any file sytem at all. Without this fstab-entry, nothing works with this device.
 Zeitmessung Zeitmessung
Die Erde dreht sich plötzlich schneller als je zuvor und die Wissenschaftler wissen nicht, warum, uncut-news.ch, 03.08.2022
Klima/Natur/Wetter
Die Erde hat sich vor kurzem mit 1,59 Millisekunden unter 24 Stunden so schnell wie nie zuvor gedreht, und die Folgen für unsere Zeitmessung haben Experten in aller Welt alarmiert.
https://uncutnews.ch/die-erde-dreht-sich-ploetzlich-schneller-als-je-zuvor-und-die-wissenschaftler-wissen-nicht-warum/
 Experte über Privatsphäre: "Ich frage mich ständig, warum die Leute das alles noch mitmachen", STERN.de, 09.06.2019 Experte über Privatsphäre: "Ich frage mich ständig, warum die Leute das alles noch mitmachen", STERN.de, 09.06.2019
Marc Al-Hames kennt alle Tricks der Werbeindustrie. Im Gespräch mit dem Stern erklärt er, warum die plötzlichen Datenschutz-Bekenntnisse einiger Konzerne nicht ernstzunehmen sind und was der größte Unterschied zwischen Apple und Google in puncto Datenschutz ist.
[...]."Facebook zum Beispiel hat Privatsphäre nie verstanden und versteht sie auch jetzt nicht."
[...] "Umfragen zufolge liest der Großteil der Nutzer keine Geschäftsbedingungen und stimmt allen Anfragen zu."
https://www.stern.de/digital/online/datenschutz---die-werbe-industrie-kann-uns-ueber-alle-geraete-hinweg-verfolgen--denen-entgeht-nichts--8723748.html
"Das Internet must get away!"
Schlecky Silberstein surfs in our filter bubble
Christian Brandes aka Schlecky Silberstein würde gern das Medium abschaffen, das ihn ernährt. In "Das Internet muss weg" beschreibt der Blogger, wie wir von Algorithmen, Trollen und Tech-Firmen gebrainwasht werden. Aber ist er nicht selbst ein Teil davon? Eine Rezension.
https://netzpolitik.org/2018/schlecky-silberstein-surft-in-unserer-filterbubble/
 (gegebenfalls erst in Zukunft) Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018 (gegebenfalls erst in Zukunft) Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018
Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018
Wer im Internet miteinander kommuniziert, hinterlässt unweigerlich Spuren. Wiener Forscher wollen jetzt ein Verfahren entwickelt haben, das die Kommunikation auch in einem größeren Netzwerk abhörsicher macht.
Die Quantenkryptografie will in Zukunft eine abhörsichere Kommunikation im Internet ermöglichen. Österreichische Forscher haben nun - nach eigenen Angaben - eine wichtige Hürde auf diesem Weg genommen. Ihnen gelang, dass vier Teilnehmeung sind die Eigenschaften der beiden individuellen Teilchen unbestimmt. Wird dann bei einem der beiden Teilchen eine Eigenschaft wie beispielsweise die Schwingungsrichtung gemessen, nimmt das andere Teilchen augenblicklich eine korrespondierende Eigenschaft an. Die Verschränkung endet. Auf diese Weise ist es möglich, abhörsicherer Schlüssel bei Sender und Empfänger zu erzeugen.
Lauscher können Anwesenheit nicht verschleiern
Entscheidend ist: Der Schlüssel kann von Hackern nicht abgefangen werden. Denn es werden nur einzelne Lichtteilchen (Photonen) ausgetauscht. Und nach den Gesetzen der Quantenphysik ist es unmöglich, den Quantenzustand eines einzelnen Lichtteilchens ohne Fehler zu kopieren. Ein Lauscher kann seine Anwesenheit daher nicht verschleiern und würde sich sofort verraten. Die verschlüsselte Nachricht wird dann auf klassischem Weg ausgetauscht.
Bisher nur bei zwei Teilnehmern nachgewiesen
Bisher ließen sich auf diese Weise meist jedoch nur zwei Teilnehmer mit einer garantiert abhörsicheren Leitung verbinden. Weitere Verbindungen seien kompliziert, fehleranfällig und mit Kommunikationseinschränkungen behaftet.
Das Team versorgte nun vier Teilnehmer aus einer zentralen Quelle mit verschränkten Photonen, sodass alle vier miteinander kryptographische Schlüssel erzeugen und für eine abhörsichere Kommunikation verwenden konnten. "Ein entscheidender Vorteil dieser Architektur ist ihre Flexibilität", betont Ursin in einer Mitteilung der Akademie. "Wir sind damit in der Lage, neue Kommunikationspartner in das Quantennetzwerk zu integrieren - und zwar mit lediglich minimalen Eingriffen. Damit ist gezeigt, dass Quantennetzwerke Realität werden können - für Jedermann."
https://www.tagesschau.de/ausland/quanten-101.html
 Die Blockchain-Gesellschaft: Web 3.0, virtuelle Realität und der Netzwerkstaat, uncut-news.ch, 04.08.2022 Die Blockchain-Gesellschaft: Web 3.0, virtuelle Realität und der Netzwerkstaat, uncut-news.ch, 04.08.2022
Was bringt uns zu "Web3", das die Probleme von Web2 lösen und gleichzeitig die Infrastruktur für neue, bahnbrechende Technologien bereitstellen soll.
"Web3" soll folgendes leisten:
Dezentralisiert (d. h. keine Organisationen kontrollieren Ihre Daten);
Genehmigungsfrei (jeder kann auf das Netzwerk zugreifen);
Unzensierbar (einmal veröffentlichte Inhalte können nicht verändert oder entfernt werden);
Monetarisierbar (Schöpfer können für den von ihnen geschaffenen Wert bezahlt werden, ohne Zwischenhändler);
Privat (Identität ist verschlüsselt und Anonymität ist optional).
Klingt gut, aber wie wird das erreicht? Die Idee ist, dass das Internet so umgebaut wird, dass es um Blockchain und Kryptowährungen herum neu strukturiert wird.
Sehen Sie, Geld ist ein uraltes Tauschmittel, das seit Jahrhunderten verwendet wird. Tatsächlich hat sich das Konzept des Geldes im Laufe der Zeit kaum verändert, auch wenn es sich physisch von dem unterscheidet, was es in der Vergangenheit war. Aber bisher gab es kein Geld als Protokoll, das Teil des Internets ist.
Das wird sich mit Web3 ändern: Die Idee ist, dass wir durch die Integration von Geld in die Struktur des Internets selbst die Online-Welt von invasiver Werbung befreien können, die auf der massenhaften Sammlung privater Daten beruht, und dass wir die Macht autoritärer, großer Technologiemonopole brechen können.
Mit "Web3" wird das Internet eine massive Umstrukturierung erfahren, die auf den folgenden 4 "Schichten" aufbaut:
Die Blockchain gehört niemandem und wird von niemandem kontrolliert und befindet sich nicht auf einem einzigen Server. Vielmehr werden Kopien der Blockchain bei Tausenden von Teilnehmern des Netzwerks gespeichert. Man kann sie sich wie eine dezentrale Datenbank für Transaktionen vorstellen.
Um Konsistenz, Sicherheit und Objektivität zu gewährleisten, müssen sich die einzelnen Knoten (Teilnehmer) jedoch über den aktuellen Zustand des Netzwerks einigen. Diese Einigung wird algorithmisch durch einen Konsensmechanismus wie Proof-of-Work oder Proof-of-Stake erzielt.
Der Proof-of-Work (PoW) wird von "Minern" erbracht, die darum wetteifern, neue Transaktionen zu verifizieren und der Kette als "Blöcke" hinzuzufügen (daher "Blockchain"). Der Gewinner teilt den neuen Block mit dem Rest des Netzwerks und erhält als Belohnung Kryptowährung. Das Rennen gewinnt der Computer, der am schnellsten ein mathematisches Rätsel lösen kann, das die kryptografische Verbindung zwischen dem aktuellen Block und dem vorhergehenden Block herstellt. Das Lösen dieses Rätsels ist die "Arbeit" in "proof-of-work".
https://uncutnews.ch/die-blockchain-gesellschaft-web-3-0-virtuelle-realitaet-und-der-netzwerkstaat/
 Harvard-Professor entlarvt Google und Facebook, T.H.G., 15.12.2022 Harvard-Professor entlarvt Google und Facebook, T.H.G., 15.12.2022
Das Produkt ist alles, was sie leise und rücksichtslos von Ihrer Identität abziehen und stehlen, um Profit zu machen. Sie wissen nicht einmal, dass dies geschieht.
GESCHICHTE AUF EINEN BLICK
In ihrem Buch "Das Zeitalter des Überwachungskapitalismus" enthüllt die Sozialpsychologin und Harvard-Professorin Shoshana Zuboff, wie die größten Technologieunternehmen der Welt ohne unser Wissen oder unsere Zustimmung unsere persönlichen Daten - die so genannten "überschüssigen Verhaltensdatenströme" - an sich gerissen haben und sie gegen uns verwenden, um Gewinne zu erzielen.
Wie Sie Ihre Online-Daten schützen können
Zweifellos brauchen wir einen völlig neuen gesetzlichen Rahmen, um den Überwachungskapitalismus einzudämmen. In der Zwischenzeit gibt es jedoch Möglichkeiten, wie Sie Ihre Privatsphäre online schützen und die über Sie gesammelten "überschüssigen Verhaltensdaten" einschränken können.
Robert Epstein, leitender Forschungspsychologe des American Institute of Behavioral Research and Technology, empfiehlt die folgenden Schritte zum Schutz Ihrer Privatsphäre:
Verwenden Sie ein virtuelles privates Netzwerk (VPN) wie Nord, das nur etwa 3 Dollar pro Monat kostet und auf bis zu sechs Geräten genutzt werden kann. Meiner Meinung nach ist dies ein Muss, wenn Sie Ihre Privatsphäre schützen wollen. Epstein erklärt:
"Wenn Sie Ihr Mobiltelefon, Ihren Laptop oder Ihren Desktop auf die übliche Weise benutzen, ist Ihre Identität für Google und andere Unternehmen sehr leicht zu erkennen. Sie können sie über Ihre IP-Adresse feststellen, aber es gibt immer mehr ausgefeiltere Methoden, mit denen sie wissen, dass Sie es sind. Eine davon ist das so genannte Browser-Fingerprinting.
Das ist etwas, das sehr beunruhigend ist. Im Grunde ist die Art Ihres Browsers und die Art und Weise, wie Sie Ihren Browser verwenden, wie ein Fingerabdruck. Sie verwenden Ihren Browser auf einzigartige Weise, und allein durch die Art und Weise, wie Sie tippen, können diese Unternehmen Sie jetzt sofort identifizieren.
Brave bietet einen gewissen Schutz gegen Browser-Fingerabdrücke, aber Sie müssen wirklich ein VPN verwenden. Ein VPN leitet alles, was Sie tun, über einen anderen Computer an einem anderen Ort um. Das kann überall auf der Welt sein, und es gibt Hunderte von Unternehmen, die VPN-Dienste anbieten. Das Unternehmen, das mir im Moment am besten gefällt, heißt Nord VPN.
Sie laden die Software herunter und installieren sie, wie jede andere Software auch. Es ist unglaublich einfach zu bedienen. Man muss kein Techniker sein, um Nord VPN zu nutzen, und es zeigt eine Weltkarte an, auf der man einfach auf ein Land klicken kann.
Das VPN lässt es im Grunde so aussehen, als wäre Ihr Computer nicht Ihr Computer. Es schafft im Grunde eine Art falsche Identität für Sie, und das ist eine gute Sache. Sehr oft werde ich über die Computer von Nord in den Vereinigten Staaten gehen. Manchmal muss man das tun, oder man kann bestimmte Dinge nicht erledigen. PayPal mag es zum Beispiel nicht, wenn man sich im Ausland aufhält."
Nord, wenn es auf Ihrem Mobiltelefon verwendet wird, maskiert auch Ihre Identität bei der Verwendung von Anwendungen wie Google Maps.
Verwenden Sie Gmail nicht, da jede E-Mail, die Sie schreiben, dauerhaft gespeichert wird. Sie wird Teil Ihres Profils und dient dazu, digitale Modelle von Ihnen zu erstellen, die es ihnen ermöglichen, Vorhersagen über Ihre Denkweise und jeden Wunsch zu machen. Viele andere ältere E-Mail-Systeme wie AOL und Yahoo werden ebenso wie Gmail als Überwachungsplattform genutzt. ProtonMail.com, das eine Ende-zu-Ende-Verschlüsselung verwendet, ist eine gute Alternative und das Basiskonto ist kostenlos.
Verwenden Sie nicht den Chrome-Browser von Google, da alles, was Sie dort tun, überwacht wird, einschließlich Tastenanschläge und jede Webseite, die Sie jemals besucht haben. Brave ist eine großartige Alternative, die den Datenschutz ernst nimmt. Brave ist außerdem schneller als Chrome und unterdrückt Werbung. Es basiert auf Chromium, der gleichen Software-Infrastruktur, auf der auch Chrome basiert, sodass Sie Ihre Erweiterungen, Favoriten und Lesezeichen problemlos übertragen können.
Verwenden Sie nicht Google als Suchmaschine oder eine Erweiterung von Google, wie Bing oder Yahoo, die beide Suchergebnisse von Google beziehen. Das Gleiche gilt für den persönlichen Assistenten Siri auf dem iPhone, der alle Antworten von Google bezieht. Zu den von Epstein empfohlenen alternativen Suchmaschinen gehören SwissCows und Qwant. Er empfiehlt, StartPage zu meiden, da es kürzlich von einem aggressiven Online-Marketing-Unternehmen gekauft wurde, das wie Google auf Überwachung angewiesen ist.
Verwenden Sie kein Android-Handy, und zwar aus den bereits erwähnten Gründen. Epstein verwendet ein BlackBerry, das sicherer ist als Android-Handys oder das iPhone. Das kommende Modell von BlackBerry, das Key3, wird eines der sichersten Handys der Welt sein, sagt er.
Verwenden Sie keine Google-Home-Geräte in Ihrem Haus oder Ihrer Wohnung - Diese Geräte zeichnen alles auf, was in Ihrem Haus passiert, sowohl Sprache als auch Geräusche wie Zähneputzen und kochendes Wasser, selbst wenn sie scheinbar inaktiv sind, und senden diese Informationen an Google. Auch Android-Telefone hören immer mit und zeichnen auf, ebenso wie Googles Heimthermostat Nest und Amazons Alexa.
Löschen Sie Ihren Cache und Ihre Cookies - wie Epstein in seinem Artikel erklärt:
"Unternehmen und Hacker aller Art installieren ständig invasiven Computercode auf Ihren Computern und Mobilgeräten, hauptsächlich, um Sie im Auge zu behalten, manchmal aber auch für schändlichere Zwecke.
Auf einem mobilen Gerät können Sie den größten Teil dieses Mülls löschen, indem Sie das Einstellungsmenü Ihres Browsers aufrufen, die Option "Datenschutz und Sicherheit" auswählen und dann auf das Symbol klicken, das Ihren Cache und Ihre Cookies löscht.
Bei den meisten Laptop- und Desktop-Browsern führt das gleichzeitige Drücken von drei Tasten - STRG, UMSCHALT und ENTF - direkt zum entsprechenden Menü; ich verwende diese Technik mehrmals täglich, ohne darüber nachzudenken. Sie können auch die Browser Brave und Firefox so konfigurieren, dass Ihr Cache und Ihre Cookies automatisch gelöscht werden, wenn Sie Ihren Browser schließen."
Verwenden Sie Fitbit nicht, da es vor kurzem von Google aufgekauft wurde und alle Ihre physiologischen Daten und Aktivitätswerte an Google weitergibt, zusätzlich zu allem anderen, was Google bereits über Sie hat.
Artikel als PDF:
Quellen:
1 Goodreads.com Czesław Miłosz Quotable Quotes
2 Youtube.com, Shoshana Zuboff on Surveillance Capitalism
3 Nature September 13, 2012; 489: 295-298 (Archived)
4 PNAS June 17, 2014; 111(24): 8788-8790 (Archived)
5 New York Times March 23, 2020 (Archived)
6 New York Times January 24, 2020
7 New York Times January 24, 2020 (Archived)
8 New York Times January 24, 2020
9 New York Times January 24, 2020 (Archived)
10 New York Times January 24, 2020 (Archived)
11 The Guardian May 1, 2017 (Archived)
12 New York Times January 24, 2020 (Archived)
13 New York Times January 24, 2020 (Archived)
14 Medium March 17, 2017
15 Medium March 17, 2017
Quelle: Harvard Professor Exposes Google and Facebook, https://takecontrol.substack.com/p/surveillance-capitalism
https://uncutnews.ch/harvard-professor-entlarvt-google-und-facebook/
How secure is the browser? And what about the WLAN?
Check out carefully the relais (EntryGurads and ExitNodes) for TOR and the net traffic, by using netstat, iptraf, wireshark, ethereal, snort, airsnort, aircrack, conntrack (Linfw3), log-entries and so on: especially the easy understandable iptraf.
Contact the authors resp. maintainers of Linux kernel and the browser, if something´s wrong.
 (gegebenfalls erst in Zukunft) Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018 (gegebenfalls erst in Zukunft) Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018
Kommunikation im Netz: Abhörsicher mithilfe der Quantenphysik?, tagesschau.de, 16.12.2018
Wer im Internet miteinander kommuniziert, hinterlässt unweigerlich Spuren. Wiener Forscher wollen jetzt ein Verfahren entwickelt haben, das die Kommunikation auch in einem größeren Netzwerk abhörsicher macht.
Die Quantenkryptografie will in Zukunft eine abhörsichere Kommunikation im Internet ermöglichen. Österreichische Forscher haben nun - nach eigenen Angaben - eine wichtige Hürde auf diesem Weg genommen. Ihnen gelang, dass vier Teilnehmeung sind die Eigenschaften der beiden individuellen Teilchen unbestimmt. Wird dann bei einem der beiden Teilchen eine Eigenschaft wie beispielsweise die Schwingungsrichtung gemessen, nimmt das andere Teilchen augenblicklich eine korrespondierende Eigenschaft an. Die Verschränkung endet. Auf diese Weise ist es möglich, abhörsicherer Schlüssel bei Sender und Empfänger zu erzeugen.
Lauscher können Anwesenheit nicht verschleiern
Entscheidend ist: Der Schlüssel kann von Hackern nicht abgefangen werden. Denn es werden nur einzelne Lichtteilchen (Photonen) ausgetauscht. Und nach den Gesetzen der Quantenphysik ist es unmöglich, den Quantenzustand eines einzelnen Lichtteilchens ohne Fehler zu kopieren. Ein Lauscher kann seine Anwesenheit daher nicht verschleiern und würde sich sofort verraten. Die verschlüsselte Nachricht wird dann auf klassischem Weg ausgetauscht.
Bisher nur bei zwei Teilnehmern nachgewiesen
Bisher ließen sich auf diese Weise meist jedoch nur zwei Teilnehmer mit einer garantiert abhörsicheren Leitung verbinden. Weitere Verbindungen seien kompliziert, fehleranfällig und mit Kommunikationseinschränkungen behaftet.
Das Team versorgte nun vier Teilnehmer aus einer zentralen Quelle mit verschränkten Photonen, sodass alle vier miteinander kryptographische Schlüssel erzeugen und für eine abhörsichere Kommunikation verwenden konnten. "Ein entscheidender Vorteil dieser Architektur ist ihre Flexibilität", betont Ursin in einer Mitteilung der Akademie. "Wir sind damit in der Lage, neue Kommunikationspartner in das Quantennetzwerk zu integrieren - und zwar mit lediglich minimalen Eingriffen. Damit ist gezeigt, dass Quantennetzwerke Realität werden können - für Jedermann."
https://www.tagesschau.de/ausland/quanten-101.html
Computer - Suneater - Spongebob - TV-Comic-classics Spongebob Schwammkopf - The autopilot and further on
Video von Facebook
European juvenile court
Each person has the right to get to know, where data about him landed and what happens with them, tagesschau.de, 01.12.2023
https://www.tagesschau.de/ausland/eugh-persoenliche-daten-weitergabe-101.html
It might already be risky to get an E-mail from Gmail (and other freemailer), because of its include getting stored and distributed.
The best, one can do, is to resign from any E-mail-account. If you must have one, remove it after use. If you still have one, never tell more people about your E-mail-address than necessary.
From Gooken News&Links#Aktuell#gk.12hp.de
Frankreich
Nach den Maßstäben der französischen Ermittler wird so jede:r zum Klandestinen, der seine Privatsphäre schützt
Umstrittene Terror-Ermittlungen: Der Messenger Signal als "Kult der Geheimhaltung", netzpolitik.org, 13.06.2023
In einem Verfahren mit bislang wenigen Beweisen versuchen französische Ermittlungsbehörden die Nutzung von weit verbreiteten Verschlüsselungstechniken als Beleg für klandestines Verhalten heranzuziehen. Die Bürgerrechtsorganisation La Quadrature du Net kritisiert dieses Vorgehen.
Tastatur mit Schraubenschlüsseln und der Aufschrift "Pssst"
Nach den Maßstäben der französischen Ermittler wird so jede:r zum Klandestinen, der seine Privatsphäre schützt. (Symbolbild) - Alle Rechte vorbehalten IMAGO / Panthermedia
Die französische Digital-Rights-Organisation "La Quadrature du Net" berichtet von Ermittlungen gegen eine Gruppe von linken Aktivist:innen, denen Terrorismus vorgeworfen wird. In der sogenannten "Affäre des 8. Dezember 2020" stellen die Ermittlungsbehörden laut der Bürgerrechtsorganisation die alleinige Nutzung von Verschlüsselungstechniken und Anonymisierungswerkzeugen als eine Art Beweis dar, dass die Gruppe klandestin handele und damit ein "terroristisches Verhalten" an den Tag lege. Die französische Justiz wirft den festgenommenen Personen vor, dass sie Anschläge auf Polizei und Militär geplant hätten. Die sieben unter Terrorverdacht Festgenommenen bestreiten die Vorwürfe.
Laut La Quadrature taucht ein Satz in den Akten etwa 100 Mal auf: "Alle kontaktierten Mitglieder verhielten sich klandestin, mit erhöhter Sicherheit der Kommunikationsmittel (verschlüsselte Anwendungen, Tails-Betriebssystem, TOR-Protokoll, das anonymes Surfen im Internet und im öffentlichen WLAN ermöglicht)." Gleichzeitig habe man den mutmaßlichen Mitgliedern der Gruppe laut der Ermittlungsakte etwa 150 Fragen zu Verschlüsselung und Anonymisierung gestellt.
In den Untergrund wegen Jitsi und VPN?
Über mehrere Seiten versuchen die Ermittlungsbehörden laut la Quadrature die Nutzung solcher Tools, und besonders hervorgehoben der Messenger Signal, als Beweis zu beschreiben. So zitiert die Bürgerrechtsorganisation aus der Akte:
Die Protagonisten des Falles zeichneten sich alle durch ihren Kult der Geheimhaltung und ihre Besessenheit von Diskretion aus, sowohl bei ihren Kontakten als auch bei ihrem Surfen im Internet. Die verschlüsselte Anwendung Signal wurde von allen Angeklagten genutzt, von denen einige ausschließlich über diese Anwendung kommunizierten.
Auch würde mit der Betonung angeblich großer Computerkompetenz, die zum Beispiel damit begründet wird, dass ein Verdächtigter das Betriebssystem Linux mit Verschlüsselung auf seinem Computer installiert habe, ein "alarmierendes Narrativ" konstruiert, so La Quadrature. Handschriftliche Notizen zur Installation alternativer Handy-Betriebssysteme oder zur Nutzung der Videokonferenzsoftware Jitsi bestätigten laut der Akte "den Wunsch von X, in den Untergrund zu gehen und ihre Aktivitäten zu verbergen". Einem Verdächtigen wird laut den Akten vorgehalten, dass er seine Mutter zur Nutzung von Signal überzeugt hätte. Zu den Fragen, die sich die Verdächtigen anhören mussten, gehörte laut Quadrature auch, ob die Verdächtigen gegen Google, Apple, Facebook und Amazon (GAFA) seien.
"Weit verbreitete und harmlose digitale Gewohnheiten"
Enthalten in der Akte sind laut der Bürgerrechtsorganisation auch Fehler, die auf ein mangelndes technisches Verständnis der Ermittlungsbehörden hinweisen. La Quadrature kritisiert, dass im vorliegenden Fall "weit verbreitete und harmlose digitale Gewohnheiten" zu dem einzigen Zweck benutzt würden, eine "Verschwörungs"-Atmosphäre zu schaffen, die angeblich kriminelle Absichten verrate.
An dieser Stelle verweist die Bürgerrechtsorganisation auf die Terror-Ermittlungen im Fall Tarnac. Damals war einem Verdächtigen unterstellt worden, dass er klandestin handle, weil er kein Handy habe. Die französische Polizei hatte eine Landkommune unter Terrorverdacht gestellt, doch das Verfahren scheiterte, der Terrorverdacht wurde zurückgenommen, es kam zu Freisprüchen.
