Gooken
Gooken
 Exkurs
Exkurs
- Ausgangssituation
- Theoretische Grundlagen
- "Universal Linux"
- MS Windows & Co.
- Datensicherung
- SSD optimieren
- Updaten
- Zugriffsrechte
- ACL - erweiterte Zugriffsrechte
- System-Zugriffsdatei: /etc/passwd
- msec-Sicherheitsebenen
- Domain-Zugriffsrechte (MAC Tomoyo)
- Sandboxen: docker-io, firejail
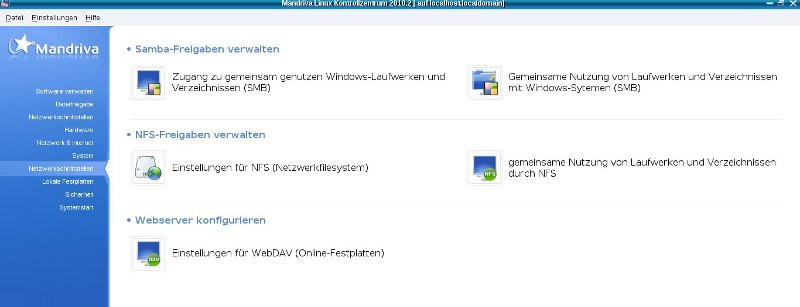
- Freigaben (LAN)
- FSE (Full System Encryption)
- iptables/LINFW3
- Intrusion Detection System (IDS)
- weitere Filterkonzepte
- lokaler DNS (pdnsd)
- Einzelmaßnahmen und Reparatur
- Troubleshooting: Drucker
- Downloads
- Datenblatt
- Alle Kategorien anzeigen →
Exkurs
 News&Links
News&Links
 Links
Links
- CCC
- BSI
- weitere Links
- Alle Kategorien anzeigen →
More Links
 Gästebuch
Gästebuch


 Worth at mind report from uncut-news.ch:
Worth at mind report from uncut-news.ch:
 ... and if, such decades ago, even my own mother meant... / ... und wenn vor Jahrzehnten sogar die eigene Mutter zum Thema Maja Schmidt schon meinte ( ist das aber fertig: die eigene Mutter dann auch noch, das kriegt ihr aber wieder...!):
... and if, such decades ago, even my own mother meant... / ... und wenn vor Jahrzehnten sogar die eigene Mutter zum Thema Maja Schmidt schon meinte ( ist das aber fertig: die eigene Mutter dann auch noch, das kriegt ihr aber wieder...!):


 Gooken - the at times breaking full, large "china restaurant"... Do you want the everlasting peace with your computer as a system (backported Fedora Core (fc): updates from year 2010-2026 resp. lifetime) with covering software (backported too) on powersaving and cheap lifetime-hardware, providing the incredible high security level? Contribute to Gooken for the manufacturing of the (consistent) IT-security-standard! For correspondent please click here!
Gooken - the at times breaking full, large "china restaurant"... Do you want the everlasting peace with your computer as a system (backported Fedora Core (fc): updates from year 2010-2026 resp. lifetime) with covering software (backported too) on powersaving and cheap lifetime-hardware, providing the incredible high security level? Contribute to Gooken for the manufacturing of the (consistent) IT-security-standard! For correspondent please click here!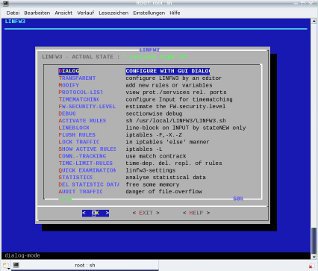

 Regardless from all Linux-distributions, one and the same Linux gets installed package by package, although this might not possible for each distribution as a fault of their specific architectures (library-structure and so on).
Regardless from all Linux-distributions, one and the same Linux gets installed package by package, although this might not possible for each distribution as a fault of their specific architectures (library-structure and so on).