Auch die Beweise gegen die neuerliche angebliche Terror-Gruppe sind dünn. Beschlagnahmt wurden bei Hausdurchsuchungen laut Le Monde diplomatique ein Jagdgewehr, eine Pistolen-Attrappe und ein Helm der französischen Bereitschaftspolizei CRS, dazu noch Chemikalien wie Wasserstoffperoxid, Salzsäure und Aceton, die auch in ganz normalen Haushalten zu finden sein dürften.
In den Fokus der Behörden waren die Festgenommen geraten, weil sie im syrischen Rojava auf Seiten der kurdischen Verbände gegen den Islamischen Staat gekämpft hatten. Daraufhin hatte sich die französische Polizei bei der Rückkehr 2018 entschlossen, einige der Personen zu überwachen. Von den Festgenommenen ist noch eine Person im Gefängnis, das Gerichtsverfahren soll dieses Jahr stattfinden.
https://netzpolitik.org/2023/umstrittene-terror-ermittlungen-der-messenger-signal-als-kult-der-geheimhaltung/
Ständige Vertreter: EU-Staaten wollen Chatkontrolle trotz Warnung ihrer Juristen, netzpolitik.org, 14.06.2023
Die EU-Staaten sind mehrheitlich für die Chatkontrolle, auch bei verschlüsselter und Audio-Kommunikation. Das haben die Ständigen Vertreter der Mitgliedstaaten besprochen. Damit setzen sie sich über die Warnungen ihrer eigenen Juristen hinweg. Wir veröffentlichen eine Umfrage und ein Verhandlungsprotokoll.
https://netzpolitik.org/2023/staendige-vertreter-eu-staaten-wollen-chatkontrolle-trotz-warnung-ihrer-juristen/
USA/Das Imperium - Im Westen Nix Niue
Berichte von anderen - oft ganz ähnlich also ...
Das ist ja wie längst bei uns im US-Westen, jedenfalls so ähnlich:
China
Menschenrechte Fehlanzeige
Job verloren, Eigentum beschlagnahmt: Wie die KP Chinas Gläubige verfolgt, epochtimes.de, 07.06.2023
Die chinesische Kultur ist seit Jahrtausenden von einer tiefen spirituellen Tradition geprägt. Doch mit der Machtübernahme der Kommunistischen Partei Chinas änderte sich die Situation für die Gläubigen im Reich der Mitte. Sie werden systematisch diskriminiert und verfolgt. Einige ausgewählte Fallbeispiele.
Die Verfolgung religiöser Gruppen ist weltweit ein Problem, aber in China erreicht sie ein beispielloses Ausmaß. Um Gläubige "umzuerziehen", greift die Kommunistische Partei Chinas (KPC) zu gewaltsamen Methoden. Diese reichen von Inhaftierung, Folter, sexuellen und psychischen Missbrauchs bis zum erzwungenen Organraub (-> siehe Organspender-Thematik in Deutschland, 2014 bis dato, Anm. Red. Gooken).
Doch die Verfolgung von Gläubigen beschränkt sich nicht nur auf Haft und Zwangsarbeit: Betroffene berichten von finanzieller Ausbeutung und der Beschlagnahmung ihres Eigentums. Sie werden auch sozial diffamiert, sodass sie kein Arbeitgeber mehr einstellen wollte - und durfte.
"Zerstört ihren Ruf, ruiniert sie finanziell und vernichtet sie physisch." Das sind die drei politischen Leitlinien der KPC, seit sie begonnen hat, Praktizierende der spirituellen Bewegung Falun Gong zu verfolgen. Dies geht aus den "Neun Kommentaren über die Kommunistische Partei" hervor, die die chinesischsprachige Ausgabe der Epoch Times im Jahr 2004 veröffentlichte.
Falun Dafa, auch bekannt als Falun Gong, ist eine alte chinesische Kultivierungsmethode. Sie basiert auf den Prinzipien Wahrhaftigkeit, Güte und Nachsicht und beinhaltet neben einer tiefgründigen Lehre zur Selbstverbesserung fünf einfach zu erlernende, meditative Übungen. Seit über 23 Jahren ist Falun Gong Ziel der Verfolgung durch die KPC.
Es gibt unzählige Fälle, wie Falun-Gong-Praktizierende in China diskriminiert und verfolgt werden. Einer von ihnen ist Luo Xiang.
Der Fall von Luo Xiang
Dr. Luo Xiang hat seine Promotion am Institut für Theologie an der Universität Peking abgeschlossen. Trotz seiner herausragenden Leistungen fand er keine Anstellung. Der Grund: Sein "politischer Werdegang" entsprach nicht der Vorstellung der KPC.
Regelmäßig werden Personen in China derartigen routinemäßigen Bewertungen unterzogen und die Ergebnisse in einer Art "politischen Akte" notiert. Darin sind alle wichtigen und sensiblen Informationen enthalten - sowohl persönliche als auch berufliche. Bei Luo war festgestellt worden, dass er nach Beginn des Praktizierens von Falun Gong im Jahr 1999 aus der Kommunistischen Partei Chinas ausgetreten war.
Luo hatte sich im Jahr 2004 um eine Lehrstelle an der Hunan Normal University beworben, wie Minghui.org berichtete. Mit Erfolg. Das College war erfreut über seine Bewerbung und nahm seine Kurse in den Lehrplan für das kommende Semester auf. Als man später jedoch aus seiner politischen Akte erfuhr, dass er Falun Gong praktizierte, bekam Luo schließlich eine Absage.
An der Universität Wanzhou wurde Luo gesagt, dass keine Hochschule ihn einstellen würde, solange seine Verbindung zu Falun Gong in der politischen Akte dokumentiert sei. Daher beantragte er beim Verwaltungsbüro der Pekinger Universität, den Hinweis entfernen zu lassen. Eine Antwort erhielt er jedoch bis heute nicht.
Firma, Grundstück und Vermögen beschlagnahmt
Hu Yanmin aus der Provinz Liaoning wurde im Jahr 2014 verhaftet, weil sie Falun Gong praktiziert. Während ihrer siebenjährigen Haft beschlagnahmten die Behörden ihre Firma. Sie verlor ihr Grundstück, alle Anlagen sowie Materialien. Die Behörden setzten auch ihre Altersrente aus. Selbst nach ihrer Freilassung erhielt sie nie die Rentenerhöhung, die ihr gesetzlich zustand.
Vor der staatlichen Enteignung hatte Hu ein florierendes Unternehmen. Sie beschäftigte rund 50 Mitarbeiter und erzielte einen Jahresgewinn von über 800.000 Yuan (etwa 100.000 Euro). Ihr finanzieller Verlust beläuft sich über die Jahre auf mindestens 5,6 Millionen Yuan (etwa 735.000 Euro).
Viele Falun-Gong-Praktizierende haben ihre Arbeit im Zuge der Verfolgung verloren. Um sie zu unterstützen, gründeten Li Wensheng und seine Frau Wu Jinping im Jahr 2003 eine eigene Reinigungsmittelfirma. Das Unternehmen in der Stadt Chaoyang, Provinz Liaoning, bot vielen Praktizierenden Arbeit und ein sicheres Einkommen. Durch ihre harte Arbeit konnten sie schnell gute Vertriebskanäle aufbauen und den Markt erschließen.
Im Jahr 2008 wurde das Ehepaar jedoch von der Polizei verhaftet. Viele ihrer Besitztümer, darunter Computer, ein Drucker, ein Sparbuch mit 20.000 Yuan und über 100.000 Yuan Bargeld (zusammen etwa 15.700 Euro), wurden beschlagnahmt.
Die Polizisten forderten das Ehepaar auch auf, ihren Safe zu öffnen. Dieser enthielt die Scheckbücher des Unternehmens, die öffentlichen Siegel, das Finanzsiegel und die Siegel des gesetzlichen Vertreters. Als Li angab, den Schlüssel nicht zu haben, prügelten die Polizisten auf ihn ein und nahmen den Safe mit. Das Firmenauto wurde ebenfalls beschlagnahmt und der angestellte Chauffeur verhaftet, während das Paar ins Gefängnis überführt wurde.
https://www.epochtimes.de/china/job-verloren-eigentum-beschlagnahmt-wie-die-kp-china-glaeubige-verfolgt-a4256337.html
Art Uighuren - nicht erkennbar besonders Judas-Jüdische (USA 81/82, 1912), z.B.( diätlose ) Linke, Penner und einige Moslems & Co., Nicht-CDU/CSU-Wähler, Burschenschaftsjustiz, Wahlrecht in Dt. (uncutnews berichtete...), "nie stattgefundene Revolution", manch Journalisten, non-registrated customers, Fans anderer Fußballvereine als vor Ort, Katholiken im Protestantensektor (?), Menschen mit Computer, Menschen ohne Computer, Menschen mit MS Windows, Menschen mit Apple (beide: Mitgliedschaft in einer gewissen Vereinigung), Menschen mit Linux (Mitgliedschaft in einer ungewissen Vereinigungen), ...
.. - ....
... - ....
... - ....
usw. etc.
Was nicht alles: "Kannste ja wohl vergessen"
Gesundheit
Rätsel einer Volkskrankheit
Zu viel Eisen im Gehirn: Eine mögliche Ursache für Alzheimer?, epochtimes.de, 05.06.2023
Könnte ein Überschuss an Eisen im Gehirn Alzheimer verursachen? Diese Frage gewinnt zunehmend an Bedeutung in der Demenzforschung. Ein Wissenschaftlerteam aus den USA hat ein neues bildgebendes Verfahren entwickelt, das dazu beitragen könnte, das Rätsel um Alzheimer-Erkrankungen weiter zu entschlüsseln.
Bis 2050 wird die Anzahl an Patienten mit Alzheimer in Deutschland auf etwa 2,4 Millionen geschätzt. Im letzten Jahr wurden bundesweit knapp 1,8 Millionen Demenzkranke gezählt. Bislang gilt die Krankheit als nicht heilbar. Auch die Ursachen von Alzheimer ist bisher nicht eindeutig geklärt.
https://www.epochtimes.de/gesundheit/zu-viel-eisen-im-gehirn-eine-moegliche-ursache-fuer-alzheimer-a4287408.html
 Folloowing our online-excursion, you have done all so far. Still censorship? Then following artice might help: Folloowing our online-excursion, you have done all so far. Still censorship? Then following artice might help:
It becomes more and more important! methods and techniques to bypass online-censorship, uncut-news.ch, 10.13.2023
Umgehen Sie Internetfilter, Zensur im App-Store, Zensur von Big Tech und mehr. Online-Zensur nimmt zu, selbst demokratische Länder erlassen umfassende Gesetze, die die Meinungsfreiheit der Bürger zensieren und ihren Zugang zu Informationen einschränken. Auch Big Tech-Unternehmen beschränken zunehmend die Meinungsfreiheit ihrer Nutzer.
Glücklicherweise gibt es viele Tools und Techniken, die Sie verwenden können, um Internetbeschränkungen zu umgehen und auf Inhalte zuzugreifen, die Regierungen, Tech-Plattformen und andere Zensoren verhindern wollen, dass Sie sie sehen.
Dieser Beitrag identifiziert vier Hauptarten von Online-Zensur und listet verschiedene Tools und Techniken auf, die Ihnen helfen, jede Form von Zensur zu umgehen. Arten von Internetzensur:
Glücklicherweise gibt es viele Tools und Techniken, die Sie verwenden können, um Internetbeschränkungen zu umgehen und auf Inhalte zuzugreifen, die Regierungen, Tech-Plattformen und andere Zensoren verhindern wollen, dass Sie sie sehen.
Quelle: https://reclaimthenet.org/online-censorship-circumvention-tools-techniques
https://uncutnews.ch/es-wird-immer-wichtiger-anwendung-und-techniken-zur-umgehung-von-online-zensur/
 Policies for anomyization of your online-actitivies, uncut-news.ch, 11.20.2023 Policies for anomyization of your online-actitivies, uncut-news.ch, 11.20.2023
Standardmäßig wird fast alles, was Sie online tun, aufgezeichnet. Ihre Surfgewohnheiten sind mit einer Internet-Protokoll-Adresse (IP-Adresse) verknüpft, die mit Ihrem physischen Standort und Ihrem Internet-Dienstanbieter (ISP) verbunden ist. Und die Konten, die Sie für den Zugang zu Online-Diensten einrichten, sind oft mit Ihrer echten Identität verknüpft.
Dies ermöglicht es privaten Unternehmen nicht nur, Ihre Online-Aktivitäten zu überwachen, sondern es gibt in der Regel auch keine technischen Barrieren, die sie daran hindern, diese Daten absichtlich oder versehentlich an andere weiterzugeben.
Öffentliche Transparenzberichte von nur drei der vielen Technologieunternehmen, die Zugang zu diesen Daten haben (Apple, Google und Microsoft), zeigen, dass jedes Jahr Daten von Hunderttausenden von Nutzerkonten an Regierungen weitergegeben werden. Und das ist nur die Spitze des Eisbergs, denn der Whistleblower Edward Snowden hat 2013 durchgesickerte Dokumente veröffentlicht, aus denen hervorgeht, dass die Nationale Sicherheitsbehörde der Vereinigten Staaten (NSA) direkten Zugang zu den Servern dieser Unternehmen hat.
Die Tatsache, dass diese Daten gesammelt werden, birgt auch das Potenzial für Datenschutzverletzungen, die es böswilligen Akteuren ermöglichen, sich Zugang zu diesen Daten zu verschaffen. Allein im ersten Halbjahr 2021 wurden 18,8 Milliarden Datensätze aufgrund von Datenschutzverletzungen offengelegt. Zum Vergleich: In diesen sechs Monaten wurden bereits mehr Datensätze aufgrund von Datenschutzverletzungen offengelegt als im gesamten Jahr 2019.
Da das Internet in unserem modernen Leben immer mehr an Bedeutung gewinnt, wird die Menge der Daten, die durch Vereinbarungen über die gemeinsame Nutzung von Daten, staatliche Überwachung und Datenschutzverletzungen gesammelt und offengelegt werden, wahrscheinlich weiter zunehmen.
Eine der besten Möglichkeiten, sich vor diesem zunehmenden Zugriff auf Ihre persönlichen Daten zu schützen, besteht darin, sich über die verschiedenen Möglichkeiten zu informieren, wie Sie Ihre persönlichen Daten anonymisieren und die Grundsätze der Online-Anonymität umsetzen können, wenn Sie nicht möchten, dass Ihre Online-Aktivitäten überwacht werden.
In diesem Artikel stellen wir Ihnen sowohl Grundlagen für Anfänger als auch für Fortgeschrittene zum Thema Online-Anonymität vor. Die Grundsätze für Anfänger zeigen Ihnen, wie Sie die meisten Ihrer Daten anonymisieren können, ohne Ihre Surfgewohnheiten wesentlich ändern zu müssen, während die Grundsätze für Fortgeschrittene Ihnen zeigen, wie Sie fast alle Ihre Daten anonymisieren können, indem Sie größere Änderungen an der Art und Weise vornehmen, wie Sie das Internet nutzen.
Grundprinzipien für den Einstieg in die Online-Anonymität
Die meisten Ihrer Online-Aktivitäten sind über Ihre IP-Adresse, Ihre E-Mail-Adresse und Ihre Online-Konten mit Ihrer wirklichen Identität verknüpft. Es ist relativ einfach, alle drei Datenpunkte zu anonymisieren, unabhängig von Ihren technischen Kenntnissen. Dieser Leitfaden für Einsteiger konzentriert sich auf diese niedrig hängenden Früchte und hebt die kleinen Änderungen hervor, die Sie vornehmen können, um anonym zu surfen und Online-Konten zu erstellen.
1: Trennen Sie Ihre anonymen Aktivitäten von Ihrer wahren Identität.
Unabhängig von den Methoden und Werkzeugen, die Sie verwenden, um online anonym zu bleiben, kann eine unzureichende Trennung Ihrer anonymen Aktivitäten von Ihrer echten Identität dazu führen, dass Sie enttarnt werden. Wenn Sie sich beispielsweise über ein virtuelles privates Netzwerk (VPN) bei einem Konto anmelden, das mit Ihrer echten Identität verknüpft ist, oder wenn Sie Ihren echten Namen angeben, während Sie von einem Ihrer anonymen Konten aus kommunizieren, haben Sie Ihre Anonymität aufgegeben.
Wenn Sie die anderen Grundsätze der Online-Anonymität in diesem Artikel anwenden, sollten Sie daher nichts tun, was Ihre wahre Identität preisgeben oder darauf hindeuten könnte, z. B. Ihren richtigen Namen angeben, sich bei Konten anmelden, die mit Ihrer wahren Identität verknüpft sind, über Ihre anonymen Konten mit Personen kommunizieren, die Ihre wahre Identität kennen, oder dieselbe IP-Adresse für den Zugriff auf Ihre echten und Ihre anonymen Konten verwenden.
Wenn Sie mit Ihrer echten Identität arbeiten, sollten Sie auch nichts tun, was Ihre Anonymität gefährden könnte, z. B. sich bei Ihren anonymen Konten anmelden oder diese erwähnen.
Der Schlüssel zur Wahrung Ihrer Anonymität liegt darin, dass Sie sich stets darüber im Klaren sind, wie sich Ihre Handlungen auf Ihre Anonymität auswirken und wie Sie am besten zwischen Ihrer echten Identität und Ihren anonymen Aktivitäten unterscheiden können.
Da moderne Geräte, Browser und Anwendungen standardmäßig viele persönliche Daten speichern und Sie bei Ihren Konten angemeldet halten, ist eine der effektivsten Möglichkeiten, Ihre anonymen Aktivitäten von Ihrer echten Identität zu trennen, die Einrichtung separater Gerätebenutzerkonten oder Profile für jeden Zweck.
Sobald Sie diese eingerichtet haben, installieren Sie nur die Anwendungen, die Sie für die Anonymität benötigen (z. B. die Tools zur Maskierung Ihrer IP-Adresse, die wir im nächsten Abschnitt dieses Beitrags besprechen werden), auf den Gerätekonten für die Anonymität, verwenden Sie diese Konten nur, wenn Sie anonym arbeiten, und führen Sie von diesen Konten aus keine Aktivitäten durch, die mit Ihrer echten Identität in Verbindung stehen.
Wenn Sie unter Ihrer echten Identität arbeiten, verwenden Sie nur die Gerätekonten, die Ihrer echten Identität zugeordnet sind, und führen Sie von diesen Konten aus keine Aktivitäten durch, die mit Ihrer anonymen Aktivität in Verbindung stehen.
Wenn Sie diese Trennung auch auf Hardware-Ebene aufrechterhalten möchten, können Sie noch einen Schritt weiter gehen und für jeden Zweck separate Computer und Telefone verwenden. Installieren Sie die Anwendungen, die Sie für Ihre Anonymität benötigen, auf Ihren anonymen Computern und Telefonen und verwenden Sie diese ausschließlich für anonyme Aktivitäten. Wenn Sie mit Ihrer echten Identität arbeiten möchten, wechseln Sie zu den Computern oder Telefonen, die für Ihre echte Identität bestimmt sind.
2: Maskieren Sie Ihre IP-Adresse.
Standardmäßig wird Ihre echte IP-Adresse übertragen, wenn Ihr Computer oder Telefon eine Verbindung zum Internet herstellt. Diese echte IP-Adresse verrät allen Websites oder Online-Diensten, die Sie besuchen, Ihren Internetdienstanbieter und Ihren Standort.
Außerdem kann Ihr Internetanbieter, der bereits Ihren richtigen Namen, Ihre genaue Adresse, Ihre Kontaktdaten und Ihre Rechnungsadresse kennt, standardmäßig jede Website sehen, die Sie besuchen. In vielen Ländern können Internetanbieter gesetzlich verpflichtet sein, diese Daten über einen längeren Zeitraum zu speichern. Nach dem britischen Investigatory Powers Act können Internet-Diensteanbieter beispielsweise dazu verpflichtet werden, den Browserverlauf ihrer Nutzer bis zu einem Jahr lang zu speichern.
Durch die Maskierung Ihrer echten IP-Adresse können Sie verhindern, dass Websites und Online-Dienste diese Daten einsehen können, und Sie können auch verhindern, dass Ihr Internetanbieter Ihren Browserverlauf ausspioniert.
Es gibt zwei wichtige Werkzeuge, mit denen Sie Ihre IP-Adresse verschleiern können: Virtual Private Networks (VPNs) und Tor (The Onion Router).
VPNs bauen einen verschlüsselten Tunnel zwischen Ihrem Gerät und dem VPN-Server auf, der Ihren gesamten Datenverkehr zu den VPN-Servern leitet und ihn verschlüsselt, bevor er ins Internet übertragen wird. Sie können auch wählen, Ihren Datenverkehr über eine Reihe von VPN-Servern zu leiten, die sich überall auf der Welt befinden und jeweils eine eigene IP-Adresse haben. Da diese eindeutigen IP-Adressen mit anderen Nutzern des VPN-Dienstes geteilt werden, ist Ihr Internetverkehr für Dritte weitgehend anonym, da er mit dem Verkehr vieler anderer Nutzer vermischt wird.
Wenn Sie ein VPN verwenden, können die Websites und Online-Dienste, mit denen Sie sich verbinden, nur die IP-Adresse des von Ihnen verwendeten VPN-Servers sehen. Der verschlüsselte Tunnel verhindert auch, dass Ihr Internetanbieter sieht, welche Websites Sie besuchen.
Wenn Sie ein VPN verwenden, ist es am besten, einen Anbieter zu wählen, bei dem Sie anonym mit Bargeld oder Kryptowährungen bezahlen können (wir behandeln anonyme Kryptowährungstransaktionen im Abschnitt "Kryptowährungen für anonyme Zahlungen verwenden" in diesem Artikel), damit der VPN-Anbieter keine Finanzinformationen hat, die Ihr VPN-Konto mit Ihrer echten Identität in Verbindung bringen. Sowohl ProtonVPN als auch Mullvad VPN erfüllen dieses Kriterium.
Ein kostenloses ProtonVPN-Konto erhalten Sie hier, ein kostenloses MullvadVPN-Konto hier.
Tor leitet deinen Internetverkehr durch das dezentrale Tor-Netzwerk, das aus über 6.000 Tor-Knoten oder Relays (Server, auf denen die Open-Source-Software Tor läuft) besteht, die alle eine eigene IP-Adresse haben und über die ganze Welt verteilt sind. Dein Internetverkehr wird dreimal durch das Tor-Netzwerk geleitet und verschlüsselt, bevor er über einen Ausgangsknoten ins Internet gelangt. Dein Internetverkehr wird mit dem von Millionen anderen Tor-Benutzern vermischt und Tor wechselt automatisch alle 10 Minuten den Knoten.
Wenn du Tor benutzt, können die Webseiten und Online-Dienste, mit denen du dich verbindest, nur die IP-Adresse deines aktuellen Ausgangsknotens sehen, die sich ständig ändert. Auch dein Internetanbieter kann nicht sehen, welche Webseiten du besuchst, sondern nur, dass du Tor benutzt.
Den Tor-Browser kannst du hier herunterladen.
Wenn du den gesamten Internetverkehr deines Gerätes durch Tor leiten möchtest, kannst du Orbot für Android oder Tails für den Desktop benutzen (eine portable Linux-Distribution, die wir im Abschnitt "Stopp dem Datenversand deines Betriebssystems an Big Tech" in diesem Artikel genauer beschreiben).
Von der gleichzeitigen Nutzung von VPN und Tor wird generell abgeraten. Die gemeinnützige Organisation, die das Tor-Netzwerk betreibt, The Tor Project, rät davon ab, es sei denn, man ist ein fortgeschrittener Nutzer, der weiß, wie man beide so konfiguriert, dass die Privatsphäre nicht gefährdet wird.
Anonymität: Wenn du einen VPN-Anbieter wählst, der seinen Sitz in einem Land mit strengen Datenschutzgesetzen hat, und der es dir ermöglicht, ein Konto einzurichten, ohne persönliche Daten preiszugeben, bieten dir sowohl VPNs als auch Tor mehr Anonymität als dein Internetanbieter. Die Art und Weise, wie Tor deinen Datenverkehr über ein dezentralisiertes Netzwerk leitet, macht es jedoch anonymer als VPNs, die technisch in der Lage sind, deine Internetdaten zu sehen, auch wenn die meisten von ihnen versprechen, diese Daten nicht zu protokollieren oder weiterzugeben.
Nutzer insgesamt: Obwohl Tor technisch gesehen anonymer ist als VPNs, hat es weniger als drei Millionen tägliche Nutzer. VPNs haben eine weitaus größere Nutzerbasis mit geschätzten 142 Millionen Nutzern allein in den USA. Es ist also unwahrscheinlicher, dass du in der Masse untergehst, wenn du Tor benutzt, als wenn du ein VPN benutzt.