 Instead the platform independent
Instead the platform independent 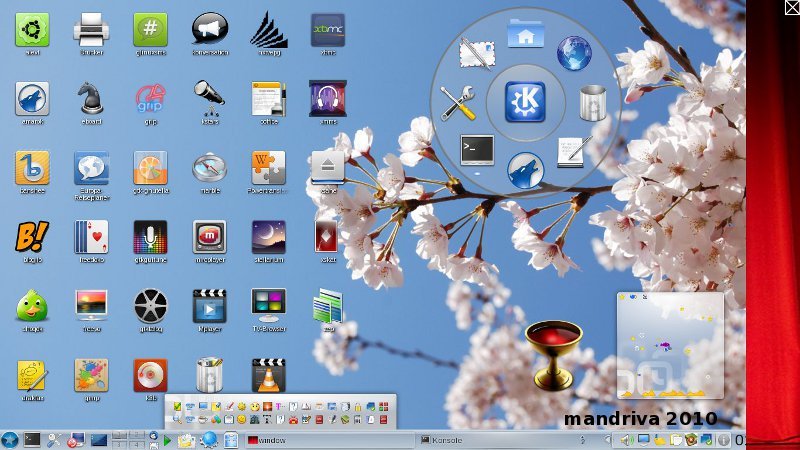

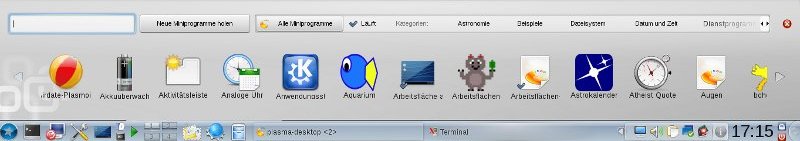

























 Cairo-Dock from http://fr2.rpmfind.net or http://www.glx-dock.org/
Cairo-Dock from http://fr2.rpmfind.net or http://www.glx-dock.org/
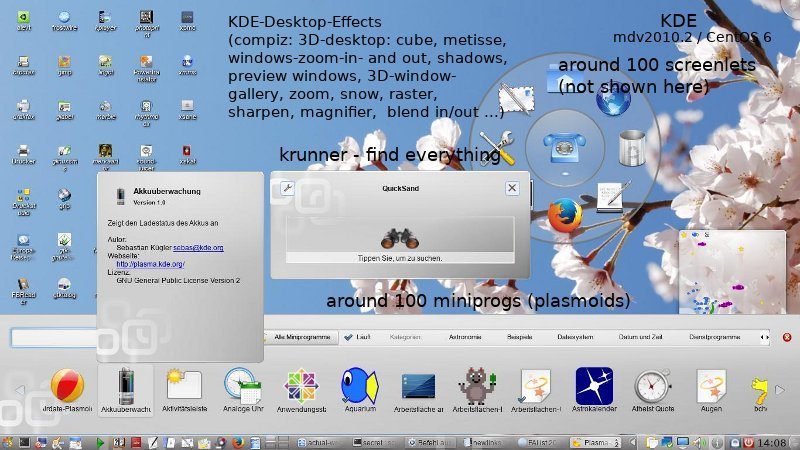
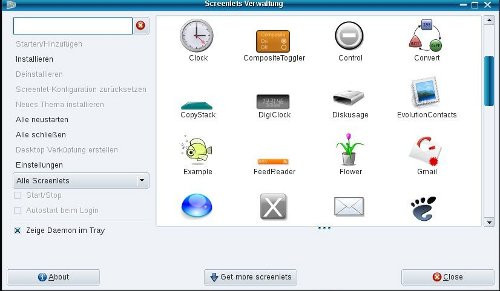 Desktop-Screenlets, image: GUI-Screenlet-administration with more than 100 screenlets additionaly downloadable ones and screenlet-daemon, screenlet in the fore- and background, scalable size, widget-attribute, more attributes like: growing flower ( to give some water from time to time), slideshow, pager, control (to add more screenlets), radio, meter, stocks, speech, sensors, ringssensors, ruler, convert, example of howto create a screenlet, copystack, clear weather von weather.com, ...
Desktop-Screenlets, image: GUI-Screenlet-administration with more than 100 screenlets additionaly downloadable ones and screenlet-daemon, screenlet in the fore- and background, scalable size, widget-attribute, more attributes like: growing flower ( to give some water from time to time), slideshow, pager, control (to add more screenlets), radio, meter, stocks, speech, sensors, ringssensors, ruler, convert, example of howto create a screenlet, copystack, clear weather von weather.com, ...