Geschwindigkeit: Die Internetgeschwindigkeit ist in der Regel langsamer, wenn man ein VPN oder Tor benutzt. VPNs sind aber normalerweise viel schneller als Tor.
Benutzerfreundlichkeit: VPNs sind in der Regel einfacher zu benutzen als Tor und die meisten VPNs haben intuitive Anwendungen, mit denen du den gesamten Internetverkehr deines Geräts nahtlos über VPN-Server leiten kannst. Den Browserverkehr mit dem Tor-Browser durch das Tor-Netzwerk zu leiten ist relativ einfach, aber den gesamten Internetverkehr deines Geräts durch das Tor-Netzwerk zu leiten ist technisch komplizierter. Außerdem werden bei der Verwendung von Tor mehr CAPTCHAs ausgelöst und der Zugriff auf Webseiten wird häufiger blockiert als bei der Verwendung von VPNs.
3: Verbergen Sie Ihre richtige E-Mail-Adresse.
Wenn Ihre Haupt-E-Mail-Adresse mit Ihrem echten Namen verknüpft ist und Sie diese E-Mail-Adresse jedes Mal verwenden, wenn Sie sich bei einem Online-Konto anmelden, geben Sie mehreren Unternehmen Zugang zu einem Datenpunkt, der dazu verwendet werden kann, Sie zu identifizieren. Wenn Sie Ihre echte E-Mail-Adresse verbergen, können Sie selbst entscheiden, ob Sie anonym bleiben möchten, wenn Sie zur Eingabe einer E-Mail-Adresse aufgefordert werden.
Um Ihre echte E-Mail-Adresse zu verbergen, müssen Sie ein anonymes E-Mail-Konto bei einem Anbieter einrichten, der keine persönlichen Daten verlangt, und die Verwendung von Burner-E-Mails in Betracht ziehen.
ProtonMail und Tutanota sind zwei Anbieter, die keine persönlichen Daten für die Anmeldung verlangen. Beide bieten außerdem eine Ende-zu-Ende-Verschlüsselung für zusätzlichen Datenschutz. Bei beiden Diensten müssen Sie lediglich Ihre E-Mail-Adresse und ein Passwort auswählen, um Ihr neues anonymes E-Mail-Konto einzurichten.
Um Ihre Anonymität zu erhöhen, sollten Sie unterschiedliche E-Mail- und VPN-Anbieter verwenden. Wenn Sie ProtonVPN zur Maskierung Ihrer IP-Adresse verwenden, sollten Sie ProtonMail nicht für Ihr anonymes E-Mail-Konto verwenden. Wenn Sie ProtonMail für Ihren anonymen E-Mail-Account verwenden, verwenden Sie nicht ProtonVPN, um Ihre IP-Adresse zu maskieren.
Ein kostenloses ProtonMail-Konto erhalten Sie hier, ein kostenloses Tutanota-Konto hier.
Sie sollten auch die Verwendung von Burner-E-Mails in Betracht ziehen, um zu verhindern, dass diese einzelne anonyme E-Mail-Adresse eine möglicherweise verräterische Datenspur hinterlässt, die dazu verwendet werden könnte, die mit der E-Mail-Adresse verbundenen Interessen und Aktivitäten zu überwachen, wenn sie weitergegeben oder geteilt wird.
Mit Burner-E-Mails können Sie jedes Mal, wenn Sie sich bei einem Online-Konto anmelden, eine neue, eindeutige E-Mail-Adresse erstellen. Jede dieser Burner-E-Mails leitet Nachrichten an Ihre anonyme E-Mail-Adresse weiter und kann jederzeit deaktiviert werden. Wenn eine dieser Burner-E-Mails weitergeleitet wird oder durchsickert, wird sie nicht mit einem Ihrer anderen Online-Konten verknüpft.
Burner-E-Mails eignen sich hervorragend, um den digitalen Fußabdruck, den Ihr anonymes E-Mail-Konto hinterlässt, zu minimieren, haben aber auch einige Nachteile.
Erstens kennt der Burner-E-Mail-Provider Ihre anonyme E-Mail-Adresse und kann alle Ihre Burner-E-Mails und die damit verbundenen Konten mit dieser einen anonymen E-Mail-Adresse verknüpfen.
Zweitens sind Sie bei der Anmeldung für Online-Konten von zwei Anbietern abhängig (Ihrem Burner-E-Mail-Anbieter und Ihrem anonymen E-Mail-Anbieter) anstatt von einem.
Wenn Sie die Anzahl der Unternehmen, auf die Sie sich bei der Verwaltung Ihrer anonymen E-Mails verlassen, minimieren möchten, ist Burner-E-Mail möglicherweise nicht das Richtige für Sie. Wenn Sie jedoch die Erstellung von Datenprofilen auf der Grundlage Ihrer anonymen E-Mail minimieren möchten, sind Burner-E-Mails eine Überlegung wert.
AnonAddy ist eines der besten Tools für Burner-E-Mails, um Ihre Anonymität zu wahren, da Sie kostenlos eine unbegrenzte Anzahl von Aliasnamen erstellen können, nur eine E-Mail-Adresse und ein Passwort zum Einloggen benötigen und Zahlungen in Kryptowährungen unterstützen. Für maximale Anonymität nutzen Sie die geteilten Domain-Aliase von AnonAddy. Sie erhalten 20 geteilte Domain-Aliase kostenlos und können 50 geteilte Domains für $1 pro Monat oder unbegrenzte geteilte Domains für $3 pro Monat erhalten.
Hier erfahren Sie, wie Sie mit AnonAddy Burnmail einrichten.
4: Verbergen Sie Ihre persönlichen Online-Konten
Die meisten Ihrer Online-Konten sind eng mit Ihrer wirklichen Identität verknüpft und speichern wahrscheinlich Informationen wie Ihren wirklichen Namen, Ihre wirkliche E-Mail-Adresse, Ihre wirkliche Adresse und Ihre Finanzdaten. Wenn Sie anonyme Konten einrichten, die diese persönlichen Daten nicht enthalten, können Sie deren Funktionen anonym nutzen.
Bei den meisten Online-Konten können Sie sich nur mit einer E-Mail-Adresse anmelden. Wenn Sie diese Grundregeln befolgen, können Sie die meisten Online-Konten einrichten, ohne Ihre wahre Identität preiszugeben.
Wenn Sie jedoch ein Konto einrichten müssen, für das Sie eine Telefonnummer, eine Adresse oder eine Zahlungsmethode angeben müssen, lesen Sie den Abschnitt "Erweiterte Grundsätze der Online-Anonymität", um zu erfahren, wie Sie diese anonym einrichten können.
Grundsätze für Fortgeschrittene zum Erreichen von Anonymität im Internet
Während die Grundprinzipien es Ihnen ermöglichen, im Internet zu surfen und Konten zu eröffnen, ohne Ihre wahre Identität preiszugeben, können Sie mit den fortgeschrittenen Prinzipien viel weiter gehen, indem Sie Ihr Betriebssystem anonymisieren und lernen, wie Sie anonym Telefonnummern einrichten, Zahlungen vornehmen und eine Adresse erhalten.
Diese fortgeschrittenen Prinzipien verlangen von Ihnen viel mehr Arbeit. Um sie vollständig umzusetzen, müssen Sie wahrscheinlich neue Hardware kaufen, die Art und Weise ändern, wie Sie mit Ihren Geräten interagieren, und rechtlichen Rat einholen. Sobald Sie diese Prinzipien jedoch umgesetzt haben, werden Sie Ihre Anonymität im Internet weit über das hinaus ausdehnen können, was mit den Grundregeln für Anfänger möglich ist.
1: Verbergen Sie Ihre richtige Telefonnummer.
Bei einigen Online-Diensten müssen Sie eine Telefonnummer angeben, bevor Sie ein Konto einrichten können. Da Ihre Haupttelefonnummer mit Ihrem echten Namen verknüpft ist, werden Sie durch die Angabe dieser Nummer enttarnt. Indem Sie Ihre echte Telefonnummer verbergen, haben Sie die Freiheit, sich für Privatsphäre und Anonymität zu entscheiden, wenn ein Online-Dienst Ihre Telefonnummer verlangt.
Prepaid-SIM-Karten sind eine der einfachsten Möglichkeiten, eine anonyme Telefonnummer zu erhalten. Wenn Sie sie in Geschäften wie Walmart, 7/11 oder Target mit Bargeld oder Geschenkkarten kaufen, gibt es keine digitale Zahlung, die Sie mit dem Kauf in Verbindung bringt. Es kann sein, dass es Überwachungsvideos von Ihrem Kauf gibt, aber viele Geschäfte bewahren diese nicht für immer auf. Wenn Sie die SIM-Karte mindestens einen Monat vor der geplanten Nutzung kaufen, erhöhen Sie die Wahrscheinlichkeit, dass der Kauf anonym bleibt.
Eine andere Möglichkeit, eine Prepaid-SIM-Karte anonym zu kaufen, besteht darin, jemanden zu bitten, die Karte als Geschenk für Sie zu kaufen und sie dann persönlich abzuholen.
Bevor Sie eine SIM-Karte kaufen oder als Geschenk erbitten, sollten Sie überlegen, ob Sie eines der datenschutzfreundlichen mobilen Betriebssysteme verwenden, die im nächsten Abschnitt dieses Leitfadens behandelt werden. Wenn Sie ein datenschutzfreundliches mobiles Betriebssystem verwenden möchten, vergewissern Sie sich, dass die von Ihnen erworbene Prepaid-SIM-Karte freigeschaltet und mit einem Gerät kompatibel ist, das das von Ihnen gewählte datenschutzfreundliche mobile Betriebssystem unterstützt.
Sobald Sie Ihre Prepaid-SIM-Karte haben, sollten Sie sich darüber im Klaren sein, dass sie bei der Aktivierung und Nutzung Funkmasten anpingt und Ihren ungefähren geografischen Standort übermittelt. Dadurch werden Sie zwar nicht enttarnt, da der Dienstanbieter Ihre wahre Identität nicht kennt, aber wenn Sie die Prepaid-SIM-Karte nur von zu Hause aus verwenden, erhält der Dienstanbieter eine ungefähre Vorstellung davon, wo Sie sich aufhalten. Daher sollten Sie die Karte auch außerhalb Ihrer Wohnung aktivieren und von verschiedenen Orten aus nutzen.
Im Idealfall sollten Sie die anonyme Telefonnummer nur dann verwenden, wenn Sie sich für Konten anmelden müssen, für die eine Telefonnummer erforderlich ist. Wenn Sie jedoch über diese anonyme Telefonnummer kommunizieren möchten, sollten Sie nur mit Personen kommunizieren, die Ihre wahre Identität nicht kennen, und nichts sagen, was Ihre wahre Identität bei dieser Kommunikation offenbaren könnte.
Sie sollten auch die Verwendung von Wegwerf-Telefonnummern in Erwägung ziehen, um zu verhindern, dass Ihre anonyme Telefonnummer einen digitalen Fußabdruck hinterlässt, der mehrere Konten mit einer einzigen Nummer verknüpft.
Mit Burner-Telefonnummern können Sie für jedes Online-Konto, für das Sie sich anmelden, eine neue Nummer erstellen. Diese "Burner"-Nummern werden mit keinem Ihrer anderen Online-Konten in Verbindung gebracht und tragen dazu bei, die Erstellung von Profilen auf der Grundlage einer einzigen anonymen Telefonnummer zu verhindern.
Es gibt jedoch einige Dinge, die Sie beachten sollten, bevor Sie Wegwerfnummern verwenden.
Erstens akzeptieren einige Online-Konten keine Nummern von Wegwerfnummern-Diensten, so dass Sie jedes Konto testen müssen und möglicherweise für einige Konten Ihre anonyme Telefonnummer verwenden müssen.
Zweitens: Im Gegensatz zu Burner-E-Mail-Diensten, bei denen Sie kostenlos oder gegen eine geringe monatliche Gebühr eine unbegrenzte Anzahl von Burner-E-Mails generieren können, müssen Sie bei Burner-Telefonnummern für zusätzliche Nummern Gebühren bezahlen. Wenn Sie mehr als eine Burner-Telefonnummer verwenden, ist die monatliche Gebühr wahrscheinlich höher als die Gebühr, die Sie für unbegrenzte Burner-E-Mails bei anderen Diensten zahlen. Und wenn Sie mehr als drei Burner-Telefonnummern verwenden, werden die Kosten erheblich sein.
Da nur relativ wenige Online-Dienste bei der Einrichtung eines Kontos die Angabe einer Telefonnummer verlangen, ist eine einzige anonyme Telefonnummer für die meisten Anwendungsfälle ausreichend. Wenn Sie jedoch Ihre Online-Präsenz auf mehrere Telefonnummern aufteilen möchten, ist eine einzige anonyme Telefonnummer relativ erschwinglich und bietet Ihnen die Flexibilität, Ihre Online-Präsenz auf zwei Nummern aufzuteilen.
Hushed ist ein großartiges Tool für anonyme Telefonnummern, das über das Internet von einem Computer und einem Telefon aus erreichbar ist. Außerdem kann man damit anonym mit Kryptowährung bezahlen.
Sie können sich hier für Hushed registrieren.
2: Stoppen Sie die Datenübermittlung Ihres Betriebssystems an Big Tech.
Google Android, Windows, macOS und iOS dominieren den Markt für Betriebssysteme und alle vier senden regelmäßig Daten an ihre Erfinder - Apple, Google und Microsoft. Durch die Verwendung eines datenschutzfreundlichen Betriebssystems können Sie den Datenfluss von Ihrem Betriebssystem zu diesen Big-Tech-Unternehmen unterbrechen und Ihre Anonymität und Privatsphäre verbessern.
Wenn Sie bisher ein Betriebssystem der großen Technologiekonzerne verwendet haben, wird der Wechsel zu einem alternativen Betriebssystem wahrscheinlich einige erhebliche Änderungen an der Art und Weise erfordern, wie Sie Ihren Computer und Ihr Telefon verwenden.
Das Ausmaß der Änderungen hängt von mehreren Faktoren ab, unter anderem davon, wie stark Sie in diese Big-Tech-Ökosysteme eingebunden sind, wie viele Betriebssystemfunktionen Sie nutzen und auf welches datenschutzfreundliche Betriebssystem Sie wechseln. Wenn Sie viele Betriebssystemfunktionen nutzen und stark von Big-Tech-Diensten abhängig sind, verlieren Sie möglicherweise den Zugang zu App-Stores, Apps, geräteübergreifender Datenabstimmung, Push-Benachrichtigungen und Zahlungsdiensten wie Apple Pay und Google Pay oder müssen alternative Lösungen finden.
Außerdem sind einige datenschutzfreundliche Betriebssysteme nur mit bestimmten Computern und Telefonen kompatibel und erfordern mehr technisches Know-how als die Betriebssysteme großer Unternehmen.
Auf dem Desktop ist die Open-Source-Linux-Gemeinschaft der populärste Anbieter von Software für Betriebssysteme, die nicht von Großunternehmen stammen, und es stehen zahlreiche Distributionen zur Verfügung. Keine der großen Linux-Distributionen sendet Ihre Daten an Big Tech zurück, sodass sie alle anonymer sind als Big Tech OS-Software. Es gibt jedoch auch Distributionen, bei denen die Benutzerfreundlichkeit im Vordergrund steht, während andere Distributionen eher technisch orientiert sind, sich aber besonders auf Anonymität, Datenschutz und Sicherheit konzentrieren.
Wenn Benutzerfreundlichkeit für Sie an erster Stelle steht, ist Ubuntu einfach zu bedienen und zu navigieren, hat eine aktive Community, läuft auf einer Vielzahl von Hardware und ist in hohem Maße anpassbar.
Prüfen Sie hier, ob Ubuntu mit Ihrem aktuellen Computer kompatibel ist, und laden Sie Ubuntu hier herunter.
Wenn du Tor als Hauptwerkzeug zur IP-Maskierung nutzen möchtest und bereit bist, ein Betriebssystem auszuprobieren, das nicht so einfach zu bedienen ist, gibt es zwei Linux-Distributionen, die sich auf Privatsphäre, Sicherheit und Anonymität konzentrieren und die du in Betracht ziehen solltest - Qubes OS und Tails.
Beide Distributionen ermöglichen es dir, Tor auf dem gesamten System laufen zu lassen und beide wurden von Edward Snowden, dem Whistleblower der National Security Agency (NSA), empfohlen.
Qubes OS ist eine auf Privatsphäre und Sicherheit ausgerichtete Linux-Distribution, die auch das private und anonyme virtuelle Betriebssystem Whonix integrieren kann. Es ist weniger komplex als Tails, hat aber eine eingeschränkte Kompatibilität.
Sie können hier sehen, ob Qubes OS mit Ihrem aktuellen Computer kompatibel ist und Qubes OS hier herunterladen.
Tails ist eine portable Linux-Distribution, die auf jedem USB-Stick mit mindestens 8 GB Speicherplatz installiert werden kann. Es läuft auf den meisten Computern, die nicht älter als 10 Jahre sind. Standardmäßig löscht es beim Herunterfahren alles, obwohl es eine Option gibt, einige Dateien in einem verschlüsselten permanenten Speicher zu speichern. Allerdings ist es schwieriger zu booten und zu benutzen als Qubes OS.
Tails kann hier heruntergeladen werden.
Auf mobilen Geräten sind zwei der besten Möglichkeiten, Big Tech aus dem Betriebssystem zu entfernen, die Verwendung von entgoogelten Android-Distributionen oder die Verwendung von Linux-Handys. De-Googled Android ist für normale Benutzer am einfachsten zu verwenden und unterstützt die meisten Android-Anwendungen. Wenn Sie jedoch viel Erfahrung mit Linux haben, sollten Sie ein Linux-Telefon bevorzugen.
GrapheneOS und LineageOS sind zwei der besten De-Googled Android-Distributionen, bei denen der Datenschutz im Vordergrund steht. LineageOS kann auf einer breiteren Palette von Telefonen installiert werden, aber GrapheneOS hat mehr Datenschutzfunktionen in das Betriebssystem integriert (z.B. Schutz vor Fingerabdrücken und Sandboxing für Wi-Fi und GPS).
Weitere Informationen zu GrapheneOS finden Sie hier und zu LineageOS hier.
Eine Installationsanleitung für GrapheneOS finden Sie hier.
Librem 5 (auf dem die Linux-Distribution PureOS läuft) und das PinePhone (das mit der Linux-Distribution Manjaro ausgeliefert wird, die grafische Oberfläche Plasma Mobile verwendet und alle wichtigen Linux-Telefon-Projekte unterstützt) sind zwei der besten Linux-Telefone mit Fokus auf Datenschutz.
Weitere Informationen zum Librem 5 finden Sie hier und zum PinePhone hier.
Unabhängig davon, für welches Betriebssystem Sie sich entscheiden, deaktivieren Sie GPS, Mobilfunk, Bluetooth und alle anderen Ortungsdienste, bis Sie sie benötigen. Wenn Sie auf diese Dienste angewiesen sind, sollten Sie sie außerhalb des Hauses verwenden, da sie Ihren ungefähren Standort an Mobilfunkmasten und Ihren genauen Standort an alle Anwendungen und Dienste auf dem Gerät übermitteln, die auf Ihren Standort zugreifen können.
5: Verwenden Sie Kryptowährungen für anonyme Zahlungen.
Kartenzahlungen, Banküberweisungen, Zahlungsdienste wie PayPal und die meisten anderen Online-Zahlungsmethoden sind mit Ihrer echten Identität verknüpft. Auf diese Weise können diese Zahlungsanbieter alles überwachen, was Sie kaufen. Kryptowährungen sind eine der wenigen Online-Zahlungsmöglichkeiten, die es Ihnen ermöglichen, Einkäufe zu tätigen, ohne dass Dritte diese Einkäufe mit Ihrer echten Identität in Verbindung bringen können.
Der Nachteil ist, dass diese Anonymität je nach verwendeter Kryptowährung variiert und davon abhängt, ob Sie Ihre Kryptowährung erwerben, ohne Ihre Identität preiszugeben und ohne sicherzustellen, dass niemand jemals herausfindet, welche Kryptowährungs-Wallets Sie besitzen.
Fast alle Kryptowährungen nutzen öffentliche Blockchains. Einige Kryptowährungen wie Monero verschleiern Daten wie die Absender- und Empfängeradresse und den Transaktionsbetrag. Die meisten Kryptowährungen, einschließlich der beliebtesten Kryptowährung Bitcoin, zeigen jedoch alle Wallet-Adressen und alle von diesen Wallets gesendeten und empfangenen Transaktionen auf einer öffentlichen Blockchain an.
Das bedeutet, dass jeder, der keine Kryptowährung mit Datenschutz- und Anonymitätsmaßnahmen verwendet, die Blockchain analysieren und alle von einer Wallet gesendeten und empfangenen Gelder leicht einsehen kann. Diese Wallet-Adresse ist zwar standardmäßig anonym, aber wenn Sie versehentlich Ihren Besitz einer oder mehrerer Wallet-Adressen offenlegen, sind alle Transaktionen dieser unmaskierten Wallets für die Welt sichtbar.
Theoretisch würde die Verwendung von Monero für alle Kryptowährungstransaktionen dieses Problem lösen. Viele Websites, die Kryptowährungen akzeptieren, akzeptieren jedoch nur weitverbreitete Kryptowährungen wie Bitcoin und Ethereum. Daher müssen Sie wissen, wie Sie Kryptowährungen anonym erhalten und Ihren Besitz anonym halten können, unabhängig von den Datenschutzvorkehrungen einer bestimmten Kryptowährung.
Die beiden wichtigsten Möglichkeiten, Kryptowährungen anonym zu erwerben, sind das Mining und der Kauf von Kryptowährungen mit Bargeld oder Gutscheinen.
Das Mining von Kryptowährungen ermöglicht es, Kryptowährungen zu erwerben, ohne sich auf Dritte verlassen zu müssen und ohne Spuren der Transaktion zu hinterlassen. Das Mining ist jedoch mit höheren Vorabkosten verbunden (da Sie in Mining-Hardware investieren müssen) und erfordert eine steilere Lernkurve.
Weitere Informationen über das Schürfen von Kryptowährungen finden Sie hier.
Der Kauf von Kryptowährungen mit Bargeld oder Geschenkkarten ist mit geringeren Vorabkosten verbunden als das Mining (da Sie nur für die Kryptowährung bezahlen, die Sie benötigen) und einfacher zu erlernen als das Mining von Kryptowährungen. Allerdings müssen Sie Transaktionen mit Dritten durchführen, und obwohl es keine Verbindung zwischen diesen Transaktionen und Ihrer echten Identität gibt, gibt es dennoch einen Zahlungsweg.
Um Kryptowährungen mit Bargeld oder Geschenkkarten zu kaufen, müssen Sie eine Börse nutzen, die keine Kundenverifizierung (KYC) verlangt und keine persönlichen Daten sammelt. Börsen wie HodlHodl und Bisq erfüllen dieses Kriterium.
Sie müssen sich auch vergewissern, dass die Börse die Kryptowährung, die Sie kaufen möchten, auflistet, bevor Sie sich anmelden, Geld senden oder Ihr Wallet anschließen.
Eine Liste von Kryptowährungsbörsen, die keine KYC-Anforderungen stellen, finden Sie hier.
Sobald Sie Ihre Kryptowährung erhalten haben, müssen Sie sie anonym halten. Wenn Sie Monero verwenden, können Sie eine der empfohlenen Wallets auf der Download-Seite verwenden, um anonym zu handeln.
Sie können eine der empfohlenen Wallets für Monero hier herunterladen.
Wenn Sie eine andere Kryptowährung verwenden, sollten Sie bewährte Verfahren befolgen, um sicherzustellen, dass niemand Ihre anonymen Wallet-Adressen mit Ihrer echten Identität in Verbindung bringen kann. Dazu gehört, dass Sie niemals eine Wallet verwenden, die mit Ihrer echten Identität verknüpft ist (z. B. eine Coinbase-Wallet), um Gelder direkt an eine Ihrer anonymen Wallets zu senden, dass Sie niemals Ihre anonymen Wallets verwenden, um Gelder an eine Wallet zu senden, die mit Ihrer echten Identität verknüpft ist, und Sie niemals Ihre anonymen Wallet-Adressen veröffentlichen oder darauf verweisen, wo sie mit Ihrer echten Identität verknüpft sind.
Einige Kryptowährungs-Wallets verfügen auch über integrierte Datenschutzfunktionen, die Ihre Anonymität erhöhen können. Beispielsweise rotieren einige Bitcoin-Wallets Ihre Adressen, um Ihre Transaktionen zu verschleiern.
Sie können den Wallet-Selektor von Bitcoin.org hier aufrufen, um die Datenschutzfunktionen verschiedener Bitcoin-Wallets zu überprüfen.
Für andere Kryptowährungen müssen Sie die verfügbaren Wallets recherchieren und herausfinden, welche die besten Datenschutz- und Anonymitätsfunktionen für Ihren Anwendungsfall bieten.
6: Maskieren Sie Ihre Identität mit einer anonymen Gesellschaft mit beschränkter Haftung (LLC).