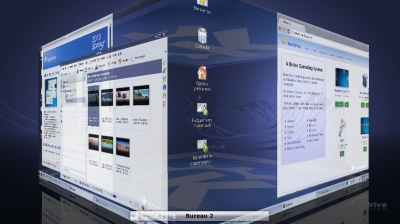
 Mandriva Metisse takes 3D to a New Level, http://cybernetnews.com/mandriva-metisse-linux-takes-3d-to-a-new-level/
Mandriva Metisse takes 3D to a New Level, http://cybernetnews.com/mandriva-metisse-linux-takes-3d-to-a-new-level/ Abb.: System tray (plasmoid) out of Krandr (screen resolution), kmix, Klipper, parcellite (additional configuration of klipper), NetworkManager, Stardict, USB-connections and encrypted partitions, kgpg, korganizer (calender and. dating planner with reminder function), printer-applet (printer jobs), nepomuk (semantic search), i - information for system messages by kwrited (actually not started, that means still without: knotes or tomboy, tvbrowser, ...), clock with date and calendar and the fast screenlock- and poweron-off-plasmoid; enfastened load of the tray after the deinstallation of interfering draksnapshot
Abb.: System tray (plasmoid) out of Krandr (screen resolution), kmix, Klipper, parcellite (additional configuration of klipper), NetworkManager, Stardict, USB-connections and encrypted partitions, kgpg, korganizer (calender and. dating planner with reminder function), printer-applet (printer jobs), nepomuk (semantic search), i - information for system messages by kwrited (actually not started, that means still without: knotes or tomboy, tvbrowser, ...), clock with date and calendar and the fast screenlock- and poweron-off-plasmoid; enfastened load of the tray after the deinstallation of interfering draksnapshot
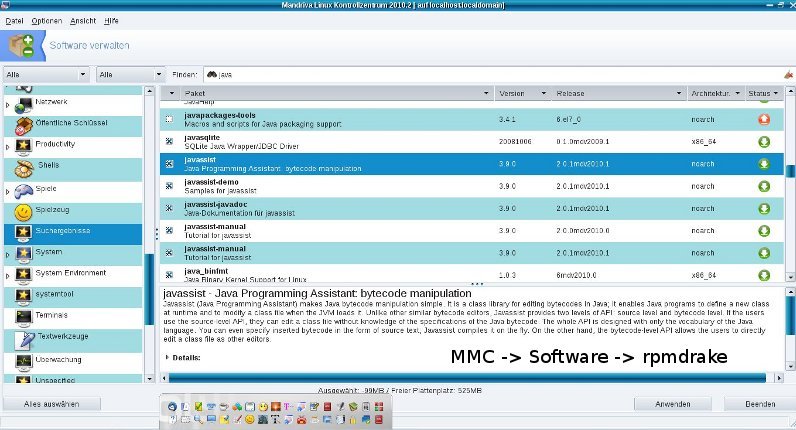
 proprietary software (opensource against liablity, more clearance of question about liablity), cost-traps (here: billing by handies and SMS, overread of additional parts of contracts and the conditions), blackmail for unlocking suddenly locked computers (see our report under links), abuse of copyrights and patents, cult for criminals, billions hard investment into spying software and techniques, missing, confusing or the fluctuating IT-security-concept, hard-disk-scans, defragmentation (unnecessary for many UNIX-file-systems), harddrives (instead of MC-SSD, cite: "A magentic harddrive is much to risky to intrust data. Although a lot of improvements took place, who has not heart or - in worst cases - made the experience of lost data. Therefore enough reasons are relevant." (source: poshtar@datensicherx.com, 13.05.2014)), the demand for a registry, registry-errors (UNIX-systems have no registry), degeneracy of the registry, suddenly or inpredictable lost files, explosion (of net-adapter), fire (net-adapter, porous PC-lautspeaker-cable, ...), your own ununderstandable blackened company (enlighted by our PHP-MySQL-company management Mycompanies), virtual blackmail by encrypting harddrives against ransom, shooting through unmanned flying objects as a technical response to stored data, kontermination (through chipsets, preventable by IGP and all-in-one-mainboards) and radiation, WLAN-radiation (see our linkside), CRT-radiation, CD-burner-radiation, netadapter-radiation, warning high SAR-value (handies), zero-emission (reflectable monitor emissionf or example by special PCMCIA-cards prevented by special editors like the zero emission pad), hardware-recognigtion (standarized driver, Kernel ver. greater 2.6.30), infiltration of social networks, handy-hunts through nets, inconsistency (vs. everlasting science), need for upgrades (new tarballs, zip-archives, functionality), updates, patches and bugfixes (vs. functionality), browser with outdated ssl3.0 (modern usage is provided by TLS), changeovers to different security software, missing changelogs, software-overload on harddisc (Opensource, independency-checks, other introduced methods), hacker (STATE-NEW lined iptables-blocking), large holes in firewalls (iptables block-rate), intrusion and valdalism, viruses (access-rights of UNIX-filesystems), freak (patch or prefer browsers like Firefox or Konqueor instead), abuse by virus scanner (standard opensource clamav), worms, rootkits (rkhunter) resp. botnets and trojans (no botnets and no trojans by correct usage