Für einige Aufgaben, wie z.B. den Empfang von Paketen, benötigen Sie eine reale Identität. Mit einer anonymen Gesellschaft mit beschränkter Haftung (GmbH) können Sie diese reale Identität erhalten, ohne dass eine persönliche Verbindung zu Ihnen besteht.
Die Durchführbarkeit einer anonymen GmbH hängt von Ihrem Wohnort und Ihren persönlichen Umständen ab. Bevor Sie eine anonyme Gesellschaft mit beschränkter Haftung gründen, sollten Sie sich rechtlich beraten lassen, die steuerlichen Auswirkungen berücksichtigen und prüfen, wie gut eine anonyme Gesellschaft mit beschränkter Haftung Ihre Privatsphäre schützen kann. In einigen Bundesstaaten wie Nevada, New Mexico und Wyoming können Sie eine anonyme LLC gründen, ohne dass der Eigentümer registriert wird.
Sobald Sie die anonyme LLC gegründet haben, können Sie ein Postfach einrichten, das mit der anonymen LLC verknüpft ist, und dieses Postfach verwenden, um Pakete zu empfangen, ohne Ihre Identität preiszugeben.
Abschließende Empfehlungen zum Erreichen von Online-Anonymität
Wie wir in diesem Artikel immer wieder betont haben, können diese Prinzipien und Werkzeuge Ihnen helfen, Ihre wahre Identität bei der Nutzung des Internets zu verbergen, aber es kommt wirklich darauf an, wie Sie sie einsetzen.
Unabhängig davon, welche Grundsätze Sie anwenden, bleiben Sie wachsam und konzentrieren Sie sich stets darauf, Ihre anonymen Aktivitäten von Ihrer wahren Identität zu trennen.
Quelle: Principles for anonymizing your online activity, https://reclaimthenet.org/online-anonymity-principles
https://uncutnews.ch/grundsaetze-zur-anonymisierung-ihrer-online-aktivitaeten/
 Our VPN-recommendation for the PC: the optional security increasing OpenSource-addition to Tor (Tor-Netzwerk, Socks5-Proxy for Browser like Pale Moon or the tor-browser ): Our VPN-recommendation for the PC: the optional security increasing OpenSource-addition to Tor (Tor-Netzwerk, Socks5-Proxy for Browser like Pale Moon or the tor-browser ):
OpenVPN, OpenSwan oder Strongswan
StrongSwan is an OpenSource IPsec-based VPN Solution for Linux * runs both on Linux 2.4 (KLIPS IPsec) and Linux 2.6 (NETKEY IPsec) kernels * implements both the IKEv1 and IKEv2 (RFC 4306) key exchange protocols * Fully tested support of IPv6 IPsec tunnel and transport connections * Dynamical IP address and interface update with IKEv2 MOBIKE (RFC 4555) * Automatic insertion and deletion of IPsec-policy-based firewall rules * Strong 128/192/256 bit AES or Camellia encryption, 3DES support * NAT-Traversal via UDP encapsulation and port floating (RFC 3947) * Dead Peer Detection (DPD, RFC 3706) takes care of dangling tunnels * Static virtual IPs and IKEv1 ModeConfig pull and push modes * XAUTH server and client functionality on top of IKEv1 Main Mode authentication * Virtual IP address pool managed by IKE daemon or SQL database * Secure IKEv2 EAP user authentication (EAP-SIM, EAP-AKA, EAP-MSCHAPv2, etc.) * Optional relaying of EAP messages to AAA server via EAP-RADIUS plugin * Support of IKEv2 Multiple Authentication Exchanges (RFC 4739) * Authentication based on X.509 certificates or preshared keys * Generation of a default self-signed certificate during first strongSwan startup * Retrieval and local caching of Certificate Revocation Lists via HTTP or LDAP * Full support of the Online Certificate Status Protocol (OCSP, RCF 2560). * CA management (OCSP and CRL URIs, default LDAP server) * Powerful IPsec policies based on wildcards or intermediate CAs * Group policies based on X.509 attribute certificates (RFC 3281) * Storage of RSA private keys and certificates on a smartcard (PKCS #11 interface) * Modular plugins for crypto algorithms and relational database interfaces * Support of elliptic curve DH groups and ECDSA certificates (Suite B, RFC 4869) * Optional built-in integrity and crypto tests for plugins and libraries * Smooth Linux desktop integration via the strongSwan NetworkManager applet This package triggers the installation of both, IKEv1 and IKEv2 daemons. Authors: -------- Andreas Steffen and others
In detail: https://www.strongswan.org
... Gooken 1000% security 1000% - can´t it be true?
So roll up your arms for your PC operated by - as we hope - Linux upon hardware like the one we recommend in our data sheed, and you just need to "hammer" upon all kind of settings of your smartphone running with - as we hope - Orbot (Tor and VPN and VPN-Firewall all in one) and the for Wifi (WLAN) configured Orbot-Proxy for security, wherever you can,
... and you got it: the promised: Gooken - 1000% security 1000% -. Gooken !
Have a lot of fun.
 Internet Browser for the PC: Gooken recommends OpenSource-browser Pale Moon (actual version 32.5.2 from 12/2023) and belonging extensions like "Certificate Patrol" (all from palemoon.org), Firefox nightly for Smartphones. Internet Browser for the PC: Gooken recommends OpenSource-browser Pale Moon (actual version 32.5.2 from 12/2023) and belonging extensions like "Certificate Patrol" (all from palemoon.org), Firefox nightly for Smartphones.
 Browser-certifactes, certifying organisations and their meanings Browser-certifactes, certifying organisations and their meanings
"eIDAS-Artikel 45 - Dieses System würde die Regierungen der EU-Mitgliedstaaten einen Schritt näher an den Punkt bringen, an dem sie Man-in-the-Middle-Angriffe gegen ihre eigenen Bürger durchführen könnten. Außerdem müssten sie Zugang zu den Netzen erhalten. Die Regierungen sind in der Lage, das zu tun"
Die EU will die Internetnutzung der Europäer ausspionieren, T.H.G., uncut-news.ch, 01.17.2024
Bevölkerungskontrolle und oder Neue Weltordnung (NWO), EU/Europa, Zensur
Von Robert Blumen
Die Europäische Kommission ist ein EU-Gesetzgebungsorgan mit Regulierungsbefugnis für digitale Technologien. Der eIDAS-Artikel 45, ein Verordnungsvorschlag der Europäischen Kommission, würde bewusst Bereiche der Internetsicherheit schwächen, die die Industrie seit über 25 Jahren sorgfältig entwickelt und gehärtet hat. Der Artikel würde den 27 EU-Regierungen weitreichende Überwachungsbefugnisse über die Internetnutzung einräumen.
Die Vorschrift würde von allen Internet-Browsern verlangen, dass sie einem zusätzlichen Stammzertifikat einer Behörde (oder einer regulierten Einrichtung) aus jedem der nationalen Regierungen der EU-Mitgliedstaaten vertrauen. Für die nicht technisch versierten Leser werde ich erklären, was ein Root-Zertifikat ist, wie sich das Vertrauen in das Internet entwickelt hat und was Artikel 45 damit zu tun hat. Und dann werde ich einige Kommentare aus der Tech-Community zu diesem Thema hervorheben.
Im nächsten Abschnitt dieses Artikels werde ich erklären, wie die Vertrauensinfrastruktur des Internets funktioniert. Dieser Hintergrund ist notwendig, um zu verstehen, wie radikal der vorgeschlagene Artikel ist. Die Erläuterung soll auch für einen nichttechnischen Leser verständlich sein.
In der fraglichen Verordnung geht es um die Sicherheit des Internets. Mit "Internet" sind hier vor allem die Browser gemeint, die Websites besuchen. Die Sicherheit des Internets besteht aus vielen verschiedenen Aspekten. Artikel 45 zielt darauf ab, die Public Key Infrastructure (PKI) zu ändern, die seit Mitte der 90er Jahre Teil der Internetsicherheit ist. Die PKI wurde zunächst eingeführt und dann über einen Zeitraum von 25 Jahren verbessert, um Nutzern und Herausgebern die folgenden Garantien zu bieten:
Datenschutz bei der Kommunikation zwischen dem Browser und der Website: Browser und Websites kommunizieren über das Internet, ein Netz von Netzwerken, die von Internetdienstanbietern und Tier-1-Carriern betrieben werden, oder von Mobilfunkanbietern, wenn das Gerät mobil ist. Das Netz selbst ist nicht von Natur aus sicher oder vertrauenswürdig. Ihr neugieriger Internetdienstanbieter zu Hause, ein Reisender in der Flughafenlounge, in der Sie auf Ihren Flug warten, oder ein Datenhändler, der Leads an Werbetreibende verkaufen will, könnten Sie ausspionieren wollen. Ohne jeglichen Schutz könnte ein böswilliger Akteur vertrauliche Daten wie ein Passwort, den Kontostand Ihrer Kreditkarte oder Gesundheitsinformationen einsehen.
Stellen Sie sicher, dass Sie die Seite genau so sehen, wie sie Ihnen von der Website übermittelt wurde: Wenn Sie eine Webseite aufrufen, könnte sie zwischen dem Herausgeber und Ihrem Browser manipuliert worden sein? Ein Zensor könnte Inhalte entfernen wollen, die Sie nicht sehen sollen. Inhalte, die als "Fehlinformationen" bezeichnet wurden, wurden während der Covid-Hysterie weitgehend unterdrückt. Ein Hacker, der Ihre Kreditkarte gestohlen hat, möchte vielleicht die Beweise für seine betrügerischen Abbuchungen entfernen.
Vergewissern Sie sich, dass die Website, die Sie sehen, auch wirklich diejenige ist, die in der Standortleiste des Browsers angezeigt wird: Wenn Sie eine Verbindung zu einer Bank herstellen, woher wissen Sie, dass Sie die Website dieser Bank sehen und nicht eine gefälschte Version, die identisch aussieht? Sie überprüfen die Standortleiste in Ihrem Browser. Könnte Ihr Browser so getäuscht werden, dass er Ihnen eine gefälschte Website anzeigt, die mit der echten identisch zu sein scheint? Woher weiß Ihr Browser mit Sicherheit, dass er mit der richtigen Website verbunden ist?
In den Anfängen des Internets gab es keine dieser Zusicherungen. Im Jahr 2010 ermöglichte ein im Add-on-Store erhältliches Browser-Plugin die Teilnahme am Facebook-Gruppenchat eines anderen Nutzers in einem Café-Hotspot. Heute können Sie sich dank PKI dieser Dinge ziemlich sicher sein.
Diese Sicherheitsmerkmale werden durch ein System geschützt, das auf digitalen Zertifikaten basiert. Digitale Zertifikate sind eine Art Ausweis - die Internetversion eines Führerscheins. Wenn ein Browser eine Verbindung zu einer Website herstellt, legt die Website dem Browser ein Zertifikat vor. Das Zertifikat enthält einen kryptografischen Schlüssel. Der Browser und die Website arbeiten mit einer Reihe von kryptografischen Berechnungen zusammen, um eine sichere Kommunikation aufzubauen.
Gemeinsam bieten der Browser und die Website die drei Sicherheitsgarantien:
Datenschutz: durch Verschlüsselung des Gesprächs.
Kryptografische digitale Signaturen: um sicherzustellen, dass der Inhalt während der Übertragung nicht verändert wird.
Überprüfung des Herausgebers: durch die von der PKI bereitgestellte Vertrauenskette, auf die ich weiter unten näher eingehen werde.
Eine gute Identität sollte schwer zu fälschen sein. In der Antike diente ein Wachsabdruck eines Siegels diesem Zweck. Die Identitäten der Menschen beruhen auf biometrischen Merkmalen. Ihr Gesicht ist eine der ältesten Formen. In der nicht-digitalen Welt werden Sie nach einem Lichtbildausweis gefragt, wenn Sie Zugang zu einem altersbeschränkten Bereich benötigen, z. B. wenn Sie ein alkoholisches Getränk bestellen.
Ein weiteres biometrisches Merkmal aus der Zeit vor der Digitalisierung war der Abgleich Ihrer frischen Unterschrift mit der Originalunterschrift auf der Rückseite Ihres Personalausweises. Da diese älteren Arten der Biometrie immer leichter zu fälschen sind, hat sich die menschliche Identitätsprüfung angepasst. Heute ist es üblich, dass eine Bank Ihnen einen Validierungscode auf Ihr Handy schickt. Die App verlangt von Ihnen, dass Sie eine biometrische Identitätsprüfung auf Ihrem Mobiltelefon durchführen, um den Code anzuzeigen, z. B. eine Gesichtserkennung oder Ihren Fingerabdruck.
Neben den biometrischen Merkmalen ist der zweite Faktor, der einen Ausweis vertrauenswürdig macht, der Ausweisaussteller. Weithin akzeptierte Ausweise hängen von der Fähigkeit des Ausstellers ab, zu überprüfen, ob die Person, die einen Ausweis beantragt, diejenige ist, die sie vorgibt zu sein. Die meisten der am meisten akzeptierten Ausweise werden von staatlichen Behörden ausgestellt, z. B. vom Kraftfahrzeugamt. Wenn die ausstellende Behörde über zuverlässige Mittel verfügt, um nachzuvollziehen, wer und wo sich die betreffenden Personen aufhalten, wie z. B. Steuerzahlungen, Beschäftigungsnachweise oder die Nutzung von Wasserversorgungsdiensten, dann ist die Wahrscheinlichkeit groß, dass die Behörde überprüfen kann, ob es sich bei der auf dem Ausweis genannten Person um diese Person handelt.
In der Online-Welt haben sich die Regierungen in den meisten Fällen nicht an der Identitätsprüfung beteiligt. Zertifikate werden von privatwirtschaftlichen Unternehmen ausgestellt, die als Zertifizierungsstellen (CAs) bekannt sind. Während Zertifikate früher recht teuer waren, sind die Gebühren inzwischen so weit gesunken, dass sie teilweise kostenlos sind. Die bekanntesten CAs sind Verisign, DigiCert und GoDaddy. Ryan Hurst zeigt, dass die sieben großen CAs (ISRG, DigiCert, Sectigo, Google, GoDaddy, Microsoft und IdenTrust) 99 % aller Zertifikate ausstellen.
Der Browser akzeptiert ein Zertifikat nur dann als Identitätsnachweis, wenn das Namensfeld des Zertifikats mit dem Domänennamen übereinstimmt, den der Browser in der Adressleiste anzeigt. Selbst wenn die Namen übereinstimmen, ist damit sichergestellt, dass ein Zertifikat mit der Aufschrift "apple.com" dem Unterhaltungselektronikunternehmen Apple, Inc. gehört? Identitätssysteme sind nicht kugelsicher. Minderjährige können sich gefälschte Ausweise besorgen. Wie menschliche Ausweise können auch digitale Zertifikate gefälscht oder aus anderen Gründen ungültig sein. Ein Softwareentwickler, der kostenlose Open-Source-Tools verwendet, kann mit ein paar Linux-Befehlen ein digitales Zertifikat mit dem Namen "apple.com" erstellen.
Das PKI-System stützt sich auf Zertifizierungsstellen, die jedes Zertifikat nur für den Eigentümer der Website ausstellen. Der Arbeitsablauf zum Erwerb eines Zertifikats sieht folgendermaßen aus:
Der Herausgeber einer Website beantragt bei seiner bevorzugten Zertifizierungsstelle ein Zertifikat für eine Domäne.
Die CA prüft, ob der Zertifikatsantrag vom tatsächlichen Eigentümer der Website stammt. Wie stellt die CA dies fest? Die CA verlangt, dass die antragstellende Stelle einen bestimmten Inhalt unter einer bestimmten URL veröffentlicht. Die Fähigkeit, dies zu tun, beweist, dass die Einrichtung die Kontrolle über die Website hat.
Sobald die Website nachgewiesen hat, dass sie Eigentümerin der Domäne ist, fügt die Zertifizierungsstelle dem Zertifikat eine kryptografische digitale Signatur mit ihrem eigenen privaten kryptografischen Schlüssel hinzu. Die Signatur weist die CA als Aussteller aus.
Das signierte Zertifikat wird an die antragstellende Person oder Einrichtung übermittelt.
Der Herausgeber installiert sein Zertifikat auf seiner Website, so dass es den Browsern angezeigt werden kann.
Kryptografische digitale Signaturen sind "ein mathematisches Verfahren zur Überprüfung der Authentizität digitaler Nachrichten oder Dokumente". Sie sind nicht dasselbe wie die Online-Dokumentensignatur, die von DocuSign und ähnlichen Anbietern bereitgestellt wird. Wenn die Signatur gefälscht werden könnte, wären die Zertifikate nicht vertrauenswürdig. Im Laufe der Zeit wurde die Größe der kryptografischen Schlüssel erhöht, um eine Fälschung zu erschweren. Kryptographieforscher sind der Meinung, dass die derzeitigen Signaturen in der Praxis unmöglich zu fälschen sind. Eine weitere Schwachstelle besteht darin, dass der CA ihre geheimen Schlüssel gestohlen werden.
Der Dieb könnte dann gültige Signaturen dieser Zertifizierungsstelle erstellen.
Sobald das Zertifikat installiert ist, wird es bei der Einrichtung einer Webkonversation verwendet. The Register erklärt, wie das geht:
Wenn das Zertifikat von einer bekannt guten Zertifizierungsstelle ausgestellt wurde und alle Angaben korrekt sind, ist die Website vertrauenswürdig, und der Browser versucht, eine sichere, verschlüsselte Verbindung mit der Website herzustellen, so dass Ihre Aktivitäten auf der Website für einen Lauscher im Netzwerk nicht sichtbar sind. Wenn das Zertifikat von einer nicht vertrauenswürdigen Zertifizierungsstelle ausgestellt wurde, das Zertifikat nicht mit der Adresse der Website übereinstimmt oder einige Details falsch sind, lehnt der Browser die Website ab, weil er befürchtet, dass er sich nicht mit der tatsächlichen Website verbindet, die der Benutzer wünscht, sondern mit einem Imitator.
Wir können dem Browser vertrauen, weil der Browser der Website vertraut. Der Browser vertraut der Website, weil das Zertifikat von einer "bekannt guten" CA ausgestellt wurde. Aber was ist eine "bekannt gute CA"? Die meisten Browser verlassen sich auf die vom Betriebssystem bereitgestellten CAs. Die Liste der vertrauenswürdigen CAs wird von den Geräte- und Softwareherstellern festgelegt. Die großen Computer- und Gerätehersteller - Microsoft, Apple, die Hersteller von Android-Telefonen und die Open-Source-Linux-Distributoren - statten das Betriebssystem ihrer Geräte mit einer Reihe von Stammzertifikaten aus.
Diese Zertifikate weisen die von ihnen überprüften und als zuverlässig erachteten Zertifizierungsstellen aus. Diese Sammlung von Stammzertifikaten wird als "Vertrauensspeicher" bezeichnet. Der Windows-PC, auf dem ich diesen Artikel schreibe, verfügt über 70 Stammzertifikate in seinem Trusted Root Certificate Store, um ein Beispiel aus meiner Nähe zu nennen. Auf der Support-Website von Apple sind alle Stammzertifikate aufgeführt, denen die Sierra-Version von MacOS vertraut.
Wie entscheiden die Computer- und Telefonhersteller, welche Zertifizierungsstellen vertrauenswürdig sind? Sie verfügen über Prüfungs- und Compliance-Programme, um die Qualität der Zertifizierungsstellen zu bewerten. Nur diejenigen, die sie bestehen, werden aufgenommen. Siehe z. B. den Chrome-Browser (der einen eigenen Vertrauensspeicher bereitstellt und nicht den auf dem Gerät vorhandenen verwendet). Die EFF (die sich selbst als "die führende gemeinnützige Organisation zur Verteidigung der bürgerlichen Freiheiten in der digitalen Welt" bezeichnet) erklärt dies:
Browser verwenden "Root-Programme", um die Sicherheit und Vertrauenswürdigkeit der Zertifizierungsstellen, denen sie vertrauen, zu überwachen. Diese Root-Programme stellen eine Reihe von Anforderungen, die von der Frage, wie das Schlüsselmaterial gesichert werden muss, über die Frage, wie die Kontrolle der Domänennamen validiert werden muss, bis hin zu der Frage, welche Algorithmen für die Signierung der Zertifikate verwendet werden müssen, reichen.
Nachdem eine Zertifizierungsstelle von einem Anbieter akzeptiert wurde, wird sie von diesem weiterhin überwacht. Die Anbieter werden die Zertifizierungsstellen aus dem Vertrauensspeicher entfernen, wenn die Zertifizierungsstelle die erforderlichen Sicherheitsstandards nicht einhält. Zertifizierungsstellen können abtrünnig werden oder aus anderen Gründen versagen, was auch geschieht. The Register berichtet:
Zertifikate und die CAs, die sie ausstellen, sind nicht immer vertrauenswürdig, und Browserhersteller haben im Laufe der Jahre CA-Root-Zertifikate von CAs mit Sitz in der Türkei, Frankreich, China, Kasachstan und anderen Ländern entfernt, wenn sich herausstellte, dass die ausstellende Stelle oder eine mit ihr verbundene Partei den Webverkehr abfing.
Im Jahr 2022 berichtete der Forscher Ian Carroll über Sicherheitsprobleme mit der Zertifizierungsstelle e-Tugra. Carroll "fand eine Reihe alarmierender Probleme, die mich hinsichtlich der Sicherheitspraktiken innerhalb des Unternehmens beunruhigen", wie etwa schwache Anmeldedaten. Carrolls Berichte wurden von den großen Softwareanbietern bestätigt. Infolgedessen wurde e-Tugra aus ihren vertrauenswürdigen Zertifikatsspeichern entfernt.
Die Timeline of Certificate Authority Failures berichtet über weitere derartige Vorfälle.
Es gibt immer noch einige bekannte Lücken in der PKI, wie sie derzeit besteht. Da ein bestimmtes Problem für das Verständnis von eIDAS Artikel 45 wichtig ist, werde ich es im Folgenden erläutern. Das Vertrauen einer Zertifizierungsstelle ist nicht auf die Websites beschränkt, die ihre Geschäfte mit dieser Zertifizierungsstelle abwickeln. Ein Browser akzeptiert ein Zertifikat von einer beliebigen vertrauenswürdigen Zertifizierungsstelle für eine beliebige Website. Es gibt nichts, was die CA daran hindert, einem schlechten Akteur eine Website auszustellen, die nicht vom Eigentümer der Website angefordert wurde. Ein solches Zertifikat wäre im rechtlichen Sinne betrügerisch, weil es für denjenigen ausgestellt wurde, dem es gehört. Der Inhalt des Zertifikats wäre jedoch aus Sicht des Browsers technisch gültig.
Wenn es eine Möglichkeit gäbe, jede Website mit ihrer bevorzugten Zertifizierungsstelle zu verknüpfen, dann würde jedes Zertifikat für diese Website von einer anderen Zertifizierungsstelle sofort als betrügerisch erkannt werden. Certificate Pinning ist ein weiterer Standard, der einen Schritt in diese Richtung macht. Aber wie wird diese Zuordnung veröffentlicht und wie kann man diesem Herausgeber vertrauen?
Auf jeder Ebene dieses Prozesses stützt sich die technische Lösung auf eine externe Vertrauensquelle. Aber wie wird dieses Vertrauen hergestellt? Indem man sich auf eine noch vertrauenswürdigere Quelle auf der nächsthöheren Ebene verlässt? Diese Frage veranschaulicht die "Schildkröten, den ganzen Weg nach unten" Natur des Problems. Die PKI hat eine Schildkröte am unteren Ende: den Ruf, die Sichtbarkeit und die Transparenz der Sicherheitsbranche und ihrer Kunden. Vertrauen wird auf dieser Ebene durch ständige Überwachung, offene Standards, die Softwareentwickler und die Zertifizierungsstellen geschaffen.
Es wurden bereits gefälschte Zertifikate ausgestellt. Im Jahr 2013 berichtete ArsTechnica, dass eine französische Agentur dabei erwischt wurde, SSL-Zertifikate zu prägen, die sich als Google ausgaben:
Im Jahr 2011 entdeckten Sicherheitsforscher ein gefälschtes Zertifikat für Google.com, mit dem sich Angreifer als der E-Mail-Dienst und andere Angebote der Website ausgeben konnten. Das gefälschte Zertifikat wurde hergestellt, nachdem Angreifer die Sicherheit des in den Niederlanden ansässigen Unternehmens DigiNotar geknackt und die Kontrolle über dessen Systeme zur Ausstellung von Zertifikaten erlangt hatten.
Die Secure Sockets Layer (SSL)-Zertifikate wurden von einer gültigen Zertifizierungsstelle digital signiert… Tatsächlich handelte es sich bei den Zertifikaten um nicht autorisierte Duplikate, die unter Verstoß gegen die von Browserherstellern und Zertifizierungsstellen aufgestellten Regeln ausgestellt wurden.