of the OWNER-concept of iptables), manipulation by system-administrators upon software, files and configurations, ddos-attacks (almost on the base of bots and trojans), inactual alarms, false-alarms, forgotten or coded warnings and error-messages, ad- and spyware as much as Trackingscripts (firefox-addons), Driveby-Downloads, Canvas Fingerprinting (see under online check), forced acquisition because of truncated customer support for old operating systems (lifetime installation-support for all mdv/mdk over "pointed 1-" to "pointed 0" versions), product-manufacturing fault right on the surface of installation-CD/-DVD, aggressive marketing, need of updates and upgrades instead of functionality, unknown authors behind the named, burn-errors, problems with the BIOS and during the system-startup resp. boot, flush and reset, intransparent boot-processes, hard undestandable process-names (partial standarizement by UNIX/Linux), unmushed nets (failsafed mushed nets), video- and voice-recording, judge-microphons, observing satellite technique (see under links), spanish flies, night viewers, evaluation of such recordings (audit, protocolling files), text- and image-manipulation, manipulation of websits by webhoster, instability, system-breakdowns, broken USB-Sticks (secure umount and never before, fsck), usage of USB-hubs instead of prolonging USB-cables only, manipulated electric meter and cables (UPS: unbreakablel power supply), ineffective encryption through non scientific based cryptograhic methods from highschools, the search for important function-keys,iweak point human, insufficient set of (security-) system-commands, hangons and newstarts, anomal login attempts (LADS - login anomally detection system), inactual alarms and warnings, installation of malware by the opening of e-mail-attachements, unsigned installation from anywhere, installation by everyone, inportability, defect peripherals and hardware, restricted presentation of websides, keylogger and other malware, wiretrapping bedbugs (from USB-cards and other devices), hack of sensible data from USB-sticks through their microcontroller, crack of WLAN-encryption-keys, spy-nets, false email-sender-addresses (disabled browser-cache, header of email-source-text, digital signatures by public signature-keys, de-Mail), DoS-attacks, root-rights providing buffer-overflows (bugs),
proprietary software (opensource against liablity, more clearance of question about liablity), cost-traps (here: billing by handies and SMS, overread of additional parts of contracts and the conditions), blackmail for unlocking suddenly locked computers (see our report under links), abuse of copyrights and patents, cult for criminals, billions hard investment into spying software and techniques, missing, confusing or the fluctuating IT-security-concept, hard-disk-scans, defragmentation (unnecessary for many UNIX-file-systems), harddrives (instead of MC-SSD, cite: "A magentic harddrive is much to risky to intrust data. Although a lot of improvements took place, who has not heart or - in worst cases - made the experience of lost data. Therefore enough reasons are relevant." (source: poshtar@datensicherx.com, 13.05.2014)), the demand for a registry, registry-errors (UNIX-systems have no registry), degeneracy of the registry, suddenly or inpredictable lost files, explosion (of net-adapter), fire (net-adapter, porous PC-lautspeaker-cable, ...), your own ununderstandable blackened company (enlighted by our PHP-MySQL-company management Mycompanies), virtual blackmail by encrypting harddrives against ransom, shooting through unmanned flying objects as a technical response to stored data, kontermination (through chipsets, preventable by IGP and all-in-one-mainboards) and radiation, WLAN-radiation (see our linkside), CRT-radiation, CD-burner-radiation, netadapter-radiation, warning high SAR-value (handies), zero-emission (reflectable monitor emissionf or example by special PCMCIA-cards prevented by special editors like the zero emission pad), hardware-recognigtion (standarized driver, Kernel ver. greater 