Eine betrügerische Ausstellung von Zertifikaten kann vorkommen. Eine betrügerische Zertifizierungsstelle kann eines ausstellen, aber sie wird nicht weit kommen. Das schlechte Zertifikat wird entdeckt. Die betrügerische Zertifizierungsstelle wird die Compliance-Programme nicht erfüllen und aus den Vertrauensspeichern entfernt werden. Ohne Akzeptanz wird die Zertifizierungsstelle ihr Geschäft aufgeben müssen. Certificate Transparency, ein neuerer Standard, ermöglicht eine schnellere Erkennung von betrügerischen Zertifikaten.
Warum sollte eine CA abtrünnig werden? Welchen Vorteil kann der Bösewicht aus einem nicht genehmigten Zertifikat ziehen? Mit dem Zertifikat allein nicht viel, selbst wenn es von einer vertrauenswürdigen Zertifizierungsstelle unterzeichnet wurde. Wenn sich der Bösewicht jedoch mit einem Internetdienstanbieter zusammentun oder anderweitig auf das vom Browser verwendete Netzwerk zugreifen kann, gibt das Zertifikat dem Bösewicht die Möglichkeit, alle Sicherheitsgarantien der PKI zu umgehen.
Der Hacker könnte einen Man-in-the-Middle-Angriff (MITM) auf die Konversation durchführen. Der Angreifer könnte sich zwischen den Browser und die eigentliche Website einschleusen. In diesem Szenario würde der Benutzer direkt mit dem Angreifer sprechen, und der Angreifer würde die Inhalte mit der echten Website hin- und herleiten. Der Angreifer würde dem Browser das gefälschte Zertifikat vorlegen. Da es von einer vertrauenswürdigen Zertifizierungsstelle signiert wurde, würde der Browser es akzeptieren. Der Angreifer konnte die von einer der beiden Parteien gesendeten Daten einsehen und sogar ändern, bevor die andere Seite sie erhielt.
Nun kommen wir zum unheilvollen eIDAS der EU, Artikel 45. Dieser Verordnungsvorschlag sieht vor, dass alle Browser einem Korb von Zertifikaten von durch die EU benannten Zertifizierungsstellen vertrauen müssen. Siebenundzwanzig, um genau zu sein: eines für jedes Mitgliedsland. Diese Zertifikate sollen Qualified Website Authentication Certificates genannt werden. Das Akronym "QWAC" hat einen unglücklichen Beigeschmack von Quacksalberei - oder vielleicht will uns die EU nur auf den Arm nehmen.
Die QWACs würden entweder von Regierungsbehörden oder von dem, was Michael Rectenwald als "governmentalities" bezeichnet, herausgegeben: "Konzerne und Unternehmen und andere Hilfsorgane des Staates, die sonst als ‚privat‘ bezeichnet werden, aber in Wirklichkeit als Staatsapparate fungieren, indem sie staatliche Narrative und Diktate durchsetzen."
Dieses System würde die Regierungen der EU-Mitgliedstaaten einen Schritt näher an den Punkt bringen, an dem sie Man-in-the-Middle-Angriffe gegen ihre eigenen Bürger durchführen könnten. Außerdem müssten sie Zugang zu den Netzen erhalten. Die Regierungen sind in der Lage, das zu tun. Wenn der Internetdienstanbieter ein staatliches Unternehmen ist, dann haben sie ihn bereits. Handelt es sich bei den Internet-Diensteanbietern um Privatunternehmen, dann könnten die lokalen Behörden die Polizeibefugnisse nutzen, um Zugang zu erhalten.
Ein Punkt, der in der öffentlichen Diskussion nicht hervorgehoben wurde, ist, dass ein Browser in einem der 27 EU-Mitgliedsländer verpflichtet wäre, jedes einzelne QWAC zu akzeptieren, eines aus jedem EU-Mitglied. Das bedeutet, dass ein Browser in Spanien beispielsweise einem QWAC von Einrichtungen in Kroatien, Finnland und Österreich vertrauen müsste. Der spanische Nutzer, der eine österreichische Website besucht, müsste über österreichische Teile des Internets gehen. Die oben angesprochenen Probleme würden für alle Länder innerhalb der EU gelten.
The Register erklärt in einem Artikel mit dem Titel Bad eIDAS: Europa ist bereit, Ihre verschlüsselten HTTPS-Verbindungen abzufangen und auszuspionieren eine mögliche Vorgehensweise:
Die Regierung kann ihre befreundete Zertifizierungsstelle um eine Kopie des [QWAC-]Zertifikats bitten, damit sie sich als die Website ausgeben kann - oder sie kann ein anderes Zertifikat anfordern, dem die Browser vertrauen und das sie für die Website akzeptieren. Auf diese Weise kann die Regierung mit Hilfe eines Man-in-the-Middle-Angriffs den verschlüsselten HTTPS-Verkehr zwischen der Website und ihren Nutzern abfangen und entschlüsseln, so dass das Regime jederzeit genau überwachen kann, was die Nutzer auf dieser Website tun.
Nachdem der Schutzschild der Verschlüsselung durchbrochen wurde, könnte die Überwachung darin bestehen, die Passwörter der Nutzer zu speichern und sie dann zu einem anderen Zeitpunkt zu verwenden, um auf die E-Mail-Konten der Bürger zuzugreifen. Neben der Überwachung könnten die Regierungen auch die Inhalte selbst verändern. Zum Beispiel könnten sie die Inhalte, die sie zensieren wollen, entfernen. Sie könnten abweichende Meinungen mit lästigen staatlichen Faktenprüfungen und Inhaltswarnungen versehen.
Beim derzeitigen Stand der Dinge müssen die Zertifizierungsstellen das Vertrauen der Browsergemeinschaft aufrechterhalten. Derzeit warnen die Browser den Nutzer, wenn eine Website ein abgelaufenes oder anderweitig nicht vertrauenswürdiges Zertifikat vorlegt. Nach Artikel 45 wären Warnungen oder der Ausschluss von Vertrauensmissbrauchern untersagt. Die Browser sind nicht nur verpflichtet, den QWACs zu vertrauen, sondern Artikel 45 verbietet es den Browsern, eine Warnung anzuzeigen, dass ein von einem QWAC signiertes Zertifikat vorliegt.
Letzte Chance für eIDAS (eine Website mit dem Mozilla-Logo) setzt sich gegen Artikel 45 ein:
Jeder EU-Mitgliedsstaat hat die Möglichkeit, kryptografische Schlüssel für die Verteilung in Webbrowsern zu bestimmen, und den Browsern ist es untersagt, das Vertrauen in diese Schlüssel ohne staatliche Genehmigung zu widerrufen.
… Es gibt keine unabhängige Kontrolle oder Ausgewogenheit der Entscheidungen, die die Mitgliedsstaaten in Bezug auf die von ihnen genehmigten Schlüssel und deren Verwendung treffen. Dies ist besonders besorgniserregend, wenn man bedenkt, dass die Einhaltung der Rechtsstaatlichkeit nicht in allen Mitgliedsstaaten einheitlich ist und es dokumentierte Fälle von Nötigung durch die Geheimpolizei zu politischen Zwecken gibt.
In einem offenen Brief, der von mehreren hundert Sicherheitsforschern und Informatikern unterzeichnet wurde:
Artikel 45 verbietet auch Sicherheitsprüfungen von EU-Webzertifikaten, es sei denn, sie sind durch die Verordnung ausdrücklich erlaubt, wenn verschlüsselte Internetverbindungen hergestellt werden. Anstatt eine Reihe von Mindestsicherheitsmaßnahmen festzulegen, die als Basis durchgesetzt werden müssen, wird effektiv eine Obergrenze für die Sicherheitsmaßnahmen festgelegt, die ohne Genehmigung des ETSI nicht verbessert werden kann. Dies steht im Widerspruch zu etablierten globalen Normen, bei denen neue Cybersicherheitstechnologien als Reaktion auf schnelllebige technologische Entwicklungen entwickelt und eingesetzt werden.
Die meisten von uns verlassen sich bei der Zusammenstellung der Liste der vertrauenswürdigen Zertifizierungsstellen auf ihre Anbieter. Als Benutzer können Sie jedoch auf Ihren eigenen Geräten nach Belieben Zertifikate hinzufügen oder entfernen. Microsoft Windows verfügt über ein Tool, das dies ermöglicht. Unter Linux sind die Stammzertifikate Dateien, die sich in einem einzigen Verzeichnis befinden. Eine CA kann durch einfaches Löschen der Datei als nicht vertrauenswürdig eingestuft werden. Wird auch dies verboten werden? Steve Gibson, bekannter Sicherheitsexperte, Kolumnist und Gastgeber des seit langem laufenden Podcasts Security Now, stellt diese Frage:
Die EU erklärt jedoch, dass die Browser verpflichtet sind, diese neuen, unbewiesenen und ungetesteten Zertifizierungsstellen und somit alle von ihnen ausgestellten Zertifikate ohne Ausnahme und ohne Regressansprüche anzuerkennen. Bedeutet das, dass mein Firefox rechtlich verpflichtet ist, meinen Versuch, diese Zertifikate zu entfernen, abzulehnen?
Gibson stellt fest, dass einige Unternehmen eine ähnliche Überwachung ihrer Mitarbeiter innerhalb ihres eigenen privaten Netzwerks durchführen. Unabhängig davon, was man von diesen Arbeitsbedingungen hält, gibt es in einigen Branchen legitime Gründe für Prüfungen und die Einhaltung von Vorschriften, um zu verfolgen und aufzuzeichnen, was die Mitarbeiter mit den Unternehmensressourcen machen. Aber, so Gibson weiter,
Das Problem ist, dass sich die EU und ihre Mitgliedstaaten stark von den Angestellten eines privaten Unternehmens unterscheiden. Wenn ein Angestellter nicht ausspioniert werden möchte, kann er sein eigenes Smartphone benutzen, um das Netzwerk seines Arbeitgebers zu umgehen. Und natürlich ist das private Netzwerk eines Arbeitgebers genau das: ein privates Netzwerk. Die EU möchte dies für das gesamte öffentliche Internet tun, aus dem es kein Entrinnen gibt.
Nun haben wir den radikalen Charakter dieses Vorschlags festgestellt. Es ist an der Zeit zu fragen, welche Gründe die Europäische Kommission für diese Änderung anführt. Die EK sagt, dass die Identitätsüberprüfung im Rahmen der PKI nicht ausreichend ist. Und dass diese Änderungen notwendig sind, um sie zu verbessern.
Ist an den Behauptungen der Kommission etwas Wahres dran? Die derzeitige PKI verlangt in den meisten Fällen nur, dass der Antragsteller die Kontrolle über die Website nachweist. Das ist zwar nicht schlecht, garantiert aber nicht, dass beispielsweise die Webadresse "apple.com" dem Unterhaltungselektronikunternehmen Apple Inc. mit Hauptsitz in Cupertino, Kalifornien, gehört. Ein böswilliger Benutzer könnte ein gültiges Zertifikat für eine Domäne erhalten, die dem Namen eines bekannten Unternehmens ähnelt. Das gültige Zertifikat könnte für einen Angriff verwendet werden, der darauf beruht, dass einige Benutzer nicht genau genug hinschauen, um zu bemerken, dass der Name nicht ganz übereinstimmt. Dies ist dem Zahlungsdienstleister Stripe passiert.
Für Herausgeber, die der Welt beweisen möchten, dass es sich wirklich um dasselbe Unternehmen handelt, haben einige Zertifizierungsstellen Extended Validation (EV)-Zertifikate angeboten. Der "erweiterte" Teil besteht aus zusätzlichen Überprüfungen des Unternehmens selbst, wie z. B. der Geschäftsadresse, einer funktionierenden Telefonnummer, einer Geschäftslizenz oder -gründung und anderen Attributen, die typisch für ein bestehendes Unternehmen sind. EVs werden zu einem höheren Preis aufgeführt, da sie mehr Arbeit für die Zertifizierungsstelle erfordern.
Früher zeigten Browser ein hervorgehobenes visuelles Feedback für ein EV an, z. B. eine andere Farbe oder ein robusteres Schlosssymbol. In den letzten Jahren waren EVs auf dem Markt nicht besonders beliebt. Sie sind weitgehend verschwunden. Viele Browser zeigen die unterschiedliche Rückmeldung nicht mehr an.
Trotz der immer noch vorhandenen Schwachstellen hat sich die PKI im Laufe der Zeit deutlich verbessert. Nachdem die Schwachstellen bekannt wurden, wurden sie behoben. Die kryptografischen Algorithmen wurden verstärkt, die Verwaltung wurde verbessert, und Schwachstellen wurden beseitigt. Die Steuerung durch einen Konsens der Branchenakteure hat recht gut funktioniert. Das System wird sich weiter entwickeln, sowohl technologisch als auch institutionell. Abgesehen von der Einmischung der Regulierungsbehörden gibt es keinen Grund, etwas anderes zu erwarten.
Wir haben aus der glanzlosen Geschichte der EVs gelernt, dass der Markt sich nicht so sehr für die Überprüfung der Unternehmensidentität interessiert. Wenn die Internetnutzer dies jedoch wünschen, müsste man die bestehende PKI nicht zerstören, um sie ihnen zu geben. Einige kleine Änderungen an den bestehenden Arbeitsabläufen würden ausreichen. Einige Kommentatoren haben vorgeschlagen, den TLS-Handshake zu ändern; die Website würde ein zusätzliches Zertifikat vorlegen. Das Primärzertifikat würde wie bisher funktionieren. Das Sekundärzertifikat, das von einem QWAC signiert wird, würde die zusätzlichen Identitätsstandards implementieren, die die Europäische Kommission anstrebt.
Die angeblichen Gründe der Europäischen Kommission für eIDAS sind einfach nicht glaubwürdig. Die angegebenen Gründe sind nicht nur unplausibel, die EU-Kommission macht sich auch nicht die Mühe, mit dem üblichen scheinheiligen Gejammer darüber aufzuwarten, dass wir wichtige Freiheiten im Namen der Sicherheit opfern müssen, weil wir mit der ernsten Bedrohung durch [wählen Sie eines aus] Menschenhandel, Kindersicherheit, Geldwäsche, Steuerhinterziehung oder (mein persönlicher Favorit) Klimawandel konfrontiert sind. Es lässt sich nicht leugnen, dass die EU uns in die Irre führt.
Wenn die EU ihre wahren Motive nicht offen legt, was will sie dann? Gibson sieht eine ruchlose Absicht:
Und es gibt nur einen möglichen Grund dafür, dass sie [die Browser dazu zwingen, QWACs zu vertrauen], nämlich das Abhören des Internetverkehrs während des laufenden Betriebs, genau wie es in Unternehmen geschieht. Und das ist bekannt.
(Was Gibson mit "Abhören des Internetverkehrs" meint, ist der oben beschriebene MITM-Angriff.) In anderen Kommentaren wurden die unheilvollen Auswirkungen auf die Redefreiheit und den politischen Protest hervorgehoben. Hurst argumentiert in einem langen Aufsatz mit der Gefahr des Abrutschens:
Wenn eine liberale Demokratie diese Art der Kontrolle über die Technologie im Internet ungeachtet ihrer Folgen einführt, legt sie den Grundstein dafür, dass autoritärere Regierungen ungestraft nachziehen können.
Mozilla zitiert in Techdirt (ohne Link zum Original) sagt mehr oder weniger das Gleiche:
Browser zu zwingen, automatisch staatlich unterstützten Zertifizierungsstellen zu vertrauen, ist eine wichtige Taktik autoritärer Regime, und diese Akteure würden durch die legitimierende Wirkung der EU-Maßnahmen ermutigt werden…
Gibson macht eine ähnliche Beobachtung:
Und dann gibt es da noch das sehr reale Gespenst, welche anderen Türen sich dadurch öffnen: Wenn die EU dem Rest der Welt zeigt, dass sie erfolgreich die Vertrauensbedingungen für die von ihren Bürgern verwendeten unabhängigen Webbrowser diktieren kann, welche anderen Länder werden dann mit ähnlichen Gesetzen folgen? Jetzt kann jeder einfach verlangen, dass die Zertifikate des eigenen Landes hinzugefügt werden. Dies führt uns genau in die falsche Richtung.
Der vorgeschlagene Artikel 45 ist ein Angriff auf die Privatsphäre der Nutzer in den EU-Ländern. Sollte er angenommen werden, wäre dies ein massiver Rückschlag nicht nur für die Sicherheit im Internet, sondern auch für das gewachsene System der Governance. Da stimme ich mit Steve Gibson überein:
Was völlig unklar ist, und was ich nirgendwo gefunden habe, ist eine Erklärung, mit welcher Befugnis die EU glaubt, die Gestaltung der Software anderer Organisationen diktieren zu können. Denn genau darauf läuft es hinaus.
Die Reaktionen auf den vorgeschlagenen Artikel 45 waren massiv negativ. Die EFF schreibt in Artikel 45 wird die Web-Sicherheit um 12 Jahre zurückwerfen: "Dies ist eine Katastrophe für die Privatsphäre aller Internetnutzer, insbesondere aber für diejenigen, die das Internet in der EU nutzen."
Die eIDAS-Bemühungen sind ein vierfaches Alarmfeuer für die Sicherheitsgemeinschaft. Mozilla - Hersteller des Open-Source-Webbrowsers Firefox - hat eine gemeinsame Erklärung der Industrie veröffentlicht, in der sie sich dagegen ausspricht. Die Erklärung ist von einer ganzen Reihe von Internet-Infrastrukturunternehmen unterzeichnet, darunter Mozilla selbst, Cloudflare, Fastly und die Linux Foundation.
Aus dem oben erwähnten offenen Brief:
Nach der Lektüre des fast endgültigen Textes sind wir sehr besorgt über den vorgeschlagenen Text für Artikel 45. Der aktuelle Vorschlag erweitert radikal die Möglichkeiten der Regierungen, sowohl ihre eigenen Bürger als auch Einwohner in der gesamten EU zu überwachen, indem er ihnen die technischen Mittel an die Hand gibt, um den verschlüsselten Internetverkehr abzufangen, und untergräbt die bestehenden Kontrollmechanismen, auf die sich die europäischen Bürger verlassen.
Wohin soll das führen? Die Verordnung wird schon seit einiger Zeit vorgeschlagen. Eine endgültige Entscheidung war für November 2023 vorgesehen. Webrecherchen zeigen, dass es seither keine neuen Informationen zu diesem Thema gibt.
In den letzten Jahren hat die totale Zensur in all ihren Formen zugenommen. Während des Covid-Irrsinns schlossen sich Regierung und Industrie zusammen, um einen zensur-industriellen Komplex zu schaffen, mit dem falsche Darstellungen effizienter verbreitet und Andersdenkende unterdrückt werden können. In den letzten Jahren haben sich Skeptiker und unabhängige Stimmen gewehrt, vor Gericht und durch die Schaffung standpunktneutraler Plattformen.
Obwohl die Zensur der Meinungsäußerung weiterhin eine große Gefahr darstellt, sind die Rechte von Schriftstellern und Journalisten besser geschützt als viele andere Rechte. In den USA schützt der erste Verfassungszusatz ausdrücklich die Redefreiheit und die Freiheit, die Regierung zu kritisieren. Die Gerichte können der Meinung sein, dass alle Rechte oder Freiheiten, die nicht durch eine sehr spezifische gesetzliche Formulierung geschützt sind, Freiwild sind. Dies mag der Grund dafür sein, dass der Widerstand in Bezug auf die Redefreiheit mehr Erfolg hatte als bei anderen Bemühungen, anderen Machtmissbrauch wie Quarantänen und Bevölkerungsabriegelungen Einhalt zu gebieten.
Anstatt eines gut verteidigten Gegners verlagern die Regierungen ihre Angriffe auf andere Ebenen der Internet-Infrastruktur. Diese Dienste, wie z. B. Domainregistrierung, DNS, Zertifikate, Zahlungsabwickler, Hosting und App-Stores, bestehen größtenteils aus privaten Markttransaktionen. Diese Dienste sind weitaus weniger gut geschützt als die Meinungsäußerung, da in den meisten Fällen niemand das Recht hat, einen bestimmten Dienst von einem bestimmten Unternehmen zu erwerben. Und die eher technischen Dienste wie DNS und PKI werden von der Öffentlichkeit weniger gut verstanden als die Veröffentlichung im Internet.
Das PKI-System ist besonders anfällig für Angriffe, weil es auf der Grundlage von Reputation und Konsens funktioniert. Es gibt keine einzelne Behörde, die das gesamte System beherrscht. Die Akteure müssen sich ihren Ruf durch Transparenz, Einhaltung der Vorschriften und ehrliche Meldung von Fehlern verdienen. Und das macht es anfällig für diese Art von störenden Angriffen. Wenn die PKI in der EU an die Regulierungsbehörden fällt, erwarte ich, dass andere Länder folgen werden. Nicht nur die PKI ist in Gefahr. Wenn erst einmal bewiesen ist, dass andere Schichten des Stacks von den Regulierungsbehörden angegriffen werden können, werden sie ebenfalls ins Visier genommen werden.
Quelle: The EU Wants to Spy on Europeans´ Internet Use, https://brownstone.org/articles/the-eu-wants-to-spy-on-europeans-internet-use/
https://uncutnews.ch/die-eu-will-die-internetnutzung-der-europaeer-ausspionieren/
 Free yourself from censorship and propaganda with this simple info-tool: The meaning of RSS-Feeds, uncut-news.ch, 04.09.2024 Free yourself from censorship and propaganda with this simple info-tool: The meaning of RSS-Feeds, uncut-news.ch, 04.09.2024
Dr. Joseph Mercola
*RSS: Rich Site Summary sind Dateiformate für Web-Feeds. Sie zeigen Änderungen auf Websites, z. B. auf News-Seiten, Blogs, Audio-/Video-Logs etc. Das Akronym steht aktuell für Really Simple Syndication; vormals waren bereits andere Bedeutungen gegeben.
Analyse von Dr. Joseph Mercola
Die Geschichte auf einen Blick
Obwohl sie von den Algorithmen der sozialen Medien überschattet werden, sind RSS-Feeds nach wie vor ein leistungsfähiges Instrument, das Ihnen hilft, sich mit Informationen zu versorgen, die von den Mainstream-Medien ignoriert oder absichtlich zensiert werden.
Mit RSS können Sie Ihre eigenen Nachrichtenquellen zusammenstellen und sich so dem Einfluss der Mainstream-Medien entziehen.
Es gibt verschiedene RSS-Feed-Reader, jeder mit seinen eigenen Merkmalen und Funktionen.
Durch die Nutzung von RSS-Feeds können Sie die Kontrolle über Ihre Informationsaufnahme zurückgewinnen und die Themen, die Sie interessieren, nach Priorität ordnen.
Da RSS-Feeds Echtzeit-Updates von den von Ihnen gewählten Quellen liefern, erhalten Sie zeitnahe Informationen, ohne sich auf verzögerte oder gefilterte Berichte von traditionellen Medienkanälen verlassen zu müssen.
In einer Ära, die von Social-Media-Algorithmen und kuratierten Newsfeeds dominiert wird, gerät der bescheidene RSS-Feed oft ins Abseits und wird als Relikt aus der Vergangenheit des Internets abgetan.
Dabei sind RSS-Feeds keineswegs veraltet und irrelevant, sondern nach wie vor eines der leistungsfähigsten Instrumente, um im digitalen Zeitalter auf dem Laufenden zu bleiben. Wahrscheinlich wurden sie absichtlich in den Hintergrund gedrängt, weil sie eine legitime Bedrohung für die Machthaber darstellen, da sie es ermöglichen, die Medienzensur zu umgehen.
RSS (Really Simple Syndication) ermöglicht es Ihnen, Ihre eigenen Nachrichtenquellen zusammenzustellen und Ihre Informationsaufnahme auf Ihre persönlichen Vorlieben abzustimmen. Ich vermute, dass seine mangelnde Popularität nicht auf Ineffizienz zurückzuführen ist, sondern auf die Tatsache, dass RSS eine echte Bedrohung für die Wächter der Informationen darstellt. Daher wird seine Verwendung vom Medienestablishment nicht mehr so gefördert wie früher.
Die Nutzung von RSS-Feeds gibt Ihnen die Möglichkeit, sich von den Zwängen kuratierter Propaganda zu befreien und auf den Wissensschatz zuzugreifen, der jenseits der Zensur liegt.
Quelle: https://articles.mercola.com/sites/articles/archive/2024/04/03/rss-feeds.aspx (english version)
https://uncutnews.ch/befreien-sie-sich-von-zensur-und-propaganda-mit-diesem-einfachen-info-tool-die-bedeutung-von-rss-feeds/

Spend or pay Gooken by PayPal.me :
Spend resp. pay Gooken by Paypal.me: Please click here!
Now you can start...:
 Protect yourself and your data when using Facebook, securityinabox.org, updated 2021 Protect yourself and your data when using Facebook, securityinabox.org, updated 2021
Setup
Know how hard it is to move what you have posted off social media
Test how effective it is to use the "download my data" functions of each platform you use. Start the download process, then take a thorough look at what data it provides. You may find that what is downloaded is not in a format you find easy to use.
Allow some time for this process. If you have had an account for a long time, there will be a lot of data to download, and the service may take a day or so to bundle it for your download.
Download your data
Learn why we recommend this
Decide whether you will use a real or fake name, and maintain separate accounts
Be aware that even if you provide a fake name to a social media site, you may still be identifiable by the network you connect from and the IP address it assigns to your device unless you use a VPN or Tor to hide this information.
Use a VPN when setting up an account for the first time to make it harder for someone to associate your profile with your IP address.
Use VPN or Tor every time you access your account.
Do not use the app on your phone. Connect using a browser instead.
You can access Facebook using their Tor address https://facebookcorewwwi.onion/ if you are using Tor.
Consider using separate accounts or separate identities/pseudonyms for different campaigns and activities. You will likely want to keep your personal and work accounts separate, at the very least.
Remember that the key to using a social network safely is being able to trust people in that network. You and the others in your network will want to know that the people behind the accounts are who they say they are, and have ways to validate this. That does not necessarily mean you have to use your real name, but it may be important to use consistent fake names.
Be aware that Facebook´s "real name" policy gives them the right to remove your account if they believe you are using a name that is not your legal name. Facebook also has a poor track record of recognizing "real" names, particularly when they are not in English.
Learn why we recommend this
Set up with a fresh email address
Set up a new e-mail address while using the Tor Browser or a trusted VPN.
Suggested privacy-friendly mail services:
Proton Mail
If you have a friend who can invite you, Riseup Mail
Autistici
Learn why we recommend this
Don’t associate your phone number with your account
If possible, when setting up a new account, do not enter your phone number. Facebook will allow you to set up a new account with only an email address, and that can be harder to associate with you.
Remove your phone number, or adjust who can see it
Learn why we recommend this
Skip �����find friends”
"Skip" or dismiss Facebook´s requests to "allow access" to contacts on your device, import your contacts, connect with your other social media accounts, or find more connections when you first set up an account. You can select your contacts more carefully afterwards.
Turn off automatic contact uploading
Delete contacts
Consider only connecting to people you know, whom you trust not to misuse the information you post.
If you need to connect to an online community of like-minded individuals whom you have never met, consider carefully what information you will share with these people.
Do not share your employer or educational background, as social media may use this information to share your profile with others unexpectedly.
Learn why we recommend this
Designate someone to manage your account if you are unable to do it yourself
Note that for legal reasons, Facebook will not give a loved one or colleague access to your account. Rather, if you give them permission, they will make it possible to close and "memorialise" your account. If you expect someone else will need to access your account in the event of an emergency, arrange to share your login information with them using encrypted communication or the sharing function of your password manager.
If a colleague has been arrested or detained, contact Access Now´s Helpline or Front Line Defenders for assistance in working with Facebook to secure access to their accounts.
Consider setting up a legacy contact in case of your death
Learn about getting access to the account of someone who is incapacitated
Learn why we recommend this
Account protection
Check recovery email and phone
Check your recovery email
Check your recovery phone number
Change this information immediately if you lose access to your email address or phone number.
Learn why we recommend this
Use strong passwords
Use strong passwords to protect your accounts. Anyone who gets into your social media account gains access to a lot of information about you and anyone you are connected to. See our guide on how to create and maintain secure passwords for more information.
Set up multifactor authentication (2FA)
Use a security key, authenticator app, or security codes for multifactor authentication.
Do not use SMS or a phone call if possible, so you do not have to associate your phone number with your account. This is particularly important if your name is not already associated with your account.
Set up 2FA
Also go through the "How to keep your account secure" checkup, which will check your password and login alerts
Learn why we recommend this
Get a verification code to get back into your account
Get recovery codes
Store those codes in your password manager.
Alternately, print these codes out before you are in a situation where you might need them. Keep them somewhere safe and hidden, like your wallet or a locked safe.
Learn why we recommend this
Compare emails you may have received about security to those the app or service says it sent you
Learn more here
Look for official Facebook messages here
Learn why we recommend this
Look for suspicious access
Check active sessions and authorized devices, review account activity and security events
Look at the following pages listing which devices have recently logged in to your account (including using browsers or apps). Does every login look familiar?
Look for "Where you´re logged in"
Look for "authorized logins"
Follow these instructions on how to log out devices that are not yours.
Note that if you are using a VPN or Tor Browser, which can conceal your location, you may see your own device, connected in unexpected locations.
If you see suspicious activity on your account, immediately change your password to a new, long, random passphrase you do not use for any other accounts. Save this in your password manager.
Learn why we recommend this
Get notified about logins
Set notifications to be sent to the email address you associated with this account.
Avoid using your phone number for notifications (see "avoid associating your phone number with accounts," above).
Follow these steps
or see "Setting up extra security" > "Get alerts about unrecognized logins"
Learn why we recommend this
If your account has been lost, stolen, or hacked
Take these actions on this page
Or use this step-by-step walkthrough
Review other sites and apps that can access your account
Avoid using your accounts to log in to other sites (like news sites, etc.) It is convenient, but that means it is convenient for attackers as well as for you, and may also leave more evidence of what you have viewed online. Use a different password for every site, and save it in your password manager.
Be careful when connecting your social network accounts. You may be anonymous on one site, but exposed when using another.
Review apps here
Also review Advanced > "Recover external accounts" here to see whether you recognize the other accounts you have used Facebook to log into
Check and change the passwords used by these apps
Learn why we recommend this
Download data for further analysis (advanced)
Suggestions of what to look for
Instructions
Download here
Learn why we recommend this
Decide what to post
The more information about yourself you reveal online, the easier it becomes for the authorities and others to identify you and monitor your activities. For example, if you share (or "like") a page that opposes some position taken by your government, agents of that government might very well take an interest and target you for additional surveillance or direct persecution. This can have consequences even for those not living under authoritarian regimes: the families of some activists who have left their home countries have been targeted by the authorities in their homelands because of things those activists have posted on social media.
Information that should never be sent on social media, even via direct message (DM)
Passwords
Personally identifying information, including
your birthday
your phone number (does it appear in screenshots of communications?)
government or other ID numbers
medical records
education and employment history (these can be used by untrustworthy people who want to gain your confidence)
Information that you might not want to post on social media, depending on your assessment of the threats in your region:
Your email address (at least consider having more- and less-sensitive accounts)
Details about family members
Your sexual orientation or activity
Even if you trust the people in your networks, remember it is easy for someone to copy your information and spread it more widely than you want it to be.
Agree with your network on what you do and do not want shared, for safety reasons.
Think about what you may be revealing about your friends that they may not want other people to know; be sensitive about this, and ask them to be sensitive about what they reveal about you.
Don’t share location
Turn off location
Learn why we recommend this
Share photos and videos more safely
Consider what is visible in photos you post. Never post images that include
your vehicle license plates
IDs, credit cards, or financial information
Photographs of keys (it is possible to duplicate a key from a photo)
Think hard before you post pictures that include or make it possible to identify
your friends, colleagues, and loved ones (ask permission before posting)
your home, your office, or other locations where you often spend time
if you are hiding your location, other identifiable locations in the background (buildings, trees, natural landscape features, etc.)
Facebook performs automatic face recognition on photos. Set this to "off."
Delete albums or photos
Remove EXIF data before you post photos
Learn why we recommend this
Change who can see when you "like" things
Change "Who can see your social interactions alongside ads" here to "only me"
Learn why we recommend this
Don´t share your birthday
It is always possible to give a birthday that is not your own. However, do keep track of what you enter, in case you need it to regain access to your account.
Limit the audience for viewing your birthday
Learn why we recommend this
Decide who can see
Share to select people
Go through the "Who can see what you share" walkthrough here. Set everything under "Profile information" to "Only me." Set limits you think are reasonable on subsequent screens. Consider "Limit past posts" to make it harder for others to see things you posted some time ago.
Look at the section "Your Activity," here
Limit who can see what Facebook apps you use
Manage who can reply to what you post
Turn comments off on your page
Stop people from posting to your page
You can also set it so you review posts before you make them visible (this means you have to do more work)
Learn why we recommend this
Think about group membership and who you connect with
Control who can "friend" or "follow" you
review this article as well
Check whether groups you are in are public or private. Public groups can be seen by anyone, and can be found via search.
Be aware that third parties can create apps that have access to groups; learn how to see if they do
How to leave a group (note that if the group was public, information about your past membership may still be online)
Remove or block someone from a group you manage
Delete posts or comments from a group you manage
Learn why we recommend this
Review tags/disallow tags
Instructions are here
Set this to "only me"
Learn why we recommend this
Limit who can contact you
Go through the "How people can find you on Facebook" walkthrough here
Limit "Who can send you friend requests?" to "Friends of friends"
Set "Choose who can look you up by your phone number and email address." to something more limited than "Everyone" (Consider that "friends of friends" may still make it possible for malicious people to sneak into your network)
In the last step, consider whether you want people to be able to find your Facebook profile using search engines like Google
Learn why we recommend this
Manage advertising
Look for "manage your off-facebook activity" > "clear history" and > "Manage future activity"
Set "Ads shown off Facebook" to "Not allowed"
In "Categories used to reach you", make sure all switches are set to "off" and remove individual "interest categories" and "other categories"
Make sure switches in "Data about your activity from partners" is off
Learn why we recommend this
Learn what social media will turn over to governments or law enforcement
Search for "Facebook" and the name of your country or jurisdiction on Lumen
Look for "How we respond to legal requests" here
Learn why we recommend this
Leave no trace
Precautions when using a public or shared device
Avoid accessing your social network account from shared devices (like an internet cafe or other people´s devices).
Delete your password and browsing history when you use a web browser on a public machine. Change the passwords of any accounts you accessed from shared devices as soon as you can, using your own device.
Delete search history
Clear searches from your activity log
Clear history of your off-Facebook activity
Learn why we recommend this
Handle abuse
Report abuse
Overview about reporting
Reporting inappropriate or abusive content
Learn why we recommend this
Report harassment that reveals information about you
Learn about reporting harassment
Learn why we recommend this
Identify and report coordinated inauthentic activity (botnets and spam)
Report spam
Learn why we recommend this
Report impersonation
How to report impersonation
Learn why we recommend this
Hide stressful content
Block or unfriend people by taking these actions
Learn why we recommend this
Learn how to recover your account if it is disabled or suspended
Learn about disabled accounts
Report that your account has been disabled
Learn why we recommend this
Take a break from your account
Temporarily suspend your account
Learn why we recommend this
Learn how social media use your information
For a useful add-on which clarifies the Terms of Service of many popular sites, see Terms of Service; Didn´t Read.
Learn about Facebook´s privacy policy
https://securityinabox.org/en/tools/facebook/
Monopol power Google: Why Google shut get scuppered, netzpolitik.org, 09.09.2024
Nach einem historischen Urteil im August beginnt heute in den USA ein weiteres Monopolverfahren gegen Google.In einem Gastbeitrag erklärt der Monopolexperte Ulrich Müller, was auf Google zukommen könnte - und warum auch Europa mehr Entflechtung wagen sollte.
https://netzpolitik.org/2024/monopolmacht-warum-google-jetzt-zerschlagen-werden-sollte/
 German trail lowers lever Tor-anonymization, epochtimes.de, 09.18.2024 German trail lowers lever Tor-anonymization, epochtimes.de, 09.18.2024
Deutsche Ermittlungsbehörden können offenbar das Tor-Netzwerk überwachen - und die Anonymität der Nutzer aufhebeln. Durch die zeitliche Zuordnung, eine "Timing-Analyse" einzelner Datenpakete, lassen sich anonymisierte Verbindungen zum Tor-Nutzer zurückverfolgen.
Tor ist das weltweit größte Netzwerk, um sich anonym im Internet zu bewegen. Tor-Nutzer leiten ihre Verbindung über Server, sogenannte Tor-Knotenpunkte, um zu verschleiern, was sie tun. Mit dme Tor-Browser können sie Websites im Internet anonym oder Seiten im sogenannten Darknet aufrufen.
https://www.epochtimes.de/politik/deutschland/deutsche-strafverfolger-hebeln-tor-anonymisierung-aus-a4871021.html
 ExpressVPN, CyberGhost, Private Internet Access, ZenMate, Intego Antivirus and a lot of tech-websites ExpressVPN, CyberGhost, Private Internet Access, ZenMate, Intego Antivirus and a lot of tech-websites
Exposed:: How Israeli spy do control your VPN, uncut-news.ch, 09.18.2024
Alan Macleod via Mintpressnews
Schätzungsweise 1,6 Milliarden Menschen verlassen sich auf VPNs, um die sensibelsten Aufgaben online zu erledigen, von der Betrachtung illegaler Videos bis hin zu sexuellen oder politischen Aktivitäten. Aber nur wenige Menschen wissen, dass ein beträchtlicher Teil dieses Marktes - darunter drei der sechs beliebtesten VPNs - stillschweigend von einem Unternehmen in israelischem Besitz betrieben wird, das enge Verbindungen zum nationalen Sicherheitsstaat dieses Landes unterhält, darunter die Eliteeinheiten Unit 8200 und Duvdevan der israelischen Streitkräfte (IDF).
Frühere Untersuchungen von MintPress News zur wachsenden Kontrolle Israels über die Technologiebranche haben gezeigt, dass diese Einheiten an vielen der empörendsten Hacking-, Überwachungs- und Attentatsprogramme Israels beteiligt waren und als Spione und Todesschwadronen fungierten. Die Einheit 8200 beispielsweise war die Quelle vieler der berüchtigtsten Spionagesoftwares der Welt, darunter Cellebrite und Pegasus, das Programm, das zur Bespitzelung von Zehntausenden der weltweit führenden Politiker und Journalisten eingesetzt wurde, unter anderem von Saudi-Arabien, das es zur Aufspürung und Ermordung des Kolumnisten der Washington Post, Jamal Khashoggi, nutzte.
Vor diesem Hintergrund ist die berechtigte Befürchtung angebracht, dass die Kontrolle über ein riesiges VPN-Imperium den Einfluss Israels auf die Welt der Online-Informationen und -Sicherheit noch verstärken und dem israelischen Geheimdienst Hintertüren öffnen könnte, um eine groß angelegte kompromat-Operation gegen Nutzer auf der ganzen Welt durchzuführen.
Diese Untersuchung ist Teil einer Reihe, die die Macht der wachsenden israelischen Technologiebranche, auf die Daten von Menschen zuzugreifen und sie zu kontrollieren, hervorhebt und detailliert beschreibt.
Ein Unternehmen wie kein anderes
Kape Technologies ist ein wichtiger Akteur in der Welt des Online-Datenschutzes, einer der drei Giganten, die gemeinsam den Markt kontrollieren. Das Unternehmen besitzt viele der weltweit führenden VPNs, darunter ExpressVPN, CyberGhost, Private Internet Access, ZenMate, Intego Antivirus und eine Vielzahl von Tech-Websites, die für seine Produkte werben. Die Marken von Kape treten als Sponsoren einer Vielzahl von Personen des öffentlichen Lebens auf, darunter Tucker Carlson, Angry Video Game Nerd, Drew Gooden, Lex Fridman, Cody Ko, Uncle Roger und Ben Shapiro.
"Wir leben in einer Ära der Tyrannei", sagt Shapiro in einem Video, in dem er das Unternehmen unterstützt, und fügt hinzu:
Quelle: https://www.mintpressnews.com/exposed-how-israeli-spies-control-your-vpn/288259/
https://uncutnews.ch/enttarnt-wie-israelische-spione-ihr-vpn-kontrollieren/
 G DATA Index G DATA Index
Deutsche unterschätzen die Gefahr von Cyberangriffen zunehmend. Trotz der steigenden Zahl von Cyberattacken weltweit und in Deutschland fühlen sich die Menschen immer weniger bedroht. Dieses wachsende Sicherheitsgefühl steht in krassem Gegensatz zur tatsächlichen Bedrohungslage., trojaner-info.de, 01.12.2024
https://www.trojaner-info.de/daten-sichern-verschluesseln/aktuelles/zusammenfassung-des-g-data-index.html
 Software, insbesonders Firmen- und Bankensoftware, lässt sich immer besser debuggen und selbst bei Open Source im Code beliebig verändern (manipulieren/korrumpieren), lenken und konfigurieren. Nur frei Hand oder von Intrusion-Detection-Systemen (IDS) vorgenommene Prüfsummen-Checks und direkte Einsicht in die Quelltexte stellen solche Veränderungen wirklich fest., Anm., Gooken, die Red., 05.04.2024 Software, insbesonders Firmen- und Bankensoftware, lässt sich immer besser debuggen und selbst bei Open Source im Code beliebig verändern (manipulieren/korrumpieren), lenken und konfigurieren. Nur frei Hand oder von Intrusion-Detection-Systemen (IDS) vorgenommene Prüfsummen-Checks und direkte Einsicht in die Quelltexte stellen solche Veränderungen wirklich fest., Anm., Gooken, die Red., 05.04.2024
Auch haben bekanntlich, wenns ums Geld geht, manche so viel Geld, dass.
 Linux-Software xz - xz command is a program for compressing files Linux-Software xz - xz command is a program for compressing files
.
XZ Utils are an attempt to make LZMA compression easy to use on free (as in freedom) operating systems. This is achieved by providing tools and libraries which are similar to use than the equivalents of the most popular existing compression algorithms. LZMA is a general purpose compression algorithm designed by Igor Pavlov as part of 7-Zip. It provides high compression ratio while keeping the decompression speed fast.
Average compression ratio of LZMA is about 30% better than that of
gzip, and 15% better than that of bzip2.
Decompression speed is only little slower than that of gzip, being two to five times faster than bzip2.
(S+) Hintertür in xz: Knapp am Computer-GAU vorbei, SPIEGEL.de, 04.04.2024
Auf der Gefahrenskala erreicht die Sicherheitslücke zehn von zehn Punkten. Durch Zufall hat ein Computerexperte eine außergewohnliche Schadsoftware gefunden. Der oder die Täter steckten jahrelang Arbeit in die Operation...
https://www.spiegel.de/netzwelt/hintertuer-in-xz-knapp-am-computer-gau-vorbei-a-32ea6693-7ff7-4825-8dcb-b2ddfe8c30c?sara_ref=re-so-app-sh
Lesermeinung Gooken
... Zeitungsente?
Wir können in den zugehörigen rpm-Paketen von https://fr2.rpmfind.net nix finden (Changelog, Fehlverhalten, Updates, ... Source Code?, ...). Doch Pardon:
Nach XZ-Backdoor: Open-Source-Software als Risiko oder strategischer Vorteil?, heise.de, 20.04.2024
Ist öffentlich entwickelte Open Source Software besonders anfällig für Social-Engineering-Angriffe oder bietet gerade sie eher strukturelle Resilienz dagegen?
[...] Mit der Änderung der Projekt-Webseite auf eine bei GitHub gehostete Site im Februar 2024 und dem darauffolgenden Erstellen von Releases der xzUtils war das Ziel erreicht: Alle Prozesse des Projekts waren nun auch in der Hand von Jian Tan und es war inzwischen auch üblich, dass er diese Tätigkeiten durchführte. So konnte er im März 2024 die offiziellen Sourcecode-Releases der Versionen 5.6.0 und 5.6.1 der XZ Utils eigenständig als "Tarballs" (.tar.gz-Archive) veröffentlichen.
Zusammenfassung der Ereignisse
Auf den ersten Blick erscheinen die Beiträge von Jia Tan in den dreieinhalb Jahren von Oktober 2021 bis März 2024 weitgehend positiv: konstruktive E-Mails sowie zahlreiche Patches beziehungsweise Pull Requests, die augenscheinlich echte Probleme lösen. Im Nachhinein lässt sich dagegen nachvollziehen, dass er systematisch und schrittweise angefangen hat, soziale Nähe zu erzeugen und dann die Grundlagen für eine technisch komplexe Schadfunktion in kleinen Häppchen unter zahlreichen Codebeiträgen versteckt in die XZ Utils eingebracht hat. Die beim "OSS Fuzz"-Projekt eingereichte Änderung hat dafür gesorgt, dass das Projekt den Schadcode nicht entdeckt hat.
Schließlich hat der Angreifer über eine "Verbesserung" von Testdateien den Code der eigentlichen Schadfunktion extrem gut versteckt in komprimierter und chiffrierter Form eingebracht. Er landete in Dateien der XZ Utils, in denen niemand nach bösartigem Code suchen würde, da es sich augenscheinlich um reine Datendateien zum Testen der XZ Utils auf korrektes Funktionieren handelt, versteckt in einer Form, in der weder manuelle Code-Reviews noch maschinelle Codescans den Schadcode identifizieren können.
Darüber hinaus wurde die Schadfunktion nur erstellt, wenn man die XZ Utils aus den Release-Tarballs kompilierte, nicht jedoch, wenn man den Sourcecode direkt dem GitHub-Repository entnahm. Der eigentliche Clou ist aber, dass die Schadfunktion eine Hintertür in OpenSSH öffnet, wenn diese mit XZ-Unterstützung kompiliert wurde, und dann auch nur auf x86-64 Rechnern unter Linux mit systemd. Dies sind genau einzuhaltende Rahmenbedingungen, die aber für die meisten Linux-Distributionen auf Rechnern mit CPUs von Intel oder AMD gegeben sind. Des Weiteren ist diese Hintertür nur mit Kenntnis eines bestimmten, geheimen Schlüssels nutzbar.
In der Summe hat der Angreifer also über dreieinhalb Jahre hinweg viel Energie und Hirnschmalz investiert, um in einem etwas aus der Mode gekommenen und daher inzwischen wenig beachteten Datenkompressor möglichst unauffällig eine Schadfunktion einzubringen, die eine Hintertür in der meistgenutzten Fernzugriffssoftware auf fast allen x86-64 Rechnern unter Linux öffnet, die aber nur Personen mit Kenntnis eines bestimmten kryptografischen Schlüssels nutzen können.
https://www.heise.de/hintergrund/Nach-XZ-Backdoor-Open-Source-Software-als-Risiko-oder-strategischer-Vorteil-9692061.html
 Linux Linux
Kritische Sicherheitslücken in CUPS bedrohen Millionen von Geräten, trojaner-info.de, 01.12.2024
Eine neue Sicherheitslücke in CUPS, dem Common Unix Printing System, stellt eine erhebliche Gefahr für Millionen von Linux-Systemen dar. Die Schwachstelle, entdeckt von Simone Margaritelli, ermöglicht es Angreifern, beliebigen Code auf betroffenen Geräten auszuführen.
https://www.trojaner-info.de/sicher-anonym-im-internet/aktuelles/kritische-sicherheitsluecken-in-cups-bedrohen-millionen-von-geraeten.html
Microsoft boasts of having developed ´entirely new state of matter´; will kick-start quantum computing, uncut-news.ch, 02.25.2025
Leo Hohmann
Wissenschaft/ Neue Technologien/Künstliche Intelligenz(KI)/Energie/ Transhumanismus
Bevor sich die Menschheit 2.0 voll entfalten kann, muss mit Hilfe einer extrem leistungsfähigen KI der Nagel in den Sarg der Menschheit 1.0 geschlagen werden.
Microsoft enthüllt neuen Materiezustand – Revolution für die Computerbranche?
[...] Der dystopische Schatten der Technologie
Während Microsoft von einer technologischen Revolution spricht, warnen Kritiker vor den möglichen Konsequenzen. Diese Technologie könnte das globale Überwachungssystem auf ein völlig neues Niveau heben.
Quantencomputer könnten bestehende Verschlüsselungssysteme in kürzester Zeit knacken – und damit die Privatsphäre endgültig eliminieren. Regierungen und Großkonzerne hätten uneingeschränkten Zugriff auf alle Daten, wodurch totale Kontrolle über das Verhalten der Menschen möglich werde.
Dies entspräche exakt der Vision von Larry Ellison, dem Oracle-Gründer, der mit Trumps Regierung am sogenannten Stargate-Projekt arbeitet. Ziel sei der Aufbau gigantischer Datenerfassungszentren in den USA, um sämtliche gesammelten Informationen einer omnipräsenten, alles dominierenden KI zuzuführen.
Ellison selbst erklärte, dass Menschen sich "besser benehmen" würden, wenn sie wüssten, dass sie rund um die Uhr überwacht werden. Doch wenn dieses System Realität werde, warnt er, würden Menschen letztlich bedeutungslos – nur noch dazu da, Maschinen zu dienen, während diese wiederum dem "Bestiensystem" unterworfen seien.
Quelle: Microsoft boasts of having developed ´entirely new state of matter´; will kick-start quantum computing, https://leohohmann.substack.com/p/microsoft-boasts-of-having-developed
https://uncutnews.ch/microsoft-enthuellt-neuen-materiezustand-revolution-fuer-die-computerbranche/
 Was your data leaked? How to find out, what to do about it, and howto prevent it, uncut-news.ch, 02.25.2025 Was your data leaked? How to find out, what to do about it, and howto prevent it, uncut-news.ch, 02.25.2025
reclaimthenet
Datenlecks sind heute erschreckend häufig. Selbst vorsichtige Nutzer können betroffen sein. Falls Sie eine Mitteilung erhalten haben, dass Ihre persönlichen Daten kompromittiert wurden, sollten Sie ruhig bleiben, die Situation bewerten und sofort Schutzmaßnahmen ergreifen.