2.6.30), infiltration of social networks, handy-hunts through nets, inconsistency (vs. everlasting science), need for upgrades (new tarballs, zip-archives, functionality), updates, patches and bugfixes (vs. functionality), browser with outdated ssl3.0 (modern usage is provided by TLS), changeovers to different security software, missing changelogs, software-overload on harddisc (Opensource, independency-checks, other introduced methods), hacker (STATE-NEW lined iptables-blocking), large holes in firewalls (iptables block-rate), intrusion and valdalism, viruses (access-rights of UNIX-filesystems), freak (patch or prefer browsers like Firefox or Konqueor instead), abuse by virus scanner (standard opensource clamav), worms, rootkits (rkhunter) resp. botnets and trojans (no botnets and no trojans by correct usage of the OWNER-concept of iptables), manipulation by system-administrators upon software, files and configurations, ddos-attacks (almost on the base of bots and trojans), inactual alarms, false-alarms, forgotten or coded warnings and error-messages, ad- and spyware as much as Trackingscripts (firefox-addons), Driveby-Downloads, Canvas Fingerprinting (see under online check), forced acquisition because of truncated customer support for old operating systems (lifetime installation-support for all mdv/mdk over "pointed 1-" to "pointed 0" versions), product-manufacturing fault right on the surface of installation-CD/-DVD, aggressive marketing, need of updates and upgrades instead of functionality, unknown authors behind the named, burn-errors, problems with the BIOS and during the system-startup resp. boot, flush and reset, intransparent boot-processes, hard undestandable process-names (partial standarizement by UNIX/Linux), unmushed nets (failsafed mushed nets), video- and voice-recording, judge-microphons, observing satellite technique (see under links), spanish flies, night viewers, evaluation of such recordings (audit, protocolling files), text- and image-manipulation, manipulation of websits by webhoster, instability, system-breakdowns, broken USB-Sticks (secure umount and never before, fsck), usage of USB-hubs instead of prolonging USB-cables only, manipulated electric meter and cables (UPS: unbreakablel power supply), ineffective encryption through non scientific based cryptograhic methods from highschools, the search for important function-keys,iweak point human, insufficient set of (security-) system-commands, hangons and newstarts, anomal login attempts (LADS - login anomally detection system), inactual alarms and warnings, installation of malware by the opening of e-mail-attachements, unsigned installation from anywhere, installation by everyone, inportability, defect peripherals and hardware, restricted presentation of websides, keylogger and other malware, wiretrapping bedbugs (from USB-cards and other devices), hack of sensible data from USB-sticks through their microcontroller, crack of WLAN-encryption-keys, spy-nets, false email-sender-addresses (disabled browser-cache, header of email-source-text, digital signatures by public signature-keys, de-Mail), DoS-attacks, root-rights providing buffer-overflows (bugs),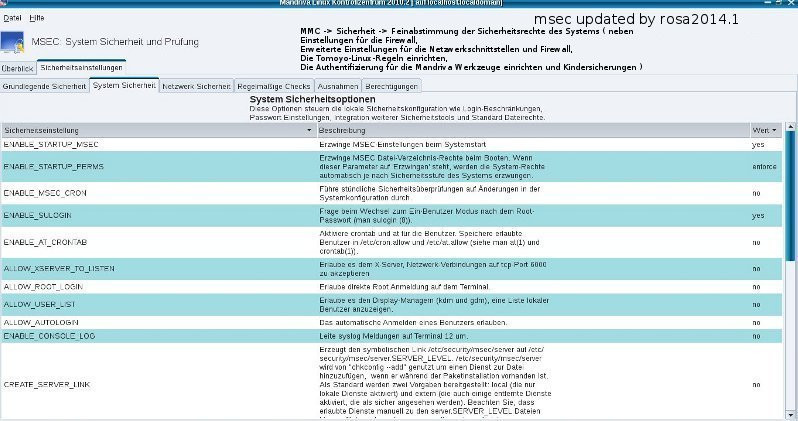
 the possibilities to build transparent rules, but you have to find out the correct or effective iptables-/ipchains from a set out of a lot of ineffective, bad structured or just false ones. Intelligent file systems like those for UNIX (resp. Linux) do not need any defragmentation as there are quit no fragments created, source. SuSE 7.3 reference manual. The same for SSD no defragmentation can be made for not having any read/write-heads.
the possibilities to build transparent rules, but you have to find out the correct or effective iptables-/ipchains from a set out of a lot of ineffective, bad structured or just false ones. Intelligent file systems like those for UNIX (resp. Linux) do not need any defragmentation as there are quit no fragments created, source. SuSE 7.3 reference manual. The same for SSD no defragmentation can be made for not having any read/write-heads.