Wenn ein Unternehmen von einem Datenleck betroffen ist, veröffentlicht es oft eine Erklärung darüber, welche Informationen gehackt wurden. Diese Mitteilungen können jedoch unvollständig oder verzögert sein. Daher sollten Sie die Angaben aus mehreren Quellen überprüfen:
Offizielle E-Mails: Falls Sie betroffen sind, erhalten Sie möglicherweise eine Benachrichtigung vom Unternehmen. Lesen Sie sie sorgfältig und prüfen Sie, welche Daten kompromittiert wurden.
Unternehmenswebsite: Viele Firmen veröffentlichen Sicherheitsmeldungen oder Blogbeiträge zu Datenlecks.
Nachrichtenquellen: Journalisten decken oft zusätzliche Details auf, die Unternehmen nicht sofort preisgeben.
Regulierungsbehörden: In einigen Ländern müssen Firmen Datenlecks melden, z. B. an die US-FTC oder die europäischen Datenschutzbehörden (GDPR).
2. Liste der kompromittierten Informationen erstellen
Nachdem Sie sich informiert haben, sollten Sie Ihre betroffenen Daten kategorisieren.
Wichtige Kategorien:
Bestätigt geleakte Daten - Informationen, die in den offiziellen Meldungen genannt wurden.
Möglicherweise betroffene Daten - Informationen, die nicht erwähnt, aber wahrscheinlich betroffen sind.
Datenart Risikoniveau Missbrauchsmöglichkeiten
E-Mail-Adresse Mittel Phishing, Spam, Identitätsdiebstahl
Telefonnummer Hoch SMS-Phishing, SIM-Swap-Angriffe
Passwörter Hoch Kontoübernahmen, Identitätsdiebstahl
Kreditkartendaten Hoch Betrug, finanzielle Verluste
Sozialversicherungsnummer Kritisch Identitätsdiebstahl, Finanzbetrug
Adresse Mittel Identitätsdiebstahl, gezielte Betrugsversuche
Geburtsdatum Mittel Sicherheitsfragen erraten, Identitätsmissbrauch
Sicherheitsfragen Hoch Kontoübernahmen
Beispiel: Falls Ticketmaster ein Datenleck bestätigt, das Namen, E-Mail-Adressen, Rechnungsadressen und Kreditkartendaten umfasst, könnten Ihre Passwörter oder Sicherheitsfragen ebenfalls betroffen sein.
3. Prüfen, ob Ihre Daten in früheren Lecks aufgetaucht sind
Datenlecks bleiben oft monatelang unbemerkt. Es gibt Tools, mit denen Sie prüfen können, ob Ihre Daten bereits früher kompromittiert wurden:
Have I Been Pwned (HIBP): Zeigt an, ob Ihre E-Mail-Adresse oder Telefonnummer in Datenlecks enthalten ist.
Breach-Benachrichtigungen aktivieren: Dienste wie HIBP oder Passwort-Manager (z. B. Proton Pass) warnen Sie bei neuen Leaks.
Dark-Web-Überwachung: Einige Sicherheitstools wie Experian Dark Web Scan oder Norton LifeLock prüfen, ob Ihre Daten verkauft werden.
4. Maßnahmen zur Sicherung Ihrer Konten
Falls Ihre Daten betroffen sind, sollten Sie sofort Ihre Online-Sicherheit verbessern.
Passwörter aktualisieren
Länge und Komplexität: Mindestens 16 Zeichen, Groß- und Kleinbuchstaben, Zahlen, Symbole.
Kein Wiederverwenden von Passwörtern: Falls ein Passwort kompromittiert wurde, sollte es nicht für mehrere Konten genutzt werden.
Passwort-Manager nutzen: Tools wie Bitwarden oder 1Password erstellen und speichern starke Passwörter sicher.
Multi-Faktor-Authentifizierung (MFA) aktivieren
Erhöhen Sie die Sicherheit Ihrer Konten durch Zwei-Faktor-Authentifizierung (2FA). Die sichersten Methoden sind:
Hardware-Sicherheitsschlüssel (z. B. YubiKey)
Authentifikator-Apps (z. B. Google Authenticator, Authy)
Biometrische Identifikation (Fingerabdruck, Face ID)
SMS-basierte 2FA ist unsicher! SIM-Swap-Betrüger können Ihre Telefonnummer übernehmen.
E-Mail-Sicherheit verbessern
Falls Ihr E-Mail-Konto betroffen ist, sollten Sie:
Ihr Passwort ändern
MFA aktivieren
Verdächtige Aktivitäten überwachen
Sicherheitsfragen anpassen oder entfernen
E-Mail-Alias-Dienste wie Proton Pass nutzen
5. Finanzielle Schutzmaßnahmen ergreifen
Falls Ihre Kreditkartendaten oder Bankinformationen geleakt wurden:
Karte sperren oder neu ausstellen lassen
Betrugstransaktionen melden
Bankbenachrichtigungen aktivieren für verdächtige Aktivitäten
Virtuelle Kreditkarten verwenden (z. B. Privacy.com oder Revolut)
Regelmäßige Kontoauszüge prüfen
Kreditüberwachung aktivieren (z. B. Experian Credit Lock)
Falls Ihre Sozialversicherungsnummer betroffen ist, sollten Sie zusätzlich eine Kreditfrost-Sperre bei Equifax, Experian und TransUnion einrichten.
6. Schutz Ihrer Telefonnummer
SIM-Swap-Angriffe ermöglichen Hackern, Ihre Telefonnummer zu übernehmen und Passwörter zurückzusetzen. Schützen Sie sich, indem Sie:
Eine PIN oder ein Passwort bei Ihrem Mobilfunkanbieter einrichten
"Port Lock" aktivieren, falls verfügbar
Ihre Nummer nicht unnötig in Online-Formularen angeben
Virtuelle Nummern für Online-Dienste nutzen (z. B. Hushed, Google Voice)
7. Adresse schützen und Betrug vermeiden
Falls Ihre Adresse geleakt wurde, können Betrüger Identitätsdiebstahl begehen oder unerwünschte Post und Besuche provozieren.
Löschen Sie Ihre Adresse von Datenbroker-Websites (z. B. Whitepages, Spokeo).
Nutzen Sie eine private Mailbox (UPS Store, virtuelle Briefkästen).
Verbessern Sie Ihre Haussicherheit (Überwachungskameras, Alarmanlagen).
Vermeiden Sie unnötiges Speichern Ihrer Adresse bei Online-Shops.
Fazit: Langfristige Sicherheit durch gute Gewohnheiten
Der Schutz persönlicher Daten ist keine einmalige Maßnahme, sondern ein fortlaufender Prozess. Hacker entwickeln ständig neue Taktiken, daher sollten Sie wachsam bleiben und regelmäßig:
Passwörter aktualisieren und einen Passwort-Manager nutzen
Multi-Faktor-Authentifizierung (MFA) aktivieren
Bank- und Kreditkartentransaktionen überwachen
Virtuelle Karten für Online-Zahlungen verwenden
Verdächtige Aktivitäten auf Dark-Web-Monitoring-Diensten prüfen
Während niemand Datenlecks komplett verhindern kann, senken proaktive Maßnahmen das Risiko erheblich. Sicherheit beginnt mit Aufmerksamkeit - schützen Sie Ihre digitalen Identitäten!
Quelle: Was Your Data Leaked? How to Find Out, What To Do About it, and How to Prevent It, https://reclaimthenet.org/data-breach-guide
https://uncutnews.ch/wurde-ihre-daten-geleakt-so-finden-sie-es-heraus-und-schuetzen-sich-davor/
Lesermeinung Gooken
Ist uns auch mal passiert (Gesundheitsdaten/SAP-Mann Christian Reimann). Gleich drei Richter verwiesen uns auf das Ding der nahezuen Unmöglichkeit: Alles gehört genau nachgewiesen. Die Beweislast trägt man selbst.
 "Big Brother made in Germany" "Big Brother made in Germany"
Utiq: Tracking jetzt auch am Internetanschluss zu Hause, netzpolitik.org, 30.06.2025
Aus vielen Tracking-Firmen sticht eine heraus: Utiq. Das Unternehmen arbeitet mit Internetzugangsanbietern zusammen. Damit kann Utiq Internetanschlüsse auf eine besondere Art verfolgen. Anfangs war die Technologie auf Mobilfunk beschränkt, doch mittlerweile trackt Utiq auch Festnetzanschlüsse.
Gegenüber Internetnutzern spricht Utiq von seiner "sozialen Verantwortung, die Daten der Menschen zu schützen und ihre Privatsphäre zu erhalten". An mögliche Kunden gerichtet wirbt die Tracking-Firma dagegen damit, auch "Zielgruppen in schwer zu trackenden Umgebungen zu erreichen, ohne auf 3rd-Party-Cookies zu setzen". Immer mehr Internetnutzer blockieren die kleinen Dateien zum Tracking von Drittanbietern, die Anbieterfirma von Utiq positioniert sich als Alternative.
Das Unternehmen Utiq gibt es seit etwa zwei Jahren - ursprünglich war die Trackingtechnologie für Mobilfunkanschlüsse vorgesehen. Die Bundesbeauftragte für den Datenschutz und die Informationsfreiheit (BfDI) sieht das Verfahren "zwiespältig". Den Internetanbietern - ohne deren Zusammenarbeit Utiq nicht funktionieren würde - komme ein besondere Vertrauensstellung zu. Dies sei mit dem Utiq-Tracking nur schwer vereinbar. Doch neben Mobilfunkanschlüssen trackt Utiq mittlerweile auch Breitband-Festnetzanschlüsse der Deutschen Telekom. Das zeigt eine Liste von teilnehmenden Telekommunikationsanbietern, die Utiq im Netz veröffentlicht.
Das Unternehmen Utiq gibt es seit etwa zwei Jahren - ursprünglich war die Trackingtechnologie für Mobilfunkanschlüsse vorgesehen. Die Bundesbeauftragte für den Datenschutz und die Informationsfreiheit (BfDI) sieht das Verfahren "zwiespältig". Den Internetanbietern - ohne deren Zusammenarbeit Utiq nicht funktionieren würde - komme ein besondere Vertrauensstellung zu. Dies sei mit dem Utiq-Tracking nur schwer vereinbar. Doch neben Mobilfunkanschlüssen trackt Utiq mittlerweile auch Breitband-Festnetzanschlüsse der Deutschen Telekom. Das zeigt eine Liste von teilnehmenden Telekommunikationsanbietern, die Utiq im Netz veröffentlicht.
Der digitalpolitische Verein D64 veröffentlichte letztes Jahr eine Recherche zu der Trackingtechnologie, die der Verein mit "Big Brother made in Germany" betitelt hat. Gegenüber netzpolitik.org erneuert D64 diese Kritik: "Ausleitung von Informationen der Telekommunikationsunternehmen zu Werbezwecken sehen wir nach wie vor kritisch."
Grundsätzlich lehne D64 jegliches Tracking zu Werbezwecken ab.
Was ist an Utiq besonders?
Utiq arbeitet mit Internetanbietern zusammen. Deshalb kann das Unternehmen Surfverhalten über den Internetanschluss wiedererkennen, selbst nachdem Nutzer Cookies gelöscht, den Browser gewechselt oder gar ein neues Gerät genutzt haben. Mehrere Geräte in einem WLAN kann Utiq jedoch nicht auseinanderhalten.
Für die Nachverfolgung erhält die Firma von den teilnehmenden Anbietern keine persönlichen Daten wie die Mobilfunknummer oder Vertragsnummer, sondern eine einzigartige, pseudonyme Kennung.
Mehr dazu: News&Links#Nachtraege#Online-Exkurs und
https://netzpolitik.org/2025/utiq-tracking-jetzt-auch-am-internetanschluss-zu-hause/
 Der Plan der EU, private Nachrichten zu verbieten, könnte globale Auswirkungen haben (und: was man dagegen tun kann), uncut-news.ch, 18.07.2025 Der Plan der EU, private Nachrichten zu verbieten, könnte globale Auswirkungen haben (und: was man dagegen tun kann), uncut-news.ch, 18.07.2025
Christina Maas, reclaimthenet
Es ist immer ein interessanter Moment, wenn eine Regierung ankündigt, sie wolle Ihre Privatsphäre schützen, indem sie neue Wege findet, sie zu zerstören. Das ist der Drahtseilakt, der derzeit in Brüssel stattfindet, wo EU-Beamte einen Fahrplan vorgestellt haben, der sich wie eine Blaupause dafür liest, digitale Schlösser in dekorative Vorschläge zu verwandeln.
Der Plan, der Teil der Agenda der Kommission mit dem aufmunternden Titel ProtectEU ist, verspricht, der Polizei bis zum Ende des Jahrzehnts die nötigen Werkzeuge an die Hand zu geben, um Ihre private Kommunikation zu entschlüsseln - natürlich legal. Nichts steht so sehr für moderne europäische Werte wie grenzenlose Überwachung und kontinentweite Datenabhörung.
Die Show begann offiziell am 24. Juni, als die Kommission die Bühne mit einem Dokument betrat, das vorgibt, ein Problem zu lösen, sich aber eher wie eine Wunschliste der Abteilung "Wir hassen Verschlüsselung" von Europol liest.
Es handelt sich um ein sechsstufiges staatlich gefördertes Vorhaben, um alles aufzubrechen, von dem Sie dachten, dass es fest verschlossen sei. Und es hat einen Namen, der einen Bond-Bösewicht erröten lassen würde: das "Going Dark"-Mandat.
Die "Going Dark"-Gruppe: ...
Ihre Schlussfolgerung, die im März 2025 veröffentlicht wurde, könnte von der Spyware-Lobby verfasst worden sein: Verschlüsselung ist schlecht, weil sie uns daran hindert, das zu sehen, was wir wollen.
In dem Bericht werden die üblichen Verdächtigen angeführt: VPNs, verschlüsselte Messaging-Apps und Tools zum Schutz der Privatsphäre, die den Mut haben, zu funktionieren - als existenzielle Bedrohungen für die Ermittlungen. Sie schlug dann ruhig vor, dass der einzige Weg, diese Bedrohungen zu besiegen, darin besteht, genau die Schutzmaßnahmen zu brechen, von denen die Tech-Welt schreit, dass wir mehr davon brauchen.
Die sechs apokalyptischen Reiter der Krypto-Zukunft
EU-Offizielle haben ihre Ambitionen großzügig in sechs Teile unterteilt - wie eine gute dystopische Fortsetzung. Jeder Abschnitt ist ein kleines Wunder an bürokratischer Irreführung:
Datenaufbewahrungsregeln: Tech-Unternehmen sollen Ihre Daten länger speichern - nicht weil sie nützlich wären, sondern weil man sie vielleicht später braucht. Denken Sie an Horten, aber mit Ihren privaten Nachrichten.
Grenzüberschreitendes Abhören: Bis 2027 soll die Echtzeit-Spionage EU-weit einheitlich werden. Nationale Grenzen stören nur beim Abhören.
Digitale Forensik: Werkzeuge zur Datenextraktion selbst nach dem Löschen werden gefördert. Ihr Handy-Papierkorb hat bald weniger Rechte als ein Milchkübel.
Entschlüsselungstechnologien: 2026 kommt ein EU-Leitfaden für Verschlüsselungshintertüren. Bis 2030 könnten Europol &Co. eigene Entschlüsselungstools haben.
Harmonisierung von Sicherheitsinstrumenten: Behörden, Unternehmen und Geheimdienste sollen sich einig werden, was "Sicherheit" bedeutet. Vertrauen durch Vereinheitlichung.
KI-gestützte Datenanalyse: Bis 2028 durchsucht maschinelles Lernen Ihre digitalen Spuren und extrahiert alles, was rechtlich oder politisch brauchbar ist.
Sicherheit durch Schwäche
Das Ganze wird mit einer Mischung aus technokratischem Ernst und digitaler Euphorie verkauft. Kommissar Magnus Brunner nannte es "effizient und zukunftssicher", als ob Massenentschlüsselung eine Innovation des zivilen Lebens wäre. Angeblich soll dieser Plan "hohe Cybersicherheitsstandards und Datenschutzrechte wahren", was in etwa so glaubwürdig ist wie ein Dieb, der für mehr Türschlösser wirbt.
Experten warnen, dass Verschlüsselung zu brechen schlicht dumm ist. Sie ist der Grund, warum Ihre Nachrichten nicht längst für Teenager-Hacker mit Pineapple-WiFi lesbar sind. Ironischerweise empfehlen dieselben Regierungen, die Verschlüsselung schwächen wollen, deren Nutzung.
Starke Verschlüsselung ist nicht das Problem - sie ist der Anfang von Sicherheit.
In Brüssel jedoch ist Verschlüsselung nur noch ein ärgerliches Hindernis auf dem Weg zur totalen Kontrolle. Seit Jahren wird versucht, Gesetze wie Chat Control durchzusetzen - teils erfolgreich durch die Hintertür. Jetzt setzt man auf Geduld und Bürokratiedeutsch.
Vertrauen Sie nicht den App-Stores
Apps wie Signal oder Session sind nur dann sicher, wenn sie nicht aus regulierten App-Stores stammen. Apple und Google können auf Anweisung der EU Hintertüren einbauen. Nutzen Sie stattdessen Open-Source-Versionen direkt von GitHub oder verifizierte APKs. Denn was heute in Frankreich im Store erscheint, könnte morgen in Berlin "angepasst" sein.
Ihr Telefon könnte das Problem sein
Wenn Sie iOS nutzen: Willkommen im Luxusgefängnis. Installationen sind nur mit Apples Erlaubnis möglich. Wer volle Kontrolle über seine Privatsphäre will, sollte ein entgoogeltes Android nutzen - z. B. GrapheneOS oder CalyxOS.
Wählen Sie Apps, als hinge Ihr Leben davon ab
Signal: Der Goldstandard. Open Source. APK von GitHub.
Session: Kein zentraler Server, keine Telefonnummer.
Threema: Schweizer, datenschutzfreundlich, keine Nummer nötig.
Dezentralisieren Sie, solange Sie noch können
Die EU will nicht nur Zugriff - sie will Kontrolle. Dezentralisierung verhindert das. Tools wie Matrix, IPFS oder Secure Scuttlebutt (SSB) entziehen sich zentraler Kontrolle. Keine Server, keine Anlaufstellen für Regulierung.
Lokal verschlüsseln, bevor die Cloud zuschlägt
Nutzen Sie VeraCrypt oder Cryptomator, um Ihre Daten vor dem Upload zu verschlüsseln. Nur wenn Sie die Schlüssel kontrollieren, bleibt Ihre Privatsphäre wirklich gewahrt.
Forward Secrecy & Zero-Knowledge-Proofs
Forward Secrecy verhindert rückwirkende Entschlüsselung. Tools wie OMEMO erzeugen für jede Sitzung neue Schlüssel. Zero-Knowledge-Proofs ermöglichen Authentifizierung ohne Datenpreisgabe - z. B. beweisen, dass man über 18 ist, ohne das Geburtsdatum zu verraten.
Gerichte könnten alles stoppen
Artikel 7 & 8 der EU-Grundrechtecharta schützen Kommunikation &Daten. Es gibt keinen Absatz "außer, wenn die Polizei mitlesen will". Die EU-Verordnung greift alle - nicht nur Verdächtige - an und ist damit systemisch verfassungswidrig.
Der EuGH hat ähnliche Gesetze in Fällen wie Digital Rights Ireland (2014), Tele2 Sverige (2016) und La Quadrature du Net (2020) bereits gekippt. Auch nationale Gerichte - etwa in Deutschland - pochen auf Verhältnismäßigkeit und Grundrechte.
Fazit: Der Gerichtssaal ist die letzte Verteidigungslinie.
Wenn Politik offen fordert, auf alle privaten Nachrichten zuzugreifen, können nur noch Gerichte sagen: "Das ist verfassungswidrig."
Ob der Plan durchkommt, hängt nicht davon ab, wie laut Politiker schreien - sondern ob die Gerichte die Charta noch ernst nehmen.
Quelle: The EU´s Plan To Ban Private Messaging Could Have a Global Impact (Plus: What To Do About It), https://reclaimthenet.org/eu-encryption-roadmap-privacy-risks-decryption-backdoors
https://uncutnews.ch/der-plan-der-eu-private-nachrichten-zu-verbieten-koennte-globale-auswirkungen-haben-und-was-man-dagegen-tun-kann/
 Das riesige Netzwerk israelischer Spionagetechnologie hinter dem modernen Überwachungsstaat, uncut-news.ch, 08.08.2025 Das riesige Netzwerk israelischer Spionagetechnologie hinter dem modernen Überwachungsstaat, uncut-news.ch, 08.08.2025
Nate Bear via Do Not Panic!
Geheimdienste/NSA/Überwachung/BigData, Überwachung
[...] Der Umfang der Nutzung und die Bandbreite der Möglichkeiten dieser israelischen Spionagetechnologie sind enorm. Sie reicht von Gesichts- und Stimmerkennungssoftware über Abhör- und Abhörtechnologie bis hin zu verdeckter Standortverfolgung und der erzwungenen Datenextraktion aus Smartphones und anderen Geräten.
Die Technologie, die von Software-Ingenieuren entwickelt wurde, die ihre Sporen beim Schreiben von Code verdient haben, um die Vorherrschaft Israels über die Palästinenser und die Apartheid gegen sie zu ermöglichen und durchzusetzen, wird an Sicherheitsdienste, Polizeikräfte und Einwanderungsbehörden im gesamten Westen verkauft.
[...] NSO, ein israelisches Unternehmen, das von den ehemaligen Offizieren der Einheit 8200 Shalev Hulio und Omri Lavie gegründet wurde, wurde 2019 von einem kalifornischen Gericht wegen des Verkaufs seiner Software "Pegasus" an Regierungen verurteilt, damit diese WhatsApp-Konten hacken konnten. Pegasus, das in der Lage war, sogenannte "Zero-Click"-Angriffe auszuführen, um ohne Wissen des Nutzers auf ein Smartphone zuzugreifen, wurde von Regierungen zur Überwachung von Dissidenten, Menschenrechtsaktivisten und Journalisten eingesetzt ...
Ebenfalls von Biden im Rahmen derselben Durchführungsverordnung auf die schwarze Liste gesetzt wurde ein weiterer israelischer Spionagesoftwarehersteller namens Candiru, dessen Hacking-Software nicht die gleiche Aufmerksamkeit auf sich zog wie die NSO Group. Candiru, ebenfalls von ehemaligen Mitarbeitern der Einheit 8200 gegründet, verkaufte Spionagesoftware an Regierungen, um Menschenrechtsaktivisten, Journalisten, Akademiker, Botschaftsangehörige und Dissidenten auszuspionieren.
Im Jahr 2023 setzte die Biden-Regierung erneut zwei israelische Spyware-Unternehmen ohne großes Aufsehen auf die schwarze Liste, und wieder einmal ohne Maßnahmen gegen Israel zu ergreifen. Die beiden Unternehmen, Cytrox und Intellexa, wurden von Tal Dilian gegründet, der 24 Jahre in der IDF verbrachte und zum Oberbefehlshaber der Einheit 8200 aufstieg. Im Jahr 2019 erhielt Dilian, der in Zypern lebt, Besuch von einem Forbes-Journalisten, dem er demonstrierte, wie seine Software innerhalb von Sekunden ein Telefon aus der Ferne hacken kann.
In Europa haben sich Zypern und Barcelona zu Drehscheiben für ehemalige Mitglieder der Einheit 8200 entwickelt, die dort Spionagesoftware-Unternehmen gründen.
Ein weiteres israelisches Spionageunternehmen, Paragon Solutions, wurde Anfang dieses Jahres identifiziert, als es still und heimlich Daten aus WhatsApp, Signal, Messenger und Gmail extrahierte, ohne dass eine Interaktion der Nutzer erforderlich war. Gegen Paragon wurde in Rom Strafanzeige erstattet, nachdem ein italienischer Journalist von der italienischen Regierung mit Hilfe von Paragon-Software gehackt worden war. Weitere rechtliche Schritte wurden jedoch nicht unternommen. Das Unternehmen, das von den Kommandanten der Einheit 8200 Ehud Schneorson, Idan Nurick und Igor Bogudlov gegründet wurde und vom ehemaligen israelischen Premierminister Ehud Barak beraten wird, wurde weder von der EU noch von den USA auf die schwarze Liste gesetzt und kann weiterhin frei agieren.
Diese Unternehmen sind nur die Spitze des Eisbergs, Namen, die sich in rechtlichen Grauzonen bewegten und entweder irgendwann mit dem Gesetz (so wie es ist) in Konflikt gerieten und ins Visier der Behörden gerieten oder deren illegale Spionageaktivitäten aufgedeckt wurden.
Noch heimtückischer sind die israelischen Spyware-Unternehmen, die offen Verträge mit westlichen Sicherheitsdiensten und -behörden abschließen, um Mobiltelefone und andere Geräte auszuspionieren und zu knacken.
Da diese Unternehmen mit legalen staatlichen Stellen zusammenarbeiten, behaupten sie, ein anderes Modell zu verfolgen als die NSO Group, Candiru und andere, die sich auf illegale Hacking-Dienste konzentrieren. In vielen Fällen ist ihre Software jedoch ähnlich, wenn nicht sogar identisch, und der volle Umfang ihrer Aktivitäten ist unbekannt. An der Spitze steht Cellebrite, gegründet vom ehemaligen IDF-Soldaten Yossi Carmil und besetzt mit Dutzenden von ehemaligen Mitarbeitern der Einheit 8200 des israelischen Geheimdienstes.
Das Flaggschiff-Tool von Cellebrite heißt Universal Forensic Extraction Device und extrahiert Daten wie Kontakte, Standorte, gelöschte Nachrichten und Anrufe aus einer Reihe von Geräten, darunter Smartphones, Tablets, SIM-Karten und GPS-Geräte. In den USA hat Cellebrite einen 30-Millionen-Dollar-Vertrag mit der ICE und einen 1,6-Millionen-Dollar-Vertrag mit der Zoll- und Grenzschutzbehörde, um Daten von an der Grenze beschlagnahmten Handys auszulesen. Das Überwachungsunternehmen arbeitete auch mit dem FBI zusammen, um das Telefon von Thomas Crook, dem potenziellen Attentäter von Trump, zu entsperren. Und Cellebrite strebt eine noch tiefere Verankerung im Sicherheits- und Überwachungsapparat der USA an. Drop Site News enthüllte im vergangenen Jahr, dass Cellebrite eine Lobbying-Firma engagiert und einen eigenen Geschäftsbereich eingerichtet hat, um mehr Aufträge der US-Regierung zu erhalten, nachdem das Unternehmen 2024 mehr als 18 Millionen Dollar aus Verträgen mit der US-Bundesregierung eingenommen hatte. Im Dezember 2023 prahlte Cellebrite damit, einen Millionenvertrag mit "einer der größten Polizeibehörden des Landes" abgeschlossen zu haben, ohne jedoch zu verraten, um welche es sich handelt. Da sie als "langjähriger Kunde" bezeichnet wurden, ist der wahrscheinlichste Kandidat die NYPD, die nachweislich seit Jahren mit Cellebrite zusammenarbeitet.
Darüber hinaus habe ich recherchiert, dass Cellebrite aktive Verträge mit einer Reihe von US-Bundesbehörden hat, darunter die Marine, die DEA, die Küstenwache und der Fish and Wildlife Service. Eine Reihe von US-Botschaften haben ebenfalls Verträge mit Cellebrite, darunter die US-Botschaften in Lima, Bogota und Asuncion. Das US Special Operations Command, die Behörde, die die verschiedenen Spezialeinsatzprogramme der US-Streitkräfte überwacht, bezahlt ebenfalls für Cellebrite-Tools, ebenso wie das Global Strike Command, die für Nuklearangriffe zuständige Einheit der US-Luftwaffe.
Cellebrite ist in Großbritannien ebenso aktiv. Im Jahr 2020 unterzeichnete das Unternehmen einen Dreijahresvertrag über zwei Millionen Pfund mit der Londoner Metropolitan Police für das Premiumprodukt von Cellebrite. Die Londoner Polizei erklärte, die Software von Cellebrite sei die einzige auf dem Markt, "die die Anforderungen der Londoner Polizei erfüllt", insbesondere hinsichtlich ihrer Fähigkeit, Android-Handys zu knacken. Es ist unklar, ob dieser Vertrag verlängert wurde.
Im Jahr 2018 unterzeichnete die schottische Polizei einen Vertrag über 370.000 Pfund mit Cellebrite über die Lieferung von 41 mobilen "Cyber-Kiosken", die in ganz Schottland eingesetzt werden sollen und das Knacken von Handys vor Ort ermöglichen. Und im Jahr 2022 zahlte die Polizei von Nordwales Cellebrite über eine Viertelmillion Pfund für eine Reihe von Tools, die das "Umgehen von Passwörtern" und das "Brute-Force-Knacken" von Handys ermöglichten.
Die Polizei von Kent, deren bewaffnete Polizeikräfte kürzlich damit drohten, Menschen wegen des Zeigens von Palästina-Flaggen festzunehmen, unterzeichnete im vergangenen Jahr einen Einjahresvertrag mit Cellebrite. Und in diesem Jahr haben zwei weitere britische Polizeibehörden Verträge mit Cellebrite unterzeichnet. Im Februar zahlte die City of London Police, die Polizei für Londons Finanzviertel, die von der Met Police getrennt ist, hunderttausend Pfund für Cellebrite-Tools. Und im April unterzeichnete die Polizei von Leicestershire einen Einjahresvertrag mit Cellebrite, der sie 328.700 Pfund kostete. Cellebrite hat auch einen Vertrag mit dem britischen Verkehrsministerium.
In Großbritannien ist Cellebrite ein zugelassener Lieferant im Rahmen des sogenannten "Digital Forensics Dynamic Purchasing System", das laut der für die Unterzeichnung von Handelsverträgen für britische Polizeibehörden zuständigen Stelle "eine optimierte Beschaffung von Cellebrite-Tools für alle britischen Polizeibehörden ermöglicht".
Wie weit verbreitet der Einsatz von Cellebrite-Tools bei den britischen Polizeibehörden ist, ist nicht bekannt. Auf Grundlage von Informationsfreiheitsanfragen wurde zuvor festgestellt, dass 26 der 47 Polizeibehörden im Vereinigten Königreich den Einsatz dieser Technologie zugegeben haben, während andere einen Testlauf planen. Neuere Informationsfreiheitsanfragen an britische Polizeibehörden in diesem Jahr bezüglich ihrer Nutzung von Cellebrite, von Südwales bis West Yorkshire, wurden aus Gründen der "nationalen Sicherheit" abgelehnt.
Cellebrite wird auch von der australischen Polizei und Regierungsbehörden in großem Umfang eingesetzt. Eine Untersuchung aus dem Jahr 2023 ergab, dass seit 2011 128 Verträge zwischen australischen Regierungsbehörden und dem Unternehmen geschlossen wurden, darunter die australische Bundespolizei, das Verteidigungsministerium und die australische Steuerbehörde.
Cellebrite rühmt sich seiner Arbeit, die den Völkermord Israels in Gaza ermöglicht hat, und behauptet, seit dem 7. Oktober "maßgeblich" an der Bereitstellung von Telefonhackerdiensten für den israelischen Geheimdienst beteiligt zu sein.
Noch ausgefeiltere Tools werden wohl von dem israelischen Spionagetechnologieunternehmen Cobwebs Technologies angeboten, das von den ehemaligen Offizieren der IDF-Einheit 8200 Omri Timianker, Udi Levy und Shay Attias gegründet wurde und eine Reihe ehemaliger Mitglieder der Einheit 8200 beschäftigt. Zu den Dienstleistungen von Cobwebs (das 2023 an ein Unternehmen namens PenLink verkauft wurde, aber das CobWebs-Team behielt) gehört ein KI-gestützter Dienst, der die Gesichts- und Bilderkennung in sozialen Medien und im Deep Web ermöglicht, sowie eine Funktion namens WebLoc, mit der die Bewegungen von Mobiltelefonen in einem vom Benutzer ausgewählten Gebiet verfolgt werden können. Diese als Geofencing bezeichnete Funktion wird durch In-App-Werbung ermöglicht, die personenbezogene Daten von Smartphones abruft, die dann an Spionagetechnologieunternehmen wie Cobwebs verkauft werden, um sie in Tools wie WebLoc zu integrieren. Eine inzwischen gelöschte Pressemitteilung aus dem Jahr 2019 beschreibt in der Sprache der Unternehmen die angebotenen Dienstleistungen. Cobwebs hat zuvor einen Vertrag über 2,7 Millionen Dollar mit ICE unterzeichnet, hat einen aktiven Vertrag über 3,2 Millionen Dollar mit dem US-Heimatschutzministerium und hat im Juni letzten Jahres einen riesigen Vertrag über 5,3 Millionen Dollar mit dem texanischen Ministerium für öffentliche Sicherheit abgeschlossen. Ein Bericht aus dem Jahr 2024 ergab außerdem, dass die LAPD seit mehreren Jahren die Überwachungs- und Ortungstools von Cobwebs einsetzt.
Im Jahr 2020 eröffnete das Unternehmen ein Büro in London mit der Absicht, seine Spionagetechnologie an britische Polizei- und Sicherheitsdienste zu liefern, aber es gibt keine öffentlichen Informationen über britische Stellen, die mit Cobwebs zusammenarbeiten.
Ein weiteres israelisches Spionagetechnologieunternehmen, das mit westlichen Sicherheitsdiensten, Polizeikräften und Regierungsbehörden zusammenarbeitet, ist Cognyte. Das Unternehmen, das aus einem anderen israelischen Spionagetechnologieunternehmen namens Verint hervorgegangen ist, wird von Elad Sharon, Gil Cohen und Ronny Lempel geleitet, die alle Absolventen der IDF und der Einheit 8200 sind. Das LinkedIn-Banner von CEO Sharon ist ein Bild mit dem Cognyte-Logo, auf dem das Unternehmen seine Unterstützung für Israel bekundet.
Cognyte entwickelt "Netzwerkintelligenz"-Tools, die riesige Mengen an Informationen sammeln, darunter alles, was über 4G/5G-Sendemasten läuft, Telekommunikations-Metadaten, Messaging-Plattformen, Telefonate und Netzwerksignale, um Muster und Anomalien in der Kommunikation zu erkennen. Diese Daten werden in eine Datenplattform-"Lösung" eingespeist, die es den Nutzern ermöglicht, Zusammenhänge herzustellen und Informationen zu analysieren. All dies ist angeblich legal, aber Informationen über die Art der Arbeit und die Behörden, die Cognyte beauftragen, sind rar. Cognyte gibt die Aufträge bekannt, aber niemals die Endnutzer.
Was wir wissen, ist, dass westliche Strafverfolgungsbehörden, nationale Sicherheitsbehörden und Militärs in den letzten 18 Monaten Verträge mit Cognyte im Gesamtwert von fast 60 Millionen Dollar abgeschlossen haben. Dazu gehören ein Dreijahresvertrag über 20 Millionen Dollar mit einer nationalen Sicherheitsbehörde in Europa, ein Vertrag über 3 Millionen Dollar mit einer US-Polizeibehörde und ein Vertrag über 10 Millionen Dollar mit einem europäischen Militär, der erst letzte Woche bekannt gegeben wurde. In der Pressemitteilung zu dem Militärvertrag heißt es, dass "Cognyte weiterhin bewährte Lösungen liefert, die Militärteams an vorderster Front mit den umsetzbaren Informationen versorgen, die sie für ihren Einsatz benötigen".
Zwei Käufer, die ich auf einer Website für US-Behördenaufträge identifiziert habe, sind der US-Geheimdienst und die US-Botschaft in El Salvador. Und im Jahr 2023 enthüllte Reuters, dass Cognyte kurz vor dem Militärputsch, der die Junta an die Macht brachte, die einen Völkermord an den Rohingya begangen hat, Abhörsoftware an das staatliche Telekommunikationsunternehmen von Myanmar verkauft hatte.
Ähnlich wie bei Cellebrite und Cobwebs findet man bei einer Suche auf LinkedIn nach ehemaligen Mitarbeitern der Einheit 8200, die jetzt bei Cognyte arbeiten, Dutzende von Namen.
Das Unternehmen, aus dem Cognyte hervorgegangen ist, Verint, ist ebenfalls israelisch, wurde von ehemaligen Geheimdienstmitarbeitern gegründet und hat auch mit westlichen Sicherheitsbehörden zusammengearbeitet. Im Jahr 2014 baute Verint die Abhör- und Überwachungsinfrastruktur der Schweiz auf und erhielt 2017 35 Millionen Dollar vom US-Verteidigungsministerium für die Arbeit an einem großen, geheimen Projekt. Im Jahr 2018 erhielt Verint einen Teil eines 50-Millionen-Pfund-Auftrags zur Ausstattung der britischen Polizei mit neuen Cyber-Intelligence-Fähigkeiten. Seitdem hat Verint sein Geschäftsmodell auf Kundenbindungsplattformen umgestellt und einen Großteil seiner Militär- und Sicherheits-Spionagetechnologie an Cognyte ausgegliedert.
Ein weiteres israelisches Unternehmen, das mit britischen Polizeikräften zusammenarbeitet, ist Corsight AI, das seine Gesichtserkennungstechnologie an die Polizei von Essex verkauft hat. Die Software von Corsight, die die Identifizierung und den Abgleich von Gesichtern ermöglicht, wurde zunächst an Palästinensern im Gazastreifen und im Westjordanland perfektioniert. Dem verlinkten Artikel zufolge wurde die Technologie während des Völkermords in Gaza eingesetzt. Gründer und Vorsitzender der Muttergesellschaft von Corsight, Cortica, ist Igal Raichelgauz, ein ehemaliger israelischer Geheimdienstoffizier. Corsight hat seine Gesichtserkennungstechnologie auch an die Militärpolizei von São Paulo und an die Stadtpolizei von Bogotá verkauft.
Das israelische Gesichtserkennungsunternehmen Briefcam hat ebenfalls Verträge mit britischen Polizeibehörden sowie mit Polizeibehörden in den USA. In Großbritannien nutzt die Polizei von Cumbria das Analysesystem von Briefcam in ihrem landesweiten Netzwerk von Überwachungskameras, behauptet jedoch, die Gesichtserkennungskomponente deaktiviert zu haben. In Frankreich wurden die Verträge mit Briefcam 2023 gekündigt, nachdem bekannt wurde, dass zahlreiche Polizeibehörden im ganzen Land das System illegal und unter Verstoß gegen die französischen Datenschutzgesetze einsetzten. Auch die Polizei in Brüssel und Warschau nutzt die Gesichtserkennung von Corsight, und in den USA haben die Polizeibehörden von Chicago, Springfield und Beverly Hills den Einsatz von Corsight bestätigt.
NICE, ein israelisches Unternehmen, das von ehemaligen Soldaten der israelischen Streitkräfte gegründet wurde, hat den Markt für die Identifizierung von Finanzbetrug erobert und bedient 85 % der Fortune-500-Unternehmen sowie eine Reihe europäischer Regulierungsbehörden. Das milliardenschwere Unternehmen hat auch Überwachungsinstrumente für Städte bereitgestellt, darunter Kennzeichenerkennung, Gesichtserfassung sowie handheld GPS-basierte Videoterminals und mobile Videosensoren zur Verfolgung von Bürgern. Eine Untersuchung von Buzzfeed aus dem Jahr 2015 ergab, dass NICE geheime Überwachungssoftware an eine Reihe von Ländern geliefert hat.
Eine unrühmliche Erwähnung verdient das israelische Unternehmen Black Cube, das von den ehemaligen Geheimagenten der Einheit 8200, Dan Zorella und Avi Yanus, gegründet wurde. Black Cube wurde bekanntlichvom Hollywood-Vergewaltiger Harvey Weinstein (ein Mann, der sagte, er sei "in seinem Herzen und in seinem Geist Israeli") angeheuert, um seine Anklägerinnen auszuspionieren und Informationen über sie zu sammeln. BlackCube ist in eine Reihe von Spionageskandalen verwickelt und hat in der Vergangenheit westliche Diplomaten beschäftigt, darunter Vivian Bercovici, Kanadas ehemalige Botschafterin in Israel.
Dieses Kompendium zeigt, dass Israel und seine Apartheidwirtschaft im Zentrum des Strebens nach einer vollständig überwachten Welt ohne jegliche Meinungsfreiheit stehen. Weltweit läutet israelische Spionagesoftware einen ausgeprägten Faschismus des 21. Jahrhunderts ein, der neue Kontrolltechnologien mit einem bewährten Rahmenwerk verbindet, das darauf abzielt, zu spionieren, zu unterdrücken und zu dominieren. Unter dem Deckmantel der Sicherheit der Bürger und der Verbrechensbekämpfung schmiert israelische Technologie die Räder des Autoritarismus.
Israels permanenter Krieg und seine Apartheid-Wirtschaft sowie die von israelischen Geheimdienstmitarbeitern geführten Spionage-Technologieunternehmen, die aus dieser Wirtschaft hervorgehen, sind die größte Bedrohung für die bürgerlichen Freiheiten in der heutigen Welt. Und es ist keine Überraschung, dass Israel diesen Markt erobert hat. Israel produziert Menschen und Projekte, die auf Dominanz ausgerichtet sind, weil Israelis in einer Militärkultur der Straflosigkeit aufwachsen und davon umgeben sind. Eine Kultur, in der Technologie nur zur Dominanz geschaffen wird, Versuchspersonen reichlich vorhanden sind und Regeln für den Einsatz nicht existieren.
Indem wir die Werkzeuge eines Apartheidstaates für Sicherheits- und Strafverfolgungstechnologie kaufen und uns darauf verlassen, sehen wir, wie Israels Apartheid und Völkermord selbst für westliche Regierungen in ihrem Streben nach vollständigen Sicherheitsstaaten unverzichtbar werden.
Unsere Welt wird immer autoritärer und faschistischer, weil Instrumente, die von Autoritären und Faschisten entwickelt wurden, im öffentlichen und privaten Bereich eingesetzt werden.
Deshalb müssen wir, wie ich in meinem letzten Artikel argumentiert habe, die Welt de-zionisieren.
Die Überwachungs- und Spionagetechnologieindustrie ist nur ein weiterer Strang des tiefen und schädlichen Einflussnetzes, das Israel über den Westen gespannt hat, ein Netz, das unsere Politik erstickt, unsere bürgerlichen Freiheiten einschränkt und zu einem Holocaust geführt hat.
Unsere Zukunft und die Zukunft der Palästinenser hängen davon ab, dass dieses Netz zerstört und der Einfluss Israels in unseren Gesellschaften beseitigt wird.
Quelle: The Vast Network of Israeli Spy Tech Behind The Modern Surveillance State, https://www.donotpanic.news/p/the-vast-network-of-israeli-spy-tech
https://uncutnews.ch/das-riesige-netzwerk-israelischer-spionagetechnologie-hinter-dem-modernen-ueberwachungsstaat/
 The Illusion of Anonymized Data, uncut-news.ch, 10.24.2025 The Illusion of Anonymized Data, uncut-news.ch, 10.24.2025
Christina Maas, reclaimthenet
Anonymisierung verspricht Unsichtbarkeit, liefert aber nur eine Papiermaske - leicht abziehbar von denselben Systemen, die vorgeben, sie zu schützen.
Ein bekanntes Sprichwort passt zum Moment: "Hüte dich vor Technik, die Geschenke bringt." Wenn Datensammler von Anonymisierung sprechen, meinen sie selten echten Schutz.
Der Begriff klingt klinisch und eindeutig. In der Praxis dient er oft eher als juristischer Deckmantel denn als tatsächliche Sicherheitsmaßnahme. Er signalisiert den Nutzern, sie müssten sich keine Sorgen machen - während das System genau so weiterläuft, wie es gedacht ist.
Anonymisierung wird als Endpunkt behandelt. Sobald Daten als anonym markiert sind, endet die Prüfung. Regulierungsbehörden verweisen auf Anonymisierung als Erfolg. Plattformen sehen darin den Beweis für Verantwortung.
Unterdessen haben die Unternehmen, die Werkzeuge zur Reidentifizierung entwickeln, keinerlei Illusionen über deren Dauerhaftigkeit.
Quelle: https://reclaimthenet.org/how-anonymized-data-can-be-a-myth
https://uncutnews.ch/die-illusion-der-anonymisierten-daten/
END OF EXCURS"
  
|
 Gooken
Gooken
 Exkurs
Exkurs
 News&Links
News&Links
 Links
Links
 Gästebuch
Gästebuch





 Beware building network profiles within drakconf (MMC, mdv2010)! This can destroy the building up of connections in some situations. So delete all profiles out of network profiles, do not backup any of them here!
Beware building network profiles within drakconf (MMC, mdv2010)! This can destroy the building up of connections in some situations. So delete all profiles out of network profiles, do not backup any of them here!

 Most features of the dynamic firewall linfw3:
Most features of the dynamic firewall linfw3:



 easy configuration by almost simple „yes“/„no“-settings
easy configuration by almost simple „yes“/„no“-settings
 with CONNection-LIMITation and XOR-encryption of packages and connections
with CONNection-LIMITation and XOR-encryption of packages and connections





 Plasmoids resp. plasma (applets) for the desktop and the controlbar (please notice, that in differnence to mdv2010-rpm-packages actually not all of them do function, so we have to wait, and that some of them get their information to present out of the internet): Daisy (free program choice within rings or bars), Lancelot (desktop-menu), timezones and weather, birthday-reminder, calculator, widget-dashboard, system-monitoring, multiple rowed fast-loader (more-rowed compressing collector for icons with optional mini-pull-down-(up-)menu), unit-conversion, LCD-weather-station, weather forecast, wordclock with timezones, accu-check, image frame, comic, egg-clock, jumping ball, colorchoosing stick, calculator, moon phases, zoom, social desktop, ToDo-lists, remember the milk, system-monitor, guitar-tuner, image-preview, widget-dashboard, birthday-reminder, flickr, language-translator, sun-system, fishtank, DVB-signal-meter, newsticker, Mountoid, Bundesliga, Facebook, Flickr, bsun (wandernde Sonne), FrustML resp. (Mensch-Ärger-Dich-Nicht), Fancy Tasks (quickstarter similar to cairo-dock), Koala (similar to Tamagocchi), Astrocalendar, Plasmio (SMS), daisy (desktop-icons in a cricle), 15 stones,Tomatoid, egg-clock, spell verification, blackboard, WorkContext (nepomuk) and much more ...
Plasmoids resp. plasma (applets) for the desktop and the controlbar (please notice, that in differnence to mdv2010-rpm-packages actually not all of them do function, so we have to wait, and that some of them get their information to present out of the internet): Daisy (free program choice within rings or bars), Lancelot (desktop-menu), timezones and weather, birthday-reminder, calculator, widget-dashboard, system-monitoring, multiple rowed fast-loader (more-rowed compressing collector for icons with optional mini-pull-down-(up-)menu), unit-conversion, LCD-weather-station, weather forecast, wordclock with timezones, accu-check, image frame, comic, egg-clock, jumping ball, colorchoosing stick, calculator, moon phases, zoom, social desktop, ToDo-lists, remember the milk, system-monitor, guitar-tuner, image-preview, widget-dashboard, birthday-reminder, flickr, language-translator, sun-system, fishtank, DVB-signal-meter, newsticker, Mountoid, Bundesliga, Facebook, Flickr, bsun (wandernde Sonne), FrustML resp. (Mensch-Ärger-Dich-Nicht), Fancy Tasks (quickstarter similar to cairo-dock), Koala (similar to Tamagocchi), Astrocalendar, Plasmio (SMS), daisy (desktop-icons in a cricle), 15 stones,Tomatoid, egg-clock, spell verification, blackboard, WorkContext (nepomuk) and much more ...
 Desktop-Screenlets: GUI screenlet-administration and -daemon with actually more than 100 screenlets plus downloadable ones, running in the foreground, background, scalable size, widget-option, many settings like: growing flower (to give some water and so on), slideshow, pager, control for adding screenlets, radio, meter, stocks, speech, sensors, ringssensors, ruler, convert, example of howto create a screenlet, copystack, clear weather from weather.com, ...
Desktop-Screenlets: GUI screenlet-administration and -daemon with actually more than 100 screenlets plus downloadable ones, running in the foreground, background, scalable size, widget-option, many settings like: growing flower (to give some water and so on), slideshow, pager, control for adding screenlets, radio, meter, stocks, speech, sensors, ringssensors, ruler, convert, example of howto create a screenlet, copystack, clear weather from weather.com, ...


 Python-Games, "small games for the long pause": https://www.pygame.org/wiki/GettingStarted, http://pygame.org/tags/pygame: solarwolf (el6), spacepong (el6) and much, much more python games in the rubriques:
Python-Games, "small games for the long pause": https://www.pygame.org/wiki/GettingStarted, http://pygame.org/tags/pygame: solarwolf (el6), spacepong (el6) and much, much more python games in the rubriques:
 6) Routing and navigation: comfortable Nunav only fullfills the demands.
6) Routing and navigation: comfortable Nunav only fullfills the demands. Theme: Optical mouse radiates and causes pain to the hand
Theme: Optical mouse radiates and causes pain to the hand http://bencane.com/2013/10/29/managing-dns-locally-with-etchosts/
http://bencane.com/2013/10/29/managing-dns-locally-with-etchosts/ Do you want the everlasting peace with your computer?
Do you want the everlasting peace with your computer?